



Key Intelligence Signals:
Impulse Team Operating Affiliate Program to Scam People at Global Level
Summary:
In a recent observation, a researcher detected years long scamming operation, led by a threat actor named Impulse Team, based in Russia. The threat actor is running an affiliate program known as the Impulse project, the same project was advertised on a Russian forum. Affiliate programs attract more threat actors to be part of the program and this program grew enough that the number of affected victims crossed a thousand and the whole scam happened at the global level. Further research revealed that the threat actor used Twitter’s DM to lure the victims into visiting the fake website. The message via Twitter’s DM informed victims about winning 0.7 bitcoin, which is worth 21,190 USD, to withdraw the amount, the victim needs to visit the given link and register to withdraw the whole amount. After registration is done, the victim is asked to make a deposit of 0.01 BTC (that is 270USD) on mentioned Bitcoin wallet address for account activation. There were more than a thousand websites with exact same dummy content that belonged to the Impulse project. The same luring technique was used on another micro-blogging site, Mastodon, similar to Twitter. The Impulse Team operates a project where new affiliates can join by subscribing to their service. Affiliates register their own domain names and configure them with scripts, provided by the Impulse Team. Each affiliate operates independently and receives a single database for their websites. Victims’ credentials work across all websites, operated by the same affiliate. The project involves fees for joining and a percentage of fraudulent transactions goes to the Impulse Team.
Insights:
We have observed unknown threat actors employing a similar campaign strategy. In this case victims are approached via WhatsApp call, then manipulates unsuspecting victims into investing small sums of money on fraudulent trading websites. Initially, the perpetrators provide victims with modest returns to establish a sense of trust, once trust is established, the perpetrators lure victims into investing larger amounts, directing them to various fake bank accounts or cryptocurrency wallets. By the time victims start suspecting the ongoing scam, the unknown threat actor withdraws whole amount and disappears.
The U.S. National Security Agency (NSA) stated in a press release that it has partnered with five U.S. and Republic of Korea agencies to release a cybersecurity advisory (CSA) titled, “North Korea Using Social Engineering to Enable Hacking of Think Tanks, Academia, and Media.” The Reconnaissance General Bureau (RGB), North Korea’s primary intelligence organization, is noted in the advisory as being in charge of spear-phishing efforts, noting that North Korean cybercriminals have a history of conducting spear-phishing attacks while acting as legitimate journalists, scholars, or other people with established connections to North Korean political circles. The DPRK uses social engineering to gather information on geopolitical developments, foreign policy initiatives, and diplomatic endeavours that are relevant to its goals, by obtaining unauthorized access to its targets’ private papers, studies, and communications.
The statement named the threat actors associated with these attacks as Kimsuky, Thallium, APT43, Velvet Chollima, and Black Banshee. To establish trust with their targets, threat actors frequently pose as legitimate journalists. Once trust has been established, the actors frequently probe their targets about current circumstances and U.S. authorities’ insights into North Korean matters. In email conversations, the actors will also pretend to be academics, think tank advisers, and government representatives. Once fraudsters get the target’s email address, they will eventually send a phony email asking them to reset their password and threatening to permanently erase their account if they don’t. All prospective targets are advised by the NSA to think about the hazards before clicking on links delivered through email from shady sources. They also advise educating staff members about spear-phishing.
PowerDrop, a new malicious PowerShell script, was discovered by researchers to have infected machines at an unspecified US aerospace defense contractor. The malware uses a combination of Windows PowerShell script and Windows Management Instrumentation (WMI) to create a new remote access trojan (RAT). The usage of PowerShell for remote access is used by numerous APTs from numerous countries, however, researchers have noted, that this specific malware hasn’t surfaced before and that it represents the middle ground between “off-the-shelf” code and advanced tactics used by Advanced Persistent Threat (APTs) Groups. Though attribution remains inconclusive so far, the hack has likely originated from a nation-state-backed group, according to the researchers. As of now, it is unknown whether this incident is part of a larger campaign targeting multiple organizations, but the list of the most likely perpetrators contains the usual suspects from China and Russia to Iran and North Korea, albeit is not limited to these cyber players.
Russian cyber auxiliary NoName057(16) has been conducting a distributed denial-of-service (DDoS) and defacement campaign against Lithuanian websites this week. Recently the group announced that it will be attacking Lithuania in response to the country’s continued support of Ukraine and the decision to classify Russia as a terrorist state for its numerous crimes, committed during the invasion of Ukraine. The Lithuanian government has released a statement reading that “The war against Ukraine by the Russian Federation is a genocide of the Ukrainian nation, carried out by Russia. The Russian Federation is a country that supports and executes terrorism,” which led the group to launch the attacks.
The group claims it has attacked thirty-nine Lithuanian websites, since May 29th, however, several attacks by the group have also targeted neighbouring Latvia, which has a very similar attitude to Russia, given its history of violent occupation and repression by the Soviet Union. All three Baltic countries in fact share a history of being targets of unprovoked Russian aggression and hostile takeover in the last century. Following the disbanding of the Soviet Union, all three countries sought protection of NATO and membership in the European Union, in order to reconnect to their historical roots, being incorporated in the Western world. Their own experience with Russia leads them to be the firmest supporters of Ukraine in its plight against Russian aggression, which puts a big target on all of them. However, in the recent campaign, given the relative unsophistication of the threat actor, so far, the attacks seem to be on the nuisance level and are dispersed across sectors that include agriculture, finance, and energy, with NoName seeking easy targets. This however does not mean the Baltic countries can get complacent about cyber security since they are likely to receive the attention of top Russian government-sponsored APTs.
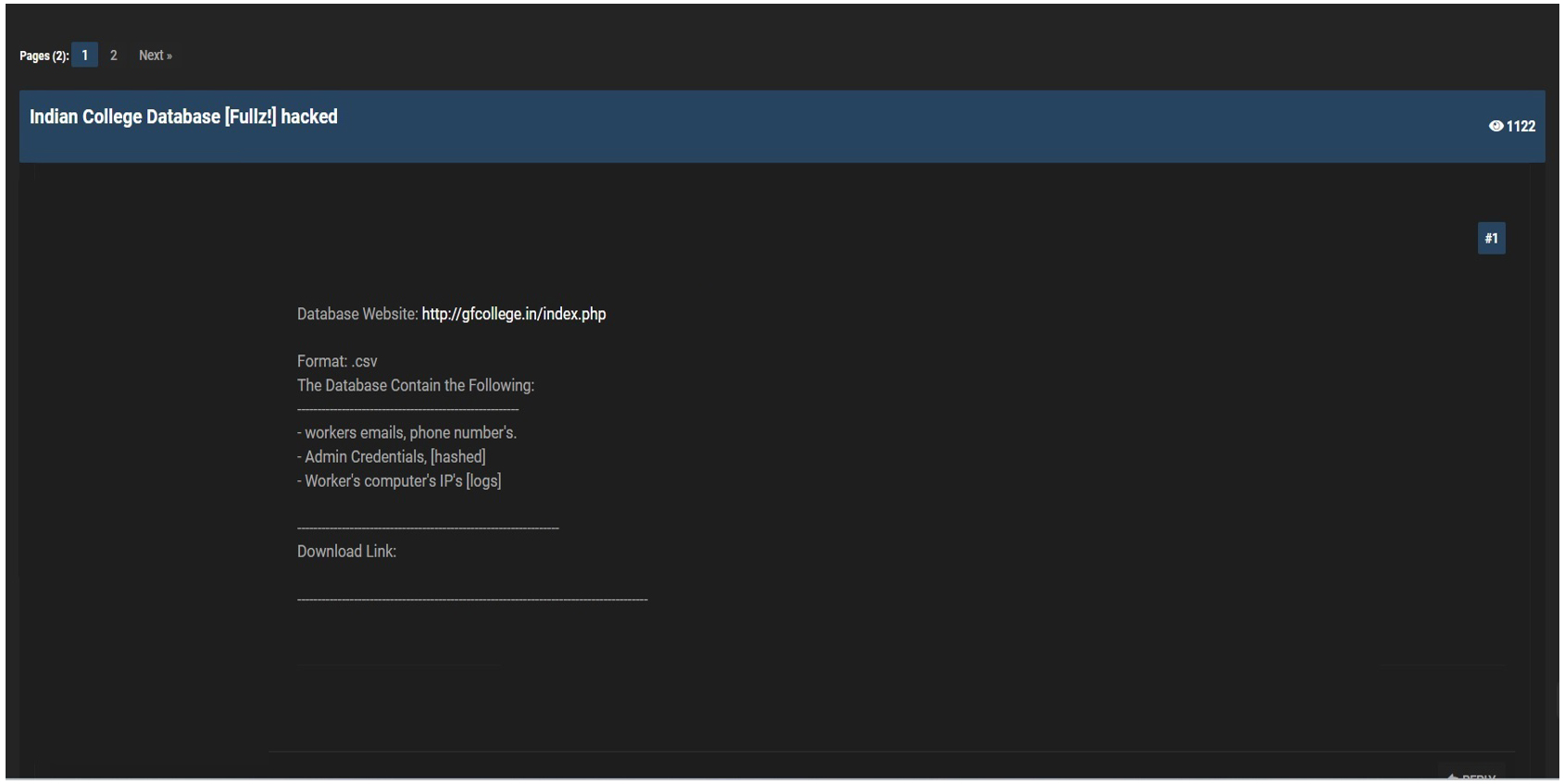
CYFIRMA Research team observed a potential data leak related to Gandhi Faiz-E-Aam College, (www[.]gfcollege[.]in). Gandhi Faiz-E-Aam College is a company that operates in the Education industry. It is headquartered in India. The exposed data comprises a range of sensitive information, including employees’ email addresses, phone numbers, IP logs of their computers, administrative credentials (in hashed form), and other confidential data.
Source: Underground forums