



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Faust ransomware in the wild while monitoring various underground forums as part of our Threat Discovery Process.
Faust Ransomware
Faust is a variant of the Phobos ransomware family which was first seen at the end of 2022. The Phobos ransomware family, originating in 2019, is infamous for its encryption of victims’ files, marking a significant presence in cybercrime operations.
Researchers found a document with VBA script that spreads the FAUST ransomware, a Phobos variant. The attackers utilized the Gitea service to store several files encoded in Base64, each carrying a malicious binary. Once injected into a system’s memory, these files trigger a file encryption attack.
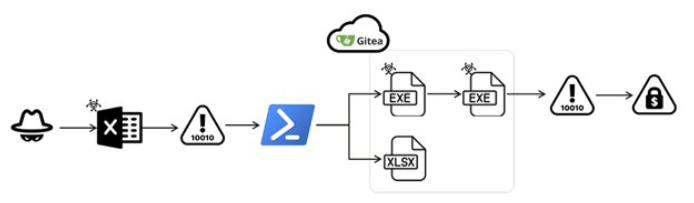
Attack flow (Source: Surface web) Document Analysis
In the identified XLAM document, a VBA script is embedded (It appears that threat actors may have utilized phishing methods to deliver the document).
When the document is opened, the script initiates PowerShell through the “Workbook_Open()” function. It proceeds to fetch Base64-encoded data from Gitea, decoded into a harmless XLSX file. This file is saved in the TEMP folder and automatically opened, creating a deceptive appearance of completion and safety, which can mislead users.
The image below reveals the code extracted from the variable “SkSLjvNc.” The PowerShell script downloads data from hxxps://gitea[.]com/JoinPokingo/JingaPol/raw/branch/main/cfmifs_CRPT[.]txt. It then extracts the specific malicious portion from “cfmifs_CRPT[.]txt” using the pattern “DICK{(.*)}DICK” and decodes the result from Base64.
Finally, a random folder is chosen within “$env:APPDATA..\Local,” and two randomly generated characters are added to the folder name, providing it with a new identity. The executable, named “AVG update.exe,” is then stored in this freshly named folder.
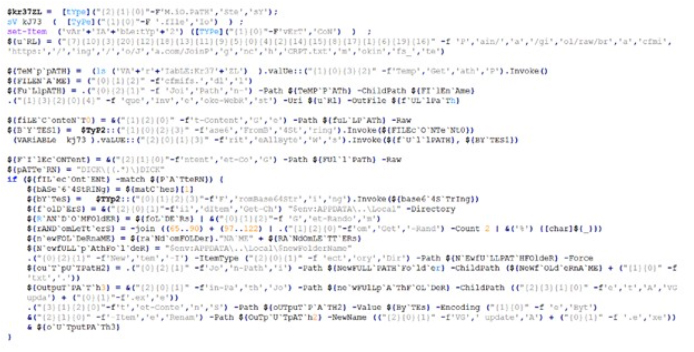
The PowerShell script(Source: Surface web)
EXE File Downloader
The “AVG update.exe” executable works as a downloader, designed with extra code to avoid detection and make analysis difficult. It uses a technique to inject the malicious code into a new process by allocating Read-Write-Execute (RWE) memory. Furthermore, the file encodes all its strings and combines them with specific hexadecimal keys before using them.
Below figure shows the assembly code for obtaining a DLL name from the encoded string “blogaudit” utilizing XOR hex keys.
“blogauditblo” ^ 0x29293d292439575B5A262023 = “KERNEL32.DLL”
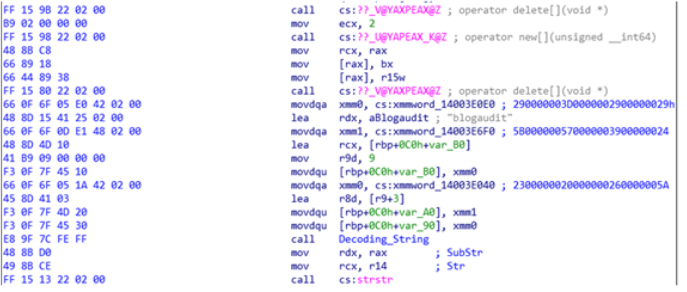
Decoding the DLL name (Source: Surface web) It includes the following functions:
The attacker reserves a portion of the target process’s memory, inserts malicious code, and invokes the payload’s entry point.
Ransomware:
The ransomware verifies the Mutex object to confirm singular process execution. It establishes persistence by creating a registry entry in “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” and duplicating itself into two directories: “%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup” and “C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup.”
These folders play a role in Windows startup settings. The first is personalized for users, initiating programs at their login, while the second is system-wide, impacting all users during system startup. They are essential for the automatic execution of the FAUST Ransomware.
To prevent system damage, double encryption of files, or encryption of its ransom information, the ransomware includes an exclusion list:
Similar to the typical behavior of Phobos variants, FAUST ransomware preserves the decryption function within its configuration.
It also initiates multiple threads to perform various tasks. These tasks include deploying encryption, scanning logical drives, searching for network/sharing resources, scanning files individually, and explicitly seeking database-related files (such as fdb, sql, 4dd, 4dl, abs, abx, accdb, accdc, accde, adb, adf, ckp, db, db-journal, db-shm, db-wal, db2, db3, dbc, dbf, dbs, dbt, dbv, dcb, dp1, eco, edb, epim, fcd, gdb, mdb, mdf, ldf, myd, ndf, nwdb, nyf, sqlitedb, sqlite3, and sqlite).
The ransomware encrypts the file and encrypted files carry the extension “.id[<<ID>>- 3512].[[email protected]].faust.”, additionally it creates info.txt and info.hta files in the directories containing the encrypted files.
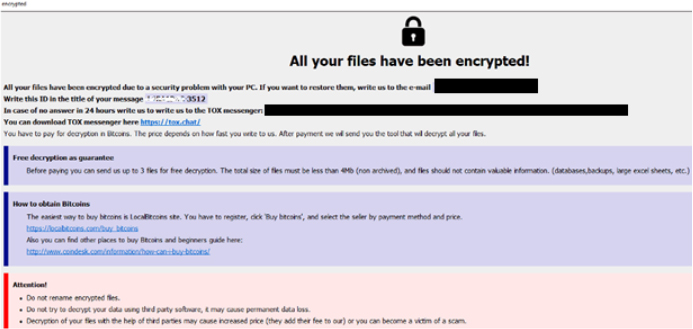
Ransom note of Faust (info.hta) (Source: Surface web)
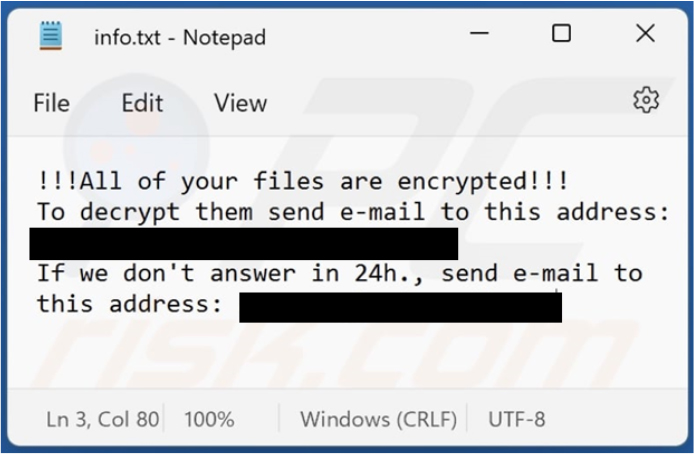
Screenshot of Faust’s text file (“info.txt”) (Source: Surface web)
Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1053: Scheduled Task/Job |
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1055: Process Injection | ||
| T1134: Access Token Manipulation | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1134: Access Token Manipulation | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.001: Hide Artifacts: Hidden Files and Directories | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056: Input Capture | ||
| 6 | TA0007: Discovery | T1012: Query Registry |
| T1016: System Network Configuration Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1005: Data from Local System |
| T1056: Input Capture | ||
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
ETLM Assessment:
CYFIRMA’s assessment, based on available information, suggests that the FAUST ransomware variant, being a member of the notorious Phobos family, will likely continue to evolve and adopt new tactics in trying to bypass cybersecurity measures. With its sophisticated encryption techniques and ability to target a wide range of industries, we anticipate an increase in cyberattacks using FAUST ransomware in future. Organizations should prioritize robust cybersecurity measures and regular threat intelligence updates to mitigate the risk of falling victim to such attacks.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Sigma Rule
title: Boot Configuration Tampering Via Bcdedit.EXE tags:
– attack.impact
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection_img:
– Image|endswith: ‘\bcdedit.exe’
– OriginalFileName: ‘bcdedit.exe’ selection_set:
CommandLine|contains: ‘set’ selection_cli:
– CommandLine|contains|all:
– ‘bootstatuspolicy’
– ‘ignoreallfailures’
– CommandLine|contains|all:
– ‘recoveryenabled’
– ‘no’
condition: all of selection_* fields:
– ComputerName
– User
– CommandLine falsepositives:
– Unlikely level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Remote Access, Espionage
Threat Actor: Patchwork
Target Technology: Android OS
Target Geographies: Pakistan, India
Active Malware of the Week
This week “VajraSpy” is trending.
Summary
Researchers have identified a new cyberespionage campaign linked to the Patchwork APT group. The campaign utilized An Android remote access trojan (RAT) known as VajraSpy was found in 12 malicious applications, six were available on Google Play containing VajraSpy RAT codes, and additional six were spread in the wild. The Google Play apps garnered over 1,400 installs and remain accessible on alternative platforms. Weak operational security in one of the apps resulted in the exposure of victim data, enabling the researchers to geolocate 148 compromised devices in Pakistan and India. These locations are indicative of the likely actual targets of the attacks.
VajraSpy
VajraSpy, a malware, has a range of espionage functionalities that can be expanded based on the permissions granted to the app bundled with its code. Its capabilities are summarized as follows:
Decoding VajraSpy: Malicious Apps on the Prowl
In January 2023, researchers identified a trojanized news app named Rafaqat تقافر (the Urdu word translates to Fellowship), designed to steal user information. Subsequent investigation revealed several other applications sharing the same malicious code as Rafaqat تقافر, some of which had identical developer certificates and user interfaces. A total of 12 trojanized apps were analysed, with six (including Rafaqat تقافر) initially available on Google Play and the remaining six discovered elsewhere. The Google Play apps were collectively downloaded over 1,400 times.
The researchers suggest that the threat actors likely employed a romance scam tactic to trick victims into installing the malware. All apps on Google Play were uploaded between April 2021 and March 2023. Notably, they share similarities such as being messaging applications and being bundled with the VajraSpy RAT code. MeetMe and Chit Chat have identical user login interfaces, while Hello Chat (not on Google Play) and Chit Chat share the same developer certificate. The apps’ appearance dates on Google Play range from April 2021 to March 2023, with Chit Chat being the most recent, appearing in March 2023. The following applications were previously available on Google Play but are no longer accessible on the platform:
In addition to the previously available Google Play apps, six more messaging applications were identified on VirusTotal. YohooTalk was the first, appearing in February 2022, followed by TikTalk in late April 2022.Researchers identified TikTalk and shared its download domain (fich[.]buzz). Subsequently, Hello Chat was uploaded in April 2023, and Nidus and GlowChat in July 2023. Lastly, Wave Chat appeared in September 2023. All six of these trojanized apps share the same malicious code as those initially found on Google Play. The Following apps found outside of Google Play are fraudulent messaging applications.
VajraSpy, a customizable trojan typically posing as a messaging app, is employed for user data exfiltration. Researchers have observed consistent class names across all instances of the malware, even in samples discovered by other researchers.
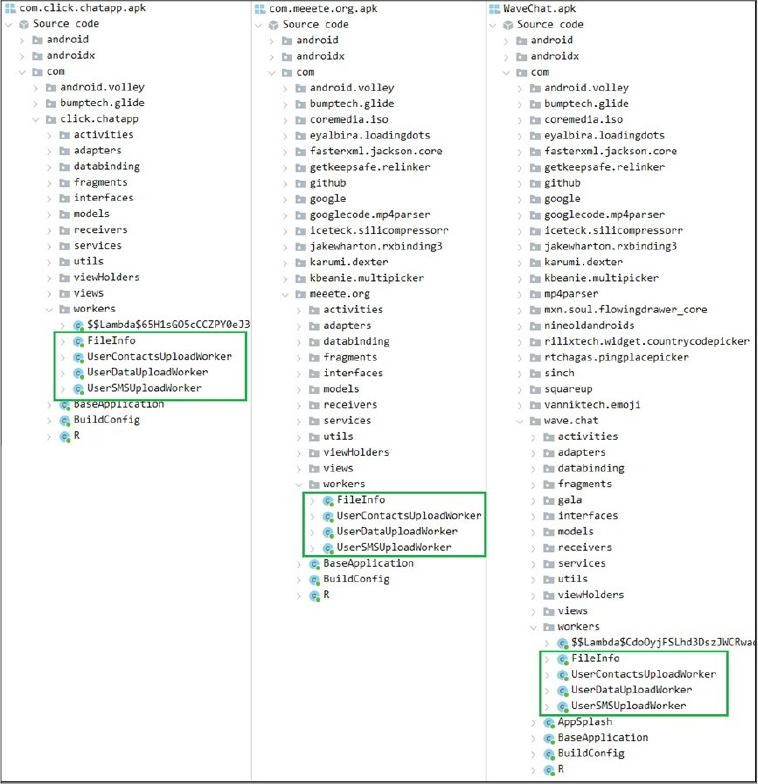
VajraSpy’s malicious capabilities vary depending on the permissions granted to the trojanized application. To facilitate analysis, researchers have categorized the trojanized apps into three groups.
Group 1: Trojanized messaging applications with basic functionalities
The initial group consists of trojanized messaging applications that were once on Google Play, such as MeetMe, Privee Talk, Let’s Chat, Quick Chat, GlowChat, and Chit Chat, along with Hello Chat, which wasn’t available on Google Play. Despite offering standard messaging features, these apps mandate users to create accounts. Account creation involves phone number verification through a one-time SMS code. However, VajraSpy operates irrespective of account creation status. The potential purpose of verifying the phone number may be to ascertain the victim’s country code, though this is speculative. These apps share the same malicious functionality, being capable of exfiltrating the following:
Certain apps have the capability to exploit permissions to access notifications. With this permission, VajraSpy can intercept messages from various messaging applications, including SMS messages. The attackers utilized Firebase Hosting, a web content hosting service, as the Command and Control (C&C) server. Besides functioning as the C&C server, it was employed to store victims’ account information and exchanged messages. The researchers reported the server to Google, as it falls under Firebase, a service provided by Google.
Group 2: trojanized messaging applications with advanced functionalities
Group Two includes TikTalk, Nidus, YohooTalk, Wave Chat, and VajraSpy variants like Crazy Talk. Similar to Group One, these apps prompt users to create accounts and verify phone numbers through a one-time SMS code, with VajraSpy running regardless of account creation status. Apps in Group Two have enhanced capabilities compared to Group One. In addition to Group One’s features, they can utilize built-in accessibility options to intercept communication in WhatsApp, WhatsApp Business, and Signal.
VajraSpy logs and uploads this communication to the Firebase-hosted C&C server, showing real-time logging of WhatsApp communication. These apps can spy on chat communications, intercept notifications, and exfiltrate received notifications and exchanged messages in WhatsApp, WhatsApp Business, and Signal.
Wave Chat, part of Group Two, stands out with additional malicious capabilities. Upon launch, it requests accessibility services, automatically enabling necessary permissions and expanding VajraSpy’s device access. In addition to previous functionalities, Wave Chat can also
It receives C&C commands to take pictures and record audio, either for 60 seconds (by default) or for the amount of time specified in the server response, sending the data via POST requests to the C&C. Wave Chat employs a Firebase server for commands and storing user messages, SMS messages, and contact lists, while a different C&C server, using Retrofit (Retrofit is an Android REST client in Java that makes it easy to retrieve and upload data via a REST-based web service), handles other exfiltrated data through unencrypted HTTP uploads.
Group 3: non-messaging applications
The only application in Group Three is the one that initiated this research – Rafaqat تقافر. Unlike other Group Three apps, it doesn’t serve as a messaging app but claims to deliver news. As news apps typically don’t request intrusive permissions, Rafaqat تقافر’s malicious capabilities are limited compared to other analyzed apps.
Uploaded on October 26th, 2022, on Google Play by a developer named Mohammad Rizwan, Rafaqat تقافر gained over a thousand installs before removal. Interestingly, the same developer submitted two more apps with an identical name and malicious code weeks before Rafaqat تقافر, but they were not published on Google Play. The app requires a phone number for login but lacks number verification, allowing the use of any phone number. Rafaqat تقافر can intercept notifications and exfiltrate contacts and files with specific extensions (.pdf, .doc, .docx, .txt, .ppt, .pptx, .xls, .xlsx, .jpg, .jpeg, .png, .mp3, .Om4a, .aac, and .opus).
INSIGHTS
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | Persistence | T1398: Boot or Logon Initialization Scripts |
| 2 | Discovery | T1420: File and Directory Discovery |
| T1422: System Network Configuration Discovery | ||
| T1426: System Information Discovery | ||
| T1418: Software Discovery | ||
| 3 | Collection | T1533: Data from Local System |
| T1430: Location Tracking | ||
| T1636.002: Protected User Data: Call Logs | ||
| T1636.003: Protected User Data: Contact List | ||
| T1636.004: Protected User Data: SMS Messages | ||
| T1517: Access Notifications | ||
| T1429: Audio Capture | ||
| T1512: Video Capture | ||
| T1417.001: Input Capture: Keylogging | ||
| 4 | Command and Control | T1437.001: Application Layer Protocol: Web Protocols |
| T1481.003: Web Service: One-Way Communication | ||
| 5 | Exfiltration | T1646: Exfiltration Over C2 Channel |
| 6 | Impact | T1641: Data Manipulation |
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that in the evolving landscape of cybersecurity, cybercriminals are increasingly leveraging social engineering as a formidable weapon, indicating a trend of collecting private information from high-profile users. The multifaceted nature of VajraSpy’s espionage functionalities, ranging from data theft to the interception of encrypted communications and even the potential compromise of the device’s camera for surveillance purposes, suggests ongoing and future risks to both personal privacy and sensitive corporate information. Given its sophisticated and adaptive nature, there is an anticipation that this campaign or threat actor may extend their target geographies in the future.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
Security Awareness training should be mandated for all company employees. The training should ensure that employees:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Nation-based Threat Actor Breached into Cloudflare Network
Summary:
In a recent observation Cloudflare revealed that in November 2023, they detected a security breach, nine days after a threat actor utilized credentials obtained from the October Okta hack to access their internal systems. The stolen login information, including an access token and three service account credentials, had not been rotated post-Okta incident, allowing the attackers to conduct reconnaissance activities on Cloudflare’s systems from November 14. Although network segmentation prevented access to certain critical systems, the attackers managed to infiltrate an AWS environment and Atlassian Jira and Confluence. They searched the wiki for specific keywords related to Cloudflare’s network and accessed a total of 36 Jira tickets and 202 wiki pages. The attackers created and maintained an Atlassian account for persistent access, installed the Sliver Adversary Emulation Framework to move laterally within the environment, and attempted access to non-production servers.
While they viewed and downloaded source code repositories related to backups, network configuration, and identity management, Cloudflare promptly rotated encrypted secrets and terminated unauthorized accounts upon detection. The company implemented firewall rules to block attacker IP addresses and removed the malicious framework. Cloudflare confirmed no evidence of access to critical systems beyond the Atlassian suite and initiated comprehensive security measures, including rotating credentials, triaging systems, and reimagining machines across its global network. Despite the attack’s goal to gain insight into Cloudflare’s infrastructure, no further compromise was detected following investigations.
Relevancy & Insights:
The breach occurred solely due to the theft of credentials in a prior attack into Okta from where the threat actor fetched credentials and orchestrated another attack in November. Similar to this attack, threat actors whether they are ransomware groups or advanced persistent threat (APT) actors, are exploiting stolen credentials documented in stealer logs to gain unauthorized access to internal networks and accomplish their objectives.
ETLM Assessment:
The threat actor believed to be nation-based, employed stolen credentials to carry out their malicious agenda. The increasing prevalence of stealer logs poses a growing threat, with these logs frequently utilized for cyber-attacks across various industries. Major compromises in the threat landscape have been attributed to the exploitation of stealer logs. Implementing credential rotation and enforcing strict policies regarding the use of company laptops exclusively for company purposes are essential best practices. It is imperative to adopt these measures to mitigate the risk of successful attacks and limit the opportunity for threat actors to exploit credentials obtained from stealer logs.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
US agencies warn of Chinese cyber threat in a Congressional hearing
The directors of the FBI, NSA, and the Cybersecurity and Infrastructure Security Agency have warned of the growing Chinese cyber threat at a recent congressional hearing. According to their statement, the Volt Typhoon hacking group is planting malware bombs on network routers and other internet-connected devices that, if triggered, could disrupt water, power, and rail services, possibly causing widespread chaos or even injuring and killing US citizens.
FBI Director Christopher Wray told Congress that the Chinese government is targeting US critical infrastructure, including the power grid, water treatment facilities, and pipelines, in order to stage future destructive attacks. According to the agency, China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities, if and when China decides the time has come to strike. The new wave of Chinese hackers has diversified their targets beyond political and military entities. These groups have positioned themselves across civilian infrastructure in a way that gives it a possibility to wreak havoc on the general public in the event of a conflict.
According to CISA, a cyber-attack on infrastructure could cause massive disruption. The agency chief warned of a Colonial Pipeline-like scenario (2021 cyber-attack that shut down gas to the Eastern Seaboard for several days) on a massive scale. If not one pipeline, but many pipelines were to be disrupted and telecommunications were to go down or trains to get derailed, the disruption could be of catastrophic consequences.
ETLM Assessment:
Last year, Volt Typhoon and other APTs like Mustang Panda have been focused on countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has allegedly been targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. As we have warned in an earlier report, given the increasingly assertive Chinese posturing, it was likely that Beijing’s hackers were trying to position themselves in a way it could try to paralyze U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is inherent part of Chinese military doctrine and targeting of critical infrastructure in Guam could affect U.S. military operations in significant way.
Netherlands calls out Chinese hacking campaign
Dutch intelligence agencies have disclosed that Chinese state-sponsored hackers gained access to a computer network used by the Dutch Ministry of Defense last year. The campaign has been uncovered on devices on a network used for unclassified research and development. For the first time, the Dutch Defense Ministry has chosen to make public a technical report on the working methods of Chinese hackers. According to a statement by the ministry, it is important to publicly attribute such espionage activities to China, in order to increase international resilience against this type of cyber espionage.
ETLM Assessment:
The recent moves by Western countries to a more balanced trade relationship with China is pushing Beijing to double down on covert efforts to illegally gain intellectual property. China is a global champion in using cyber-attacks as a tool of statecraft, and the hands-on role of the government in the economy only reinforces the drive to use cyber-attacks for IP theft, even in matters that are of no military or dual use. China has a bigger hacking program than that of every other major nation combined, and any large company in industries outlined in Chinese development plans will need to invest into external threat landscape management solutions to stay ahead of relentless and repeated assaults by Chinese hackers.
The LockBit 3.0 Ransomware impacts the Manitou Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from France; (www[.]manitou-group [.]com), was compromised by LockBit 3.0 Ransomware. Manitou Group, headquartered in France, is a heavy equipment manufacturer specializing in forklifts, telehandlers, aerial work platforms, and warehousing equipment. The compromised data encompasses a broad spectrum of information, including specifications, equipment drawings, developments, sources, tests, program code, and electrical data. It also comprises client records containing addresses, telephone numbers, payment details, Non-Disclosure Agreements (NDAs), contracts, and postal correspondence. Additionally, employee records are compromised, which include Social Security Numbers (SSNs), residential addresses, phone numbers, email addresses, dates of birth (DOB), contracts, salary information, 401(k) forms, and other sensitive documents. Furthermore, financial data such as budgets, Ernst & Young (EY) audit results, balance sheets, tax returns, project calculations, year-to-date (YTD) reports, invoices, sales reports, and numerous other financial documents have been compromised. Moreover, working documentation including operational activities, projects, price lists, internal documents, marketing materials, service work details, and spare parts data are also affected. In total, the compromised data amounts to 400 GB.
The following screenshot was observed published on the dark web:
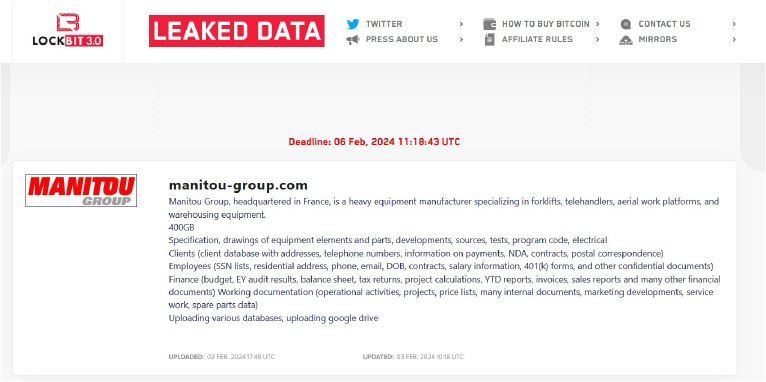
Source: Dark Web
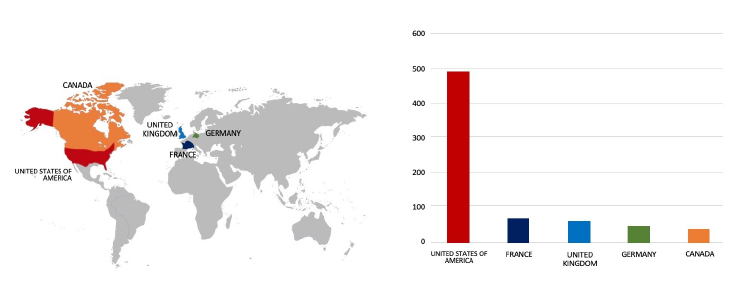
Relevancy & Insights:
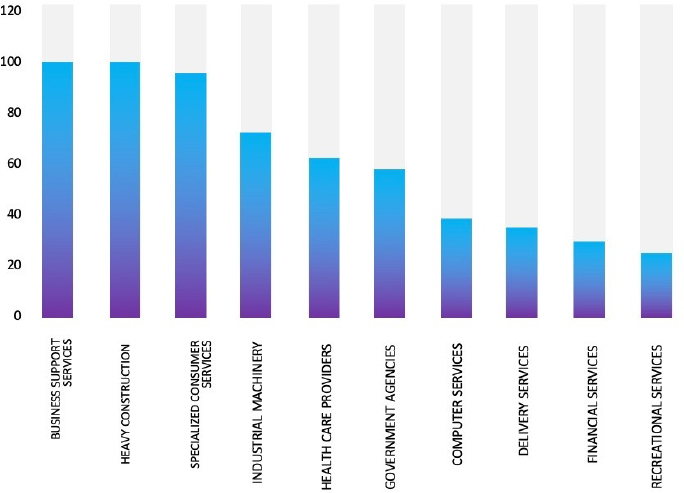
ETLM Assessment:
CYFIRMA’s assessment underscores the persistent and widespread threat posed by LockBit 3.0 Ransomware to companies worldwide. Our observations reveal an escalating pattern, wherein LockBit 3.0 Ransomware exploits vulnerabilities in diverse products to infiltrate systems, facilitating lateral movement within organizational networks. The recent cyber incident involving the Manitou Group; a French-based manufacturing company, highlights the pervasive global danger associated with this ransomware variant.
Vulnerability in AVEVA Edge
Summary:
The vulnerability allows a local user to compromise vulnerable system.
Relevancy & Insights:
The vulnerability exists due to the application loads DLL libraries in an insecure manner.
Impact :
A local user can place a specially crafted .dll file and execute arbitrary code on the victim’s system.
Affected Products: https[:]//www[.]aveva[.]com/content/dam/aveva/documents/support/cyber-security- updates/Security_Bulletin_AVEVA-2024-002.pdf
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
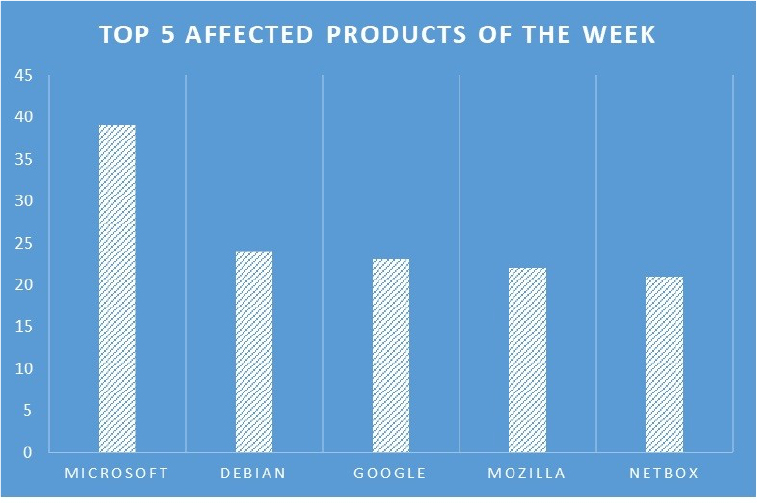
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
Hackers steal data of 2 million in SQL injection, cross-site scripting (XSS) attacks
Summary:
We observed that a threat group named ‘ResumeLooters’ has stolen the personal data of over two million job seekers after compromising 65 legitimate job listings and retail sites using SQL injection and cross-site scripting (XSS) attacks. The attackers mainly focus on the APAC region, targeting sites in Australia, Taiwan, China, Thailand, India, and Vietnam to steal job seekers’ names, email addresses, phone numbers, employment history, education, and other relevant information. The threat group ResumeLooters, since its beginning, in November 2023, attempted to sell the stolen data through Telegram channels. ResumeLooters primarily employs SQL injection and XSS to breach targeted sites, mainly job-seeking and retail shops.
Relevancy & Insights:
ResumeLooters conducts SQL injection, cross-site scripting (XSS) attacks for financial gains, attempting to sell stolen data to other cybercriminals via at least two Telegram accounts that use Chinese names, namely “渗透数据中心” (Penetration Data Center) and “万国数据阿力” (World Data Ali).
ETLM Assessment:
The utilization of Chinese-speaking groups and tools, such as the Chinese version of X-Ray, by ResumeLooters strongly suggests a potential connection to China. Assessments conducted by CYFIRMA indicate a notable likelihood of ResumeLooters continuing their endeavors to infiltrate companies on a global scale. Their primary objective appears to be securing considerable financial gains through the execution of SQL injection and cross-site scripting (XSS) attacks. This persistence and global focus underscore the severity of the threat posed by ResumeLooters and necessitate heightened vigilance and robust cybersecurity measures to mitigate their activities effectively.
Emirates Investment Bank Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential access to website sale related to Emirates Investment Bank, {www[.]eibank[.]com}. Emirates Investment Bank is an independent private bank based in Dubai. It offers a wide range of investment and banking services to an exclusive, but diverse, client base of high-net-worth individuals from across the region and worldwide. Access to the Emirates Investment Bank website is being offered for sale for 10,000 USD.

Source: Underground forums
Relevancy & Insights:
Financially motivated cybercriminals consistently monitor unprotected and vulnerable systems and applications, lured by the promise of monetary rewards. Many of these perpetrators’ frequent clandestine online forums, where they participate in discussions and transactions revolving around stolen digital assets. What distinguishes these cybercriminals from other groups driven by financial gains, such as ransomware or extortion groups, is their inclination towards operating discreetly. They exploit vulnerabilities in systems or applications to gain access to valuable data, which they then advertise for sale on underground forums. Subsequently, this unlawfully obtained data is repurposed by other attackers for their own campaigns.
ETLM Assessment:
An emerging threat actor known as JustAnon69, driven primarily by financial motives, is currently engaged in actively selling access to websites within dark forums. As per CYFIRMA’s assessment, organizations located in the United Arab Emirates, which possess insufficient security measures, are identified as potential targets by this specific threat actor.
CYFIRMA Research team observed a potential data leak related to Beamstart, {www[.]beamstart[.]com}. BEAMSTART is a global business networking app that offers a job board, business news and content, as well as career resources. The platform allows users to hire talent, promote their companies, raise capital, and form professional connections with people around the world. The compromised data includes Account IDs, Profiles, Names, Emails, Phone Numbers, Hashed Passwords, Usernames, City, Country, and other sensitive information. The total size of the compressed data file is approximately 81.6 MB.
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS