



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found LostInfo ransomware while monitoring various underground forums as part of our Threat Discovery Process.
LostInfo
Researchers discovered the LostInfo ransomware by late July 2024. This malicious software encrypts files and demands a ransom for their decryption.
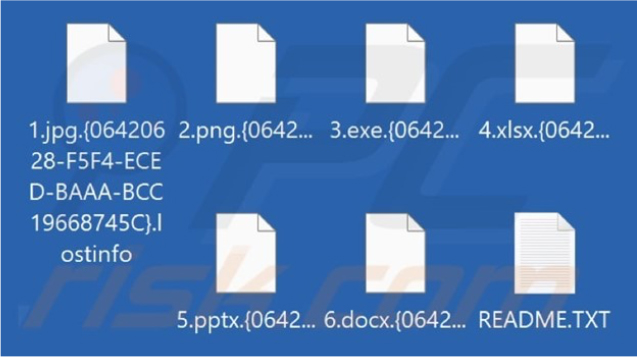
Upon execution, the LostInfo ransomware initiates an encryption process and alters their original names by appending a unique ID and the “.lostinfo” extension. Following the completion of encryption, it generates a file named “README.TXT,” which contains instructions for a ransom payment to restore access to the encrypted files.
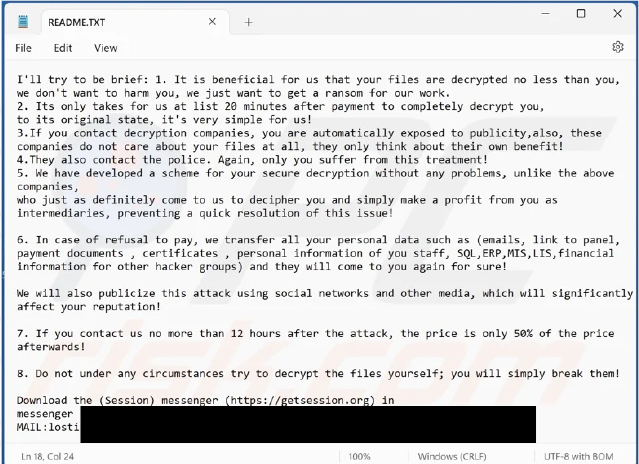
The ransom note left by ransomware informs victims that their files have been encrypted. It assures them of decryption after ransom payment and advises against seeking help from third parties.
To recover their data, victims are required to pay a ransom, though the amount is unspecified. If the attackers are contacted within 12 hours, the ransom amount will be reduced by 50%. If the victim refuses to pay, the attackers threaten to share their private and financial data with other cybercriminals.
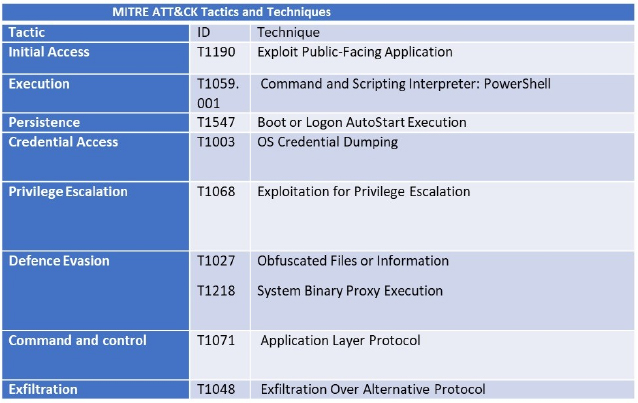
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070: Indicator Removal | ||
| T1134: Access Token Manipulation | ||
| T1222: File and Directory Permissions Modification | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056.001: Input Capture: Keylogging | ||
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1016: System Network Configuration Discovery | ||
| T1018: Remote System Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1005: Data from Local System |
| T1056.001: Input Capture: Keylogging | ||
| T1074: Data Staged | ||
| T1114: Email Collection | ||
| 9 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol | ||
| T1573: Encrypted Channel | ||
| 10 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
Based on the available data, CYFIRMA’s assessment indicates that the ransomware is likely to target a wide range of industries, including business services, construction, telecommunications, finance, banking and manufacturing, to maximize its ransom revenue. The ransomware’s focus on Windows systems, along with advanced techniques such as disabling system logs and deleting Volume Shadow Copies, poses a significant threat across these sectors. Furthermore, the group’s threat to share exfiltrated data with other cybercriminals highlights the broader, collaborative nature of their operations. There is also a notable risk that the ransomware may have already targeted regions such as the US, UK, Europe, Southeast Asia, and other economically developed nations to earn ransom.
SIGMA Rule:
title: Uncommon File Created In Office Startup Folder tags:
– attack.resource_development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
– TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\STARTUP’
filter_exclude_word_ext: TargetFilename|endswith:
– ‘.docb’ # Word binary document introduced in Microsoft Office 2007
– ‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
– ‘.docx’ # Word document
– ‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
– ‘.mdb’ # MS Access DB
– ‘.mdw’ # MS Access DB
– ‘.pdf’ # PDF documents
– ‘.wll’ # Word add-in
– ‘.wwl’ # Word add-in selection_excel_paths:
– TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
– ‘.xll’
– ‘.xls’
– ‘.xlsm’
– ‘.xlsx’
– ‘.xlt’
– ‘.xltm’
– ‘.xlw’ filter_main_office_click_to_run:
Image|contains: ‘:\Program Files\Common Files\Microsoft Shared\ClickToRun\’ Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps:
Image|contains:
– ‘:\Program Files\Microsoft Office\’
– ‘:\Program Files (x86)\Microsoft Office\’ Image|endswith:
– ‘\winword.exe’
– ‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_* falsepositives:
– False positive might stem from rare extensions used by other Office utilities. level: high
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Stealing financial information, Data exfiltration
Target Technology: Android OS
Target Geography: Turkey Target Industry: Banks
Active Malware of the Week
This week “BlankBot” is trending.
BlankBot
Researchers have discovered a new Android banking trojan called BlankBot that impersonates utility applications and is not associated with any known malware families, targeting Turkish users to steal financial information. As identified on July 24, 2024, BlankBot is actively under development. It exploits Android’s accessibility service permissions to gain full control over infected devices, posing a significant threat to users’ financial security. The malware logs everything on the device, including SMS texts, sensitive information, and a list of applications used. It also conducts custom injections to steal banking information, such as payment card data and device lock patterns. Initial communication with its controller starts with a “GET” request, where HTTP headers provide device details like battery level, screen size, model, manufacturer, and OS version, followed by communication over port 8080 via a WebSocket connection. While primarily targeting Turkish users, no specific financial institutions were identified, suggesting potential for broader distribution in campaigns against users in different countries.
Technical Analysis
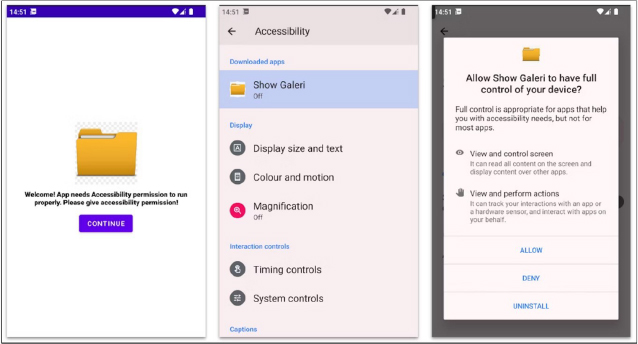
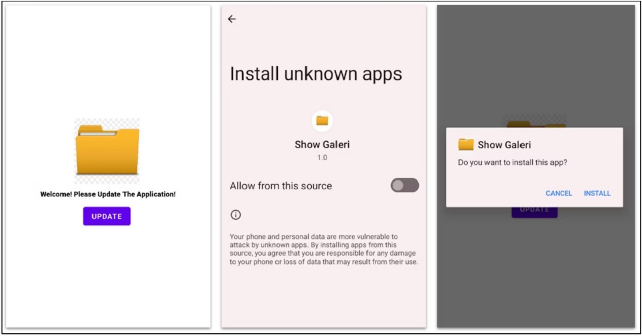
The initial delivery method of the BlankBot APK remains unclear. Once installed, the malicious app does not display an icon on the device launcher. Instead, it prompts the user to grant accessibility permissions with a message stating, “Welcome! App needs Accessibility permission to run properly. Please give accessibility permission!”
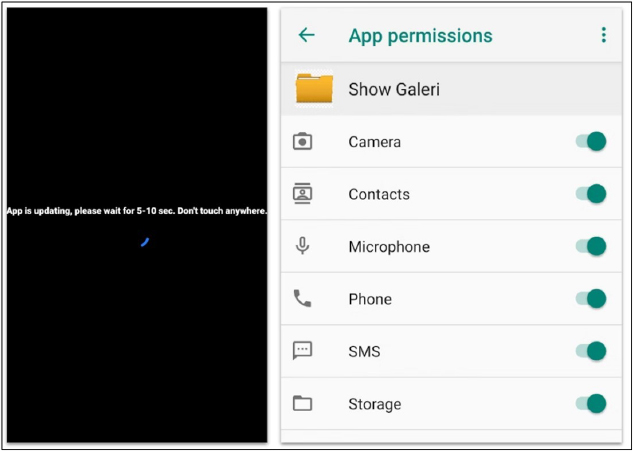
The malware initiates communication with the control server by sending an HTTP “GET” request and then switches to the WebSocket network connection protocol. Once accessibility service access is granted, BlankBot displays a black screen indicating an update while automatically obtaining all necessary permissions in the background.
On devices with Android 13 or newer, BlankBot uses a session-based package installer to bypass the restricted settings feature. It prompts the victim to allow installations from third-party sources, retrieves the APK file from the application’s assets directory without encryption, and proceeds with the installation process.
Capabilities of BlankBot
BlankBot exhibits a range of advanced capabilities, including screen recording, keylogging, custom injections, command execution, and defense evasion.
Screen recording
The malware employs Android’s MediaProjection and MediaRecorder APIs for screen recording. It captures video using the MediaProjection API, saving it as an MP4 file in the app’s internal storage, though this feature is still under development and varies between samples. The MediaRecorder API is used to capture screen images, specifying device dimensions, image format, and acquisition limits. These JPEG images are Base64 encoded and sent to a remote server.
Keylogging
Similar to other Android banking trojans, BlankBot relies on accessibility services to intercept and steal confidential information. It uses these services to collect data from infected devices, including application lists, notifications, typed text, and other sensitive information displayed or copied by the victim.
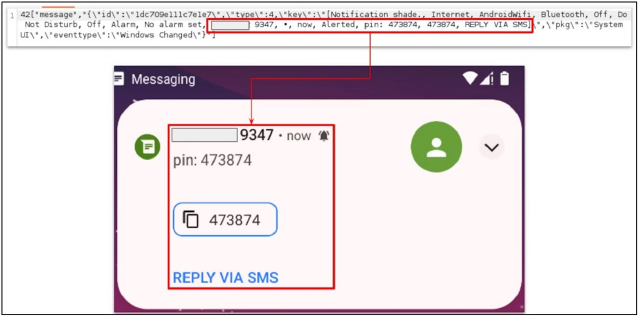
BlankBot distinguishes itself by using a custom virtual keyboard implemented through the “InputMethodService” class, unlike most other malware. This functionality is designed specifically to intercept and transmit the keys that users press on their keyboards.
Injections
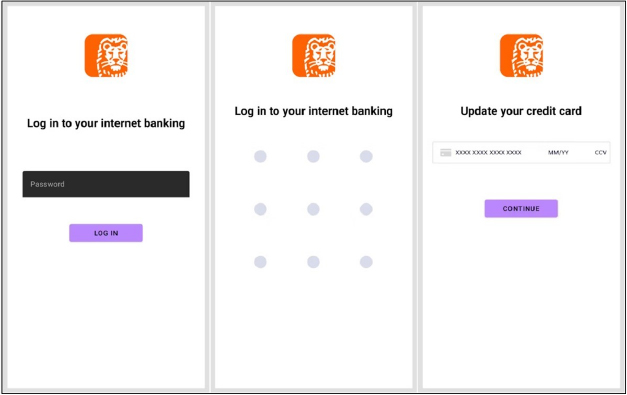
Upon receiving a specific command from the command-and-control (C2) server, BlankBot can create a customizable overlay tailored to the threat actors’ needs. This overlay can be used to request banking credentials, personal information, payment card data, or to steal the device’s lock pattern. The malware developers incorporated two external open-source libraries to facilitate the implementation of these custom injection templates.
Researchers simulated the control server’s functionality to test various BlankBot capabilities, issuing a command to create three customized views with the ING bank logo and UI text elements. All user input was logged and promptly exfiltrated to the control server.
Commands
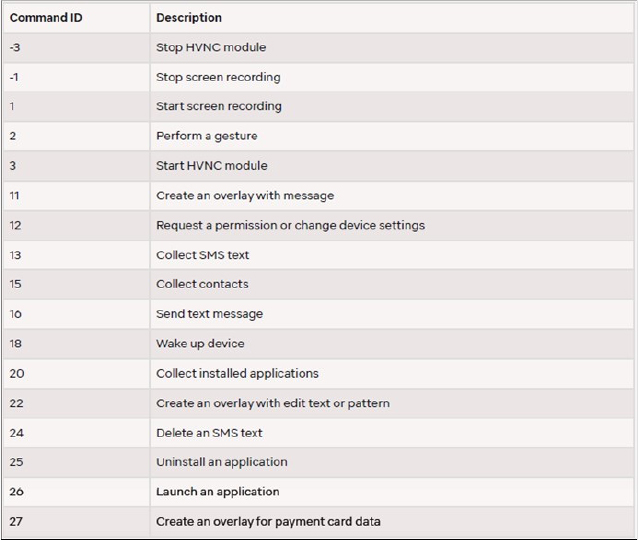
BlankBot uses a WebSocket connection to communicate with the C2 server for data exfiltration and receiving various commands. The botmaster can start and stop screen recording to view the infected device’s display in real-time. For apps with “FLAG_SECURE” protection, the botmaster can use a hidden virtual network (HVNC) module to capture UI layouts via accessibility services. The malware supports on-device fraud (ODF) by remotely controlling the device with gestures like clicks and swipes. Additionally, BlankBot can create overlays, collect contacts, SMS texts, and a list of installed applications. Following are the commands supported by BlankBot:
Defense evasion
Once installed, the malware checks if the device is an emulator. If the device is deemed legitimate, it tries to maintain persistence by blocking the user from accessing settings or antivirus applications. It achieves this by using accessibility services to monitor all events and specific words displayed on the device screen.
INSIGHTS
ETLM ASSESSMENT
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT41 likely compromised Taiwanese government-affiliated research institute with ShadowPad and Cobalt Strike
Summary:
APT41, a Chinese hacking group known for its sophisticated cyber espionage activities, compromised a Taiwanese government-affiliated research institute starting in July 2023. The attack began with the deployment of the ShadowPad malware and Cobalt Strike, leveraging an outdated Microsoft Office IME binary as a loader to bypass security measures. Once inside the network, the attackers used advanced techniques such as remote code execution and privilege escalation to maintain persistence and avoid detection.
The group utilized a variety of tools, including Mimikatz for credential harvesting, Web Browser Pass View for extracting passwords from web browsers, and 7zip for compressing and exfiltrating stolen data. They also exploited a remote code execution vulnerability CVE-2018-0824 CVSS 7.5 to further infiltrate the system. This breach allowed APT41 to access and potentially exfiltrate sensitive and proprietary information related to government research and technological development.
The attack underscores the significant threat posed by state-sponsored cyber actors targeting critical infrastructure and research institutions. It highlights the need for robust cybersecurity measures, regular security updates, and comprehensive incident response strategies to protect against such sophisticated threats. The compromise of the research institute not only disrupted its operations but also posed a risk to national security and the integrity of sensitive data which could be used for further malicious intent.
Relevancy & Insights:
APT 41 has adopted several key patterns and trends in its cyber activities. They have increasingly blended espionage with financial motives, using the same tools for data theft and financial gains, often monetizing stolen information. The group frequently targets software supply chains, breaching providers to distribute malware widely and enhance their impact. Known for their sophisticated techniques, including custom malware, evasive maneuvers, and advanced social engineering, APT 41 is adept at maintaining long-term access. Recently, they have also embraced ransomware, combining their traditional espionage tactics with disruptive methods that involve demanding ransoms and causing operational disruptions.
ETLM Assessment:
APT41 is a Chinese state-sponsored cyber espionage group known for targeting East and Southeast Asia, including Taiwan with a global reach. They focus on industries, such as government, technology, healthcare, and telecommunications, and employ sophisticated malware like Shadow Pad and Cobalt Strike. APT41 exploits vulnerabilities in widely used software. Their operations involve both state-sponsored espionage and financially motivated attacks, using malware like PlugX and Winnti in the past. The group’s evolving tactics and broad targeting pose a significant ongoing threat to global cybersecurity, necessitating robust defences and constant vigilance.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian hackers freed in prisoner swap, Kremlin doubling down on privateering
The US government has released two cybercriminals as part of a prisoner swap with Russia, which signals Kremling doubling down on its privateering strategy. The deal secured the release of sixteen people from Russia, including three American citizens and one American green-card holder. Moscow received eight citizens in exchange, including convicted cybercriminals Vladislav Klyushin and Roman Seleznev. Klyushin had been serving nine years for his role in “an elaborate hack-to-trade scheme that netted approximately $93 million through securities trades based on confidential corporate information stolen from U.S. computer networks.” Seleznev was serving fourteen years for his involvement in a $50 million identity theft and credit card fraud operation.
ETLM Assessment:
In a report last fall, we warned that Russia seems to be increasingly employing privateering actors, motivated by financial gains to bolster its cyber capability. Such a trend is expected to continue as privateers are offered ever more leniency: in the eyes of the Kremlin, the more global instability, the better. Any campaign that helps to divert attention from Moscow’s war on Ukraine means fewer resources available to oppose it. Now Moscow seems to double down on this strategy, effectively taking hostages from the ranks of innocent Western citizens in order to ransom out the criminal hackers it employed to disrupt its adversaries in its political war on the whole international system. The recent developments should signal increasing recklessness on the part of Russia that could result in much broader targeting of any business by Russian hackers with impunity.
Chinese APT compromised ISP to distribute malware
Researchers have recently published their findings on the China-linked threat actor known as Evasive Panda, which has compromised an internet service provider (ISP) last year in order to distribute malware. The researchers determined that Evasive Panda was altering DNS query responses for specific domains tied to automatic software update mechanisms. appeared to target software that used insecure update mechanisms, such as HTTP, and did not properly validate the digital signatures of installers. Therefore, when these applications went to retrieve their updates, instead of installing the intended update, they would install malware, including but not limited to MACMA and POCOSTICK (aka MGBot).
ETLM Assessment:
Evasive Panda is a Chinese APT group that has been active since at least 2012, conducting cyber espionage targeting individuals, government institutions, and organizations. It is a highly skilled and aggressive threat actor which uses a wide variety of malware and which invests significant effort into its operations. MgBot, in particular, has been a tool for Evasive Panda for more than a decade, and last year it was used against China’s Tibetan population. In this campaign, the cyber-attack was likely a part of a state-driven espionage campaign.
The Hunters International Ransomware impacts the Khandelwal Laboratories Pvt. Ltd.
Summary:
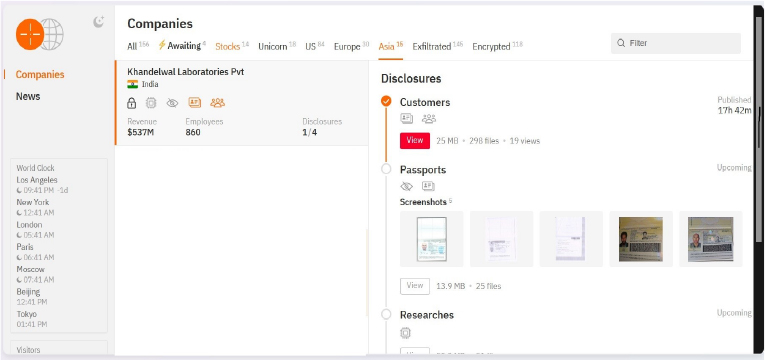
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; (www[.]khandelwallab[.]com), was compromised by the Hunters International Ransomware. Khandelwal Laboratories Pvt. Ltd. is a well-known company in the field of manufacturing and supplying high-quality pharmaceutical products. Established in India, the company has a strong reputation for adhering to strict quality control measures and maintaining high standards of product efficacy. Their portfolio includes a wide range of pharmaceutical formulations, including tablets, capsules, liquid injectables, dry syrups, and ointments. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. Specifically, the scale of the data exposure measures approximately 25 megabytes, comprising a total of 298 discrete files.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
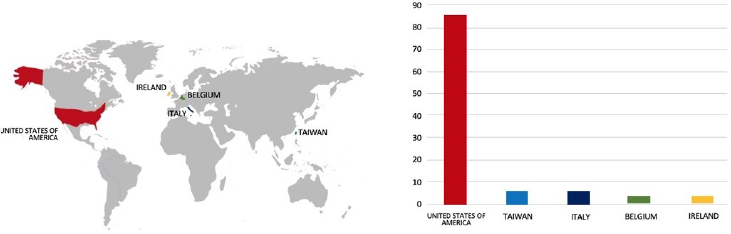
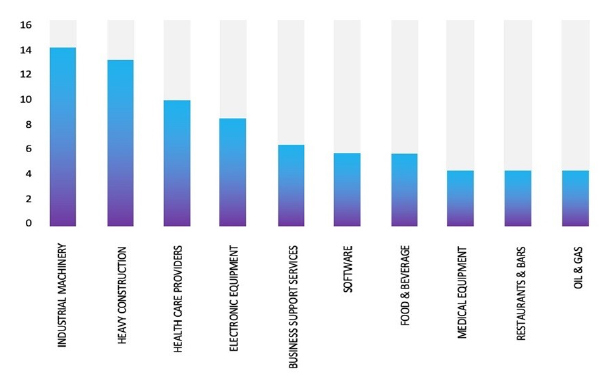
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that Hunters International Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on Khandelwal Laboratories Pvt. Ltd., a prominent Manufacturing company in India, highlights the extensive threat posed by this ransomware strain in the South Asia region.
The Meow Ransomware impacts WPG Holdings
Summary:
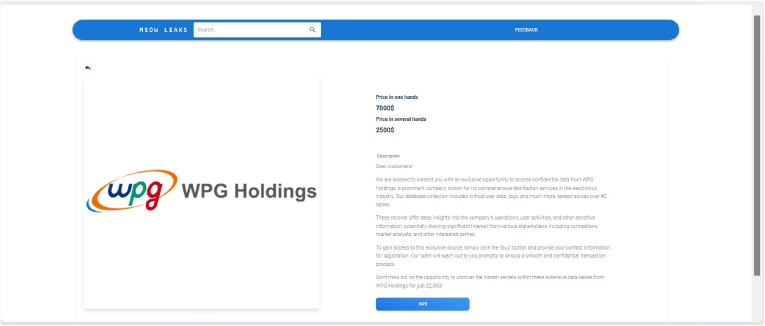
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan; (www[.]wpgholdings[.]com), was compromised by the Meow Ransomware. WPG Holdings, operating as WPG Holdings Limited, is a Taiwan-based technology conglomerate. Their main activities are focused on the distribution of electronic components, supply chain management services, and solutions for the semiconductor industry. WPG Holdings has grown to become one of the largest distributors in the Asia-Pacific region, with a global presence spanning across continents. WPG Holdings played a significant role in connecting semiconductor and electronic component manufacturers with businesses across electronics manufacturing services (EMS), original equipment manufacturers (OEMs), and original design manufacturers (ODMs). The company’s wide range of services includes procurement, logistics, design-in, technical support, and after-sales services, which help streamline the supply chain and optimize inventory management for their clients. The breached database collection includes critical user data, logs, and much more, spread across over 40 tables. These records offer deep insights into the company’s operations, user activities, and other sensitive information, potentially drawing significant interest from various stakeholders, including competitors, market analysts, and other interested parties. The price for compromised data is 7000$.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
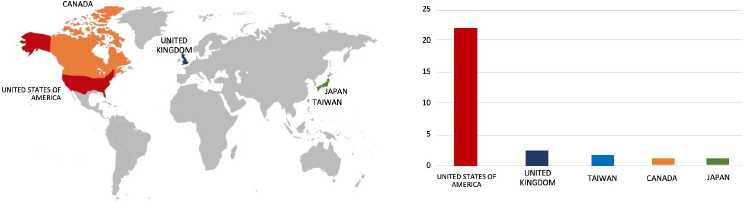
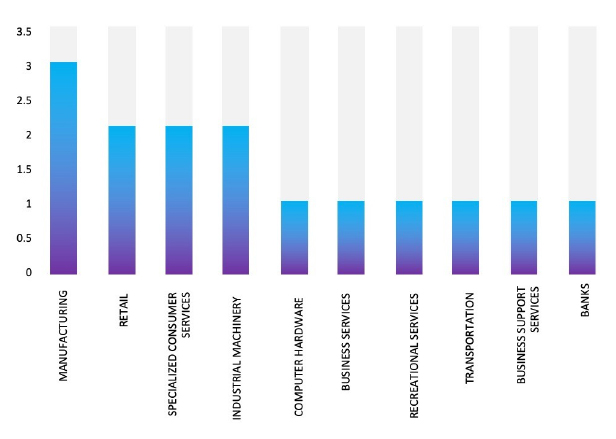
ETLM Assessment:
Meow Ransomware employs various infection methods, including phishing emails, exploit kits, Remote Desktop Protocol (RDP) vulnerabilities, and malvertising. Based on recent assessments by CYFIRMA, Meow ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on WPG Holdings, a leading Manufacturing firm in Taiwan, highlighting Meow Ransomware’s significant threat presence in the East Asia region.
Vulnerability in Vim
Summary:
The vulnerability allows a remote attacker to crash the application.
Relevancy & Insights:
The vulnerability exists due to a boundary error within the dialog_changed() function.
Impact:
A remote attacker can trick the victim to open a specially crafted file, trigger a double- free error, and crash the application.
Affected Products:
https[:]//github[.]com/vim/vim/security/advisories/GHSA-46pw-v7qw-xc2f
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
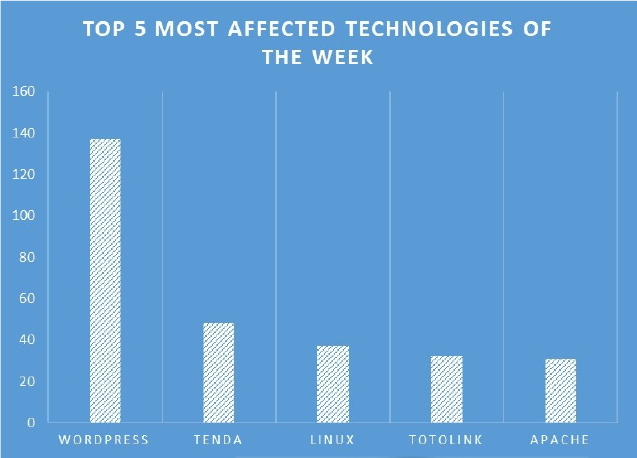
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Vim can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Vim is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding text editing and data manipulation activities, especially on UNIX systems, across different geographic regions and sectors.
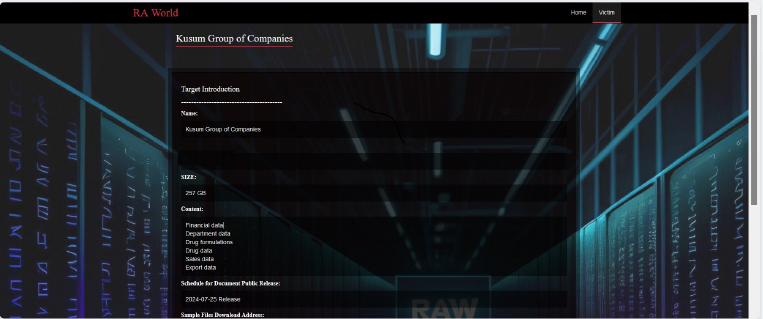
Raworld Ransomware attacked and Published data of Kusum Group of Companies
Summary:
Recently we observed that Raworld Ransomware attacked and published data of Melchers Singapore (www[.]kusumhealthcare[.]com) on its dark web website. Kusum Group of Companies. is a prominent pharmaceutical company based in India, specializing in the manufacturing and distribution of high-quality medicines. Known for its high-quality products and reliable services, Kusum Group has a significant presence in the agricultural sector, offering a wide array of agricultural inputs, such as seeds, pesticides, and fertilizers. The data leak, following the ransomware attack, includes financial data, Department data, Drug formulations, Drug data, Sales data, Export data, and other sensitive and confidential information related to the organization. The total size of the compromised data is 257GB.
Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment suggests that RA World Ransomware will persist in targeting various industries globally, particularly focusing on the United States, Europe, and Asia. The recent attack on Kusum Group of Companies, a prominent Manufacturing company in India, highlights the significant threat posed by this ransomware strain in the South Asia region.
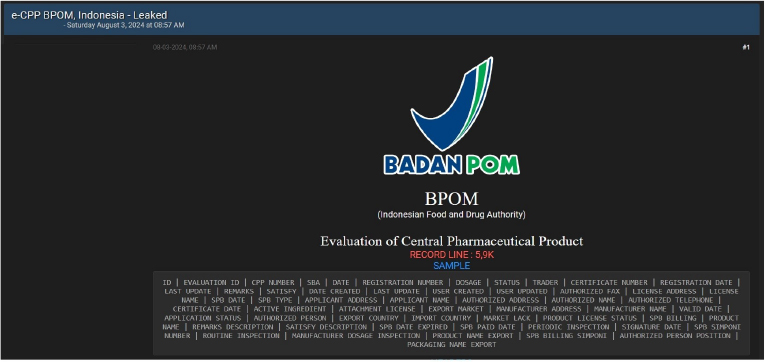
Badan Pengawas Obat dan Makanan (BPOM) (Indonesian Food and Drug Authority) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to Badan Pengawas Obat dan Makanan (BPOM) (Indonesian Food and Drug Authority) in an underground forum. The Indonesian Food and Drug Authority, known as Badan Pengawas Obat dan Makanan (BPOM), operates under the Ministry of Health and is responsible for ensuring the safety, efficacy, and quality of food, drugs, cosmetics, and health supplements in Indonesia. Established to protect public health, BPOM evaluates and monitors products to ensure they meet regulatory standards before being marketed. The breached data includes a variety of sensitive and confidential information, such as ID, evaluation ID, CPP number, date, registration number, dosage, status, trader, certificate number, registration date, last update, remarks, date created, user-created, user updated, and additional private details.
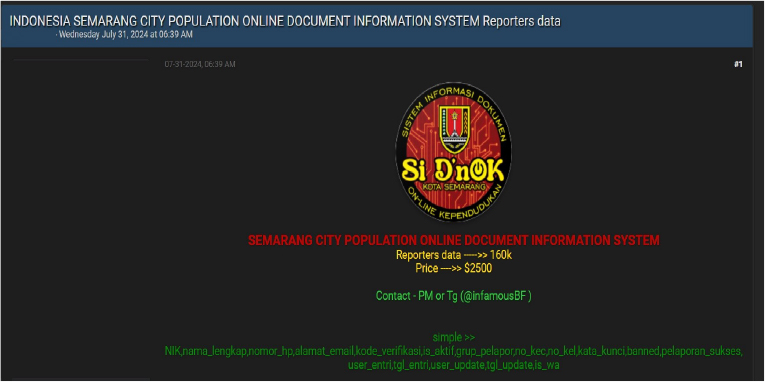
INDONESIA SEMARANG CITY POPULATION data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to the INDONESIA SEMARANG CITY POPULATION in an underground forum. A threat actor known as “Infamous” claims to be selling data from the Semarang city population’s online document information system. The purported data set includes 160,000 records, comprising full names, phone numbers, email addresses, and other personal details. The data is being offered for $2,500.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as ” Infamous ” poses a significant risk to organizations. This group is known for targeting various institutions and profiting from selling sensitive data on the dark web or underground forums. Organizations targeted by ” Infamous ” typically have inadequate security measures, making them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
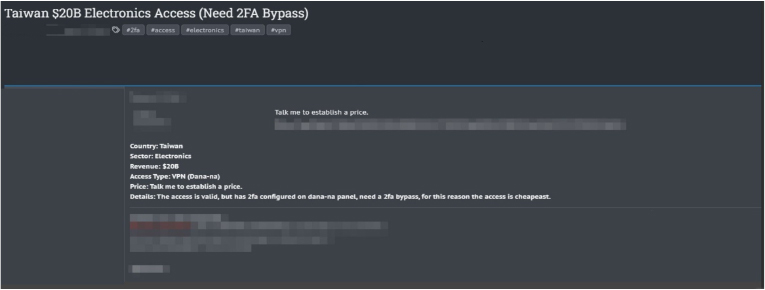
The CYFIRMA Research team observed a potential sale of VPN Access related to a Taiwanese Electronics Company. A new cyber incident post from a threat actor has emerged, claiming to offer VPN access to a major electronics company in Taiwan with an annual revenue of $20 billion. Allegedly, the access is announcement configured through the “Dana-na” panel but is protected by two-factor authentication (2FA), necessitating a bypass to utilize the access fully.
Due to the requirement for a 2FA bypass, the threat actor is offering the access at a discounted price and is open to negotiations to establish the final price. This situation highlights significant security concerns for the targeted company, underscoring the importance of robust 2FA systems and the potential vulnerabilities that can arise even with such measures in place.
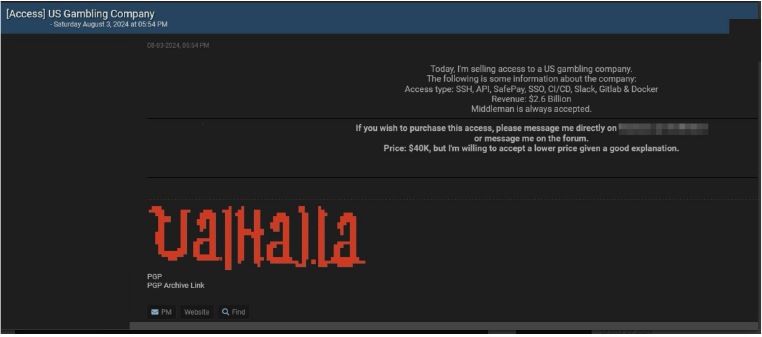
The CYFIRMA Research team observed a potential Access sale related to a US Based Gambling Company. According to a threat actor “IntelBroker” on a dark web forum, an access is for sale for a US-based gambling company. The post doesn’t state the name of the company but according to the threat actor, the revenue of the organization is $2.6 Billion.
According to the threat actor, the alleged access type is as follows: SSH, API, SafePay, SSO, CI/CD, Slack, Gitlab & Docker.
The price for the alleged access is $40K but the threat actor accepts negotiation. A middleman is also accepted for the deal.tted in JSON.
ETLM Assessment:
The “IntelBroker” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
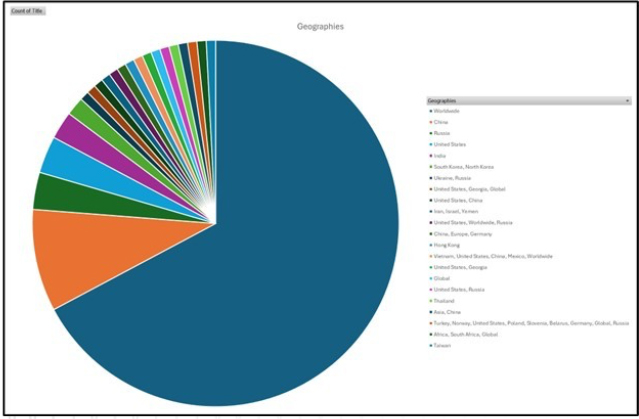
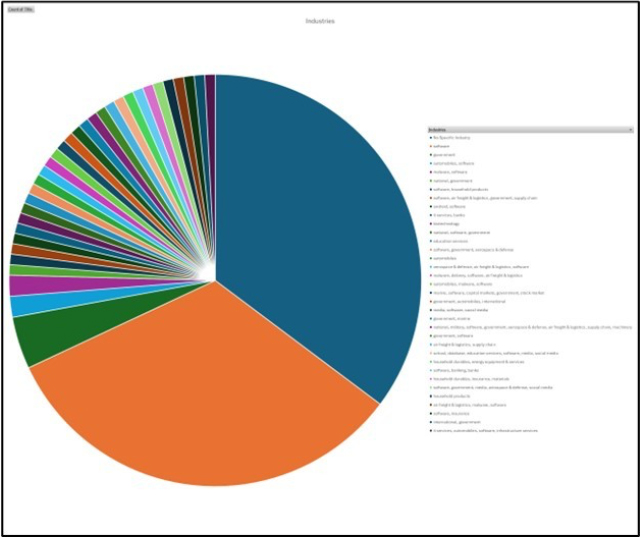
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.