



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found ransomware known as FreeWorld while monitoring various underground forums as part of our Threat Discovery Process.
FreeWorld:
FreeWorld is a recently emerged Mimic Ransomware variant.
The Ransomware once executed will encrypt files and append their filenames with a “.FreeWorldEncryption”. Once this process is concluded, a ransom note “FreeWorld- Contact.txt” – will be created.
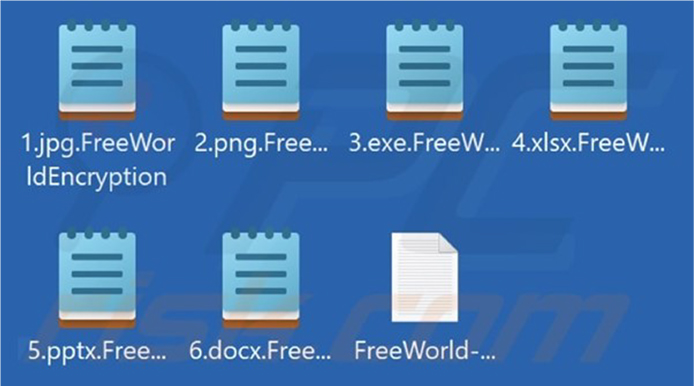
Screenshot of files encrypted by FreeWorld ransomware. (Source: Surface Web)
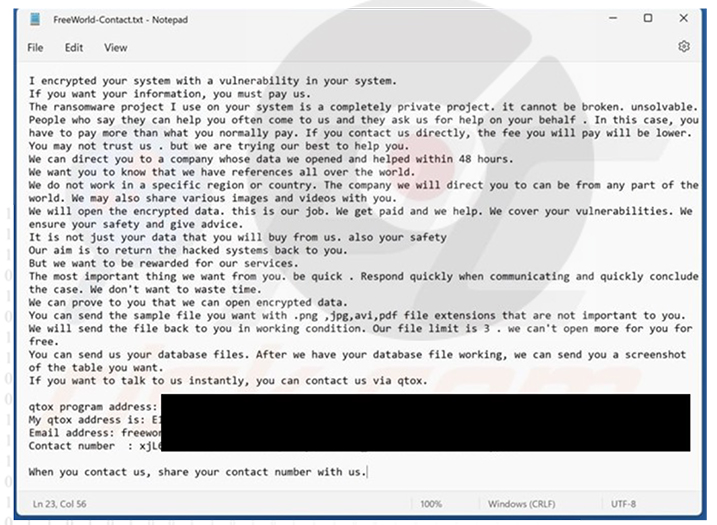
FreeWorld ransomware note. (Source: Surface Web)
Initial Access
In a recent attack campaign, hackers employed brute-force attacks to infiltrate MSSQL servers. After gaining authentication, they promptly initiated the process of listing or identifying information within the database, with a particular focus on seeking out other login credentials.
Execution
Subsequently, upon realizing that the MSSQL function xp_cmdshell stored procedure was activated, the assailants initiated the execution of shell commands on the host. Typically, this function should remain disabled unless it is necessary.
Discovery
The enumeration process involved the utilization of a few fundamental commands, primarily wmic.exe, net.exe, and ipconfig.exe. Each of these commands was executed via the MSSQL xp_cmdshell.
Defense Evasion
After confirming the target system’s legitimacy, the attackers proceeded to impair its defences by executing various commands. These actions involved creating three new users (Windows, adminv$, and mediaadmin$) and adding them to “remote desktop users” and “administrators” groups. The attackers employed a multi-language command to increase their chances of success, allowing them to adapt to different system languages. This approach provided a streamlined method for their malicious activities.
The attackers took an aggressive approach by disabling the Windows Firewall entirely using the command “netsh firewall set opmode disable.” This action bypassed the need to manage or check the firewall state. With many of the system’s defences, especially network protection and RDP authentication, now disabled, the attackers focused on establishing persistence. They began connecting to a remote SMB share for transferring tools. Initially, they detached various network shares, though their specific motivations remain unclear, as this action could disrupt running processes and alert administrators.
Persistence
The attackers will execute commands for each of the mentioned users. Once the users and groups are established, they will run the following commands to prevent password expiration and ensure the users were never logged off:
Command and Control
It became evident that the attackers preferred using RDP to connect to the victim’s machine. Later, they were observed using Ngrok proxy software. However, before proceeding, the attackers conducted an enumeration to assess the current state of the RDP environment.
Network share analysis
The network share provided the attacker with the capability to transfer files to and from the victim system and install malicious tools. Researchers observed that although many files had obscure and random names, their intended functions became evident through their usage patterns.
During this phase, researchers detected a shift in the attackers’ strategies. They moved away from executing commands via the xp_cmdshell method and began utilizing commands from an SMB-delivered binary known as svr.exe. This binary appeared to serve as a command and control payload for Cobalt Strike. The researchers observed the binary establishing DNS connections with gelsd[.]com.
Ngrok usage
The attackers tried to establish RDP persistence using Ngrok, a tool that can bypass firewalls by running a host service and providing a public IP and port for the attacker to connect to. They placed the Ngrok binary in C:\Windows\System32, renaming it to n.exe. An unsuccessful attempt was made to create a connection using the svr.exe command.
AnyDesk used as a RAT
The attackers, undeterred by previous setbacks, turned to the use of AnyDesk, a legitimate remote access software often abused by threat actors as a Remote Access Trojan (RAT) to deploy ransomware. They executed a batch file named “a2.bat” through the svr.exe process to download and run the AnyDesk installation. However, the batch file seemed to be set to self-delete, making it impossible to observe its contents.
Having established a strong level of persistence, the attackers shifted their focus to lateral movement within the network. They downloaded an advanced port scanner utility, placing it in the desktop directory of the newly created user “windows”. In addition, they executed Mimikatz through a batch file called “start.bat”.This batch file first modified the registry to force clear text credentials, employing a WDigest downgrade attack by executing the command. Subsequently, the batch file executed Mimikatz to dump credentials. The results were stored on the “windows” user’s desktop.
Ransomware:
The attackers used a harmful software called “Mimic ransomware” to take control of a computer. FreeWorld is ransomware that is the variant of this Mimic. Both use a program called “Everything” to find and lock up important files on the computer.
First, they downloaded a file called “5000.exe” and put it on the computer’s desktop. Then, they ran it by clicking on it. This “5000.exe” program did some things behind the scenes. It took another program called “7zip” and “Everything” and put them in a temporary folder on the computer. Then, it told “7zip” to open a special locked file called “everything64.dll” using a secret password.
After that, they took the actual ransomware program and put it in a hidden folder on the computer. This ransomware program was called “dc.exe”. When they ran it, it started locking up the computer’s files and gave them a special name with “.FreeWorldEncryption” at the end.
Once it finished doing its bad work, it created a text file called “FreeWorld-Contact.txt” with instructions on how the victim could pay them to unlock their files.
Relevancy and Insights:
ETLM assessment
CYFIRMA’s assessment, based on the information available, indicates that the FreeWorld ransomware could pose a serious threat to organizations that rely heavily on Microsoft SQL Server (MS SQL) for data storage. We will continue to monitor, and provide a more comprehensive assessment when further information becomes available.
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001:Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002:Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1546.012: Event Triggered Execution: Image File Execution Options Injection | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1547.008: Boot or Logon Autostart Execution: LSASS Driver | ||
| 4 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1546.012: Event Triggered Execution: Image File Execution Options Injection | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
||
| T1547.008: Boot or Logon Autostart Execution: LSASS Driver | ||
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.002: Obfuscated Files or Information: Software Packing | ||
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools |
||
| 6 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056.001: Input Capture: Keylogging | ||
| 7 | TA0007: Discovery | T1012: Query Registry |
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614.001: System Location Discovery: System Language Discovery | ||
| 8 | TA0008:Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1056.001: Input Capture: Keylogging |
| T1005: Data from Local System | ||
| T1185: Browser Session Hijacking | ||
| 10 | TA0010:Exfiltrati on | T1567: Exfiltration Over Web Service |
| 11 | TA0011: Command and Control | T1105: Ingress Tool Transfer |
| T1572: Protocol Tunneling | ||
| T1573.001: Encrypted Channel: Symmetric Cryptography | ||
| T1219: Remote Access Software | ||
| 12 | TA0040:Impact | T1486: Data Encrypted for Impact |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule:
title: UAC Bypass via ICMLuaUtil tags:
– attack.defense_evasion
– attack.privilege_escalation
– attack.t1548.002 logsource:
category: process_creation product: windows
detection: selection:
ParentImage|endswith: ‘\dllhost.exe’ ParentCommandLine|contains:
– ‘/Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}’
– ‘/Processid:{D2E7041B-2927-42FB-8E9F-7CE93B6DC937}’
filter:
– Image|endswith: ‘\WerFault.exe’
– OriginalFileName: ‘WerFault.exe’ condition: selection and not filter
falsepositives:
– Unknown level: high
(Source: Surface Web)
Type: Remote Access Trojan (RAT)
Objective: Data theft, Espionage, and Remote Access
Target Organization: Civil Society Groups
Suspected Threat Actor: Kimsuky (aka APT43)
Active Malware of the Week
This week “SuperBear” is trending.
Researchers have uncovered a new and unique remote access trojan (RAT) called SuperBear RAT that has been identified in a malware campaign and specifically targets journalists. This malware is deployed using open-source AutoIT scripts, posing a significant security concern for media professionals.
Researchers received a targeted sample sent to a journalist, containing a lure to open the document. The journalist received an email from an activist, thinking it was from an organization member, but it contained a malicious .LNK document. When opened, it executed a malicious PowerShell command along with a legitimate DOCX file related to the organization. Further analysis by researchers revealed that after the initial compromise, an AutoIT script was used to perform process injection through process hollowing.
Attack Method
Upon executing the .LNK file, a hidden PowerShell window was triggered alongside a legitimate document. The actor employed obfuscation techniques to load and execute a PowerShell command. This command decoded a value, resulting in a VBS script saved to the user profile directory. The VBS script contained commands with “su” additions to evade file-based detection signatures. The payload delivery site was a compromised WordPress instance of a legitimate website. Following the command retrieved two payloads from the domain.
Payloads
AutoIT3 was executed with the compiled script as a parameter, leading to a process injection operation.
AutoIT process injection using process hollowing
The AutoIT script used in this malware campaign employs a process hollowing technique, involving native Windows API calls. It begins by creating a suspended instance of Explorer.exe with “CreateProcess,” then unmapping the suspended process using “NtUnmapViewOfSection” before injecting malicious code. The process is then resumed through “VirtualAllocEx,” “WriteProcessMemory,” “SetThreadContext,” and “ResumeThread.” It establishes a connection with a C2 server at IP Address: 89[.]117[.]139[.]230 and Domain: hironchk[.]com. The RAT carries out one of three primary attack operations:
The default action for the C2 server instructs clients to exfiltrate system data. Additionally, the RAT can execute shell commands or download a malicious DLL onto the infected machine, with the DLL being named “SuperBear” if it can’t generate a random filename.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
Lazarus Group Behind Malicious Python Packages, Part of Supply Chain Attack
Summary:
In a recent observation, the North Korean state-sponsored Advanced Persistent Threat group; Lazarus, was observed uploading malicious packages to the Python Package Index (PyPI) repository. Security researchers uncovered a malicious supply chain campaign. This campaign involved the upload of two dozen malicious Python packages onto the Python Package Index (PyPI) open-source repository. This campaign started in August, and the packages were removed from PyPI after accumulating downloads. The group disguised these packages as legitimate software, with one of them masquerading as a VMware vSphere connector module called vConnector. One of the malicious packages, named VMConnect, targeted IT professionals seeking virtualization tools and was downloaded 237 times. Two other packages, ‘ethter’ and ‘quantiumbase,’ were also found to contain the same code and were downloaded 253 and 216 times, respectively. Researchers found additional packages linked to the same operation, such as ‘tablediter’ (736 downloads), ‘request- plus’ (43 downloads), and ‘requestspro’ (341 downloads). These packages attempted to pass as legitimate software by appending “plus” and “pro” suffixes to their names. The malicious packages closely resembled the legitimate ones in terms of descriptions and file structures. However, they contained modifications that executed a malicious function, collecting data from infected machines and sending it to the attacker’s command and control servers. The attackers employed various techniques to avoid detection, such as typosquatting and impersonation of legitimate packages. One example is the tablediter package, which closely resembled the popular prettytable tool but executed its malicious code only when used in a project, rather than during installation.
Relevancy & Insights:
PyPI stands as the primary repository for Python packages, serving as a crucial resource for software developers seeking foundational components for their projects. Regrettably, its widespread usage renders it an appealing target for threat actors aiming to compromise developers or their undertakings. Frequently, these malicious packages are introduced under the umbrella of useful tools or emulate well-known projects by subtly altering their names. Given the immense volume of package uploads, PyPI lacks the capacity to thoroughly inspect each submission. Consequently, it relies on user reports to identify and eliminate malicious files. Unfortunately, by the time these files are removed, they have often accrued several hundred downloads.
ETLM Assessment:
This incident is not a lone case of malicious code infiltrating PyPI packages to execute harmful actions. It represents another instance in a series of supply chain attacks, where malicious PyPI packages have been employed for malicious purposes in the past. This latest occurrence underscores the strong probability of future software supply chain attacks, similar to the VMConnect campaign. Software supply chain attacks have gained popularity among both cybercriminals and state-sponsored threat actors due to their potential for widespread impact and their inherent difficulty in detection.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
South African news site attack in conjunction with coverage of India during BRICS Summit
Daily Maverick; a South African news website, said that an Indian DDoS attack forced it to close the site off to the whole domain of India, in order to safeguard its operation. The alleged attack came a day after the portal had claimed that Indian Prime Minister Narendra Modi had delayed his arrival at Pretoria’s Waterkloof Air Force Base for the 2023 BRICS Summit until he would be greeted by Deputy President Paul Mashatile. The news outlet reported that Indian Prime Minister Narendra Modi would not get off the plane since South African President Cyril Ramaphosa would greet Chinese President Xi Jinping when he arrived for the summit, while no similar delegation was available to greet Modi. The news came paradoxically after Indian National security advisor Ajit Doval called for collective efforts to deal with challenges stemming from cyberspace at the Friends of BRICS meeting, a month prior.
Infamous Chisel malware used by Russian military intelligence as a combat support tool
The UK’s Ministry of Defence (MoD) has reviewed the recently exposed Infamous Chisel campaign against Ukrainian military targets. The MoD sees it as an instance of cyber operations, used as combat support. The National Cyber Security Centre (NCSC) has published a report on a malware campaign targeting Android mobile devices, used by the Ukrainian military, as reported on earlier by CYFIRMA. The malware, referred to as ‘Infamous Chisel’, has been used by the Russian cyber threat group known as Sandworm, previously linked to the Russian military intelligence agency’s (GRU) Main Centre for Special Technologies (GTsST). The malware enables persistent access to, and the collation and exfiltration of data and compromised Android devices. This includes targeting applications used by the Ukrainian military. Infamous Chisel has highly likely been used with the aim of stealing sensitive military information. This activity demonstrates Russia’s continued use of cyber capabilities to support the invasion of Ukraine.
Attack Type: Ransomware
Target Industry: Household Durables
Target Geography: The United States of America
Ransomware: 8Base Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]petkusbrothers[.]com), was compromised by 8Base Ransomware. Petkus Brothers is California’s Sunroom, Room Addition, and Remodelling Specialists. The compromised information includes invoices, receipts, accounting records, personal data certificates, employment agreements, and various other sensitive documents.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
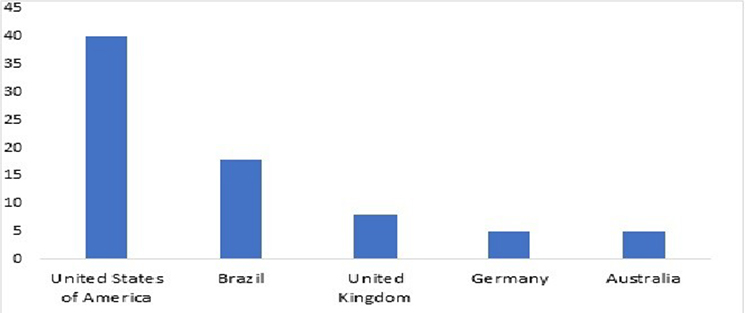
It is CYFIRMA’s assessment that while not a lot is known about 8Base, given the significant targeting of US companies as compared to other countries, globally in such a small timeframe, we assess their target geography will remain the same in the near future, which as per our assessment as a RaaS operating model is likely to provide the largest profit margins. We will continue to monitor and provide a more comprehensive assessment in due course. Remember that no single measure can guarantee complete protection, so it’s essential to adopt a layered security approach. Regularly reviewing and updating your security measures is crucial as the threat landscape evolves.
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Relevancy & Insight:
The vulnerability exists as the application does not properly control consumption of internal resources within the ‘django.utils.encoding.uri_to_iri()’ method.
Impact :
A remote attacker can pass a large number of characters to the affected method and perform a denial of service (DoS) attack. Affected Products: https[:]//www.djangoproject[.]com/weblog/2023/sep/04/security- releases/
Recommendations:
German financial agency has been experiencing disruptions due to a DDoS attack
Threat Actors: unknown
Attack Type: DDoS
Objective: Operational Disruption
Target Technology: Web Application
Target Geographies: Germany
Target Industries: Banking and Finance
Business Impact: Operational Disruption
Summary:
The German Federal Financial Supervisory Authority (BaFin) disclosed that its website
has been under an ongoing distributed denial-of-service (DDoS) attack since last Friday. BaFin, as Germany’s financial regulatory body, operates under the Federal Ministry of Finance and holds the responsibility of overseeing 2,700 banks, 800 financial institutions, and 700 insurance service providers. The regulatory authority is recognized for its law enforcement functions both within Germany and on the global stage. Over the past few years, it has levied fines of $10 million against Deutsche Bank and $5 million against Bank of America for a range of infractions. The German agency announced that it has implemented all necessary security measures and defensive actions to protect its operations against cyberattacks. The perpetrators of the DDoS attack on the German financial authority remain unidentified, but there is speculation that pro-Russian hacktivists may be involved due to Germany’s supportive stance towards Ukraine, which includes providing financial and military equipment assistance.
Relevancy & Insights:
ETLM Assessment:
Given Germany’s continued support for the war in Ukraine and continued military aid, we assess further DDoS attacks or similar targeting of other Federal German institutions. The DDoS attack on The German Federal Financial Supervisory Authority (BaFin) is a reflection of the motivations of the suspected threat actors to disrupt and embarrass major institutions associated to Governments that support the Ukrainian war effort.
myBillBook’s Data Advertised in Leak Site
Attack Type: Data Leaks
Target Industry: Software
Target Geography: India
Target Technology: SQL Database
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to myBillBook, {www[.]niobook[.]com}. myBillBook GST billing software helps businesses create professional invoices in just a few clicks. The compromised data consists of the public user’s ID, email, password, first name, last name, mobile number, and additional confidential information in SQL format, with a combined data size of 4 gigabytes.
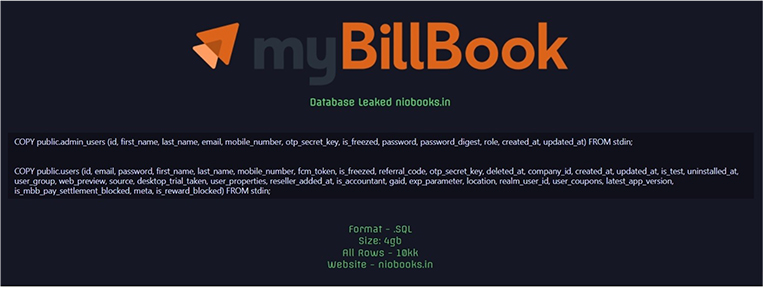
Source: Underground forums
Relevancy & Insights:
Source: Underground forums