



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Target Geography: Germany
Introduction
CYFIRMA Research and Advisory Team has found PlayBoy LOCKER Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
PlayBoy LOCKER
Researchers identified a new ransomware strain named Playboy Locker.
This ransomware strain encrypts files and appends the “.PLBOY” extension to each filename. After encryption, it creates a text file named “INSTRUCTIONS.txt” containing the ransom note and alters the desktop wallpaper to pressure the victim further.
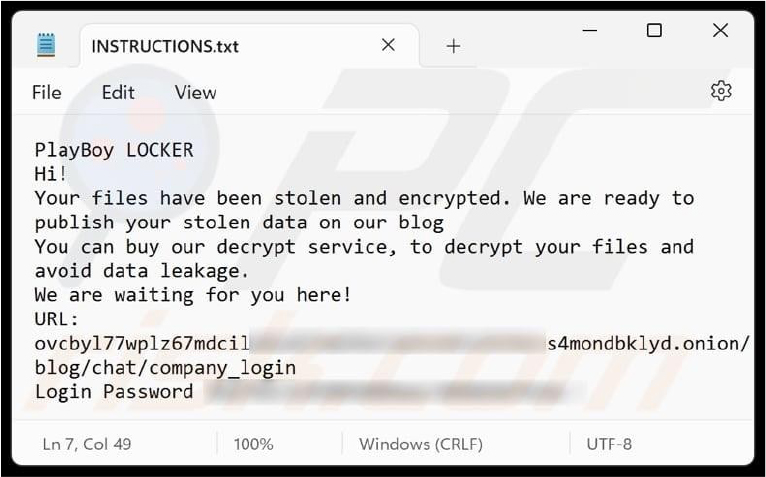
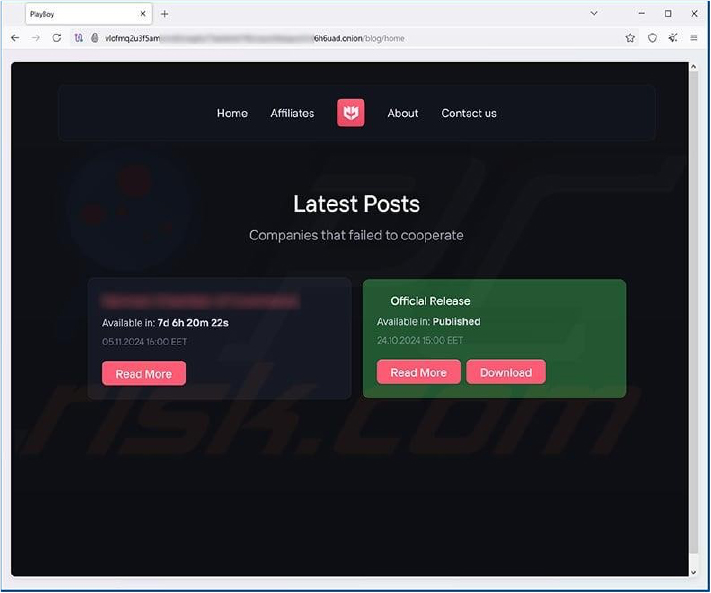
PlayBoy LOCKER’s ransom note warns victims that their files have been both stolen and encrypted, threatening to publish the data unless a decryption service is purchased. The note includes a URL and login credentials for communication, pressuring victims to pay to prevent data exposure and recover their files.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| T1569.002: System Services: Service Execution | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0005: Defense Evasion | T1027.005: Obfuscated Files or Information: Indicator Removal from Tools |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1134: Access Token Manipulation | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1074: Data Staged | ||
| T1114: Email Collection | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop | ||
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CyFirma’s analysis of current data suggests that the PlayBoy ransomware group may expand its operations to target economically developed nations and a wider range of industries. Having initially struck Germany, a developed nation, this group demonstrates the potential to intensify its focus on high-value targets, aiming at industries with critical assets and the capacity to meet ransom demands. Therefore, maintaining vigilance and implementing robust cybersecurity measures are crucial to mitigating these evolving threats effectively.
Sigma Rule
title: Suspicious Volume Shadow Copy Vsstrace.dll Load tags:
– attack.defense-evasion
– attack.impact
– attack.t1490 logsource:
category: image_load product: windows
detection: selection:
ImageLoaded|endswith: ‘\vsstrace.dll’ filter_windows:
– Image:
– ‘C:\Windows\explorer.exe’
– ‘C:\Windows\ImmersiveControlPanel\SystemSettings.exe’
– Image|startswith:
– ‘C:\Windows\System32\’
– ‘C:\Windows\SysWOW64\’
– ‘C:\Windows\Temp\{‘ # Installers
– ‘C:\Windows\WinSxS\’ filter_program_files:
# When using this rule in your environment replace the “Program Files” folder by the exact applications you know use this. Examples would be software such as backup solutions
Image|startswith:
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ condition: selection and not 1 of filter_*
falsepositives:
– Unknown level: high
(Source: Surface web)
IOCs:
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Stealing Sensitive Information, Remote Access | Target Technology: Android OS | Target Industry: Financial institutions
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “FakeCall” is trending.
FakeCall
Researchers have recently uncovered a new variant of the FakeCall malware, which uses Vishing (voice phishing) to target mobile users. This approach involves deceptive phone calls or voice messages aimed at tricking victims into revealing sensitive information, including login credentials, credit card details, or banking information. This malware operates as an advanced Vishing attack that allows attackers to gain near- total control over a victim’s mobile device. This includes intercepting calls, both incoming and outgoing, and manipulating the user’s experience to appear legitimate. Victims are misled into calling fraudulent numbers managed by the attacker, further enhancing the malware’s ability to harvest confidential information. This evolution in mobile threats underscores the increasing sophistication of social engineering tactics.
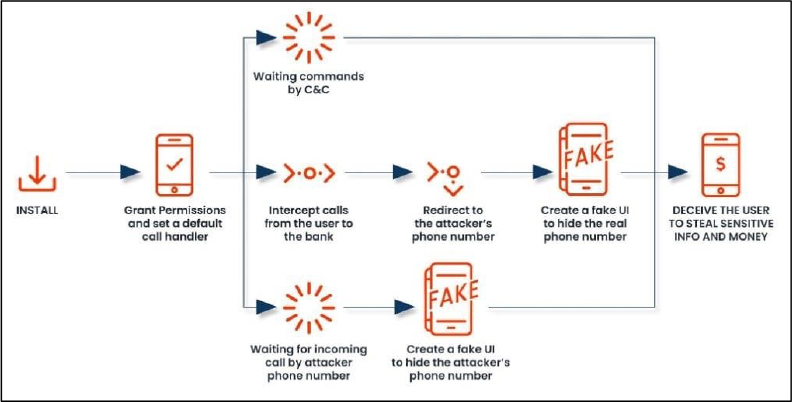
Attack Method
The FakeCall malware attack initiates when victims unknowingly download an APK file onto their Android device via a phishing attack. This file acts as a dropper, installing the primary malicious payload in a second stage. Upon launch, the app prompts users to set it as the default call handler, granting it control over all incoming and outgoing calls. It operates alongside the OutgoingCallReceiver to intercept the android.intent.action.NEW_OUTGOING_CALL intent, extracting the phone number with getResultData(). The app then presents a custom interface that mimics the native com.android.dialer app, seamlessly integrating its malicious functions without raising suspicion. Once installed, FakeCall communicates with a Command and Control (C2) server to covertly execute its actions, with newly discovered variants being heavily obfuscated while retaining characteristics consistent with earlier versions. This evolution in tactics is designed to evade detection and enhance malware’s capabilities.
The main purpose of this application is to monitor outgoing calls and relay this information to an external Command and Control (C2) server. However, its potential for abuse is quite high:
Identity Fraud: By taking advantage of its role as the default call handler, the app can alter the dialed number using the setResultData() method, tricking users into making calls to fraudulent numbers.
Call Hijacking: The malware has the capability to intercept both incoming and outgoing calls, enabling it to establish unauthorized connections without the user’s knowledge. Users may remain unaware of this interference until they uninstall the app or restart their device.
For example, if a compromised user tries to call their financial institution, the malware can redirect the call to a fraudulent number that the attacker controls. The malicious app will present a convincing fake user interface that looks like the legitimate Android call screen, even displaying the actual bank’s phone number. The victim will not realize they are being manipulated, as the malware’s imitation of the legitimate banking experience allows the attacker to gather sensitive information or gain unauthorized access to the victim’s financial accounts.
Technical Analysis
The analysis of FakeCall began with a detailed examination of its AndroidManifest.xml file, where researchers discovered several activities, services, and receivers absent from the decompiled code—hinting at a more complex, layered architecture. This malware variant employs a dynamically decrypted .dex file to load hidden code, which researchers successfully extracted from device memory for deeper static analysis.
Notably, the identified services and activities closely resemble those in an older malware variant, indicating a strategic evolution: certain malicious functions have been migrated to native code, enhancing its ability to bypass detection. By referencing code from the previous variant, researchers aim to gain a comprehensive understanding of the extended capabilities of this newly evolved FakeCall sample. Additionally, the latest variants in this campaign introduce additional functionalities, some of which appear to be still under development. Below is a summary of the features observed in the analyzed samples:
Bluetooth Receiver
The receiver in this malware functions mainly as a listener that monitors Bluetooth status and changes. Currently, there is no clear evidence of malicious behavior in the source code, which raises questions about its purpose and whether it might serve as a placeholder for potential future functionalities.
Screen Receiver
Like the Bluetooth receiver, this component solely monitors the screen’s state (on/off) and does not indicate any malicious activity within the source code.
Accessibility Service
The malware features a new service derived from the Android Accessibility Service, which provides it with extensive control over the user interface and allows it to capture data displayed on the screen. The decompiled code reveals the implementation of methods such as onAccessibilityEvent() and onCreate() in native code, which obscures their true malicious purposes.
Phone Listener Service
This service functions as a link between the malware and its Command and Control (C2) server, enabling attackers to send commands and perform actions on the infected device. Similar to previous versions, the new variant offers a robust set of capabilities, with some functionalities transitioned to native code and new features introduced. These
enhancements significantly strengthen the malware’s potential to compromise devices. Additionally, the new variant includes a range of commands listed in the table below, reflecting the malware’s ongoing development and its persistent efforts to expand its capabilities to better serve the attacker’s interests.
| Command | Description | JSON response sent to C&C |
| turnoff_bluetooth | Disable Bluetooth | |
| get_thumbnail_list | Get a list of thumbnails from the DCIM directory of the external storage and sent the following JSON to the C&C |
{ “imei”: “Settings.System.getString(context0.getContentResolver(), ‘android_id’)”, “thumbnails”: [ { “lastModified”: “date last time was modified”, “imagePath”: “image path”, “imageName”: “image name” } , { … } ], “total”: “Number of element in external storage excluding folder” } |
| upload_thumbnail_list | Compress the thumbnail listed to .jpg and upload to the C&C | |
| Upload_full_image | Upload a specific image indicated from a parameter received from the C&C, compressed it and send via POST | |
| Delete_image | Delete a specific image specified by the C&C | |
| Remote_homekey | Use accessibility services to simulate the press of the home button | |
| Remote_wakeup | This command determines whether the device’s screen is currently locked. If locked, it unlocks the device momentarily and disables auto-relocking. The command returns a value of true indicating successful unlocking. | |
| Remote_click | Utilize accessibility features to mimic a tap on the device at the coordinates designated by the C&C. | |
| Request_phoneManager | Check what is the application set as default dialer manager | |
| Request_phone_call | Set the malware as default dialer manager | |
| Remote_start | Initiate a video stream capturing the screen contents of our device using the MediaProjection API | |
| Remote_stop | Terminate the video stream transmission, thereby halting the broadcast of the infected device’s screen contents | |
| Remote_get_image | Capture an image of the infected device’s display by taking a screenshot |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that FakeCall malware is set to become a stealthier and more complex threat as attackers advance their methods to target employees on a broader scale. As mobile devices become central to workplace communication, attackers may develop increasingly convincing Vishing and Smishing tactics, embedding company-specific details to create highly personalized scams. This evolution could enable attackers not only to steal financial data but also to gain unauthorized access to sensitive corporate information or proprietary assets. Looking ahead, campaigns may evolve beyond traditional fraud tactics, employing subtle social engineering to manipulate employees into actions that compromise organizational security on a deeper level, including espionage and data manipulation, putting the very integrity of corporate data and operations at risk.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
Recommendations:
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Phishing Campaign Exploits Copyright Infringement Lure to Deploy Infostealers
SUMMARY
A newly identified phishing campaign targeting Facebook business and advertising account users in Taiwan has been linked to an unknown threat actor since at least July 2024. This campaign specifically targets traditional Chinese speakers through deceptive emails that impersonate the legal departments of prominent technology and media companies, warning recipients about copyright infringement. The phishing emails contain malicious links to a password- protected RAR file hosted on Google Appspot and Dropbox, which, when downloaded, reveals a fake PDF executable designed to deliver either LummaC2 or Rhadamanthys information stealers embedded in legitimate software binaries. LummaC2 is capable of exfiltrating sensitive information, while Rhadamanthys employs advanced anti- detection techniques, including modifying Windows Registry entries for persistence and utilizing process injection to run within legitimate system processes. The threat actor employs various evasion strategies, such as code obfuscation and inflating file sizes to bypass antivirus detection. Researchers observed ongoing command and control (C2) activities, indicating the campaign’s persistence.
Relevancy & Insights:
The threat actor involved in the recent phishing campaign targeting Facebook business users in Taiwan exhibits patterns that align with previous attacks attributed to similar groups. Historically, such actors have focused on social engineering techniques, leveraging urgency and fear—often through legal threats or claims of copyright infringement—to manipulate victims into engaging with malicious content.
ETLM Assessment:
The threat actor behind the phishing campaign targeting Facebook business users in Taiwan remains unidentified but showcases advanced social engineering skills, effectively manipulating victims through localized content and legal impersonation. The campaign specifically targets users in Taiwan, focusing on sectors such as technology, media, manufacturing, and online retail.
Utilizing popular platforms like Google Appspot and Dropbox for malware delivery, the actor embeds malicious payloads within legitimate software binaries to evade detection. This reflects a broader trend in the threat landscape where attackers increasingly exploit human vulnerabilities, especially the urgency surrounding perceived legal threats, to prompt action from targets.
As cybercriminals refined their tactics, organizations face a growing risk from targeted phishing attacks that leverage credible impersonation and localized messaging. Future assessments indicate that these threats will continue to evolve, with actors likely adopting more sophisticated methods and targeting emerging technologies. Ongoing vigilance and enhanced security measures will be crucial for mitigating these evolving threats.
Recommendations:
1. Strengthen Email Security:
Filter Emails with Legal Keywords: Configure email filtering systems to flag or quarantine emails containing terms commonly used in legal threats, such as “copyright infringement,” “legal notice,” or “immediate action required.”
Block Known Malicious Domains: Update email security protocols to block domains identified as part of the phishing infrastructure, including those from Google Appspot and Dropbox that were used for malware delivery.
2. User Training on Targeted Phishing Techniques
Focus Training on Localized Phishing: Conduct training sessions that specifically address the use of traditional Chinese in phishing emails and educate users about the tactics of impersonating legal departments.
Highlight Real-World Examples: Use examples of the phishing email templates noted in the article to help employees recognize and report similar attempts.
3. Implement Multi-Factor Authentication (MFA)
Mandatory MFA for Facebook Business Accounts: Ensure that all accounts involved in business and advertising on Facebook have multi-factor authentication enabled to reduce the risk of unauthorized access even if credentials are compromised.
4. Endpoint Protection and Malware Detection
Deploy Advanced Malware Detection Solutions: Use endpoint security solutions that can specifically detect and block known information stealers like LummaC2 and Rhadamanthys, which were used in the campaign.
Monitor for Executable Filenames: Set up alerts for the execution of suspicious file names mentioned in the article (e.g., fake PDF executables), particularly those mimicking legal documents.
5. Incident Response Protocols
Establish a Rapid Response Plan: Develop a specific incident response plan for phishing attacks that includes immediate steps for isolating affected systems and communicating with users.
Create a Reporting Mechanism: Implement a simple process for users to report suspected phishing attempts, ensuring swift investigation and action.
6. Regular Security Audits and Updates
Audit Existing Security Measures: Regularly review and update email security measures, user access controls, and endpoint protection to ensure they are effective against the tactics described in the article.
Check for Malware Presence: Conduct periodic scans for malware using updated threat definitions to catch any infections that may have slipped through initial defenses.
7. Data Backup and Recovery Practices
Implement Regular Backups: Ensure all critical business data, particularly those related to Facebook accounts, are backed up frequently to allow for recovery in case of a malware infection.
Test Recovery Procedures: Conduct regular drills to ensure that recovery from a malware incident can be executed smoothly and efficiently.
By implementing these recommendations, organizations can bolster their defenses against the specific tactics used in this phishing campaign, minimizing the risk of compromise and enhancing overall security posture.
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Execution | T1129 | Shared Modules |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| DefenseEvasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1497.002 | Virtualization/Sandbox Evasion: User Activity Based Checks |
| Defense Evasion | T1574 | Hijack Execution Flow |
| CredentialAccess | T1056 | Input Capture |
| CredentialAccess | T1056.001 | Input Capture: Keylogging |
| Discovery | T1012 | Query Registry |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1497.002 | Virtualization/Sandbox Evasion: User Activity Based Checks |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Chinese hackers targeting Canadian government
The Canadian Centre for Cyber Security (CCCS) released its National Cyber Threat Assessment for the following two years, in which it disclosed that in the last four years alone, networks belonging to at least 20 Canadian government agencies have been compromised by Chinese state-sponsored actors. According to the report: “The People’s Republic of China’s (PRC) expansive and aggressive cyber program presents the most sophisticated and active state cyber threat to Canada today. The PRC conducts cyber operations against Canadian interests to serve high-level political and commercial objectives, including espionage, intellectual property (IP) theft, malign influence, and transnational repression. Among our adversaries, the PRC cyber program’s scale, tradecraft, and ambitions in cyberspace are second to none.”
The CCCS also outlines strategic threats from Russia and Iran, but notes that “[t]he PRC’s cyber program surpasses other hostile states in both the scope and resources dedicated to cyber threat activity against Canada.”
ETLM Assessment:
China is a global champion in using cyber-attacks as a tool of statecraft and the hands-on role of the government in the economy only reinforces the drive to use cyber-attacks for IP theft as well as classic espionage, even in matters that are purely business related with technologies of no military or dual use. China has a bigger hacking program than that of every other major nation combined and any large company in industries outlined in Chinese development plans will need to invest in external threat landscape management solutions to stay ahead of relentless and repeated assaults by Chinese hackers. The same goes for governments of NATO countries, which are seen by Beijing not only as a target themselves, but as an entry point to the Washington-dominated alliance system.
Moscow initiates a massive spearphishing campaign
Researchers have recently published a major spearphishing campaign launched by Cozy Bear (aka Midnight Blizzard or APT29), a threat actor attributed to Russia’s Foreign Intelligence Service (SVR). The threat actor is sending spearphishing emails to thousands of individuals at over a hundred organizations in the government, academia, defense, NGOs, and other sectors. The emails impersonated Microsoft employees to deliver a signed Remote Desktop Protocol (RDP) configuration file, which is a new access vector for the threat actor.
ETLM Assessment:
In this campaign, the malicious .RDP attachment contained several sensitive settings that would lead to significant information exposure. Once the target system is compromised, it connects to the actor-controlled server and bidirectionally maps the targeted user’s local device’s resources to the server. Resources sent to the server may include but are not limited to, all logical hard disks, clipboard contents, printers, connected peripheral devices, audio, and authentication features and facilities of the Windows operating system, including smart cards. This access could enable the threat actor to install malware on the target’s local drive(s) and mapped network share(s), particularly in AutoStart folders, or install additional tools such as remote access trojans (RATs) to maintain access when the RDP session is closed. This campaign represents a classic state-driven espionage enabled by cyber means with many possibly underway at the same time.
The Meow Ransomware impacts PT Transportasi Gas Indonesia
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; PT Transportasi Gas Indonesia (www[.]tgi[.]co[.]id), was compromised by Meow Ransomware. PT Transportasi Gas Indonesia (TGI), commonly known as Transgasindo, is a significant player in Indonesia’s natural gas transportation sector. The company is primarily involved in the transportation of natural gas through pipelines, serving both domestic and international markets.
The compromised data package includes a wide array of sensitive information, specifically:
The total size of the compromised data is approximately 180 GB. The asking price for the compromised data is set at $50,000 for exclusive access (single buyer) and $25,000 when shared among multiple buyers.

Relevancy & Insights:
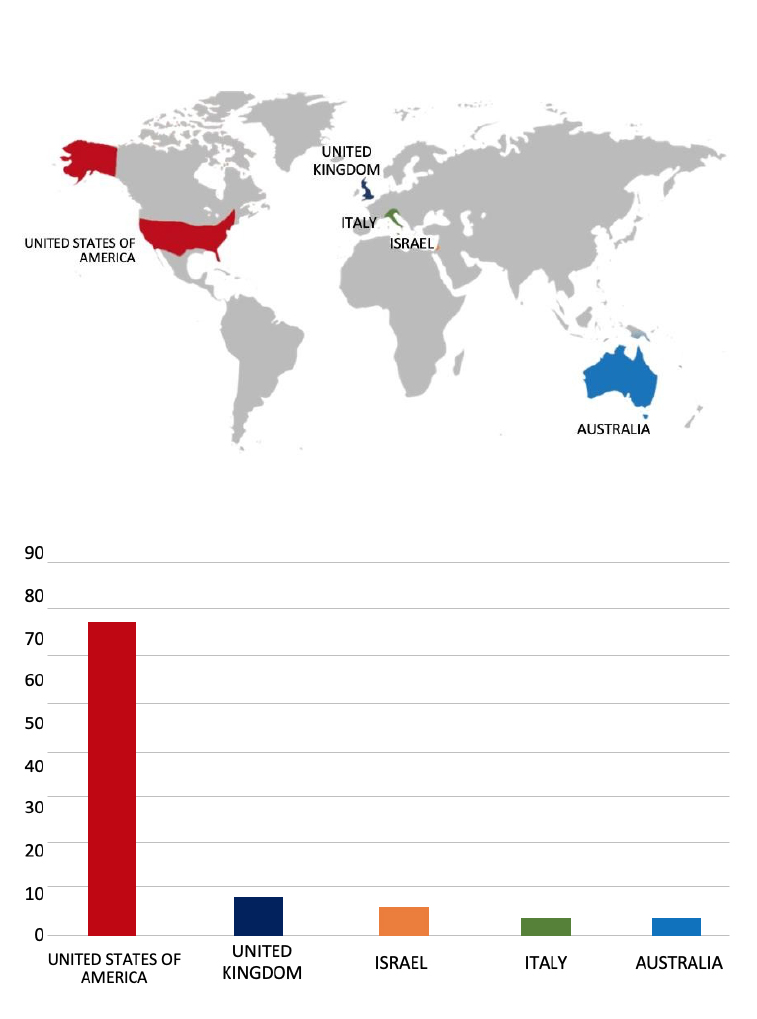
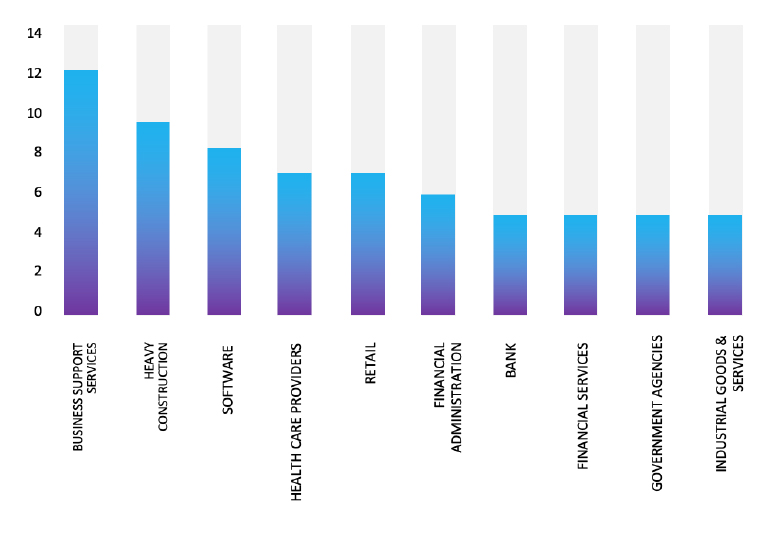
ETLM Assessment:
Meow Ransomware employs various infection methods, including phishing emails, exploit kits, Remote Desktop Protocol (RDP) vulnerabilities, and malvertising. Based on recent assessments by CYFIRMA, Meow ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on PT Transportasi Gas Indonesia, a leading Energy and Transport company in Indonesia, highlighting Meow Ransomware’s significant threat presence in the Southeast Asian region.
The RansomHub Ransomware Impacts the Sanyang Motor Co., Ltd
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Taiwan; Sanyang Motor Co., Ltd (www[.]sym-global[.]com), was compromised by RansomHub Ransomware. Sanyang Motor Co., Ltd. is a Taiwanese manufacturer of motorcycles, scooters, and automobiles. Originally known as Sanyang Industry Co., Ltd., the company has developed extensive expertise in the two-wheeler market and has expanded its operations internationally, with production facilities in Taiwan, China, and Vietnam. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. The total size of the compromised data is approximately 265 GB.
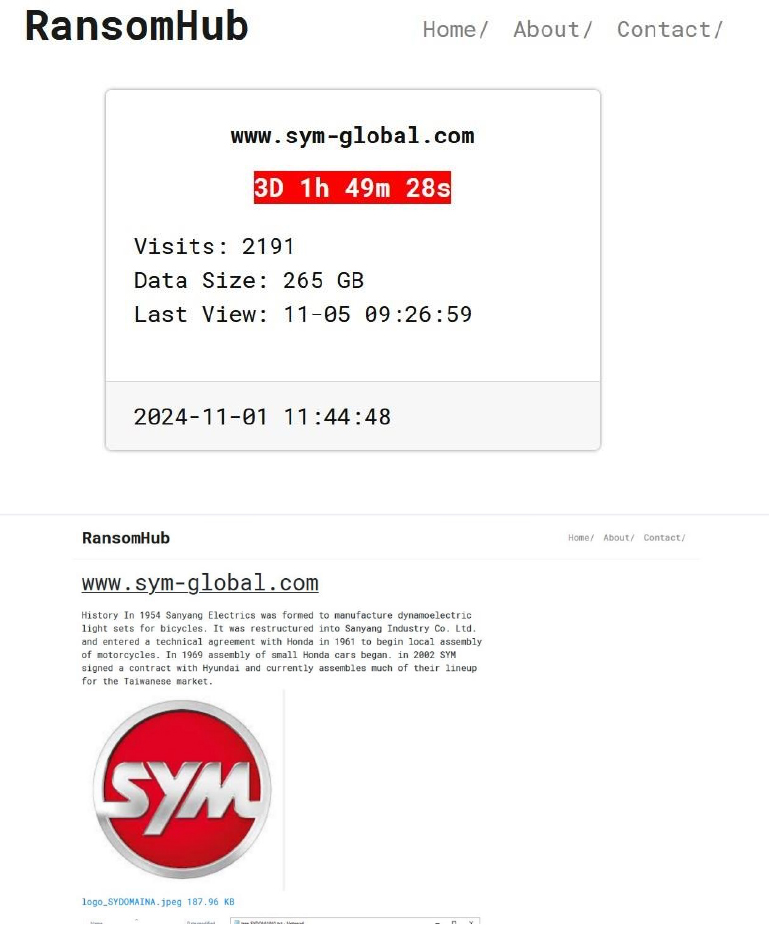
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Sanyang Motor Co., Ltd, a prominent Manufacturing company from Taiwan, highlighting RansomHub’s significant threat presence in the East Asian region.
Vulnerability in WatchTowerHQ plugin for WordPress
Summary:
The vulnerability allows a remote attacker to bypass the authentication process.
Relevancy & Insights:
The vulnerability exists due to the “watchtower_ota_token” default value is empty and the not empty check is missing in the “Password_Less_Access::login” function.
Impact:
A remote attacker can bypass the authentication process and gain unauthorized access to the application.
Affected Products:
https[:]//www[.]wordfence[.]com/threat- intel/vulnerabilities/wordpress-plugins/watchtowerhq/watchtowerhq-396- authentication-bypass-to-administrator-due-to-missing-empty-value-check
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
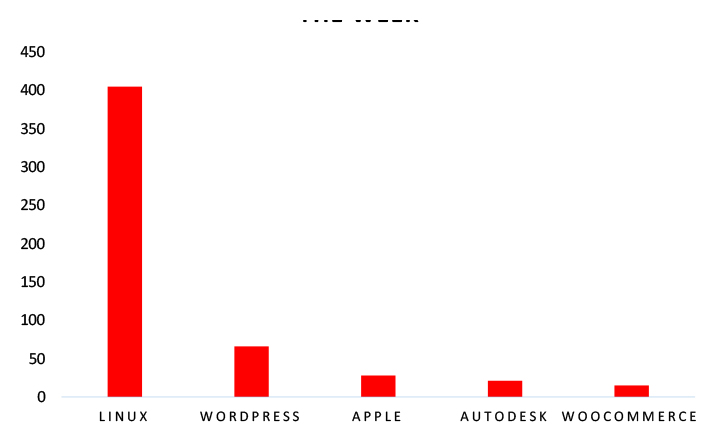
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
TOP 5 MOST AFFECTED TECHNOLOGIES OF THE WEEK
ETLM Assessment
Vulnerability in the WatchTowerHQ plugin for WordPress can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of the WatchTowerHQ plugin is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding website monitoring, management, and customer service activities across different geographic regions and sectors, especially for agencies and companies managing multiple sites.
Hunters International Ransomware attacked and published the data of Ambica Steels
Summary
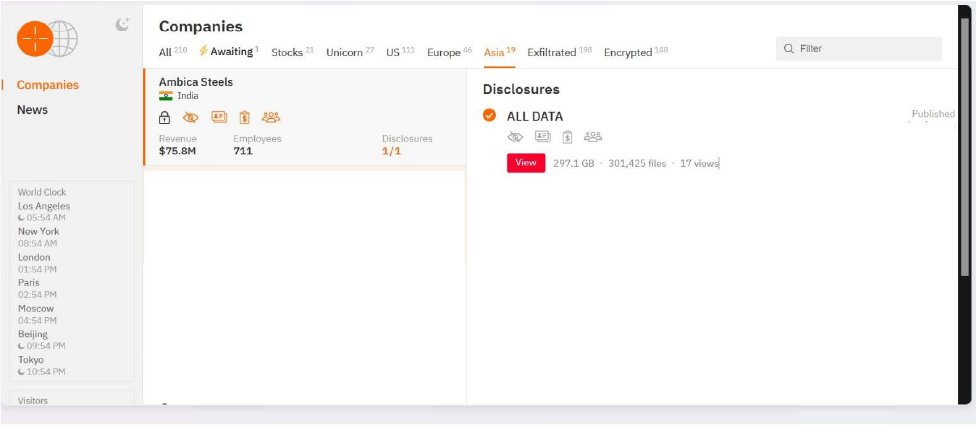
Recently, we observed that Hunters International Ransomware attacked and published the data of Ambica Steels (www[.]ambicasteels[.]com) on its dark web website. Ambica Steels Limited, based in India, is a prominent manufacturer and exporter of stainless-steel products, particularly known for its stainless-steel long products. The company is recognized for producing high-quality materials used across various industries, including automotive, construction, and energy. The company’s product portfolio features a wide array of stainless-steel bars (such as bright round, precision round, and hexagon bars), stainless steel wires, and welded wires. They also produce specialized items, such as hot-rolled bars, which are used in the forging industry due to their high formability and machinability. Additionally, Ambica Steels is the largest Indian producer of Duplex stainless-steel long products, which are noted for their durability and corrosion resistance, ideal for applications in demanding environments like seawater systems and heat exchangers. Ambica Steels has invested significantly in modern technology and infrastructure, including Electric Arc Furnaces, Argon Oxygen Decarburization (AOD) refining, and continuous casting facilities to maintain the quality and consistency of its products. This focus on quality and sustainability has enabled Ambica Steels to establish a strong global presence, exporting to over 50 countries worldwide. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database. The scale of the data exposure measures approximately 297.1 GB, comprising a total of 3,01,425 discrete files.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Hunters International ransomware group is expected to continue targeting a wide range of industries globally, with a particular focus on the United States, Europe, and Asia. A recent attack on Ambica Steels, a leading Manufacturing company in India, highlights the significant threat this ransomware poses in the South Asian region. This incident highlights the growing risk to critical industries in the area and the importance of strengthening cybersecurity defenses against such sophisticated threats.
Stamps Indonesia Data Advertised on a Leak Site
Summary
The CYFIRMA Research team observed a potential data leak related to Stamps Indonesia (https[:]//about[.]stamps[.]id/) in an underground forum. Stamps Indonesia is a leading provider of native mobile apps, customer relationship management (CRM), and order management systems with multinational clients all across Asia. Stamps Indonesia Works with companies such as Ace Hardware, Tim Hortons, Levi’s, Burger King, Popeyes & more. The breached data contains NCR Reports, Vouchers, Invoices, Transactions, Orders & more. The data breach has been attributed to a threat actor identified as “almighty4444”.

Taiwan Jewelry Store Data Advertised on a Leak Site
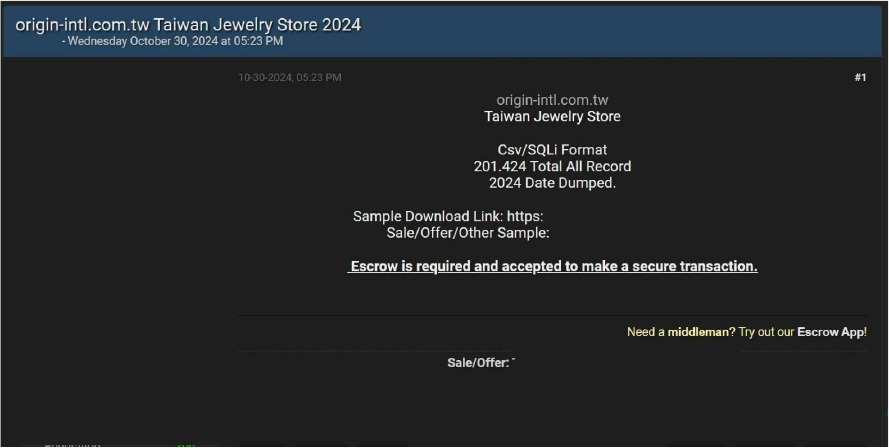
Summary:
A major data leak involving a Taiwanese jewelry store, http[:]//origin-intl[.]com[.]tw, has been put up for sale on the dark web. The breach reportedly includes 201,424 records in CSV/SQLi format. The seller is offering samples and requires escrow for secure transactions. Contact is available via Telegram for interested buyers.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Almighty4444” has recently emerged in the cybercrime landscape, drawing attention to its activities. CYFIRMA’s assessment highlights growing concerns around this actor, marking it as a potential risk to cybersecurity. Organizations are encouraged to strengthen their defenses against such rising threats.
Recommendations: Enhance the cybersecurity posture by:
In a recent post on the dark web forum, a user operating under the alias “888” has alleged a significant data breach affecting Ensinio, an e-learning provider. The individual claims to have exposed the personal information of nearly 161,000 users.
Ensinio is described in the forum post as a comprehensive platform designed for online teaching and e-learning. According to the threat actor’s claims, the breach, which allegedly occurred in October 2024, led to the exposure of various user data fields, ranging from basic identification to sensitive personal information.
The data reportedly compromised includes:
ID, Email, First Name, Last Name, Display Name, Username, Coins, Document, Document Type, Email Verified In, Gender, Bio, Date of Birth, Address, Zip Code, Public Email, Website, Phone, Asset, Admin, Super Admin, Creation Type and Created On.

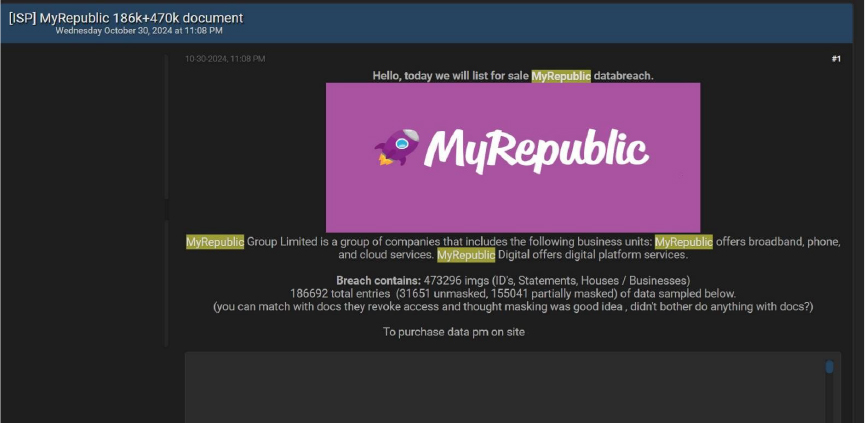
A massive data breach involving MyRepublic, a Singapore-based internet service provider, has surfaced online. The breach reportedly includes 473,296 images and 186,692 client records, with sensitive information such as ID documents, billing addresses, and contact details. Some data is masked, but over 31,000 entries are completely unmasked. The seller is promoting the data through Telegram for purchase.
ETLM Assessment
The “888” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
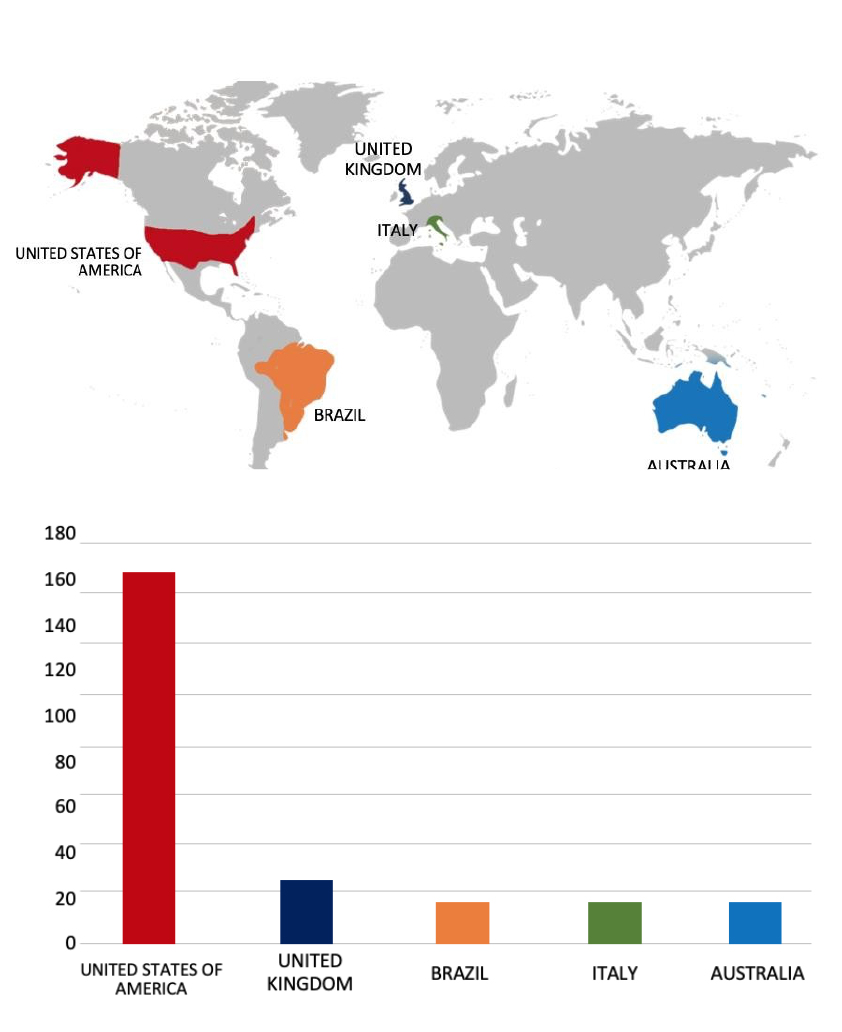
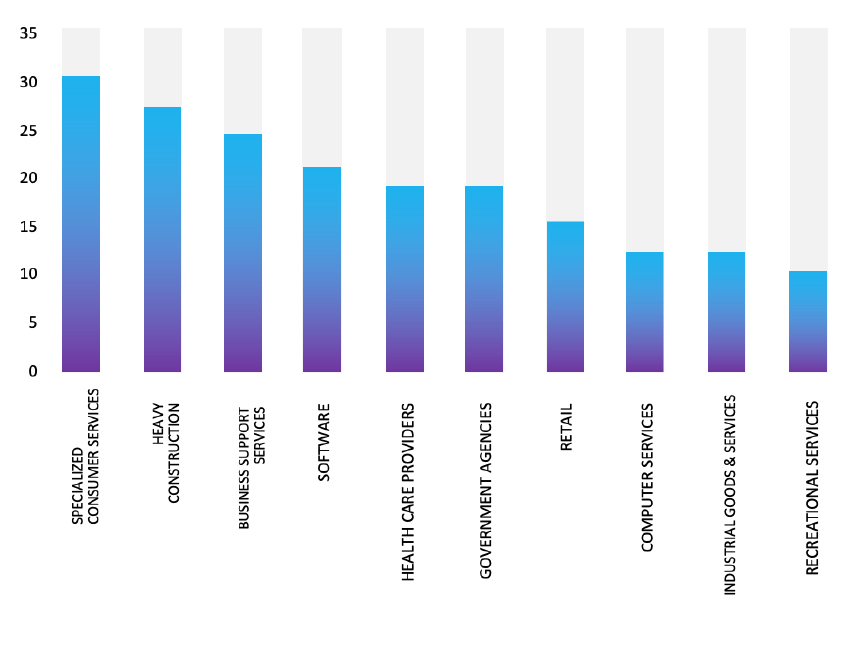
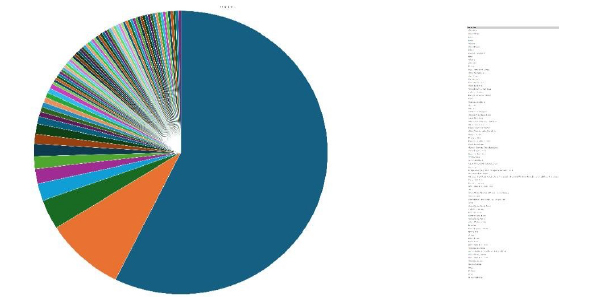
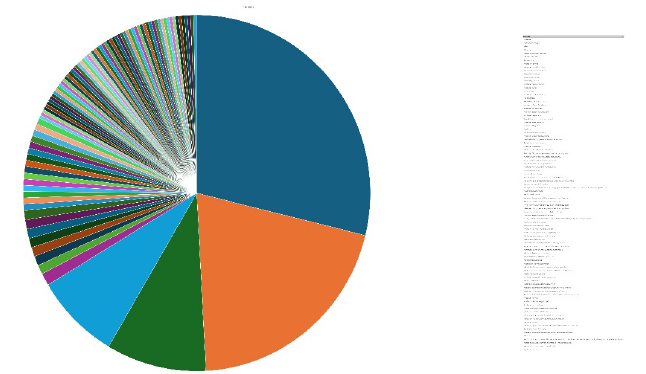
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.