Published On : 2024-03-08
Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Target Industries: Education, Healthcare, and Manufacturing.
Target Geography: Romania
Introduction
CYFIRMA Research and Advisory Team has found BackMyData ransomware while monitoring various underground forums as part of our Threat Discovery Process.
BackMyData
BackMyData ransomware, part of the Phobos ransomware family, was seen in the wild by the end of January 2024.
It propagates through exploiting insecure or improperly configured Remote Desktop Protocol (RDP) connections,
In early 2024, BackMyData ransomware was associated with a large-scale attack on HIS (Hipocrate Information System).
Upon infection, BackMyData establishes persistence by writing multiple copies of itself across the file system. The executables are duplicated and placed in various locations, ensuring the ransomware’s continued operation.
Copies of the executables are written to:
\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\
Persistence is also achieved via the Registry (Run key) in:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\ HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\
The following Volume Shadow Copy Removal / Manipulation commands are observed:
vssadmin.exe delete shadows /all /quiet WMIC.exe shadowcopy delete
Commands related to manipulating System Recovery employed by ransomware are noted below.
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures bcdedit.exe /set {default} recoveryenabled no wbadmin.exe delete catalog -quiet
The ransomware encrypts the files and appends .BACKMYDATA extension to the encrypted files.
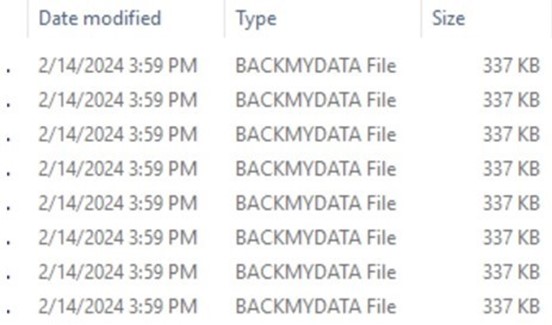
Screenshot of files encrypted by BACKMYDATA ransomware (Source: Surface Web) Ransom notes in various formats—text, HTML, and .HTA—are composed and presented on compromised hosts during infection. BackMyData favours the Session Messenger app as the primary communication platform.
Those targeted by BackMyData receive instructions to communicate with the attackers through the email address specified in the ransom notes or via the Session Messenger app. Details for contacting Session Messenger are also supplied in the ransom notes.
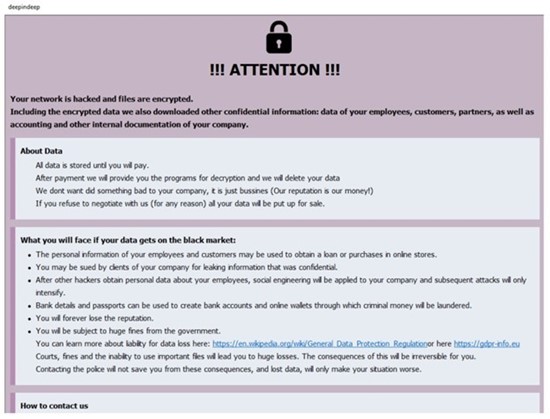
Ransom note. (Source: Surface Web)
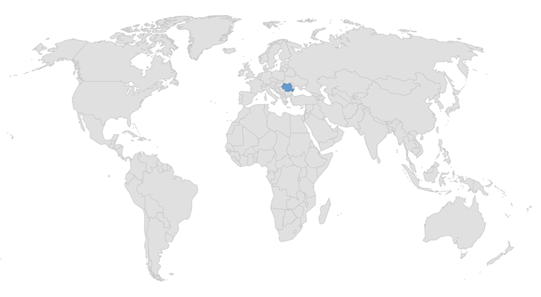
Countries targeted by Backmydata
Relevancy & Insights:
- Targeting widely used Windows operating systems, this ransomware poses a significant threat to diverse industries and organizations.
- Ransomware evades network defenses by disabling Windows Firewall, by modifying registry keys like HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Paramet ers\FirewallPolicy\PublicProfile\EnableFirewall and HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SharedAccess\Paramet ers\FirewallPolicy\PublicProfile\DoNotAllowExceptions, setting the DWORD values to
- The ransomware deletes the file “C:\$SysReset\Logs\Timestamp.xml”, this hampers the system’s ability to track events or diagnostics, impairing its capability to actively monitor and record system-related activities.
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. This technique is used by the ransomware to determine whether it is operating in a debug environment. This feature aids the ransomware in avoiding analysis and detection attempts.
- Calls to WMI: The ransomware is making calls to the Windows Management Instrumentation (WMI) framework. WMI is a powerful tool used by many legitimate applications and services, but it can also be exploited by malware to execute commands, collect information, or perform system modifications.
Following are the TTPs based on the MITRE Attack Framework.
| Sr.
No |
Tactics |
Techniques/Sub-Techniques |
| 1 |
TA0002: Execution |
T1053: Scheduled Task/Job |
| T1129: Shared Modules |
| 2 |
TA0003:
Persistence |
T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution:
Registry Run Keys / Startup Folder |
| 3 |
TA0004: Privilege Escalation |
T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution:
Registry Run Keys / Startup Folder |
|
4 |
TA0005: Defense Evasion |
T1027: Obfuscated Files or Information |
| T1036: Masquerading |
| T1070.004: Indicator Removal: File Deletion |
| T1112: Modify Registry |
| T1134: Access Token Manipulation |
| T1222: File and Directory Permissions
Modification |
| T1497: Virtualization/Sandbox Evasion |
| T1562.001: Impair Defenses: Disable or Modify
Tools |
| T1564.001: Hide Artifacts: Hidden Files and
Directories |
| 5 |
TA0006:
Credential
Access |
T1003: OS Credential Dumping |
| T1056: Input Capture |
|
6 |
TA0007:
Discovery |
T1010: Application Window Discovery |
| T1012: Query Registry |
| T1016: System Network Configuration
Discovery |
| T1057: Process Discovery |
| T1082: System Information Discovery |
| T1083: File and Directory Discovery |
| T1135: Network Share Discovery |
| T1497: Virtualization/Sandbox Evasion |
| T1518.001: Software Discovery: Security
Software Discovery |
| T1614: System Location Discovery |
| 7 |
TA0008: Lateral
Movement |
T1080: Taint Shared Content |
| 8 |
TA0009:
Collection |
T1005: Data from Local System |
| T1056: Input Capture |
| 9 |
TA0011:
Command and |
T1071: Application Layer Protocol |
ETLM Assessment:
- Based on CYFIRMA’s analysis of available data, BackMyData ransomware shows signs of tactical advancement, expanding its threat landscape. Phobos ransomware’s iterative evolution underscores its persistent adaptability and escalating sophistication in malicious strategies. With refined evasion methods and robust encryption capabilities, there’s a heightened emphasis on targeting critical system components. To mitigate risks, organizations should maintain vigilance, update cybersecurity protocols regularly, and engage in proactive threat intelligence monitoring for effective defense against evolving ransomware threats.
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigma Rule
title: Delete shadow copy via WMIC
threatname:
behaviorgroup: 18
classification: 0 mitreattack:
logsource:
category: process_creation product: windows
detection: selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’ condition: selection
level: critical
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATIONS
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATIONS
- Update all applications/software regularly with the latest versions and security patches
- Add the Sigma rules for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
1. Trending Malware of the Week
Type: Information Stealer
Objective: Credential Stealing, Data Exfiltration
Target Technology: macOS, Browsers (Chrome, Brave, Edge, Vivaldi, Firefox, and Opera), Cryptocurrency Browser Extensions, Cryptocurrency wallets (Electrum, Coinomi, Exodus, and Atomic)
Active Malware of the Week
This week “Atomic (AMOS) Stealer” is trending.
Summary
Researchers have identified a new variant of the Atomic Stealer, also known as AMOS Stealer, as a significant threat to macOS users in the past year. This new variant employs a Python script to maintain stealth. The discovery was prompted by the isolation of small- sized (1.3 MB) but suspicious macOS disk image files, leading researchers to suspect the presence of this variant. The Python script, dropped on the disk, is designed to gather sensitive data from various sources and transmit it to the C2 server, underscoring the evolving tactics of this threat.
Atomic Stealer
In April 2023, Atomic Stealer made its debut and has since maintained an active presence through ongoing updates. Positioned within the category of stealers, this malicious program is tailored specifically for macOS. This type of malware is adept at extracting and exfiltrating information from infected devices. Atomic specifically targets browsers such as Chrome, Brave, Edge, Vivaldi, and Opera, stealing crucial data like Web Data, Login Data, and Cookies. Moreover, it extends its reach to cryptowallets and cryptocurrency-related browser extensions, showcasing its versatility in targeting both general and cryptocurrency- specific data.
Attack Method
This version of the malware employs a unique approach, utilizing a combination of Python and Apple Script code to achieve its objectives. Additionally, it appears to make efforts to identify and evade sandbox or emulator execution environments.
In this attack scenario, each DMG file comprises a FAT binary with two Mach-O files for Intel and ARM architectures, functioning as droppers rather than directly engaging in data theft or information exfiltration. Upon clicking the DMG file, users are prompted to right-click and open the Crack Installer application embedded within the disk image. This tactic, commonly employed by threat actors, aims to bypass Apple’s security mechanisms, enabling the user to open the application even if it lacks digital signatures.
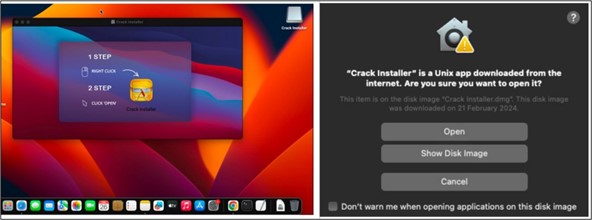
Upon opening the Crack Installer, the embedded Mach-O binary initiates the dropping of a Python script onto the disk, specifically at the path /var/tmp/olx, followed by its execution. The XOR-ed content of the script is initially stored within the const section of the binary. Subsequently, it is decoded and deposited on the disk for further action.
Python Stealer
The Python script dropped on the disk is designed to collect sensitive data from various sources, with the intention of transmitting the gathered information to the C2 server. The script’s capabilities encompass the collection of the following data:
- Files associated with installed crypto-wallet extensions and
- Browser data (Passwords, Cookies, Login Data, Forms data, Profiles data, etc)
- Files with targeted extensions from Desktop and Documents directories
- Hardware-related and system information
- The password of the local user account
The initial action of the script involves deceiving the user by presenting a fake dialog that mimics the operating system, aiming to extract the user’s password. Disguised as a system update, the malware requests the local account password. This deceptive technique is consistent with recent variants of Atomic Stealer. If the entered password is accurate, it is then recorded in a file named “psw.” The script analysis unveiled a noteworthy and unusual method involving the integration of Python with Apple Scripting. Specifically, the filegrabber() function executes an extensive block of Apple script using the osascript -e command.
The Apple Script block in this new variant of Atomic Stealer exhibits a notable resemblance to the 2nd variant of RustDoor, emphasizing the shared goal of harvesting sensitive files from the victim’s computer. The current version appears to be an advanced iteration of the script used by RustDoor, introducing additional features. Notably, it now includes the collection of the Cookies.binarycookies file, which stores Safari browser cookies and is situated at the path:
- ~/Library/Containers/com.apple.Safari/Data/Library/Cookies.
After collecting files with targeted extensions from specific locations, the script proceeds to gather detailed information about the compromised computer using the system_profiler utility integrated into the macOS operating system. By employing SPSoftwareDataType, SPHardwareDataType, and SPDisplaysDataType arguments, the attackers focus on obtaining hardware details, operating system version, and information about connected displays and graphic cards. This data may serve to identify virtual environments or executions within sandboxes. The results of this command are written to a file named “user.” Subsequently, the threat actors augment the collected file archive by including the
~/Library/Keychains/login.keychain-db file, associated with the user’s login keychain, containing sensitive information like passwords, encryption keys, and certificates.
Additionally, the ~/Library/Application Support/Binance/app-store.json file is targeted, indicating an increasing interest in cryptocurrency platforms by the Atomic Stealer variants.
Targeting browsers
The chromium() function plays a pivotal role in collecting various files from each profile of targeted Chromium-based browsers, including Chrome, Brave, Edge, Vivaldi, and Opera. The files encompass Web Data, Login Data, and Cookies. Additionally, the function strives to gather data from installed cryptocurrency browser extensions, with the script containing hardcoded IDs for 64 specific extensions. This variant of the Atomic Stealer family uses Mach-O binaries that embed IDs corresponding to the targeted browser extensions.
Complementing this, the parseFF() function is employed to gather browser information, specifically from Firefox. It accomplishes this by collecting files associated with all existing profiles in the Firefox browser.
Targeting Wallets
The script possesses the capability to collect files associated with installed cryptocurrency wallets, including Electrum, Coinomi, Exodus, and Atomic. This involves extracting the content from the directories where these applications store their sensitive data on the victim’s computer.
Sending the collected data to the C2 server
The script accumulates all the gathered data from the targeted computer into a ZIP archive stored in memory, aiming to minimize traces on the compromised device. Following the data collection phase, the content of the archive is transmitted to the hardcoded C2 address, defined at the script’s beginning, through a POST request to the /p2p endpoint.
The archive has the following structure:
INSIGHTS
- The rise of infostealers targeting Mac users, exemplified by Atomic Stealer, underscores the growing viability of threats against the macOS ecosystem. The widespread adoption of Macs in both organizational and personal settings has made them lucrative targets for threat Atomic Stealer’s dynamic evolution, marked by various versions implementing novel techniques such as the fusion of Python and Apple Scripting, showcases a high level of adaptability. This adaptability is crucial in enabling the malware to continually evolve and outpace detection mechanisms.
- The continuous improvement and added capabilities of the threat actor behind Atomic Stealer pose an ongoing risk to user Beyond its initial intrusion, the true menace lies in the malware’s potential for extensive data exfiltration, compromising sensitive information, login credentials, and personal data.
- Atomic Stealer’s operational sophistication is evident in its strategic approach to minimizing traces on compromised devices. By employing a sophisticated ZIP archive stored in memory for collected data, the malware demonstrates a nuanced understanding of evasion tactics. Furthermore, its seamless communication with a hardcoded Command and Control (C2) server, facilitated through a POST request to a designated endpoint, highlights the efficiency and control that threat actors maintain over the exfiltrated data. This level of operational finesse emphasizes the challenges of detecting and mitigating the impact of such a dynamic and well-coordinated threat.
ETLM ASSESSMENT
- From the ETLM perspective, CYFIRMA anticipates that the ongoing evolution of Atomic Stealer poses significant challenges for macOS users, especially given the popularity of the operating system. The persistent targeting of macOS by various Atomic Stealer variants, coupled with the prevalence of other malware families, raises concerns for both personal and professional users. As macOS continue to attract threat actors, the focus on compromising sensitive information and login credentials is expected to intensify. Organizations relying on macOS should adopt a proactive approach to cybersecurity, anticipating refined methodologies and potentially broader targets from threat actors behind infostealers like Atomic Stealer.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
- Deploy an Extended Detection and Response (XDR) solution as part of the organization’s layered security strategy that provides detection/prevention for malware and malicious activities that do not rely on signature-based detection methods.
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audit of workstations, servers, laptops, mobile devices to identify unauthorized/ restricted software.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT RECOMMENDATIONS
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
- Security Awareness training should be mandated for all company The training should ensure that employees:
- Avoid downloading and executing files from unverified
- Always inspect the full URL before downloading files to ensure it matches the
- Incorporate a written software policy that educates employees on good practices in relation to software and potential implications of downloading and using restricted
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts.
- Evaluate the security and reputation of each piece of open-source software or utilities before usage.
- Enforce policies to validate third-party software before
3.Weekly Intelligence Trends/Advisory
- Weekly Attack Type and Trends Key Intelligence Signals:
- Attack Type: Malware Implant, Ransomware Attacks, Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains,
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware –Play Ransomware | Malware – Atomic Stealer
- Play Ransomware – One of the ransomware
- Please refer to the trending malware advisory for details on the following:
Malware – Atomic Stealer
- Behaviour –Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
- Threat Actor in Focus
Unveiling the Cyber Threat: The Kimsuky Attack on South Korea’s Semiconductor Industry
- Threat Actors: Kimsuky
- Attack Type: Publicly exposed vulnerabilities
- Objective: Espionage
- Target Technology: Windows
- Target Geographies: South Korea
- Target Industries: Semiconductor
- Business Impact: Data Loss, Data exfiltration
Summary:
- The APT group ‘Kimsuky,’ linked to the North Korean regime, has been known for its cyber espionage activities, targeting various entities to steal sensitive information. The group has targeted South Korea’s semiconductor industry, highlighting its interest in obtaining data related to advanced technology and other strategic areas. Kimsuky is believed to be motivated by the North Korean government’s agenda, aiming to acquire information that could advance its domestic programs, such as developing weapons or other strategic capabilities.
North Korean APT groups have been targeting companies with internet-connected servers, exploiting vulnerabilities in their systems. Specifically, they have focused on the business servers of these companies, which are used to manage documents and other critical data. To carry out their attacks, they employ sophisticated techniques such as “Living off the Land” (LotL) techniques, minimizing the use of traditional malware and instead utilizing normal programs installed on the servers. This method makes their activities less noticeable and harder to detect, even with security tools. In recent incidents, the hackers breached two companies, one in December, last year and the other in February this year, they hacked into the configuration management server and stole valuable assets such as product design drawings and on-site photos of facilities.Relevancy & Insights:
- The threat actor, known as Kimsuky, linked to the North Korean regime, utilizes Living off the Land (LotL) attack techniques to target semiconductor companies in South Korea. By leveraging legitimate software and functions within the system, they evade detection, while stealing sensitive data like product designs and facility photos. North Korean threat actors have previously targeted various sectors in South Korea, including nuclear, space, semiconductor, and national defense This strategy is in line with North Korea’s efforts to advance its semiconductor capabilities amidst economic sanctions, presenting continuous challenges to cybersecurity defenses.
ETLM Assessment:
- A nation-state sponsor threat actor group known as Kimsuky, believed to be linked to North Korea, showcases the concerning use of Living off the Land (LotL) attack techniques. Kimsuky’s history of cyberattacks on South Korea spans various industry sectors, indicating a pattern of seeking intelligence for strategic gains. This trend suggests that such attacks may recur in the future. North Korean threat actors, including Kimsuky, serve national interests by targeting South Korean industries to obtain valuable intelligence. This attack underscores the evolving nature of cyber threats and the need for organizations to remain vigilant and adapt their cybersecurity strategies to effectively counter such advanced tactics.
Recommendations:
- Patch Management: Regularly update and patch software and systems to address known vulnerabilities that threat actors may exploit.
- Enhance Security Measures: Implement robust cybersecurity measures, including network segmentation, intrusion detection systems, and advanced endpoint protection, to detect and prevent unauthorized access to sensitive data.
- Employee Training: Provide comprehensive cybersecurity training to employees to raise awareness about phishing attempts, social engineering tactics, and other common attack vectors used by threat actors.
- Data Encryption: Implement encryption for sensitive data both at rest and in transit to protect it from unauthorized access in the event of a security breach
- Major Geopolitical Developments in Cybersecurity
Suspected Iranian threat actor targets aerospace and defense entities
- According to researchers, the suspected Iranian threat actor UNC1549 has been targeting aerospace, aviation, and defense entities in Middle Eastern countries with two unique backdoors dubbed “MINIBIKE” and “MINIBUS.” As of February 2024, this alleged UNC1549 activity was still continuing strong, having begun at least in June 2022. The campaign overlaps with activity by Tortoiseshell; a threat actor attributed to Iran’s Islamic Revolutionary Guard Corps (IRGC). Given the emphasis on defense- related organizations and the recent tensions with Iran in light of the Israel-Hamas conflict, the possible connection between this activity and the phishing by IRGC is remarkable. In it, the Revolutionary Guard operators pretend to be part of the ‘Bring Them Home Now’ campaign, which demands the release of the Israelis who have been abducted and are being held captive by Hamas and spread malware via campaign-related emails.
ETLM Assessment:
- In a recent report, our analysts note that Iran has seemingly concluded that the Houthis’ experiment in the Red Sea has been so successful that it bears repeating in the Mediterranean and other waterways. “They shall soon await the closure of the Mediterranean Sea, [the Strait of] Gibraltar and other waterways,” Brig. Gen. Mohammad Reza Naqdi, the coordinating commander of Iran’s Islamic Revolutionary Guard Corps, told Iranian media, apparently referring to the international community. Iran however does not possess kinetic strike capability to target targets that far. On one hand, we can assume the general is referring to Iran’s cyber capabilities and the regime’s apparent willingness to use them should Tehran feel threatened, which can easily happen in a tense situation like the one that exists in the region nowadays. On the other hand, we may rest assured that Iranian hackers are doing their best to get their hands on missile (and other) technologies, blueprints, and other forms of IP, that could be used by the regime to strengthen its kinetic military capability.
4. Rise in Malware/Ransomware and Phishing
The Play Ransomware impacts the Powill Manufacturing & Engineering
- Attack Type: Ransomware
- Target Industry: Manufacturing
- Target Geography: The United States of America
- Ransomware: Play Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
- From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]powill[.]com), was compromised by the Play Ransomware. Powill Manufacturing and Engineering Inc. specializes in the manufacturing and supply of quality machined parts and sub-assemblies for the aerospace and commercial industries. The compromised data includes private and personal confidential information, client documents, budget details, payroll records, tax information, extensive technical documentation, ongoing projects, financial data, and more.
The following screenshot was observed published on the dark web:
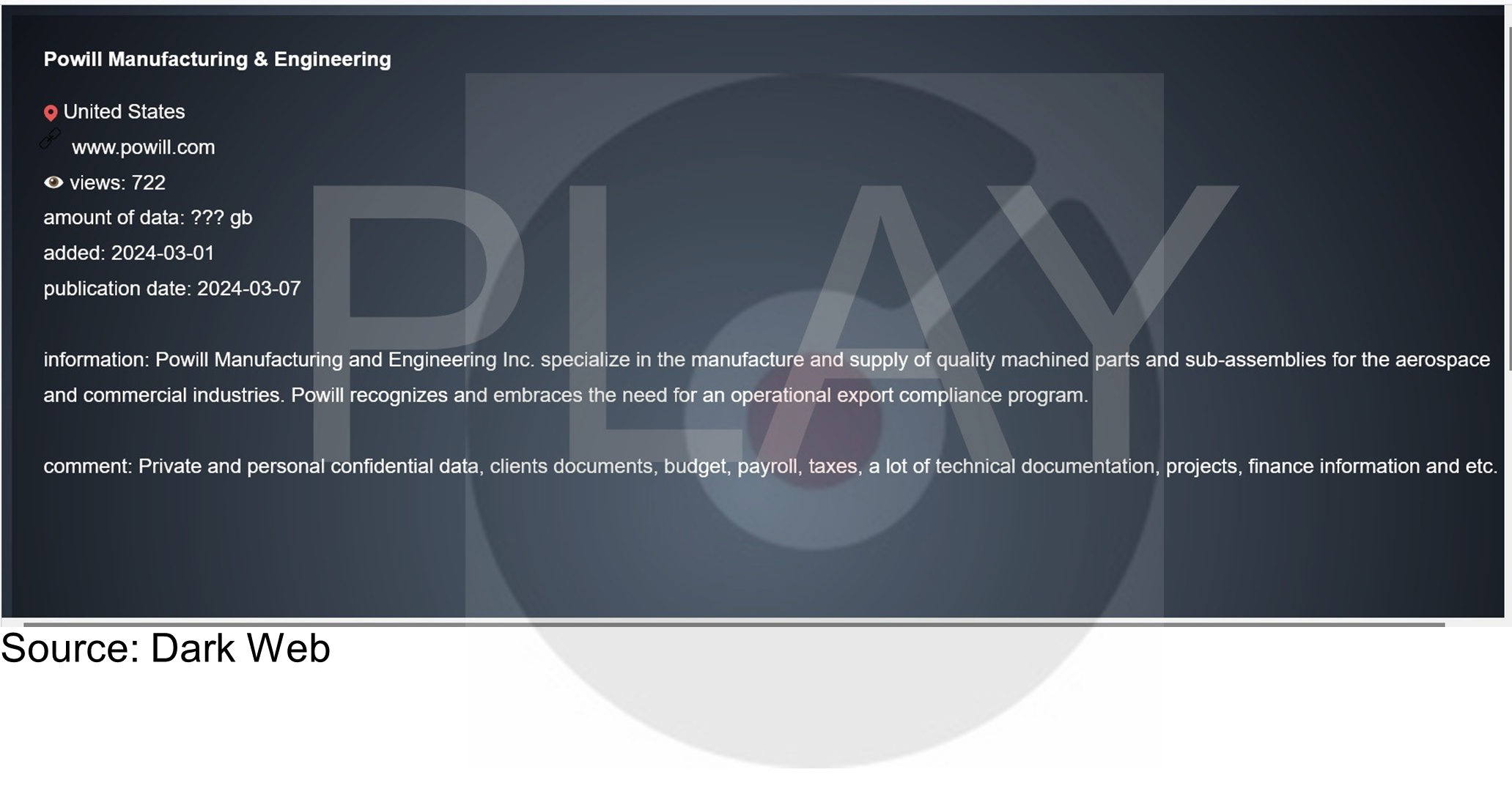
Source: Dark Web
Relevancy & Insights:
- The Play ransomware group is presumed to be a closed group, designed to “guarantee the secrecy of deals,” according to a statement on the group’s data leak website. Play ransomware actors employ a double-extortion model, encrypting systems after exfiltrating data. Ransom notes do not include an initial ransom demand or payment instructions, rather, victims are instructed to contact the threat actors via email. We observed that Play ransomware attacks have shown variation, suggesting that affiliates are following predefined playbooks, provided with the Ransomware-as-a-Service (RaaS), using identical tactics and commands.
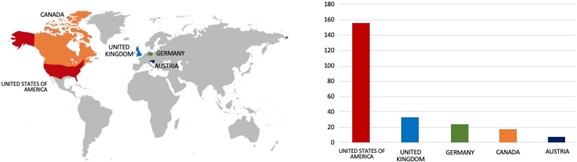
- The Play Ransomware group primarily targets countries such as the United States of America, the United Kingdom, Germany, Canada, and Austria.
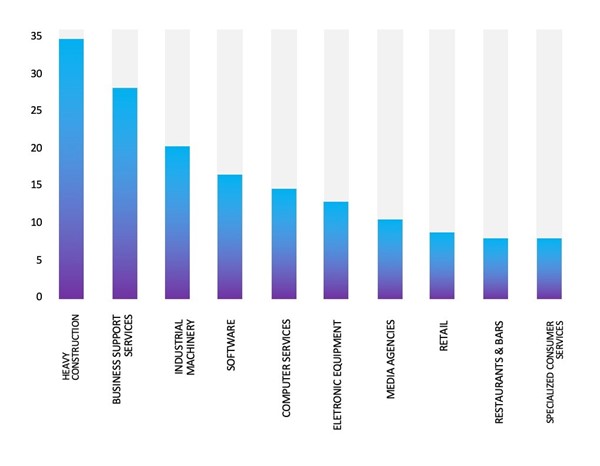
- The Play Ransomware group primarily targets industries including Heavy Construction, Business Support Services, Industrial Machinery, Software, and Computer Services.
- Based on the Play Ransomware victims list from 1 Jan 2023 to 06 March 2024, the top 5 Target Countries are as follows:
- The Top 10 Industries, most affected by Play Ransomware from 1 Jan 2023 to 06 March 2024 are as follows:
ETLM Assessment:
- Our latest findings suggest that Play Ransomware is enhancing its capabilities and are available as a service to cybercriminals. CYFIRMA believes in increased attacks on US-based companies by the Play ransomware, based on the trends Recent events, such as the Powill Manufacturing & Engineering breach highlight increased threats to manufacturing organizations.
5. Vulnerabilities and Exploits
Vulnerability in MicroDicom DICOM Viewer
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Client/Desktop application
- Vulnerability: CVE-2024-22100(CVSS Base Score 8)
- Vulnerability Type: Heap-based Buffer Overflow
- Patch: Available
Summary:
- The vulnerability allows a remote attacker to execute arbitrary code on the target
Relevancy & Insights:
- The vulnerability exists due to a boundary A remote attacker can trick a victim to open a specially crafted DCM file, trigger a heap-based buffer overflow, and execute arbitrary code on the target system.
Impact:
- Successful exploitation of this vulnerability may result in complete compromise of vulnerable systems.
Affected Products: http[:]//www[.]cisa.gov/news-events/ics-medical-advisories/icsma-24- 060-01
Recommendations:
- Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this
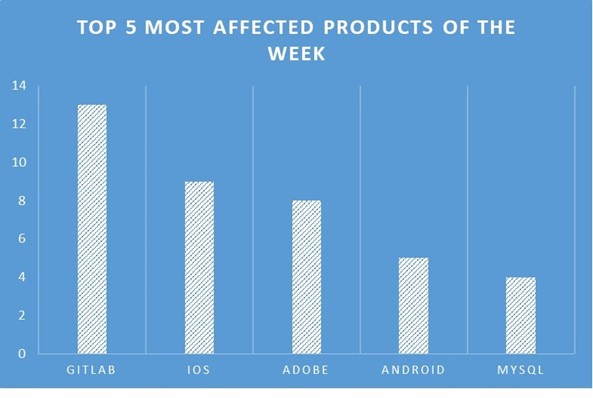
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
5.Latest Cyber-Attacks, Incidents, and Breaches
GhostLocker 2.0 Haunts Businesses Across Middle East, Africa & Asia
- Threat Actors: GhostLocker 0
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Application
- Target Geographies: Middle East, Africa & Asia
- Target Industry: Technology, Universities, manufacturing, transportation, and government
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
- Cybercriminals have recently launched an advanced iteration of the notorious GhostLocker ransomware, intensifying its impact in targeted cyber-attacks, spanning regions across the Middle East, Africa, and Asia. Two ransomware groups, GhostSec and Stormous, have joined forces in the attack campaigns with double-extortion ransomware attacks using the new GhostLocker 0 to infect organizations in Lebanon, Israel, South Africa, Turkey, Egypt, India, Vietnam, and Thailand, as well as other locations. Technology companies, universities, manufacturing, transportation, and government organizations are bearing the brunt of attacks, which attempt to scam victims into paying for decryption keys needed to unscramble data, rendered inaccessible by the file-encrypting malware. The attackers also threatened to release the stolen sensitive data unless the victims paid them money.Both the GhostLocker and Stormous ransomware groups have introduced a revised ransomware-as-a-service (RaaS) program called STMX_GhostLocker, providing various options for their affiliates. The GhostSec and Stormous groups announce their data theft in their Telegram channels and on the Stormous ransomware data leak site.Relevancy & Insights:
- GhostLocker 2.0 encrypts files on the victim’s machine using the file extension .ghost before dropping and opening a ransom note. Prospective marks warn that stolen data will be leaked unless they contact ransomware operators before a seven-day deadline expires. GhostLocker ransomware-as-a-service affiliates have access to a control panel that allows them to monitor the progress of their attacks, which are automatically registered on the dashboard. The GhostLocker 2.0 command-and-control server resolves with a geolocation in Moscow, a similar set-up to earlier versions of the
ETLM Assessment:
- The most recent iteration of GhostLocker has been coded in the GoLang programming language, a departure from its prior Python-based version. While maintaining similar functionality, the new version distinguishes itself by doubling the encryption key length from 128 to 256 bits. Ongoing assessments by CYFIRMA regarding the current campaign suggest a high probability of GhostLocker 2.0 continuing its global ransomware operations, propelled by the quest for significant financial gains.
5. Data Leaks
AlgoSec data advertised on the Leak Site
- Attack Type: Data Leaks
- Target Industry: Software
- Target Geography: The United States of America
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
- CYFIRMA Research team observed a potential data sale related to AlgoSec, {www[.]algosec[.]com}. AlgoSec is a provider of software for network security policy management, also specializing in firewall policy management. AlgoSec’s software can automate the management and enforcement of security policies across firewalls, routers, virtual private networks, and related security devices. The dataset available for sale comprises customer data, contact records, and other highly sensitive and confidential information. The total size of the dataset being sold is 227 gigabytes. The asking price for this valuable data is $2500.
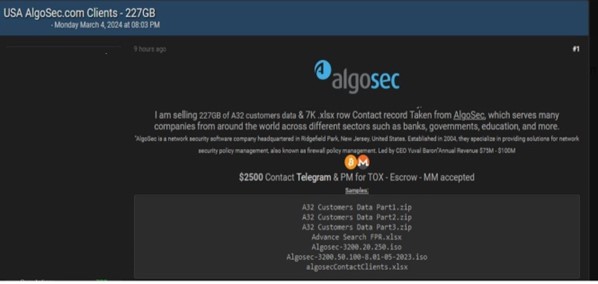
Source: Underground forums Relevancy & Insights:
In the realm of cybersecurity, opportunistic cybercriminals driven by financial incentives
are constantly seeking out exposed and vulnerable systems and applications. A significant portion of these attackers frequent underground forums, where they engage in discussions related to cybercrime and trade stolen digital assets. Unlike some financially motivated groups, such as ransomware or extortion syndicates, these attackers prefer to operate discreetly, avoiding public attention. Their modus operandi involves exploiting unpatched systems or vulnerabilities within applications to gain unauthorized access and pilfer valuable data. Subsequently, they advertise the stolen data in underground marketplaces, where it may be resold and repurposed by other malicious actors for their nefarious activities.
ETLM Assessment:
- The threat actor “Ddarknotevil” is primarily motivated by financial Currently, they are engaged in the illicit trade of sensitive data, including personally identifiable information (PII), financial records, and other confidential data obtained from AlgoSec. CYFIRMA’s assessment indicates that institutions in the United States without robust security measures and infrastructure are at an elevated risk of potential cyberattacks from this threat actor.
Other Observations
CYFIRMA Research team observed a potential data sale related to FieldLevel, {www[.]fieldlevel[.]com}. FieldLevel is an athletic recruiting tool that helps athletes find the right college teams, and coaches find the best athletes for their rosters. The data being offered for sale includes personal information such as names, addresses, email addresses, phone numbers, ages, birthdays, GPAs, heights, weights, and family details, including names, contact numbers, and parent designations. Additionally, some entries may include associated Twitter handles.
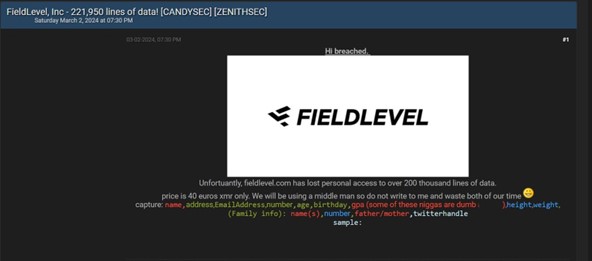
Source: Underground forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.














