


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technology: Windows
Introduction
CYFIRMA Research and Advisory Team has found Monkey Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Monkey Ransomware
Researchers have identified Monkey ransomware as a malicious program that encrypts user data and appends the “.monkey” extension to affected files. It uses strong encryption algorithms, making decryption without the attackers’ assistance nearly impossible. Once active, it also attempts to delete backups and exfiltrate sensitive information from the infected system. The ransomware typically spreads through phishing emails, malicious downloads, and trojans, and it can disguise itself as legitimate files or software. Detected under various names by multiple security vendors, Monkey ransomware primarily targets Windows systems and prevents victims from accessing their data.
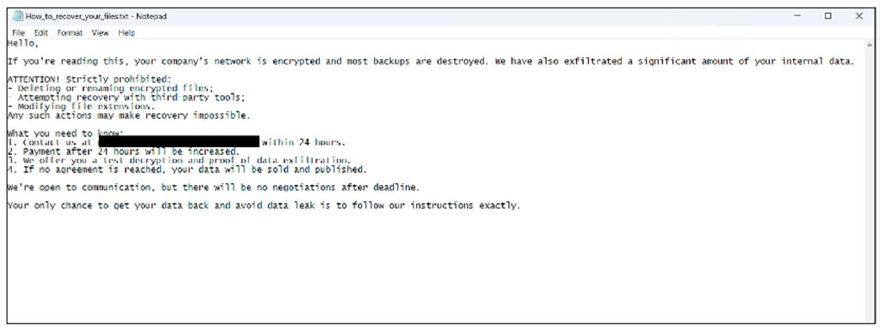
The ransom note, dropped as “How_to_recover_your_files.txt,” informs victims that their network has been compromised, backups destroyed, and data stolen. It instructs them to contact the attackers via email within 24 hours, warning that failure to comply will increase the ransom and risk public data exposure. The message forbids deleting or modifying encrypted files and offers victims a “test decryption” as proof of recovery capability. The note emphasizes strict compliance with the attackers’ instructions to avoid permanent data loss or leaks.
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1620 | Reflective Code Loading |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1485 | Data Destruction |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA assesses Monkey as a modular file-encryptor that appends .monkey and drops a How_to_recover_your_files.txt recovery note. Telemetry and sample analysis show distinct components for encryption, persistence, and data collection/exfiltration, plus implementation breadcrumbs that make the codebase easy to repackage or extend. Those traits, identifiable file/note artifacts, evidence of commodity tooling, and publicly observed samples lower the friction for iterative change: affiliates or developers can swap crypto primitives, add stealthy persistence or credential harvesters, or graft in loaders/beacons to broaden delivery and maintain access.
Operationally, Monkey could follow predictable RaaS commoditization paths: affiliate programs paired with initial-access brokers or stealer logs, and use of double/multi-extortion (encryption + data leaks). The most predictive escalation signals will be leak-site postings tied to Monkey indicators, sightings of Monkey artifacts alongside brokered access or commercial loaders, and chatter advertising affiliate offers.
Sigma rule:
title: WannaCry Ransomware Activity tags:
– attack.lateral-movement
– attack.t1210
– attack.discovery
– attack.t1083
– attack.defense-evasion
– attack.t1222.001
– attack.impact
– attack.t1486
– attack.t1490
– detection.emerging-threats logsource:
category: process_creation product: windows
detection: selection_img:
– Image|endswith:
– ‘\tasksche.exe’
– ‘\mssecsvc.exe’
– ‘\taskdl.exe’
– ‘\taskhsvc.exe’
– ‘\taskse.exe’
– ‘\111.exe’
– ‘\lhdfrgui.exe’
# – ‘\diskpart.exe’ # cannot be used in a rule of level critical
– ‘\linuxnew.exe’
– ‘\wannacry.exe’
– Image|contains: ‘WanaDecryptor’ selection_cmd:
CommandLine|contains: ‘@[email protected]’ condition: 1 of selection_*
fields:
– CommandLine
– ParentCommandLine falsepositives:
– Unknown level: critical
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan | Objectives: Credential theft, Financial Fraud, Data exfiltration | Target Technology: Android OS | Target Industry: Finance sector | Target Geography: Italy, Brazil
CYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “Herodotus” is trending.
Overview of Herodotus Malware
Researchers recently identified a new Android malware dubbed Herodotus, a fresh and evolving threat that blends original components with elements borrowed from the Brokewell family. Unlike typical successors, Herodotus represents a new creation rather than a direct upgrade. It spreads through deceptive methods, such as Smishing, where victims are lured into downloading a malicious dropper via fraudulent text messages.
Once activated, the malware focuses on complete device control, with emerging capabilities that attempt to imitate human behavior—a tactic aimed at evading biometric and behavioral security checks. Current campaigns have been detected in Italy and Brazil, while additional overlay templates uncovered by researchers suggest potential targeting of financial organizations in the United States, Turkey, the United Kingdom, Poland, and even cryptocurrency services. Its promotion as a Malware-as-a- Service during development reflects a pattern often observed in campaigns that later expand in scope or capability.
Attack Method
Herodotus typically reaches victims through sideloading, frequently after a deceptive SMS lure that directs users to download a dropper. That dropper has been seen only delivering Herodotus so far. The moment the dropper runs, it wastes no time. Its first move is to sneak past Android 13’s new defenses, installing its hidden payload under the radar. With the payload in place, it awakens Herodotus, the true agent of the operation. Then, like a magician’s trick, the dropper leads the user straight to the Accessibility Service settings, urging them to flip the fatal switch. Once the service is enabled, Herodotus throws up a fake “loading” screen — a clever illusion meant to hide the permissions quietly being granted behind the curtain.
After installation, the malware prepares for full device takeover. It inventories installed apps and reports them back to a control server, which replies with targets and overlay resources. When a designated app is opened, Herodotus places a blocking overlay that hides the genuine interface and presents a counterfeit login screen, capturing credentials while keeping the real app out of the victim’s view.
Operators can remotely control infected phones via Accessibility features — tapping elements, swiping, navigating, and inputting text. To reduce detection by behavior- based fraud engines, the malware offers a “delayed text” mode that sends characters one-by-one with randomized pauses, making automated input resemble human typing. This humanizing step is a notable distinction from many comparable device-takeover trojans.
Beyond overlays and remote control, Herodotus includes standard banking-trojan tools: SMS interception for one-time codes, screen capture and Accessibility logging, and a command channel using MQTT across multiple subdomains. Active campaigns have been observed in Italy and Brazil, and screenshots circulating on underground forums show operator consoles with controls for the human-like input feature.
The following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
| Initial Access | T1660 | Phishing |
| Privilege Escalation | T1626 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1628.002 | Hide Artifacts: User Evasion |
| Defense Evasion | T1516 | Input Injection |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Credential Access | T1453 | Abuse Accessibility Features |
| Credential Access | T1517 | Access Notifications |
| Credential Access | T1414 | Clipboard Data |
| Credential Access | T1417 | Input Capture |
| Discovery | T1418 | Software Discovery |
| Collection | T1453 | Abuse Accessibility Features |
| Collection | T1517 | Access Notifications |
| Collection | T1414 | Clipboard Data |
| Collection | T1417 | Input Capture |
| Collection | T1430 | Location Tracking |
| Collection | T1636.004 | Protected User Data: SMS Messages |
| Collection | T1513 | Screen Capture |
| Command and Control | T1437 | Application Layer Protocol |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Herodotus may eventually expand beyond its current reach, evolving into a more widespread threat across regions and user groups. As its developers refine features and make it more accessible through Malware-as-a-Service platforms, this type of attack could surface in new markets where mobile banking and digital payments are growing rapidly. The combination of human-like interaction and remote-control capabilities may enable broader fraud operations, allowing attackers to exploit both individuals and digital ecosystems on a larger scale. Over time, campaigns inspired by Herodotus could influence how future mobile threats are developed, setting a new standard for sophistication in Android malware.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule Herodotus_Indicators
{
meta:
description = “Detects Herodotus malware Indicators” author = “CYFIRMA”
malware = “Herodotus”
strings:
// SHA256 File Hashes
$sha256_1 = “53ee40353e17d069b7b7783529edda968ad9ae25a0777f6a644b99551b412083”
condition:
any of ($sha256*)
}
STRATEGIC RECOMMENDATIONS:
MANAGEMENT RECOMMENDATIONS:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Advanced Threat Update: Bronze Butler (TICK) Exploits and Tactics
About the Threat Actor
The “TICK” threat group has carried out cyber espionage operations targeting organizations in South Korea and Japan for several years. Its primary focus is on companies that possess valuable intellectual property or sensitive data, particularly within the defense and high-tech sectors. The group is known for using its custom malware Daserf, along with a mix of both commodity and proprietary tools. Tick also exploits software vulnerabilities and employs social engineering tactics to achieve its objectives.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2025-61932 | Lanscope Endpoint Manager | 9.8 | – |
| CVE-2021-27065 | Microsoft Exchange Server | 7.8 | Link1, link2 |
| CVE-2021-26855 | Microsoft Exchange Server | 9.8 | Link1, link2, link3, link4 |
| CVE-2021-26858 | Microsoft Exchange Server | 7.8 | – |
| CVE-2021-26857 | Microsoft Exchange Server | 7.8 | – |
| CVE-2018-0802 | Microsoft Office | 7.8 | – |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1053.002 | Scheduled Task/Job: At |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1053.002 | Scheduled Task/Job: At |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1053.002 | Scheduled Task/Job: At |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1550.003 | Use Alternate Authentication Material: Pass the Ticket |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1027.001 | Obfuscated Files or Information: Binary Padding |
| Defense Evasion | T1036.002 | Masquerading: Right-to-Left Override |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1124 | System Time Discovery |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1518 | Software Discovery |
| Discovery | T1018 | Remote System Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Lateral Movement | T1550.003 | Use Alternate Authentication Material: Pass the Ticket |
| Collection | T1113 | Screen Capture |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1039 | Data from Network Shared |
| Collection | T1005 | Data from Local System |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1102.001 | Web Service: Dead Drop Resolver |
Latest Developments Observed
The threat actor is suspected of exploiting a zero-day vulnerability CVE-2025-61932 in Motex LANSCOPE Endpoint Manager, a popular endpoint management solution widely deployed across Japan and other Asian nations, and deploying Gokcpdoor malware. The motive appears to be the theft of confidential information.
ETLM Insights
TICK is an espionage-focused Advanced Persistent Threat (APT) group recognized for its methodical, stealth-driven operations and long-term persistence across campaigns. The group leverages a combination of custom malware frameworks and legitimate administrative tools to maintain covert access, lateral movement, and command within targeted networks.
Recent intelligence indicates that TICK has evolved its operational sophistication, incorporating zero-day exploitation, modular malware architectures, fileless execution, and encrypted communications to enhance both stealth and operational resilience.
TICK’s activity exemplifies a disciplined, intelligence-oriented approach, emphasizing sustained infiltration, covert reconnaissance, and discreet exfiltration of sensitive information—particularly from defense, technology, and critical infrastructure sectors.
The group’s continuous evolution underscores the importance of comprehensive endpoint visibility, identity and access security, and anomaly-based behavioral detection to identify and mitigate stealth-oriented, long-term intrusions characteristic of TICK’s campaigns.
IOCs
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule Tick_Indicators { meta:
description = “Detect CVEs, IPs, domains, and Mozi-related indicators” author = “CYFIRMA”
date = “2025-11-04”
strings:
// Example CVEs
$cve1 = “CVE-2025-61932”
$cve2 = “CVE-2021-27065”
$cve3 = “CVE-2021-26855”
$cve4 = “CVE-2021-26858”
$cve5 = “CVE-2021-26857”
$cve6 = “CVE-2018-0802”
// Example IPs
$ip1 = “208.91.197.27”
$ip2 = “208.73.211.165”
$ip3 = “87.248.203.253”
$ip4 = “127.0.0.1”
$ip5 = “91.195.240.94”
$ip6 = “64.233.167.99”
// Example domains
$domain1 = “iwdellebhavmei.com”
$domain2 = “ooxxsearch.com”
$domain3 = “babylon.network”
$domain4 = “icanhazip.com”
$domain5 = “thisislea.de”
// Example Mozi indicators (file names or strings)
$mozi1 = “win32 exe”
$mozi2 = “hrm3jvh9v.dll”
$mozi3 = “mtathreadattribute.exe”
condition:
any of ($cve*) or any of ($ip*) or any of ($domain*) or any of ($mozi*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Hacking campaign against Britain’s drinking water suppliers underway
Since early 2024, hackers have targeted Britain’s drinking water suppliers with at least five cyberattacks, as reported to the Drinking Water Inspectorate (DWI). These attacks, a record for any two-year span, did not compromise the safety of drinking water but impacted the organizations managing the supplies, underscoring British intelligence warnings of growing cyber threats to critical infrastructure. The DWI received 15 reports from suppliers between January 1, 2024, and October 20, 2025, under the Network and Information Systems (NIS) Regulations, which form part of the legal framework for securing drinking water systems.
ETLM Assessment:
In recent years, the UK has faced a surge in cyber-attacks, with Russia frequently suspected as the driving force behind many of them. While definitive attribution remains complex, the sophistication of these attacks and the backdrop of geopolitical tensions strongly indicate Russian involvement. These attacks have targeted diverse organizations, causing widespread disruption and financial losses. Russia has solidified its position as a capable, motivated, and irresponsible cyber threat actor. Russian operatives have almost certainly escalated their cyber campaigns against Ukraine and its allies, aligning these operations with their military objectives and broader geopolitical ambitions.
Strained by the demands of an all-out war against Ukraine, Russia has increasingly outsourced cyber operations to privateers and other non-state actors. These groups, often beyond direct state control, introduce a heightened unpredictability to their activities. This trend is likely to persist, as the Kremlin grants these actors greater latitude. From Moscow’s perspective, fostering global instability serves to divert attention from its aggression in Ukraine, further stretching the resources of those who oppose it.
Myanmar scam center bombed
Thousands are escaping Myanmar to Thailand after a joint operation between Myanmar’s military government, China, and Thailand shut down a major cybercrime hub at the KK Park site as part of a broader crackdown on cross-border online scams and illegal gambling that began this fall. Located near Myawaddy, a significant trading town on the Myanmar-Thailand border opposite Mae Sot, KK Park operates in an area loosely controlled by Myanmar’s military government, alongside a local Karen ethnic minority militia serving as a Border Guard Force. Witnesses in Thailand reported hearing explosions and seeing smoke from the site as some of its buildings were bombed during the raid.
The Thai army’s Naresuan Task Force confirmed that Myanmar’s military and its Border Guard Force allies demolished parts of KK Park with explosives, with debris damaging several homes across the border in Thailand. Most of those fleeing Myanmar are believed to have worked at KK Park, often under coercion. Thai authorities in Tak province have established temporary shelters for them, noting they hail from 28 countries, including Thailand, India, China, the Philippines, Vietnam, Ethiopia, and Kenya. These individuals are being processed to determine if they were victims of human trafficking, with plans for repatriation to their home countries.
ETLM Assessment:
Myanmar is infamous for hosting cyber scam operations that lure workers from abroad with false job promises, only to trap them in forced criminal activities. Despite the KK Park raid, Myanmar’s independent media, such as The Irrawaddy, report ongoing scam operations in the Myawaddy area. Cambodia also serves as a major hub for similar cybercrime activities, drawing global scrutiny earlier in October when the U.S. and U.K. imposed sanctions on a Cambodian cyber scam syndicate, with its alleged leader indicted by a U.S. federal court in New York.
KK Park’s sprawling compound and others nearby are run primarily by Chinese criminal gangs and guarded by local militia groups aligned to Myanmar’s military. Amid internet restrictions in Myanmar, scam centers heavily utilize Starlink connections. Last week, SpaceX disabled over 2,500 Starlink devices suspected of supporting cybercrime groups. Saw Taw Nee suggested the actual number could be higher, noting the network’s widespread use in the region. In Myanmar, Laos, and Cambodia, criminal networks operate large-scale cyber-fraud and scam centers, powered by sophisticated transnational syndicates. These groups collaborate with interconnected networks of money launderers, human traffickers, data brokers, and an expanding array of specialized service providers and facilitators.
RansomHouse Ransomware Impacts ASKUL Corporation
Summary:
CYFIRMA observed in an underground forum that a company from Japan, ASKUL Corporation (https[:]//www[.]askul[.]co[.]jp/), was compromised by RansomHouse Ransomware. ASKUL Corporation is a prominent Japanese e- commerce company catering to both business-to-business (B2B) and business- to-consumer (B2C) markets. The company offers a wide range of products, including office supplies, daily essentials, medical items, and logistics services. The compromised data contains sensitive and confidential information pertaining to the organization, with the total volume of leaked data estimated to be approximately 1.1 terabytes.

Relevancy & Insights:
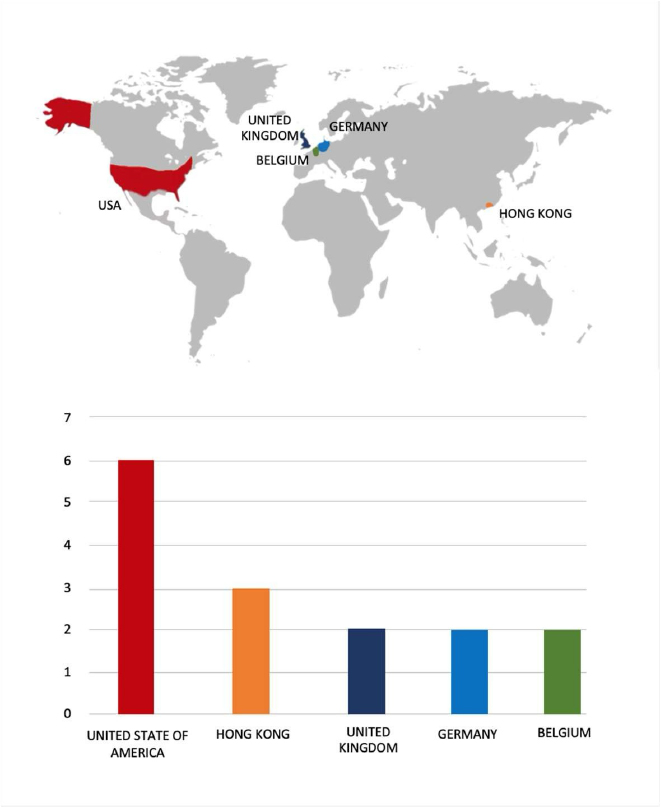
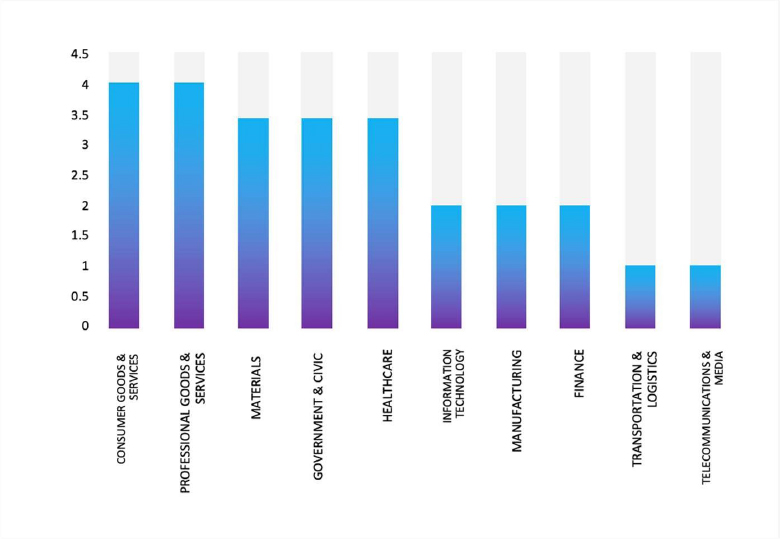
ETLM Assessment:
According to CYFIRMA’s assessment, RansomHouse ransomware predominantly targets large enterprises and high-value organizations through phishing and spear phishing campaigns. The group also employs third-party frameworks such as Vatet Loader, Metasploit, and Cobalt Strike to gain initial access and perform lateral movements within victim networks. RansomHouse typically skips data encryption, focusing instead on exfiltrating sensitive data to extort victims by threatening to publicly release the stolen information. This approach allows the group to maintain stealth and prolong their presence in targeted environments.
Qilin Ransomware Impacts Super Value Co., Ltd.
Summary
CYFIRMA observed in an underground forum that a company from Japan, Super Value Co., Ltd (https[:]//www[.]supervalue[.]jp/), was compromised by Qilin Ransomware. Super Value Co., Ltd is a Japan-based retail company. The company offers a wide range of products, including fresh foods, groceries, household goods, leisure and DIY supplies, car goods, pet products, home appliances, stationery, toys, and pharmaceuticals. The compromised data comprises sensitive financial information and other confidential organizational data, with the total size of the leaked data estimated at approximately 350 gigabytes.
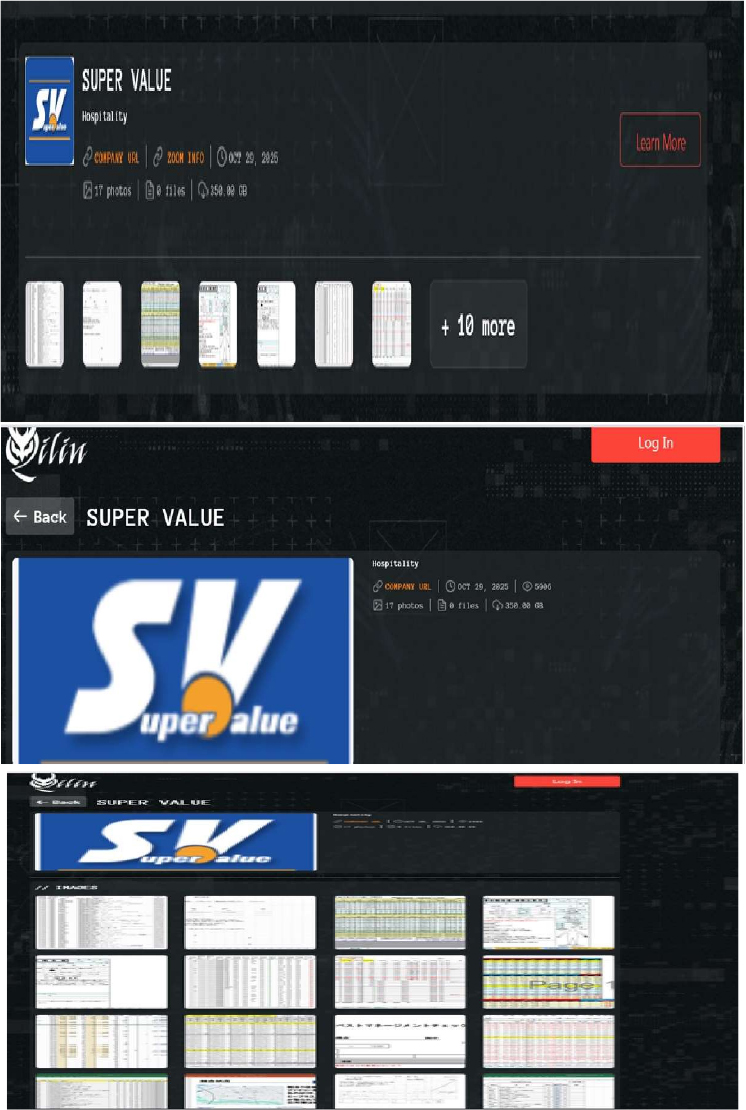
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in SailPoint IdentityIQ
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user- supplied data. A remote attacker can trick the victim to follow a specially crafted link and execute arbitrary HTML and script code in the user’s browser in the context of a vulnerable website.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to steal potentially sensitive information, change the appearance of the web page, perform phishing and drive-by-download attacks.
Affected Products:
https[:]//www[.]sailpoint[.]com/security-advisories/sailpoint- identityiq-incorrect-content-type-cross-site-scripting-vulnerability-cve-2025-10280
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
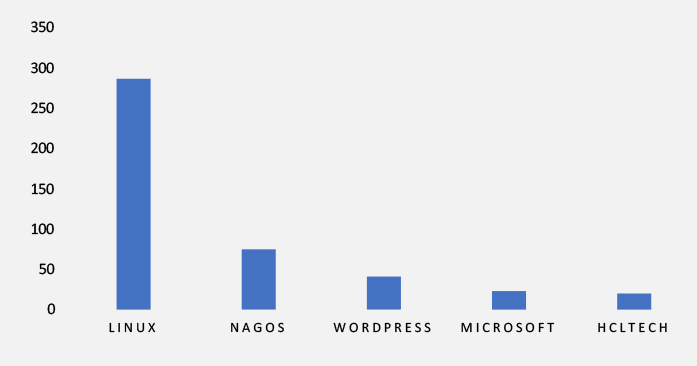
ETLM Assessment
Vulnerability in SailPoint IdentityIQ can pose significant threats to user privacy and organizational security. This can impact various industries globally, including finance, healthcare, government, and enterprise IT. Ensuring the security of SailPoint IdentityIQ is crucial for maintaining the integrity and protection of identity governance and access management systems worldwide.
Black Shrantac Ransomware attacked and published the data of Cypark Resources Berhad
Summary:
Recently, Black Shrantac Ransomware was observed attacking and publishing the data of Cypark Resources Berhad (www[.]cypark[.]com) on its dark web website. Cypark Resources Berhad is a leading Malaysian public listed company, specializing in integrated renewable energy, construction and engineering, green technology, environmental services, and waste management, including waste-to-energy (WTE) solutions. The data leak resulting from the ransomware attack on Cypark Resources Berhad includes financial information, such as invoices, insurance documents, banking records, asset details, and payroll data. It also contains human resources information like employee lists, email addresses, and physical addresses, as well as company data related to environmental engineering, landscaping, and infrastructure projects. The total volume of the compromised data is approximately 450 gigabytes.
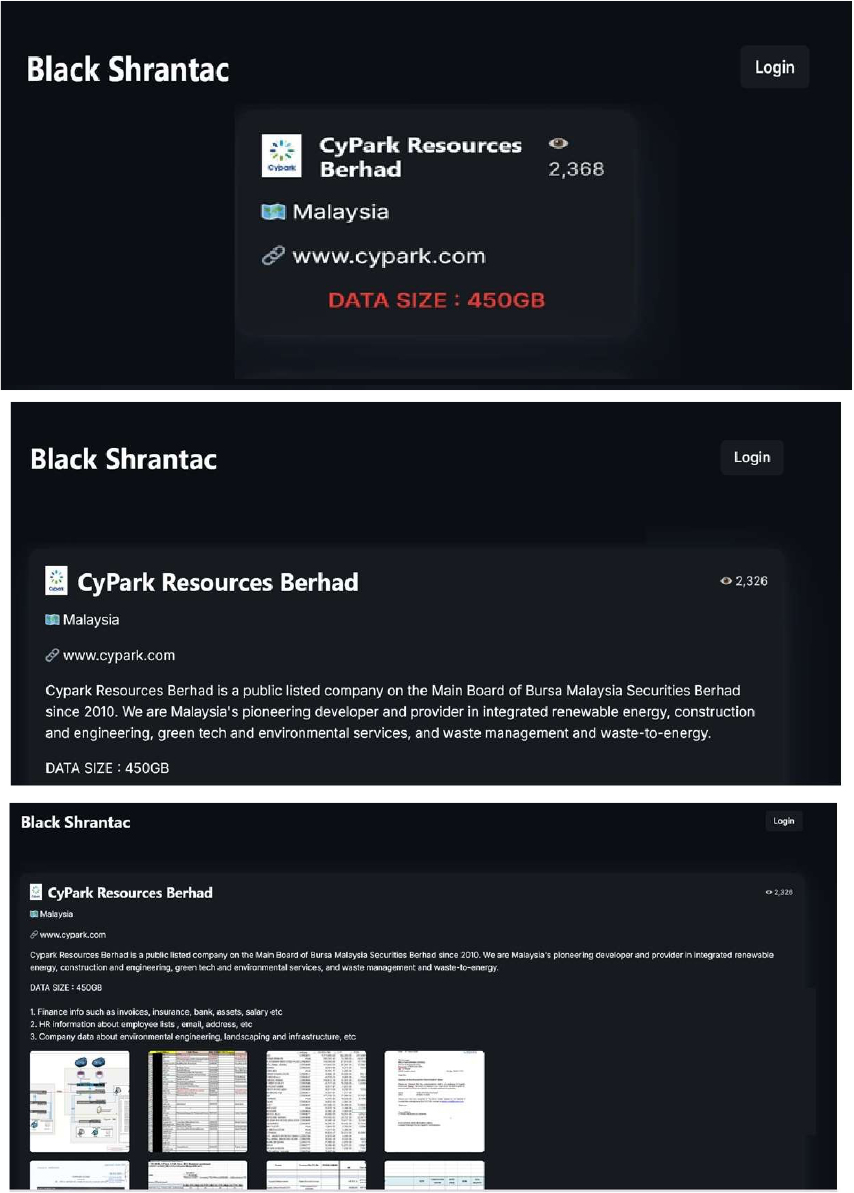
Relevancy & Insights:
Black Shrantac is a recently identified ransomware group first observed in September 2025, operating primarily as a data broker and extortion outfit. The group targets organizations, exfiltrating sensitive data and leveraging public pressure—often via a dedicated. onion (Tor) site—to coerce ransom payments.
ETLM Assessment:
According to CYFIRMA’s assessment, Black Shrantac Ransomware exemplifies the latest trend of fast-forming, adaptable data extortion groups that maintain an aggressive web presence to pressure victims using both threat and demonstration of data exposure.
Thailand’s Department of Agricultural Extension (DOAE) Data Advertised on a Leak Site
Summary: The CYFIRMA Research team observed that a threat actor, “Kazu,” claims to have breached Thailand’s Department of Agricultural Extension (DOAE). The DOAE operates under the Ministry of Agriculture and Cooperatives, providing farmers and the public with resources on crop cultivation, pest management, and agricultural technologies.
According to the actor, a database containing 5,426,069 records is being offered for sale. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

Yas Takaful Dubai Insurance Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor claims to have breached Yas Takaful Dubai Insurance, an insurance provider based in the United Arab Emirates. The actor is advertising a database containing a significant amount of client and corporate information.
According to the actor, the compromised database contains over 450,000 lines of client information. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
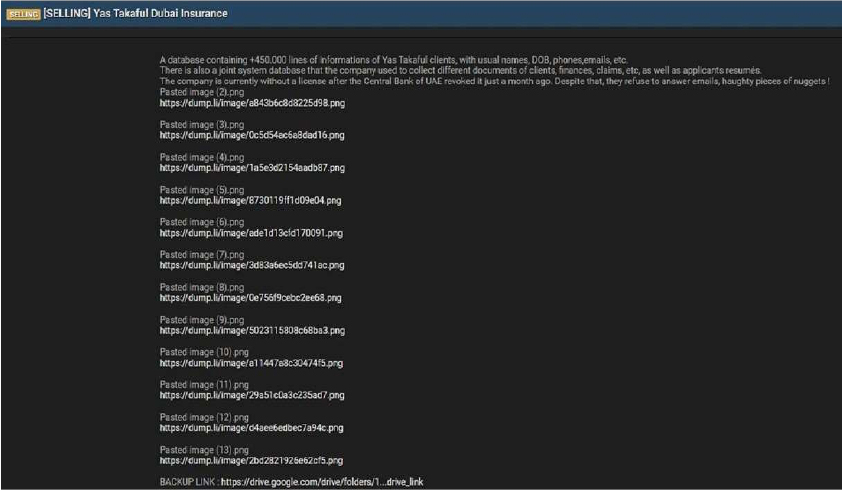
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “Kazu” has recently emerged as a notably active group engaged in data leak activities. Credible sources have tied the group to multiple security breaches involving unauthorized system access and attempts to sell stolen data on dark web marketplaces. The group’s ongoing operations illustrate the persistent and escalating cyber threats stemming from underground forums. These incidents reinforce the critical need for organizations to bolster cybersecurity through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor claims to have breached Gateworks Corporation, a US-based design and manufacturing company. Gateworks specializes in industrial Single Board Computers (SBCs) and wireless solutions for embedded systems. The breach, which allegedly occurred in October 2025, is now being offered for sale on a dark web forum.
According to the actor, the compromised data, which is being sold for $500, includes sensitive corporate documents. The data pack reportedly contains proprietary information and schematics from several of Gateworks’ partners and suppliers.
The allegedly compromised partner documents include:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
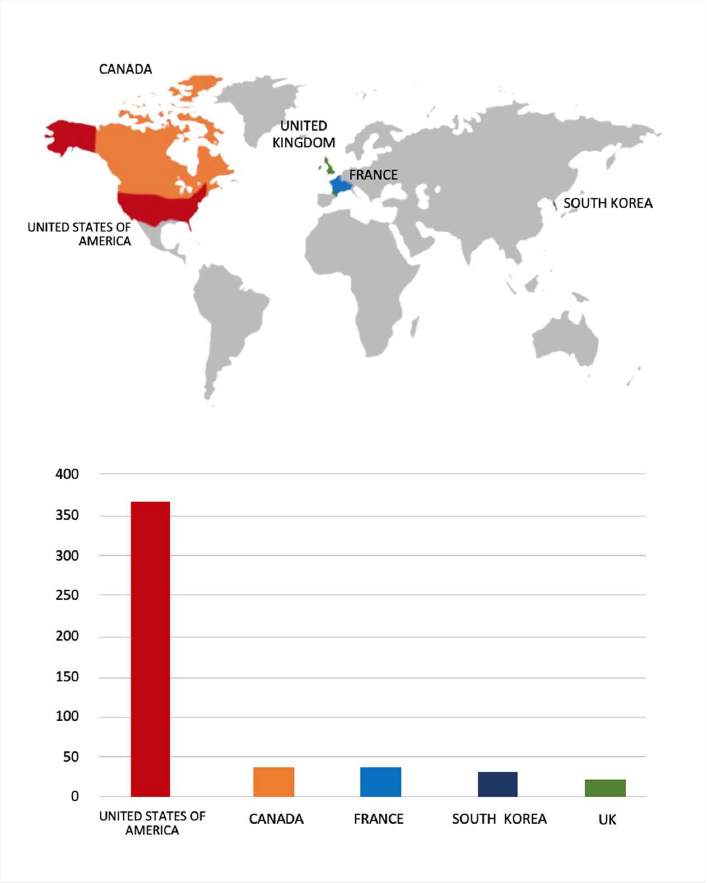
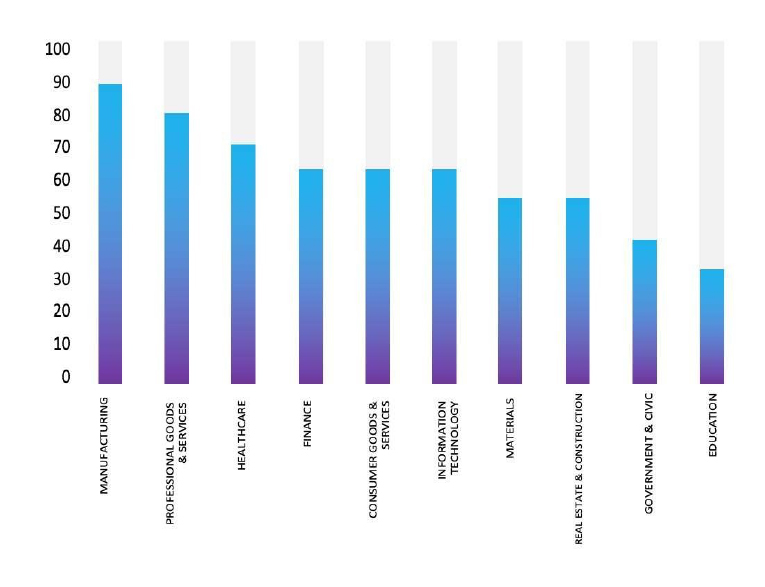
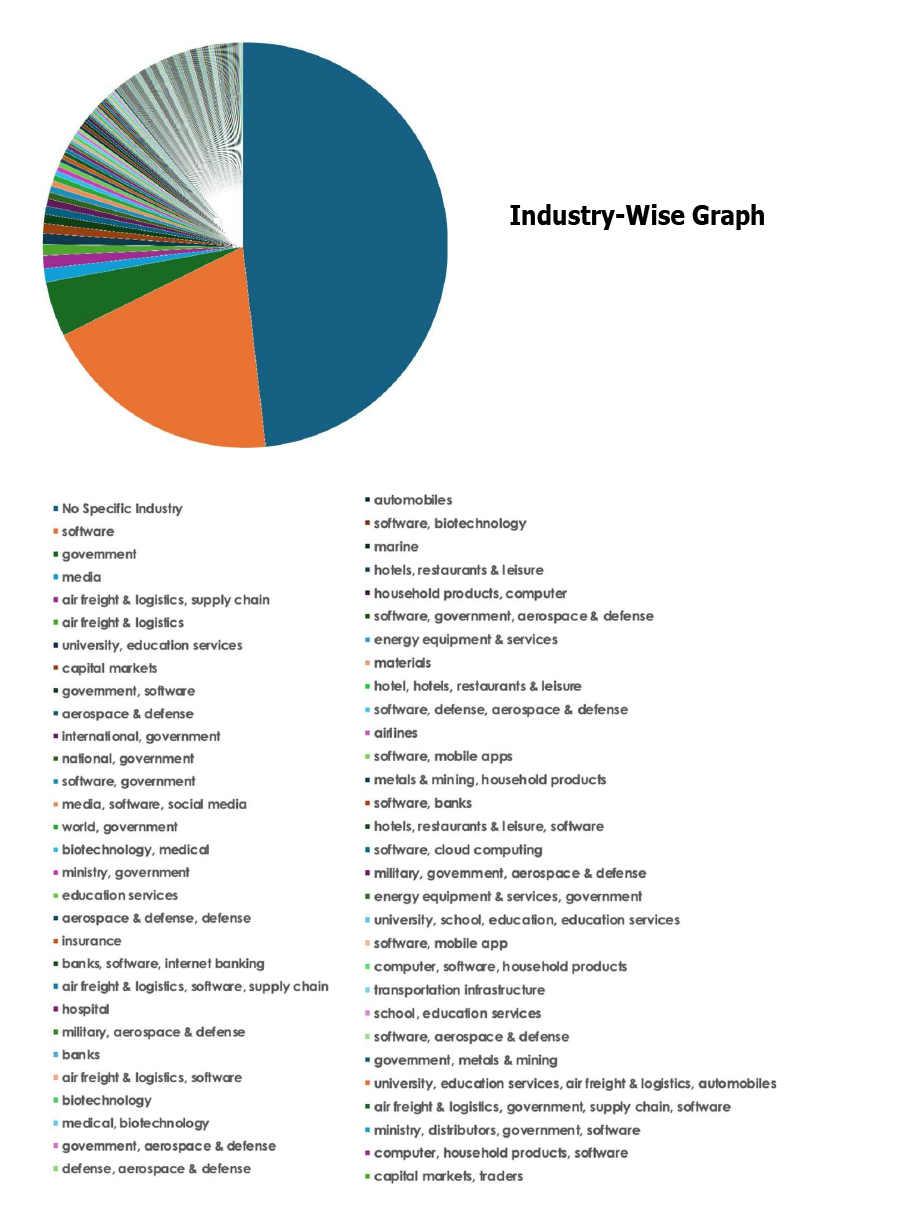
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
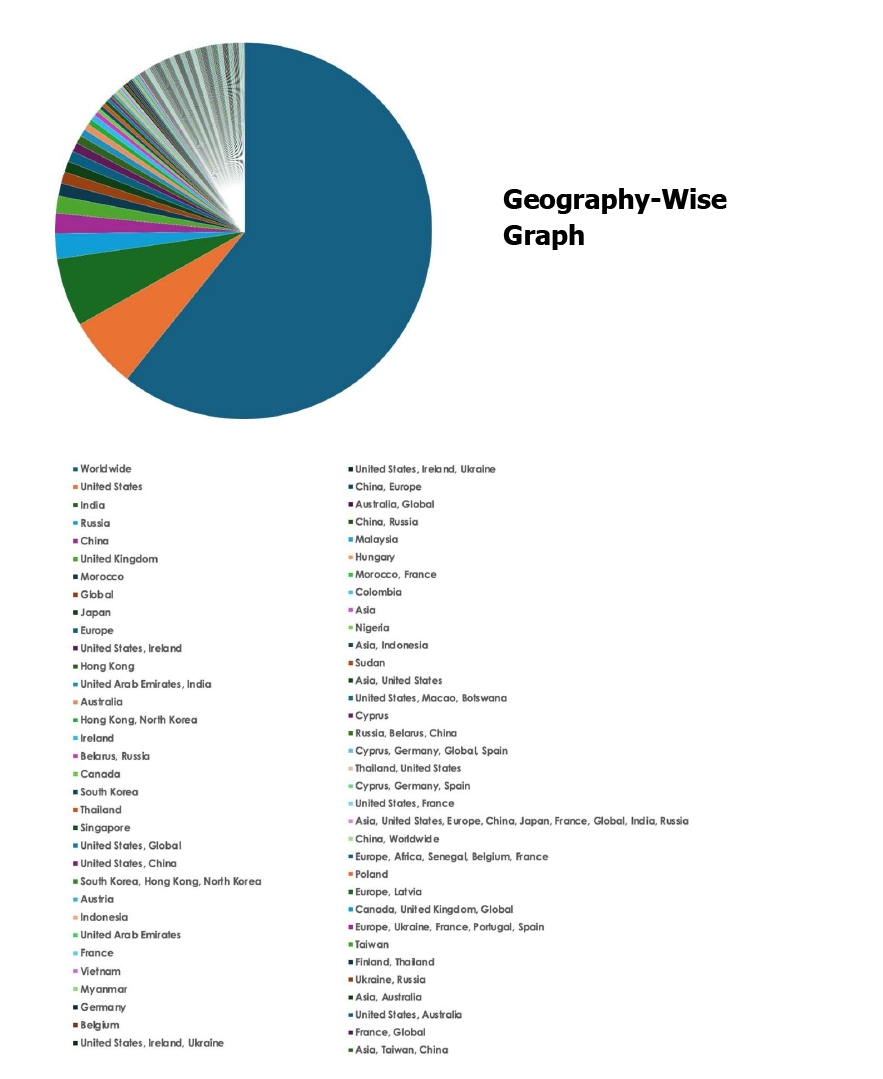

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.