



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Nett Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Nett Ransomware
By the end of May 2024, researchers uncovered a new malicious program named Nett, a variant within the MedusaLocker ransomware family. This ransomware, once activated, encrypts files and appends a “.nett” extension to their names. Upon completing the encryption process, it generates a ransom note in an HTML file titled “Recovery_Instructions.html.” Analysis of this message indicates that Nett specifically targets businesses, rather than individual home users.

Screenshot of files encrypted by ransomware (Source: Surface Web)
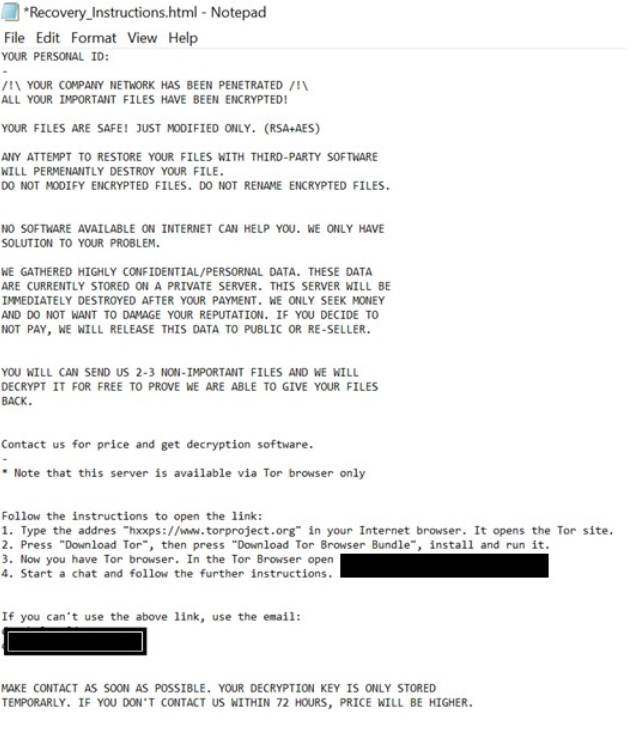
The appearance of Nett ransomware’s ransom note “Recovery_Instructions.html” (Source: Surface Web)
Nett’s ransom note informs the victim that their company’s network has been compromised, and files have been encrypted using RSA and AES cryptographic algorithms. The message cautions against renaming or modifying the encrypted files or using third-party recovery software, as these actions could result in permanent data loss.
Additionally, the note reveals that sensitive data has been stolen from the network. The attackers demand payment, threatening to increase the ransom amount if there is no contact within 72 hours. Threat actors stated that the stolen data will be leaked or sold if the victim refuses to pay.
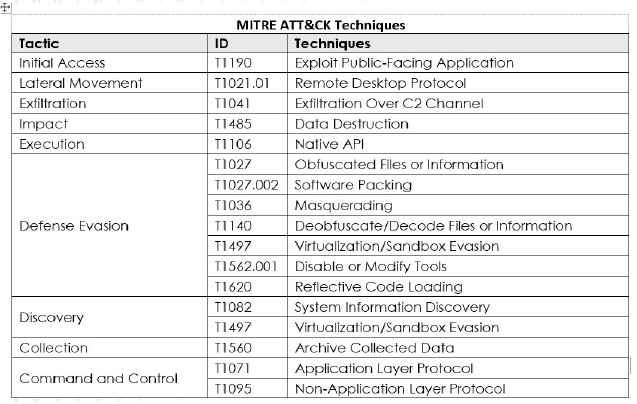
Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/ Sub-Techniques |
| 1 | TA0001:Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1053: Scheduled Task/Job |
| 3 | TA0003: Persistence | T1053:Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading |
||
| 4 |
TA0004:Privilege Escalation |
T1053:Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution:Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side – Loading | ||
| 5 | TA0005:Defense Evasion | T1027.002: Obfuscated Files or Information: Software Packing |
| T1036:Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1497:Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side – Loading | ||
| 6 | TA0006: Credential Access | T1056: Input Capture |
| 7 | TA0007: Discovery | T1012: Query Registry |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497:Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 8 | TA0008:Lateral Movement | T1080: Taint Shared Content |
| T1091: Replication Through Removable Media | ||
| 9 | TA0009: Collection | T1056: Input Capture |
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090:Proxy | ||
| T1573: Encrypted Channel | ||
| 11 | TA0040:Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis, based on available data, shows that MedusaLocker ransomware has been actively targeting a wide range of sectors—including healthcare, finance, and IT services—since 2019. Projections suggest that Nett, a sophisticated variant of MedusaLocker, will employ advanced evasion techniques to broaden its impact on individuals and businesses. This new variant is likely to continue targeting major industries worldwide. Therefore, maintaining vigilance and implementing robust cybersecurity measures are crucial to mitigate these threats effectively.
Sigma Rule
title: MedusaLocker threatname: MedusaLocker behaviorgroup: 15
classification: 0 mitreattack:
logsource:
product: windows category: registry_event
detection: selection:
EventID: 13 TargetObject:
– ‘*\Software\MDSLK*Self*’ condition: selection
level: critical
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Credentials Stealing & Sensitive Data Harvesting
Target Technology: Android OS
Target Industries: Banks
Target Geographies: US, UK, Germany, Spain, Finland, South Korea, and Singapore
Active Malware of the Week
This week “Anatsa” is trending.
Anatsa
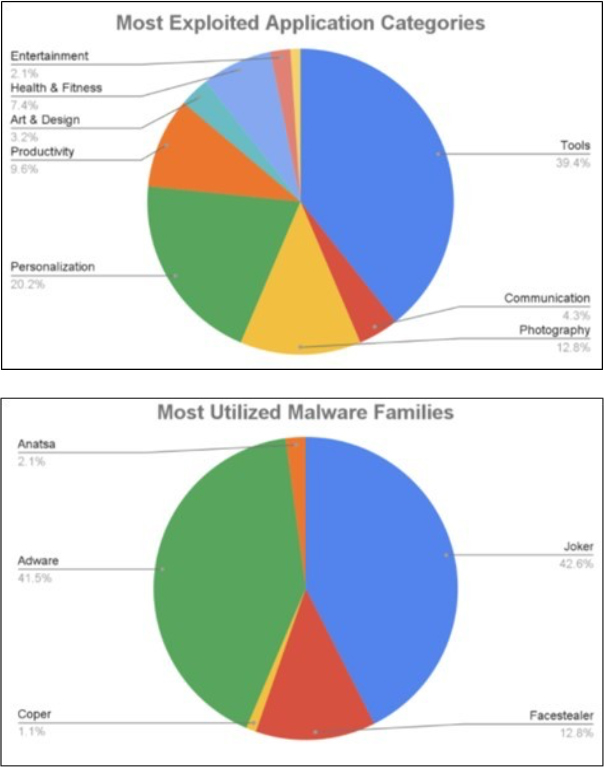
Researchers identified the Anatsa malware (also known as TeaBot) as a known Android banking malware. Initially targeting financial institutions in Europe, it has recently been focusing on banking apps in the US and UK. Current observations indicate that threat actors have expanded their targets to include banking applications in Germany, Spain, Finland, South Korea, and Singapore. This advanced malware uses dropper applications that seem harmless to users, tricking them into unknowingly installing the malicious payload. After installation, Anatsa stealthily extracts sensitive banking credentials and financial information from various global financial apps by employing overlay and accessibility methods to discreetly intercept and gather information.
Distribution Method
Researchers recently discovered two malicious payloads related to Anatsa malware distributed via the Google Play store. These payloads masqueraded as PDF reader and QR code reader apps to attract many users, amassing over 70,000 installations by the time of analysis. The high installation numbers helped deceive victims into believing the apps were legitimate.
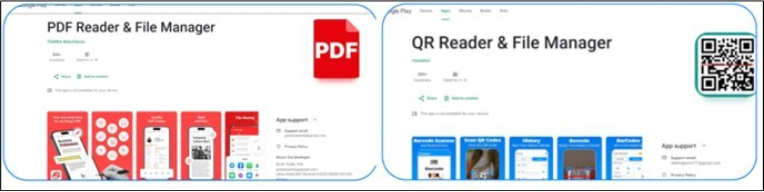
Fig: Malicious installers disguised as a legitimate PDF reader and QR code reader in the Google Play store.
Technical Analysis
Anatsa employs remote payloads fetched from C2 servers for additional malicious operations. The dropper app displays encoded links to these servers, from which the subsequent stage payload is downloaded. Alongside downloading the payload, the malware fetches a configuration file from the remote server to execute the next-stage payload.
The DEX file is then downloaded and loaded by the parent fake QR code application. Using reflection, the application invokes code from the loaded DEX file, with the necessary configuration obtained from the control server. After the next stage, the payload is downloaded, and Anatsa conducts checks for the device environment and type, likely to identify analysis environments and malware sandboxes.
Upon successful verification, it proceeds to download the third stage and final payload from the remote server. In this campaign, Anatsa malware injected uncompressed raw manifest data into the APK, intentionally corrupting compression parameters in the manifest file to impede analysis. To statically analyze the payload, the ZIP file headers must be fixed alongside the compressed data.
After loading the APK, the malware requests various permissions, including SMS and accessibility options, commonly associated with mobile banking trojans. The final DEX payload is concealed within asset files. During runtime, the payload decrypts the DEX file using a static key embedded within the code.
Upon execution, Anatsa decodes all encoded strings, including those for C2 communication. It establishes contact with the C2 server to register the infected device and retrieve a list of targeted applications for code injections. To steal data from financial applications, Anatsa downloads a target list of financial application package names and scans the victim’s device to check for installed targets. When it identifies a targeted application, Anatsa informs the C2 server, which responds with a fake login page for the banking application. This fake login page is loaded within a JavaScript Interface (JSI) enabled webview to deceive users into entering their banking credentials. Once the credentials are entered, the data is sent back to the C2 server.
INSIGHTS
ETLM ASSESSMENT
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
LilacSquid: Emerging APT Targets IT, Energy, and Pharma Sectors Across the Globe
Summary:
Cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various sectors in the United States (U.S.), Europe, and Asia as part of a data theft campaign active since at least 2021. LilacSquid’s targets include information technology organizations developing software for the research and industrial sectors in the U.S., the energy sector in Europe, and the pharmaceutical sector in Asia, indicating a broad victimology footprint. The attack chains typically exploit publicly known vulnerabilities in internet-facing application servers or use compromised remote desktop protocol (RDP) credentials to deliver a mix of open- source tools and custom malware.
A distinctive feature of the campaign is the use of MeshAgent, an open-source remote management tool, which serves as a conduit to deliver a bespoke version of QuasarRAT codenamed PurpleInk. When compromising RDP credentials, the threat actors either deploy MeshAgent or a .NET-based loader dubbed InkLoader to drop PurpleInk. Successful RDP logins lead to the download of InkLoader and PurpleInk, with these artifacts copied into desired directories on disk and InkLoader registered as a service to deploy PurpleInk.
Since 2021, LilacSquid has actively developed PurpleInk, a highly obfuscated and adaptable tool. PurpleInk can execute new applications, perform file operations, collect system information, enumerate directories and processes, initiate a remote shell, and connect to specific remote addresses provided by a command-and-control (C2) server. However, recent versions of PurpleInk discovered in 2023 and 2024 have been streamlined, focusing mainly on creating a reverse shell and communicating with a proxy for data transfer. This reduction in features is likely an effort to evade detection. Researchers identified another custom tool called InkBox, previously used by LilacSquid to deploy PurpleInk before switching to InkLoader. The use of MeshAgent in post-compromise playbooks is noteworthy, as this tactic has also been adopted by Andariel, a sub-cluster within the infamous Lazarus Group, in attacks targeting South Korean companies. Additionally, LilacSquid employs tunneling tools like Secure Socket Funneling (SSF) to maintain secondary access, creating communication channels to its infrastructure.
The motive behind these attacks is to maintain long-term access to victim organizations, enabling the ongoing theft of valuable data and potentially facilitating broader supply chain compromises. This strategy mirrors tactics used by other advanced persistent threat groups, highlighting LilacSquid’s capability and intent to operate as a significant threat in the cybersecurity landscape.
Relevancy & Insights:
Believed to be UAT-4820, “LilacSquid” is an advanced persistent threat (APT) actor whose activities reveal a persistent and evolving threat. Various tactics, techniques, tools, and procedures (TTPs) employed in this campaign show significant similarities to those used by North Korean Advanced Persistent Threat (APT) groups, including Andariel and its parent organization, Lazarus.
ETLM Assessment:
LilacSquid, believed to be UAT-4820, is an advanced persistent threat (APT) actor targeting a diverse range of industries across various regions, including information technology organizations developing software for the research and industrial sectors in the U.S., energy sectors in Europe, and pharmaceutical sectors in Asia, indicating a broad victimology footprint. The group typically exploits publicly known vulnerabilities in internet-facing application servers or uses compromised remote desktop protocol (RDP) credentials to infiltrate targets. Their toolkit includes open-source tools like MeshAgent and customized malware such as PurpleInk, along with custom loaders InkLoader and InkBox, and tunneling tools like Secure Socket Funneling (SSF). LilacSquid’s tactics bear similarities to those of North Korean APT groups, such as Andariel, which uses MeshAgent for maintaining access, and Lazarus, which employs SOCKs proxy and tunneling tools alongside custom malware. This overlap in tactics and infrastructure illustrates the serious concern that threat actors are now adopting and integrating techniques from other sophisticated groups to enhance their attacks.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russia targets European defense and transportation organizations
Researchers have recently published findings on an espionage campaign attributed to Russia’s military intelligence GRU that deployed a strain of malware called Headlace against networks across Europe between April and December 2023. The threat actor known as “BlueDelta” used credential-harvesting pages that targeted the Ukrainian Ministry of Defence, Ukrainian weapons import and export companies, European railway infrastructure enterprises, and a think tank based in Azerbaijan.
ETLM Assessment:
Russian attempts to destabilize the Ukrainian defense industry have been well documented but interference in their Western counterparts and in European transport networks has been less discussed, even though CYFIRMA analysts warned of this danger in this report last year. The Czech National Cyber and Information Security Agency (NÚKIB) has also warned of growing threats of attacks on transport targets in its report last year. The agency has been one of the strictest digital security watchdogs in Europe and was the first to issue a hawkish warning against the use of components from Chinese companies Huawei and ZTE in 5G mobile networks under construction. Russia is using the intelligence it gains in these attacks in acts of its political war against the West as well its kinetic war against Ukraine, but also as tactical means of delaying transports of Ukrainian grain to the world market as well as movements of Western equipment towards Ukraine both in civilian and military capacity. The incident shows the growing role of cyber in conflict even or rather especially between countries that are not formally at war and demonstrates the future of political relations, in which cyber will be a major means of the statecraft toolkit, affecting governments and businesses alike.
New North Korean threat actor deploying old schemes
Researchers have published a report on a new North Korean threat actor tracked as “Moonstone Sleet” that’s conducting financially motivated attacks alongside cyber espionage. The threat actor has been observed setting up fake companies and job opportunities to engage with potential targets, employing trojanized versions of legitimate tools, creating a malicious game, and delivering a new custom ransomware. The threat actor is targeting individuals and organizations in the software and information technology, education, and defense industrial base sectors.
ETLM Assessment:
North Korean cyber operations have increased in sophistication over the past two years, and our researchers noted last year in a research report that Pyongyang’s threat actors seem particularly interested in stealing information related to maritime and missile technology research, given the emphasis the Kim regime puts onto developing a full nuclear triad. The interest in software is most likely related to Pyongyang’s interest in supply chain attacks. The heavily sanctioned regime in North Korea is hungry for the off-limits technologies it cannot obtain on the open market and thus uses cyber means to obtain them.
The 8Base Ransomware impacts the Matusima
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]matusima[.]com), was compromised by the 8Base Ransomware. Matusima Corporation is engaged in the sale and maintenance of agricultural machinery/general- purpose machinery, distribution of agricultural machinery, sale and maintenance of construction machinery, piping/plumbing equipment, mechanical equipment, heating and cooling, water supply and sewerage, air conditioning, septic tank, water supply and sewerage, construction of mechanical equipment, design, and construction, rental of construction equipment, sale and maintenance of cars, sale, and construction of solar energy production systems/, and batteries. The compromised data contains Invoices, Receipts, Accounting documents, Personal data, Certificates, Employment contracts, A huge amount of confidential information, Confidentiality agreements, Personal files, and Others.
The following screenshot was observed published on the dark web:

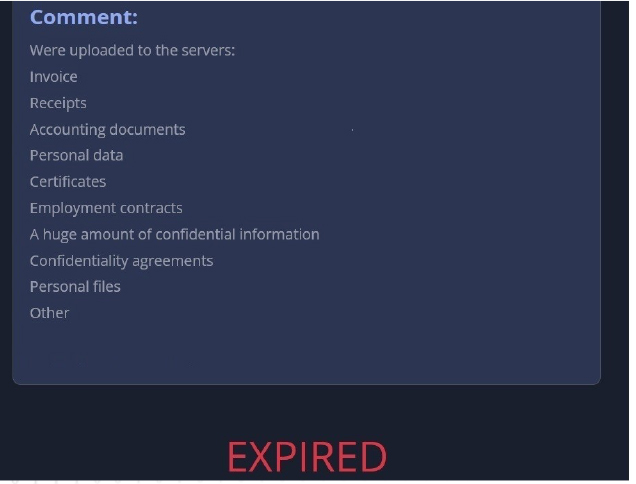
Source: Dark Web
Relevancy & Insights:
The LockBit3.0 Ransomware impacts the Kulicke & Soffa(kns)
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; (www[.]kns[.]com), was compromised by the LockBit3.0 Ransomware. Kulicke and Soffa Industries, Inc. (NASDAQ: KLIC) specializes in developing cutting-edge semiconductor and electronics assembly solutions enabling a smarter and more sustainable future. Their ever-growing range of products and services supports growth and facilitates technology transitions across large-scale markets, such as advanced display, automotive, communications, computer, consumer, data storage, energy storage, and industrial. The data that has been compromised has not yet surfaced on the leak site, suggesting ongoing negotiations between the affected party and the ransomware group. The compromised data encompasses sensitive and confidential information pertinent to the organization.
The following screenshot was observed published on the dark web:
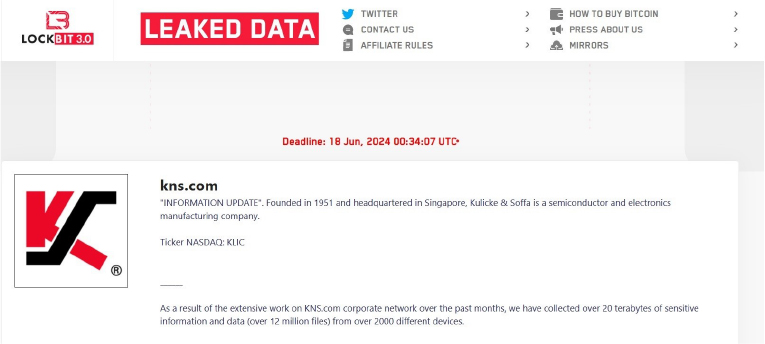
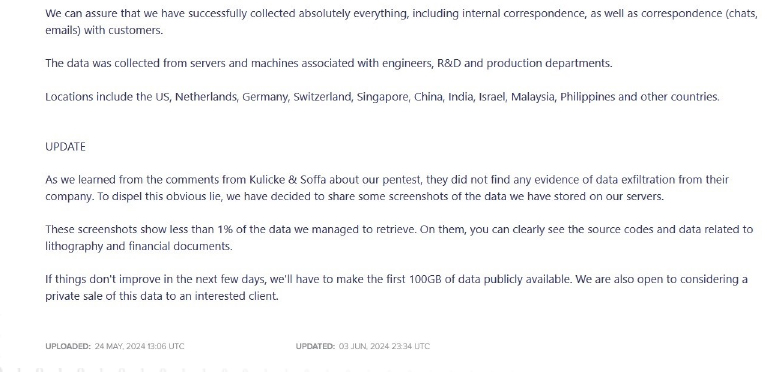
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
CYFIRMA’s assessment underscores the persistent and widespread threat posed by LockBit 3.0 ransomware to companies worldwide. Observations reveal an escalating pattern, wherein LockBit 3.0 exploits vulnerabilities in diverse products to infiltrate systems, facilitating lateral movement within organizational networks. Based on available information, CYFIRMA indicates that LockBit 3.0 will continue targeting various industries globally, with a significant emphasis on the United States, Europe, and Asian regions. A recent breach targeting Kulicke & Soffa (K&S), a leading manufacturing firm based in Singapore, serves as a potential indicator of LockBit 3.0’s inclination towards targeting organizations across Southeast Asia. This attack highlights the ransomware group’s focus on high-value targets and critical infrastructure, leveraging sophisticated techniques to evade detection and maximize impact.
Vulnerability in CasGate
Summary:
The vulnerability allows a remote attacker to bypass authorization checks.
Relevancy & Insights:
The vulnerability exists due to improper authorization in multiple API endpoints.
Impact:
A remote attacker can bypass authorization on the target system.
Affected Products:
https[:]//github[.]com/casgate/casgate/security/advisories/GHSA-mj5q- rc67-h56c
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
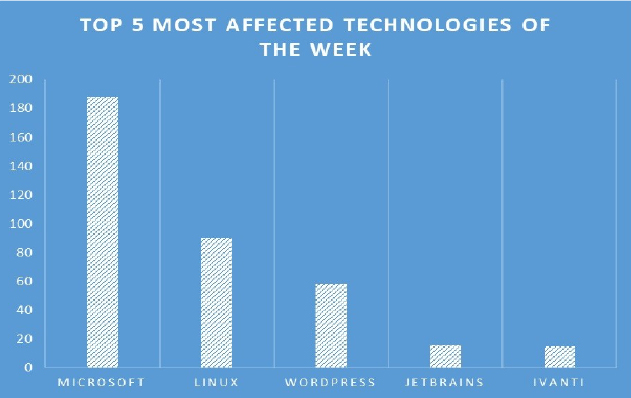
ETLM Assessment:
Vulnerability in CasGate a UI-first centralized authentication/Single-Sign-On (SSO) platform based on OAuth 2.0/OIDC can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of this SSO platform is crucial for maintaining the integrity and protection of users’ authentication and authorization data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding authentication activities across different geographic regions and sectors.
RansomHouse Ransomware attacked and Published data of ABS-CBN Broadcasting
Summary:
Recently we observed that RansomHouse Ransomware attacked and Published data of ABS-CBN Broadcasting on its darkweb website. ABS-CBN Broadcasting (www[.]abs-cbn[.]com) is considered one of the country’s leading media and entertainment companies, with service offerings across different platforms of media, servicing a wide array of customer segments. The company is driven to pioneer, innovate, and adapt as it continues to provide information, news, and entertainment that connects Filipinos with one another and with their community – wherever they may be. The data leak, following the ransomware attack, encompasses a broad spectrum of sensitive and confidential information pertinent to the organization. The total volume of compromised data is approximately 500 GB.
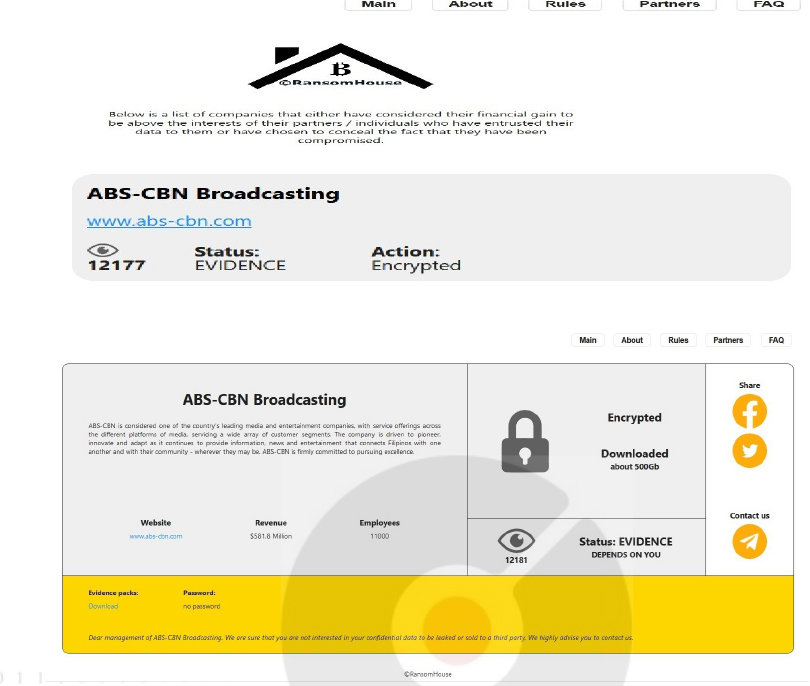
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
RansomHouse ransomware is known to target large enterprises and high-value targets. RansomHouse ransomware targets its victims through phishing and spear phishing emails. They are also known to use third-party frameworks (e.g., Vatet Loader, Metasploit, Cobalt Strike). Based on the available information, CYFIRMA’s assessment indicates that RansomHouse ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent breach targeting ABS-CBN Broadcasting, a leading Media & Internet firm based in the Philippines, serves as a potential indicator of RansomHouse ransomware’s inclination towards targeting organizations across Southeast Asia.
Dkhoon Emirates Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Dkhoon Emirates, {www[.]dkhoonemirates[.]com} in an underground forum. In a recent cyber incident, a threat actor claimed to have obtained a substantial database from Dkhoon Emirates, a prominent online retailer. The data, purportedly consisting of 1,187,492 rows, is said to include extensive customer information and transaction details. This alleged breach has been made public with a demand for $4800 USD in cryptocurrency (XMR or BTC) for a one-time sale. The seller has threatened to publish the data if no buyer comes forward.
The data, which is claimed to be updated as of June 2, 2024, is reportedly stored in a file named “Dkhoonemirates.csv,” with a size of 514MB. According to the seller, the dataset includes a comprehensive range of customer and order details, such as:
Customer Information: Names, emails, mobile numbers, and addresses. Order Details: Order status, payment methods, shipping methods, and tracking IDs. Financial Information: Payment statuses, subtotal amounts, VAT, shipping costs, cash on delivery amounts, discounts, and total amounts.
Additional Data: Google Maps locations, coupon codes, product names, SKUs, quantities, order product costs, unit prices, transaction references, and timestamps.
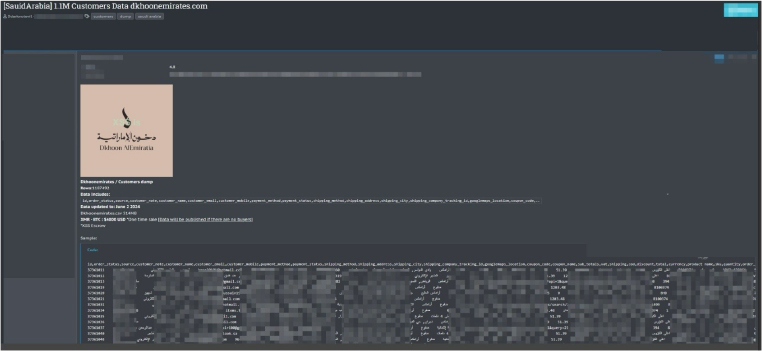
Source: Underground Forums
Chungwa Telecom data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Chungwa Telecom, {www[.]cht[.]com[.]tw } in an underground forum. A threat actor known as 303 claims to be selling unauthorized shell access to Chungwa Telecom, the largest telecom company in Taiwan. According to the threat actor, they have access to 910 GB of data from the company’s internal systems. Chungwa Telecom, with a revenue of $7.2 billion, is a major player in Taiwan’s telecommunications industry. The threat actor is offering this unauthorized access for $4,000, though they are open to negotiation. Payments are accepted in Bitcoin (BTC) and Monero (XMR).
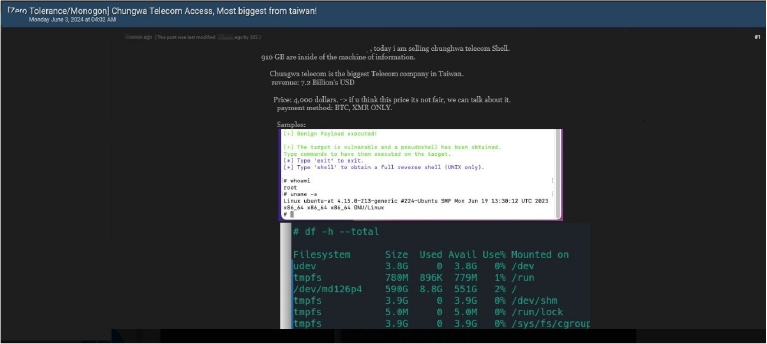
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Based on CYFIRMA’s assessment, the financially motivated threat actor known as ‘Threat Actor 303’ poses a significant risk to organizations, as they are known to target any institution and profit from selling sensitive data on the dark web or underground forums. The organizations targeted by Ddarknotevil typically have inadequate security measures in place, rendering them vulnerable to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
8. Other Observations
CYFIRMA Research team observed a potential data leak related to Heineken. Recently, threat actor “888” has purportedly leaked data associated with the renowned brewing company, Heineken. The company, with a substantial revenue of €36.4 billion, allegedly fell victim to a breach in June 2024. According to the threat actor’s claims, the leaked database comprises 8,174 employee records sourced from multiple countries. The data purportedly includes employee IDs, user IDs, full names, email addresses, company details, and respective roles within the organization.
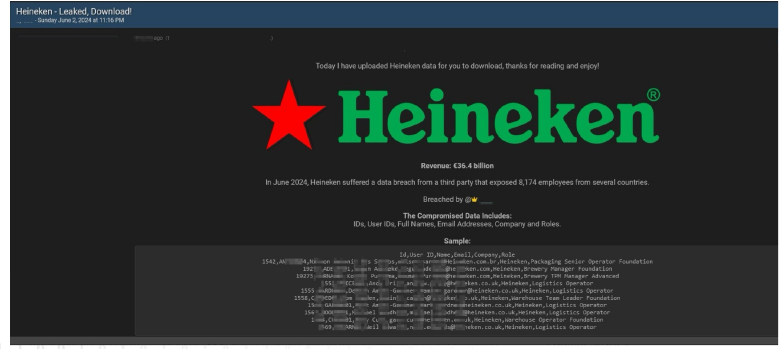
Source: Underground forums
ETLM Assessment:
Threat actor 888 group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
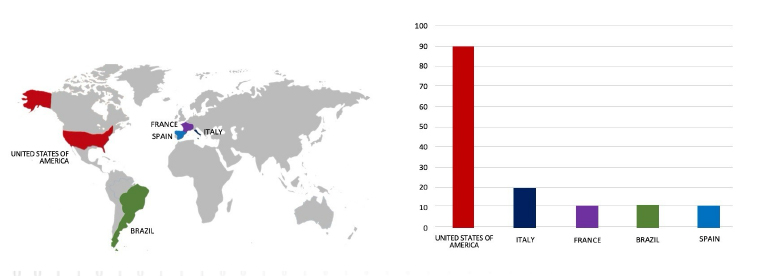
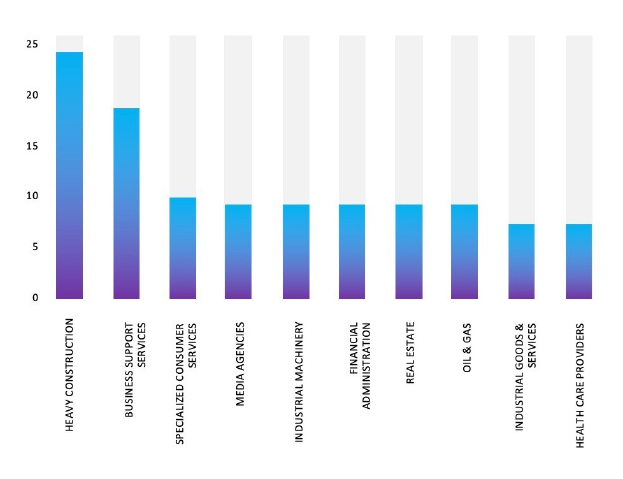
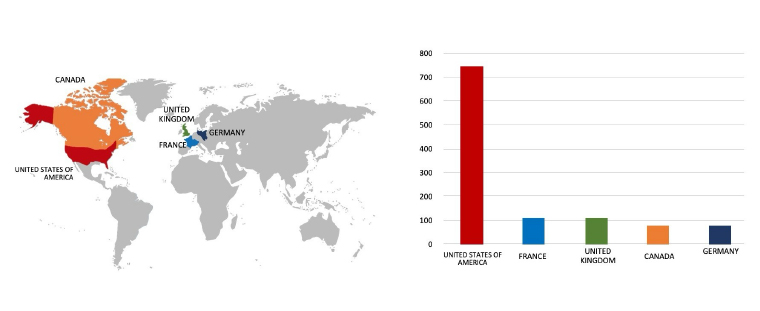
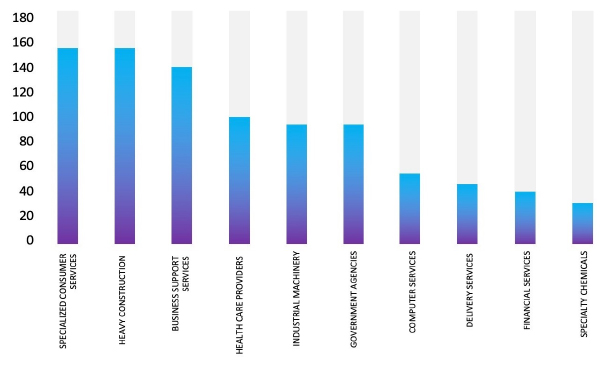
Please find the Geography – Wise and Industry – Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.