



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Geography: Australia, Brazil, Canada, China, France, Germany, India, Italy, Mexico, Netherlands, Peru, Poland, South Africa, Spain, Sri Lanka, the United Kingdom, the United States of America, and Venezuela.
Target Industry: Automobiles, Basic Resources, Business Support Services, Chemicals, Computer Hardware, Computer Services, Delivery Services, Education, Electronic Equipment Engineering & Construction, Farming, Fishing & Plantations, Financial Administration, Financial Services, Food, Health Care Providers, Hospitality, Heavy Construction, Industrial Goods & Services, Industrial Machinery, Legal Services, Media Agencies, Oil & Gas, Real Estate, Restaurants & Bars, Software, Specialized Consumer Services, Technology.
Introduction
CYFIRMA Research and Advisory Team has found ransomware known as 8base while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy: From the onset of its operation, the ransomware has targeted various industries, recent victims include:
This ransomware specifically targets the widely used Windows Operating System, which is prevalent across numerous industries and organizations.
Since March 2022, the ransomware group known as 8Base has been actively operating, but it experienced a notable surge in activity in June 2023. Describing themselves as “simple pen testers”, 8Base established a leak site where they disclosed victim details through sections like Frequently Asked Questions and Rules.
Additionally, they provided multiple contact methods for communication.
After encryption, the ransomware appends the victim’s ID, [email protected] email address, and the “.8base” extension to filenames.

Screenshot of a Files Encrypted by 8Base Ransomware. (Source: Surface Web)
Researchers found the presence of two distinct ransom notes linked to 8Base. One note bore similarities to RansomHouse, while the other exhibited characteristics consistent with Phobos ransomware. This indicates that 8Base’s operations are influenced by a diverse range of ransomware sources. The ransomware uses the bcdedit command to tamper with the boot configuration data.
It is also responsible for the modification of the autostart extensibility point (ASEP) in the registry.
During our review of 8Base, researchers observed notable resemblances between this group and RansomHouse.
The comparison of ransom notes revealed a significant similarity between the ransom note of 8Base and that of RansomHouse. The two ransom notes shared a 99% match, indicating a strong resemblance.

8Base (blue) compared to RansomHouse (red) ransom notes (Source: Surface Web)
Upon further investigation, researchers found similarities in both language and content between the respective leak sites of 8Base and the RansomHouse. Notably, even the FAQ pages seemed to have been directly copied and pasted, indicating a high degree of resemblance between the two groups.
Upon comparing Phobos ransomware and the 8Base sample, it was determined that 8Base employed version 2.9.1 of Phobos ransomware along with SmokeLoader for initial obfuscation during ransomware entry, unpacking, and loading. Since Phobos ransomware is accessible as a ransomware-as-a-service (RAAS), It allows threat actors to tailor certain aspects according to their requirements.
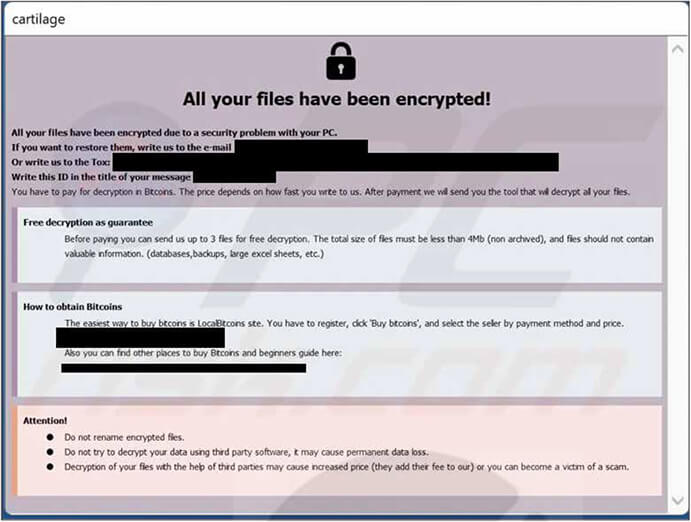
Another ransom note of 8Base Ransomware similar to Phobos. (Source: Surface Web)
While 8Base introduced its own branding customization by appending “.8base” to encrypted files, the format of the appended section remained identical to Phobos ransomware. This format consisted of an ID section, an email address, and finally the file extension. This indicates that while 8Base added its unique branding, it retained the overall structure and components of the Phobos ransomware format.
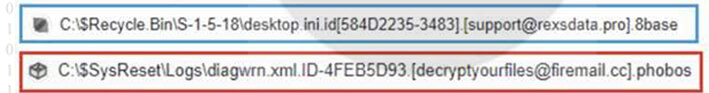
8Base (blue) compared to Phobos (red) file extensions. (Source: Surface Web)
Researchers found that the 8Base sample was obtained from the domain admlogs25[.]xyz. This domain is linked to SystemBC, a malicious remote administration tool and proxy utilized by various ransomware groups. SystemBC serves to encrypt and obscure the destination of the attackers’ Command and Control traffic, further highlighting the distinct characteristics of the 8Base Ransom Group’s operations.
The exact affiliation of 8Base with either Phobos or RansomHouse remains uncertain currently. However, the notable similarities between 8Base and RansomHouse and their utilization of Phobos Ransomware are intriguing. As of now, 8Base remains a prominent and active ransomware group within the cybersecurity landscape.
Mutexes created by 8base: Mutexes Created
Countries Targeted by 8Base.
Insights:
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques / Sub-Techniques |
| 1 | TA0002: Execution | T1053: Scheduled Task/Job T1129: Shared Modules |
| 2 | TA0003: Persiste nce | T1053: Scheduled Task/Job T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information T1027.002: Obfuscated Files or Information: Software Packing T1036: Masquerading T1070.004: Indicator Removal: File Deletion T1497: Virtualization/Sandbox Evasion T1562.001: Impair Defenses: Disable or Modify Tools T1564.001: Hide Artifacts: Hidden Files and Directories |
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping T1056: Input Capture |
| 6 | TA0007: Discovery | T1057: Process Discovery T1082: System Information Discovery T1083: File and Directory Discovery T1497: Virtualization/Sandbox Evasion T1518.001: Software Discovery: Security Software Discovery |
| 7 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 8 | TA0009: Collection | T1005: Data from Local System T1056: Input Capture |
| 9 | TA0040: Impact | 1486: Data Encrypted for Impact T1490: Inhibit System Recovery |
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
Sigam Rule:
title: Delete shadow copy via WMIC description: Delete shadow copy via WMIC threatname:
behaviorgroup: 18
classification: 0
mitreattack:
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine:
– ‘*wmic*shadowcopy delete*’
condition: selection
level: critical
(Source: Surface Web)
Type: Information Stealer
Objective: Stealing Credentials & Data Exfiltration
Target Technology: Windows, Browsers & Extensions
Active Malware of the Week
This week “Meduza Stealer” is trending.
Meduza Stealer
Researchers have recently found a new information-stealing malware called Meduza Stealer. This malware is designed to target Windows-based systems and is currently being actively developed by its creator. The main objective of the creator is to make Meduza Stealer difficult to detect by existing software security solutions. Meduza Stealer focuses on stealing various types of data from users. It targets browsing activities and extracts a range of browser-related information, including login credentials, browsing history, bookmarks, and even vulnerable extensions such as crypto wallet extensions, password managers, and 2FA extensions.
Marketing and Distribution Tactics of Meduza Stealer
The Meduza stealer is a malicious program that is being promoted using sophisticated marketing tactics. The administrator of the stealer has conducted scans of the malware sample using reputable antivirus software and shared screenshots to demonstrate its ability to evade detection. What sets Meduza Stealer apart is its design, as it doesn’t use common obfuscation techniques, making it difficult to identify and trace. It also establishes a connection with the attacker’s server before stealing data, and if the connection fails, it terminates quickly, making it harder to track. The administrator has aggressively advertised the thief on cybercrime forums and Telegram channels.
One major concern is that a significant number of antivirus software programs are ineffective against Meduza stealers, failing to detect it either statically or dynamically. The marketing strategy of the administrator includes a pricing model that offers different subscription options, such as one-month, three-month, and lifetime access plans.
Subscribers gain access to a user-friendly web panel where they can customize their binary options. The panel provides detailed information, such as IP addresses, geographical data, OS build names, and the count of stored passwords, wallets, and cookies. Subscribers can directly download or delete stolen data from the web page, giving them unprecedented control over illicit information. These features highlight the sophistication of Meduza Stealer and the determination of its creators to ensure its success.
Attack Method
Once the Meduza Stealer successfully infiltrates a computer, it follows a specific sequence of operations. It begins by checking the geolocation of the victim. If the location is on the stealer’s list of excluded countries, the malware immediately terminates.
However, if the location is not on the list, the stealer proceeds to check the accessibility of the attacker’s server. If the server cannot be reached, the stealer also aborts its activity. If both conditions are met, the stealer proceeds to gather a wide range of information, including system details, browser data, password manager information, mining-related registry data, and information about installed games. Once this comprehensive set of data is collected, it is packaged and uploaded to the attacker’s server, completing the stealer’s operation on the infected machine. The malware utilizes Windows APIs such as GetUserName, GetComputerName, GetCurrentHWProfile, and EnumDisplayDevices to gather system information, and it retrieves the public IP address using an HTTPS-based API.
System details Collected
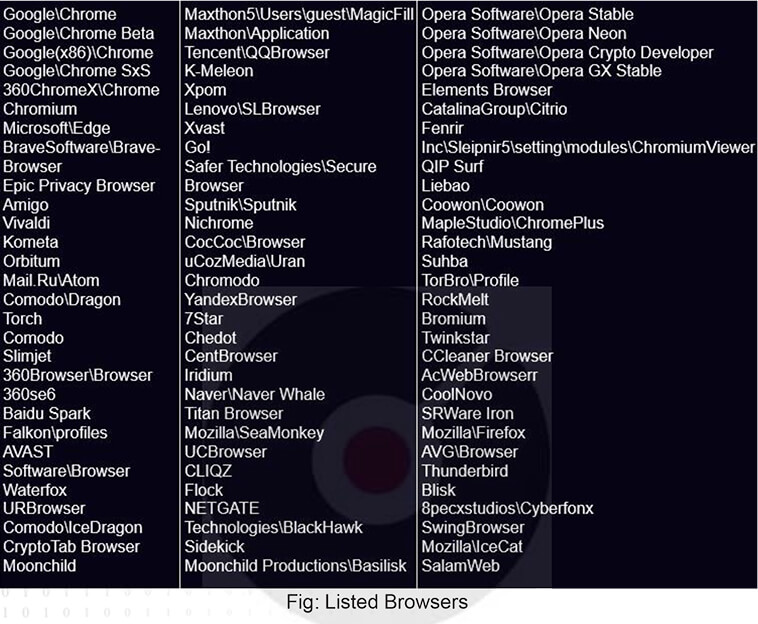
The Meduza Stealer has a predefined list of browsers and scans the “User Data” folder to extract various browser-related data, including Browser History, Cookies, Login Data, Web Data, Login Data for Account, and Local State. The following screenshot shows the list of browsers targeted by Meduza Stealer:
In addition, the stealer scans the Telegram Desktop application by checking the Windows registry, specifically the ID found in the following paths:
Targeted Clients
In addition to its primary targets, the Meduza Stealer also focuses on stealing data from various other applications and services. These include the Steam client, Discord, password manager applications, two-factor authentication (2FA) systems, and cryptocurrency wallet extensions. The malware aims to gather sensitive information from these additional clients to expand the scope of its data theft operations.
Steam client -The stealer retrieves Steam client data by reading the registry key “HKCU\SOFTWARE\Valve\Steam.” Steam is a digital distribution platform created by Valve Corporation, primarily used for video games. This registry key stores user-specific settings, game information, login data, session information, and other configuration data associated with the Steam client.
Discord – The stealer accesses the Discord folder and retrieves the configuration and other relevant details, such as:
Password manager & Two-factor authentication – The Meduza Stealer targets web browsers to extract ID details from password manager applications, two-factor authentication (2FA) systems, and cryptocurrency wallet extensions. It specifically focuses on extracting data from extensions related to 2FA and password managers, as they can contain important information and potential vulnerabilities. By gaining access to 2FA codes or exploiting weaknesses in password manager extensions, attackers can bypass security measures and gain unauthorized entry to user accounts.
Crypto wallet extensions – The malware attempts to extract cryptocurrency wallet extensions from web browsers via software plugins or add-ons that enable users to conveniently manage their cryptocurrency assets directly within web browsers like Chrome or Firefox. These extensions provide functionality for tasks such as monitoring account balances, conducting cryptocurrency transactions details.
The stealer reads the configuration and related data stored within the following registry.
After gathering stolen data, it attempts to establish a connection with a socket and utilizes a send handle to transmit the data to the attacker’s server.
INSIGHTS
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule Meduza
{
meta:
malware_name = “Meduza”
description = “Meduza is a trojan stealer that gathers sensitive data such as browser cookies, histories, crypto wallet information, and more from infected machines.”
strings:
$string_1 = “autofill-profiles.json” ascii wide
$string_2 = “formhistory.sqlite” ascii wide
$string_3 = “logins.json” ascii wide
$string_4 = “cookies.sqlite” ascii wide
$string_5 = “key4.db” ascii wide
$string_6 = “Electrum\\config” ascii wide
$string_7 = “Sparrow\\wallets” ascii wide
$string_8 = “Coinomi\\wallets” ascii wide
$string_9 = “Electrum-LTC\\wallets” ascii wide
$string_10 = “Mozilla\\SeaMonkey” ascii wide
$string_11 = “Yandex\\YandexBrowser” ascii wide
$string_12 = “BrowserPass” ascii wide
condition:
all of them
}
(Source: Surface Web)
Key Intelligence Signals:
Threat Actor in Focus
Mustang Panda Caught Running a Campaign Against European Nations
Summary:
In a recent observation, it was found that APT Mustang panda was operating a campaign named SmugX that was actively targeting embassies and foreign affairs ministries in the UK, France, Sweden, Ukraine, Czech Republic, Hungary, and Slovakia, since December 2022. The SmugX campaign employs strategically designed lure documents that revolve around European domestic and foreign policies, indicating its primary objective of espionage. Noteworthy examples collected during the investigation include a letter from the Serbian embassy in Budapest, a document outlining the priorities of the Swedish Presidency of the Council of the European Union, an invitation to a diplomatic conference issued by Hungary’s Ministry of Foreign Affairs, and an article concerning Chinese human rights lawyers. To conceal their malicious payloads, the SmugX attacks rely on two infection chains that effectively utilize HTML smuggling. This technique involves encoding the harmful elements within HTML documents, attached to the lure messages, making detection and analysis more challenging. In one variation, a ZIP archive containing a malicious LNK file triggers PowerShell to extract an archive that includes a legitimate executable from an older version of the RoboForm password manager, a malicious DLL (Roboform.dll) sideloaded using the legitimate executable, and the execution of the PlugX remote access trojan (RAT) through PowerShell. The second variation utilizes HTML smuggling to download a JavaScript file, which retrieves an MSI file from the attacker’s command and control (C2) server. The MSI file then creates a new folder within the “%appdata%\Local” directory, housing a hijacked legitimate executable, a loader DLL, and the encrypted PlugX payload named “data.dat”.
Insights:
The threat actor Mustang Panda has been involved in three different attacks. A few weeks back, they implanted a covert backdoor software called ‘Horse Shell’ through a TP-Link firmware update, in another recent case they deployed malware via infected USB drives, targeting the healthcare industry in Europe, and now in a very recent discovery, they employed HTML smuggling to target European governments. These incidents highlight the adaptability and ongoing cybersecurity challenges posed by Mustang.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Transparent Tribe seen targeting Indian military and academia again
Researchers have recently observed SideCopy; a subdivision of the Pakistan-aligned (and most likely sponsored) threat actor, Transparent Tribe, targeting the army of India and some organizations in academia. The researchers observed the threat actor using several honeytrap lures, either themed as defence procurement procedures or with the selection of officers for foreign assignments’ themes for the military, and scientific conferences in case of academia. At least one Indian scientist was recently arrested for leaking sensitive information to Pakistani agents who honey-trapped him.
Iranian hackers go spear phishing
Threat actor appears to be primarily interested in gathering intelligence via compromising account credentials and, as a result, getting into email boxes of its targets. The APT will frequently seek to get access to more systems, such as those reachable through corporate virtual private networks or other remote access services, by extracting whatever additional credentials or access they can. For instance, the threat actor pretended to be an Israeli reporter and started corresponding with the target person. After exchanging messages for a few days, the threat actor delivered the victim a password-protected file that included the malware installation instructions.
Hackers claiming to be part of the Wagner PMC attacked Russian satellite communications company
Unidentified hackers, claiming to be part of the private military company; Wagner, that has recently mutinied against the Russian Ministry of defense, have targeted Dozor, a Russian satellite communications company, and have defaced several websites, posting the logo of the PMC on the sites. The yet unidentified hackers have also uploaded a leak containing 674 files, including pdfs, images, and documents, some of the documents showing connections between the main Russian intelligence agency FSB and Dozor, including the passwords, Dozor employees were supposed to use when dealing with FSB representatives.
The company has been confirmed to be disconnected from the internet, but the claims posted by the hackers are much more substantial than that. The attackers are claiming that they have damaged some of the satellite terminals operated by the company and destroyed confidential information stored on Dozor’s servers. This information could not be confirmed as of writing and at the same, the hackers might not be affiliated with Wagner at all, as none of the long-term affiliated channels and social media profiles operated by the group claimed credit for this attack. Hence, a pro- Ukrainian false flag operation remains very much a possibility in this case.
Blount Fine Foods is Impacted by Black Basta Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from The United States of America, (www[.]blountfinefoods[.]com), was compromised by Black Basta Ransomware. BlountFine Foods, formerly Blount Seafood, is a prepared foods and soup manufacturer that produces wholesale frozen and fresh soups under the Blount brand as well as Panera Bread and Legal Sea Foods. The data breach encompasses sensitive and confidential documents belonging to the organization.
The following screenshot was observed published on the dark web:
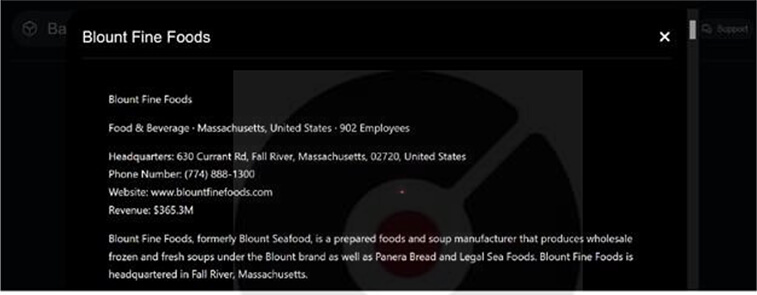

Source: Dark Web
Insights:
Vulnerability in RubyGems
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack
Insights:
The vulnerability exists due to insufficient input validation when parsing URL.
Impact :
A remote attacker can pass a specially crafted URL to the application and perform a regular expression denial of service (ReDos) attack.
Affected Products: https[:]//www[.]ruby-lang[.]org/en/news/2023/06/29/redos-in-uri-CVE- 2023-36617/
Note, the vulnerability exists due to an incomplete fix for CVE-2023-28755
NoName057 Unleashes Malicious Traffic Against Financial Sector of Poland
Summary:
Recently, the pro-Russian hacktivist group; NoName057 made the announcement of targeting Poland’s cyber assets on their telegram channel. The threat actor is known for targeting nations and governments with anti-Russian stances. The group on their telegram channel said, “Today we chose Russophobic Poland as the target of the attack” and blamed Poland for supporting Ukraine in the ongoing war and claimed of paralyzing the website of PKO Bank Polski. The attack didn’t stop there, then the threat actor started targeting various other services of Bank Pekao, including Plus Bank of Poland and shifted their focus towards the energy sector by targeting Polska Grupa Energetyczna.
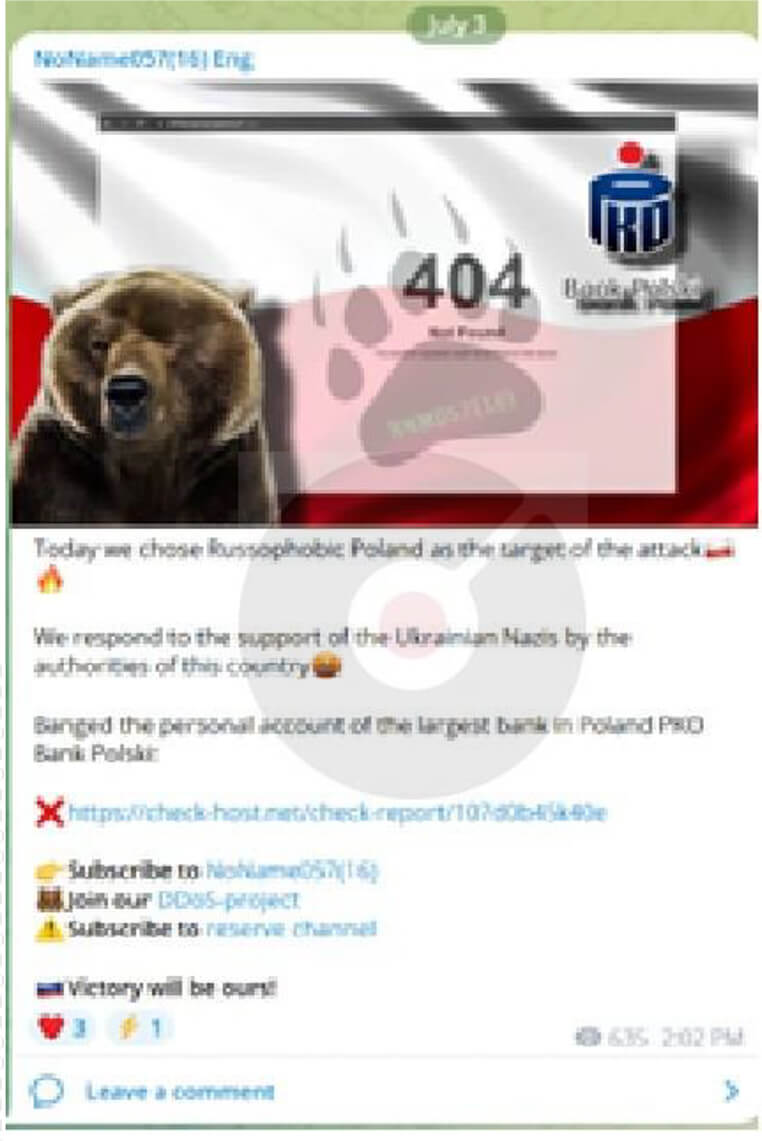
Source: Telegram channel
Insights:
The threat actor has their own tool called DDoSia. The tool was initially written in Python, the latest version is written in Golang and was released on 19 April 2023. This new version supports an additional security mechanism to conceal the list of targets. Besides the growth in community size, which also translates to more disruptive attacks, DDoSia has also improved its toolset and introduced binaries for all major OS platforms, increasing its reach to a broader audience.
Data Leaks
Rockpoint Legal Funding Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Rockpoint Legal Funding, {www[.]rockpointlegalfunding [.]com}. Rockpoint provides funds and accessible medical treatment to plaintiffs as well as capital to law firms to level the playing field in litigation. The collection of compromised data includes a range of sensitive information, such as user_id, user_name, resource_type, resource_id, payload, message, response_code, and other confidential details. The compromised data has a total size of approximately 5 gigabytes (GB).
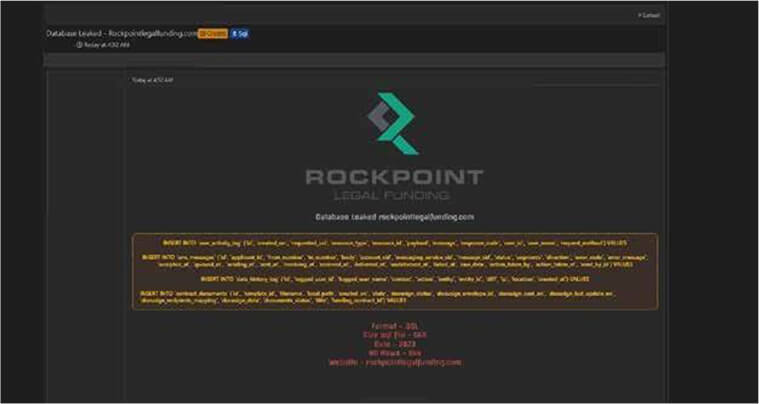
Source: Underground forums
Insights:
Financially motivated cybercriminals are constantly searching for vulnerable systems and applications, employing opportunistic strategies. Many of these attackers participate in underground forums, where they discuss and conduct illegal transactions involving stolen digital assets. Unlike ransomware or extortion groups, who often publicize their attacks, these individuals prefer to maintain a low profile. They exploit unpatched systems and application vulnerabilities to gain unauthorized access and steal valuable data. This stolen data is later advertised, sold, and repurposed by other attackers for their own malicious activities.
CYFIRMA Research team observed a potential data leak related to (www[.]Justice[.]fr). The Ministry of Justice is a ministerial department of the Government of France, also known in French as la Chancellerie. It is headed by the Minister of Justice, also known as the Keeper of the Seals, a member of the Council of Ministers. The data that has been made public comprises a broad spectrum of sensitive and confidential information, including Name Surname, Fixed Telephone, Mobile Phone, Court, City, Fax, IBAN, E-mail, Address, and Zip Code.
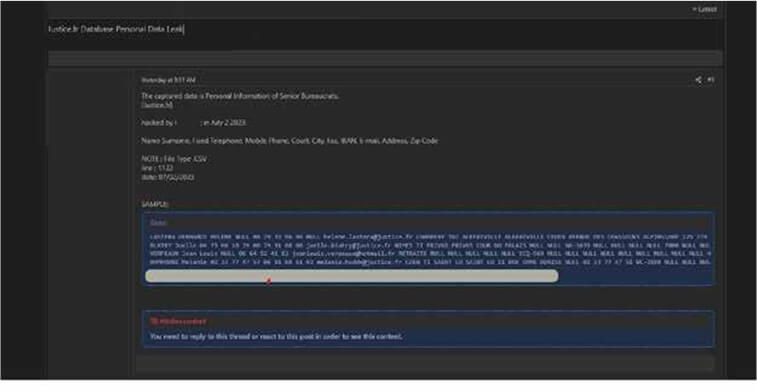
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS