



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Target Industries: Construction, Finance, Hospitality, Investment Banking, IT, Manufacturing, Retail.
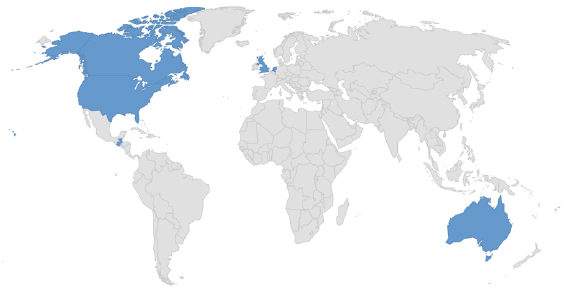
Target Geographies: Australia, Canada, Guatemala, Netherlands, United Kingdom, United States.
Introduction
CYFIRMA Research and Advisory Team has found Lynx ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Lynx
Researchers have recently identified the Lynx ransomware, a threat active since July 2024, but showing significantly aggressive behavior by late August 2024. This ransomware encrypts files and demands a ransom for decryption.
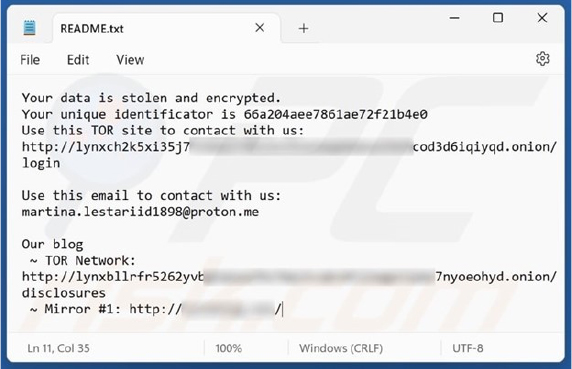
Upon executing, the Lynx ransomware encrypts files and appends the “.LYNX” extension to the name.
They claim to have a strict policy against targeting governmental organizations, hospitals, non-profits, and other sectors vital to society.
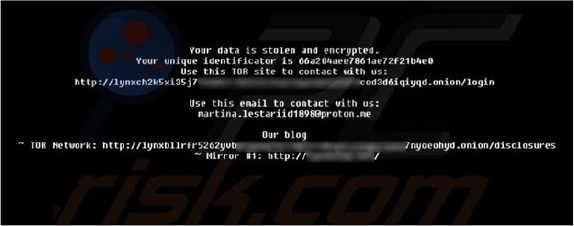
After the encryption process, Lynx altered the desktop wallpaper and placed a text file named “README.txt,” both containing the same ransom note.

Both the text file and the modified desktop wallpaper display an identical, concise ransom message informing the victim that their files have been encrypted and sensitive data has been stolen, urging them to contact the attackers promptly.
In many ransomware attacks, data exfiltration is used as a double-extortion tactic, pressuring victims to pay under the threat of leaking their confidential information. While Lynx’s message does not explicitly threaten to release the stolen data, it includes a link to the attackers’ Tor website, which is known for publishing such compromised data.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1129: Shared Modules |
| T1059: Command and Scripting Interpreter | ||
| T1569.002: System Services: Service Execution | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0005: Defense Evasion | T1027.002: Obfuscated Files or Information: Software Packing |
| T1036: Masquerading | ||
| T1134: Access Token Manipulation | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 6 | TA0007: Discovery | T1007: System Service Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1135: Network Share Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518: Software Discovery | ||
| 7 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 8 | TA0009: Collection | T1074: Data Staged |
| T1113: Screen Capture | ||
| 9 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| 10 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
Based on the available data, CYFIRMA’s assessment indicates that the Lynx ransomware is actively targeting high-value sectors such as Manufacturing, Finance, and Banking, posing a severe threat, particularly to these industries. Given its aggressive attack patterns, we anticipate that Lynx will not only intensify its focus on these sectors but will also evolve to target a broader range of geographies, potentially amplifying its impact on the global ransomware landscape.
SIGMA Rule:
title: Suspicious desktop.ini Action tags:
– attack.persistence
– attack.t1547.009 logsource:
product: windows category: file_event
detection: selection:
TargetFilename|endswith: ‘\desktop.ini’ filter_generic:
Image|startswith:
– ‘C:\Windows\’
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_jetbrains:
Image|endswith: ‘\AppData\Local\JetBrains\Toolbox\bin\7z.exe’ TargetFilename|contains: ‘\JetBrains\apps\’
filter_upgrade:
TargetFilename|startswith: ‘C:\$WINDOWS.~BT\NewOS\’ condition: selection and not 1 of filter_*
falsepositives:
– Operations performed through Windows SCCM or equivalent
– Read only access list authority level: medium
(Source: SurfaceWeb)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Stealing financial information, Remote Access
Target Technology: Android OS
Target Industry: Banks
Target Geography: Brazil
Active Malware of the Week
This week “Rocinante” is trending.
Rocinante
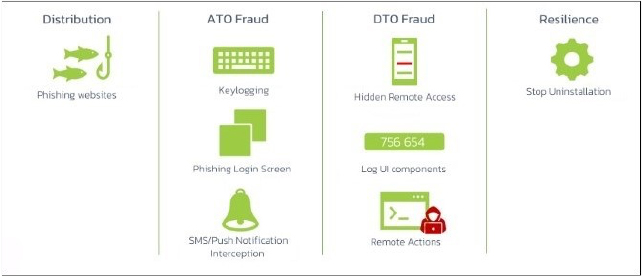
Recently, researchers identified a new strain of malware named Rocinante, originating from Brazil and actively targeting most banking institutions in the region. This malware represents the latest wave of mobile banking threats, reflecting the ongoing growth and diversification in the field. Rocinante utilizes the Accessibility Service to perform keylogging and steal personally identifiable information (PII) through phishing screens mimicking various banks. It can also use the exfiltrated data to execute a Device Takeover (DTO), gaining full remote access to the infected device by exploiting these privileges. Rocinante employs a combination of Firebase messaging, HTTP traffic, WebSocket traffic, and the Telegram API to register infected devices, exfiltrate information, and perform DTO. Influenced by threat developments in other regions, the authors of Rocinante have incorporated parts of the source code from Ermac and Hook into their implementation. The malware authors name their bot “Pegasus” or “PegasusSpy,” which clashes with NSO Group’s infamous Pegasus spyware used to surveil activists and dissidents. To avoid confusion, the researchers have named this malware family “Rocinante,” inspired by Don Quixote’s horse. Rocinante targets Brazilian banking institutions for financial gain and lacks advanced spyware capabilities like “Pegasus”.
Attack Method
The malware is initially distributed through phishing websites that deceive users into installing a malicious APK, which poses as a security solution or a banking institution app. After the victim launches the application and grants Accessibility Services, he / she is welcomed with a choice screen. Each option leads to a distinct phishing page, requesting the victim’s personal identifiable information (PII), with each login page customized to resemble a different bank the malware is mimicking.
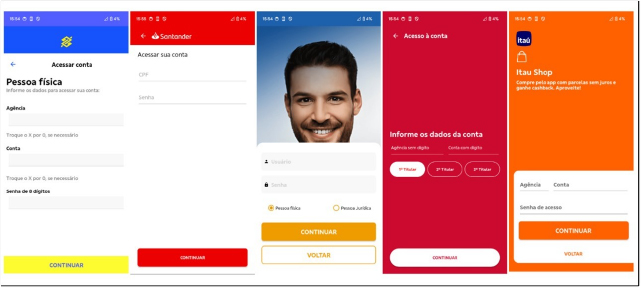
Features and capabilities
Rocinante malware is equipped with a range of sophisticated capabilities and features, including C2 communication, keylogging, phishing screens, and data exfiltration. It also supports remote actions and command execution, making it a formidable threat in mobile cybersecurity.
C2 communication
Rocinante employs a multi-protocol approach for communication from infected devices. Initially, it uses HTTP to obtain a token from Firebase, which is then used for subsequent communication with Command and Control (C2) servers. The malware sets up WebSocket communication to transmit keylogging data and receive commands. The initial communication is directed to the Firebase messaging server, which registers the bot’s installation on the infected device and issues a token. This token is later used for communication with one of the C2 servers. This token also serves to link the unique ID used in WebSocket communication with the specific malware installation. Next, the malware reaches out to its first-stage C2 server through an HTTP GET request, requesting an upgrade to WebSocket communication. Once established, the bot transmits keylogging data to the WebSocket server and simultaneously awaits commands. Additionally, a third C2 server is used to relay the installation token from Firebase and correlate it with the WebSocket ID.
Keylogging, Phishing screens, and Exfiltration
Once granted Accessibility Service privileges, Rocinante begins to log all activity on the device, capturing every UI event in detail. These logs, which record everything displayed to the user, are sent via the WebSocket channel, enabling attackers to track any actions or information shown on the infected device. The most crucial data, particularly PII gathered from phishing pages, is processed on the device and sent through a different method. Each Rocinante variant is connected to a Telegram Bot that receives this sensitive information.
The bot then extracts and formats the PII, such as device details, CPF numbers, passwords, and account numbers, and shares it in a chat accessible to cybercriminals. The specifics of the data can vary based on the phishing page used to collect it.
Remote Actions
A key feature of Rocinante, and one that criminals are continuously enhancing, is its capability to execute remote actions on the infected device. Utilizing Accessibility Service privileges, this banking malware can simulate touches and gestures, as well as alter text in EditText and MultiAutoCompleteTextView fields. These capabilities enable it to navigate through the device’s UI to initiate and authorize fraudulent transactions. The malware receives its instructions from the C2 server through the WebSocket channel, with specific commands outlined in the following section:
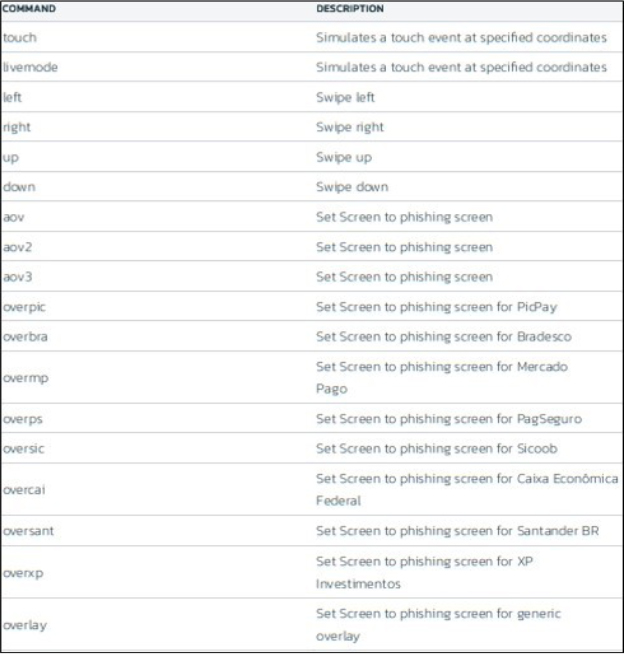
DTO malware targeting Brazil
Rocinante aligns with the typical behavior of banking malware targeting Brazil, where static target lists are preferred over dynamic ones. Unlike global campaigns that dynamically retrieve targets from a C2 server to adapt to different regions, Brazilian-focused malware, including Rocinante, often has fixed targets. This suggests that local cybercriminals are more focused on their immediate geographical area and have little interest in expanding beyond it, reducing the need for flexible targeting mechanisms. The distribution methods for Rocinante include campaigns masquerading as security updates, courier applications, rewards apps, and even banking applications. Phishing websites play a central role in these campaigns, luring users into downloading and installing malicious APKs disguised as legitimate software. This distribution strategy reflects the tailored approach of Brazilian cybercriminals, who exploit local user behaviors and preferences to maximize the impact of their attacks.

INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as Rocinante evolves, its impact on organizations and employees is likely to grow significantly. In the future, we can anticipate a rise in sophisticated phishing attacks and financial fraud targeting employees within organizations, especially those in financial sectors. With its remote access capabilities, Rocinante could facilitate more extensive and persistent intrusions, allowing attackers to monitor and manipulate sensitive data and transactions continuously. Organizations might face increased operational disruptions and financial losses due to unauthorized transactions and compromised accounts. Employees could experience heightened risks of identity theft and personal financial damage. As cybercriminals adopt and adapt advanced techniques, the emergence of new malware variants could lead to more versatile and adaptive threats, intensifying the challenges for organizations in maintaining security.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
State-Sponsored Hackers and Commercial Spyware Vendors Use Identical Exploits – APT29
Summary:
Between November 2023 and July 2024, multiple exploit campaigns targeted Mongolian government websites through a watering hole attack. These campaigns employed an iOS WebKit exploit and a Chrome exploit chain, leveraging vulnerabilities with existing patches to target unpatched devices. The attacks are assessed with moderate confidence to be linked to the Russian government-backed APT29. Notably, the exploits used were either identical or strikingly similar to those previously utilized by commercial surveillance vendors (CSVs), such as Intellexa and NSO Group.
The watering hole attacks initially compromised the Mongolian sites cabinet[.]gov[.]mn and mfa[.]gov[.]mn to deliver an exploit for CVE-2023-41993 targeting iOS versions older than 16.6.1. This exploit, involving a cookie stealer framework, was observed again in a similar form in February 2024. In July 2024, the focus shifted to Android users, with a Chrome exploit chain targeting CVE-2024-5274 and CVE-2024-4671 delivered through a newly compromised iframe.
The iOS attack involved a reconnaissance payload identifying device specifics before deploying the WebKit exploit to exfiltrate browser cookies. This exploit did not affect iOS 16.7 or devices with lockdown mode enabled. The Chrome attack, on the other hand, required an additional sandbox escape to bypass Chrome’s site isolation, employing obfuscated JavaScript to deliver the payload. The Chrome exploit involved storing status information using indexedDB and ultimately exfiltrated cookies, account data, login credentials, and browser history.
The exploits used in these campaigns were either identical or very similar to those from CSVs, indicating that APT actors are repurposing n-day exploits, initially used as zero- days by commercial entities. Despite the overlap in exploit techniques, the delivery methods and secondary objectives of the campaigns exhibited differences.
Relevancy & Insights:
APT29, also known as Cozy Bear, has a history of high-profile espionage operations targeting government entities, diplomatic institutions, and political organizations, such as their involvement in the 2016 Democratic National Committee breach. Their modus operandi typically involves sophisticated, stealthy attacks aimed at extracting sensitive information for intelligence purposes. In the recent campaign against Mongolian government websites, APT29 has continued this pattern by leveraging advanced, repurposed exploits to target vulnerabilities in iOS and Chrome. This suggests a strategic intent to gather intelligence on regional political and diplomatic activities. The current incident underscores a broader threat landscape where state actors are increasingly utilizing and adapting commercial surveillance tools for espionage. Organizations and governments involved in regional and international diplomacy, as well as those with significant political or strategic value need to be particularly vigilant. The use of advanced, repurposed exploits highlights the importance of robust security practices, timely patch management, and continuous monitoring to mitigate these sophisticated threats.
ETLM Assessment:
The threat actor behind the attacks is APT29, also known as Cozy Bear, a Russian state-backed group associated with intelligence operations. Their recent campaigns targeted government websites in Mongolia, with a specific focus on high-profile sites such as cabinet[.]gov[.]mn and mfa[.]gov[.]mn. The industries affected are primarily governmental, with a particular emphasis on those involved in state affairs and diplomacy. The technology targeted includes iOS devices and Google Chrome, exploiting vulnerabilities like CVE-2023-41993 and CVE-2024-5274. These exploits, which were used to bypass existing patches, reveal a concerning trend of state actors repurposing n-day vulnerabilities, originally developed by commercial surveillance vendors like Intellexa and NSO Group. The threat landscape is marked by an increase in the use of advanced, repurposed exploits that blur the lines between state and commercial surveillance techniques. Looking forward, this indicates a growing sophistication in the methods employed by state actors and a potential rise in the frequency of similar attacks. Organizations must remain vigilant, ensuring timely updates and implementing robust security measures to counteract evolving threats.
Recommendations:
Enhance Patch Management
Immediate Action: Ensure that all systems are up-to-date with the latest security patches to close vulnerabilities such as CVE-2023-41993 and CVE-2024-5274. Regular Updates: Implement a robust patch management policy that includes routine checks for updates and patches for all software and systems.
Strengthen Endpoint Security
Advanced Threat Protection: Deploy advanced endpoint detection and response (EDR) solutions to monitor for unusual activity and potential exploit attempts.
Device Hardening: Apply configuration best practices and harden devices, including disabling unnecessary services and features.
Implement Comprehensive Security Training
User Awareness: Conduct regular training sessions for employees and officials to recognize phishing attempts and other social engineering tactics.
Incident Response: Educate staff on proper incident reporting and response procedures.
Collaborate with Security Vendors and Intelligence Agencies
Threat Intelligence Sharing: Engage with threat intelligence sharing communities and vendors to stay informed about emerging threats and vulnerabilities.
Vendor Solutions: Utilize threat intelligence from commercial surveillance vendors, if appropriate, to understand and counteract sophisticated threats.
Strengthen Incident Response and Recovery Plans
Prepare for Incidents: Develop and regularly test incident response plans to ensure quick and effective action in the event of a security breach.
Backup and Recovery: Implement and regularly test backup and recovery procedures to minimize data loss and ensure business continuity.
Regularly Review and Update Security Policies
Policy Revisions: Continuously review and update security policies and procedures to reflect current threat landscapes and technological advancements.
Compliance: Ensure that security practices comply with industry standards and regulatory requirements.
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial Access | T1189 | Drive-by Compromise |
| Executions | T1203 | Exploitation for Client Execution |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1082 | System Information Discovery |
| Collection | T1114 | Email Collection |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1489 | Service Stop |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Iranian state-sponsored hackers moonlighting as cybercriminals
An Iranian state-sponsored threat actor tracked by researchers as “Pioneer Kitten” has been observed collaborating with criminal ransomware groups for financial gains, according to a joint advisory issued by the US Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense Cyber Crime Center (DC3). The threat actor operates under the cover of an IT company called “Danesh Novin Sahand.” According to the authorities, a significant percentage of these threat actors’ operations against US organizations are intended to obtain and develop network access to then collaborate with ransomware affiliate actors to deploy ransomware.
The group has been previously deployed by the Iranian government to conduct cyberespionage operations towards countries and organizations consistent with Iranian state interests, and typically not of interest to the group’s ransomware affiliate contacts, such as U.S. defense sector networks, and those in Israel, Azerbaijan, and the United Arab Emirates.
ETLM Assessment:
There already is a simmering low-level cyber war ongoing on the sidelines of the conflict between Israel and Hezbollah. In case of a full-scale war, all bets would be off, and every hacktivist and state actor in the region would be incentivized to cause maximum damage, opportunistically choosing targets. However, as we have mentioned in our recent report, as the country is not ready for potential cyber retaliation from Israel or its allies, Iran may prefer to outsource some of its state-driven cyber campaigns to smaller groups outside its territory. Iran might enable some groups to go after government services, energy, banking, finance, and telecommunications in countries considered hostile, and to help finance these operations, these groups might partake in criminal activity like ransomware attacks or intellectual property theft. At the same time, with the Iranian economy crumbling, Iran state-sponsored actors might take the North Korean route and engage in the illicit money-making activity themselves, as seen in this recent case, either with tacit approval of the Revolutionary Guards or with the implied knowledge of impunity before the law.
Chinese hackers broke into the networks of American internet service providers
Chinese hackers have recently infiltrated the networks of at least three U.S. internet service providers (ISPs), gaining deep access. According to U.S. intelligence officials, the attackers used this access to conduct surveillance on government officials and undercover operatives. Some of the techniques employed resemble those used by the Chinese-backed group Volt Typhoon, which has been involved in several significant hacks targeting U.S. critical infrastructure in recent months, possibly with the intent of causing physical damage.
ETLM Assessment:
This spring, U.S. Secretary of State Antony Blinken traveled to Beijing in the latest of a series of high-level meetings between Chinese and U.S. leadership to ease tensions after China complained about the movement of US Navy ships in international waters around Taiwan. That followed last year’s campaigns in the South China Sea regions by other Chinese actors like Volt Typhoon. Its hacking campaigns have been focused on the countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has allegedly been targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. As we have warned in an earlier report, given the increasingly assertive Chinese posturing, it was likely that Beijing’s hackers were trying to position themselves in a way that could try to paralyze U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is an inherent part of Chinese military doctrine and targeting of critical infrastructure in Guam could affect U.S. military operations in a significant way.
The RansomHub Ransomware impacts the Prasarana Malaysia Berhad
Summary:
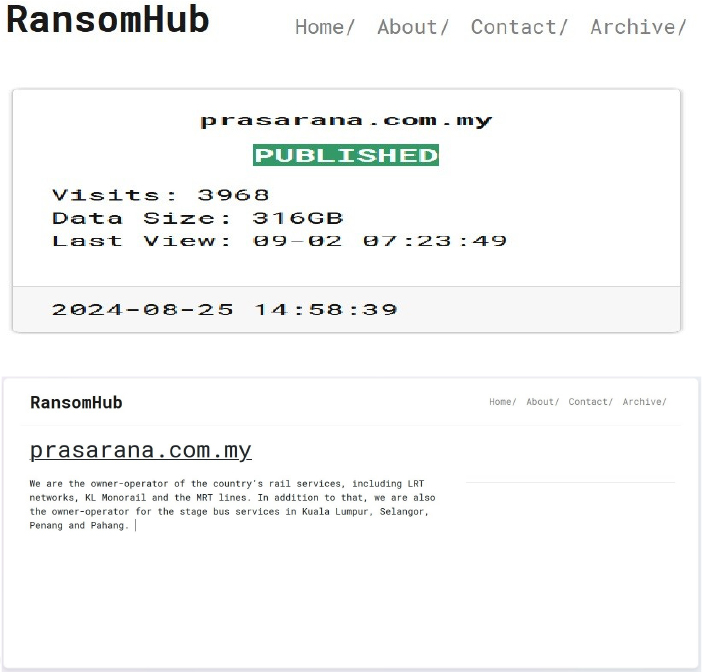
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; Prasarana Malaysia Berhad (www[.]prasarana[.]com[.]my), was compromised by the RansomHub Ransomware. Prasarana Malaysia Berhad is a major public transportation provider in Malaysia, managing urban rail and bus services in key major areas. The company operates the Rapid KL, Rapid Penang, and Rapid Kuantan networks, ensuring efficient and reliable transit solutions. Prasarana also oversees infrastructure development and maintenance, contributing to Malaysia’s sustainable urban mobility. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 316 GB.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Prasarana Malaysia Berhad, from Malaysia, highlighting RansomHub’s significant threat presence in the Southeast Asia region.
The Everest Ransomware Impacts the Mitsubishi Chemical Group
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Mitsubishi Chemical Group (www[.]mcgc[.]com), was compromised by Everest Ransomware.
Mitsubishi Chemical Group is one of the world’s largest chemical companies, with a diverse global presence. Mitsubishi Chemical provides a wide range of products, from basic materials like monomers and polymers to advanced solutions like battery materials, 3D printing materials, and composites. The compromised data includes 6 terabytes of sensitive internal information, such as drawings, developments, contracts, and records of incidents within the company. This data is being offered for sale at a price of $3,000,000.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that Everest Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on Mitsubishi Chemical Group, a prominent Chemical company in Japan, highlights the extensive threat posed by this ransomware strain in the Asia Pacific region.
Vulnerability in IDEC Programmable Logic Controllers
Summary:
The vulnerability allows a remote attacker to compromise the target system.
Relevancy & Insights:
The vulnerability exists due to the generation of predictable numbers or identifiers.
Impact:
A remote attacker can predict some packet header IDs of the device and interfere with communications.
Affected Products: https[:]//jvn[.]jp/en/vu/JVNVU96959731/index.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
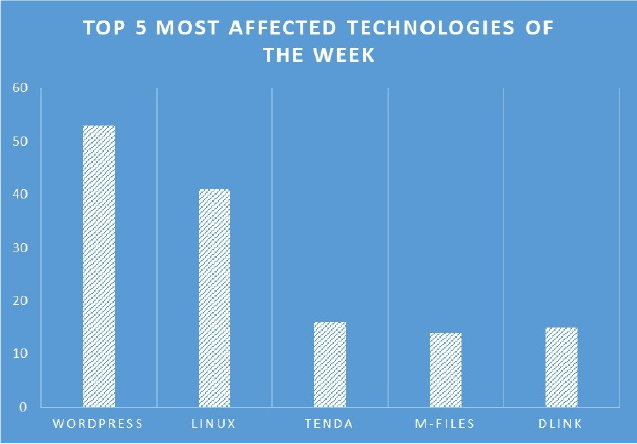
ETLM Assessment:
Vulnerability in IDEC micro programmable logic controllers (PLCs) can pose significant threats to user privacy and security. This can impact various industries globally, including manufacturing, technology, and beyond. Ensuring the security of IDEC PLCs is crucial for maintaining the integrity and protection of industrial control systems worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding the control and automation of large machines or small-scale manufacturing facilities across different geographic regions and sectors.
ElDorado Ransomware attacked and Published the data of CURVC Corp
Summary:
Recently, we observed that the ElDorado Ransomware attacked and published data of CURVC Corp(www[.]curvc[.]com) on its dark web website. CURVC Corp. is a South Korean company specializing in DevOps consulting and software engineering solutions. The company focuses on enhancing productivity in software development through consulting services that leverage various tools, including Atlassian products, SonarQube, and JFrog. The data leak, following the ransomware attack, encompasses sensitive and confidential information related to the organization.
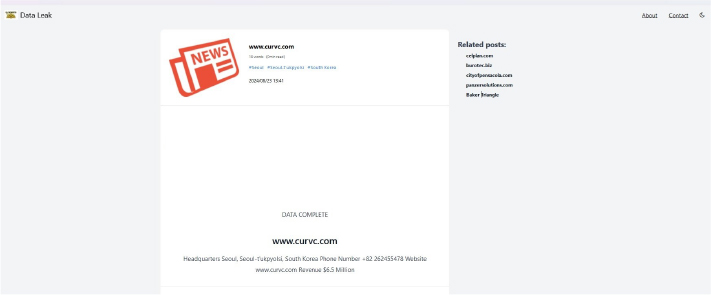
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Eldorado Ransomware is likely to continue its global campaign, targeting a wide range of industries, with a heightened focus on the United States, Europe, and Asia. A recent attack on CURVC Corp, a leading Technology company from South Korea reflects the broader risk Eldorado presents to organizations worldwide, especially in regions where cyber threats are escalating.
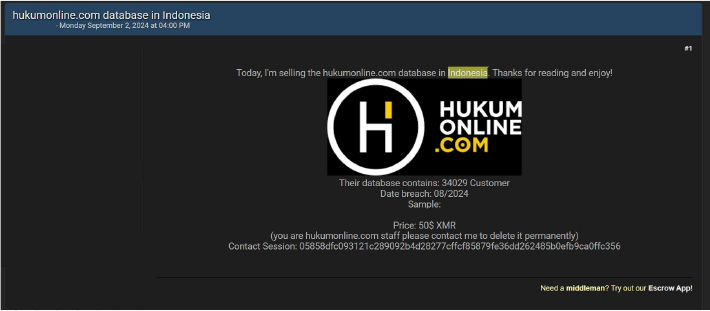
Hukumonline Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to Hukumonline( www[.]hukumonline[.]com) in an underground forum. Hukumonline is a leading legal platform in Indonesia. It serves as a comprehensive resource for legal professionals, offering a wide range of services and products designed to meet the needs of legal practitioners, companies, law firms, and government agencies. The data being offered for sale includes a database containing information on 34,029 customers, with a selling price set at 50 XMR (Monero). The data breach has been attributed to a threat actor identified as “Agreindex”.
PT DUNIA EXPRESS TRANSINDO(Dunex)Indonesia data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to the PT DUNIA EXPRESS TRANSINDO(Dunex)Indonesia (www[.]dunextr[.]com) in an underground forum. PT Dunia Express Transindo, also known as Dunex, is a leading logistics service provider in Indonesia. The company specializes in offering comprehensive logistics solutions, including transportation, warehousing, and distribution services. The compromised data includes users’ email addresses, usernames, and passwords.

Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s assessment, the threat actor known as ” Agreindex ” poses a serious risk to organizations due to its financial motivations and ability to exploit vulnerable institutions. This actor is notorious for infiltrating organizations with weak security measures and profiting by selling stolen sensitive data on the dark web or underground forums. The typical targets of ” Agreindex ” are institutions with inadequate cybersecurity defenses, making them particularly susceptible to the sophisticated cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
The CYFIRMA Research team observed a potential data sale related to a Boutiqaat. A threat actor is claiming to sell the complete database of Boutiqaat.com, a prominent Kuwaiti beauty e-commerce platform. Boutiqaat, which has grown to a valuation of $500 million, serves as one of the largest social e-commerce platforms in the Middle East with 3 million users.
The leaked database reportedly includes sensitive user information, such as IDs, names, emails, phone numbers, addresses, and more. The actor offers the database for $1,500, with full access priced at $2,500.

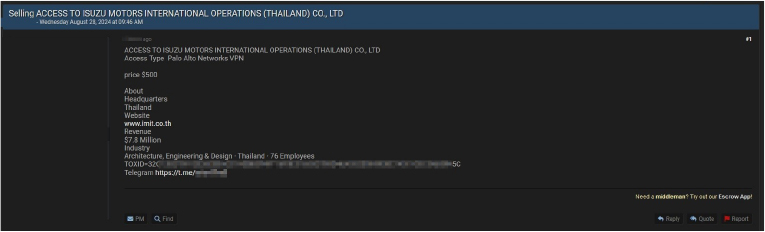
A threat actor has emerged, claiming to offer unauthorized access to the Palo Alto Networks VPN of Isuzu Motors International Operations (Thailand) Co., Ltd., a company with a reported revenue of $7.8 million. The hacker is selling this access for $500, raising significant security concerns for the company, which operates in the architecture, engineering, and design industry in Thailand.
According to the threat actor’s announcement, the access being sold includes full VPN entry into Isuzu Motors International Operations’ network, potentially exposing sensitive corporate information and internal systems. The company, headquartered in Thailand with 76 employees, is a critical part of Isuzu’s international operations. The alleged sale of such access poses a significant risk, not only to Isuzu but also to its partners and customers, highlighting the increasing threats faced by companies in today’s digital landscape.
ETLM Assessment:
The “Amlexo” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
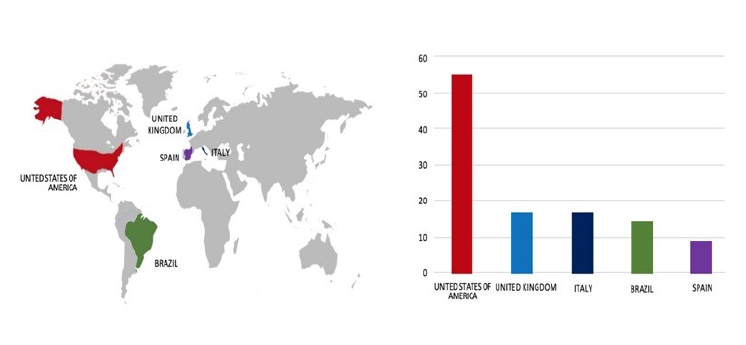
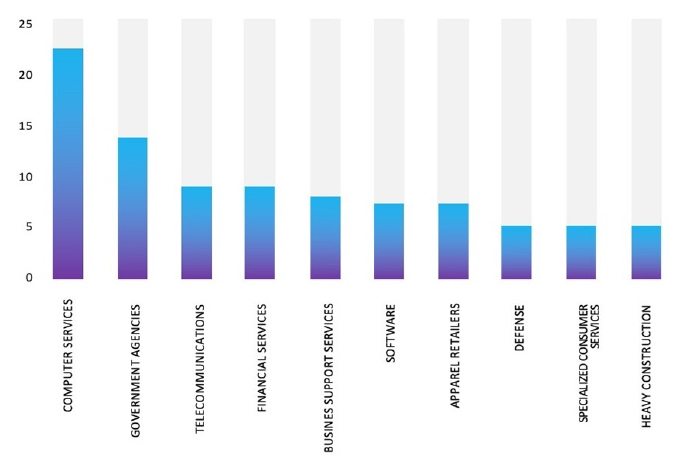
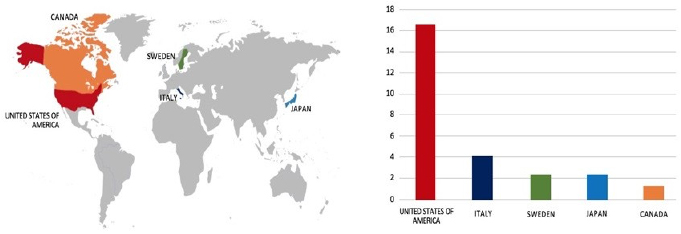
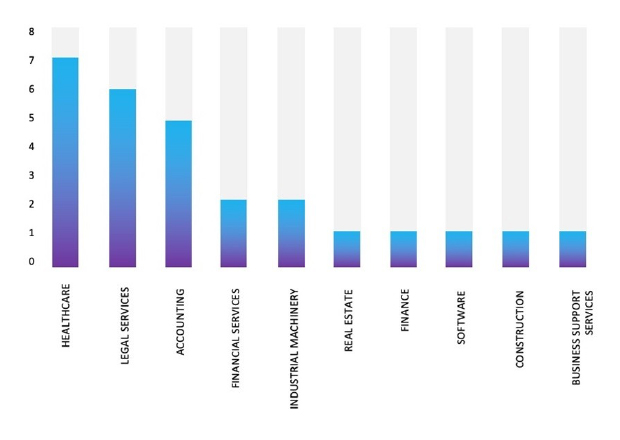
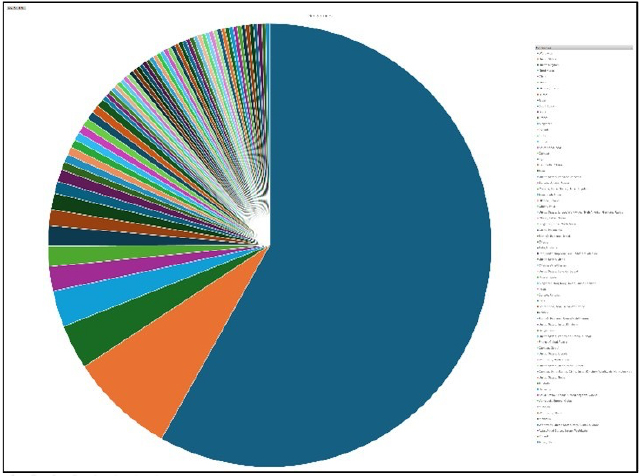
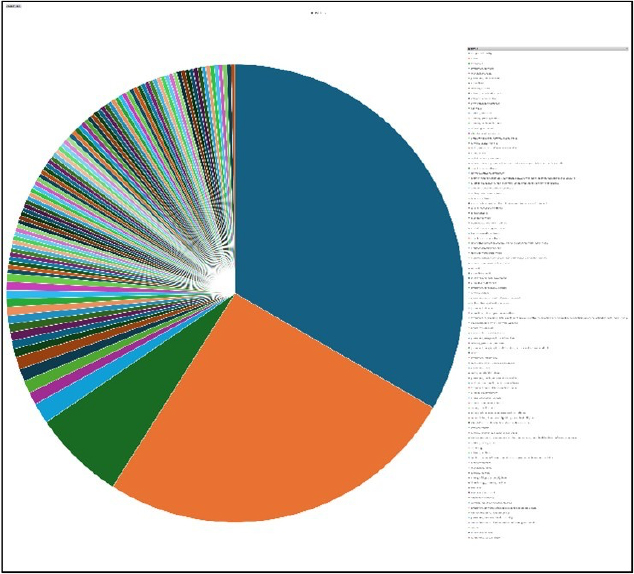
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.