



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Target Geographies: Argentina, Canada, Germany, Italy, Mexico, Romania, United Kingdom, United States.
Target Industries: Construction, E-commerce, Education, FMCG, Food & Beverage, Government, Health Care, IT, Manufacturing, Real Estate, Telecommunication, Transportation & Logistics.
CYFIRMA Research and Advisory Team has found ransomware known as LostTrust while monitoring various underground forums as part of our Threat Discovery Process.
LostTrust is a newly emerging ransomware that encrypts files and adds the “.losttrustencoded” extension to the names of the encrypted files.
The ransomware generates ransom notes named “!LostTrustEncoded.txt” in every folder on the device. In these notes, the threat actors initially presented themselves as former white hat hackers who had transitioned to cybercrime due to inadequate compensation.
Researchers believe that LostTrust is likely a rebrand of MetaEncryptor. LostTrust began targeting organizations in March 2023 but gained notoriety in September when it started using a data leak site, listing 53 victims globally.
The ransomware variants LostTrust and MetaEncryptor show only slight distinctions such as ransom notes, embedded public keys, names of ransom notes, and file extensions used for encryption.
Furthermore, researchers noted the presence of the ‘METAENCRYPTING’ string in the encryptor, indicating its modification from the MetaEncryptor variant.
The encryptor can be launched with two optional command line arguments, –onlypath (encrypt a specific path) and –enable-shares (encrypt network shares).
Once activated, LostTrust goes to lengths to disable various Windows services, ensuring the encryption of all files, including those related to Firebird, MSSQL, SQL, Exchange, wsbex, postgresql, BACKP, tomcat, SBS, and SharePoint. Additionally, it targets and disables further services associated with Microsoft Exchange.
Ransom demands for LostTrust vary, ranging from $100,000 to several million dollars.

Screenshot of Files Encrypted by LostTrust Ransomware. (Source: Surface Web)
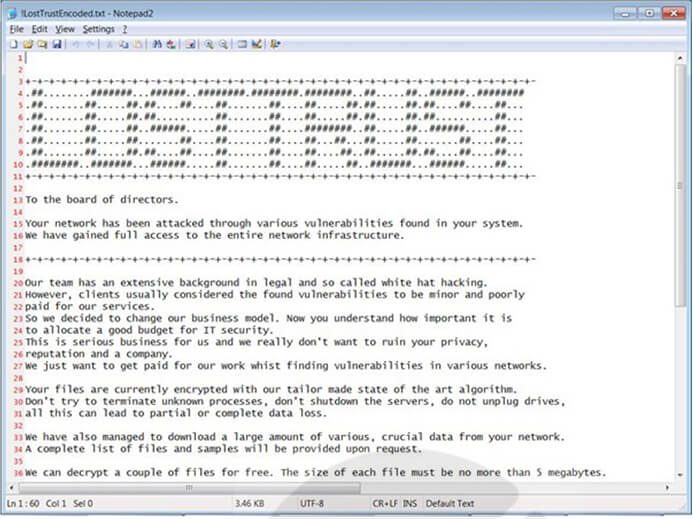
Screenshot of a ransom note by LostTrust Ransomware.

Countries Targeted by LostTrust Ransomware
CYFIRMA’s Assessment based on available information states that, LostTrust ransomware is likely to continue its malicious activities, with a particular focus on the widely used Windows Operating System. Moreover, its adaptability to disable debugging environments and exploit WMI suggests ongoing efforts to evade detection and expand its reach. Organizations, especially those in the US and other developed nations, should remain vigilant and enhance cybersecurity measures to mitigate the evolving threat posed by LostTrust ransomware.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| T1569.002: System Services: Service Execution | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| 3 | TA0004: Privilege Escalation | T1134: Access Token Manipulation |
| T1543.003: Create or Modify System Process: Windows Service | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1070: Indicator Removal | ||
| T1070.001: Indicator Removal: Clear Windows Event Logs | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1070.006: Indicator Removal: Timestomp | ||
| T1134: Access Token Manipulation | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| 5 | TA0006: Credential Access | T1056: Input Capture |
| 6 | TA0007: Discovery | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1135: Network Share Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1056: Input Capture |
| T1560.002: Archive Collected Data: Archive via Library | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1095: Non-Application Layer Protocol | ||
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Kindly refer to the IOCs section to exercise controls on your security systems.
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense_evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
Type: Loader
Objective: Malware Implant, Data Theft and Remote Access
Target Technology: Windows OS, Browsers, Messaging Applications, VPN
This week “BunnyLoader” is trending.
Researchers have identified and disclosed a new C/C++-based malware-as-a-service (MaaS) threat called BunnyLoader, currently advertised for sale on various cybercrime underground forums at a price of $250. It offers multiple functionalities, including downloading and executing a second-stage payload and stealing browser credentials and system information. BunnyLoader employs a keylogger to log keystrokes as well as a clipper to monitor the victim’s clipboard and replace cryptocurrency wallet addresses with actor-controlled cryptocurrency wallet addresses. After gathering the information, BunnyLoader compresses the data into a ZIP archive and transmits it to a command-and- control (C2) server.
Researchers have analysed a BunnyLoader malware sample, and upon its execution, the loader performs the following actions:
If a sandbox is identified, BunnyLoader throws the following error message:
“The version of this file is not compatible with the current version of Windows you are running. Check your computer’s system information to see whether you need an x86 (32- bit) or x64 (64-bit) version of the program, and then contact the software publisher.”
Otherwise, BunnyLoader performs an HTTP registration request to a C2 server.
Following registration, BunnyLoader sends a task request to the C2 server “http[:]//37[.]139[.]129[.]145/Bunny/TaskHandler.php?BotID=
BunnyLoader is designed to execute various tasks, Such as:
BunnyLoader executes two types of downloads and executes functions. The first involves downloading a file from a C2-provided URL, saving it in the AppData\Local directory, and executing it. The second type uses fileless execution, creating a suspended “notepad.exe” process, downloading the payload with the user agent “BunnyLoader_Dropper,” and storing it in a memory buffer. BunnyLoader then employs Process Hollowing to inject the payload into the “notepad.exe” process. Upon task completion, BunnyLoader sends a task completion request with the user agent “TaskCompleted” and the Task ID as the CommandID.
BunnyLoader employs a simple keylogger utilizing GetAsyncKeyState() to log keystrokes, with the logged data stored in the file “C:\Users\<username>\AppData\Local\Keystrokes.txt.”
BunnyStealer is sophisticated malware designed to extract diverse data from web browsers, cryptocurrency wallets, VPNs, and messaging applications. The harvested information is stored in the “BunnyLogs” folder within the Appdata\Local Directory, compressed into a ZIP archive, and sent to the C2 server. The targeted web browsers encompass popular ones like Google Chrome, Yandex, Vivaldi, Microsoft Edge, BraveBrowser, and others. BunnyLoader specifically steals AutoFill data, credit card details, downloads, browsing history, and passwords from these browsers. Additionally, it targets cryptocurrency wallets such as Armory, Ethereum, Jaxx, Exodus, Coinomi, and Electrum. Steals credentials from VPN clients like ProtonVPN and OpenVPN and extracts information from messaging applications like Skype, Tox, Signal, Element, and ICQ. This comprehensive data theft underscores the malware’s intent to compromise various sensitive information sources.
BunnyLoader’s clipper module scans a victim’s clipboard for cryptocurrency addresses and substitutes them with a wallet address under the threat actor’s control. The replacement addresses are obtained from the C2 server. The targeted cryptocurrencies include:
BunnyLoader carries out remote command execution via the C2 panel, receiving commands through an “echoer” request to the C2 server (e.g., http[:]//37[.]139[.]129[.]145/Bunny/Echoer.php) with the user agent set as “BunnyTasks.” The malware parses the response, executing commands like “help,” “cd,” and “pwd” using _popen. The command output is then sent to the C2 server as the “&value=” parameter in a result command request (e.g., http[:]//37[.]139[.]129[.]145/Bunny/ResultCMD.php) with the user agent “BunnyShell.” Additionally, BunnyLoader sends a heartbeat request with the user agent “HeartBeat_Sender” to inform the C2 that the infected system is online.
The BunnyLoader C2 panel displays a range of tasks, encompassing the download and execution of additional malware, keylogging, credential theft, clipboard manipulation for cryptocurrency theft, and remote command execution on infected machines. The panel includes parameters for download URLs and cryptocurrency wallet addresses.
Furthermore, it offers statistics on infections, total connected/disconnected clients, active tasks, and stealer logs, with the capability to clear information. Notably, the C2 panel allows remote control of infected machines.
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:

Iranian Advance Persistent Threat Group APT34 Deployed New Malware Named Menorah
Summary:
In a recent observation, a new malware linked to the Iranian-based APT34 advanced persistent threat group was detected behind a phishing attack. APT34, a sophisticated cyberespionage group, specializes in targeting Middle Eastern organizations, engaging in spear phishing campaigns, and employing advanced techniques for network access. The malware named Menorah, was discovered in a document used during the targeted attack. Menorah was designed for cyberespionage, with capabilities to identify, read, and upload files from the infected machine, as well as download additional files or malware. The victim of this attack was likely an organization in Saudi Arabia, as indicated by pricing information in Saudi Riyal, found in the document. The malware infection process involves a malicious document dropping Menorah and establishing a scheduled task for persistence upon being opened by the victim. Menorah, written in .NET, possesses various capabilities including fingerprinting the target system, listing directories and files, uploading selected files, executing shell commands, and downloading files. Compared to a previous variant, the new SideTwist variant employed by APT34 uses additional techniques to hide its communication with the command-and-control server. The malware checks for specific arguments during execution to ensure its operations run smoothly, terminating if it detects an analytic environment. The C&C server used by the malware was inactive during analysis, but the malware was observed to be capable of executing commands, listing files, and uploading/downloading specific files based on instructions received from the server. This Menorah malware shares significant similarities with the SideTwist backdoor malware, particularly in how they fingerprint compromised systems and communicate with the C&C server.
Relevancy & Insights:
The APT34 initially utilized the SideTwist malware in 2021, and since then, it has been employed in various targets. It appears that the threat actor has made modifications to potentially evade detection. This suggests that the successful attacks using the SideTwist, now transformed into Menorah malware, are still in use by the threat actor because of its successful malicious activity.
ETLM Assessment:
APT34 aka OilRig, a threat group believed to have roots in Iran, has been directing its cyber operations towards Middle Eastern and global targets, since at least 2014. Their focus spans across diverse industries such as finance, government, energy, chemicals, and telecommunications, predominantly within the Middle East. CYFIRMA assess the group will persist in its activities, driven by the objective of advancing Iranian interests in relation to countries with strained relations. The adaptation and modification of their malware strongly indicates an intention to conduct future attacks, with a potential for further improvements in their existing arsenal of malicious tools.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
The U.S. and Japan warn of Chinese hackers’ activity
The US and Japanese security and intelligence agencies issued a Joint Cybersecurity Advisory, in which they are warning of BlackTech, an industrial espionage activity cluster operated by China. The Chinese threat actor is exploiting security loopholes in everyday networking equipment and has shown advanced abilities to modify router firmware to stay undetected to exploit routers’ domain-trust relationships. According to the joint advisory, BlackTech often hacks subsidiary networks to leverage access to more sensitive targets including government agencies, defense companies, and telecommunications firms in Japan, the U.S., and countries in East Asia. In January 2023, the U.S. and Japan signed an agreement updating their operational collaboration on cybersecurity issues and to enhance the cybersecurity of industrial control systems, while Japan is rearranging its security posture, influenced by the threat from an increasingly more assertive China.
ETLM Assessment:
The Asia–Pacific region is a host to the most prolific users of cyber as a tool of statecraft with China being by far the largest state sponsor of cyber-attacks in the world. Many of these tensions in the region and with extra-regional powers like the
U.S. have the potential to escalate into conflicts. CYFIRMA assesses any potential future conflict that is likely to begin in cyberspace. The goal of BlackTech’s collection has for the most part been the acquisition of intellectual property, as part of an ongoing massive Chinese state-drive industrial espionage programme.
North Korean hackers targeting Spanish aerospace firm
According to analysts, North Korean hackers connected to the infamous Lazarus Group have successfully targeted Spanish aerospace company with a sophisticated campaign. Employees of the unnamed company were sent messages on LinkedIn from a fake Meta recruiter and tricked into opening malicious files that purported to be coding quizzes or challenges as a part of a bogus hiring process. When opened, the files infected the victim’s device with a backdoor that would allow the hackers to exfiltrate data.
ETLM Assessment:
Pyongyang is working to develop a robust nuclear triad: land-launched stationary and mobile missiles, submarine-launched missiles, and aircraft-launched missiles, although, all vectors remain underdeveloped because of a lack of resources available to the North Korean regime. Since development is very difficult without external expertise and the country is under sanctions, they have little access to external help, the regime is increasingly turning to cyber espionage in order to gain access to dual use and military technologies, especially in the maritime and aerospace domain. This activity on the part of North Korean hackers has been on the rise and similar incidents are to be expected in the future. The technique used in the current attacks appears to be in a similar line to the Operation Dream Job campaign launched by the threat actor a year back.
Ted Pella Inc is Impacted by 8Base Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America; (www[.]tedpella[.]com), was compromised by 8Base Ransomware. Ted Pella Inc is a manufacturer and markets tools, consumables, and equipment for microscopy and nanotechnology applications. The company offers transmission and scanning electron, atomic force, confocal laser, and light microscopy products The data that was exposed has not been disclosed on the 8Base Ransomware leak site as of now. According to the leak site, the compromised data includes Invoices, Receipts, Accounting records, Personal information, Certificates, Employment agreements, a substantial volume of confidential data, Confidential agreements, Personal documents, and Additional sensitive information.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:


ETLM Assessment:
CYFIRMA’s assessment remains unchanged: we anticipate 8Base Ransomware will continue to focus their targeting American businesses and Subsidiaries that hold large amounts of PII. However, recent incidents like the attack on Ted Pella Inc., highlight
that even well-known manufacturing comp2a1nies are v©uClnYeFrIaRbMleA t2o02p3o,teAnLtLiaRl ItGaHrgTeStiAngR.E RESERVED.
Vulnerability in Arm Mali GPU Kernel Drivers
Relevancy & Insights:
The vulnerability exists due to a use-after-free error within Mali GPU Kernel Driver.
Impact :
A local application can trigger memory corruption and execute arbitrary code with elevated privileges.
Affected Products:
https[:]//developer[.]arm[.]com/Arm%20Security%20Center/Mali%20GPU%20Driver%20Vul nerabilities
Recommendations:
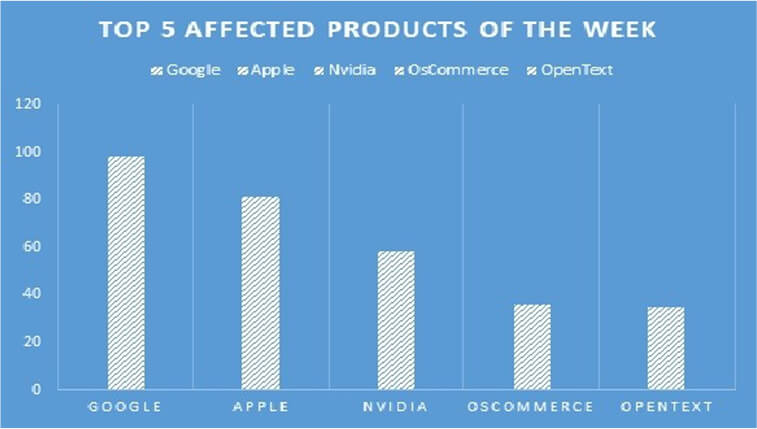
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 products most affected.
The British royal family’s website experienced disruption due to a DDoS attack
Summary:
On Sunday, the website of the British royal family suffered an outage lasting over an hour, attributed to a distributed denial-of-service attack, carried out by the hacktivist group; Killnet, which is associated with pro-Russia activities. Killnet claimed that it launched the DDoS intrusion as part of its “attack on paedophiles,” in reference to allegations of sexual abuse with a minor involving Prince Andrew; Duke of York. However, the attack also came days after King Charles III expressed support for Ukraine amid its ongoing war with Russia. The U.S. Department of Health and Human Services Health Sector Cybersecurity Coordination Center has previously identified Killnet as a group that has shown a tendency to target nations aligned with Ukraine, particularly those of NATO members. While Killnet’s connections to official Russian government entities like the Russian Federal Security Service (FSB) or the Russian Foreign Intelligence Service (SVR) remain unverified, it is prudent to regard the group as a potential threat to government and critical infrastructure entities, including healthcare.
Relevancy & Insights:
The British royal family’s website experienced disruption for over an hour due to a distributed denial-of-service (DDoS) attack conducted by the hacktivist group; Killnet. The timing of the attack is notable, occurring shortly after King Charles III expressed support for Ukraine during its ongoing conflict with Russia.
ETLM Assessment:
Based on CYFIRMA’s analysis, it is anticipated that the British royal family’s website is at risk of continued DDoS attacks, and the severity of these attacks could increase. This escalation could result in significant operational disruptions, leading to substantial reputational damage. The Royal Family’s continued support for Ukraine and the media attention surrounding the DDoS attacks could embolden the threat actors to continue their attacks.
BANK SYARIAH INDONESIA Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to BANK SYARIAH
INDONESIA, {www[.]bankbsi[.]co[.]id}. Bank Syariah Indonesia is a state-owned Islamic bank in Indonesia. The bank was officially founded on 1 February 2021 because of the merger between state-owned Sharia banks. The exposed data comprises of ID, Name, MSISDN, IMEI, Activation Code, Registration Information, User Level, Creation Date, Email, Last Access, Access Count Platform, Version, Permanent Block Status, Type, and various other confidential details.

Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial incentives are constantly searching for unprotected and weakly defended systems and software applications. Most of these malicious actors are active within hidden online communities, where they participate in discussions related to cybercrime and trade stolen digital assets. Unlike other financially motivated groups, such as ransomware or extortion gangs, who often publicize their attacks, these cybercriminals prefer to remain discreet. They gain unauthorized access and pilfer valuable information by capitalizing on unpatched systems or exploiting vulnerabilities in software or hardware. Subsequently, they advertise the stolen data on underground forums, where it is either resold or repurposed by other attackers for their own nefarious purposes.
ETLM Assessment:
Indonesia consistently maintains its position as one of the primary targets for cybercriminals on a global scale. CYFIRMA’s analysis suggests that Indonesian financial organizations along with other South Asian financial institutions with inadequate security measures and infrastructure remain exposed to an elevated risk of potential cyberattacks.
CYFIRMA Research team observed a potential data leak related to the Supreme Court of Indonesia, {www[.]mahkamahagung[.]go[.]id}. The Supreme Court of the Republic of Indonesia (Indonesian: Mahkamah Agung Republik Indonesia) is the independent judicial arm of the state. It maintains a system of courts and sits above the other courts and is the final court of appeal. It can also re-examine cases if new evidence emerges. The compromised dataset comprises of confidential and sensitive information stored in SQL format, with a combined data volume of 1.68 gigabytes.

Source: Underground forums