


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Datarip Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Datarip Ransomware.
Researchers recently identified Datarip as a new ransomware strain and linked it to the MedusaLocker family. Upon execution, it encrypts files and appends the “.datarip” extension.
Datarip also modifies the victim’s desktop wallpaper and drops a ransom note titled “RETURN_DATA.html”.
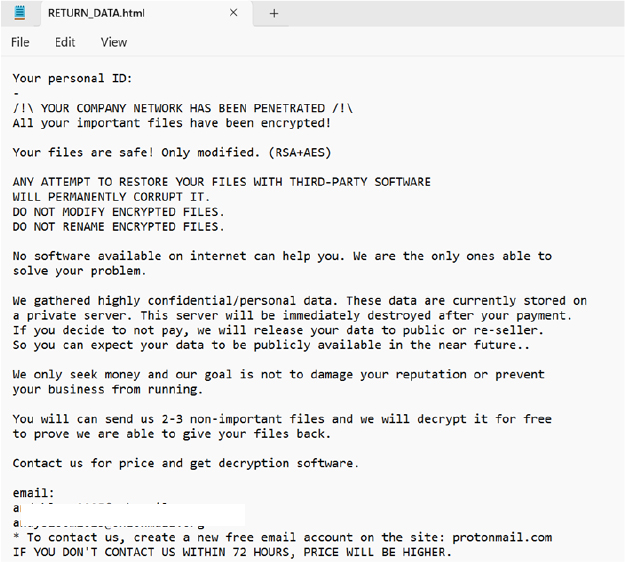
The ransom note states that files have been encrypted using a combination of RSA and AES algorithms. It clarifies that files are not deleted but altered, and warns that using third- party recovery tools or tampering with encrypted files—such as renaming or modifying them—may result in irreversible damage.
The note further claims that only the attackers possess the means to recover the data and alleges that confidential information has been exfiltrated and stored on a private server. It threatens that this stolen data will be published or sold if the ransom is not paid.
Victims are instructed to reach out to the attackers via the provided email addresses. Additionally, the note warns that failing to make contact within 72 hours will lead to an increased ransom amount.
Following are the TTPs based on the MITRE Attack Framework.
| Tactic | ID | Technique |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation |
T1055 | Process Injection |
| Privilege Escalation |
T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation |
T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation |
T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation |
T1574 | Hijack Execution Flow |
| Defense Evasion |
T1014 | Rootkit |
| Defense Evasion |
T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion |
T1055 | Process Injection |
| Defense Evasion |
T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion |
T1112 | Modify Registry |
| Defense Evasion |
T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion |
T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion |
T1202 | Indirect Command Execution |
| Defense Evasion |
T1222 | File and Directory Permissions Modification |
| Defense Evasion |
T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion |
T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion |
T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion |
T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion |
T1574 | Hijack Execution Flow |
| Credential Access |
T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Lateral Movement |
T1091 | Replication Through Removable Media |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control |
T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data shows that MedusaLocker ransomware has been actively targeting various sectors, including manufacturing, healthcare, finance, and IT services, since 2019. The emergence of Datarip ransomware, an advanced MedusaLocker variant, indicates the use of enhanced evasion techniques to broaden its impact on individuals and enterprises. Projections suggest its continued global threat to key industries, emphasizing the urgent need for strong cybersecurity measures to combat these evolving risks effectively.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Botnet
Objective: Operational Disruption, Credentials Stealing, Data Exfiltration Target Technology: Linux OS
Target Geography: Global
Active Malware of the Week
This week “PumaBot” is trending.
PumaBot
Researchers discovered a new Go-based Linux botnet called PumaBot that targets embedded Linux Internet of Things (IoT) devices. Unlike traditional botnets that scan the web for victims, PumaBot uses a pre-selected list of targets provided by its command-and- control server, making it more focused on its attacks. It attempts to gain access by brute- forcing SSH credentials and then secures its foothold by adding itself as a persistent system service.
Technical Analysis
PumaBot starts its attack by brute-forcing SSH credentials from a list of targeted IP addresses, aiming to find a way in. Once it successfully logs in, it installs itself on the device and begins spreading. To avoid detection by security systems or honeypots, it performs environment checks and looks for certain device names, such as “Pumatronix,” a manufacturer of surveillance and traffic cameras, hinting at a possible focus on IoT devices. If the environment looks safe, it collects system details like the OS, kernel version and architecture. This information—along with the victim’s IP address, port, username, and password—is then sent back to its control server in a JSON format, giving the attacker a detailed view of infected devices.
The malware communicates with its control server using a unique API key to stay connected and receive commands. It hides itself by pretending to be a legitimate system file and creates a hidden service to keep running even after the device restarts. To ensure ongoing access, it adds its own SSH keys to the device so attackers can regain entry even if the main service is removed. The malware includes a function that continuously tries to run commands named “xmrig” and “networkxm.” These commands are launched without specifying their full locations, suggesting they might be downloaded or placed somewhere on the system later. This loop uses timed delays to ensure mining operations remain active or get restarted if interrupted.
Researchers also found several related binaries that are part of a larger campaign targeting Linux systems. These binaries work in concert to maintain access, escalate privileges, and steal sensitive information:
ddaemon: A Go-based backdoor that monitors its own integrity by regularly verifying its file hash and can automatically update itself by downloading newer versions from its command-and-control server. It also fetches and installs the “networkxm” binary and runs a bash script to maintain persistence through a systemd service that starts Ddaemon every time the system boots.
networkxm: An SSH brute-force tool, this binary repeatedly downloads password lists and target IP addresses from the command server to attempt unauthorized SSH logins. Like ddaemon, it checks for updates and replaces itself if needed. It also ensures persistence by creating its own systemd service.
installx.sh: This bash script is downloaded and executed by the malware to retrieve another script called “jc.sh.” It sets up the environment and clears traces by deleting bash history.
jc.sh: This script detects the Linux distribution and locates the system’s PAM file, which controls user authentication. It then replaces this PAM file with a malicious version downloaded from a remote server. This replacement acts as a rootkit to intercept login credentials and steal user passwords. The script also modifies security settings, disables certain protections like SELinux, and restarts SSH to apply changes.
pam_unix.so_v131: The malicious PAM library installed by jc.sh is designed to capture credentials from all authenticated users, including SSH logins. It stores stolen data locally in a hidden file.
Binary “1”: This component acts as a watchdog for the malicious PAM file. It runs silently in the background, monitors the stolen credentials file, and exfiltrates this information back to the attacker’s server. It also ensures persistence through its own systemd service and deletes evidence after sending stolen data.
Together, these components form a sophisticated malware ecosystem capable of maintaining long-term control, spreading across networks, and stealing valuable credentials from compromised Linux devices.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that PumaBot is likely to evolve its capabilities beyond simply compromising devices, potentially developing new modules or features that enable it to scale its operations more effectively. Its focus on SSH brute-forcing and credential harvesting suggests it may increasingly target a wider array of systems, adapting to new technologies and vulnerabilities as they emerge. As it expands, it could quietly infiltrate environments previously considered secure, making detection and mitigation even more challenging. This potential for evolution underscores the need for continuous vigilance as attackers find new ways to blend in, bypass defenses, and maintain a persistent foothold.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Linux_PumaBot
{
meta:
description = “Rule to match on PumaBot samples” strings:
$xapikey = “X-API-KEY” ascii
$get_ips = “?count=5000” ascii
$exec_start = “ExecStart=/lib/redis” ascii
$svc_name1 = “redis.service” ascii
$svc_name2 = “mysqI.service” ascii
$uname = “uname -a” ascii
$pumatronix = “Pumatronix” ascii condition:
uint32(0) == 0x464c457f and all of (
$xapikey,
$uname,
$get_ips,
$exec_start
) and any of (
$svc_name1,
$svc_name2
) and $pumatronix
}
(Source: Surface Web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Scheduling Malware: APT41’s TOUGHPROGRESS Tactic
Summary:
Researchers have identified an advanced malware operation conducted by the threat group APT41 (HOODOO), which exploited a government website to distribute a malicious payload named TOUGHPROGRESS. The attack was initiated with spear-phishing emails directing victims to a ZIP file hosted on the compromised site. Inside the archive, a disguised LNK file (posing as a PDF) and a folder containing seven JPG images of insects were found. Among these, “6.jpg” (an encrypted payload) and “7.jpg” (a malicious DLL) facilitated the malware’s execution.
The attack followed a multi-stage process:
1. PLUSDROP – A DLL that decrypted and loaded the next stage directly into memory.
2. PLUSINJECT – Hijacked a legitimate svchost.exe process via process hollowing to deploy the final payload.
3. TOUGHPROGRESS – The primary malware module, which used Google Calendar for C2 communications.
TOUGHPROGRESS employed sophisticated evasion techniques to avoid detection, including memory-only execution that prevented disk writes and LZNT1 compression for payload obfuscation. The malware further obscured its control flow through indirect register calls, dynamic address calculations, 64-bit register overflow techniques, and a function dispatch table to complicate reverse engineering. Additionally, it stored an embedded shellcode within the “.pdata” section of its binary, which was later decompressed and executed in memory.
For command and control (C2), the malware utilized a hardcoded Google Calendar, creating and monitoring events on specific predetermined dates (2023-05-30, 2023-07-30, and 2023-07-31). Data exfiltration and command execution were conducted by encrypting communications within calendar event descriptions. The encryption process involved a static 10-byte XOR key combined with a dynamically generated 4-byte XOR key for each message, with LZNT1 compression applied prior to encryption for additional obfuscation. Beyond its C2 mechanisms, APT41 distributed the malware through free hosting services, including Cloudflare Workers, TryCloudflare, and InfinityFree, while employing URL shorteners such as lihi.cc, tinyurl.com, my5353.com, and reurl.cc to mask malicious links. All identified malicious domains associated with this campaign were proactively blocked via Safe Browsing protections to mitigate further exploitation.
Relevancy & Insights:
The discovery of Dodge Box and MoonWalk underscores APT41’s (Earth Baku) continued evolution in stealthy malware deployment and cloud-based C2 tactics. The group’s use of DLL sideloading via a legitimate Sandboxie-signed executable (taskhost.exe) mirrors past techniques seen in StealthVector campaigns, demonstrating their preference for abusing trusted software to evade detection. The loader’s role in decrypting MoonWalk—a backdoor leveraging Google Drive for C2—aligns with APT41’s history of exploiting cloud services (e.g., Google Calendar in TOUGHPROGRESS) to blend malicious traffic with legitimate activity.
This latest operation reinforces APT41’s focus on espionage, targeting high-value entities across government, technology, and critical infrastructure sectors. The shift toward fileless payloads (memory-only execution) and cloud abuse highlights their adaptability in bypassing traditional defenses. Defenders must prioritize monitoring DLL sideloading anomalies, suspicious Google API usage, and unusual process hollowing, as APT41 is likely to further refine these TTPs in future campaigns.
ETLM Assessment:
APT41, a sophisticated threat actor, has a history of targeting governments, logistics, media, and technology sectors using multi-stage malware, spear-phishing, and cloud service abuse. Past campaigns like VOLDEMORT and DUSTTRAP involved compromised websites and free hosting platforms, while the latest TOUGHPROGRESS campaign employs encrypted payloads and Google Calendar for stealthy C2 communication. Their primary motive is espionage, with a focus on long- term intelligence gathering, making government agencies, logistics firms, and tech companies key targets. Future attacks may further exploit cloud services and refine evasion techniques, requiring heightened vigilance against similar tactics.
As cloud-based C2 techniques gain traction, APT41 is likely to refine its use of legitimate platforms (e.g., Google Calendar) to evade detection. Future attacks may incorporate more advanced obfuscation methods and target emerging vulnerabilities in collaboration tools.
Strategic Recommendations
Tactical Recommendations
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1106 | Native API |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1014 | Rootkit |
| Credential Access | T1056 | Input Capture |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1012 | Query Registry |
| Command and Control | T1071 | Application Layer Protocol |
| Impact | T1496 | Resource Hijacking |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Czech Republic accuses China of cyber-attack on foreign ministry
The Czech government revealed that Chinese state-sponsored hackers had infiltrated the foreign ministry’s unclassified communications network — the latest in a string of cyber-attacks attributed to Beijing.
“China is interfering in our society — through manipulation, propaganda, and cyber- attacks,” said Czech foreign minister Jan Lipavský, noting that he had summoned the Chinese ambassador for discussions. While Prague did not disclose the specific impact of the breach, it confirmed that a new communications system has since been implemented. NATO described the incident as having caused “damage and disruption.” Authorities identified the perpetrators as APT31, a group reportedly linked to China’s Ministry of State Security. Officials said the cyber campaign had been ongoing since 2022.
The Czech Republic has taken an increasingly assertive stance in support of Taiwan, which Beijing views as part of its territory. In 2023, on his first day in office, Czech President Petr Pavel became the first elected European head of state to speak with then-Taiwanese President Tsai Ing-wen.
Both NATO and the EU condemned the cyber-attack on Prague, noting that similar incidents had affected multiple European countries since 2021. Kaja Kallas, the EU’s high representative for foreign and security policy, called the attack “a clear and unacceptable violation of international norms,” adding that Brussels has repeatedly raised concerns with Beijing and will continue to do so. NATO Secretary-General Mark Rutte expressed solidarity with the Czech Republic, describing the incident as part of a “growing pattern of malicious cyber activities stemming from China.”
ETLM Assessment:
Last year, U.S. and U.K. authorities accused the Wuhan-based hacking group APT31 of carrying out cyber-attacks targeting Capitol Hill, the British Electoral Commission, and several members of the U.K. Parliament. APT31—also known as “Judgment Panda” by cybersecurity researchers—has been linked by Western governments to China’s Ministry of State Security and is believed to be involved in extensive espionage and disinformation campaigns. Another Chinese group, APT40, reportedly operating out of Hainan province, has also been blamed for cyber intrusions into government institutions, corporations, and universities across the U.S., Canada, Europe, and the Middle East, allegedly under the direction of the Chinese state.
NATO Considers Cybersecurity to Be Included in New Spending Target
NATO has proposed expanding the scope of eligible defense-related spending to include cybersecurity, border and coastal security, and other activities, as part of a new target that would see members allocate 5% of GDP toward defense.
A new proposed framework floated before the upcoming NATO summit would dedicate 3.5% of GDP to hard defense expenditures and allow an additional 1.5% for broader defense-related outlays. These could include spending on critical infrastructure, non- military intelligence services, and cyber security or space-related initiatives.
ETLM Assessment:
The push for increased defense spending follows pressure from U.S. President Donald Trump, who earlier this year called for allies to commit 5% of GDP to defense or risk losing U.S. protection. While initially dismissed as unrealistic, the proposal has gained traction amid growing recognition that European and Canadian defense budgets must rise significantly. As of NATO’s April annual report, only 23 of the alliance’s 32 members had reached the existing 2% spending benchmark—but all are expected to meet it by this summer.
Pentagon’s IT agency and CISA to lose workforce
The Pentagon’s IT agency – the Defense Information Systems Agency (DISA) – will lose nearly 10 percent of its total staff as part of the Trump administration’s push to slash the federal workforce. U.S. Defense Secretary Pete Hegseth recently cancelled several IT consulting contracts, including one for help desk services similar to the one DISA offers. In the meanwhile, The Cybersecurity and Infrastructure Security Agency (CISA) would also lose nearly 1,000 full-time employees under the Trump administration’s proposed fiscal year 2026 budget, a stark downsizing of the government’s frontline civilian cybersecurity force even as digital threats from nation- states and cybercriminals continue to escalate.
The proposed budget includes a $45 million reduction to Cyber Defense Education and Training. It also calls for cutting 35 positions and trimming $70 million from the National Risk Management Center, which plays a key role in analyzing and mitigating cyber and physical threats to critical infrastructure. Beyond CISA, other components of the federal cybersecurity and intelligence landscape are also facing decreased funding.
ETLM Assessment:
Established in 2018 during Trump’s first term, CISA has become the federal government’s primary voice in responding to cyberattacks, election security threats, and foreign espionage. However, it has drawn criticism from the Trump administration, particularly for its efforts to debunk 2020 election fraud claims, its public stance on disinformation, and what administration officials characterize as bureaucratic overreach and politicization. The move comes at a very inopportune moment, as CYFIRMA warned in a recent report. In cyberspace, the current heightened tensions in the geopolitical sphere increase the risk of cyberattacks, as trade wars spill into digital domains. The industries the U.S. government is trying to cushion off can find themselves in the crosshairs of foreign threat actors while the U.S. administration is removing safeguards by downsizing budgets among the federal cyber defense agencies. This means private enterprises will have to take a bigger share of the heavy lifting and invest more heavily in their cyber defenses.
The Play Ransomware Impacts Media Links
Summary:
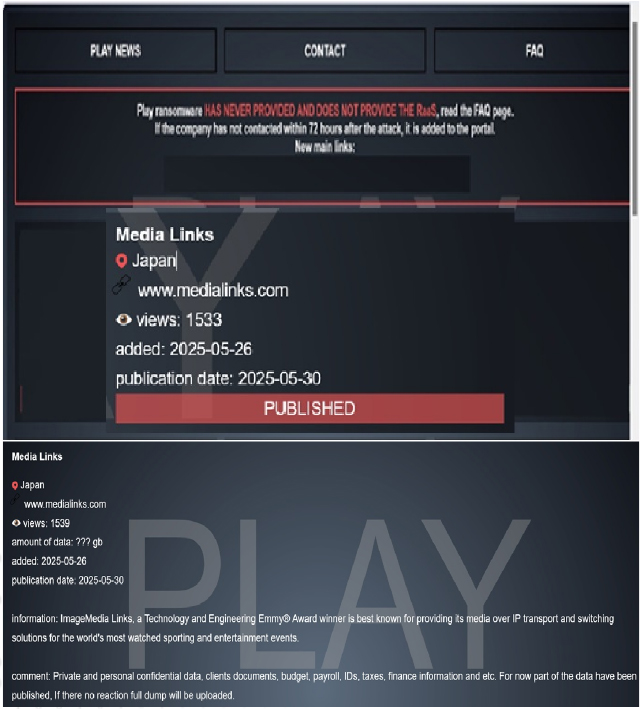
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, Media Links (www[.]medialinks[.]com), was compromised by Play Ransomware. Media Links is a global leader in IP-based media transport and switching solutions, serving broadcasters, telecom operators, and content providers worldwide. The company is renowned for pioneering technologies that enable the reliable movement of high-quality video, audio, and data across multi-service Ethernet/IP networks. The compromised data contains private and personal confidential data, clients’ documents, budget, payroll, IDs, taxes, financial information, etc.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Play Ransomware continues to evolve as a significant threat within the cybersecurity landscape, marked by its innovative tactics and recent collaborations with other threat actors. Organizations are advised to enhance their cybersecurity measures by implementing robust defenses against phishing attacks, maintaining updated security protocols, and monitoring for unusual network activity to mitigate risks associated with this evolving threat actor. Continuous vigilance is essential as ransomware groups adapt their strategies and expand their operations.
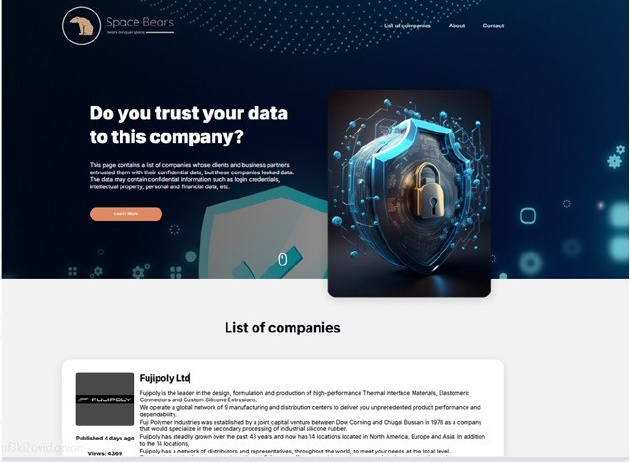
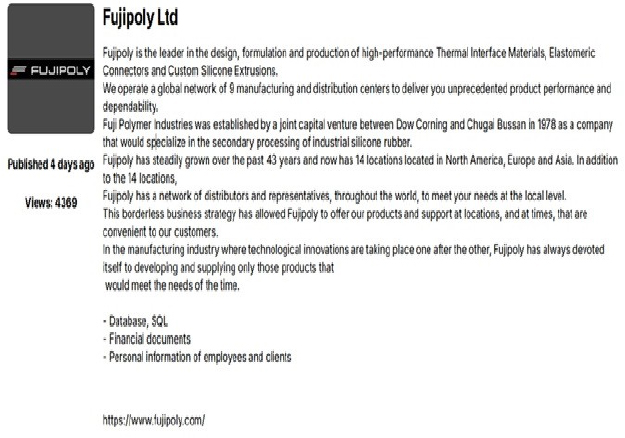
The Space Bears Ransomware Impacts Fujipoly Ltd
Summary: From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Fujipoly Ltd(https[:]//www[.]fujipoly[.]com/), was compromised by Space Bears Ransomware. Fujipoly Ltd, officially known as Fuji Polymer Industries Co., Ltd., is a Japanese company specializing in the design, formulation, and production of high-performance silicone-based materials. The compromised data includes database records, SQL financial documents, and personal information of both employees and clients.
The following screenshot was observed published on the dark web:
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Space Bears ransomware represents a significant threat in the evolving landscape of cybercrime. With its aggressive tactics, association with established ransomware operations like Phobos, and focus on double extortion, organizations are advised to bolster their cybersecurity measures to mitigate risks associated with such attacks. Continuous monitoring of this group’s activities will be essential for understanding their methods and potential impact on various sectors.
Vulnerability in Timeworks
Summary:
The vulnerability allows a remote attacker to perform directory traversal attacks.
Relevancy & Insights:
The vulnerability exists due to input validation error when processing directory traversal sequences.
Impact:
A remote attacker can send a specially crafted HTTP request and read arbitrary files on the system.
Affected Products:
https[:]//jvn[.]jp/en/jp/JVN37075430/
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
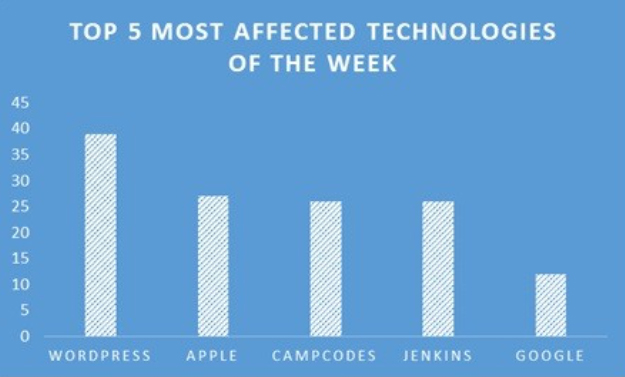
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Timeworks, an attendance and employment management system, can pose significant threats to user privacy and security. This can impact various industries globally, including manufacturing, services, healthcare, and enterprise HR operations. Ensuring the security of Timeworks is crucial for maintaining the integrity and protection of sensitive workforce data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding centralized time tracking, multi-location operations, and employment management—whether deployed via cloud (SaaS) or on- premises (package)—across different geographic regions and sectors.
Everest Ransomware attacked and published the data of the Department of Culture and Tourism Abu Dhabi
Summary:
Recently, we observed that Everest Ransomware attacked and published the data of the Department of Culture and Tourism Abu Dhabi (https://dct.gov.ae/) on its dark web website. The Department of Culture and Tourism – Abu Dhabi (DCT Abu Dhabi) is the government entity responsible for promoting and preserving the cultural heritage, arts, and tourism sector in Abu Dhabi. The department plays a key role in developing Abu Dhabi as a global cultural and tourism destination, supporting cultural initiatives, heritage preservation, and tourism growth. The ransomware attack resulted in a data breach that exposed employees’ personal information as well as sensitive internal documents. Approximately 1,500 personal records were compromised. The leaked data includes passports, visas, university diplomas, birth and marriage certificates, employment history, and other confidential materials. In total, around 12 GB of data was affected.
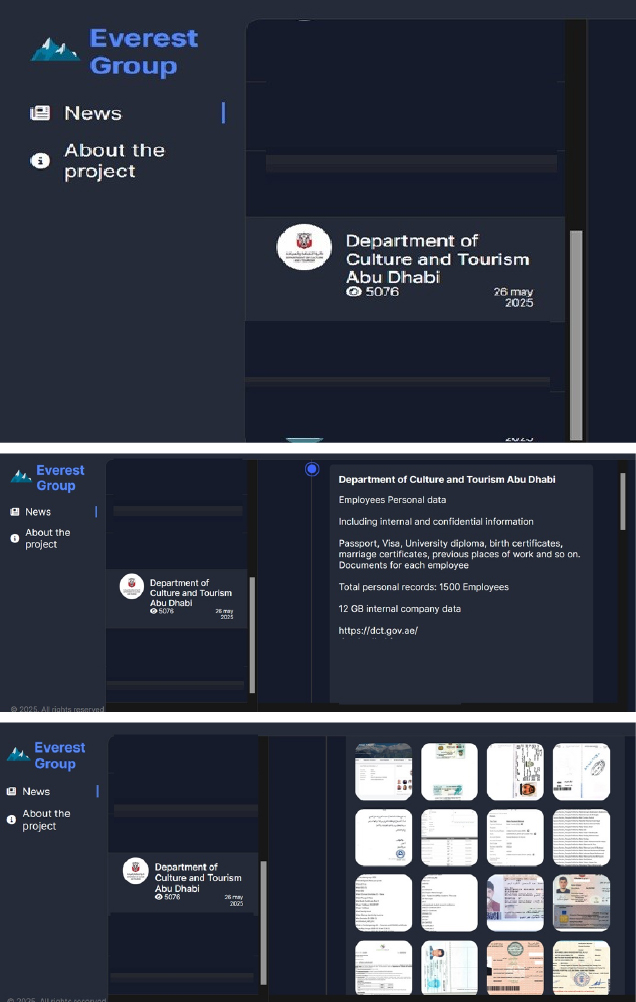
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Everest Ransomware remains a persistent and evolving threat in 2025. Despite the takedown of its leak site, the group continues to target new sectors, expand its operations as an initial access broker, and leverage data leak extortion as its primary tactic. Organizations should remain vigilant, strengthen access controls, monitor for lateral movement and Cobalt Strike activity, and ensure robust incident response capabilities to defend against Everest’s ongoing campaigns.
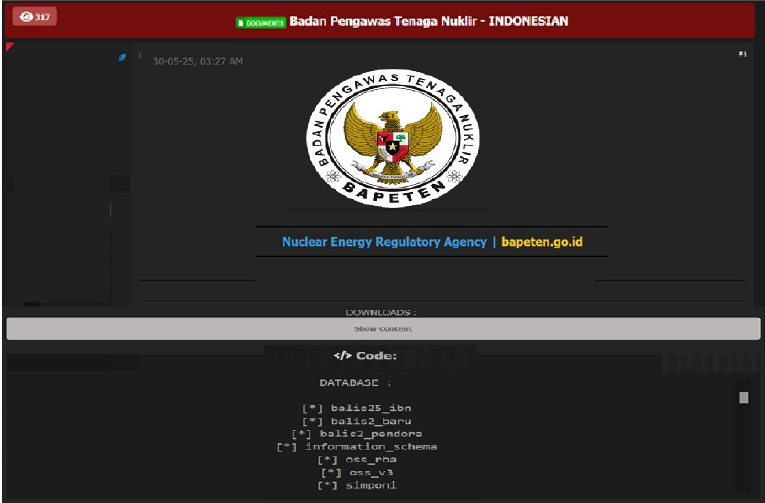
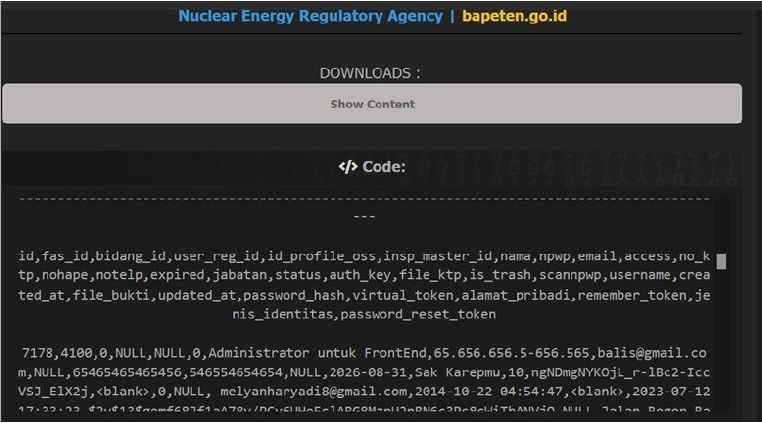
Indonesian Nuclear Energy Regulator BAPETEN Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to the Indonesian Nuclear Energy Regulator BAPETEN(https[:]//bapeten[.]go[.]id/) in an underground forum.
Indonesia’s Nuclear Energy Regulatory Agency (BAPETEN), the primary governmental body responsible for overseeing the use of nuclear energy and ensuring radioactive material safety across the nation, has allegedly suffered a major data breach. Highly sensitive information, purportedly belonging to the agency, has been exposed and circulated online, raising significant concerns given BAPETEN’s critical role in national security and public safety.
The scale of the alleged breach appears extensive. The exposed data reportedly includes: Detailed action logs Information concerning nuclear materials Various application data, including submissions related to ports, internal messages, projects, nuclear reactors, and radioactive sources Data from dosage and radiation measuring equipment Extensive user and personnel records, allegedly containing names, National Identity Card (KTP) numbers, phone numbers, email addresses, physical addresses, usernames, and hashed passwords Document management system files, including document categories, inspection reports (MIR documents), and other supporting documents Invoice and billing details Survey data collected by the agency Operational support system (OSS) tokens User data related to permit access A variety of other internal system data pertaining to inspections, material classifications, and operational tasks. This compromised information was allegedly made available for download via an online posting. The nature of the data, particularly from an institution integral to managing nuclear safety and sensitive materials, poses substantial risks. These could range from identity theft and targeted attacks against individuals to potential exploitation of operational vulnerabilities, highlighting the urgent need to address the implications of this alleged security incident.
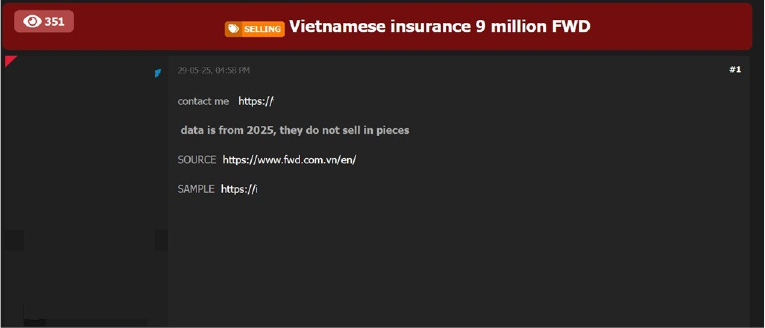
FWD Group Holdings Limited Vietnam Insurance Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data sale related to FWD Group Holdings Limited Vietnam Insurance(https[:]//www[.]fwd[.]com[.]vn/en/) in an underground forum. The alleged breach specifically points to FWD Vietnam, a significant player in the Vietnamese insurance market. FWD Group, headquartered in Hong Kong, operates across 10 markets in Asia, offering life and medical insurance, general insurance, and employee benefits. The company serves millions of customers and is recognized as a rapidly growing insurer in the region. The listing explicitly states that the data is not sold in smaller pieces. The breach has been linked to a threat actor known by the alias “Giorggios.”
The sample data, as observed, allegedly includes:
Full Name
ID Number
Date of Birth
Gender
Phone Number
Address
Company/Organization
Name
Location/Region
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “Giorggios” has been linked to multiple data breaches, with credible reports indicating their involvement in unauthorized system intrusions and the sale of stolen data on dark web forums. Their ongoing activity underscores the persistent and evolving nature of cyber threats originating from the dark web. These incidents highlight the urgent need for organizations to strengthen their cybersecurity posture through continuous monitoring, the use of threat intelligence, and the implementation of proactive defense strategies to protect critical data assets.
Recommendations: Enhance the cybersecurity posture by
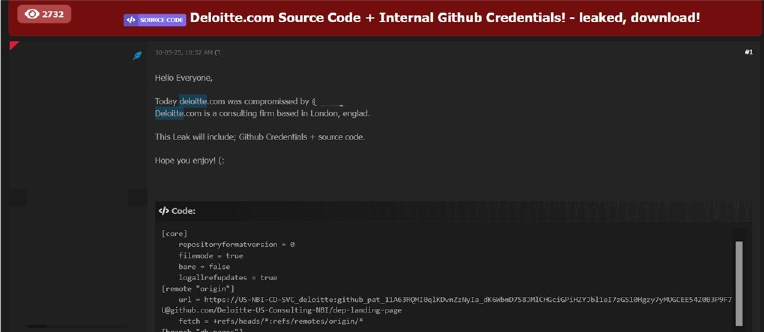
The CYFIRMA Research team observed that the Global consulting giant Deloitte has allegedly suffered a significant data breach, with internal GitHub credentials and source code reportedly leaked on an online forum. The multinational professional services network, headquartered in London, is one of the “Big Four” accounting firms, providing a wide array of services including audit, consulting, tax, and advisory services to many of the world’s largest corporations. The scale and importance of its clientele make any potential compromise of its data a serious concern.
The alleged breach appears to have originated from a post on a dark web forum, where an individual claims to have compromised Deloitte’s systems. The post included snippets of what appears to be configuration files and repository information. The full extent and validity of the breach are yet to be officially confirmed by Deloitte.
The leaked data allegedly includes:
GitHub Credentials Source Code
This incident highlights the persistent threat of cyberattacks against even the most prominent global organizations and underscores the critical importance of robust cybersecurity measures to protect sensitive corporate and client information. Further investigation will be required to determine the full scope of the alleged breach and its potential impact.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
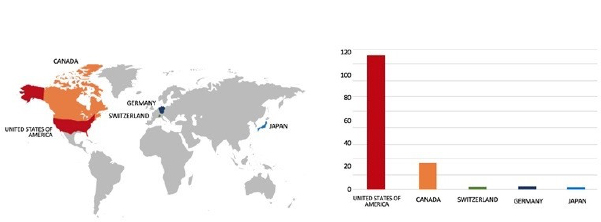
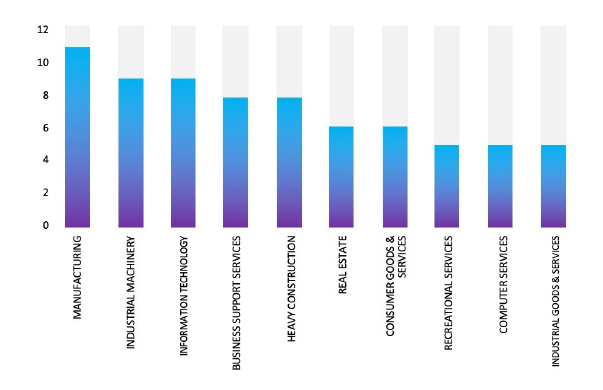
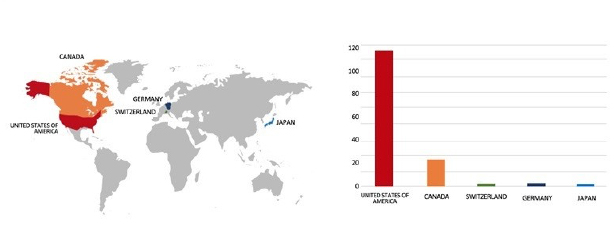
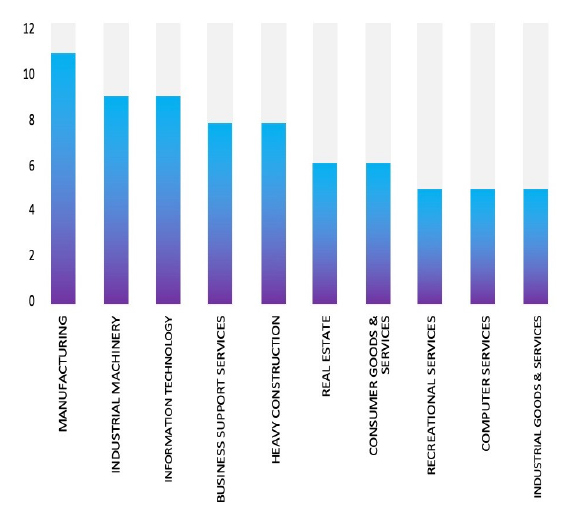
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.