



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found WeHaveSolution Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
WeHaveSolution Ransomware
Researchers have identified a new ransomware strain named WeHaveSolution. Upon infecting a system, it encrypts files, modifies the desktop wallpaper, creates a ransom note titled “READ_NOTE.html,” and appends the “.wehavesolution247” extension to affected filenames.
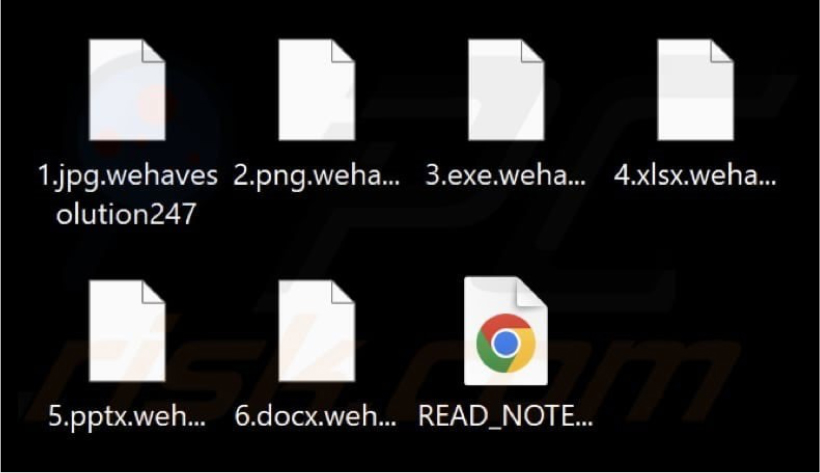
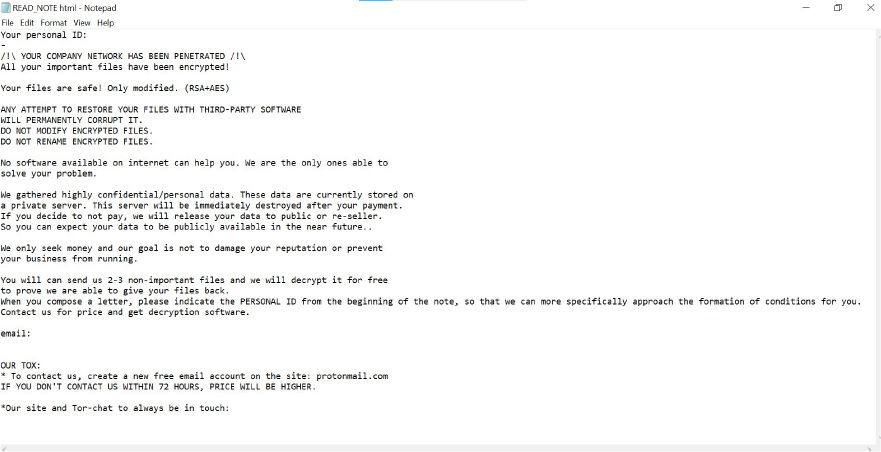
According to the ransom note, the attackers assert that they have infiltrated the company’s network and encrypted files using RSA and AES encryption. They caution against attempting to use third-party recovery tools or altering the encrypted files, as doing so could cause irreversible damage. The attackers also claim to have stolen sensitive data and threaten to leak or sell it unless a ransom is paid.
To demonstrate their ability to restore the data, they offer to decrypt 2–3 non-critical files for free. They provide a contact method through a Tor website and caution that the ransom amount will increase if they are not contacted within 72 hours.

| Tactic | ID | Technique |
| Initial Access | T1091 | Replication Through Removable Media |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| DefenseEvasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| DefenseEvasion | T1036 | Masquerading |
| DefenseEvasion | T1055 | Process Injection |
| DefenseEvasion | T1070.004 | Indicator Removal: File Deletion |
| DefenseEvasion | T1112 | Modify Registry |
| DefenseEvasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| DefenseEvasion | T1140 | Deobfuscate/Decode Files or Information |
| DefenseEvasion | T1202 | Indirect Command Execution |
| DefenseEvasion | T1222 | File and Directory Permissions Modification |
| DefenseEvasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| DefenseEvasion | T1542.003 | Pre-OS Boot: Bootkit |
| DefenseEvasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| DefenseEvasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1018 | Remote System Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614 | System Location Discovery |
| LateralMovement | T1091 | Replication Through Removable Media |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1491 | Defacement |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
According to the assessment from CYFIRMA, the ransom note associated with WeHaveSolution ransomware indicates a primary focus on targeting enterprises to maximize financial returns. This suggests that ransomware is likely to become a serious threat to developed nations, with industries such as Manufacturing, Healthcare, Hospitality, and Finance expected to be key targets due to their substantial ransom payment capacities and heavy reliance on critical data.
Furthermore, the ransomware warns that non-compliance could lead to the exposure or sale of sensitive corporate information.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface web)
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Remote Access Trojan (RAT) | Objectives: Espionage, Financial theft, Remote Access | Target Technologies: Android OS, Pix (Payment Platform), UPI (Unified Payments Interface) | Target Industries: Banks, Financial Sector | Target Geography: Brazil, India, Italy, and Mexico.
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “PixPirate” is trending.
Summary
Researchers have identified a new campaign of PixPirate, which primarily targets Brazilian banks through the Pix payment service, with nearly 70% of infections concentrated in Brazil. However, the campaign has also expanded its reach globally, affecting countries like India, Italy, and Mexico. India has become the second-most affected country, accounting for nearly 20% of all infections worldwide, despite no Indian banks being explicitly targeted. Researchers suggest that the malware’s developers are laying the groundwork for future campaigns in India, leveraging the widespread adoption of India’s Unified Payments Interface (UPI), which serves hundreds of millions of users and is regulated by the Reserve Bank of India.
PixPirate: An Evolving Threat
PixPirate, a sophisticated remote access tool (RAT) malware first identified in late 2021, operates through two key components: a downloader and a droppee application. The downloader spreads via Smishing campaigns or WhatsApp spam, masquerading as a legitimate authentication app to deceive users into downloading it. Once installed, it runs the droppee, executes commands, and facilitates the malware’s malicious activities. PixPirate’s capabilities include remote-control functionality for fraud execution, data theft, spreading through messaging platforms, SMS interception, and recording user activities. It also employs anti-removal and anti-virtual machine (anti-VM) techniques to evade detection, with its latest version introducing a method to hide its icon on the home screen, further enhancing its stealth. This evolution from a region-specific threat to a global challenge underscores PixPirate’s growing potential to exploit emerging payment ecosystems worldwide.
Attack Strategy: How PixPirate Installs and Activates Malware
The latest PixPirate campaign introduces a sophisticated new downloader variant, enhancing its ability to execute malware on victim devices. This downloader is distributed through Smishing and WhatsApp spam messages and includes a link to a YouTube tutorial, which has already garnered over 78,000 views. The video deceptively guides users into installing a malicious Android package kit (APK), disguised as a legitimate financial service app. By following the video, users unknowingly grant the necessary permissions for the malware to execute. Upon installation, the downloader requests users to install an updated version. This update, however, installs the PixPirate droppee application, the actual malware. Once installed, the malware operates invisibly on the device by hiding its icon, making it difficult for the user to detect. Despite this, the malware remains active and is capable of executing fraud, as the downloader continuously manages its execution.
To overcome the challenge of activating the invisible malware, PixPirate’s downloader plays a key role. In this new campaign, the downloader has been enhanced to run the droppee using a refined method. The downloader queries specific activity names associated with the droppee, such as “com.ticket.stage.Service” and “com.sell.allday.Service,” using the “queryIntentActivities” API. This function retrieves all activities related to the droppee, enabling the downloader to launch the malware by creating a targeted intent and invoking the “startActivity” API. By maintaining control over the execution of the droppee, PixPirate’s downloader ensures that the malware remains operational even when hidden, allowing it to conduct fraudulent activities on the victim’s device.
Exploiting WhatsApp: PixPirate’s Advanced Infection Strategy
To further enhance its infection strategy, PixPirate malware employs a sophisticated method to spread and infect devices. During installation, the downloader checks if WhatsApp is installed on the victim’s device. If not, it prompts the victim to install the WhatsApp APK, which is unusually large (nearly 100MB) compared to typical malware downloaders. Once installed, the PixPirate malware uses WhatsApp to send phishing messages from the victim’s account, spreading the infection to their contacts and groups. The new capabilities and functionality related to the WhatsApp app can include:
Additionally, PixPirate uses an overlay technique to hide its activities, making it less noticeable to the victim.
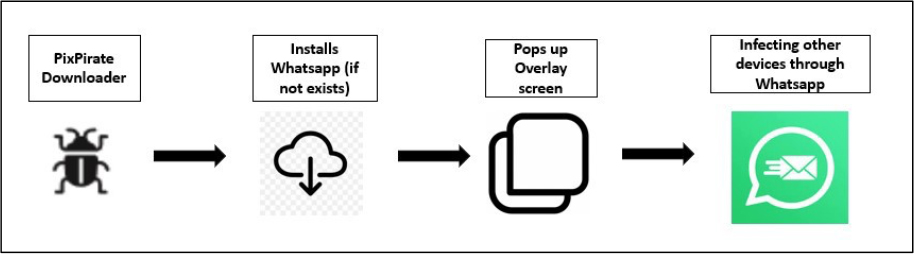
PixPirate malware uses a function that enables it to send malicious WhatsApp messages from the victim’s account. This function takes three parameters:
The malware uses the victim’s contact list to create a unique intent for each message, with the WhatsApp package name set to “com.whatsapp.” The malware then triggers the sending action by starting the corresponding activity. To send the messages, PixPirate uses the device’s Accessibility service to click on the “send” button, mimicking the behavior of a legitimate user.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that as PixPirate continues to evolve, it may expand its reach to target a broader range of global digital payment systems, including emerging platforms like UPI and Pix, increasing the risks of financial fraud and data theft. As mobile payments gain traction worldwide, organizations could face heightened threats, especially with employees using personal devices that may unknowingly facilitate the malware’s spread, compromising sensitive corporate data. The malware’s exploitation of trusted platforms like WhatsApp suggests a future rise in social engineering tactics, making employees increasingly vulnerable to phishing and fraud. As PixPirate adapts to new payment technologies and communication channels, it will likely present an escalating threat, demanding more sophisticated cybersecurity measures and defense strategies to protect both individuals and enterprises from these evolving attacks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
ANEL Strikes Again: The Resurgence of the Earth Kasha Spear-Phishing Campaign in 2024
Since June 2024, a spear-phishing campaign targeting individuals and organizations in Japan has been attributed to the threat actor Earth Kasha, which researchers classify as distinct from APT10, though potentially linked. This operation marks the reappearance of the ANEL backdoor, previously utilized by APT10 until 2018, alongside the NOOPDOOR malware, associated with Earth Kasha. The campaign’s targets include individuals linked to political organizations, research institutions, think tanks, and those involved in international relations, particularly with a focus on Japan’s national security. Unlike their 2023 operations, which mainly targeted vulnerabilities in edge devices, Earth Kasha shifted tactics by focusing on spear- phishing emails as the primary intrusion method. The spear-phishing emails in this campaign are crafted to appeal to the targeted individuals, with subjects related to Japan’s economic security and government institutions. The emails typically contain a URL pointing to a OneDrive link, where the victim is encouraged to download a malicious ZIP file. This file is the infection vector, and its contents vary depending on the target. One infection method involves a macro-enabled document, named ROAMINGMOUSE, which, once opened, executes embedded malicious components related to ANEL. Another method involves a shortcut file combined with an SFX file or PowerShell, which ultimately drops ROAMINGMOUSE and proceeds with the same infection flow. ROAMINGMOUSE is designed as a dropper for the ANEL payload, leveraging sandbox evasion techniques, such as responding to specific mouse movements and using custom Base64 encoding to hinder automated analysis. The payload is executed through WMI (Windows Management Instrumentation), bypassing typical detection methods. Once executed, the ANEL backdoor is activated using a legitimate application, which sideloads a malicious DLL. The ANEL-related components include an encrypted payload that is decrypted using AES-256, with further encryption and evasion techniques employed to hinder detection. The ANEL backdoor has been updated in this campaign, with new versions observed. The updates introduce minor fixes, remove features for evasion (such as HTTP cookie error codes), and add new commands, including one that enables the exploitation of a UAC bypass technique using the CMSTPLUA COM interface. The use of NOOPDOOR, another modular backdoor, in conjunction with ANEL suggests that Earth Kasha is leveraging multiple tools for different levels of access. NOOPDOOR is typically deployed on high-value targets, providing additional functionalities for post-exploitation activities, such as taking screenshots or executing system commands. The combination of these tools highlights the advanced and evolving nature of Earth Kasha’s operations, which involve extensive use of custom malware and sophisticated evasion techniques. This campaign reflects a shift in Earth Kasha’s targeting strategy, focusing on individuals rather than enterprises, and employing a mix of old and new tactics, tools, and procedures (TTPs). The attack methods, including spear-phishing and the use of ANEL and NOOPDOOR, are indicative of an ongoing, sophisticated threat actor looking to infiltrate specific high-value targets for espionage purposes.
Relevancy Insights:
This group is focused on telecommunications, technology, defense, and energysectors, with past attacks emphasizing intelligence gathering and data theft. One of their most significant campaigns, Cloud Hopper, involved targeting managed service providers (MSPs) to infiltrate global networks, exfiltrating sensitive data from high-value organizations worldwide. Previously, Earth Kasha relied on malware like ChinaChopperand PlugXfor remote access and persistence in compromised networks.
In 2024, Earth Kasha has pivoted to Japan, focusing on national security, political organizations, and research institutions. Their current malware arsenal includes ANELand NOOPDOOR, showing an evolution of tactics, but a consistent pattern of using spear- phishing and social engineeringfor initial compromise. These tactics are like previous campaigns, indicating a sustained emphasis on stealthy, long-term access for espionage.
The current attack shares many similarities with past operations, particularly in the group’s approach to targeting critical infrastructure and geopolitical intelligence. Despite the evolution of their tools and focus, Earth Kasha’s core goal remains the same: leveraging cyber tools to gather valuable intelligence from high-profile targets across global industries.
ETLM Assessment:
The threat actor Earth Kasha is a sophisticated cyber espionage group. Historically, Earth Kasha has focused on espionage campaigns targeting high-value political, governmental, and economic targets. In the current campaign, which started in mid-2024, Earth Kasha has shifted its focus to individuals and organizations based in Japan, with a particular emphasis on those involved in national security, political organizations, and research institutions. The group uses spear-phishing emails as the primary attack vector, leveraging social engineering tactics to lure victims into downloading malicious attachments, often tied to economic and political themes relevant to Japan. Their attacks are highly targeted, leveraging a mix of sophisticated malware, including the ANEL backdoor, NOOPDOOR, and ROAMINGMOUSE dropper, to establish initial footholds and enable continued surveillance and data exfiltration. These tools allow Earth Kasha to bypass traditional security measures, using custom malware that relies on evasion techniques, such as Base64 encoding, WMI execution, and UAC bypass. In the past, Earth Kasha also used a wider range of tools, including ChinaChopper and PlugX in older campaigns. The group’s ability to continuously evolve its tactics is evident in their use of newer malware variants and updated versions of ANEL in this campaign. The targeted technologiesinclude Windows-based systems, PowerShell, and various legitimate applications exploited for malware delivery. As the threat landscape continues to shift towards more targeted individuals and nation-state espionage, Earth Kasha is expected to increasingly refine its spear-phishing techniques and expand its malware arsenal, leveraging emerging vulnerabilities to continue its operations. Given their focus on high-profile political and defense targets, the threat remains persistent, with the potential for further targeting of countries involved in geo-politicalactivities in the Asia-Pacific region, especially those with strategic relations with Japan. Future assessments indicate the continued evolution of Earth Kasha’s TTPs, emphasizing the need for enhanced defensive postures and detection capabilitiesfor organizations and individuals in the targeted sectors.
Strategic Recommendations:
Tactical Recommendations:
Operational Recommendations:
| MITRE framework | ||
| Tactic | Technique ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1082 | System Information Discovery |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Collection | T1005 | Data from Local System |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1071.001 | Application Layer Protocol: Web Protocols |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T0826 | Loss of Availability |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
China hosts the tenth annual World Internet Conference
China’s Cyberspace Administration held the 2024 World Internet Conference (WIC) summit in Wuzhen, Zhejiang. The tenth annual conference was themed “Embracing a People-centered and AI-for-good Digital Future: Building a Community with a Shared Future in Cyberspace,” and included subforums on AI governance, global data cooperation, and the Global Development Initiative. The conference hosted technology exhibitions, bilateral ministerial meetings, and an entrepreneurs’ forum.
The conference launched an AI Committee, led by Alibaba Cloud founder Wang Jian, which will bring together over 170 domestic and international experts from academic research institutes, think tanks, and industry to collaborate on AI innovation and safety. Language in speeches at the forum echo China’s broader language on multilateral and cooperative governance. China presents a deliberate alternative to cooperation with the United States on technology standard-setting, calling on a “brighter digital future” and respect for individual countries’ policy objectives.
ETLM Assessment:
China has been accelerating efforts to build its influence in technology governance in recent years, particularly pushing cross-border data flow and establishing collaborations with countries in the Global South. Just this week, while Xi and Brazilian President Lula met and elevated ties, China launched an Open Science initiative with South Africa, the African Union, and Brazil. The language of “respect for individual countries’ policy objectives” aims at steering the internet from one open world network into a series of fragmented “sealed-off national internets” akin to the system in China, where the government pushes its own population behind the so-called “great firewall”. China is trying to export its model both to undermine the current geopolitical order and to gain business opportunities for its companies, which build the great firewall and would be eager to export it to other countries.
Europe’s critical infrastructure is becoming dangerously vulnerable
A former NATO secretary-general Anders Fogh Rasmussen has issued an open letter, warning Europe of its critical infrastructure vulnerability. Rasmussen writes:
Europe’s subsea cables network is a grave cause for concern. Former Russian president Dmitry Medvedev has openly threatened an attack in response to support for Ukraine. These cables carry around 98 percent of the world’s internet traffic, and three EU countries are fully reliant on them for their connectivity. Without these cables, our phones, cars, televisions, and even fridges, will cease to function effectively. The Russian general staff’s main directorate for deep sea research has been linked to sabotage threats to undersea cables. Russian submarine activity to chart the locations of these highly vulnerable cables has also increased significantly, including off the coast of Ireland.
ETLM Assessment
The essay largely echoes our previous assessment from two reports published this spring, one dealing with undersea cables and one titled Threat to Offshore Infrastructure in a Maritime-Centric Century, in which CYFIRMA analysts conclude: The most important evolving threat to the electric grid is associated with cybersecurity and physical security. The power grid in the US, and more so in Europe, is experiencing a transformation as the world shifts to sustainable energy: this transformation, however, is introducing new vulnerabilities to the system as offshore infrastructure is susceptible to physical and cybernetic attacks. Both the US and EU governments have aimed to bolster collaboration between critical infrastructure owners and operators as well as sector risk management agencies, but the hasty nature of the grid transformation will likely leave many openings for sophisticated cyber attackers for years to come.
The Hunters International Ransomware Impacts CK Power Public Manufacturing
Summary
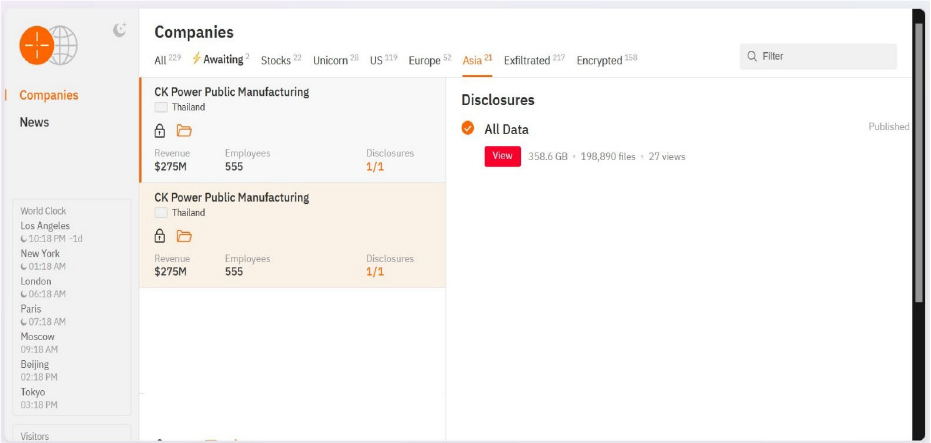
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand; CK Power Public Manufacturing (www[.]ckpower[.]co[.]th), was compromised by Hunters International Ransomware. CK Power Public Company Limited (CKP) is a leading electricity producer in Thailand specializing in renewable energy. CKP operates power generation projects across multiple sectors, including hydroelectric, solar, and thermal power. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database. The scale of the data exposure measures approximately 358.6 GB, comprising a total of 1,98,890 discrete files.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Hunters International ransomware represents a significant threat within the ransomware landscape due to its sophisticated tactics and focus on double extortion strategies. Organizations are advised to enhance their cybersecurity measures by implementing robust backup solutions, conducting regular employee training on phishing awareness, and maintaining updated security protocols to mitigate risks associated with this evolving threat actor. Continuous monitoring of Hunters International’s activities will be essential for understanding its impact on global cybersecurity efforts.
The Killsec Ransomware Impacts GajiCermat
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; GajiCermat (www[.]gajicermat[.]com), was compromised by KillSec Ransomware. GajiCermat, operated by PT GajiCermat Mandiri Digital Indonesia, is a cloud-based platform offering HR and payroll management solutions. It is designed to streamline administrative tasks, such as payroll processing, attendance tracking, and employee management for businesses of various sizes. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
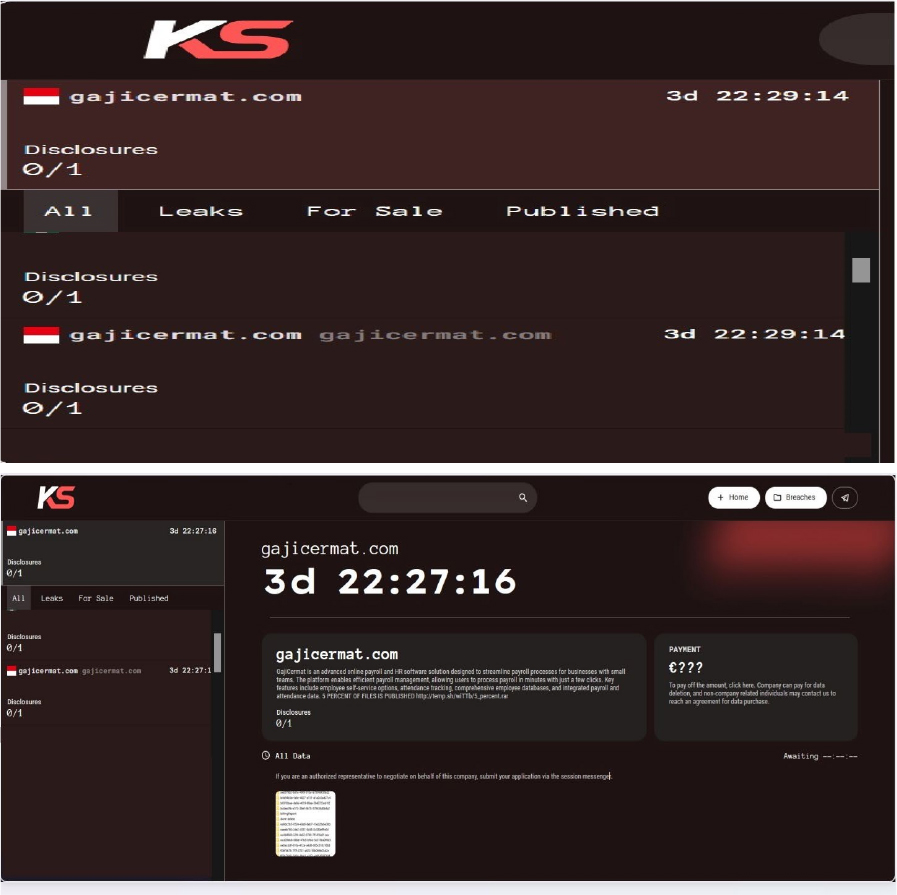
Relevancy & Insights:

ETLM Assessment:
The emergence and evolution of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
Vulnerability in SimpleSAMLphp
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user-supplied XML input in saml2/src/SAML2/DOMDocumentFactory.php when parsing SAML messages. A remote attacker can pass a specially crafted XML code to the affected application and view the contents of arbitrary files on the system or initiate requests to external systems.
Impact: Successful exploitation of the vulnerability may allow an attacker to view the contents of arbitrary files on the server or perform network scanning of internal and external infrastructure.
Affected Products: https[:]//github[.]com/simplesamlphp/xml- common/security/advisories/GHSA-2×65-fpch-2fcm
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
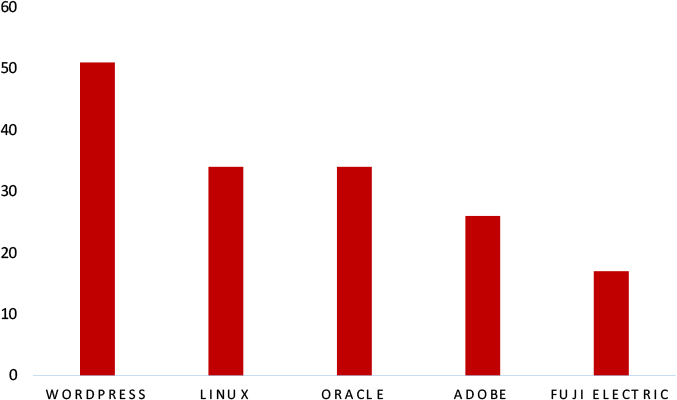
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in SimpleSAMLphp can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of SimpleSAMLphp is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding authentication processes and identity management in PHP applications across different geographic regions and sectors.
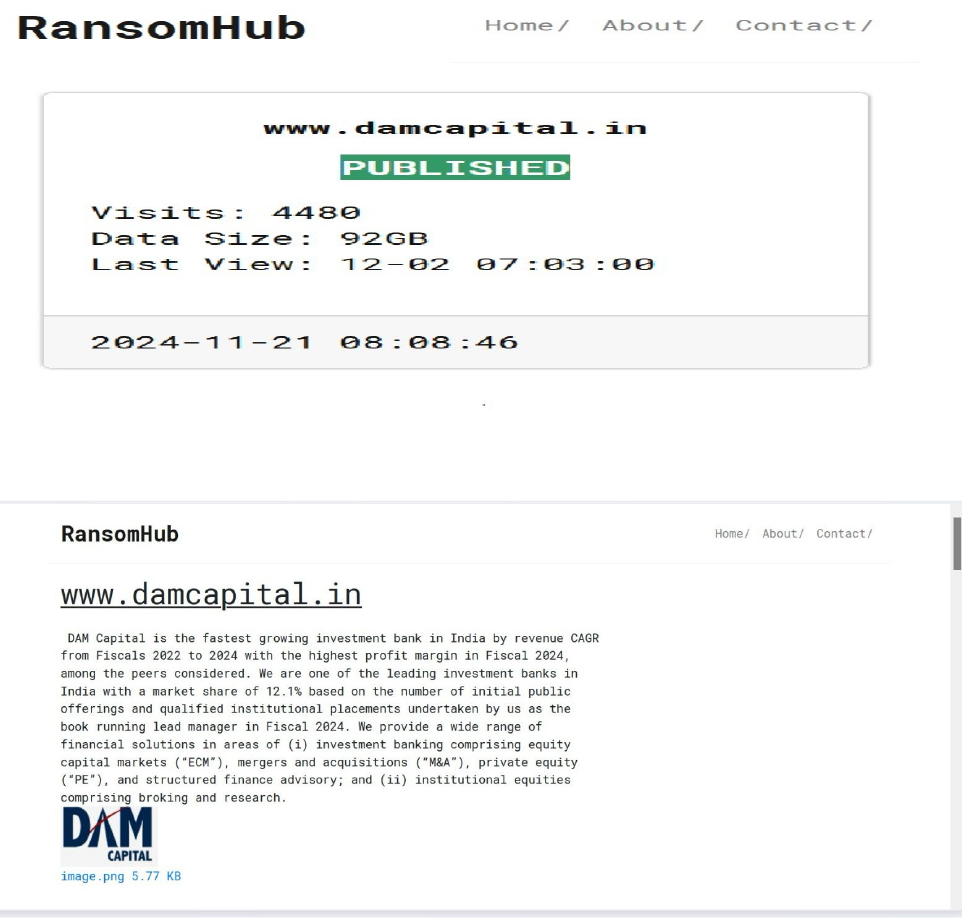
RansomHub Ransomware Attacked and Published the Data of DAM Capital Advisors Limited
Summary
Recently, we observed that Ransomhub Ransomware attacked and published the data of DAM Capital Advisors Limited (www[.]damcapital[.]in) on its dark web website. Capital Advisors Limited is a prominent investment bank in India, focusing on financial advisory services in sectors such as capital markets, equity and debt placement, and corporate finance. The company operates as a SEBI-registered entity, offering services including merchant banking, research analysis, and brokerage activities. The data leak, following the ransomware attack, encompasses sensitive and confidential records, originating from the organizational database.
The scale of the data exposure measures approximately 92 GB.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, RansomHub’s rapid ascent in the ransomware ecosystem poses significant challenges for organizations across various sectors. Its sophisticated tactics, aggressive recruitment strategies, and focus on double extortion highlight the evolving nature of cyber threats. Organizations are urged to enhance their cybersecurity measures, including robust incident response plans and employee training on recognizing phishing attempts, to mitigate the risks associated with this emerging threat actor. Continuous monitoring of RansomHub’s activities will be essential for understanding its impact on global cybersecurity efforts.
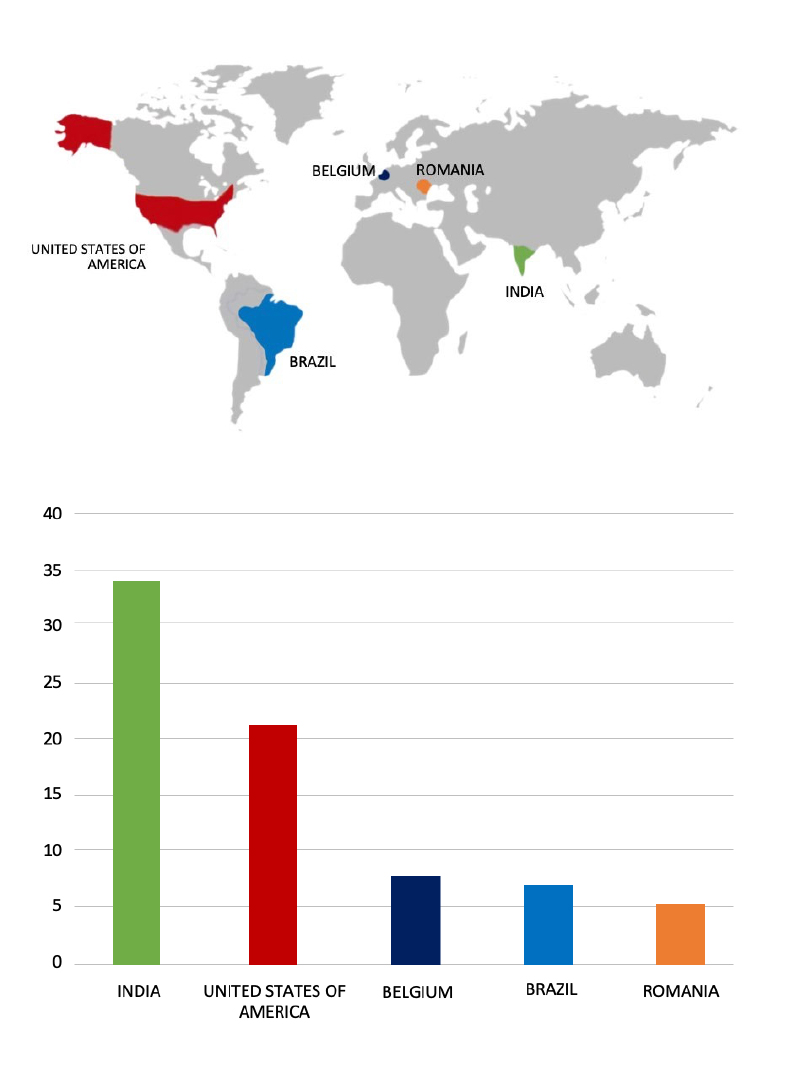
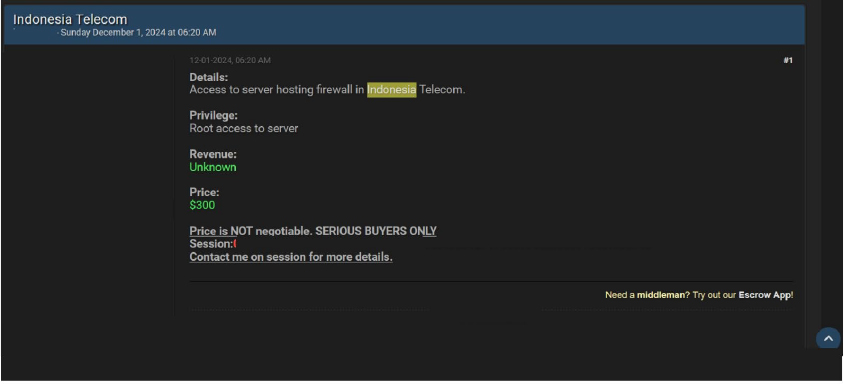
Indonesia Telecom Access Advertised on a Leak Site
Summary: The CYFIRMA Research team observed an Access sale related to Indonesia Telecom in an underground forum. The details of the sale involve access to server hosting with a firewall in Indonesia Telecom. The offering includes root access to the server, granting full administrative privileges. The access is being sold by a threat actor identified as “Miyako” for a price of $300.
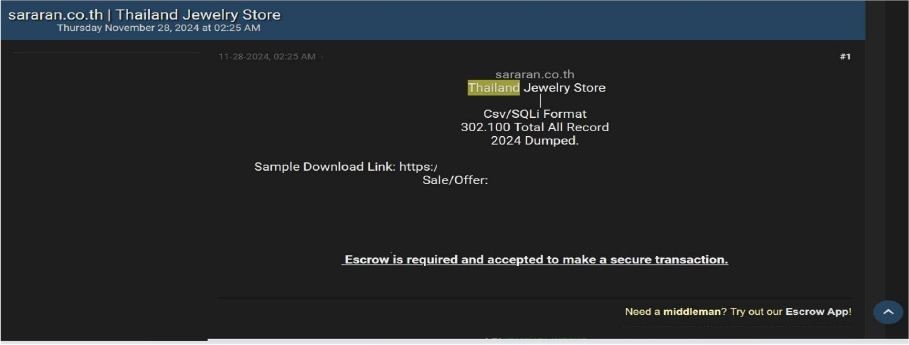
Sararan Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a data leak related to Sararan(www[.]sararan[.]co[.]th) in an underground forum. Sararan is a Jewelry store based in Thailand that specializes in handmade fashion accessories. The leaked data consists of a total of 3,02,100 records in CSV/SQL format. The data breach has been linked to a threat actor known as “NanC.”
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data.
Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor “NanC” poses a significant cybersecurity risk, and organizations are urged to enhance their security protocols to counteract this emerging threat. This includes implementing regular software updates, conducting employee training to recognize phishing attempts, and maintaining robust defense systems. To mitigate the risks associated with NanC and similar groups, continuous surveillance and sharing of cybersecurity intelligence are essential. Collaborative efforts will be key to understanding and addressing the evolving tactics employed by these threat actors.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed a data leak related to Entrena Virtua(https[:]//www[.]entrenavirtual[.]es) in an underground forum. Entrena Virtual is a fitness center that provides gym classes and personal training services. The compromised data includes the following details: full name, username, last activity date, registration information, email address, order history, total expense, PMV (potentially a metric for monetary value), country, city, region, and postal code.
The breach has been linked to a threat actor identified as “888.”
The CYFIRMA Research team observed a data and access sale related to EazyDiner (www[.]eazydiner[.]com) in an underground forum. EazyDiner, a prominent platform for restaurant reservations and payments, providing access to over 25,000 restaurants in India and Dubai, has reportedly experienced a data breach. The breach is attributed to a threat actor identified as “0xy0um0m.”
The compromised data includes:
Additionally, the access for sale includes a base system and access to AWS S3 storage. The threat actor is asking for a price of $13,500 for this package (base + AWS S3 access).
ETLM Assessment
The threat actor group “888” has gained notoriety in underground forums, emerging as a significant force in cybercrime, primarily motivated by financial gains. This group has already targeted a wide range of industries, including government, industrial conglomerates, retail, staffing, business consulting, banking, e-commerce, and utilities. Their diverse targeting patterns suggest that they plan to broaden their scope and potentially expand their attacks to additional industries worldwide in the future.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
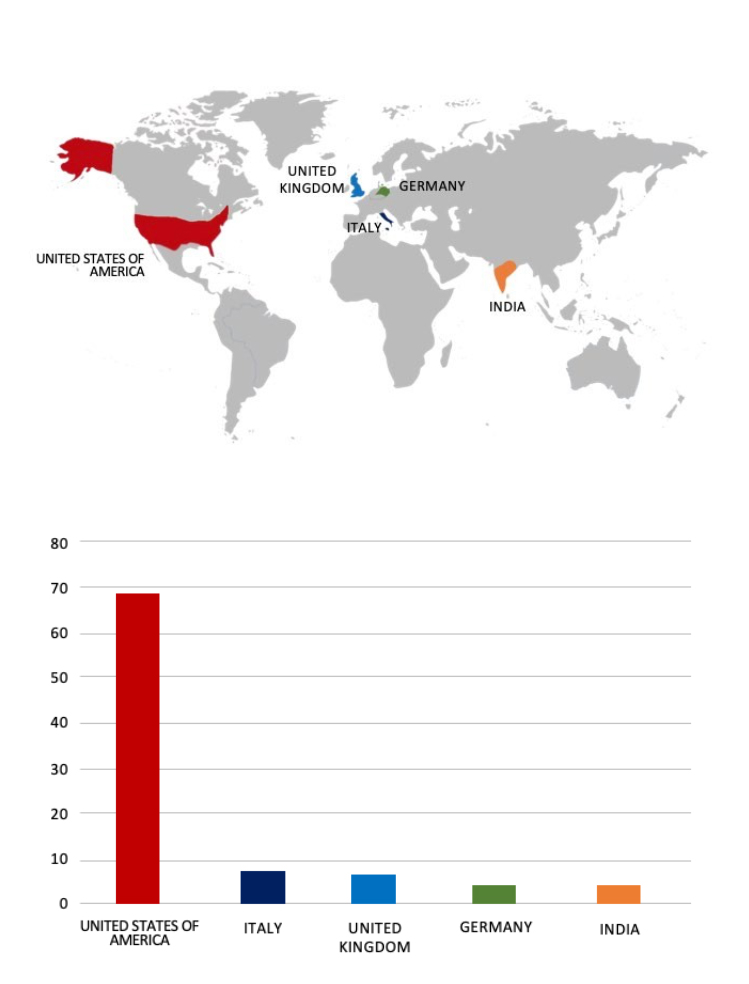
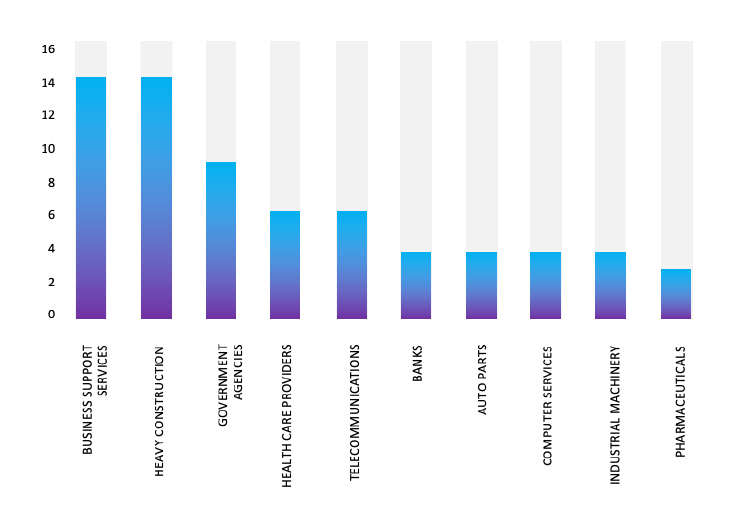
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.