


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction:
CYFIRMA Research and Advisory Team has found NEZHA Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
NEZHA Ransomware:
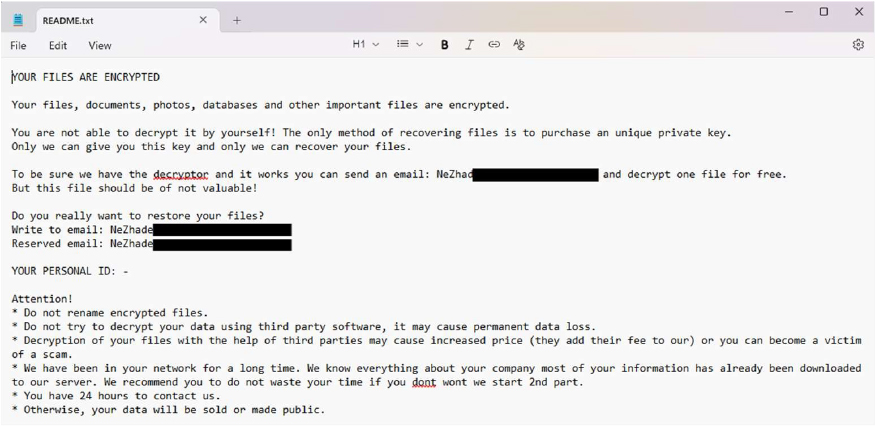
Researchers have discovered a new ransomware strain called NEZHA. This ransomware Encrypts victims’ files, renaming them with the .NEZHA extension. Infected systems are left with a ransom note titled README.TXT.

The ransom note states that all files have been encrypted and can only be restored with the attackers’ private key, obtainable by contacting them via the provided emails. Victims are offered free decryption of one non-valuable file as proof. The note warns against using third-party tools or renaming files, claiming this could cause permanent loss. Attackers assert they have had long-term access to the victim’s network, exfiltrated sensitive data, and threaten to leak or sell it if no contact is made within 24 hours.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that the NEZHA ransomware group is in its early phase but demonstrates clear indicators of rapid evolution. Evidence from observed artifacts (.NEZHA extension, README.TXT ransom note), confirmed IOCs, and TTPs such as WMI execution, credential theft, and extensive system discovery strongly support this trajectory. With these capabilities already in play, it is highly likely that NEZHA will expand into double or triple extortion, adopt dedicated leak sites, and transition toward a Ransomware-as-a-Service model, positioning it as a scalable and persistent global threat.
Sigma rule:
title: Suspicious desktop.ini Action tags:
– attack.persistence
– attack.t1547.009 logsource:
product: windows category: file_event
detection: selection:
TargetFilename|endswith: ‘\desktop.ini’ filter_generic:
Image|startswith:
– ‘C:\Windows\’
– ‘C:\Program Files\’
– ‘C:\Program Files (x86)\’ filter_jetbrains:
Image|endswith: ‘\AppData\Local\JetBrains\Toolbox\bin\7z.exe’ TargetFilename|contains: ‘\JetBrains\apps\’
filter_upgrade:
TargetFilename|startswith: ‘C:\$WINDOWS.~BT\NewOS\’ condition: selection and not 1 of filter_*
falsepositives:
– Operations performed through Windows SCCM or equivalent
– Read only access list authority level: medium
Source: Surface Web
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan | Objectives: Credential Theft, Cryptocurrency Theft, Device Control, Data Exfiltration |Target Technology: Android OS | Target Industry: Financial Services, Cryptocurrency Platforms | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Brokewell” is trending.
Overview of Brokewell Malware
Researchers identified a new wave of malicious activity within Meta’s advertising system, where cybercriminals are adapting their tactics to reach a wider pool of victims. After months of targeting Windows desktop users with fake ads for counterfeit trading and cryptocurrency platforms, the focus has now shifted to Android users worldwide. The latest campaign involves deceptive Facebook ads offering a free premium version of the TradingView app, which in reality delivers an upgraded variant of the Brokewell malware designed to steal cryptocurrency. This discovery highlights how attackers are refining their strategies, hiding behind trusted financial tools, and leveraging the growing popularity of mobile trading apps to maximize their gains.
Attack Method
The attack began with deceptive Facebook ads carrying TradingView’s branding, sometimes paired with unusual visuals such as a Labubu character, to capture attention. While desktop users clicking these ads were shown harmless content, Android users were redirected to a fraudulent website mimicking TradingView’s official page. From there, victims were tricked into downloading an initial malicious app, known as a dropper, disguised as a free premium app. The dropper decrypted and installed the actual malicious payload — an evolved form of the Brokewell malware.
Upon the successful installation of the actual malware, to avoid being detected, the dropper gets itself uninstalled. The fake app had already requested powerful permissions, including accessibility access, and attempted to obtain the user’s lock screen PIN, granting attackers further control and unauthorized access. To maximize its reach, the malware also requested permissions in multiple languages — including English, Spanish, Portuguese, German, French, Italian, Turkish, and Finnish — reflecting its design for global campaigns. The malware was designed to conceal its activities, target cryptocurrency wallets, and communicate securely with attackers over TOR, giving them full control over infected devices and access to sensitive information. Once granted the necessary permissions, Brokewell is capable of the following actions:
Following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
| Initial Access | T1456 | Drive-By Compromise |
| Persistence | T1624.001 | Event Triggered Execution: Broadcast Receivers |
| Persistence | T1541 | Foreground Persistence |
| Privilege Escalation | T1626 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1628 | Hide Artifacts |
| Defense Evasion | T1628.001 | Hide Artifacts: Suppress Application Icon |
| Defense Evasion | T1655 | Masquerading |
| Defense Evasion | T1516 | Input Injection |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Defense Evasion | T1406.002 | Obfuscated Files or Information: Software Packing |
| Credential Access | T1517 | Access Notifications |
| Credential Access | T1414 | Clipboard Data |
| Credential Access | T1417 | Input Capture |
| Credential Access | T1417.001 | Input Capture: Keylogging |
| Credential Access | T1417.002 | Input Capture: GUI Input Capture |
| Credential Access | T1634 | Credentials from Password Store |
| Discovery | T1420 | File and Directory Discovery |
| Discovery | T1430 | Location Tracking |
| Discovery | T1418 | Software Discovery |
| Discovery | T1426 | System Information Discovery |
| Collection | T1517 | Access Notifications |
| Collection | T1513 | Screen Capture |
| Collection | T1429 | Audio Capture |
| Collection | T1616 | Call Control |
| Collection | T1414 | Clipboard Data |
| Collection | T1417 | Input Capture |
| Collection | T1417.001 | Input Capture: Keylogging |
| Collection | T1417.002 | Input Capture: GUI Input Capture |
| Collection | T1430 | Location Tracking |
| Collection | T1636.002 | Protected User Data: Call Log |
| Collection | T1409 | Stored Application Data |
| Command & Control | T1437 | Application Layer Protocol |
| Exfiltration | T1646 | Exfiltration Over C2 Channel |
| Impact | T1616 | Call Control |
| Impact | T1582 | SMS Control |
| Impact | T1516 | Input Injection |
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that in the future, Brokewell-style campaigns will blur the line between personal and professional risks, as attackers disguise malware behind trusted brands and lure employees through seemingly legitimate tools. Infections on devices could quietly serve as gateways into corporate environments, expanding the threat surface for organizations worldwide. Employees may find it increasingly difficult to distinguish authentic apps and ads from malicious ones, leading to growing distrust in digital platforms and disruptions to workplace efficiency. With its globally adaptable design, such malware could enable simultaneous large-scale campaigns across regions, where even a single compromised employee device may trigger systemic risks affecting entire organizational ecosystems.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Brokewell_Indicators
{
meta:
description = “Detects Brokewell malware indicators” author = “CYFIRMA”
malware_family = “Brokewell” strings:
// MD5 File Hashes
$md5_1 = “788cb1965585f5d7b11a0ca35d3346cc”
$md5_2 = “58d6ff96c4ca734cd7dfacc235e105bd”
// SHA256 File Hashes
$sha256_1 = “39669a3663829b380c7a776857021ac8a325cf6c0f709dd502f5f0a0945da953”
$sha256_2 = “6dd93a18b00db0f16042cd95ed45227aca0f850844e1cb9923e83df405757660”
$sha256_3 = “78b3db9b68a4b62c6c4fffdcf0d0125aca464dbb4a6ef3526ac7c7ea1cfe88e4”
$sha256_4 = “66b5cf0fe3eb2506ce38701acabc242323e1cdbdb2b0a96909936477e03e0cf3”
// Domains
$domain_1 = “new-tw-view.online”
$domain_2 = “tradiwiw.online” condition:
any of ($domain*) or any of ($md5*) or any of ($sha256*)
}
STRATEGIC:
MANAGEMENT:
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT37: An Evolving Cyber Threat from North Korea
About the Threat Actor
Reaper (APT37) is a suspected North Korean cyber espionage group active since 2012, known for its advanced malware development and sophisticated tactics, techniques, and procedures (TTPs). Initially targeting South Korea, the threat group has expanded its attack surface footprints to other geographies. Notable campaigns include Operation Daybreak, Erebus, Golden Time, FreeMilk, Are You Happy•, and Evil New Year.
Additionally, malware families and tools, such as Konni, Nokki, DogCall, and CarrotBat, have been associated with the group’s operations, further demonstrating its technical capability and adaptability. The group has been linked to attacks on academic and strategic institutions, including a Japanese entity associated with a UN human rights project. Reaper’s activities align closely with North Korean state objectives, making it a persistent and evolving threat.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2018-4878 | Adobe Flash Player | 9.8 | Link |
| CVE-2022-41128 | Windows Scripting Languages | 8.8 | – |
| CVE-2024-38178 | Scripting Engine Memory | 7.5 | – |
| CVE-2020-1380 | Internet Explorer | 8.8 | Link |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1559.002 | Inter-Process Communication: Dynamic Data Exchange |
| Execution | T1106 | Native API |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control |
| Defense Evasion | T1036.001 | Masquerading: Invalid Code Signature |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.003 | Obfuscated Files or Information: Steganography |
| Defense Evasion | T1055 | Process Injection |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Discovery | T1120 | Peripheral Device Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Collection | T1123 | Audio Capture |
| Collection | T1005 | Data from Local System |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1529 | System Shutdown/Reboot |
Latest Developments Observed
The threat actor is suspected of conducting a campaign, Operation HanKook Phantom, characterized by highly tailored spear-phishing attacks utilizing malicious LNK loaders, fileless PowerShell execution, and covert data exfiltration techniques. The campaign appears to primarily target government entities, research institutions, and academic organizations in South Korea, with the likely objective of intelligence collection and long-term espionage.
ETLM Insights
APT37 demonstrates increasingly sophisticated and evolving tactics, techniques, and procedures (TTPs), including spear-phishing campaigns, exploitation of software vulnerabilities, and advanced malware development capabilities. The group has expanded its digital footprint beyond its traditional regions of operation, aligning its activities with state objectives and supporting government priorities. Its targeting scope extends across a broader technology stack, spanning Windows, Android, web browsers, and cloud infrastructure, underscoring its focus on intelligence collection and long-term espionage. It is anticipated that future campaigns by the threat group are likely to employ cross-platform malware, AI-driven spear-phishing, and large-scale strategic web compromises.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule APT37_Indicators
{
meta:
description = “Detects indicators related to APT37 (ScarCruft) including CVEs, IPs, and domains”
author = “CYFIRMA” date = “2025-09-02”
threat_actor = “APT37 / ScarCruft / TA-RedAnt” strings:
// Known CVE strings often referenced in attack artifacts or logs
$cve1 = “CVE-2018-4878”
$cve2 = “CVE-2022-41128”
$cve3 = “CVE-2024-38178”
$cve4 = “CVE-2020-1380”
// Domains linked to APT37 infrastructure
$domain1 = “st0746.net”
$domain2 = “crowdon.info”
$domain3 = “joinupvts.org”
$domain4 = “seoulhobi.biz”
// IP addresses associated with malicious activity
$ip1 = “209.85.147.147”
$ip2 = “209.85.147.106”
$ip3 = “209.85.147.99”
$ip4 = “209.85.146.147”
$ip5 = “209.85.146.106”
condition:
any of ($cve*) or any of ($domain*) or any of ($ip*)
}
Recommendations Strategic
Management
Tactical
Chinese cyberespionage targets diplomats in Southeast Asia
Earlier this year, a cyber-espionage campaign targeted Southeast Asian diplomats, likely supporting China’s strategic interests, according to researchers. The attacks, attributed to the China-linked UNC6384 group, used social engineering and malware disguised as software updates. About two dozen victims, potentially including government officials or contractors, downloaded the malware, while China’s Ministry of Foreign Affairs denied awareness of the issue.
ETLM Assessment:
The findings heighten US-China cybersecurity tensions, following previous reports of Chinese state-sponsored hackers exploiting software flaws and Beijing’s claims of US cyberattacks on Chinese military firms. The hackers breached Wi-Fi networks to trick diplomats into downloading SOGU.SEC malware, disguised as Adobe plug-ins, which were installed in device memory to evade detection. According to the researchers, sensitive diplomatic documents were likely accessible, though the extent of data loss remains unclear. This cyber-espionage campaign, targeting Southeast Asian diplomats with social engineering and malware to access sensitive documents, exemplifies standard government-backed tactics to covertly gather strategic intelligence, which has been heavily utilized by China in recent years, with many more similar campaigns likely underway at the same time.
Chinese Salt Typhoon APT hacked more than 80 countries
A years-long cyber-espionage campaign linked to Beijing, initially thought to target U.S. telecoms and Donald Trump’s phone calls, impacted over 80 countries, compromising millions of call records and potentially tracking U.S. citizens’ movements globally, according to the FBI cyber unit. The “Salt Typhoon” operation, active since at least 2019 but uncovered last year, accessed sensitive U.S. customer data, private communications, law-enforcement systems used for court-authorized wiretapping, and technical network details, raising significant national security concerns. Described as a highly damaging operation, it breached major U.S. carriers like Verizon, AT&T, and T-Mobile, with varying degrees of success, and targeted networks globally for intelligence aggregation beyond typical espionage norms. Beijing denies involvement, claiming the U.S. lacks evidence and accusing it of fabricating claims. The FBI, alongside international partners, has contained much of the activity, issuing a memo with technical details to help companies detect the hackers, who exploited known software and device vulnerabilities, including routers.
ETLM Assessment:
U.S. officials describe the breach as a damaging and well-executed espionage operation by Beijing, and investigators now believe the activity was broader and more indiscriminate than previously understood, and beyond what countries usually understand to be espionage, Leatherman said. The activity potentially allowed Chinese spies to use cell phone geolocation data to track Americans’ movements, including outside the country. One of the facts that points to a large-scale coordinated operation is that the hackers got into networks by exploiting a range of known vulnerabilities in software and devices connected to the networks, including routers. China is deploying significant resources to conduct sophisticated, global cyber-espionage campaigns of which Salt Typhoon is just one example.
Qilin Ransomware Impacts DAOR E&C Co., Ltd
Summary:
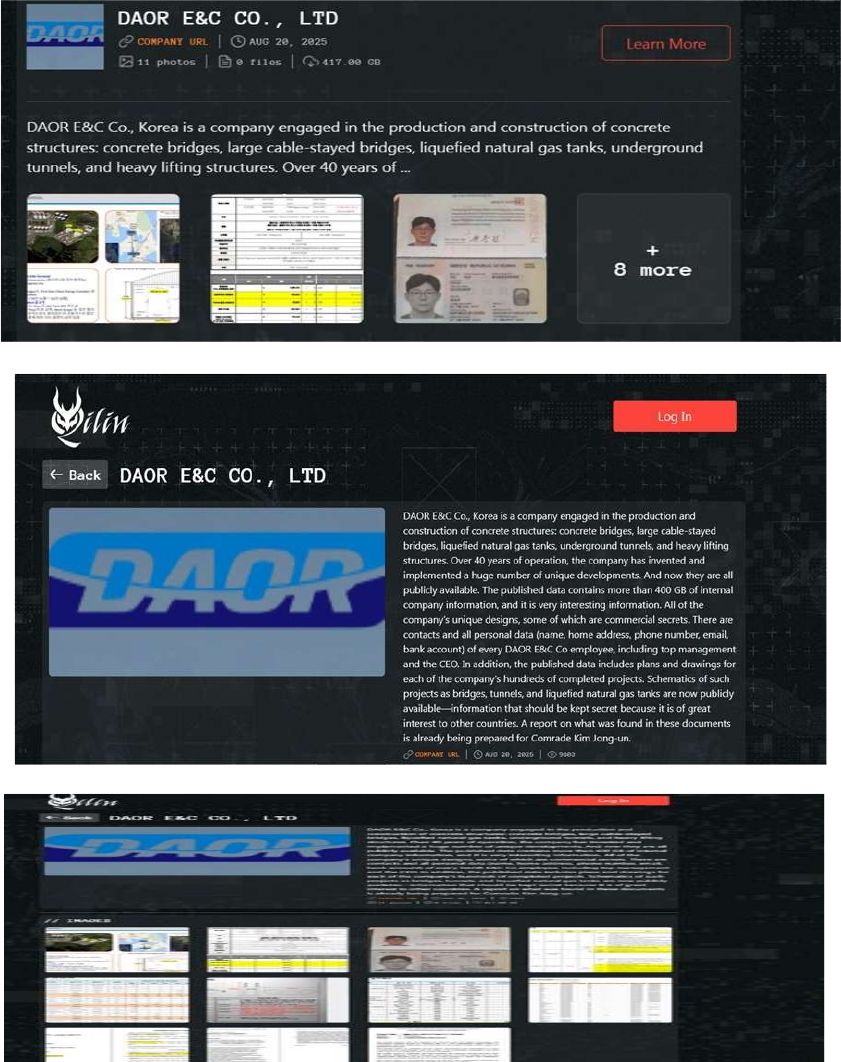
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from South Korea, DAOR E&C Co., Ltd(http[:]//www[.]daorenc[.]com), was compromised by Qilin Ransomware. DAOR E&C Co., Korea, is a company engaged in the production and construction of concrete structures: concrete bridges, large cable-stayed bridges, liquefied natural gas tanks, underground tunnels, and heavy lifting structures. The leaked data reportedly contains over 400 GB of internal company information, including proprietary designs regarded as trade secrets. It also exposes the personal details of all DAOR E&C Co. employees, including top management and the CEO—such as names, home addresses, phone numbers, email addresses, and bank account information. Additionally, the dataset includes plans and technical drawings for hundreds of completed projects, with schematics of bridges, tunnels, and liquefied natural gas (LNG) tanks now publicly accessible. This highly sensitive information should remain confidential, as it holds significant value and potential interest to foreign entities.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Lynx Ransomware Impacts HK Hardware & Engineering
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore, HK Hardware & Engineering(https[:]//www[.]hkhardware[.]com[.]sg/), was compromised by Lynx Ransomware. H.K. Hardware Engineering Pte Ltd is a one-stop industrial supplier for the marine offshore sector, offering a wide range of products, including cutting discs, abrasive materials, building materials, hand tools, and safety products. The compromised data includes financial documents, purchase and sale deed bills, along with other confidential and sensitive information pertaining to the organization.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
Vulnerability in ISC Kea
Relevancy & Insights:
The vulnerability exists due to a reachable assertion when handling DHCP packets. A remote attacker can send a request with some specific options, and if Kea fails to find an appropriate subnet for the client, the kea-dhcp4 process will abort with an assertion failure.
Impact:
A remote attacker can perform a denial-of-service attack.
Affected Products:
https://kb[.]isc[.]org/docs/cve-2025-40779
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
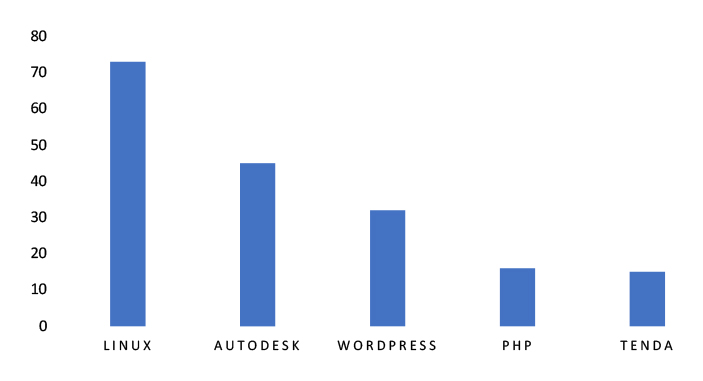
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerabilities in ISC Kea, an open-source DHCP server developed by the Internet Systems Consortium (ISC), can pose significant risks to network environments.
Exploitation could allow attackers to cause denial of service (DoS), manipulate DHCP leases, or potentially execute arbitrary code, impacting IP address management and network availability.
Sinobi Ransomware attacked and published the data of Harmony Electronics Corp
Summary:
Recently, we observed that Sinobi Ransomware attacked and published the data of the Harmony Electronics Corp (https[:]//www[.]hele[.]com[.]tw/) on its dark web website. Harmony Electronics Corp is engaged in the manufacture of quartz frequency components. The Company’s main products include quartz crystals, quartz filters, and crystal oscillators. Its quartz crystals are applied to computer peripherals, communication devices, household electronics, automobiles, and others. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
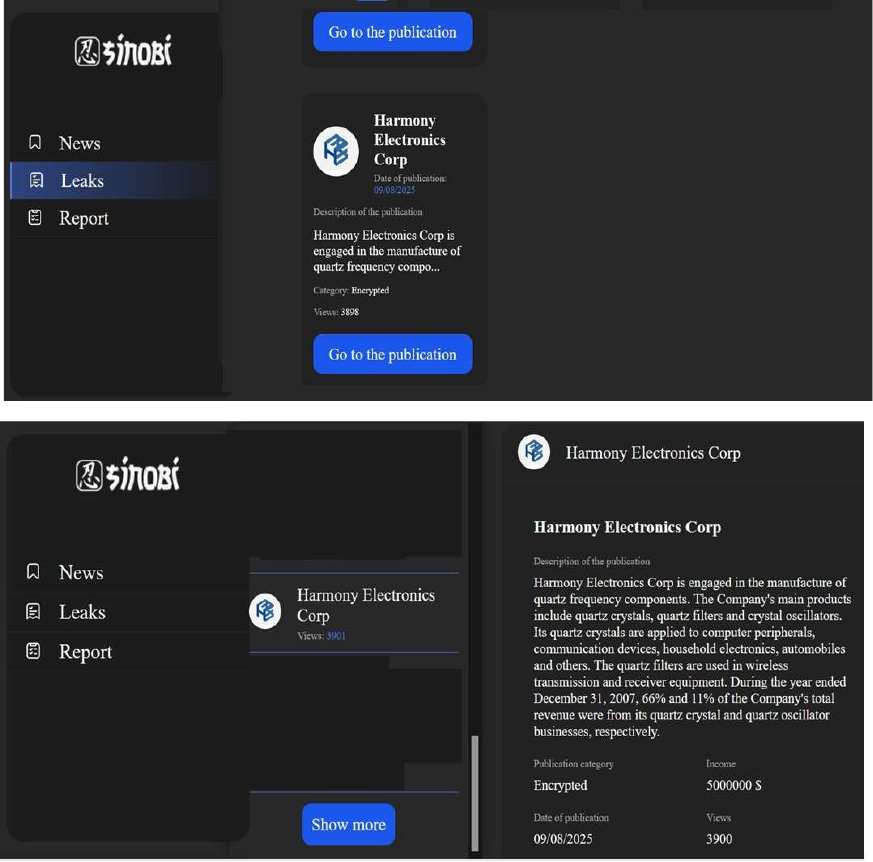
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Sinobi Ransomware represents a new, persistent threat in the ransomware landscape, capable of disruptive attacks on both enterprises and mid-sized organizations.
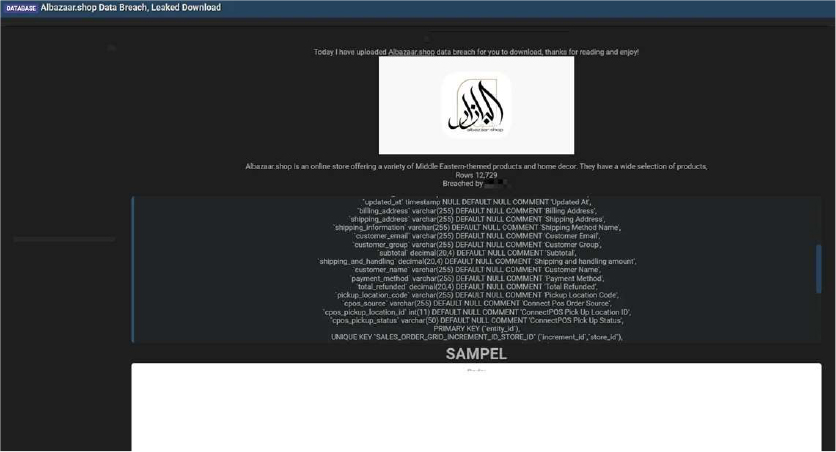
Qatari E-commerce Platform Albazaar Shop’s Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor “N1KA” has allegedly leaked a database belonging to Albazaar[.]shop, a popular Qatar-based online store specializing in Middle Eastern-themed products and home decor. The data was published on a notorious cybercrime forum and is said to contain over 12,700 rows of sensitive customer and order information. Albazaar[.]shop is a significant e- commerce platform within the region, and this alleged breach poses a serious privacy risk to its customer base.
The compromised database allegedly exposes a variety of personal and transactional details. According to the information shared by the threat actor, the leak contains specific data points that could be used by malicious actors for phishing campaigns, identity theft, or other forms of fraud. Customers of the platform are advised to be vigilant and monitor their accounts for any suspicious activity.
The leaked data allegedly includes:
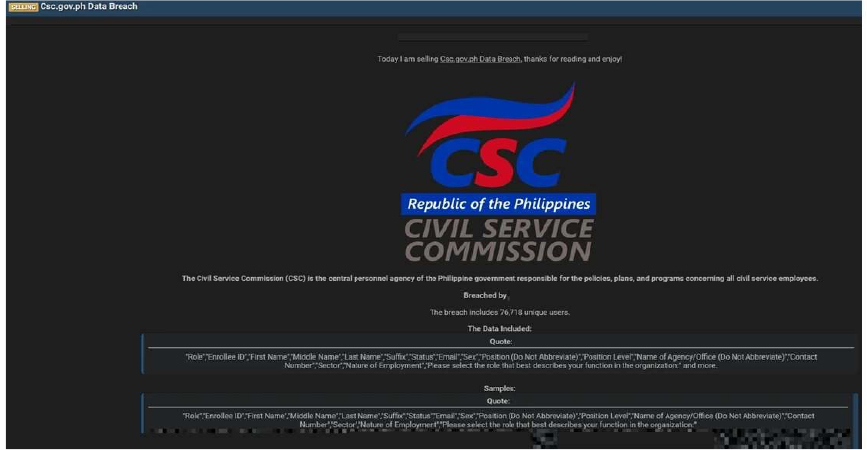
Philippine Civil Service Commission (CSC) Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team has identified that a threat actor has allegedly breached the Civil Service Commission (CSC) of the Philippines and is attempting to sell the stolen data on a dark web forum. The CSC is a highly important government body, acting as the central personnel agency for the entire Philippine government. It is responsible for the policies, plans, and programs that affect all civil service employees across the nation. The alleged breach reportedly exposes the sensitive information of 76,718 unique users, placing a significant number of government workers at risk.
Information also appears to contain detailed feedback from training sessions, further exposing personal opinions and internal data.
The data allegedly includes the following:
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor identified as “N1KA” has recently gained attention as a highly active group specializing in data leaks. Reliable sources have connected the group to multiple security breaches involving unauthorized system access and the attempted sale of exfiltrated data on dark web marketplaces. N1KA’s ongoing operations highlight the evolving and persistent nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to strengthen their cybersecurity posture through continuous monitoring, advanced threat intelligence, and proactive defense strategies to protect sensitive data and infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that a threat actor has allegedly put administrative access to an unnamed cryptocurrency exchange up for sale on a cybercrime forum. The seller is asking for $5,000 in exchange for what is described as “API-level administrative access.” The specific identity of the crypto exchange has not been disclosed, leaving the industry on high alert as the potential victim could be any number of platforms operating globally. The anonymity of the victim makes it difficult for customers to take precautionary measures.
The type of access being sold poses a significant and severe threat. API-level administrative privileges could potentially allow a malicious actor to execute unauthorized trades, withdraw funds from user accounts, access sensitive customer data, and manipulate market data on the platform. Such a breach would be catastrophic for the exchange and could lead to devastating financial losses for its clients. The incident underscores the persistent targeting of the digital asset industry by cybercriminals seeking to exploit vulnerabilities for financial gain.
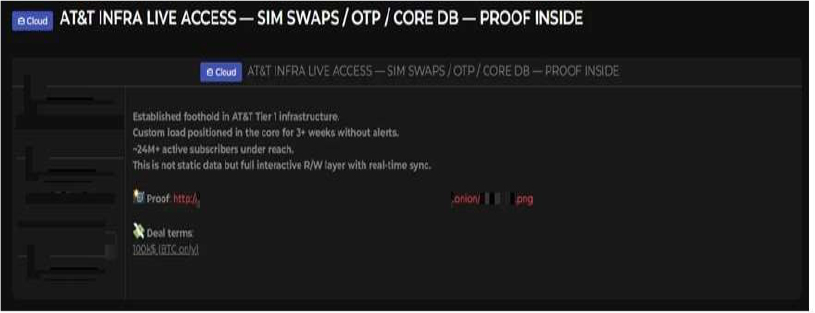
The CYFIRMA Research team has identified that a threat actor is allegedly offering live access to the core infrastructure of AT&T, a leading American multinational telecommunications company headquartered in Dallas, Texas. AT&T, one of the largest telecommunications providers in the United States, delivers mobile and fixed-line services to millions of customers. According to the seller, they have established a persistent presence within the company’s Tier 1 infrastructure, with interactive read/write access to a database containing data of approximately 24 million active subscribers. Such access could reportedly allow the actor to perform SIM swaps and intercept One-Time Passwords (OTPs), creating a significant security threat to impacted customers.
According to the post on a dark web forum, the threat actor has maintained their presence within AT&T’s systems for over three weeks without being detected. As proof of their claims, they shared a screenshot of what appears to be a database management tool showing subscriber data. The actor emphasized that this is not a static data leak but a live, interactive system with real-time synchronization, which they are offering for sale for $100,000 in Bitcoin. The exposed data fields allegedly include:
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
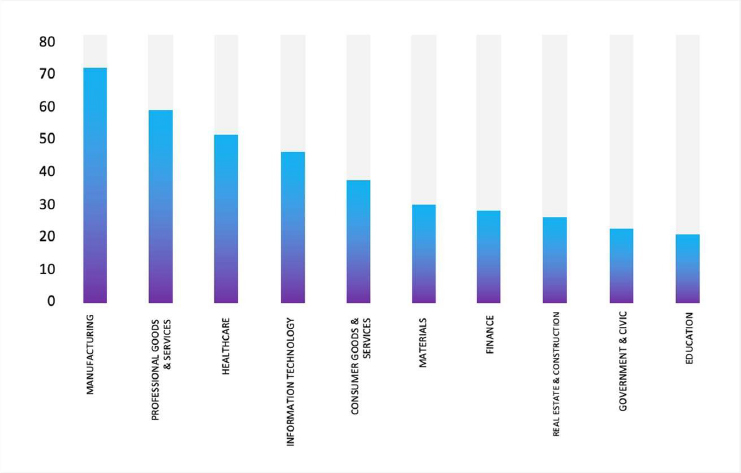
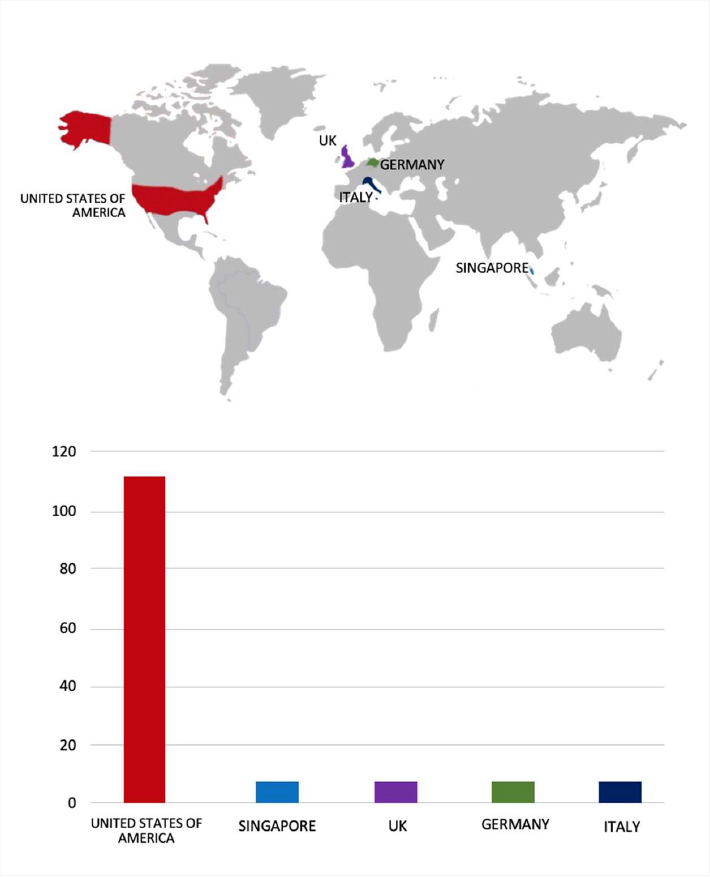
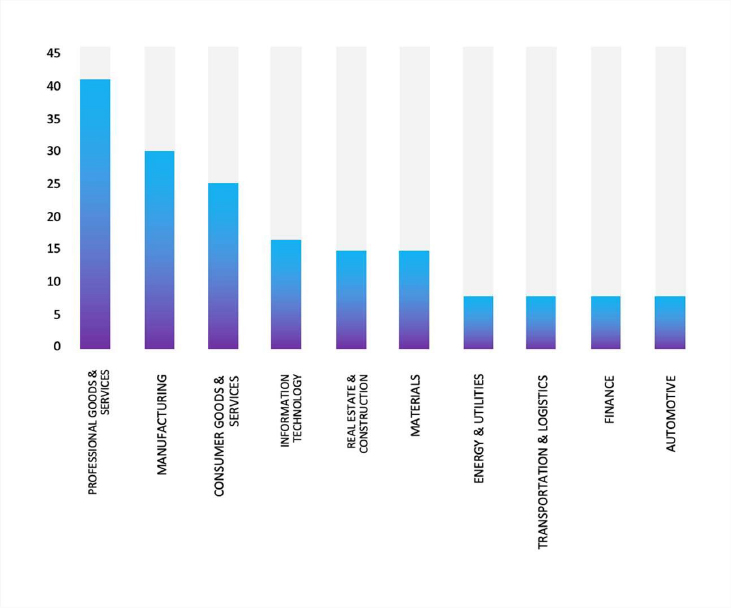
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.