Published On : 2023-05-05
Weekly Attack Type and Trends Key Intelligence Signals:
- Attack Type: Malware Implants, Spear Phishing, Ransomware Attacks, Vulnerabilities & Exploits, DDoS, Data Leak.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Payload Delivery, Espionage, and Data Destruction.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – Black Basta Ransomware | Malware – BouldSpy
- Black Basta Ransomware – One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following:
- Malware – BouldSpy
- Behavior –Most of these malwares use phishing and social engineering techniques as their initial attack vector. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus : Fancy Bear aka APT28 Targets Government in Ukraine via Bogus Windows Update Email
- Suspected Threat Actors: Fancy Bear
- Attack Type: Spear Phishing
- Target Geography: Ukraine
- Target Industry: Government
- Objective: Data Theft
- Target Technology: Windows
- Business Impact: Data Loss and Operational Disruption
Summary:
In a recent observation, Ukrainian CERT revealed attacks by a Russian state-sponsored APT named Fancy Bear aka APT28. The threat actor conducted a Spear Phishing attack against Ukrainian government departments. It’s not yet clear which government departments were the target of these spear phishing attacks. The threat actor dropped emails with “Windows update” as the subject. The email had long instructions written in the Ukrainian language, guiding users to update the Microsoft operating system for protection against hacker attacks. Further, they added illustrations demonstrating how to access the command line and execute a PowerShell command. The mentioned command in the email could initiate the process to download a PowerShell script. This script emulates the operating system update process and subsequently downloads and executes another PowerShell script. The secondary script is crafted to gather fundamental computer information using commands such as “tasklist” and “systeminfo”. It then sends the collected results to the Mocky service API using an HTTP request.
Insights:
In this attack, we have observed a unique social engineering attack in which Fancy Bear instructs and manipulates the victim to carry out a malicious activity using a carefully crafted, manual approach with detailed steps to execute a harmful PowerShell script. This marks the first instance of such behavior attributed to APT28 aka Fancy Bear.
APT28 is known for many high-profile attacks including interfering in 2016’s US elections. Last year, the group also exploited a vulnerability in Follina and used it in spear phishing attacks. Recently the Ukrainian Hacktivist called “Kiber Sprotyv” exposed a Russian national named Morgachev suspected to be the leader of APT28 and, he is also on the FBI’s wanted list.
Major Geopolitical Developments in Cybersecurity
Hackers target NGOs in China
Researchers have recently observed known Chinese APT group Evasive Panda (also known as Daggerfly), conducting a campaign to install its custom MsgBot backdoor malware to spy on Chinese users. The group utilized malicious software updates for legitimate applications as a way for gaining access to targeted devices and then exfiltrate data.
According to the researchers, most of the victims are members of international NGOs in China but individuals in Nigeria have also been targeted in the campaign. Researchers believe that Evasive Panda may have infiltrated Tencent QQ’s update servers and messaging software to target specific individuals with corrupted updates while sending authentic updates to non-targets. As a result, this campaign would be categorized as a supply chain attack because it employs upstream infiltration of outside parties to infect users downstream with malware via software upgrades.
An evasive Panda is a cyberespionage group that has been observed by researchers for more than 10 years and has previously targeted organizations and individuals in mainland China, Hong Kong, Macao, Nigeria, and East Asia.
Iran integrates influence and cyber operations
Since the summer of 2022, Iran’s efforts to influence others have become more and more sophisticated, according to researchers. The Iranian government was responsible for 24 different cyber-enabled influence operations last year, with many of the campaigns being credited to the Cotton Sandstorm group, an Iranian state actor sanctioned by the US Treasury Department for its attempts to sabotage the credibility of the 2020 US Presidential Elections.
A typical campaign by the group begins with a fake “cyber persona” announcing and usually exaggerating a low-grade cyberattack. The announcement is then taken up, spread, and amplified by false accounts on social media using the language of the intended audience. The objectives of its cyber-enabled IOs have included trying to strengthen Palestinian resistance, inciting unrest in Bahrain, and halting the increasing normalization of relations between Arab countries and Israel, with a focus on inciting fear and panic among Israeli civilians
Other Observations
CYFIRMA Research team observed that potential data leak related to Brax {www[.]brax[.]com[.]br). Brax is a Brazilian company focused on developing software for retail and wholesale companies of all sizes. The data leak contains customers’ confidential information.
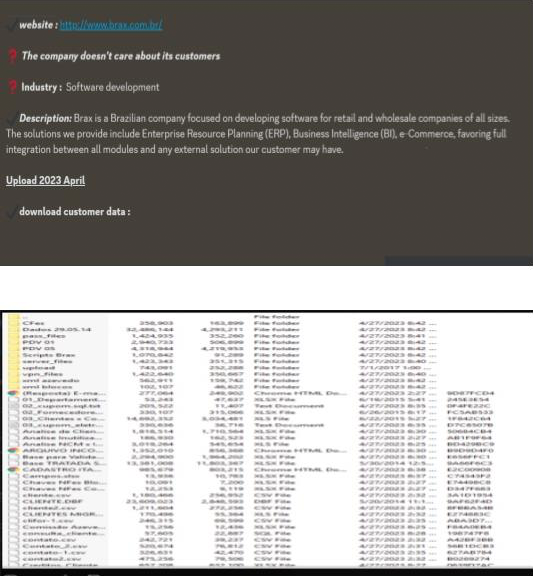
Source: Underground forums
STRATEGIC RECOMMENDATION
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATION
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATION
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improve incident response, increase the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.




