



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Target Countries: Indonesia
Target Industries: Government
Introduction
CYFIRMA Research and Advisory Team has found Brain Cipher while monitoring various underground forums as part of our Threat Discovery Process.
Brain Cipher
Researchers and its adversary team have identified a new ransomware group, Brain Cipher Ransomware, in the evolving threat landscape. This group uses a variant of the notorious Lockbit 3.0 ransomware, employing double extortion by both exfiltrating and encrypting sensitive data.
However, Brain Cipher has made some minor changes to the encryptor.
One of those changes is that it not only appends an extension to the encrypted file but also encrypts the file name.

The encryptor will also generate ransom notes named in the format [extension].README.txt. These notes provide a brief explanation of the situation, include threats, and contain links to the Tor negotiation and data leak sites.
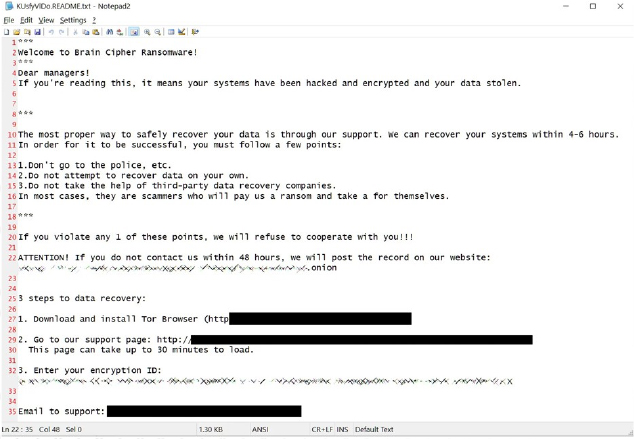
In one instance observed by researchers, the threat actor diverged from the usual template and used the file name ‘How To Restore Your Files.txt.’

Communication channel and Dataleak site overview:
Each victim receives a unique encryption ID, which must be entered into the threat actor’s Tor negotiation site. Like many recent ransomware operations, the negotiation site is quite basic, featuring a chat system for the victim to communicate with the ransomware group.

Like other ransomware operations, Brain Cipher infiltrates corporate networks and spreads to other devices. After obtaining Windows domain admin credentials, the ransomware is deployed across the network. Before encrypting files, the attackers steal corporate data to use as leverage, threatening to release it publicly if the ransom isn’t paid.
Brain Cipher recently launched a new data leak site, which currently lists no victims.
According to researchers, ransom demands have ranged from $20,000 to $8 million.


Following are the TTPs based on the MITRE Attack Framework
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| 2 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 3 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1574.002: Hijack Execution Flow: DLL Side- | ||
| Loading | ||
| 4 | TA0005: Defense Evasion | T1006: Direct Volume Access |
| T1027: Obfuscated Files or Information | ||
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1202: Indirect Command Execution | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| T1056.001: Input Capture: Keylogging | ||
| T1552.001: Unsecured Credentials: Credentials In Files | ||
| T1555.003: Credentials from Password Stores: Credentials from Web Browsers | ||
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1056.001: Input Capture: Keylogging | ||
| T1074: Data Staged | ||
| T1185: Browser Session Hijacking | ||
| 8 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| 9 | TA0040: Impact | T1485: Data Destruction |
| T1486: Data Encrypted for Impact | ||
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
Based on CYFIRMA’s analysis of available data, Brain Cipher Ransomware is likely to escalate ransom demands and expand its operations to economically developed nations in Europe, East Asia, South-East Asia, and the US. This trend is driven by the higher financial capabilities of organizations in these regions to meet ransom demands ranging from $20,000 to $8 million. The ransomware’s sophisticated tactics, including data exfiltration and encryption with file name obfuscation, indicate a continued evolution towards more targeted and lucrative attacks.
YARA
import “pe”
rule BrainCipher_Ransomware
{
meta:
description = “BrainCipher Ransomware – Detection Rule” author = “CRT”
date = “2024-07-01”
malware_type = “ransomware”
strings:
$s1 = “.rdata$zzzdbg” wide ascii
$s2 = “.text$mn” wide ascii
$sec1 = {55 8B EC 81 EC 7C ?? ?? ?? 53 56 57}
condition:
uint16(0) == 0x5A4D and all of them and
for any section in pe.sections : ( section.name == “.itext” ) and pe.imphash() == “41fb8cb2943df6de998b35a9d28668e8” and filesize >= 130KB
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Remote Access, Data Exfiltration
Target Technology: Android OS, Messaging Application (Telegram)
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the Week
This week “SpyMax” is trending.
SpyMax
Researchers have discovered SpyMax, an Android Remote Access Trojan (RAT) targeting Telegram users through a phishing campaign. This malware can collect personal and private information from infected devices without user consent and send it to a remote threat actor. Notably, SpyMax does not require the targeted device to be rooted, making it easier for attackers to cause damage. This RAT compromises the confidentiality and integrity of the victim’s privacy and data.

Attack Method
Initially distributed via a phishing page impersonates Telegram, when the user clicks on “click to download,” a malware application named “ready.apk” is downloaded from the link: https[:]//telegroms[.]icu/assets/download/ready[.]apk. Once installed, it pretends to be the Telegram app, using a similar icon in the device app drawer. After installation, the RAT repeatedly prompts the user to enable the Accessibility Service for the app until the user complies.

This APK functions as a Trojan with keylogger capabilities. It establishes a directory named “Config/sys/apps/log” in the external storage of infected devices, saving logs to files named “log-yyyy-mm-dd.log,” where yyyy-mm-dd indicates the date of keystroke capture. The malware collects location data, including altitude, latitude, longitude, precision, and device speed. SpyMax compresses this data using the gZIPOutputStream API before sending it to the C2 server. This RAT communicates with the C2 server at IP 154.213.65[.]28 on port 7771. Once connected, it sends compressed data using gzip to the C2 server, as observed in network packet headers. The server responds with compressed data containing system commands and an APK payload, which are decompressed upon receipt.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the rise of sophisticated malware like SpyMax highlights the growing cyber risks facing organizations and their employees. Beyond immediate concerns over privacy and security, SpyMax’s capabilities suggest broader implications for organizational operations and workforce productivity. Its use of phishing campaigns, which mimic trusted apps like Telegram, exploits employee trust and can lead to significant risks such as data breaches, financial losses, and damage to the organization’s reputation. Moreover, the threat extends to employees’ personal devices used for remote work, blurring the line between personal and professional security threats. This dual risk underscores the urgent need for organizations to implement robust cybersecurity measures. Educating employees about phishing and other social engineering tactics, adopting stringent security protocols such as multi-factor authentication and regular software updates, and ensuring the security of devices used for work are critical steps to mitigate these risks.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Intelligence Signals:
New Kimsuky Cyber Espionage Campaign Targets South Korean Academia
Summary:
In March 2024, a researcher uncovered new malicious activity from Kimsuky (aka APT43, Emerald Sleet, Velvet Chollima), a North Korean government-backed cyber espionage group. This threat actor, first observed in 2013, is notorious for targeting South Korean entities such as think tanks, government institutions, and the academic sector. Their recent campaign leverages malicious Google Chrome extensions, notably a new extension named “TRANSLATEXT,” to steal sensitive information. Kimsuky’s latest campaign primarily targets South Korean academia, specifically researchers involved in political research related to North Korean affairs. This focus on academic institutions aligns with their ongoing mission to gather valuable intelligence on geopolitical matters.
The initial method of attack involves delivering a malicious archive file named “한국군 사학논집 심사평서 (1).zip” (“Review of a Monograph on Korean Military History”). This archive contains decoy HWP documents and a Windows executable disguised as related documents. When executed, the malware retrieves a PowerShell script from the attacker’s server, initiating the infection chain. TRANSLATEXT, the malicious Chrome extension, is used to steal email addresses, usernames, passwords, and cookies, and capture browser screenshots. It was uploaded to Kimsuky-controlled GitHub repositories on March 7, 2024, and removed the next day to minimize exposure. This extension can bypass security measures for prominent email services like Gmail, Kakao, and Naver.
The PowerShell script associated with the attack checks for the presence of installed Chrome extensions using the Windows registry key HKCU\Software\Policies\Google\Chrome\ExtensionInstallForcelist. This key enforces the installation of specified extensions without user permission. TRANSLATEXT was registered in this key to facilitate its installation.
The malicious extension uses several JavaScript files to bypass security measures and steal information. Scripts like auth.js and gsuit.js are injected into login pages of targeted services to manipulate security features and capture credentials. A background script (background.js) employs the dead drop resolver technique to retrieve commands from a public blog service and execute actions such as capturing browser screenshots and sending stolen data to a command-and-control (C2) server.
Kimsuky’s motive is to conduct surveillance and gather intelligence on South Korean academia, particularly those researching North Korean geopolitical affairs. The stolen data includes browser login information and cookies, indicating an effort to monitor and infiltrate academic researchers’ activities.
The Kimsuky group’s use of malicious Chrome extensions like TRANSLATEXT highlights the persistent threat they pose to South Korean academia. By staying informed about their latest tactics and exercising caution with software installations, potential victims can better protect themselves from such cyber espionage activities.
Relevancy & Insights:
Kimsuky, also known as APT43, has indeed targeted South Korean academia, particularly those involved in political research related to North Korean affairs. Kimsuky employs advanced techniques such as spear-phishing and the use of double base64 encoding to evade detection. They also use malicious Google Chrome extensions, like the newly discovered “TRANSLATEXT,” to steal sensitive information. The primary targets are South Korean academic institutions, especially those researching North Korean military and political affairs1. This focus on academia allows Kimsuky to gather valuable intelligence that could enhance North Korea’s military capabilities. By exfiltrating sensitive information from these institutions, Kimsuky poses significant geopolitical risks. The stolen data could potentially be used to bolster North Korea’s strategic and military planning. The group’s sophisticated tactics include spear- phishing and the use of double base64 encoding to evade detection.
ETLM Assessment:
The threat posed by the Kimsuky group’s deployment of the “TRANSLATEXT” Chrome extension includes potential threats to various sectors beyond academia, such as government agencies, private corporations, and critical infrastructure entities that rely on similar communication platforms. The extension’s capability to steal sensitive data like email addresses, passwords, and browser activity could lead to widespread data breaches, espionage, and targeted cyber-attacks. Additionally, the sophisticated techniques used to bypass security measures suggest a high risk of undetected infiltration, raising concerns about the robustness of current cybersecurity defenses across multiple sectors.
Recommendations:

IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian hackers breach TeamViewer
The remote access software provider TeamViewer is investigating a breach of its internal corporate IT environment, which has been ascribed to the threat actor known as APT29 (also known as Cozy Bear and linked to Russia’s foreign intelligence service SVR). Based on current findings of the incident’s investigation, the threat actor leveraged a compromised employee account to copy employee directory data, i.e. names, corporate contact information, and encrypted employee passwords for the internal environment. The attack was likely contained within the internal environment and there is no evidence that the threat actor gained access to our product environment or customer data, which was likely its intent, either directly, or indirectly – through getting access to the application connected to end users’ accounts.
ETLM Assessment:
CozyBear is a sophisticated APT that enables state-driven espionage by cyber means. Recently, its operators were targeting Hewlett Packard or Microsoft, most likely with the same intention of gaining access to their products the APT could leverage for espionage purposes. This threat actor often targets governments, diplomatic entities, non-governmental organizations and IT service providers, primarily in the U.S. and Europe, a targeting mostly consistent with countries opposing the Russian war against Ukraine.
Google disrupts Chinese influence operations
Researchers have recently published an update on a coordinated influence operator that pushes content aligned with the Chinese government’s positions and is tracked under the moniker DRAGONBRIDGE. According to the researchers, DRAGONBRIDGE accounts create content reacting to breaking news, especially polarizing social issues, usually within a few weeks of the event. In general, this content is of lower quality than the content created for anticipated events, reflecting the speed with which the actor pivots to create content in response to current events. In 2023 alone Google removed more than 65,000 interactions linked to DRAGONBRIDGE, mostly on YouTube. While the operation is high-volume, its effectiveness has been largely questionable as its engagement counts from real users have been low.
ETLM Assessment:
In April of this year, China’s military underwent its largest reorganization this decade when the Strategic Support Force was eliminated, and a new Information Support Force inaugurated. Xi Jinping, the Chinese leader has hailed the new force as a “strategic force” which will (among other critical missions) “efficiently implement information support”. That would be required to enable the military to carry out successful multi-domain joint operations. The latest reorganization hints at the importance Chinese leaders ascribe to its long-standing tradition of information operations of which DRAGONBRIDGE has been just a tiny component. The new agreement will better equip China’s armed forces to fight in the region, particularly the high-stakes joint operations required to threaten and, in the worst-case scenario, overrun Taiwan. Chinese sources point to the reorganization as part of the modernization objective for 2027, which centers on getting the Chinese military ready for a cross-strait battle over Taiwan.
The BlackSuit Ransomware impacts the KADOKAWA Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]kadokawa[.]co[.]jp), was compromised by the BlackSuit Ransomware. Kadokawa Corporation is a major Japanese multimedia conglomerate, widely recognized for its influence in the publishing, film, and digital entertainment sectors. The compromised data contains contracts, DocuSign papers, various legal papers, platform-related data (emails, data usage, links opened, etc.), employee-related data (personal info, payments, contracts, emails, etc.), business planning (presentations, emails, offers, etc.), projects related data (coding, emails, payments, etc.), financial data (payments, transfers, planning, etc.), other internal-use-only papers and confidential data.
The following screenshot was observed published on the dark web:

Relevancy & Insights:

ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that BlackSuit Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on KADOKAWA Corporation, a prominent Entertainment company located in Japan, underscores the extensive threat posed by this particular ransomware strain in the Asia Pacific region.
The RansomHub Ransomware impacts the Midamea
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from South Korea; (www[.]midamea[.]com), was compromised by the RansomHub Ransomware. Midamea is an architecture firm based in South Korea known for its innovative and contemporary designs. The firm specializes in a wide range of architectural projects, including residential, commercial, and public buildings, with a focus on creating functional and aesthetically pleasing spaces. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:

Relevancy & Insights:


ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is supported by the recent attack on Midamea, a leading architectural services and consultancy firm in South Korea, highlighting RansomHub’s significant threat presence in East Asia.
Vulnerability in Artifex Ghostscript
Summary:
The vulnerability allows a remote attacker to compromise the affected system.
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user-supplied input in psi/zmisc1.c.
Impact:
A remote attacker can pass specially crafted input to the application and execute arbitrary code on the system.
Affected Products: https[:]//bugzilla[.]redhat[.]com/show_bug.cgi?id=2278775
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.

ETLM Assessment:
Vulnerability in Ghostscript can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Ghostscript is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding online activities, including interpreting and processing PostScript and PDF files, across different geographic regions and sectors.
8Base Ransomware attacked and Published data of Hokushinko Co., Ltd
Summary:
Recently we observed that 8Base Ransomware attacked and published data of Hokushinko Co., Ltd (www[.]hokushinko[.]jp) on its darkweb website. Hokushinko Co., Ltd. is a company that specializes in the construction of railway signals and traffic lights, as well as technology implementation. The data leak, following the ransomware attack, encompasses Invoices, Receipts, Accounting documents, Personal data, Certificates, Employment contracts, Confidentiality agreements, Personal files, and Others.

Relevancy & Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment indicates that 8Base Ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent incident involving an attack on Hokushinko Co., Ltd, a prominent Construction company located in Japan, underscores the extensive threat posed by this particular ransomware strain in the Asia Pacific region.
Indonesian Directorate General of Civil Aviation Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to the Indonesian Directorate General of Civil Aviation in an underground forum. According to the threat actor, the leaked database from the Indonesian Directorate General of Civil Aviation is more than 3GB and it includes data for all employees, passwords for all applications, website user data, ID card photos for all employees, drone pilot certificate participants, flight data, personal data of pilots and all activities in Indonesian air space and airports. The threat actor also included sample data from the alleged leak in the post.

Indonesia’s Ministry of Law and Human Rights (Kemenkumham) data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to Indonesia’s Ministry of Law and Human Rights (Kemenkumham) in an underground forum. The threat actor has claimed responsibility for leaking the email login credentials of the Ministry of Law and Human Rights (Kemenkumham), potentially exposing sensitive government information.
Details of the Claim:
According to the threat actor, the leaked data includes access to official email accounts used by employees. This exposure could potentially compromise sensitive government information. The threat actor provided specific details about the alleged breach:
Entity Involved:
Ministry of Law and Human Rights (Kemenkumham) Data Exposed: Email login credentials (username and password)
Potential Risks:
Unauthorized access to sensitive communications, data manipulation, identity theft, and more.

Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
According to CYFIRMA’s evaluation, the financially driven cybercriminal known as ‘Guzmanloeraxxx’ present a substantial threat to organizations. This actor indiscriminately targets various institutions and profits by selling compromised sensitive information on the dark web or underground forums. ‘Guzmanloeraxxx’ often exploits organizations with insufficient security measures, making them particularly susceptible to these orchestrated cyberattacks.
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data breach related to Scrubser Shop (www[.]scrubser-shop[.]com). A threat actor on a dark web forum shared data allegedly belonging to Scrubser Shop, a medical clothing store from Saudi Arabia. According to the threat actor, the compromised data includes customer information such as email addresses, passwords, names, billing and shipping addresses, phone numbers, and a previous backup.
The post indicates that the attack occurred in 2024 and the allegedly leaked data is approximately 5k lines. The size of the leak is 1 GB. The threat actor also shared samples from the alleged leak. There is no contact information or price in the dark web forum post.

The CYFIRMA Research team observed a potential data breach related to Cognizant’s Open Insurance Policy Administration (OIPA) system (USA). IntelBroker, a notorious threat actor, claims to have leaked a database from Cognizant’s Open Insurance Policy Administration (OIPA) system. Cognizant is a global provider of information technology, operations and technology consulting, infrastructure, and business process services.
The alleged database reportedly contains data on approximately 40,000 users and includes a 12-million-line document detailing the internal site used by these users. According to the threat actor, the compromised data includes Policy Number, Role Code, Client name, Company Code, State Code, and other sensitive and confidential data.

ETLM Assessment:
Threat Actor ‘IntelBroker’ group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
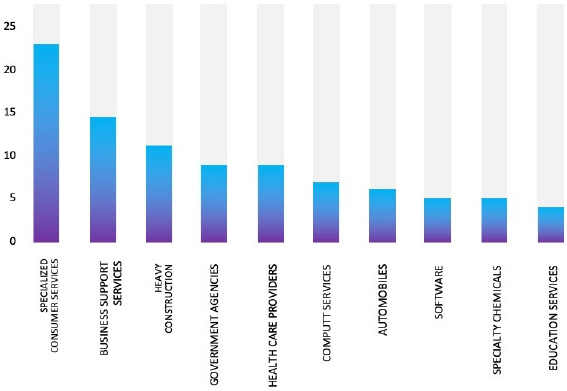
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph

Industry-Wise Graph

For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.