



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows
Target Industries: Business Services, Education, Government, Healthcare, Manufacturing.
Target Geography: United States
Introduction
CYFIRMA Research and Advisory Team has found Meow ransomware while monitoring various underground forums as part of our Threat Discovery Process.
1 Meow ransomware:
Meow ransomware, associated with the Conti ransomware, initially surfaced in August 2022 but disappeared in February 2023. Recently, it has resurfaced.
The ransomware encrypts files and appends the “.MEOW” extension to their filenames. It also drops the “readme.txt” file (a ransom note).
The Ransomware employs ChaCha20 and RSA-4096 encryption.
The ransom note says that victims must contact threat actors if they need to decrypt files. It provides meowcorp2022@aol[.]com, meowcorp2022@proton[.]me, meowcorp@msgsafe[.]io, and meowcorp@onionmail[.]org email addresses, and two Telegram usernames (@meowcorp2022 and @meowcorp123) for contacting the attackers.

Screenshot of files encrypted by Meow ransomware.
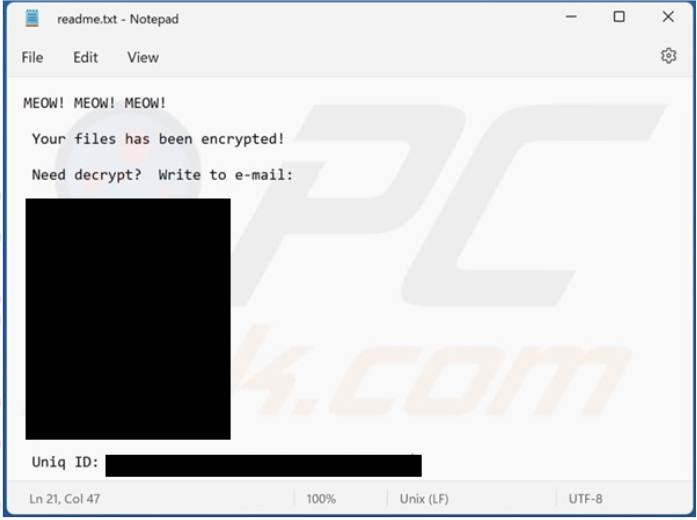
Screenshot of Meow ransomware’s Ransom note
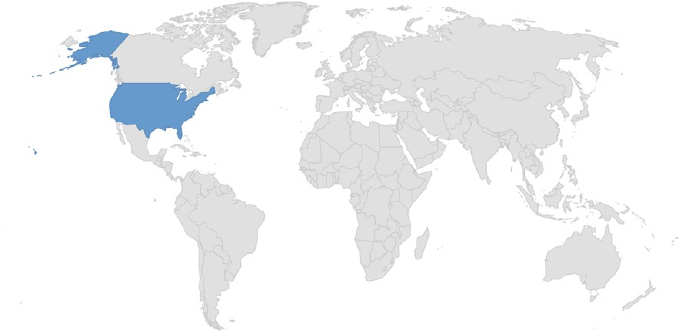
Countries targeted by Meow ransomware.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1129: Shared Modules |
| 2 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 3 | TA0006: Credential Access | T1056: Input Capture |
| 4 | TA0007: Discovery | T1057: Process Discovery |
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 5 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| 6 | TA0009: Collection | T1056: Input Capture |
| 7 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1573: Encrypted Channel | ||
| 8 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment suggests that the Meow ransomware, with its reappearance and evolving tactics, will likely remain a persistent threat. Its emphasis on Windows systems, varied target sectors, anti-analysis measures, and a strategic geographical focus on the US highlight its sophistication and adaptability. We can expect the wide spread of the ransomware to other geographies and even the new variants may emerge soon. Organizations should prioritize robust cybersecurity measures and remain vigilant against emerging variants.
Sigma Rule
title: Process Creation Using Sysnative Folder tags:
– attack.t1055 logsource:
category: process_creation product: windows
detection: sysnative:
CommandLine|startswith: ‘C:\Windows\Sysnative\’ condition: sysnative
fields:
– CommandLine
– ParentCommandLine falsepositives:
– Unknown level: medium
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Trojan
Objective: Espionage, Financial theft Target
Technology: Android OS
Target Geographies: USA, Brazil, Argentina, UK, Spain, and Germany
Target Apps/Category: Health, Games, Horoscope, and Productivity
Active Malware of the Week
This week “Xamalicious” is trending.
Xamalicious
Researchers discovered an Android backdoor named Android/Xamalicious, which utilizes the Xamarin open-source framework to build apps for Android and iOS using .NET and C#. Xamalicious trojans masquerade as apps in various categories, including health, games, horoscope, and productivity. Notably, a number of these malicious apps are still accessible for download on third-party marketplaces. Additionally, researchers have established a connection between Xamalicious and the ad-fraud app “Cash Magnet.” The latter engages in automatic clicking of ads, app installations, and other actions to fraudulently generate revenue. Users who install it may earn points that are supposed to be redeemable as a retail gift card. This suggests that the developers behind these threats are financially motivated, indicating that ad-fraud could be a primary payload of Xamalicious.
The use of the Xamarin framework enabled malware authors to operate covertly and evade detection for an extended period. They exploited the APK build process as a packing mechanism to conceal the malicious code. The authors also incorporated various obfuscation techniques and custom encryption for data exfiltration and communication with the command-and-control server. Approximately 25 malicious apps carrying this threat were identified, some of which were distributed on Google Play since mid-2020.
Attack Method
Xamalicious employs a multi-stage attack method to compromise Android devices. The backdoor employs social engineering to acquire accessibility privileges, followed by communication with a command-and-control server. It assesses whether to download a second-stage payload, dynamically injected as an assembly DLL at runtime. This allows the attacker to gain full control of the device, enabling potentially fraudulent activities like clicking on ads, installing apps, and other financially motivated actions without user consent.
Xamalicious malware operates in a multi-stage process to compromise devices Obtaining Accessibility Services
The Xamalicious trojan employs social engineering through apps like “Numerology: Personal horoscope & Number predictions” to prompt users to enable accessibility services. The activation process involves manual steps, accompanied by warnings from the operating system.
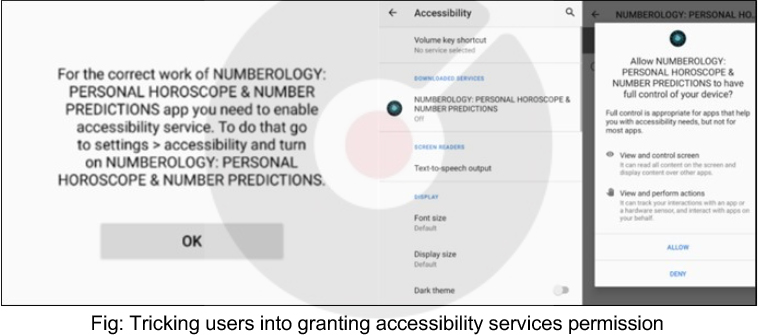
Where is the Malicious Code?
Unlike conventional Java or native ELF Android applications, the Xamalicious malware module is originally crafted in .NET and compiled into a dynamic link library (DLL). This DLL undergoes LZ4 compression, possibly residing in a BLOB file or directly accessible in the /assemblies directory within the APK structure. The loading of malicious code occurs at runtime through either a native library (ELF) or the DEX file. Certain samples demand additional steps for unpacking, and the malicious code typically manifests in two assembly files: core.dll and a
Communication with Command-and-Control Server:
After obtaining accessibility permissions, the malware establishes communication with a malicious server to dynamically load a second-stage payload.
Device Information Collection
Xamalicious collects various device data, including installed applications, to assess if the device is a suitable target for the second stage. It gathers information on location, carrier, network, rooting status, and ADB connectivity. If the device is connected via ADB or is rooted, the C2 will not provide a second-stage payload DLL for download.
Data Encryption using JWT
Communication between the Command-and-Control server and the infected device is encrypted using JSON Web Encryption (JWE) tokens with RSA-OAEP. The malware sends encrypted data via HTTP POST to the “Updater” path. Then it waits for the C2 response and passes it to the decrypt() function which has a hardcoded RSA private key to properly decrypt the received command which might contain a second stage payload for the “getURL” command.
C2 evaluation
Collected data is transmitted to the Command-and-Control server, which evaluates whether the device is an appropriate target for the second-stage payload based on multiple environment validations, including rooting status and ADB connectivity.
DLL Custom Encryption
When the infected client issues the getURL command, it requests the malicious payload. If the Command-and-Control (C&C) Server approves the device to receive the malicious library, it encrypts a Dynamic Link Library (DLL) using Advanced Encryption Standard (AES) in Cipher Block Chaining (CBC). The encryption employs a custom key generated for the specific client based on parameters such as the device ID. This symmetric encryption method allows the same key to work for both the encryption and decryption of the payload.
Payload Delivery in JWT
The encrypted DLL is delivered as part of an HTTP response in an encrypted JSON Web Token (JWT). The client decrypts the token, then decrypts the ‘url’ parameter with AES CBC and a custom key. This means that the DLL has multiple layers of encryption.
DLL Injection
Xamalicious names the DLL “cache.bin” and stores it locally, dynamically loading it using the Assembly.Load method. This second-stage payload compromises the device, granting the malware the ability to observe and interact with any activity. The downloaded second- stage payload may be limited due to specific conditions, but Xamalicious poses a high-risk backdoor, capable of dynamically executing any command on the affected device, including spying, impersonation, or financially motivated actions. The malware employs various encryption methods and efforts to conceal its activities, contributing to its success in avoiding detection by antivirus solutions.
Connection between Xamalicious and the ad-fraud app Cash Magnet
Researchers analyzed one of the Xamalicious sample, the app “LetterLink” (com.regaliusgames.llinkgame), was available on Google Play at the end of 2020, disguised with a book icon. Poorly described as a hidden version of “Cash Magnet,” it engages in ad-fraud activities such as automated clicker actions and app downloads, leading to monetization for affiliate marketing. Users are promised redeemable points for retail gift cards or cryptocurrency. Originally published on Google Play in 2019, “Cash Magnet” (com.uicashmagnet) was a passive income app removed by Google. The authors then infiltrated “LetterLink” and more recently “Dots: One Line Connector” (com.orlovst.dots), hidden versions of the same ad-fraud scheme. “LetterLink” exhibits multiple Xamalicious activities, connecting to the same C2 server and using the same private RSA certificate, establishing a link to the developers of Cash Magnet. “Dots: One Line Connector,” despite its game-like appearance, behaves differently, prompting authentication without referencing Cash Magnet. Although lacking the same DLLs as its predecessor, “Dots” maintains communication with the C2 server using similar RSA key parameters. Google promptly removed “Dots” from Google Play after it was reported by researchers.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the trajectory of Xamalicious malware suggests a potential for continued growth and impact on a global scale. As technology advances, the malware is likely to evolve, adapting its tactics to exploit emerging vulnerabilities and bypass evolving security measures. Its impact on users and organizations worldwide may intensify, with a growing number of individuals falling victim to privacy breaches, financial losses, and other malicious activities facilitated by Xamalicious. The malware’s global reach could expand, infiltrating devices across diverse regions and demographics. Its sophisticated techniques, coupled with financial motivations like ad-fraud, may make it a persistent threat, challenging cybersecurity frameworks globally.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
APT28’s Coordinated Phishing Attacks in Ukraine and Poland
Summary:
In December, state organizations faced sophisticated cyberattacks, indicating the involvement of the APT28 group with ties to Russia. These attacks were notable for their meticulous planning and advanced tactics, demonstrating a focused strategy aimed at compromising the complete information and communication systems within the targeted organizations. The attackers sought to undermine the interconnected nature of the network, emphasizing their objective to infiltrate and compromise the entire infrastructure.
The tactics of the attacks involved the use of phishing emails as a vector of compromise. These emails contained malicious links that, upon interaction, led victims to download a shortcut file through the exploitation of JavaScript and the “ms-search” application protocol. Once opened, this shortcut file executed a PowerShell command, triggering a cascade of malicious activities.
The malicious campaign involves the distribution of harmful links that lead to malicious websites. These websites utilize JavaScript to deploy a Windows shortcut file (LNK), initiating a sequence of PowerShell commands to activate a new Python malware downloader known as ‘MASEPIE.’ MASEPIE ensures its persistence on the compromised device by making changes to the Windows Registry and introducing a deceptively named LNK file (‘SystemUpdate.lnk’) into the Windows Startup folder.
The primary function of the malware is to download additional malicious software onto the infected device and pilfer sensitive data. Additionally, APT28 employs a set of PowerShell scripts called ‘STEELHOOK’ to extract data from web browsers based on Chrome. This likely includes obtaining sensitive information such as passwords, authentication cookies, and browsing history.
Another tool utilized in the attack is ‘OCEANMAP,’ a C# backdoor primarily designed for executing base64-encoded commands through cmd.exe. To maintain persistence on the system, OCEANMAP creates a .URL file named ‘VMSearch.url’ in the Windows Startup folder. OCEANMAP uses the Internet Message Access Protocol (IMAP) as a covert control channel for receiving discreet commands, storing them as email drafts containing the command, username, and OS version. Following the execution of commands, OCEANMAP stores the results in the inbox directory, allowing APT28 to silently retrieve the outcomes and adapt their attack strategy as necessary.
Geographically, the impact extended to Polish organizations, indicating a broader regional targeting strategy. CERT-UA issued a security alert on December 28, 2023, confirming APT28’s phishing attacks against Ukrainian government agencies and urging organizations to fortify their cybersecurity measures.
Relevancy & Insights:
APT28 group’s December 2023 cyberattacks underscore the persistent and evolving cyber threats organizations face. Their sophisticated tactics, including the exploitation of the “ms-search” protocol and strategic use of phishing emails, highlight the need for heightened cybersecurity awareness. As technology evolves, the relevance of proactive cybersecurity measures cannot be overstated. Insights from these attacks serve as valuable lessons, emphasizing the need for organizations to stay ahead of evolving threats through collaboration, advanced detection mechanisms, and a comprehensive cybersecurity strategy.
ETLM Assessment:
A persistent cybersecurity threat, APT28, also known as Fancy Bear, is a Russian cyber espionage group. Recent discoveries indicate that they have launched a new wave of attacks primarily targeting Ukraine and Poland. The focus of these attacks has been on Ukrainian government entities and communication companies based in Poland. APT28 employs sophisticated techniques, with their initial access often initiated through phishing. They have developed new malware, such as the Python- based MASEPIE malware, for this campaign. Once inside the targeted systems, APT 28 deploys a multi-stage attack. The MASEPIE malware is used to download and execute OPENSSH for tunneling, STEELHOOK (a PowerShell script designed for stealing data from Internet browsers), and the OCEANMAP backdoor. Furthermore, within an hour of the initial compromise, the attackers create and use tools like IMPACKET and SMBEXEC for network reconnaissance and lateral movement. The implementation of adaptive security measures is crucial to fortify defenses against potential future threats from this sophisticated cyber espionage group. These measures collectively enhance an organization’s ability to resist APT28’s sophisticated and dynamic cyber operations.
Recommendations:
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Recent incursions by Iranian hacktivist group CyberAv3ngers into control systems used in US and European municipal water systems represent a threat to industrial controls, with a special focus on systems made by Israeli companies. According to researchers, the incidents did not represent a serious attempt at physical disruption of the operation of hardware infrastructure. The attacks were probably meant to drive a geopolitical message and pose a threat that can be escalated further should Tehran choose so.
Another group probably operating from Iran called Cyber Toufan claimed to have breached dozens of Israeli organizations and has promised to dump stolen data online over the coming month. While the group poses as a grassroots Hamas activist organization, it is likely driven by political command from Tehran where it probably takes residence. In addition to Israeli organizations, Cyber Toufan claims to have also breached international firms doing business in Israel.
ETLM Assessment:
As Israel’s military campaign in Gaza continues in response to Hamas’ Oct. 7 attacks, the United States is contending with regional provocations by Iranian proxies. There have now been more than 100 attacks against U.S. and allied forces based in Iraq and Syria since mid-October, and repeated attacks by the Houthis in Yemen. More than 100 drones and missiles were fired in recent weeks against vessels in the Red Sea and Israel, in addition to low-level cyber-attacks against Israel and countries that support it. Washington announced the establishment of a multinational naval task force dubbed Operation Prosperity Guardian, to support freedom of navigation in key Red Sea waterways. America’s broad approach has thus far been primarily reactive in nature and limited in scope, though media reports suggest at least some debate within
U.S. President Joe Biden’s administration over a more robust response. In such a case, cyber-attacks by Iran and Iran-aligned forces are increasingly likely with a special focus on logistical hubs and other parts of critical infrastructure, which faces heightened risks from advanced threat actors.
Rise in Malware/Ransomware and Phishing Contimade is Impacted by the LockBit 3.0 Ransomware
Attack Type: Ransomware
Target Industry: Manufacturing
Target Geography: Czech Republic
Ransomware: LockBit 3.0 Ransomware
Objective: Data Theft, Data Encryption, Financial Gains
Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the Czech Republic; (www[.]contimade[.]cz), was compromised by LockBit 3.0 Ransomware. Contimade has been engaged in the production of containers and the development of modular solutions, which are currently being used throughout Europe, namely in Germany, Iceland, Belgium, Switzerland, Lithuania, the Netherlands, Scandinavia, the Czech Republic, and many other countries. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:
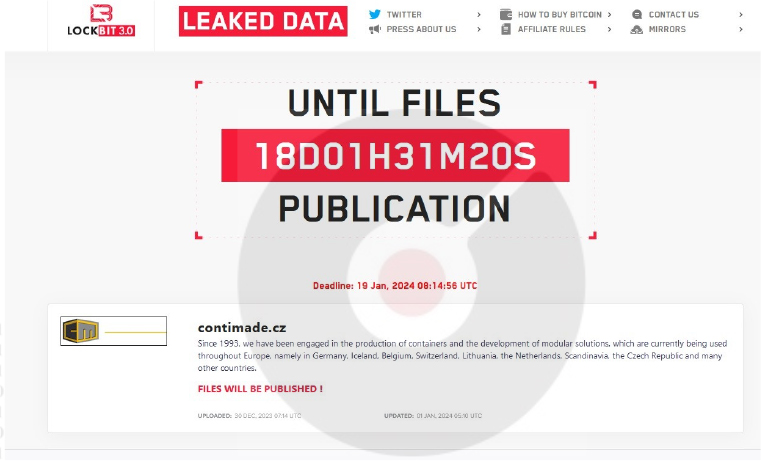
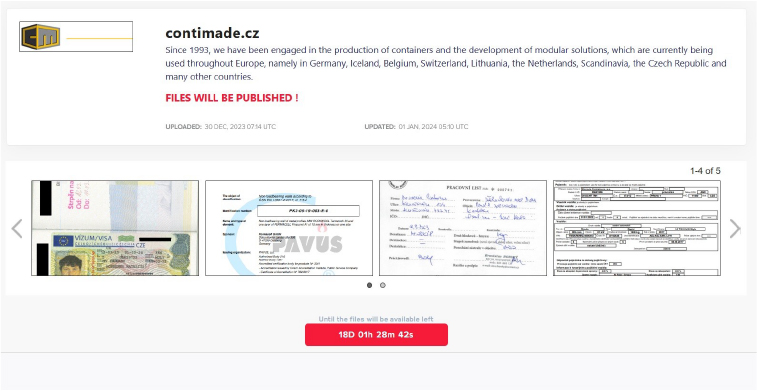
Source: Dark Web
Relevancy & Insights:
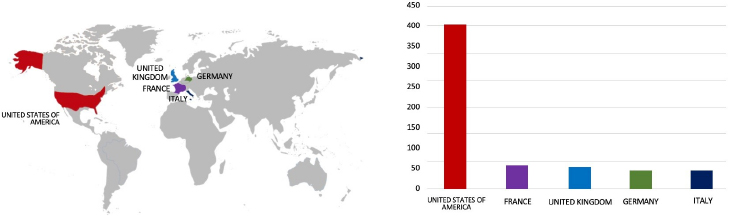
ETLM Assessment:
CYFIRMA assesses that LockBit 3.0 Ransomware remains a significant and ongoing global threat to companies across the world. Our observations indicate a growing trend where LockBit 3.0 Ransomware is actively leveraging vulnerabilities and exploits within various products to establish initial access, subsequently enabling lateral movement within organizational networks. The recent incident involving the targeting of Contimade, a manufacturing company based in the Czech Republic, underscores the pervasive global risk posed by this ransomware strain.
Vulnerability in Apache OpenOffice
Attack Type: Vulnerabilities & Eploits
Target Technology: Office Application
Vulnerability: CVE-2023-47804 (CVSS Base Score 8.8)
Vulnerability Type: Input validation error
Summary:
The vulnerability allows a remote attacker to compromise the affected system.
Relevancy & Insights:
The vulnerability exists due to insufficient validation of user-supplied input when executing internal macro with arbitrary arguments.
Impact:
A remote attacker can trick the victim into opening a specially crafted file, bypass the user approval for opening the links from the document, and execute arbitrary scripts on the system.
Affected Products: https[:]//www[.]openoffice[.]org/security/cves/CVE-2023-47804.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
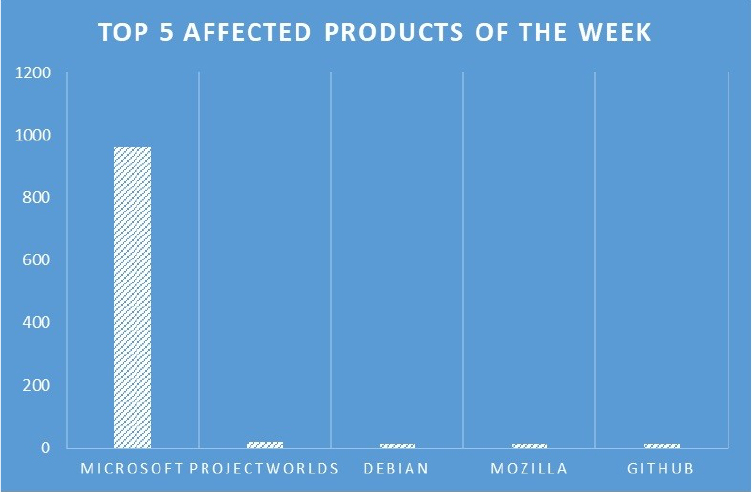
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
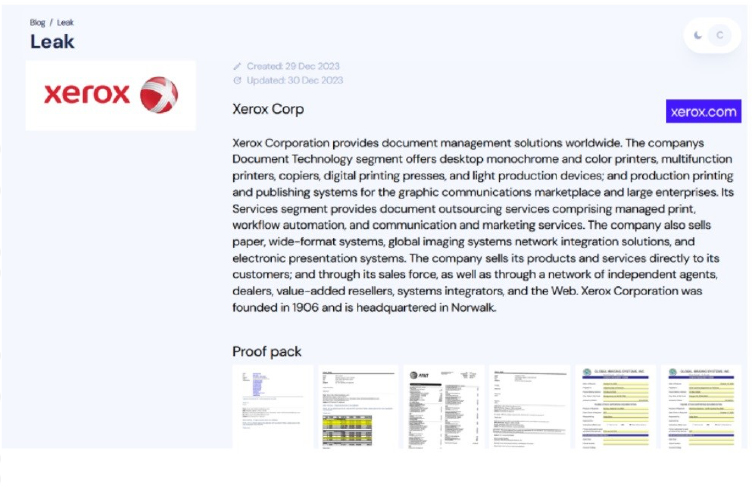
The INC RANSOM ransomware group claims to have hacked the American multinational corporation Xerox Corp
Threat Actors: INC RANSOM
Attack Type: Ransomware
Objective: Data Leak, Financial Gains
Target Technology: Web Application
Target Geographies: USA
Target Industry: Electronics
Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
The INC RANSOM ransomware group claims to have hacked the American multinational corporation Xerox Corp. The latter delivers document management solutions on a global scale. Within its Document Technology segment, the company provides an array of products, including desktop monochrome and color printers, multifunction printers, copiers, digital printing presses, and light production devices. Additionally, Xerox offers advanced production printing and publishing systems tailored for both the graphic communications marketplace and large enterprises. The INC RANSOM group added Xerox to the list of victims on its Tor leak site. The ransomware group published the images of eight documents, including emails and an invoice, as proof of the hack.
Relevancy & Insights:
INC Ransom, a recently identified ransomware group, surfaced in August 2023 and has since asserted accountability for breaching over 40 organizations as of now. The modus operandi of these threat actors involves gaining access to their targets’ networks through spearphishing emails. However, their tactics have extended to utilizing Citrix NetScaler CVE-2023-3519 exploits, showcasing a multi-faceted approach to infiltrating systems and carrying out cyberattacks.
ETLM Assessment:
INC Ransom has directed its cyber-attacks toward organizations across diverse sectors, including healthcare, education, and government, and mainly targets the United States and Europe. CYFIRMA assesses INC Ransom will continue to target companies in the US and Europe which will result in large financial gains.
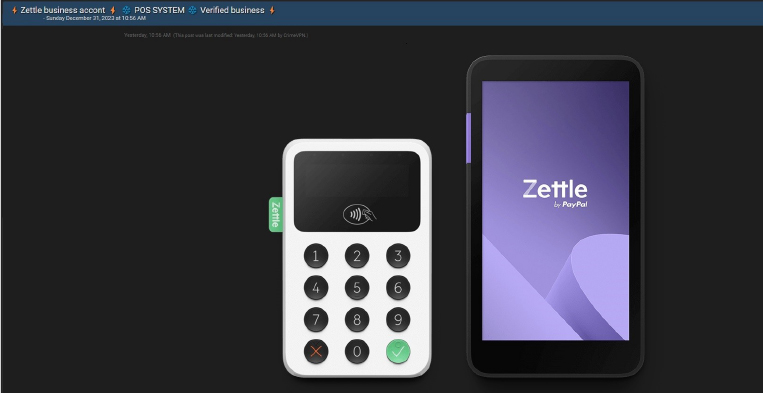
Zettle Data Advertised in Leak Site
Attack Type: Data Leaks
Target Industry: Finance
Target Geography: Sweden
Objective: Data Theft, Financial Gains
Business Impact: Data Loss, Reputational Damage
Summary:
CYFIRMA Research team observed a potential data leak related to Zettle, {www[.]Zettle[.]com}. Zettle builds game-changing commerce tools, such as mobile card readers and point-of-sale apps that empower small businesses to compete with the big players. Zettle is part of the PayPal family. The Zettle card readers make it possible for anyone to accept card payments – anytime, anywhere, while their intuitive free point-of-sale app, Zettle Go, helps users get paid, tracks sales, and lets them keep an eye on stock levels. Business-verified accounts are available for purchase at prices ranging from USD 100 to USD 150.
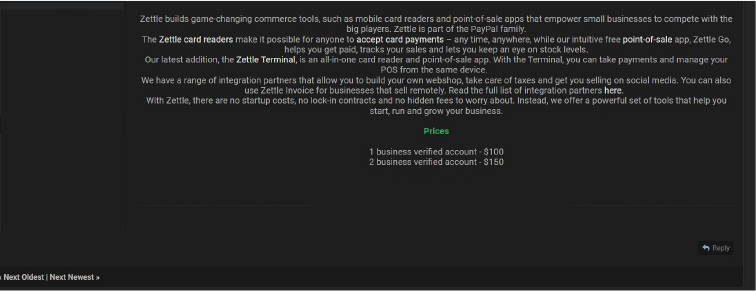
Source: Underground forums
Relevancy & Insights:
Cybercriminals driven by financial motives often seize opportunities presented by
exposed and vulnerable systems and applications. Many of these perpetrators actively participate in clandestine online forums where they discuss, and trade stolen digital assets. In contrast to some financially motivated groups, like ransomware or extortion groups that publicize their activities, these opportunistic attackers prefer to operate discreetly. They exploit unpatched systems or vulnerabilities in applications to gain unauthorized access and pilfer valuable data. Subsequently, they advertise the stolen data for sale in underground forums, where it may be resold and repurposed by other malicious actors in their attacks.
ETLM Assessment:
CrimeVPN, a recently emerged entity in the dark forum landscape, is primarily dedicated to selling VPNs. Simultaneously, they engage in advertising and selling data within dark forums for financial gain. In their ongoing data breach campaign, CrimeVPN is actively marketing verified account information. According to the CYFIRMA assessment, this new threat is honing in on financial organizations that may have insufficient security measures in place and is a threat to companies that hold significant PII information.
CYFIRMA Research team observed a potential data leak related to Cross-Switch,
{www[.]Cross-Switch[.]com}. Cross-Switch is an online payment gateway management company. The compromised data includes complete names, email addresses, phone numbers, messages, physical locations, banking details, bearer tokens, dates of birth (DOBs), usernames, and other confidential information.
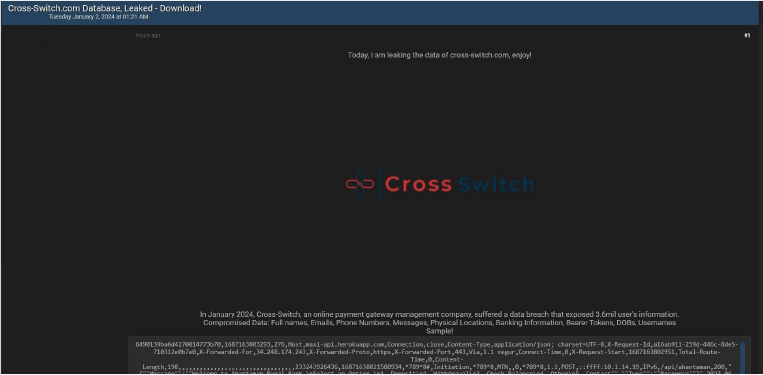
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS