



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Synapse ransomware as a service while monitoring various underground forums as part of our Threat Discovery Process.
Synapse Ransomware
Synapse ransomware was discovered in the wild at the end of February 2024, coinciding with the launch of their Ransomware-as-a-Service (RaaS) platform during the same month.
The threat actor claims their Ransomware-as-a-Service (RaaS) has advanced features. It promises no file corruption, fast encryption with five modes including full file encryption.
Other features include quick file listing, network access impersonation, and silent encryption to evade detection. Encryption priority and network scanners are also highlighted. Worm propagation methods through WMI and SMB services are touted for widespread impact, emphasizing its sophistication.
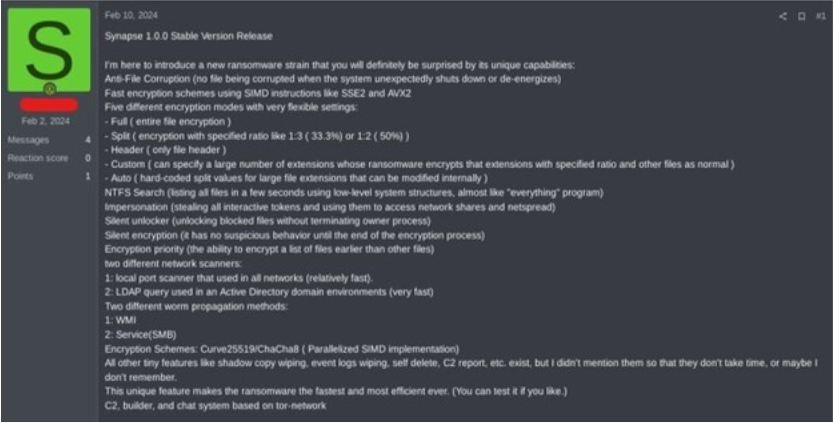
Screenshot of a Russian hacker forum post (Source: Surface Web)
The researchers uncovered a Synapse ransomware sample in the wild designed to encrypt files and extort ransom for their decryption. This malicious software appends a combination of random characters and the “.Synapse” extension to encrypted files. Furthermore, it drops a ransom note named “[Random Characters]. Readme.txt” post-encryption, detailing instructions for payment and data recovery.
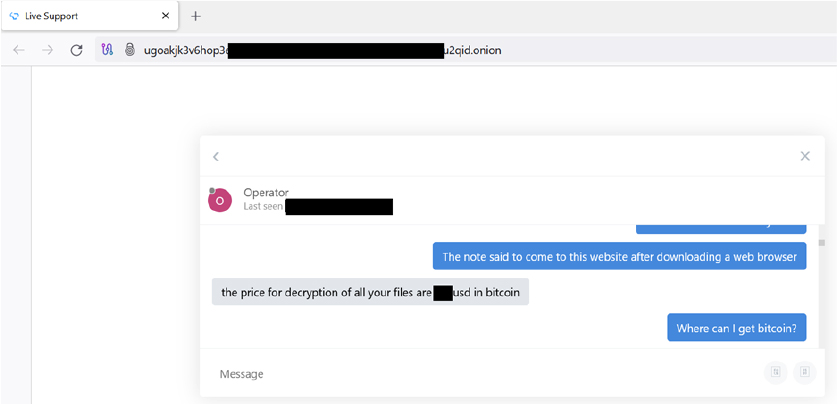
The ransomware borrowed features from Lambda ransomware linked to the VoidCrypt group, as well as Proxima and Lockbit3. Unlike some other ransomware, Synapse doesn’t have a data leak site. Instead, the affiliates communicate with the victims through an onion- based service for ransom negotiations.
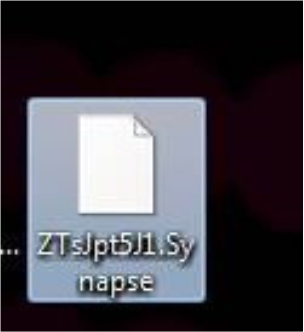
Screenshot of files encrypted by Synapse ransomware(Source: Surface Web)
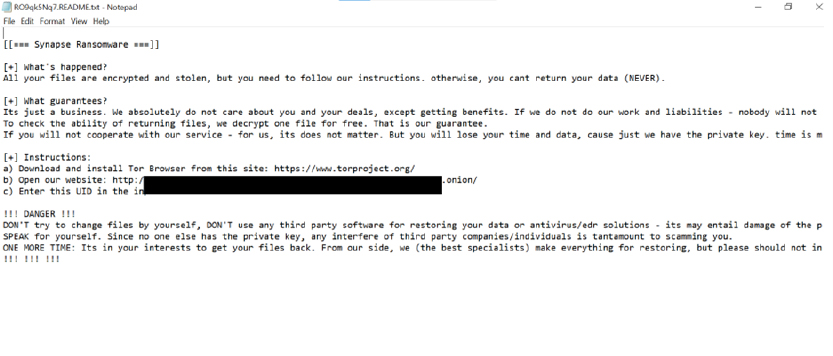
Screenshot of Ransom note. (Source: Surface Web)
The Ransomware modifies the desktop wallpaper and asks the victim to open the Ransom note as below.
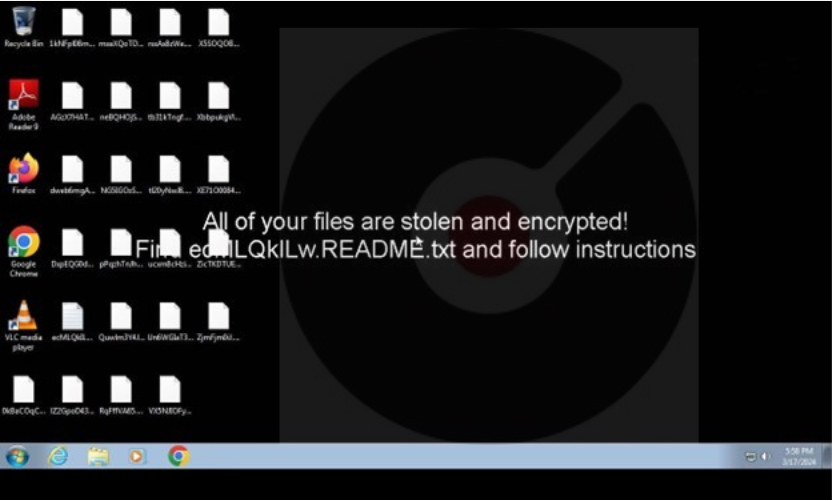
Screenshot of Desktop (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.004: Boot or Logon Autostart Execution: Winlogon Helper DLL | ||
| 4 | TA0004: Privilege Escalation | T1543.003: Create or Modify System Process: Windows Service |
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.001: Indicator Removal: Clear Windows Event Logs | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1134.001: Access Token Manipulation:Token Impersonation/Theft | ||
| T1222: File and Directory Permissions Modification | ||
| 6 | TA0006: Credential Access | T1056: Input Capture |
| 7 | TA0007: Discovery | T1007: System Service Discovery |
| T1012: Query Registry | ||
| T1016: System Network Configuration Discovery | ||
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 8 | TA0008: Lateral Movement | T1080: Taint Shared Content |
| T1091: Replication Through Removable Media | ||
| 9 | TA0009: Collection | T1056: Input Capture |
| T1074: Data Staged | ||
| T1113: Screen Capture | ||
| T1213: Data from Information Repositories | ||
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1090: Proxy | ||
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop |
Relevancy and Insights:
ETLM Assessment:
Sigma Rule
title: Disable Windows Event Logging Via Registry tags:
– attack.defense_evasion
– attack.t1562.002 logsource:
category: registry_set product: windows
detection: selection:
T a r g e t O b j e c t | s t a r t s w i t h : ‘HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\’
TargetObject|endswith: ‘\Enabled’ Details: ‘DWORD (0x00000000)’
filter_main_wevutil:
Image|endswith: ‘\Windows\system32\wevtutil.exe’ # FP generated during installation of manifests via wevtutil
filter_main_iis:
Image|startswith: ‘C:\Windows\winsxs\’
Image|endswith: ‘\TiWorker.exe’ # Many different TargetObjects filter_main_svchost:
Image: ‘C:\Windows\System32\svchost.exe’ TargetObject|contains:
– ‘\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows- FileInfoMinifilter’
– ‘\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows- ASN1\’
– ‘\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows- Kernel-AppCompat\’
– ‘\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows- Runtime\Error\’
– ‘\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows- CAPI2/Operational\’
filter_main_trusted_installer:
Image: C:\Windows\servicing\TrustedInstaller.exe
T a r g e t O b j e c t | c o n t a i n s : ‘\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-Compat- Appraiser’
filter_optional_empty: # This filter is related to aurora. Should be removed when fix is deployed. # TODO: Remove later
Image: ”
filter_optional_null: # This filter is related to aurora. Should be removed when fix is deployed. # TODO: Remove later
Image: null
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_* falsepositives:
– Rare falsepositives may occur from legitimate administrators disabling specific event log for troubleshooting
level: high
(Source: Surface web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
Type: Backdoor
Objective: Espionage, Data Exfiltration Threat Actor: Earth Krahang
Target Technology: Linux OS & Server
Target Geography: Southeast Asia, Africa, and South America
Active Malware of the Week
This week “DinodasRAT (aka Linodas)” is trending.
DinodasRAT
Recently, researchers have observed the Linux version (v11) of DinodasRAT, also known as Linodas, which has garnered less public attention compared to its Windows counterpart despite its advanced nature. They noted its maturity and specialized capabilities tailored for Linux servers. Additionally, the latest version introduces an evasion module designed to conceal its presence by modifying the execution of system binaries. Researchers have been closely monitoring a Chinese-linked cyber espionage threat actor targeting Southeast Asia, Africa, and South America, aligning with the Earth Krahang group. They utilize the DinodasRAT (XDealer) cross-platform backdoor, previously seen in attacks by Chinese actor LuoYu.
Attack Method
The Linux backdoor operates differently from its Windows counterpart, particularly concerning persistence and execution permissions. Upon execution, the backdoor checks for specific arguments (the letter d, and the calling daemon process ID) determine if it’s the first run. If these arguments are absent, it establishes persistence by calling the daemon function. It then re-runs itself properly by obtaining its process ID and self-execution path, executing a command through the system function.
Persistence Methods
The persistence process is extensive, spanning multiple Ubuntu versions and RedHat distributions. It begins by checking the current OS version through files like /proc/version and /etc/lsb-release, parsing the output. It then employs one of several methods to achieve persistence based on the gathered data.
Method 1 (Ubuntu) – rc.local enabled via system
The malware checks for the existence of specific files and directories before proceeding with persistence tasks. If the file `/lib/systemd/system/rc.local.service` doesn’t exist, it writes a string into it and creates a symlink (/lib/systemd/system/rc.local.service → /etc/systemd/system/). Then, it checks for the existence of `/etc/rc.local` and appends a string to it if found. After making `/etc/rc.local` executable, it validates the persistence and adjusts INI fields in `/lib/systemd/system/rc.local.service`.
Method 2 (Red Hat) – init.d script
The backdoor first executes a command to check if `chkconfig` is available and functioning correctly, adding it to the PATH environment variable if found. It then checks if a specific file (/etc/init.d/[SELF_FILE_NAME]) doesn’t exist and writes data into it if necessary. If the file isn’t created, it writes the same data to another file (/etc/ch.sh), executes a command to move it, and sets permissions before execution. To validate persistence, the backdoor runs `chkconfig –list | grep [SELF_FILE_NAME]`. If the result lacks “6:”, it executes two subsequent commands.
Method 3 (Red Hat) – rc.local
Persistence is achieved through the `/etc/rc.d/rc.local` file. The backdoor verifies if the file exists and checks if its self-path is already present within its contents. If not, it appends itself to the file using the string “\n[SELF_PATH]\n”.
Core Logic
After successful execution with two arguments, the backdoor proceeds to its main logic. It begins with a series of checks including root privilege, its folder path, and the calling daemon process ID, storing them in global variables. It then updates its file timestamp and those of related files using the touch command to blend in with the filesystem.
Subsequently, it reads a config file typically located at /etc/.netsc.conf. This file, usually hidden, contains various settings. It attempts to retrieve an “imei” field under the “para” section, representing the bot ID. If absent, it generates a unique machine ID based on system parameters in the following way:
After generating the bot ID, it follows the format “Linux_[TIMESTAMP]_[MD5SUM]_[RANDOM NUMBER]_V11” (e.g.,
Linux_20240310_11cb06d0bf454c3708a3658c2601ea16_40459_V11). This ID is then saved to the config file, and the config file’s timestamp is updated similarly to the executable.
Subsequently, the backdoor performs basic system enumeration to gather distribution, exact OS version, and system architecture details, storing them in global variables for later use when contacting the C2 for the first time. The C2 address, parsed from “update.microsoft-setting[.]com:443” in the latest version, is stored, along with mode and checkroot fields read from the config. Mode specifies the type of C2 communication (TCP or UDP), while checkroot determines whether the backdoor monitors logged-in users.
Following initial configuration, the backdoor creates multiple threads for monitoring and cleanup and initiates a connection to the C2 server.
Monitoring/Cleanup Threads
The backdoor spawns five threads dedicated to system monitoring, downloading helper modules, and cleaning up old reverse shell connections.
Thread #1: Logged-in user monitor.
Thread #2: C2 connection status monitoring
Thread #3: Filter modules download and setup.
Thread #4: Logged-in users monitor and logging.
Thread #5: Reverse shell old sessions cleanup
C2 Communication
Before initiating C2 communication, checks are made on two global structs: one determines TCP or UDP protocol for connection, and the other dictates whether communication halts with logged-in users. If these checks fail, C2 communication is aborted. Otherwise, the backdoor parses the C2 address (host and port), resolving a C2 domain to IPv4 if necessary. After configuring the socket in TCP or UDP mode as per the settings, the malware endeavors to establish a connection with the C2. Upon successful connection, a thread for interpreting C2 commands is initiated. Following the establishment of this primary connection and the creation of the C2 command thread, an infinite loop is executed, responsible for dispatching a heartbeat to the C2 server. The heartbeat contains the following values combined and separated by \t:
If the initial request to the C2 fails, the backdoor attempts to reestablish the connection, and the process of generating and sending the heartbeat string is repeated.
The Filter Module
In DinodasRAT v11, Thread #3 is responsible for downloading an additional module that replaces specified binaries in the system, a functionality absent in previous versions. The received filter module, named ntfsys.so6, is installed by a separate thread, which substitutes certain system binaries with it. This module acts as a proxy, controlling the output of the replaced binaries. This is how it’s done step by step:
The module serves as a rudimentary “rootkit” for threat actors, enabling them to filter values like IP, username, and process name from system utilities such as who, netstat, and ps. This tactic helps conceal DinodasRAT and its traces from vigilant victims’ monitoring efforts.
INSIGHTS
ETLM ASSESSMENT
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Threat Actor in Focus: China State-Affiliated Cyber Group APT31
Summary:
Relevancy & Insights:
APT31; a cyber threat group linked to China’s Ministry of State Security, has been accused by Finland and targeted by the US and UK for orchestrating extensive cyber espionage campaigns. Using techniques such as spear phishing, APT31 targets government institutions, businesses, and individuals across the western countries, including the UK Parliament, to gather sensitive information. Their motive, believed to be aligned with China’s strategic interests, encompasses disrupting democratic processes, influencing public discourse, and gaining geopolitical advantage. Despite China’s denial of involvement, the persistent threat posed by APT31 underscores the importance of international cooperation and robust cybersecurity measures to counter state-sponsored cyber-attacks and protect national security.
ETLM Assessment:
APT31; also known as Judgement Panda or Zirconium, operates as a sophisticated cyber threat group with ties to the Chinese Ministry of State Security. While its activities have drawn significant attention in the UK, particularly for targeting democratic institutions like the Parliament and the Electoral Commission, APT31’s reach extends beyond the UK’s borders. Notably, the group has targeted parliamentary systems in the US and Finland as well, indicating the expansion of the global scope of operations. In terms of target industries, APT31 displays a wide-ranging focus, encompassing government institutions, political organizations, critical infrastructure, financial institutions, IT Services, and healthcare providers. By infiltrating these sectors, the group aims to gather sensitive information that could provide strategic advantages to the Chinese government. Their recent activities have involved cyber espionage campaigns targeting businesses, government officials, dissidents, and politicians, demonstrating a broad scope of interest. The primary objective of APT31 is cyber espionage, with a specific focus on exfiltrating victim emails. This aligns with their goal of gathering intelligence on government policies, political strategies, and other sensitive information that could be leveraged to advance Chinese interests. The group’s tactics often involve sophisticated techniques such as spear phishing, zero-day exploits, and living off the land attacks, enabling them to maintain persistent access to compromised networks while evading detection. Its operations span across various industries and geographies, demonstrating a strategic effort by the Chinese government to advance its geopolitical interests and gather intelligence on foreign adversaries.
Recommendations:
Chinese threat actors target ASEAN entities
Researchers have recently published findings on two Chinese APTs that are
conducting cyber espionage against entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN). The first threat actor; Stately Taurus, launched malware campaigns earlier this month against organizations in Myanmar, the Philippines, Japan, and Singapore. The second threat actor has targeted government entities in Cambodia, Laos, and Singapore. This group compromised at least one entity associated with ASEAN.
ETLM Assessment:
ASEAN-affiliated organizations handle sensitive information on diplomatic relations and economic choices in the region, making them desirable targets for espionage operations. This recently reported activity is part of standard nation-state cyber espionage efforts, with many similar undetected operations probably underway at the same time.
The Hunters International Ransomware impacts the Sysmex
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; (www[.]sysmex[.]com), was compromised by the Hunters International Ransomware. Sysmex Corp. develops, manufactures, imports, exports, and sells clinical laboratory instruments, reagents, and software used in in-vitro diagnostics. The compromised data contains highly confidential and sensitive information pertaining to the organization.
The following screenshot was observed published on the dark web:
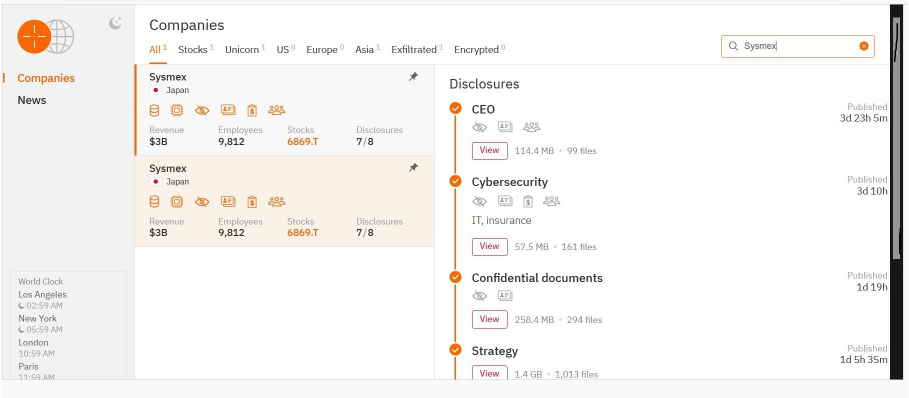
Source: Dark Web
Relevancy & Insights:
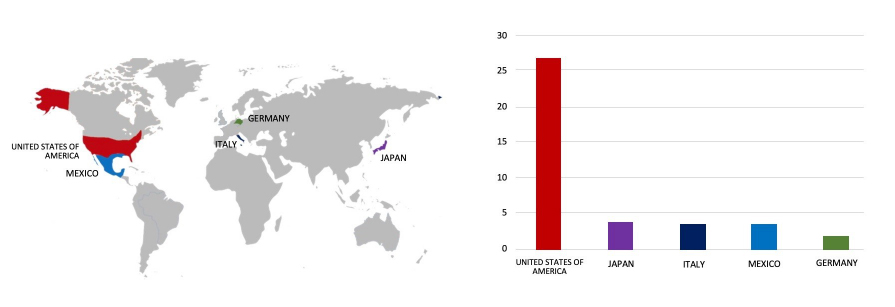
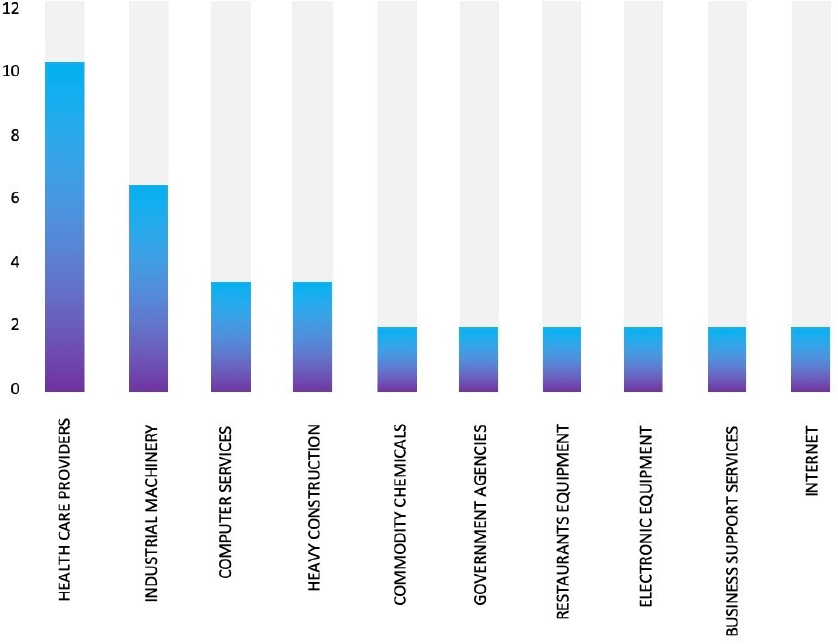
ETLM Assessment:
CYFIRMA’s assessment based on the available information suggests that Hunters International ransomware will persist in targeting a wide range of global industries, with a notable focus on the United States, European, and Asian countries. Additionally, the target organization has its offices, distributors, and customers in Southeast Asia, and Oceania, which can be possibly targeted by ransomware groups as part of the pivoting attack. Its heightened emphasis on data theft, rather than just encryption, indicates a higher level of sophistication, posing a more significant threat to victims. Its design for stealthy operations during idle periods could make detection and mitigation more challenging.
The LockBit 3.0 Ransomware impacts RJ CORP LIMITED
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from India; (www[.]rjcorp[.]in), was compromised by the LockBit 3.0 Ransomware. RJ CORP LIMITED is an international brand specializing in the Food & Beverages Industry in India. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:

Source : Dark Web
Relevancy & Insights:
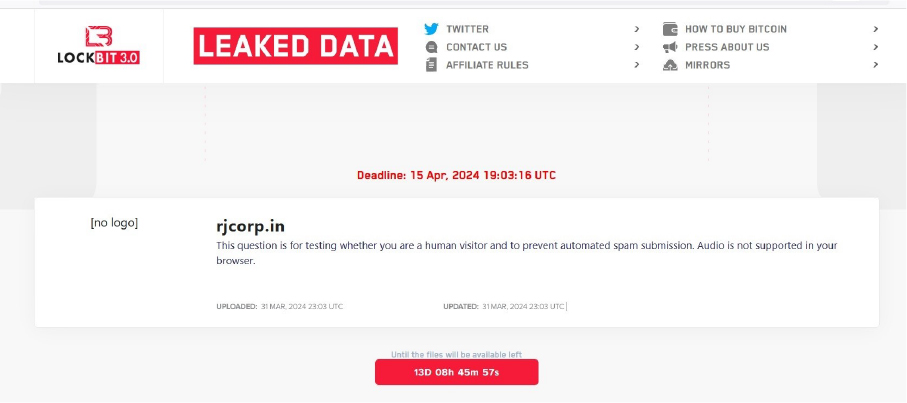
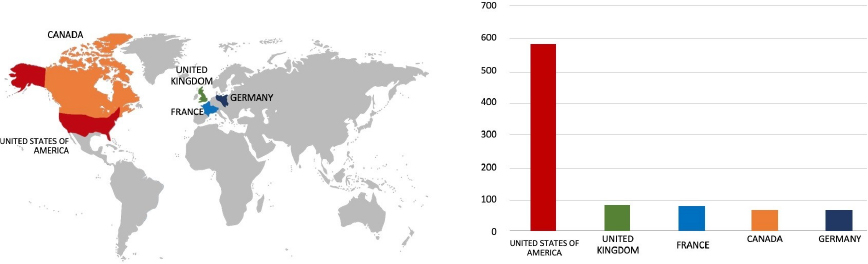
ETLM Assessment:
CYFIRMA’s assessment underscores the persistent and widespread threat posed by LockBit 3.0 Ransomware to companies worldwide. Our observations reveal an escalating pattern, wherein LockBit 3.0 Ransomware exploits vulnerabilities in diverse products to infiltrate systems, facilitating lateral movement within organizational networks. The recent cyber incident involving the RJ CORP LIMITED; India based Food & Beverage company, highlights the pervasive global danger associated with this ransomware variant. The target organization has a global presence with considerable office presence in multiple countries in Southeast Asia, and Africa, indicating that these regions could also be targeted by the ransomware groups.
Vulnerability in VMware SD-WAN Edge
Command Summary:
The vulnerability allows a remote attacker to execute arbitrary shell commands on the target system.
Relevancy & Insights:
The vulnerability exists due to improper input validation. A remote unauthenticated attacker with access to the Edge Router UI during activation can send specially crafted request to the application and execute arbitrary OS commands on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable system.
Affected Products: http[:]//www[.]vmware[.]com/security/advisories/VMSA-2024-0008[.]html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
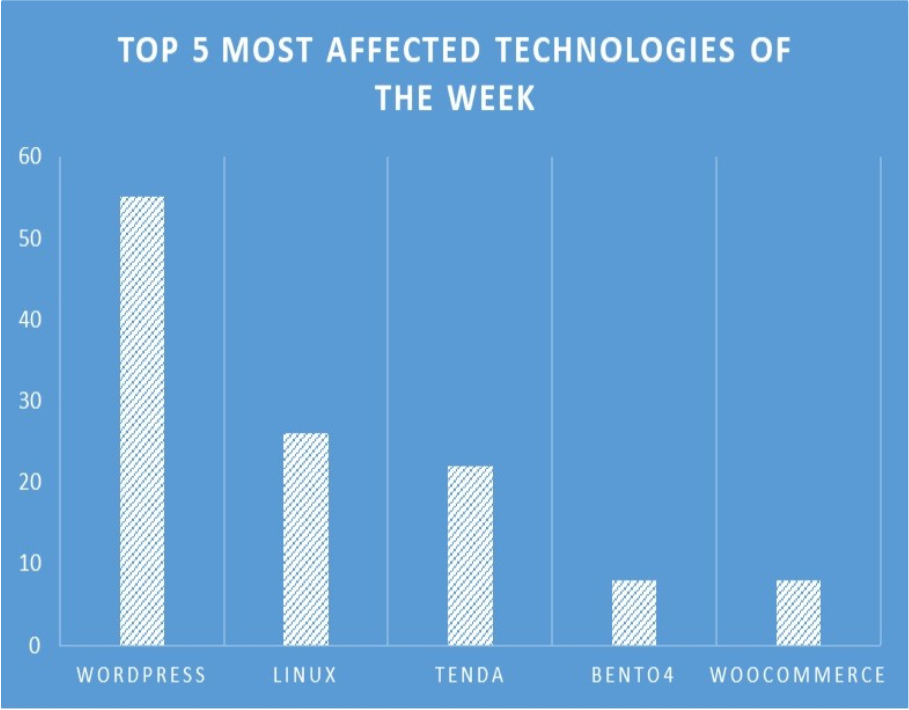
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
In the early months of 2024, CYFIRMA has observed Chinese nation state threat actor Volt Typhoon has exploited the weakness in VMWare products, targeted Critical Infrastructure, Energy, Private Sectors, Telecommunications, Defence, Government industries in the US, African region, allies of the US globally for espionage activities and operational disruptions.
INC Ransom claimed an attack on NHS Scotland
Summary:
Recently the infamous INC Ransom group claimed responsibility for the cyber-attack on NHS D&G and listed the trust as a victim on its data leak site. The group claimed to have 3 terabytes of data stolen from the trust and shared several samples of the stolen data to prove its authenticity. The sample documents contained sensitive information about doctors and patients, including their medical assessments, analysis results, and psychological reports. NHS Scotland is the national branch of the UK’s National Health Service and looks after the 14 Scottish regions, including NHS Dumfries and Galloway, which announced a serious cyberattack earlier in March month.
Relevancy & Insights:
INC Ransom has emerged as a relatively fresh addition to the cybercriminal landscape, making its debut in July 2023 and adopting a strategy of indiscriminate targeting. Its most notable achievement thus far has been the successful breach of Xerox Business Solutions; a subsidiary of the renowned tech conglomerate Xerox, previously known as Global Imaging Systems.
ETLM Assessment:
INC Ransom has targeted a selection of multiple industries, which include Healthcare, Education, Logistics, Manufacturing, IT Services, and NGOs, demonstrating its indiscriminate approach to victim selection. Despite its relatively brief tenure in the ransomware arena, the group has left a trail of attacks across diverse industries. An ongoing assessment by CYFIRMA suggests that INC Ransom targeted South America, North America, and Europe, with possible expansion to other geographies such as Africa & Asia, propelled by its relentless pursuit of significant financial gains through ransomware activities.
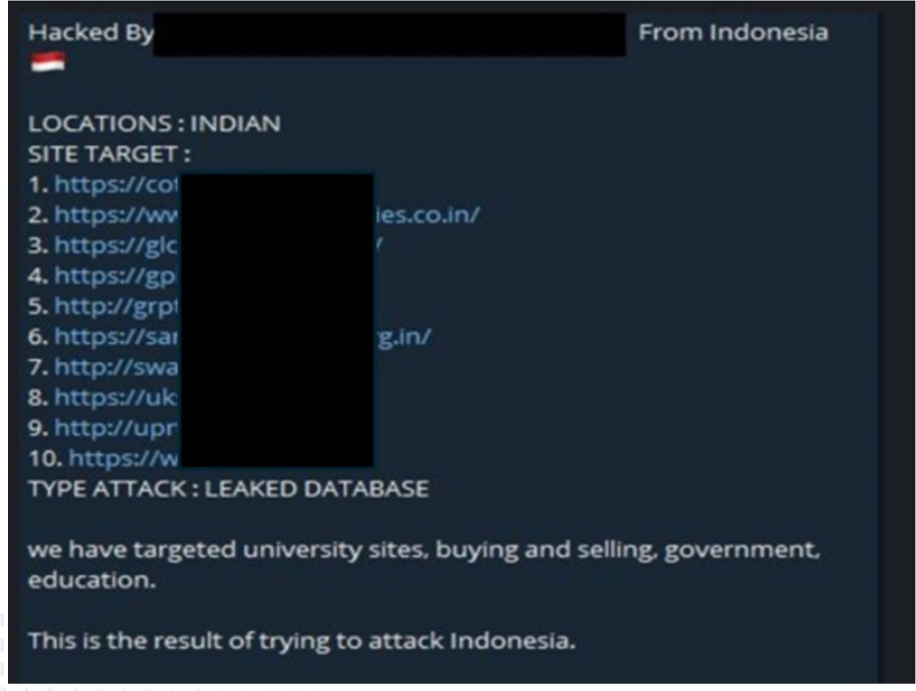
10 Indian websites’ data advertised on the Leak Site
Summary:
The CYFIRMA Research team observed a potential data sale related to 10 Indian organizations. An Indonesian threat actor, “ZALCYBER,” associated with the “Eagle Error System” group is selling data of 10 Indian organizations on the Telegram Channel.
Source: Telegram
Relevancy & Insights:
Financially driven cybercriminals constantly seek out exposed and vulnerable systems and applications for potential exploitation. Many of these actors lurk within Telegram Channels, engaging in discussions related to cybercrime and trading stolen digital assets. These opportunistic attackers prefer to operate covertly and exploit unpatched systems or vulnerabilities in applications to gain unauthorized access and pilfer valuable data. This stolen data is subsequently advertised for sale within underground markets and Telegram Channels, where it may be acquired, repurposed, and utilized by other malicious actors in their illicit endeavors.
ETLM Assessment:
According to CYFIRMA’s assessment, the Indonesian threat actor ZALCYBER is a financially motivated group and could target any organization and sell their sensitive data in dark web/underground forums for monetary benefits. The targeted institutions lacked robust security postures and were susceptible to potential cyberattacks orchestrated by this threat actor.
Recommendations: Enhance the cybersecurity posture by
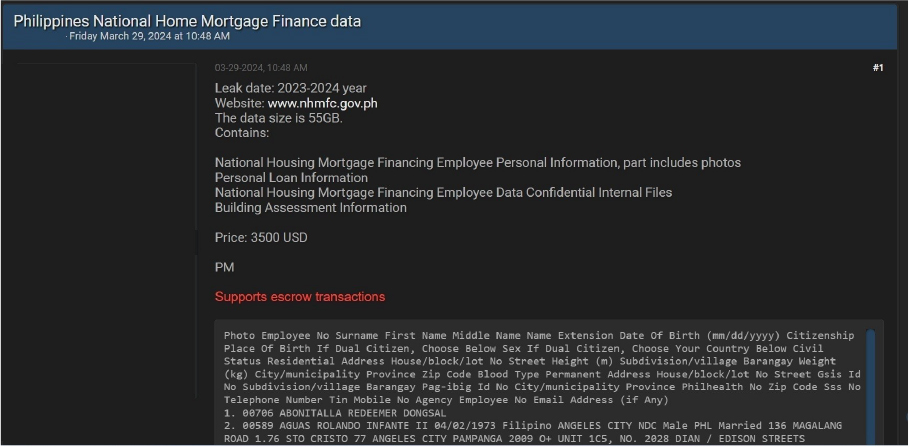
Philippines National Home Mortgage Finance data advertised on the Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to Philippines National Home Mortgage Finance, {www[.]nhmfc[.]gov[.]ph}. National Home Mortgage Finance Corp is a company that operates in the Financial Services industry. The data being offered for sale comprises personal information of National Housing Mortgage Financing employees, including personal loan details, internal files marked as confidential, building assessment information, and some containing photographs. The total size of the data for sale is 55GB, priced at 3500 USD.
Source: Underground Forums
ETLM Assessment:
A newly identified threat actor, dubbed “Applelp,” has emerged with financial motives, actively selling data from the Philippines National Home Mortgage Finance in online forums. The data being peddled includes personally identifiable information (PII), financial records, and other confidential data. This poses a significant risk to the affected organization and individuals, emphasizing the importance of robust cybersecurity measures to safeguard sensitive information from such malicious activities.
CYFIRMA Research team observed a potential data leak related to HSBC & Barclays banks, {www[.]hsbc[.]com, and www[.]home[.]barclays}. HSBC Holdings plc, the parent company of HSBC, is headquartered in London. HSBC serves customers worldwide from offices in 66 countries across Europe, Asia, North America, Latin America, the Middle East, and North Africa. Likewise, Barclays is a transatlantic consumer and wholesale bank offering products and services across personal, corporate, investment banking, credit cards, and wealth management, with a global presence. The compromised data includes sensitive information such as ID numbers, entity IDs, registration IDs, new status updates, link IDs, and other confidential details.
Source: Underground forums
ETLM Assessment:
CyberNiggers threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS