



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found ELPACO-team Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
ELPACO-team Ransomware
Researchers have uncovered a new ransomware strain named ELPACO-team, which is designed to both encrypt and rename files. After encrypting the data, it appends the “.ELPACO-team” extension to each file. ELPACO-team also displays a ransom note on the pre-login screen, alerting victims before they access their system. Additionally, the ransomware generates a text file titled “Decryption_INFO.txt,” which contains the same ransom note, instructing victims on how to proceed with payment for decryption.

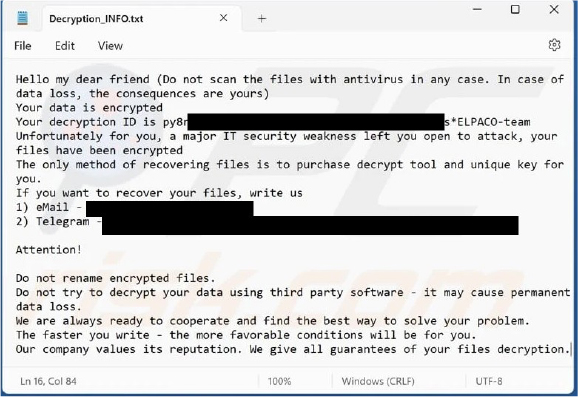
The ransom note from the ELPACO-team ransomware informs victims that their files have been encrypted due to a security vulnerability. It includes a decryption ID and instructs the victim to purchase both a decryption tool and a unique key to recover their files.
The note advises against scanning files with antivirus software, warning that doing so could lead to data loss. It also cautions against renaming encrypted files or using third-party decryption tools, as this may result in permanent loss of data.
Victims are directed to contact the attackers via email or Telegram. Additionally, the note suggests that quicker communication with the attackers could lead to more favourable terms for decryption.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1106: Native API | ||
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1546.012: Event Triggered Execution: Image File Execution Options Injection | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1547.008: Boot or Logon Autostart Execution: LSASS Driver | ||
| T1547.009: Boot or Logon Autostart Execution: Shortcut Modification | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 4 | TA0004: Privilege Escalation | T1055: Process Injection |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1546.012: Event Triggered Execution: Image File Execution Options Injection | ||
| T1547.008: Boot or Logon Autostart Execution: LSASS Driver | ||
| T1547.009: Boot or Logon Autostart Execution: Shortcut Modification | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 5 | TA0005: Defense Evasion | T1027.002: Obfuscated Files or Information: Software Packing |
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1564.003: Hide Artifacts: Hidden Window | ||
| T1574.002: Hijack Execution Flow: DLL Side- Loading | ||
| 6 | TA0006: Credential Access | T1056.001: Input Capture: Keylogging |
| T1539: Steal Web Session Cookie | ||
| 7 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 8 | TA0008: Lateral | T1091: Replication Through Removable Media |
| Movement | ||
| 9 | TA0009: Collection | T1056.001: Input Capture: Keylogging |
| T1113: Screen Capture | ||
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| T1573: Encrypted Channel | ||
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
Based on the available information, CYFIRMA’s assessment suggests that the ELPACO-team ransomware poses significant risks to various sectors, such as Manufacturing, Healthcare, Construction, Financial institutions and others, particularly in economically developed nations. By exploiting major IT security vulnerabilities, attackers expose organisations to severe data breaches. The increasing reliance on digital systems heightens the potential for operational disruptions and data loss across these industries. Furthermore, the ransom note’s advisories against using antivirus software and third-party decryption tools complicate recovery efforts, underscoring the critical need for robust cybersecurity measures to mitigate such threats. As a result, staying vigilant and adopting strong cybersecurity measures are essential to effectively mitigate these evolving threats.
SIGMA Rule:
title: Shell Open Registry Keys Manipulation tags:
– attack.defense-evasion
– attack.privilege-escalation
– attack.t1548.002
– attack.t1546.001 logsource:
category: registry_event product: windows
detection: selection1:
EventType: SetValue
TargetObject|endswith: ‘Classes\ms-settings\shell\open\command\SymbolicLinkValue’
Details|contains: ‘\Software\Classes\{‘ selection2:
TargetObject|endswith: ‘Classes\ms-settings\shell\open\command\DelegateExecute’ selection3:
EventType: SetValue TargetObject|endswith:
– ‘Classes\ms-settings\shell\open\command\(Default)’
– ‘Classes\exefile\shell\open\command\(Default)’ filter_sel3:
Details: ‘(Empty)’
condition: selection1 or selection2 or (selection3 and not filter_sel3) falsepositives:
– Unknown level: high
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Remote Access Trojan (RAT)
Objective: Espionage, Data theft, Remote Access
Target Technology: Windows OS
Target Geography: Russia
Active Malware of the Week
This week “DCRat” is trending.
DCRat
Researchers discovered that Russian-speaking users were being targeted with DCRat (aka Dark Crystal RAT), being delivered through HTML smuggling—a notable evolution in its distribution tactics that had not been previously observed for this malware. DCRat, active since 2018 and written in C#, is known for its typical RAT functions like executing shell commands, logging keystrokes, and stealing files and credentials. Historically, it has been spread through compromised websites, password-protected archives, and media such as Signal, Cobalt Strike Beacons, or spam emails containing macro-embedded attachments.
This new delivery method marks an evolution in its distribution tactics.
HTML smuggling
HTML smuggling is a payload delivery method where the malicious code is either embedded in the HTML or retrieved from a remote source. HTML smuggling is often obfuscated using compression, encoding, or encryption, allowing it to bypass network security and reach the victim’s browser more easily. Once the HTML renders in the browser, the malicious payload is restored to its original form. Anti-emulation measures may delay the transformation until user actions, like mouse movement, occur. The payload is then written to disk automatically or through user interaction, often following social engineering efforts by the attacker to encourage execution. This technique has been used by malware like Azorult, Pikabot, and now DCRat, demonstrating its effectiveness in facilitating the delivery of sophisticated threats.
Attack strategy
The initial delivery method of the HTML pages remains unknown; however, the threat actor cleverly used fake HTML pages impersonating popular Russian-language applications like TrueConf and VK Messenger to deceive users.
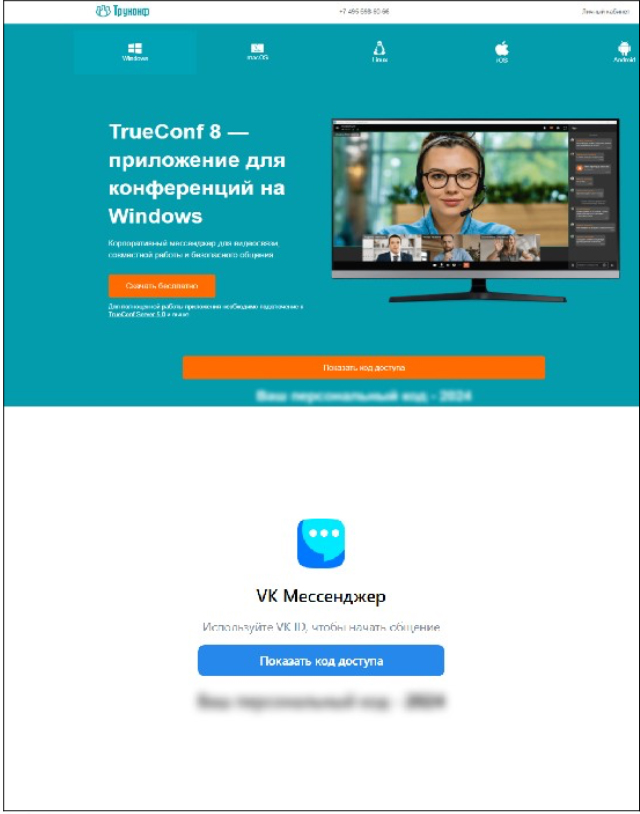
When opened in browsers like Chrome, Firefox, or Edge, the HTML files automatically downloaded a password-protected ZIP archive to the victim’s disk, with the password “2024” provided on the page. This technique evades detection by preventing security tools from accessing the encrypted payload. The smuggling code in the HTML files was based on an open-source GitHub repository, as indicated by the JavaScript structure.
DCRat execution flow
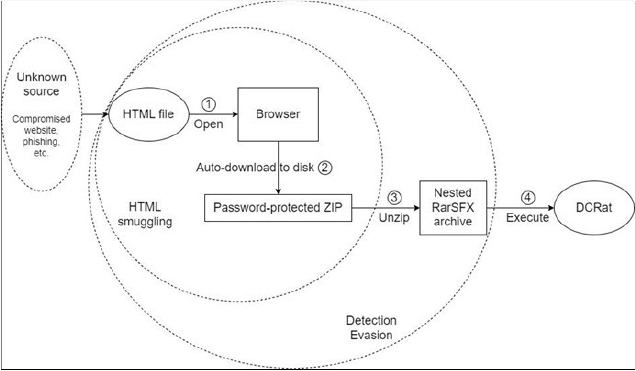
The initial password-protected ZIP payload contained a RarSFX archive mimicking applications like “trueconf.ru.exe” and “vk.exe.” This RarSFX archive held a batch file and another password-protected RarSFX archive, both using the password “riverdD.” The batch file executed the archive, providing the password via command-line, which then ran the embedded payload—DCRat, as confirmed by memory strings, mutex names, and C2 communication.
Password-protect to evade
In phishing campaigns, threat actors often send password-protected attachments, with the password included in the email body, relying on the user to open the file and enter the password. To bypass this dependency, attackers began using nested RarSFX archives, where the first archive automatically executes the password-protected RarSFX archive, eliminating the need for the user to input a password. However, in this case, the initial RarSFX archive was placed inside a password-protected ZIP file, requiring the user to decrypt the ZIP. While the embedded RarSFX archive was widely detected on VirusTotal, the password-protected ZIP had zero detections at the time of analysis, demonstrating how password protection aids in evading security mechanisms.
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that DCRat is likely to become a more prominent malware in cybercriminal campaigns, especially as attackers continue to refine its deployment techniques. With the malware becoming increasingly sophisticated at evading detection, organizations may face greater difficulties in identifying threats before significant damage occurs. This could result in a surge in data breaches, financial losses, and operational disruptions across various industries. As DCRat evolves, its global impact is expected to expand, reaching more sectors and regions. The malware-as-a-service model will continue to lower the entry barrier for threat actors, leading to more complex, multi-stage attacks that target a wider array of organizations worldwide.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
A Closer Look at Sparkling Pisces’ Tools: KLogExe and FPSpy
Summary:
Sparkling Pisces, a North Korean APT group also known as Kimsuky, THALLIUM, or Velvet Chollima, is infamous for its sophisticated cyberespionage and spear phishing campaigns, particularly targeting South Korean organizations and Japan. Recently, the group has broadened its scope to include attacks on Western countries as well.
Investigations have revealed new strains of malware, specifically KLogExe, and FPSpy, both showcasing advanced capabilities like keylogging, data exfiltration, and command execution. KLogExe operates as a keylogger, saving captured data in an INI file, while FPSpy, a DLL file, offers even more extensive functionalities, including multi- threading and the ability to download encrypted modules. Notably, both malware samples exhibit code similarities, suggesting a shared development lineage.
Relevancy & Insights:
Sparkling Pisces has a notable history of sophisticated cyberespionage, including significant attacks like the 2014 breach of Korea Hydro and Nuclear Power (KHNP). This breach aimed to collect sensitive information about South Korea’s energy infrastructure. The group typically targets government agencies, research institutions, energy companies, and large technology conglomerates.
The recent emergence of the KLogExe and FPSpy malware showcases the group’s evolving tactics and tools, building on their established focus on spear phishing and keylogging. This ongoing incident highlights a consistent pattern in their operational methods, highlighting Sparkling Pisces’ persistent commitment to espionage.
ETLM Assessment:
Sparkling Pisces primarily targets South Korea and Japan but has also extended its operations to Western countries the United States. Their focus includes government agencies and research institutions. The group employs various tactics, such as using email for spear phishing and PowerShell for stealthy malware execution. Recent malware developments include KLogExe and FPSpy, while earlier attacks utilized similar keyloggers and backdoors. They often exploit vulnerabilities in legitimate software and take advantage of user behavior, continuously adapting their methods over time. As the threat landscape evolves, Sparkling Pisces’s ability to innovate and enhance its malware toolkit poses ongoing risks.
Recommendations:
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1129 | Shared Modules |
| Persistence | T1574.002 | Hijack Execution Flow: DLL Side- Loading |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys/Startup Folder |
| Privilege Escalation | T1055.001 | Process Injection: DLL Injection |
| Defence Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defence Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defence Evasion | T1112 | Modify Registry |
| Defence Evasion | T1202 | Indirect Command Execution |
| Defence Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defence Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defence Evasion | T1036 | Masquerading |
| Defence Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1614 | System Location Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1087 | Account Discovery |
| Lateral Movement | T1021 | Remote Services |
| Collection | T1113 | Screen Capture |
| Collection | T1115 | Clipboard Data |
| Collection | T1119 | Automated Collection |
| Command and Control (C2) | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Indian hackers targeting Pakistan
Researchers have recently published a report on “SloppyLemming,” a cyberespionage actor that primarily targets Pakistani government, defense, telecommunications, technology, and energy sector organizations. The threat actor has also hit organizations in Bangladesh, Sri Lanka, Nepal, and China.
The same group is also known as “OUTRIDER TIGER,” and has a nexus with the government of India. The threat actor appears to have a particular focus on Pakistani police departments and other law enforcement agencies. Additionally, there are signs that the actor has also targeted organizations responsible for the operation and maintenance of Pakistan’s only nuclear power plant. Beyond Pakistan, SloppyLemming’s credential harvesting activities have mainly concentrated on government and military institutions in Sri Lanka and Bangladesh, with some attention also directed toward entities in China’s energy and academic sectors.
ETLM Assessment:
SloppyLemming is an advanced actor that uses multiple cloud service providers to facilitate different aspects of their activities, such as credential harvesting, malware delivery and command and control. The actor predominantly relies on open-source adversary emulation frameworks, such as Cobalt Strike, Havoc, and others. Targeted sectors predominantly consist of government entities within Pakistan and this campaign constitutes a classic state-driven espionage effort enabled by cyber means with many similar efforts probably underway at the same time.
Iranian hackers continue to target the Trump campaign
Researchers report on a continuous effort by an Iranian hacking group that appears to have continued access to the Trump campaign. Last week the threat actor shared apparent stolen materials with journalists, including a letter dated September 15th. The threat actor had previously stolen a vetting report on vice presidential nominee JD Vance and shared it with US news outlets last month.
Microsoft’s Threat Analysis Center and Google’s Threat Analysis Group have both observed Iranian state-sponsored targeting of US presidential campaigns. Tehran has denied allegations of its involvement.
ETLM Assessment:
Over the past two months, current and former intelligence officials, along with cyber threat researchers from the world’s largest IT companies, have presented growing evidence of Iran’s hacking activities. As our analysts have previously noted, Iran’s attempts to meddle in U.S. elections are not new – hackers tied to Iranian security services have been catching up to Russia and China’s information operations game and have been targeting presidential and midterm elections since at least 2018. In 2021, for instance, the U.S. Justice Department charged two Iranian hackers with election interference for posing as Trump supporters and sending threatening emails to Democrats. In 2018, during his previous term in office, President Trump unilaterally abandoned the 2015 nuclear accord that Tehran had signed with world powers and imposed waves of sanctions on the Islamic Republic, putting its economy under severe pressure. Iran’s long-term strategy is trying to maneuver the U.S. out of the Middle East, where Tehran intends to play the role of a dominant power. And to be able to fulfill this role, the Iranian regime does not want to deal with another Trump administration.
Iran is among world leaders in terms of using cyber warfare as a tool of statecraft. Iranian hackers have been repeatedly successful in gaining access to emails from an array of targets, including government staff members in the Middle East and the US, militaries, telecommunications companies, or critical infrastructure operators. The malware used to infiltrate the computers is increasingly more sophisticated and is often able to map out the networks the hackers had broken into, providing Iran with a blueprint of the underlying cyberinfrastructure that could prove helpful for planning and executing future attacks. Moreover, Iran is now supplementing its traditional cyberattacks with a new playbook, leveraging cyber-enabled influence operations (IO) to achieve its geopolitical aims. The scale of foreign disinformation targeting U.S. elections is increasing, especially with the use of artificial intelligence, which is making these efforts more sophisticated. The concerning part about AI is its ability to amplify disinformation at an exponential rate.
As we have outlined in our fresh report on the topic, looking forward, we can thus expect Iranian actors to employ all forms of statecraft including cyber-attacks against American institutions while simultaneously intensifying their efforts to sow internal divisions on US soil, driving the attention of both electorate and politicians inward.
These campaigns are likely going to be centered around amplifying existing divisive issues within the US, like racial tensions, economic disparities, and gender-related issues. This is a page from the Kremlin playbook, while the two countries cooperate more and more closely on countering the rules-based world order.
The Medusa Ransomware impacts AZPIRED
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the Philippines; AZPIRED (www[.]aspired[.]com), was compromised by the Medusa Ransomware. AZPIRED is a prominent outsourcing service provider based in the Philippines, specializing in a variety of business solutions tailored for clients primarily in the United States, Canada, and Australia. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 205 GB.
The following screenshot was observed published on the dark web:
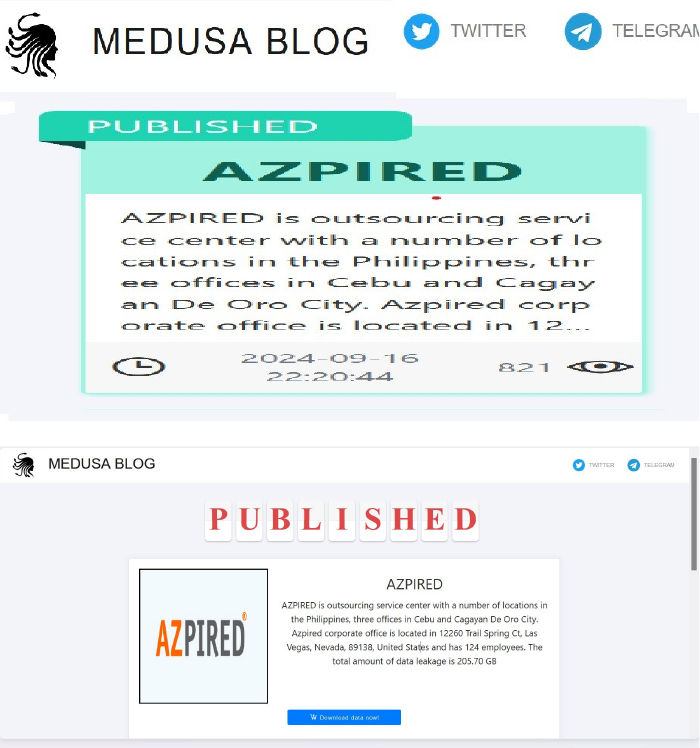
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, Medusa Ransomware continues to pose a significant threat across various sectors. The group’s sophisticated tactics and aggressive demands highlight the need for organizations to enhance their cybersecurity measures, including regular updates, employee training on phishing recognition, and robust incident response plans to mitigate risks associated with ransomware attacks.
The Brain Cipher Ransomware Impacts the Hanwa Co., Ltd. (Thailand)
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand; Hanwa Co., Ltd. (Thailand) (www[.]hanwa[.]co[.]th), was compromised by Brain Cipher Ransomware. Hanwa Co., Ltd. (Thailand) is a subsidiary of Hanwa Co., Ltd., a Japan-based global trading company. Established to expand Hanwa’s operations in Southeast Asia, this firm specializes in trading a diverse range of products, including steel, metals, food, petroleum, and chemicals. Leveraging its parent company’s extensive network, Hanwa Thailand aims to provide comprehensive trading solutions and foster strong business relationships in the region. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. The total size of the compromised data is approximately 200 GB.
The following screenshot was observed published on the dark web:

Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Brain Cipher Ransomware represents a growing threat in the cybersecurity landscape, particularly due to its focus on critical infrastructure and government entities. Organizations must enhance their cybersecurity measures, including robust incident response plans and employee training on recognizing phishing attempts, to mitigate risks associated with this evolving threat. Continuous monitoring and updating of security protocols are essential to defend against such sophisticated attacks.
Vulnerability in Zimbra Collaboration
Summary:
The vulnerability allows a remote attacker to execute arbitrary shell commands on the target system.
Relevancy & Insights:
The vulnerability exists due to improper input validation within the postjournal service. A remote unauthenticated attacker can pass specially crafted data to the application and execute arbitrary OS commands on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of a vulnerable systems.
Affected Products:
https://wiki[.]zimbra[.]com/wiki/Security_Center#ZCS_9.0.0_Patch_41_Released
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
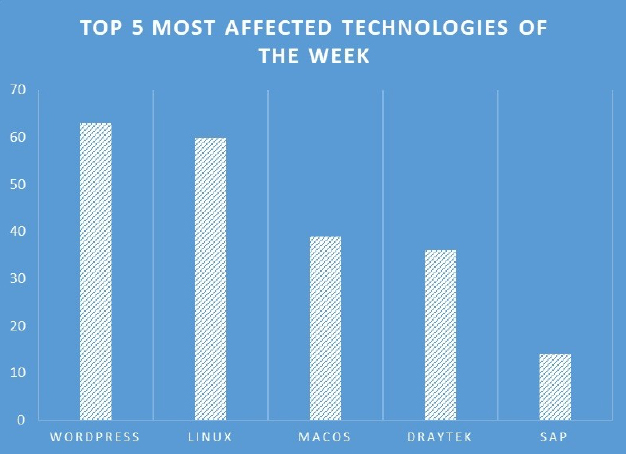
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Zimbra Collaboration can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Zimbra Collaboration is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding collaborative software activities, including email communication and web client services, across different geographic regions and sectors.
Orca Ransomware attacked and published the data of the Chernan Technology Co., Ltd.
Summary:
Recently, we observed that the Orca Ransomware attacked and published data of Chernan Technology Co., Ltd(www[.]chernan[.]com) on its dark web website. Chernan Technology Co. Ltd. is a Taiwanese company and a subsidiary of the Chernan Solder Group, specializing in the manufacturing and distribution of tin and related products. Chernan Metal Industrial Corp. provides a broad range of products, primarily used in electronics manufacturing, such as tin bars, wires, and pastes designed for soldering and circuit board applications. The data leak, following the ransomware attack, encompasses financial data, Invoices, Statements, Company infra, and others. The total size of the data breached is approximately 18 GB.

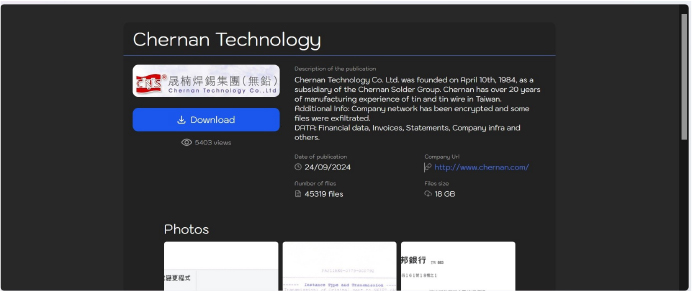
Relevancy & Insights:
ETLM Assessment:
Orca Ransomware remains a significant threat due to its effective encryption methods and aggressive double-extortion tactics. Organizations must adopt comprehensive cybersecurity measures to protect against this evolving threat and minimize potential impacts from ransomware attacks.
Kreen Data Advertised on a Leak Site
Summary:
In an alarming post on a prominent dark web forum, a threat actor has advertised a stolen database from major Indonesian digital platforms, offering sensitive user data for sale. The breach occurred in September 2024 and involved Kreen, a digital event promotion platform.
The threat actor is selling the dataset for $50 per copy, accepting only the cryptocurrency Monero (XMR) as payment. The seller has also offered an escrow service, providing additional assurance to potential buyers.
The Kreen application is a digital platform facilitating event promotion across various categories. It allows users to access information about events relevant to Indonesians both locally and abroad. According to the breach details shared by the threat actor, the stolen database contains:
205,717 event orders
86,792 individual orders
63,230 user records
According to the seller data also includes identifying information, such as names, email addresses, phone numbers, and event order details.

Thaihonda Data Advertised on a Leak Site
Summary:
A threat actor has reportedly put up for sale the database of Thai Honda( www[.]Thaihonda[.]co[.]th) Manufacturing Co., Ltd., which is responsible for producing and distributing Honda motorcycles in Thailand. Based in Samut Prakan, the company has allegedly suffered a data breach compromising extensive customer and transaction details.
Compromised Data:
The stolen database is said to include various types of sensitive information, such as customer IDs, motorcycle purchase details, VIN numbers, dealer codes, shop names, payment methods, and other personal and transaction-related data. Specifically, the compromised information spans details like:
Purchase history (buy date, price, financing details)
Customer demographics (name, email, address, phone numbers) Motorcycle models and specifications
Marketing and promotional influences Customer feedback and product preferences
Affected Records:
3.3 million Wing Center customers 38,000 Honda Big Wing customers 5,000 Cub House customers
Date of Breach:
The breach reportedly occurred in September 2024, and the threat actor is offering the data for sale at $10,000 in XMR (Monero). The actor also offers to negotiate and suggests that any staff from Thaihonda contact them for removal. The data breach has been attributed to a threat actor identified as “Thaihub”.

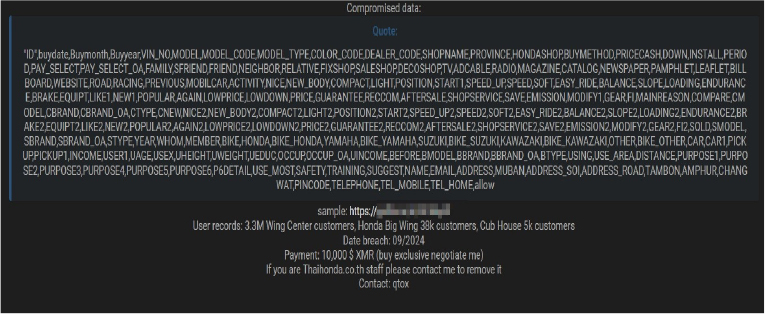
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat Actor “Thaihub” represents a significant threat in the cyber landscape, utilizing advanced tactics and a focus on high-value targets. Organizations must remain vigilant and proactive in their cybersecurity measures to protect against the evolving threats posed by this and similar groups. Continuous monitoring and updating of security protocols are essential for defending against such sophisticated attacks.
Recommendations: Enhance the cybersecurity posture by
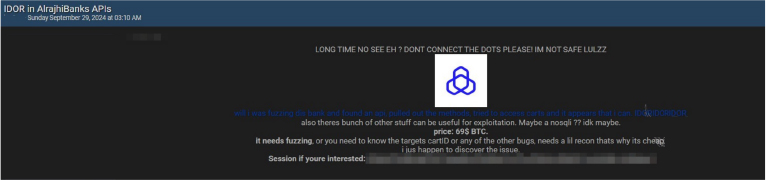
A threat actor “Cas” claims to have found an IDOR (Insecure Direct Object Reference) vulnerability in Al Rajhi Bank’s APIs. The individual allegedly discovered the flaw through fuzzing, which allows unauthorized access to user shopping carts and possibly other sensitive data.
The threat actor is selling this alleged vulnerability for $69 in Bitcoin. They suggest that with some reconnaissance, further exploitation could reveal more critical flaws, such as a possible NoSQL injection.
The bank is a major investor in Saudi Arabia’s business and is one of the largest joint stock companies in the Kingdom, with over SR 330.5 billion in AUM ($88 billion) and over 600 branches. Its head office is located in Riyadh, with six regional offices. Al Rajhi Bank also has branches in Kuwait and Jordan and a subsidiary in Malaysia and Syria.
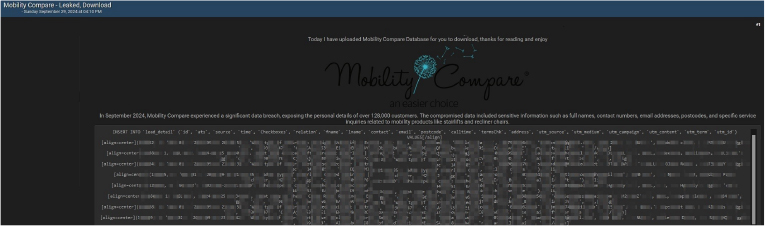
A threat actor recently posted a data dump on a dark web forum, claiming responsibility for a significant breach at Mobility Compare, a UK-based service provider specializing in mobility products. The breach, which reportedly took place in September 2024, exposed the sensitive information of more than 128,000 customers.
According to the post, the compromised data includes full names, contact numbers, email addresses, postcodes, physical addresses, and details of specific service inquiries.
The announcement offers the stolen database for download, marking yet another instance of personal information being sold or shared on illicit platforms.
ETLM Assessment:
The “Cas” threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted the Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, and Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
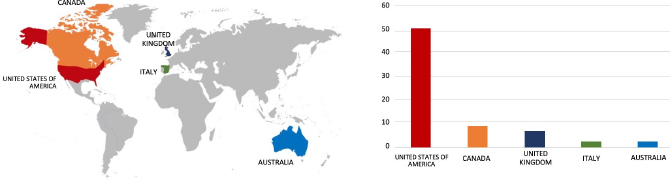
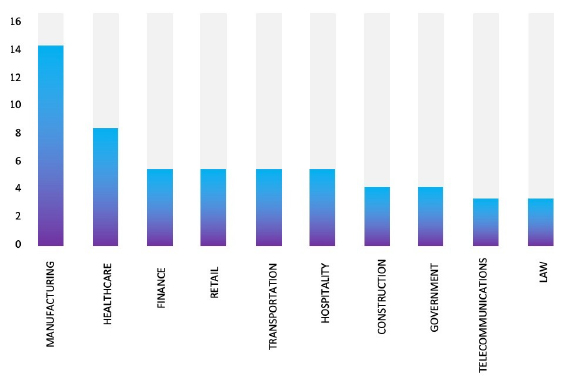
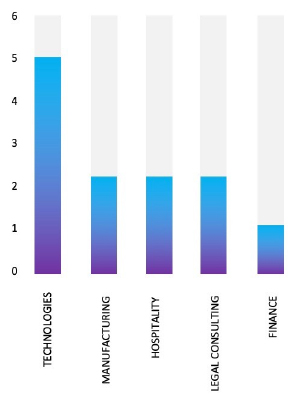
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.