



Ransomware of the Week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: Linux OS, VMware ESXi servers.
Target Geographies: Canada, Sweden, Switzerland, United Kingdom, United States of America.
Target Industries: Chemicals, Delivery Services, Food & Beverage, Health Care Providers, Heavy Construction, Industrial Engineering, Industrial goods and services, Oil & Gas, Retail, and Software.
Introduction
CYFIRMA Research and Advisory Team has found ransomware known as Abyss Locker while monitoring various underground forums as part of our Threat Discovery Process.
Relevancy: From the onset of its operation, the ransomware has targeted various industries, recent victims include:
Abyss Locker:
Abyss Locker, a ransomware operation that emerged in March 2023, has significantly increased its activity in recent days, targeting companies with more sophisticated attacks. Abyss Locker is the latest ransomware operation to develop a Linux encryptor specifically targeting VMware’s ESXi virtual machines platform.
The ransomware operators will breach corporate networks, steal data for double extortion, and encrypt devices on the network.
The ransomware has 17 known victims at the beginning of August 2023.
As can be observed from the commands below, the ‘esxcli’ command-line VMware ESXi management tool is utilized by the encryptor to first list all available virtual machines and then proceed to terminate them:
During the shutdown process, Abyss Locker employs the ‘vm process kill’ command with one of the available options: soft, hard, or forced.
The soft option facilitates a graceful shutdown, while the hard option terminates the virtual machine immediately. In cases where necessary, the force option is used as a last resort.
By terminating all virtual machines, the encryptor ensures that associated virtual disks, snapshots, and metadata can be encrypted effectively. Specifically, files with the extensions .vmdk (virtual disks), .vmsd (metadata), and .vmsn (snapshots) are encrypted for this purpose.
The ransomware encrypts all other files on the device, adding the .crypt extension to their filenames.
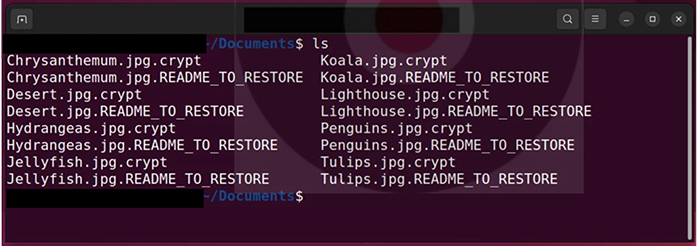
Screenshot of files encrypted by Abyss ransomware. (Source: Surface Web)
For each file, the encryptor generates a corresponding file with a .README_TO_RESTORE extension, serving as the ransom note. The ransom note provides details about the file’s situation and includes a unique link to the threat actor’s Tor negotiation site. The negotiation site is minimalistic, featuring a chat panel that allows communication with the ransomware gang for potential negotiations.
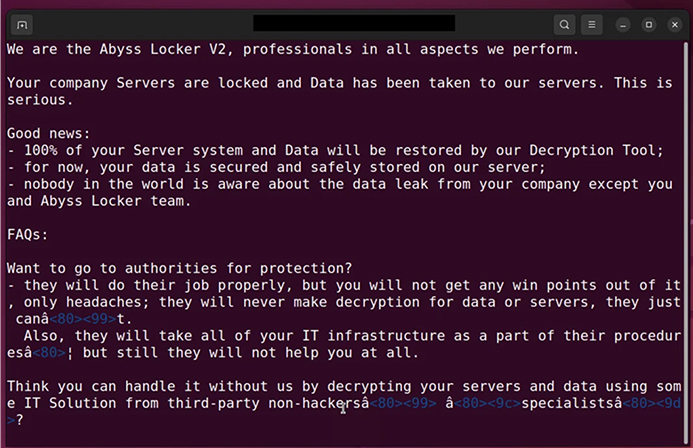
Abyss Locker Ransomware Note (source: Surface Web)
Researchers believe that the Abyss Locker Linux encryptor is derived from the Hello Kitty ransomware. It employs ChaCha encryption instead, signifying potential modifications and enhancements to the original codebase.
HelloKitty generally uses a combination of AES-256 and RSA-2048 or even NTRU+AES- 128.
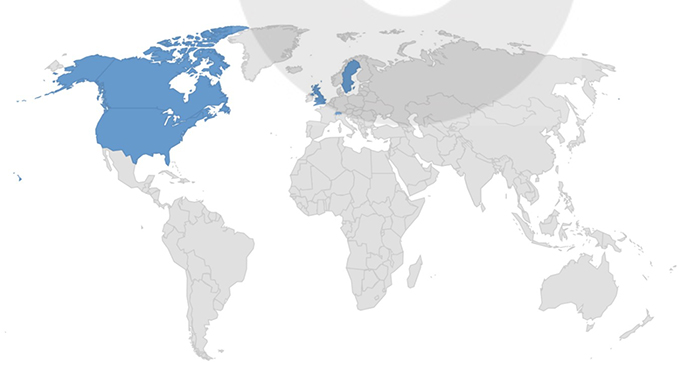
Countries targeted by Abyss Locker ransomware.
Insights:
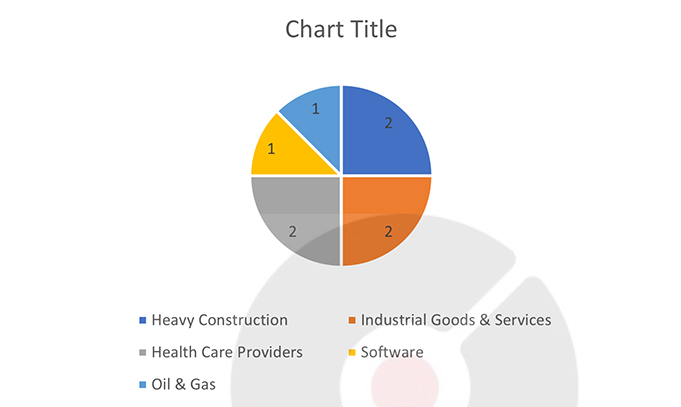
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| 2 | TA0005: Defense Evasion |
T1036: Masquerading |
| 3 | TA0007: Discovery | T1082: System Information Discovery |
| T1083: File and Directory Discovery | ||
| 4 | TA0009: Collection | T1005: Data from Local System |
| 5 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Type: Downloader
Objective: Malware Implant
Threat Actor: TA544 Target
Geography: Italy
Active Malware of the Week
This week “WikiLoader” is trending.
WikiLoader
Researchers discovered a new malware called WikiLoader, which is an advanced downloader designed to install a second malware payload. It employs sophisticated evasion techniques and custom-coded implementations to make detection and analysis challenging. It is believed that WikiLoader was created with the intention of being rented out to specific cybercriminal threat actors. As multiple threat actors have been observed using WikiLoader, researchers predict that it will likely be adopted by other threat actors, particularly those operating as initial access brokers (IABs).
Attack Method
WikiLoader uses packed downloaders, a common technique employed by threat actors to avoid detection and analysis. This technique makes the delivered executable smaller as it only serves to download the actual payload instead of embedding it in the file. It grants threat actors control over payload delivery, allowing them to implement IP filtering or limit downloads to a specific timeframe (first 24 hours of the campaign). The technical analysis of WikiLoader revealed a multi-stage execution chain, including the following stages:
These stages demonstrate the progression from the initial loader to the final payload of WikiLoader.
First Stage: Packed Loader
The first stage of WikiLoader is highly obfuscated, with call instructions replaced by push/jmp instructions to simulate a return without using the return instruction explicitly. This obfuscation poses challenges for analysis tools like IDA Pro and Ghidra. Additionally, WikiLoader employs indirect syscalls to evade endpoint detection and response (EDR) solutions and sandbox hooks.
In its initial stage, WikiLoader finds the address of NtCreateThreadEx, which allows it to create a thread pointing to GetModuleFileNameA. During this process, the malware ensures no trampolines or hooks have been placed within the NT function. These are techniques commonly used by sandboxes and EDR systems to intercept function calls. By checking the initial bytes of a given function, this behavior can be detected. Once the thread is created, WikiLoader starts it in a suspended state and hides it from debuggers using a flag. The malware further modifies the instruction pointer (RIP) using a combination of NtGetContextThread and NtSetContextThread, directing it to the decrypted shellcode.
With the modified RIP, the malware resumes the thread with NtResumeThread, initiating the next stage of the attack.
Second Stage: Shellcode
In the second stage of WikiLoader, its main objective is to decrypt the next stage of shellcode. Stage 3 is encrypted using a single-byte XOR key and is appended to the end of the stage 2 shellcode. Stage 2 locates the reference to the beginning of stage 3, decrypts it using the XOR key, and then transfers execution to stage 3. The start of the next stage of the shellcode is positioned at the end of the last function in stage 2.
Third Stage: Shellcode (part of the Packed Loader)
The third stage of WikiLoader is the primary stage where most of the loader’s functionality is implemented. It uses a decoding technique for strings, skipping over every even character to decode specific strings. The loader makes an HTTPS request to Wikipedia.com and verifies that the response contains the string “The Free.” This tactic likely serves as an evasion technique to avoid triggering automated analysis environments, ensuring the device is connected to the internet and not in a simulated environment that blocks external connections.
The loader then deliberately sends a request to an unregistered domain, and if a valid response is received, the malware terminates. This is done to evade certain automated analysis environments that return valid responses to all DNS queries by default, encouraging malware execution to continue. Organizations with DNS logs or EDR systems can identify infected systems by looking for DNS lookups related to the unique domains used by WikiLoader.
The loader checks the GetTickCount64 value, and based on whether it’s less than 125 or more, it makes requests to different hardcoded URLs. The reason for this switch based on the tick count is unclear. Later versions of the loader iterate over a set of URLs until a valid response is received. The response page contains a comment with the string “gmail” followed by base64 encoded text. The loader uses “gmail” as an anchor to retrieve the base64 text, decodes it, replaces any “+” characters with “/”, and appends the resulting string to a hardcoded Discord URL. This base64 text serves as the file path to retrieve the next stage hosted on Discord’s CDN.It is important to note that although the threat actors utilize Discord resources, this does not indicate that Discord itself has been compromised. Instead, the actors uploaded the sample to any Discord chat and copied the link to the attachment.
Fourth Stage: Shellcode (part of the Packed Loader)
In the next stage of WikiLoader, the shellcode downloaded and executed from Discord follows a similar process as the previous stage. It checks for kernel32.dll and GetProcAddress, uses string decoding, and relies on GetTickCount64 to choose the next hardcoded URL string. The URLs in this stage are the same as the previous one, except they contain “id=2” instead of “id=1”. The loader follows the same process of locating the “gmail” string, using it as an anchor to decode and modify characters in the URI to determine the location of the next file hosted on Discord. However, this time, the retrieved file is XOR encoded with a hardcoded, single byte. After decoding the file, it is executed.
Fifth Stage: Encoded PE
The fifth stage of WikiLoader downloads a PE file containing 16 encoded bytes. To create a valid PE file, the loader drops every other byte of the first 16 bytes. The final payload in this stage is the Ursnif banking trojan with GroupID “5050”.
WikiLoader Malware Evolution
Researchers have identified multiple versions of the malware, indicating ongoing development and updates. The following is a timeline with the relevant differences and updates observed in each version.
First version | 27 December 2022:
Second version | 8 February 2023
Third version | 11 July 2023
INSIGHTS
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
●
Lancefly APT Noticed Operating Cyber Espionage Campaigns with Merdoor Backdoor
Summary:
Insights:
Lancefly’s custom malware, named Merdoor, is a robust backdoor that seems to have been in operation since 2018. Researchers have detected its usage in various instances throughout 2020, 2021, and even in the recent campaign that persisted into the first quarter of 2023. It employs a dropper technique to inject itself into legitimate processes. Notably, the dropper has been observed abusing older versions of legitimate applications from well-known companies such as McAfee, Sophos, Google, Avast, and Norton for DLL sideloading.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian hackers targeting foreign diplomats
Researchers are tracking a cyberespionage campaign against diplomatic services that Russia’s foreign intelligence known as SVR ran between February and June of this year. According to the researchers, the targeting reflected Russia’s continuing interest in European governments, especially their diplomats. The attack starts with spearphishing, as is typical, with the baits imitating the ambassador’s itinerary like invitations to an embassy function or ads for used cars of a particular preference. The message then redirects to a compromised domain from which the hackers deploy malware that gives them access to their target’s network.
Cyberattacks in support of influence operations hit Kenya
Anonymous Sudan (a front for Russian intelligence services on which Cyfirma will issue a standalone report this Friday) has claimed responsibility for a cyberattack against Kenya’s eCitizen portal. The government in Nairobi acknowledged the attack, which temporarily disabled the service but said that no data had been lost. As is traditional with the group, it has used large-scale distributed denial-of-service (DDoS) attacks and claimed disproportionate impact, while pushing pro-Russian narratives at the same time. The claimed rationale Anonymous Sudan offered for the campaign was supposed to hide the more likely reason, which was a diplomatic snub of Kenya’s President William Ruto towards Russia, when the leader of Kenya declined to attend the Russo-African summit and gave as his reason the impropriety of appearing to support one side in Russia’s war on Ukraine, which has a crushing impact on the price of imported grain, which is a major concern in many African nations.
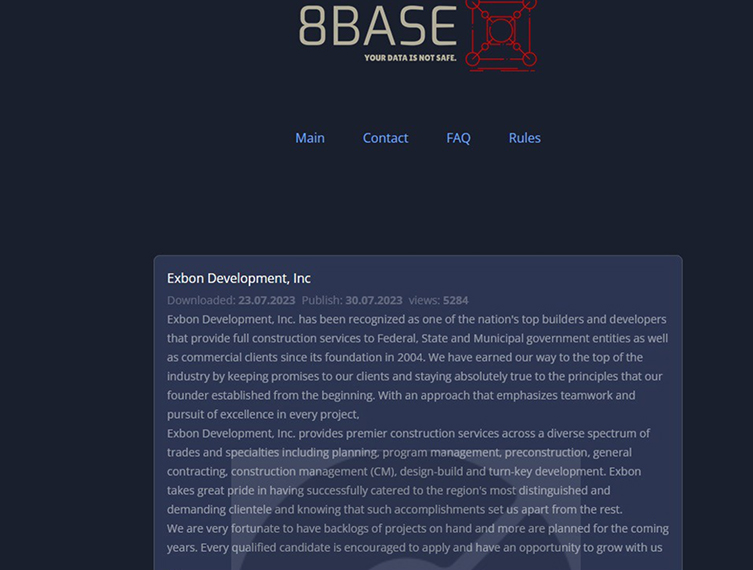
Exbon Development, Inc is Impacted by 8Base Ransomware
Summary:
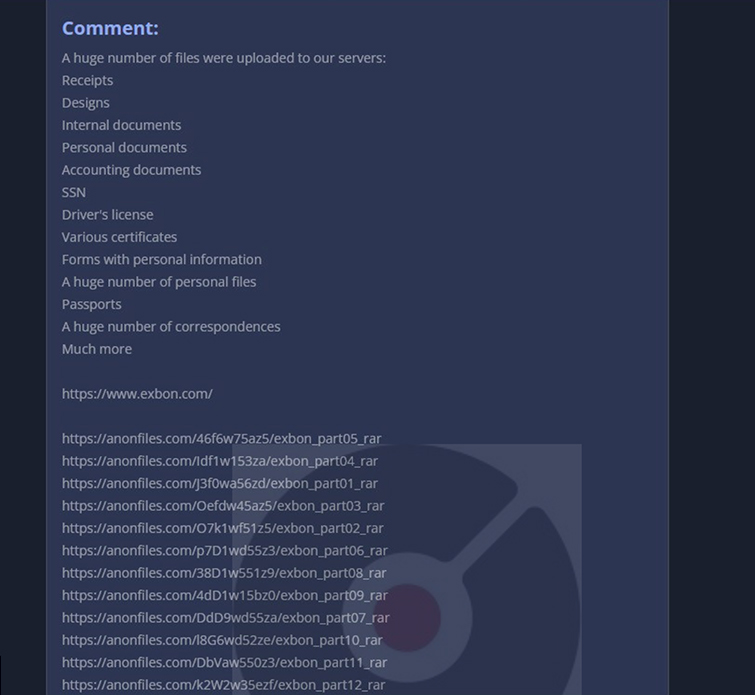
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]exbon[.]com), was compromised by 8Base Ransomware. Exbon Development, Inc. provides construction services. The Company offers general contracting services for highway and street construction. The compromised data comprises Receipts, Designs, Internal documents, Personal documents, Accounting documents, SSNs, Driver’s licenses, Various certificates, Forms containing personal information, a vast collection of personal files, Passports, and other sensitive information.
The following screenshot was observed published on the dark web:
Source: Dark Web
Insights:
Summary:
The vulnerability allows a remote attacker to execute arbitrary shell commands on the target system.
Insights:
The vulnerability exists due to improper input validation.
Impact:
A remote unauthenticated attacker can send a maliciously crafted web request containing special ANSI characters and inject arbitrary entries into the log file, which can lead to remote OS command execution when the log file is viewed via the terminal.
Affected Products: https[:]//advisory[.]splunk[.]com/advisories/SVD-2023-0702
The biggest oil refinery in Israel experiences website downtime due to a DDoS attack
Summary:
The cyber systems of BAZAN Group, the largest oil refinery operator in Israel, have been compromised, and as a result, the company’s website is currently inaccessible from many parts of the world. BAZAN Group’s websites, bazan.co.il and eng.bazan.co.il, are experiencing issues with incoming traffic, resulting in HTTP 502 errors or complete refusals by the company’s servers. The threat actors have claimed responsibility for the hack. The oil refinery’s website has been made inaccessible to most visitors from around the world. However, it is accessible from within Israel, possibly after the imposition of a geo-block by BAZAN in an attempt to thwart an ongoing cyber-attack. Over the weekend, the Iranian hacktivist group known as ‘Cyber Avengers,’ also referred to as ‘CyberAv3ngers,’ asserted that they successfully infiltrated BAZAN’s network in a Telegram channel. Furthermore, the group released what seemed to be screenshots of BAZAN’s SCADA systems, which are software applications employed for monitoring and managing industrial control systems. A representative from BAZAN has refuted the authenticity of the leaked materials, stating that they are “completely fabricated.” The hackers disclosed their method of breaching the company, stating that they exploited a vulnerability in a Check Point firewall. The IP address associated with the firewall device is confirmed to be assigned to Oil Refineries Ltd. The Check Point representative clarified that there have been no previous vulnerabilities that could have facilitated such an attack.
Insights:
The threat actor conveyed a message on Telegram, stating, “We have caused significant disruptions since 2020, but be prepared for even more severe actions in the future.” Apart from the website breach, CyberAvengers have taken credit for the 2021 fires at petrochemical plants in Haifa Bay, which were caused by a pipeline malfunction. They have also claimed responsibility for targeting industrial servers, resulting in attacks on 28 Israeli railway stations in 2020.
Masterdiskon’s Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Masterdiskon, {www[.]masterdiskon[.]com}. Masterdiskon is a company that has been in the tour and travel sector since 2019 in Jakarta, which provides you with various travel and adventure needs. It provides easy access to a wide selection of flight, train, bus, and hotel bookings on just one platform. The leaked data consists of various sensitive details, including user IDs, user codes, titles, first and last names, usernames, email addresses, password hashes with salt, referral codes, birthdates, genders, nationalities, unique national identifiers, province IDs, province names, city IDs, city names, addresses, postal codes, and other confidential information. The data is in SQL format and has a total size of 1.7 GB.
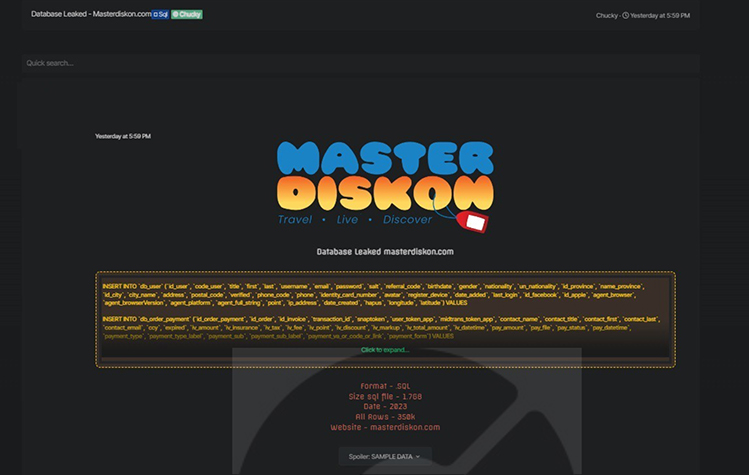
Source: Underground forums
Insights:
There are constantly vigilant cybercriminals driven by financial motives, who actively seek out exposed and vulnerable systems and applications. Most of these attackers operate in clandestine online communities, engaging in discussions and trading stolen digital assets. Unlike ransomware or extortion groups that often publicize their attacks, these attackers prefer to work discreetly. They exploit unpatched systems or vulnerabilities in applications to gain unauthorized access and pilfer valuable data. The stolen information is subsequently advertised, sold, and repurposed by other attackers for their own malicious purposes.
CYFIRMA Research team observed a potential data leak related to Qraved, {www[.]qraved[.]com}. Qraved is a one-stop dining solution. The Jakarta-based online company is a vast dining aggregation platform that facilitates unforgettable dining experiences. The data made available to the public consists of a customer database that includes unique identifiers, first names, last names, dates of birth, email addresses, phone numbers, password hashes (md5), relevance scores, and other confidential information.
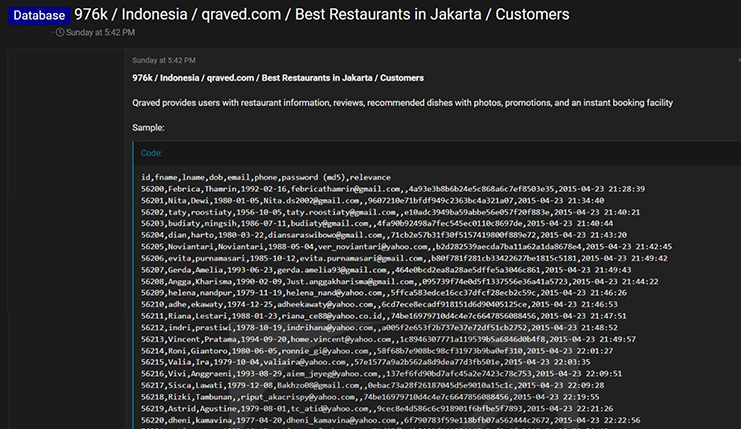
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS