



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
CYFIRMA Research and Advisory Team has found ransomware known as Good Day ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Good Day ransomware, part of the ARCrypter family, emerged in May 2023.
The Ransomware disguises itself as a Microsoft Windows Update executable named “WindowsUpdate.exe.” The ransomware is intended to be executed using a dropper or script, a tactic consistent with previous ARCrypter operations. To initiate the ransomware, the use of the /START parameter is essential.
The recognizable strings typically associated with the ARCrypter family are present in this sample as well.
Upon execution, Good Day determines the infected host’s location via the Windows Registry (HKEY_USERS…\Control Panel\International\Geo\Nation) and establishes persistence by creating an entry in the RUN key of the registry.
The ransomware also attempts to delete Volume Shadow Copies (VSS).
Furthermore, ransomware gathers information from infected systems through WMIC queries.
Following encryption, affected files receive new names with extensions like .crYptA or .crYptB, which can sequentially advance through the alphabet, ultimately reaching .crYptE as the final extension.
The ransomware makes efforts to detect its presence within specific debuggers. This list comprises S-Ice.exe, ImmunityDebugger.exe, x64dbg.exe, and others.
The Ransomware includes a predefined list of folders and files that it should not encrypt.
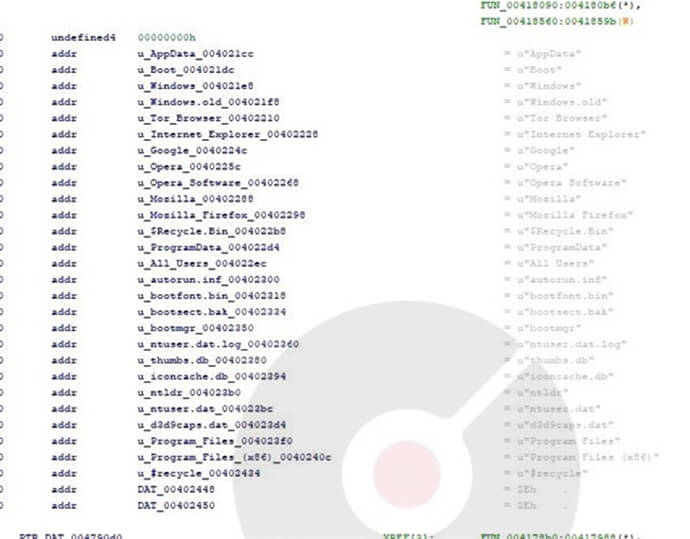
Good Day Exclusions list (Source: Surface web)
Researchers noted an increase in new ransom note samples in public malware repositories. This recent wave of Good Day attacks includes unique TOR-based victim portals for each target.
Researchers have identified distinctive Good Day ransom notes, victim portals, and analyzed a sample connected to a known Cloak extortion site. This association links Cloak’s data sales and leaks to Good Day through publicly accessible chats on TOR-based victim portals.
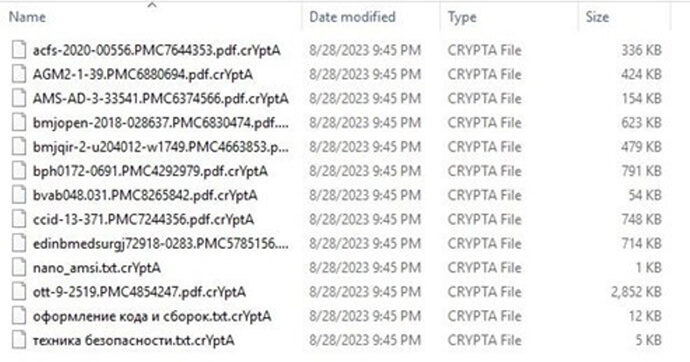
Files Encrypted by GoodDay Ransomware (Source: Surface web)
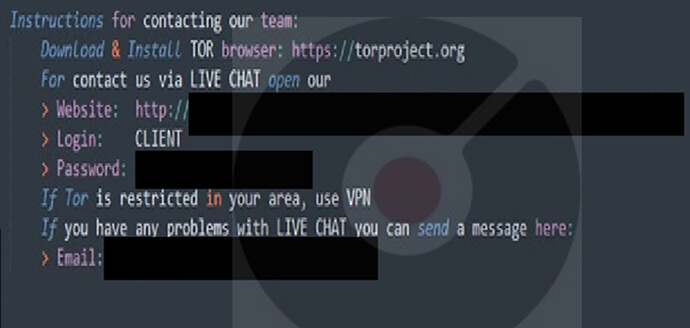
GoodDay Ransomware Note (Source: surface web)
Based on current information, Cyfirma predicts that Good Day ransomware, part of the ARCrypter family, will remain a significant cybersecurity threat. Its disguise as a Windows Update and targeting of the widely used Windows OS make it a persistent concern. Its ability to detect debug environments shows its commitment to evading analysis. Moreover, the use of idle periods suggests a stealthy operational approach, possibly during off-peak times. The rise in campaigns and its connection to Cloak underscores the importance of enhanced vigilance and preparedness against evolving cyber threats.
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter |
| T1129: Shared Modules | ||
| 2 | TA0004: Privilege Escalation | T1055: Process Injection |
| 3 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1055: Process Injection | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 4 | TA0007: Discovery | T1010: Application Window Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 5 | TA0011: Command and Control | T1090: Proxy |
| 6 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Kindly refer to the IOCs section to exercise controls on your security systems.
title: CMD Shell Output Redirect
tags:
– attack.discovery
– attack.t1082 logsource:
category: process_creation product: windows
detection: selection_cmd:
– OriginalFileName: ‘Cmd.Exe’
– Image|endswith: ‘\cmd.exe’ selection_cli:
CommandLine|contains: ‘>’ filter_idm_extension:
CommandLine|contains:
– ‘C:\Program Files (x86)\Internet Download Manager\IDMMsgHost.exe’
– ‘chrome-extension://’
– ‘\\.\pipe\chrome.nativeMessaging’ condition: all of selection_* and not 1 of filter_*
falsepositives:
– Internet Download Manager extensions use named pipes and redirection via CLI. Filter it out if you use it in your environment
level: low
(Source: Surface web)
Type: Information Stealer
Objective: Data Theft
Target Technology: Browsers, Social Media Accounts/Platforms
Target Sector: Technology
Active Malware of the Week
This week “DUCKTAIL” is trending.
Researchers observed a malicious campaign using LinkedIn messages for identity theft attacks. This campaign involves compromised LinkedIn accounts sending messages to users in an attempt to clandestine acquire their cookies, session data, and browser credentials, ultimately compromising their accounts.
In this campaign, they used the DuckTail malware, which is a sophisticated and elusive type of malware designed to avoid detection. It collects victim data, communicates with a Command-and-Control server through a Telegram Bot, and extracts data using ZIP archives. This malware variant possesses an automated feature that facilitates Facebook Business hijacking, granting attackers access to potential victims’ associated email accounts. The attacks were aimed at professionals from different Italian companies, primarily in the technology sector. The attackers particularly targeted employees in the sales and finance departments of these companies.
Initially, the campaign operates through compromised LinkedIn accounts, which distribute PDF documents disguised as job offers. Following the establishment of the initial contact with the victim, the compromised account then sends a subsequent message containing the attached PDF document, which contains the details of the job offer. In this particular instance, the deceptive job posting was for a Senior Manager position at Electronic Arts (EA) company.
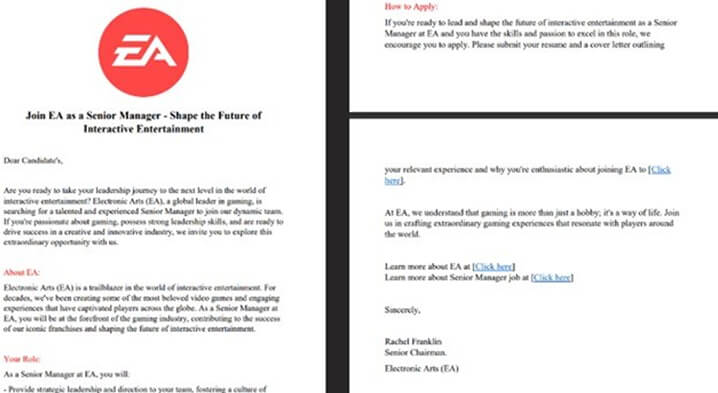
Fig: Fake Job offer document contains hyperlinks
The PDF document includes two hyperlinks that lead to malicious websites. The first hyperlink directs recipients to a phishing site(ea[.]gr8people[.]com) impersonating Electronic Arts. The page hosts both login and registration forms for candidates to submit their resumes and cover letters. The second malicious link triggers the download of a ZIP archive named Senior_Manager_EA_Sport.zip from Microsoft OneDrive.
The ZIP archive contains three MP4 video files and two identical executables that are disguised as Microsoft Word documents using the Word icon.
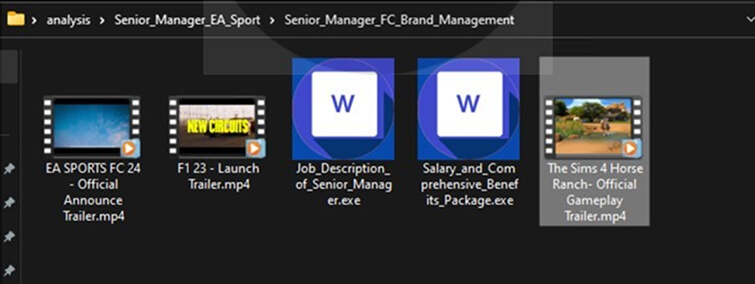
Fig: Contents of a zip archive file
These executables are 64-bit PE files with a size of 67.3 megabytes and include a decryption string “AHSDHAS092TEST.” The file seems to have been compiled using Microsoft Visual Studio and contains additional PE headers. One of these headers is associated with a Microsoft .NET executable, protected by the commercial obfuscator Smart Assembly.
The malicious file is created using the .NET Core framework and compiled as a single-file application, which consolidates all necessary libraries and files into a single executable.
This method is uncommon in malware and makes it highly elusive. Currently, only six out of seventy antivirus engines on VirusTotal have identified it as malicious, indicating its ability to avoid detection.
The “single file” application is essentially a collection of concatenated binaries, but the actual malicious code can be found by examining the executable’s dependencies. The primary DLL extracts a mutex named “ICollectVASD” to ensure the malware runs only once. It then collects victim information, including the system’s GUID and IP address, which is temporarily stored at the following path: C:\Users\<User>\AppData\Local\Temp\ic300.
The malware creates a fake PDF document as a decoy, displaying a supposed job description at this path: C:\Users\<User>\AppData\Local\Temp\Job_Description_of_Senior_Manager.pdf.
Communication with the Command and Control (C&C) server is done through a Telegram Bot (BOT ID 6263348871) using TLS encryption. The initial message is a “Start Signal,” which includes system information and a counter in an HTTP POST request to the attacker’s Telegram Bot.
TELEGRAM BOT REQUEST URL:
https[:]//api[.]telegram[.]org/bot6263348871:AAFc1F8GffaY0Bc8rWsvD2BzfK9yD- zrvRQ/sendMessage
Data is transferred in ZIP archives within POST messages, using the /sendDocument API. C&C server details are retrieved from a configuration file named “profile” within the binary’s resources, allowing for multiple profiles with different tokens, chatIDs, and email lists. The malware targets web browsers like Microsoft Edge, Google Chrome, Brave Browser, and Mozilla Firefox, extracting cookies, session data, and saved credentials via Telegram for identity theft attacks. It operates in the background, regularly sending data to the attacker through the Telegram API.The malware also includes a Facebook Business hijacking feature. It interacts with Facebook APIs, using session information from the victim’s browsers, and sends links to email addresses, potentially granting access to the associated Facebook Business Account for the attacker.
TELEGRAM BOT EXFILTRATION URL:
https[:]//api[.]telegram[.]org/bot6263348871:AAFc1F8GffaY0Bc8rWsvD2BzfK9yD- zrvRQ/sendDocument
From the ETLM perspective, CYFIRMA anticipates that DuckTail is constantly expanding its use of cloud services for hosting and distributing malicious payloads, suggesting its ongoing evolution. Future versions are likely to employ more advanced evasion techniques. The malware’s adept use of social engineering, notably on platforms like LinkedIn, indicates its operators’ skills in manipulating victims. In the future, we can expect more diverse and sophisticated delivery methods, potentially involving new social engineering tactics or exploiting vulnerabilities. DuckTail’s continued adaptability and evolution make it a persistent and ever-evolving threat in the cybersecurity landscape.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Lazarus Group Targets Same Victim Several Times
Summary:
In a recently detected campaign, the Lazarus APT group from North Korea repeatedly targeted a software vendor, exploiting vulnerabilities in their software even after multiple patches and warnings from the developer. The hackers’ relentless breaches of the same victim suggest a clear objective: the theft of valuable source code or the orchestration of a supply chain attack. Researchers detected this ongoing breach in July 2023. Their investigation revealed Lazarus employed a diverse infection chain and an array of post-compromise tools. This campaign fits into a broader pattern where Lazarus directed its focus on various software vendors from March to August 2023.
The attack primarily revolved around two malware components: SIGNBT and LPEClient. Lazarus targeted legitimate security software designed for encrypting web communications. The precise method of exploitation used by the hackers remains undisclosed. The deployment of SIGNBT involved injecting the payload into memory using shellcode, establishing persistence by adding a malicious DLL (‘ualapi.dll’) to the startup process, or making Windows Registry modifications. SIGNBT, named for its distinctive strings for command and control (C2) communications, enabled Lazarus to exchange information about compromised systems and receive execution commands. It supports various commands, including system information retrieval, process management, file operations, and more, making it a versatile tool for hackers. SIGNBT could fetch additional payloads from the C2 server, allowing Lazarus to maintain operational flexibility. They exploited this capability to load credential-dumping tools and the LPEClient malware on compromised systems. LPEClient, in its latest versions, displayed significant evolution, employing advanced techniques to enhance stealth and avoid detection.
Relevancy & Insights:
ETLM Assessment:
Recommendations:
Indicators of Compromise
Rise in privateering attacks by Russian actors
In recent weeks, Russia has stepped up cyberattacks directed against Ukraine and its international supporters. The recent increase is partly related to the fact that the Kremlin has been able to enlist cyber-criminals to do its bidding in financially motivated attacks with Moscow providing political cover for actions nominally illegal under the Russian law. For example, the Ukrainian National Cybersecurity Coordination Center (NCCC) reported that it was investigating an increase in Russian criminal attacks using Smokeloader malware. The agency has characterized the threat actors beyond the spread of the Smokeloader-related attacks as financially motivated cybercriminals, would in effect mean they are privateers who were enlisted by the Kremlin in order to supplement the efforts of Russian intelligence and security services and the hacktivist auxiliaries those services direct. Their activity has been on the rise since May, when Ukrainian financial and government organizations have been repeatedly targeted by multi-module malicious software, the functionality of which includes counter analysis methods, data theft, and remote control of the victim’s computer. The threat actors seem to be especially interested in the financial services sector.
ETLM Assessment:
Privateers are often anonymous and at the same time enjoy state protection – state backing remits their actions and makes them more difficult to detect and prosecute, which is a typical reason for their employment by governments worldwide. However, in this specific case, privateering on behalf of Russian cyber criminals is best explained as a process of national mobilization of Russian resources. The Russian official budget allocated to defense spending in 2024 will almost double compared to this year. While that is less than the 12–17 percent of GDP that the Soviet Union was officially spending on defense at the height of the Cold War, it is comparable to U.S. military expenditure in the 1980s. That means the Russian economy is seriously strained and the intelligence and military apparatus is increasingly looking for other ways to bolster its capability. The gradual enlistment of privateers should be a concern especially for the business in countries deemed hostile by the Kremlin, since the privateers are more likely to go after them.
Hamas cyber activity likely connected to Iran
Researchers have identified and analyzed an application disseminated on a Telegram Channel, used by members and supporters of the Hamas terrorist organization, which is configured to communicate with Hamas’s military wing – the Izz ad-Din al-Qassam Brigades’ – website. Based on infrastructure and domain registration tradecraft analysis, the researchers believe the app is a work of AridViper (also known as APT-C- 23, Desert Falcon) a suspected Hamas-connected group. The researchers also observed a likely Iran nexus tied to that domain. It is likely that the newly identified domains were operated by threat actors that share an organizational or ideological affiliation with the Qassam Brigades and who are connected to the Quds force, a sub- organization of Iran’s Islamic Revolutionary Guard Corps (IRGC). The Quds force has been observed to provide cyber technical assistance to Hamas and other Palestinian threat groups in the past and this observation is another link in the chain of support Iran provides to Hamas as its political proxy in the region.
ETLM Assessment:
While Iran is hostile to all other blocks of powers in the Middle East, its relationship with Israel is particularly thorny. Israel has been restrained by the United States from preventive military strike on Iran’s nuclear programme in the past as the United States were able to persuade Israel to join an American cyber warfare operation against the Natanz facility instead. However, given the internal political dynamics of all three countries and a new spiralling of violence between Israel and Iran-supported Hamas in the Gaza strip, a further escalation between Iran and Israel is increasingly likely. The conflict would be manifest in cyberspace as well as on the ground and we are likely to see a spike in the activity of Iranian APTs attacking countries that support Israel in the coming months.
Online Development is Impacted by Play Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from The United States of America, (www[.]oldi[.]com), was compromised by Play Ransomware. Online Development Inc. (OLDI) designs and manufactures factory automation products to help manufacturers simplify data transaction, control, and communications tasks. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The breached data includes sensitive personal information such as private and confidential data, client documents, IDs, payroll information, tax records, client directories, passports, financial details, and more.
The following screenshot was observed published on the dark web:

Source: Dark Web
Relevancy & Insights:
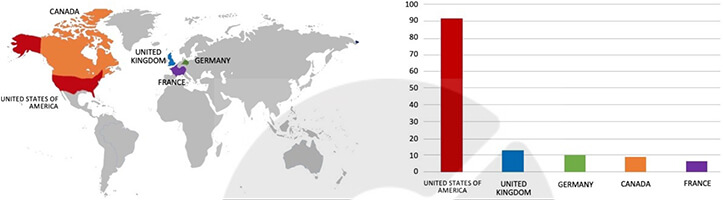
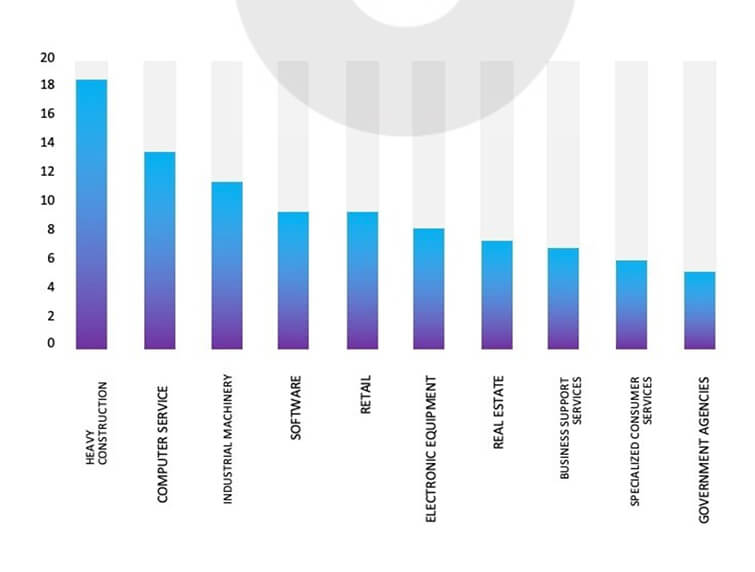
ETLM Assessment:
enumerates the files and folders in a VSS snapshot and copies them to a destination directory. The tool allows the attackers to copy files from VSS volumes on compromised machines prior to encryption. This allows the threat actors to copy files normally locked by the operating system.
Vulnerability in Twisted Web
Summary:
The vulnerability allows a remote attacker to perform HTTP request smuggling attacks.
Relevancy & Insights:
The vulnerability exists due to improper validation of HTTP requests. A remote attacker can send a specially crafted HTTP request to the server and smuggle arbitrary HTTP headers.
Impact:
Successful exploitation of vulnerability may allow an attacker to poison HTTP cache and perform phishing attacks.
Affected Products: https[:]//github[.]com/twisted/twisted/security/advisories/GHSA-xc8x- vp79-p3wm
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
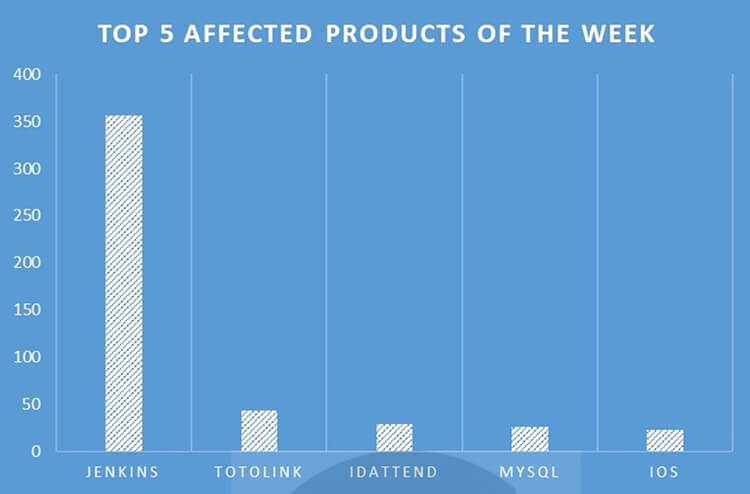
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
Ukrainian hackers disrupt internet providers in Russia-occupied territories.
Summary:
Internet services have been temporarily disabled in certain areas of the country’s territories occupied by Russia, due to actions by Ukrainian hackers. The group of cyber activists known as the IT Army said on Telegram that their distributed denial-of-service (DDoS) attack took down three Russian internet providers — Miranda-media, Krimtelekom, and MirTelekom — operating in the territories. Early on Friday, Russian internet operators confirmed that they had experienced an “unprecedented level of DDoS attacks from Ukrainian hacker groups,” temporarily disrupting their operations. The attack affected services such as cellular networks, phone calls, and internet connections. On Friday evening, Miranda-media reported that it had restored 80% of its services, including those provided by it and two other affected operators for law enforcement agencies, government organizations, and “socially significant services.” The operator’s security experts said that DDoS attacks were “carefully planned by cybercriminals.” On Saturday, internet connections in certain regions of Crimea were still disrupted as operators worked to improve their network resilience. After occupying parts of eastern Ukraine and the Crimea peninsula, Russia disconnected Ukrainian telecommunications infrastructure there and rerouted internet traffic through Russia’s network instead. Ukraine strongly criticized this move, saying that Russia wants to make its propaganda “an uncontested source of information.”
Relevancy & Insights:
The IT Army, a prominent group of cyber activists, claimed responsibility for a distributed denial-of-service (DDoS) attack that targeted Russian internet providers, including Miranda-media, Krimtelekom, and MirTelekom, operating in the affected territories. This deliberate act was described as a strategic move by the Ukrainian cyber army to impede the enemy’s military communication on the frontlines.
ETLM Assessment:
CYFIRMA assesses similar attacks will continue as the Ukraine/Russian conflict continues, with Ukrainian threat actors seeking to undermine and cause disputation to Russian infrastructure.
Turk Ekonomi Bank (TEB) Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Turk Ekonomi Bankasi (TEB), {www[.]teb[.]com[.]tr}. Turk Ekonomi Bank (TEB), a reputable and prestigious institution in the Turkish banking sector, was established in 1927. Since its inception, TEB has expanded its branch network and broadened its array of products and services. The breached data includes individuals’ names, surnames, national identification numbers, addresses, and other sensitive details.
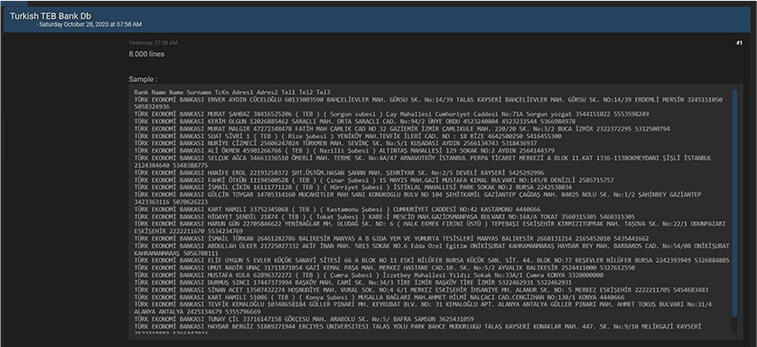
Source: Underground forums
Relevancy & Insights:
Cyber attackers driven by financial incentives continuously seek out vulnerable and insufficiently secured systems and software applications. Many of these malicious actors operate within obscured online communities, participating in discussions concerning cybercrime and the illegal trading of stolen digital assets. Setting themselves apart from other financially motivated groups like ransomware or extortion collectives, who often publicize their attacks, these cybercriminals prefer to maintain a discreet presence. By exploiting unpatched systems or weaknesses in software and hardware, they illicitly gain entry and make off with valuable information. Subsequently, they promote the pilfered data on secretive forums, where it is either sold again or repurposed by other malicious entities for their own unlawful purposes.
ETLM Assessment:
CYFIRMA assesses the banking industries of advanced economies such as Turkey, are at continued risk of attack by financially motivated threat actors.
CYFIRMA Research team observed a potential data leak related to Planetminecraft,
{www[.]planetminecraft[.]com}. Planet Minecraft is a family-friendly community that shares and respects the creative works and interests of others. The breached data includes usernames and passwords saved as MD5 hashes, alongside other sensitive information.
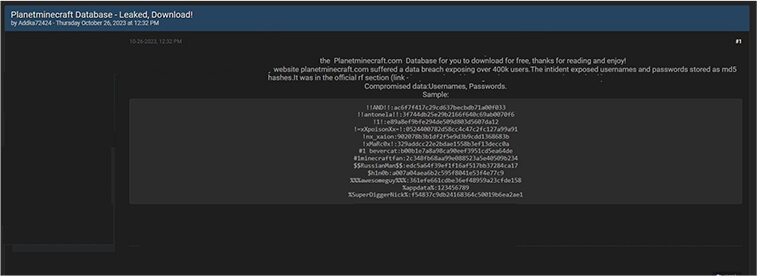
Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS