



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found new Crocodile Smile ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Crocodile Smile ransomware
The Crocodile Smile ransomware was uncovered by researchers by the end of April 2024. This malicious software functions by encrypting data and requesting ransoms for decryption. Files affected by it had their names extended with a “.CrocodileSmile” suffix. After completing this encryption process, Crocodile Smile alters the desktop wallpaper and generates a ransom note titled “READ_SOLUTION.txt”.
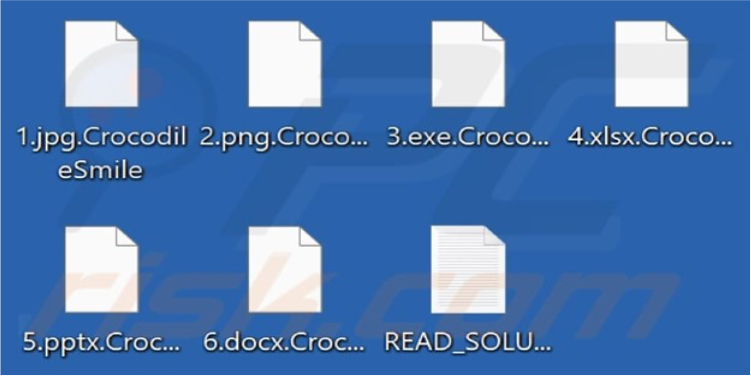
Screenshot of files encrypted by ransomware (Source: Surface Web)
From Crocodile Smile’s message, it becomes evident that this ransomware is aimed at larger entities rather than individual home users.
The Ransom message indicates that the victim’s files have been encrypted and their sensitive data has been stolen. The victim is directed to pay more than 20 BTC to decrypt their files and prevent the attackers from leaking the exfiltrated data.
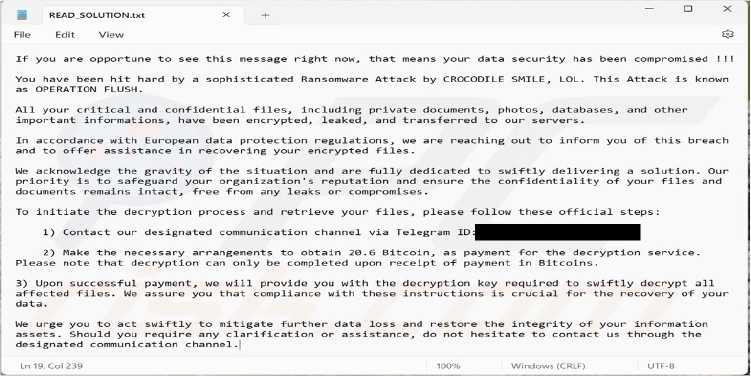
Screenshot of Crocodile Smile ransomware’s text file (“READ_SOLUTION.txt”): (Source: Surface Web)

Screenshot of Crocodile Smile desktop wallpaper (Source: Surface Web)
There’s a possibility that multiple variants of this ransomware are circulating in the wild. The following ransom note from another variant of this ransomware will provide evidence of this.
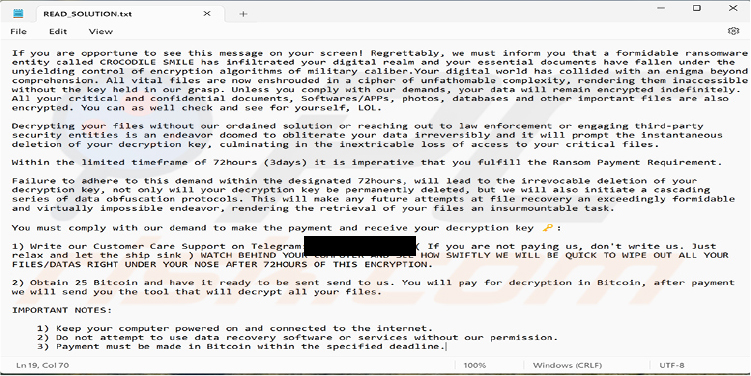
Ransom note (“READ_SOLUTION.txt”) delivered by another variant of Crocodile Smile ransomware
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1053: Scheduled Task/Job | ||
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| T1176: Browser Extensions | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 3 | TA0004: Privilege Escalation | T1053: Scheduled Task/Job |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 6 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| 7 | TA0009: Collection | T1005: Data from Local System |
| T1115: Clipboard Data | ||
| T1119: Automated Collection | ||
| T1185: Browser Session Hijacking | ||
| 8 | TA0040: Impact | T1486: Data Encrypted for Impact |
| T1490: Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment, based on available information, suggests that Crocodile Smile ransomware, with its demand for more than 20 bitcoins, is likely to target economically developed nations located in Europe, East Asia, South-East Asia, and the US, where organizations are more capable of meeting such demands. This reflects a deliberate strategy aimed at entities capable of fulfilling substantial ransom demands. Furthermore, the ransomware is anticipated to persistently target Windows OS, utilizing sophisticated evasion tactics and persistence methods. This will likely result in heightened encryption complexity and system disruption, posing considerable challenges to detection and recovery efforts across various industries. Vigilance and strong cybersecurity measures are essential to mitigate these threats effectively.
Sigma Rule
title: System File Execution Location Anomaly
tags:
– attack.defense_evasion
– attack.t1036
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith:
– ‘\svchost.exe’
– ‘\rundll32.exe’
– ‘\services.exe’
– ‘\powershell.exe’
– ‘\powershell_ise.exe’
– ‘\pwsh.exe’
– ‘\regsvr32.exe’
– ‘\spoolsv.exe’
– ‘\lsass.exe’
– ‘\smss.exe’
– ‘\csrss.exe’
– ‘\conhost.exe’
– ‘\wininit.exe’
– ‘\lsm.exe’
– ‘\winlogon.exe’
– ‘\explorer.exe’
– ‘\taskhost.exe’
– ‘\Taskmgr.exe’
– ‘\sihost.exe’
– ‘\RuntimeBroker.exe’
– ‘\smartscreen.exe’
– ‘\dllhost.exe’
– ‘\audiodg.exe’
– ‘\wlanext.exe’
– ‘\dashost.exe’
– ‘\schtasks.exe’
– ‘\cscript.exe’
– ‘\wscript.exe’
– ‘\wsl.exe’
– ‘\bitsadmin.exe’
– ‘\atbroker.exe’
– ‘\bcdedit.exe’
– ‘\certutil.exe’
– ‘\certreq.exe’
– ‘\cmstp.exe’
– ‘\consent.exe’
– ‘\defrag.exe’
– ‘\dism.exe’
– ‘\dllhst3g.exe’
– ‘\eventvwr.exe’
– ‘\msiexec.exe’
– ‘\runonce.exe’
– ‘\winver.exe’
– ‘\logonui.exe’
– ‘\userinit.exe’
– ‘\dwm.exe’
– ‘\LsaIso.exe’
– ‘\ntoskrnl.exe’
# The below processes were seen used by Lazarus Group – https://asec.ahnlab.com/en/39828/
– ‘\wsmprovhost.exe’
– ‘\dfrgui.exe’
filter_generic:
– Image|startswith:
– ‘C:\Windows\System32\’
– ‘C:\Windows\SysWOW64\’
– ‘C:\Windows\WinSxS\’
# – ‘C:\avast! sandbox’
– Image|contains: ‘\SystemRoot\System32\’
– Image:
– ‘C:\Windows\explorer.exe’
– ‘C:\Program Files\PowerShell\7\pwsh.exe’
– ‘C:\Program Files\PowerShell\7-preview\pwsh.exe’
filter_wsl_windowsapps:
Image|startswith: ‘C:\Program Files\WindowsApps\MicrosoftCorporationII.WindowsSubsystemForLinux’
Image|endswith: ‘\wsl.exe’
condition: selection and not 1 of filter_*
fields:
– ComputerName
– User
– Image
falsepositives:
– Exotic software
level: high
(Source: Surface web)
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan
Objective: Espionage, Credentials Stealing, Device Takeover and Remote Access
Threat Actor: Baron Samedit
Target Technology: Android OS
Target Industries: Banks
Active Malware of the Week
This week “Brokewell” is trending.
Brokewell
Researchers have identified a new Android banking trojan called Brokewell, capable of recording all device activities such as touches, displayed information, text input, and launched applications. The malware is delivered through a fake Google Chrome update that is shown while using the web browser. Brokewell poses a significant threat to the banking industry, providing attackers with remote access to all assets available through mobile banking. Additionally, Researchers have identified that the Brokewell malware was developed by an individual known as “Baron Samedit.” Brokewell is actively evolving, with frequent additions of new commands by its developers.
Baron Samedit
The developer behind Brokewell, identified as Baron Samedit, previously sold tools for checking stolen accounts to cybercriminals across different services for at least two years. Transitioning into mobile malware, Baron Samedit released the “Brokewell Android Loader,” reflecting the rising interest in mobile threats among cybercriminals. Additionally, a server used as a command and control (C2) for Brokewell hosted the “Brokewell Cyber Labs” repository, featuring the source code for the Brokewell Android Loader. This repository underscores cybercriminals’ efforts to professionalize illegal activities, exemplified by the landing page of “Brokewell Cyber Labs,” where various malicious products, including mobile threats, are advertised.
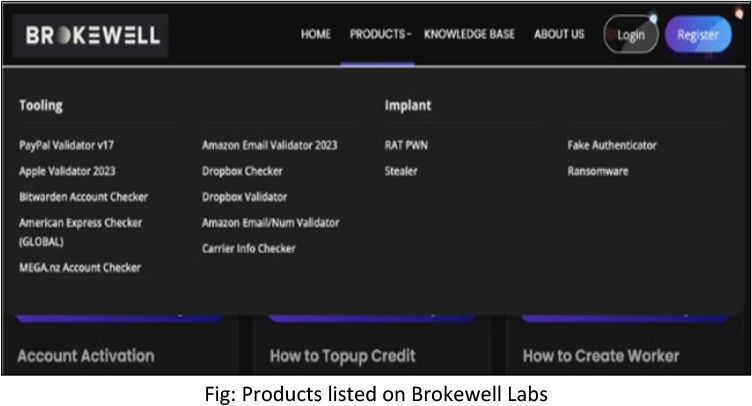
Attack Method
Researchers uncovered a deceptive tactic involving a fake browser update page aimed at tricking users into installing an Android application. This tactic initially appeared ordinary, resembling typical methods used by cybercriminals to entice victims into downloading malware. The fake update page convincingly presents itself as a legitimate browser update, blending seamlessly into normal browsing activity to deceive unsuspecting users.
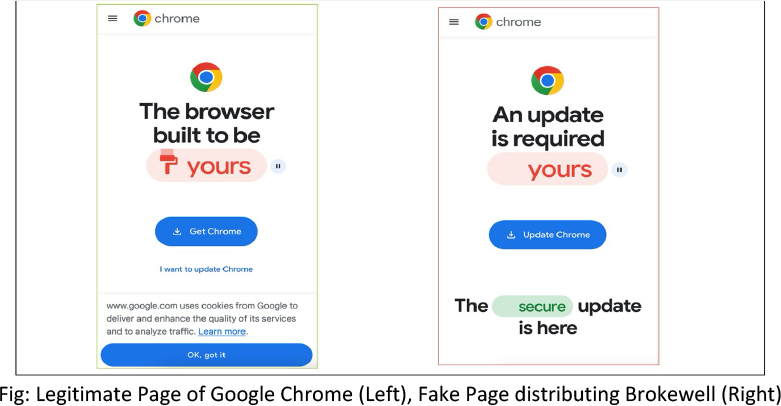
Upon analysis, it was discovered that the downloaded application is a new malware variant with extensive functionalities. Additionally, further investigation revealed previous campaigns conducted by this malware family, which targeted a popular “buy now, pay later” financial service and an Austrian digital authentication application.
Features of Brokewell Banking Malware
Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware.
Stealing data: Monitoring Everything
Brokewell employs overlay attacks, a common tactic used by Android banking malware, by displaying a fake screen over targeted apps to capture user credentials. It also steals cookies through its own WebView, intercepting the legitimate website’s login process, dumping session cookies, and transmitting them to its command-and-control server (C2). Brokewell includes “accessibility logging” to record all device events such as touches, swipes, displayed information, text input, and opened applications. This data is transmitted to a command-and-control server, enabling the theft of confidential information entered or viewed on the compromised device. Brokewell’s broad logging capability poses a risk to all installed applications on the device. Additionally, this malware acts as spyware, gathering device details, call history, geolocation data, and even recording audio.
Device Takeover via Remote Control Capabilities
After obtaining credentials, attackers can launch a Device Takeover attack using Brokewell’s remote control features. This includes screen streaming and allows the attacker to execute actions on the compromised device, such as touches, swipes, and clicks on specific elements. The malware offers a set of commands for remote control operations. Below are some of the commands utilized by the malware:
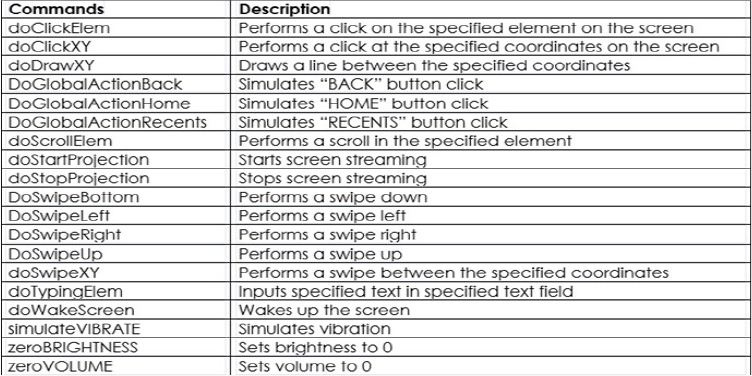
These commands demonstrate that attackers have complete control over the infected device, enabling them to act on behalf of the victim. These capabilities could be extended in the future by automating actions to enhance the Device Takeover attack, potentially leading to the development of a functional Automated Transfer System (ATS).
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the widespread adoption of online mobile banking has revolutionized user convenience in conducting financial transactions, but it has also opened doors for cybercriminals to exploit vulnerabilities and trick users into downloading malicious apps. The Brokewell malware specifically targets individuals heavily reliant on mobile banking, posing a severe threat to financial security within the banking sector. The widespread adoption of mobile banking, particularly in regions such as developed countries in Europe and America, as well as developing countries in regions like East Asia and Southeast Asia with large user bases, makes them more susceptible to banking malware like Brokewell. As digital banking becomes more widespread in these regions, the threat of cyber-attacks targeting a broader audience continues to grow. It’s crucial for individuals and organizations to prioritize cybersecurity measures to safeguard against these risks and ensure the security of financial transactions and sensitive information.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Key Intelligence Signals:
Escalating Cyber Threats: Pakistani APTs Target Indian Government Entities
Summary:
The cyberattacks on Indian government entities were orchestrated by Pakistan-linked APT groups, including SideCopy and Transparent Tribe (APT36). These groups employed sophisticated tactics, such as spear-phishing campaigns, to gain access to target systems.
The attackers initiated their operations through sophisticated spear-phishing campaigns, utilizing archive files with double extensions to deceive victims. Upon opening these files, the MSHTA process executed a remote HTA file hosted on compromised domains. These HTA files contained encoded DLLs and decoy files.
The DLLs, once executed in memory, dropped decoy files and downloaded additional HTA files from the compromised domain. These files contained EXE and DLL files, which were decoded and dropped into the public directory, allowing for further malicious activities.
The final payloads deployed were AllaKore RAT for SideCopy and Crimson RAT for Transparent Tribe. These RATs connected to command-and-control (C2) servers using different port numbers, maintaining communication through ping-pong commands to ensure the connection was active.
The attacks resulted in significant disruptions to targeted entities, potential data theft, and the compromise of sensitive information. The infrastructure and C2 servers used in the attacks showed similarities, attributing them to SideCopy and Transparent Tribe with high confidence. The attacks underscore the importance of enhanced cybersecurity measures and proactive defence strategies to mitigate the growing cyber threats posed by APT groups in the region.
Relevancy & Insights:
Transparent Tribe, also known as APT36, suspected to be based in Pakistan, has been active since at least 2013. Primarily targeting diplomatic, defence, and research organizations in India, their sophisticated cyberattacks pose significant threats to national security. In parallel, there has been a noticeable surge in the trade of access to Indian entities, encompassing both governmental and corporate sectors, facilitated by initial access brokers within underground forums. This trend coincides with a rise in high-profile ransomware incidents. In response, Indian cybersecurity forces are urged to bolster their defences by updating security protocols, conducting regular system checks, and providing personnel with comprehensive training to effectively recognize and respond to evolving cyber threats.
ETLM Assessment:
SideCopy and APT36, also known as Transparent Tribe, represent Pakistan-linked Advanced Persistent Threat (APT) groups with a strategic focus on targeting South Asian countries, particularly Indian defence and government entities. These threat actors have demonstrated a persistent intent to infiltrate and compromise governmental infrastructure to facilitate their malicious activities, leveraging compromised infrastructure to carry out their operations. This trend underscores the critical importance of heightened vigilance and robust cybersecurity measures to safeguard against the persistent threats posed by these APT groups.
Recommendations:
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Czech Republic warns of Russia’s cyber sabotage to EU railways
According to the Czech government, Russia has made thousands of attempts to damage the European railway system since the beginning of the invasion of Ukraine. Moscow is suspected of being behind “thousands of attempts to weaken our systems”, the Transport Minister said during an EU meeting in Brussels. The Russian hacking campaign includes attacks on critical infrastructure systems, including attacks on signaling equipment and on the computer networks of Czech state-owned carrier Czech Railways. In the past, the Russians have disabled ticketing systems in this way, for example, raising concerns about whether similar attacks are behind serious train accidents caused by faulty signaling equipment. Last March, the EU Cyber Security Agency (ENISA) published its first ever report on threats to the European transport system. The report mentioned hacking attacks by pro-Russian groups against railways in Latvia, Lithuania, Romania and Estonia. Czech Railways confirmed the government’s remark and acknowledged growing number of attacks on its digital infrastructure.
ETLM Assessment:
Russian attempts to destabilize European energy infrastructure have been well documented but interference in transport networks has been less discussed, even though Cyfirma analysts warned of this danger in this report last year. The Czech National Cyber and Information Security Agency (NÚKIB) has also warned of growing threats of attacks on transport targets in its report last year. The agency has been one of the strictest digital security watchdogs in Europe and was the first to issue a hawkish warning against the use of components from Chinese companies Huawei and ZTE in 5G mobile networks under construction. Russia is using the attacks both as a tool of political war against the West as well as tactical means of delaying transports of Ukrainian grain to the world market as well as movements of Western equipment towards Ukraine both in civilian and military capacity. The incident shows the growing role of cyber in conflict even or rather especially between countries that are not formally at war and demonstrates the future of political relations, in which cyber will be a major means of the statecraft toolkit, affecting governments and business alike.
The Pentagon gets a cyber czar
The US Department of Defense has opened its Office of the Assistant Secretary of Defense for Cyber Policy. Upon confirmation, the new assistant defense secretary for cyber policy (aka cyber czar) Ashley Manning will oversee spending on network operations, outreach to industry, and more. The move is aligned with the recent U.S. Navy cyber strategy, according to which non-kinetic effects rather than missiles, fighter jets and torpedoes are likely to decide the next war on the high seas. The document reflects the central idea that the next fight against a major adversary will be like no other and that the use of non-kinetic effects and defense against those effects prior to and during kinetic exchanges will likely be the deciding factor in who prevails. But the navy sees as imperative that cyber warfare is far more than networks and cybersecurity. Cyber warfare is presented as a warfighting discipline that should be considered a core competency that is going to play a key role in modern warfare.
ETLM Assessment:
The inauguration of the “cyber czar” confirms the growing role of cyber in modern conflicts, which often do not distinguish between military and civilian infrastructure and between times of war and peace. The office intends to provide the U.S. military a more civilian-facing role in the realm of cyber policy. The new office is responsible for coordinating the Pentagon’s cyber strategies, overseeing the military’s cyber operational budget, cyber workforce development and private sector outreach, among other areas.
The US military highlights the pivotal role of non-kinetic effects and defense against such effects in future conflicts. The potential for massive cyberattacks by advanced state actors like China looms large, threatening to disrupt critical infrastructure and the internet-powered amenities that underpin modern life. US documents emphasize that cyber warfare extends far beyond networks and cybersecurity issues, yet neither governments nor businesses are adequately prepared to confront this emerging threat.
The RansomHouse Ransomware impacts the Bank Pembangunan Daerah Banten Tbk PT
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Indonesia; (www[.]bankbanten [.]co[.]id), was compromised by the RansomHouse Ransomware. Bank Pembangunan Daerah Banten Tbk PT is a bank focusing on micro-enterprises and small and medium enterprises. It is a regional development bank owned by the government of Banten province. The compromised data comprises confidential and sensitive information pertaining to the organization. It totals approximately 450 GB.
The following screenshot was observed published on the dark web:
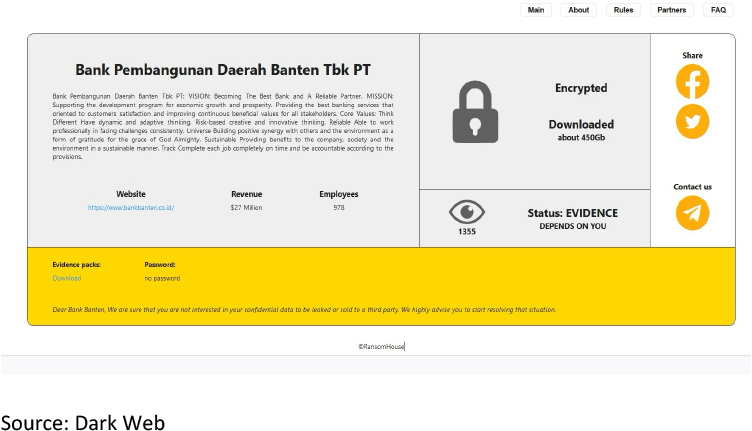
Relevancy & Insights:
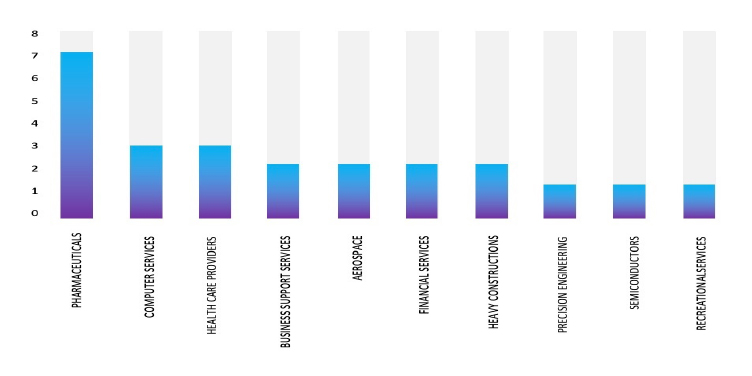
ETLM Assessment:
RansomHouse ransomware is known to target large enterprises and high-value targets. RansomHouse ransomware targets its victims through phishing and spear phishing emails. They are also known to use third-party frameworks (e.g., Vatet Loader, Metasploit, Cobalt Strike). Based on the available information, CYFIRMA’s assessment indicates that RansomHouse ransomware will continue to target various industries globally, with a significant emphasis on the United States, European, and Asian regions. The recent breach targeting the Bank Pembangunan Daerah Banten Tbk PT, a leading finance firm based in Indonesia, serves as a potential indicator of RansomHouse ransomware’s inclination towards targeting organizations across Southeast Asia.
The Cactus Ransomware impacts the Ghim Li
Summary: From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Australia; (www[.]ghimli[.]com), was compromised by the Cactus Ransomware. Ghim Li’s headquarters are located in Singapore. Ghim Li is a global textile and apparel supply chain manager of casual lifestyle knitwear apparel for major U.S. retailers. Ghim Li supplies over 62 million garments annually through a global marketing and manufacturing network. The compromised data contains highly confidential and sensitive information relevant to the organization.
The following screenshot was observed published on the dark web:

Relevancy & Insights:
ETLM Assessment:
Cactus Ransomware Group is known for breaking into networks by exploiting known vulnerabilities in VPN appliances and Qlik Sense software. The group also conducts phishing attacks, buys stolen credentials through crime forums, and partners with malware distributors. Based on CYFIRMA’s assessment, Cactus Ransomware targets worldwide organizations. The attack on Ghim Li also highlights ransomware groups’ interest in Australian and Asian organizations financially strong in the region with exploitable vulnerabilities.
Vulnerability in Moby
Summary:
The vulnerability allows a remote attacker to compromise the target system.
Relevancy & Insights:
The vulnerability exists due to the IPv6 is not disabled on network interfaces.
Impact:
A remote attacker can gain access to sensitive information or perform a denial of service (DoS) attack.
Affected Products: https[:]//github[.]com/moby/moby/security/advisories/GHSA-x84c-p2g9-rqv9
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
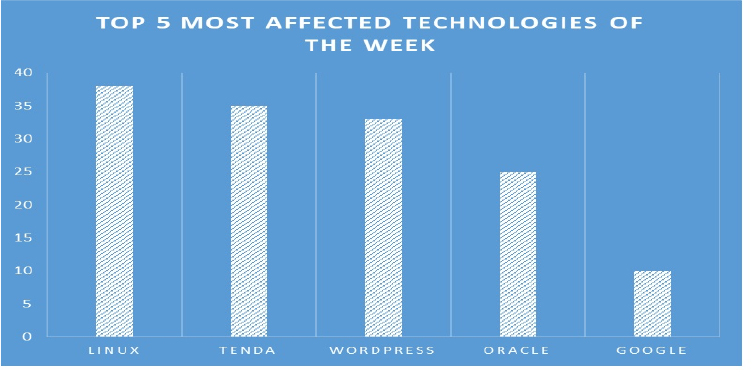
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Moby, functioning as a open framework, empowers global developers to craft custom container systems. Its impact is felt across sectors like technology, finance, healthcare, and e-commerce in diverse geographic regions. Vulnerabilities in Moby could disrupt operations and compromise containerized environments worldwide.
8Base Ransomware attacked and Published data of GPI Corporate
Summary:
Recently we observed that 8Base Ransomware attacked and Published data of GPI Corporate on its darkweb website. GPI Corporate is a fully integrated Promotional Marketing solution provider that is committed to delivering fresh ideas, creative products, and solutions that will enhance efficiencies, promote growth, and surpass expectations. The data leak, post ransomware attack encompasses a wide array of sensitive information including invoices, receipts, accounting documents, personal data, certificates, employment contracts, a substantial volume of confidential information, confidentiality agreements, personal files, and additional data.

Relevancy & Insights:
We’ve recently noted that the 8-base Ransomware has targeted prominent organizations such as LEMODOR Lüftungstechnik AG, a top-tier ventilation systems manufacturer based in Switzerland, and Tamura Corporation. Tamura, established in 1924 and headquartered in Tokyo, Japan, specializes in electronic manufacturing. These attacks underscore the 8-base Ransomware’s focus on major manufacturing entities across the globe.
ETLM Assessment:
The 8Base ransomware group first emerged in March 2022 and swiftly gained notoriety, exhibiting a notable surge in activity throughout 2023 and 2024. Though their ransom demands remain undisclosed, they employ double extortion tactics, leveraging exfiltrated data for additional leverage. Operating with remarkable sophistication, 8Base employs advanced security evasion techniques and primarily targets Windows systems, with a particular focus on sectors including business services, manufacturing, finance, and information technology. Continuous assessments conducted by CYFIRMA indicate that 8Base ransomware has set its sights on Australian, European, and Southeast Asian Nations, driven by a relentless pursuit of substantial financial gains through ransomware operations.
DAGANG GROUP INDONESIA data advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to DAGANG GROUP INDONESIA, {www[.]dagang-group[.]com } in an underground forum. Dagang Group Indonesia is a corporation that operates in the form of a business ecosystem. Dagang Group Indonesia’s range of business units is integrated with a focus on digital trade business services targeting Small and Medium Enterprises (SMEs). The compromised data encompasses a range of sensitive information, including employee details such as Employee ID, full name, barcode, organizational affiliation, job position, level, join and resign dates, employee status, end dates, sign dates, and other confidential data points. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.

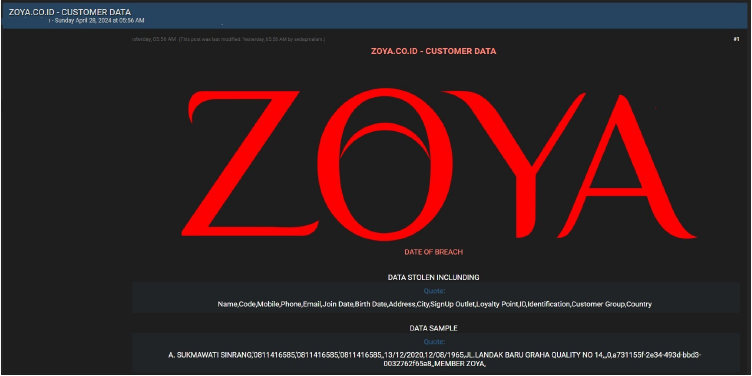
ZOYA data advertised on a Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to ZOYA, {www[.]ZOYA[.]co[.]id} in an underground forum. Zoya’s online store offers a wide range of high-quality women’s Muslim clothing and the latest hijab styles, with various pricing options to choose from. The compromised data includes personal information such as names, codes, mobile and phone numbers, email addresses, join and birth dates, addresses, cities, sign-up outlet details, loyalty points, IDs, identifications, customer groups, country information, and other confidential data. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.
TUNAS TOYOTA data advertised on a Leak Site
Summary: The CYFIRMA Research team observed a potential data leak related to TUNAS TOYOTA, {www[.]tunastoyota[.]com} in an underground forum. Tunas Toyota is a prominent automotive company known for its excellence in the industry. As one of Indonesia’s leading Toyota dealerships, Tunas Toyota has earned a reputation for providing top-notch vehicles, exceptional customer service, and innovative solutions to meet the diverse needs of its customers. The compromised data includes customer data identifiers, user IDs, phone numbers, email addresses, names, dates of birth, customer agreements, agreement dates, status information, and UTM source details. The data breach has been attributed to a threat actor identified as ‘Sedapmalam’.

Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Recommendations: Enhance the cybersecurity posture by
CYFIRMA Research team observed a potential data leak related to Kintetsu World Express, Inc. A significant data breach has been reported at Kintetsu World Express, Inc. (KWE), a major Japanese freight forwarding company, with ramifications extending across its global operations. The breach, claimed by a threat actor identified as 888, has resulted in the leakage of sensitive information from the company’s First Freight CRM Billing system. This incident has affected a substantial number of individuals, with 819 members from nearly 30 countries having their personal data compromised.

ETLM Assessment:
888 threat actor group has become active in underground forums and has emerged as a formidable force in cybercrime mainly for financial gains. The threat actor has already targeted Government, Industrial Conglomerates, Retail, Staffing, Business consulting, Banks, E-Commerce, Electric & Utilities industries, indicating its intention to expand its attack surface in the future to other industries globally.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
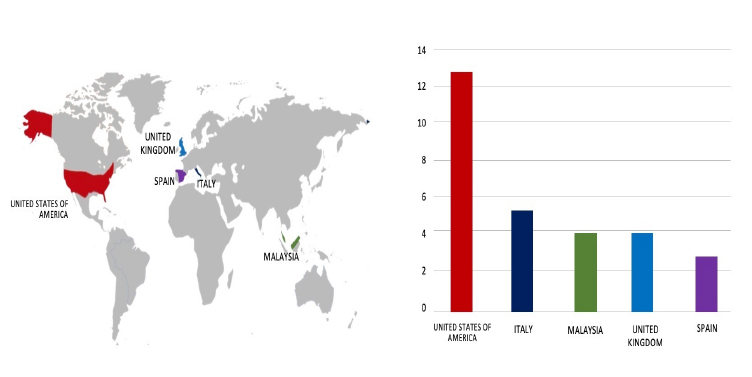
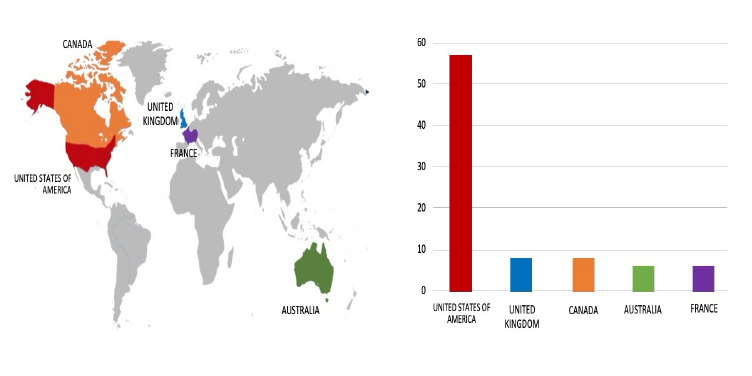
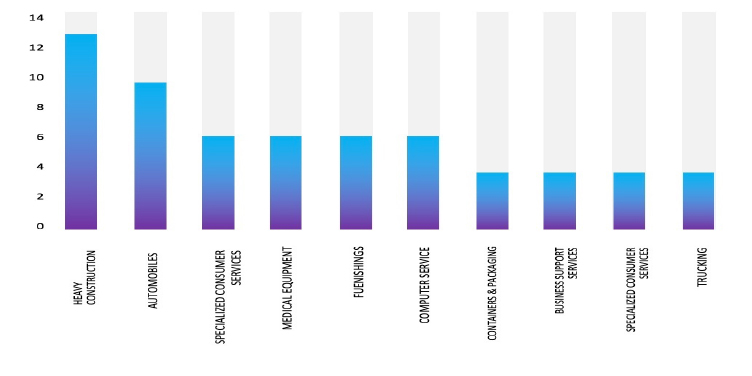
Please find the Geography – Wise and Industry- Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organization’s geography, industry, technology, please access DeCYFIR.