Published On : 2023-02-03
Weekly Attack Type and Trends
Key Intelligence Signals:
- Attack Type: Ransomware, Vulnerabilities & Exploits, Ransomware-as-a-Service (RaaS), Malware Implants, Data Exfiltration, Data Leak, Impersonations, Remote Code Execution (RCE), On-device Fraud, Rouge Mobile Apps, Telephone-Oriented Attack Delivery (TOAD), Smishing, Malvertising, USB as an Attack Vector
- Objective: Unauthorized Access, Data Theft, Financial Gains, Payload Delivery, Potential Espionage
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property
- Ransomware –BlackCat Ransomware | Malware – PY#RATION
- BlackCat Ransomware – One of the ransomware groups.
- Please refer to the trending malware advisory for details on the following: o Malware – PY#RATION
- Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vector. Apart from these techniques, exploitation of vulnerabilities, defence evasion, and persistence tactics are being observed.
Threat Actor in Focus
Gamaredon Unleashes Fresh Attack on Latvian Government
- Suspected Threat Actors: Gamaredon
- Attack Type: Spear Phishing
- Objective: Unauthorized Access, Espionage, Data Exfiltration
- Target Technology: Windows
- Target Geographies: Europe
- Target Industries: Public and Private Sector
- Business Impact: Data Theft, Operational Disruption
Summary:
Gamaredon is Russia’s state-sponsored cyber espionage group active from the year 2013. Gamaredon is known for conducting specific cyber-attacks against Ukraine including its allies. Recently, Latvia revealed facing a massive cyber-attack after coming forward in support of Ukraine, the recent cyber-attack on the Latvian government was conducted by Gamaredon. Researchers claimed the involvement of Gamaredon as the threat actor using the same domain which was used for delivering the payload in December 2022 campaign. The threat actor dropped malicious emails to several employees of the ministry, pretending to be Ukrainian government officials. They used HTML smuggling and then Zip which had LNK payload for further attack. The Latvian government hasn’t shared much with the cyber security community and claimed the attack went unsuccessful as it got detected in its initial stage.
Insights:
The threat actor has been targeting the Latvian government for many years; however, the attacks have taken some pace after the Ukraine-Russia war.
Major Geopolitical Developments in Cybersecurity
Two new malware strains in use by Russian military intelligence in a possible “combined arms” operation
- Formerly unknown malware dubbed by researchers “NikoWiper,” has been recently described by researchers in active use by the Russian military intelligence GRU. The wiper malware has been used against a company in the energy sector in Ukraine and is based on SDelete, a command line utility from Microsoft that is used for securely deleting files. The group responsible for the use was Sandworm APT, which leveraged NikoWiper on the Ukrainian energy sector in the same broader time window in which the Russian military targeted Ukrainian energy infrastructure with missile strikes. This would suggest a possible attempt at a “combined arms” operation, under which a coordinated attack of cyber and kinetic forces tried to orchestrate a blow to the national power grid.
- Days prior to the announcement of NikkoWiper, researchers observed yet another strain of wiper malware used by Sandworm, this time dubbed “SwiftSlicer”. This malware has been deployed against Ukrainian networks using Active Directory Group Policy. This wiper represents a successor to HermeticWiper and CaddyWiper, both of which the Russian military intelligence affiliate Sandworm had deployed against Ukraine in the early phases of the invasion.
- In another attack, as many as five distinct strains of wiper malware were identified in the networks of the Ukrinform national news agency. The strains and the systems affected, were: CaddyWiper (Windows), ZeroWipe (Windows), SDelete (Windows), AwfulShred (Linux), and BidSwipe (FreeBSD). Besides heavy use of wipers, Sandworm’s recent campaigns have also leveraged bespoke ransomware families, including Prestige and RansomBoggs, which is done without the traditional blackmail attempt with the sole goal of locking the targeted organizations out of their data based on political motivations.
- These recent cases of new wipers being leveraged by Russian state-sponsored APTs mark the increasing willingness to attack civilian infrastructure with the intent to cause severe physical harm among Russian hackers and should pose a warning to organizations in countries that have a hostile relationship with Russia over its invasion of Ukraine.
Rise in Iranian hacking activity reported
- The surge in activity of Iranian state-sponsored APT activity has been reported in Australia, UK, and Israel. In Australia, a parliamentary report disclosed that Iranian Revolutionary Guard-affiliated actors have launched targeted cyber-attacks on Australian organizations, with the aim of using the data obtained for extortion.
- In other campaigns, researchers analyzed the activities which they connected to the Iranian COBALT SAPLING threat group. The Iran-linked actor, also known as Moses Staff, is now leaking data stolen from Saudi Arabia government ministries, while in December it posted data stolen from Israeli companies or the personal information of individuals affiliated with an Israeli intelligence unit of the Israel Defense Forces. The motivation for the group’s actions is political as the group clearly attacks the informal Saudi-Israel security partnership targeted against the threat both countries perceive from Iran.
- The UK’s National Cyber Security Centre (NCSC) has also recently warned that Iranian intelligence services are increasing their phishing attempts. The APT42 (also known as Charming Kitten) has been singled out for continuing to successfully use spear-phishing attacks against targeted organizations and individuals in the UK and other countries, for purposes of cyber espionage. The campaigns have been selective and highly targeted, prospecting people who work in academia, defense, governmental organizations, etc. The nature of these attempted espionage campaigns appears to be motivated by the intent to gather compromising material that could later be used to blackmail targeted individuals and force them into collaboration with Iranian security services.
Other Observations
CYFIRMA Research team observed that Atlantic General Hospital in Maryland is experiencing network disruptions and outages after a significant ransomware attack.

Source: Telegram
The Team also observed a potential data leak related to www[.]ahna[.]org –
American Holistic Nurses Association. This data leak contains the names, email addresses and phone numbers of members of American Holistic Nurses Association.
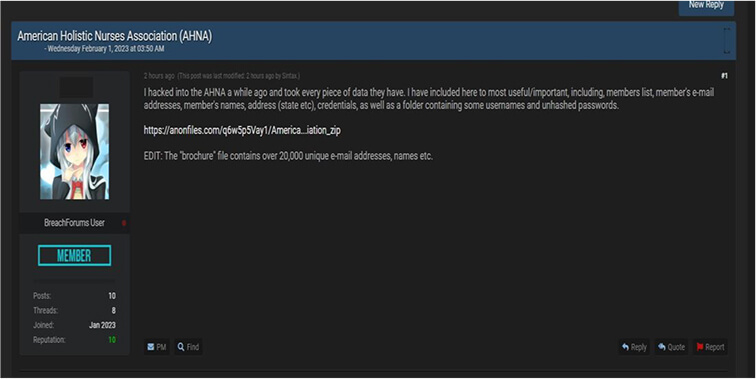
Source: Underground Forums
STRATEGIC RECOMMENDATION
- Attack Surface Management should be adopted by organizations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, active network monitoring, through next generation security solutions and ready to go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATION
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Move beyond the traditional model of security awareness towards improved simulation and training exercises that mimic real attack scenarios, account for behaviours that lead to a compromised, and are measured against real attacks the organization receives.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcoming of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATION
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthen defences based on tactical intelligence provided.
- Deploy detection technologies that are behavioural anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.





