CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
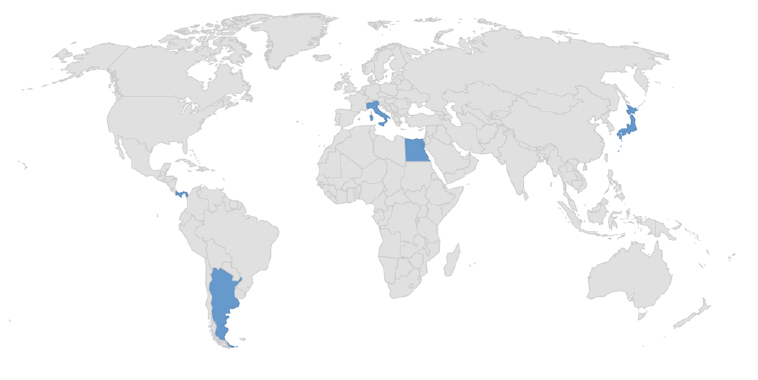
Target Geography: Argentina, Egypt, Panama, Italy, Japan.
Target Industry: Manufacturing, Healthcare, Real estate.
Introduction
CYFIRMA Research and Advisory Team has found Gunra Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Gunra Ransomware
Gunra is a ransomware that encrypts data and demands a ransom for decryption. Upon infecting a system, Gunra encrypts files, appending a “.ENCRT” extension to filenames. Following encryption, it generates a ransom note titled “R3ADM3.txt.”
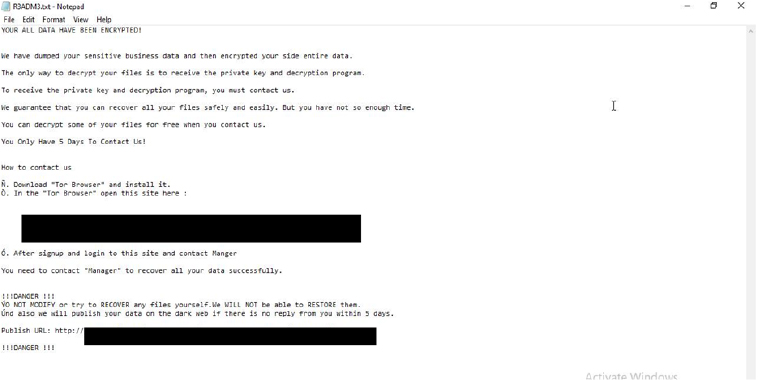
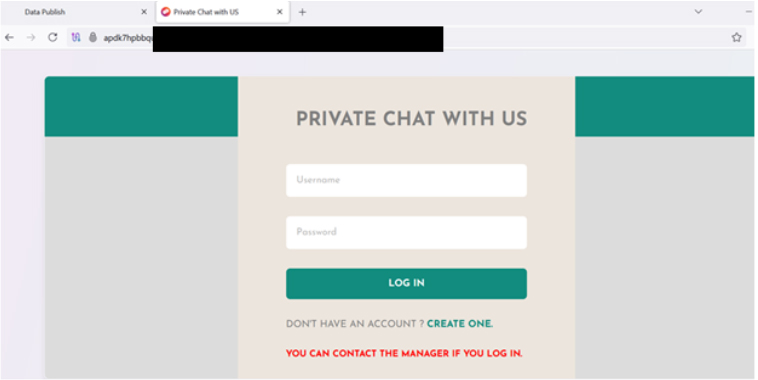
The ransom note informs victims that files have been encrypted and sensitive business data stolen. Decryption requires purchasing a key and software. Victims are allowed to decrypt several files for free as proof. They are given five days to respond, with threats of data leakage on the dark web if they refuse or delay payment. Tampering with files is strongly discouraged.
Following are the TTPs based on the MITRE Attack Framework.
| Tactic | ID | Technique |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1129 | Shared Modules |
| Persistence | T1176 | Software Extensions |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Bootkit |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Software Packing |
| Defense Evasion | T1027.005 | Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.001 | Hidden Files and Directories |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552 | Unsecured Credentials |
| Credential Access | T1552.001 | Credentials in Files |
| Credential Access | T1555 | Credentials from Password Stores |
| Credential Access | T1555.003 | Credentials from Web Browsers |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1518 | Software Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1119 | Automated Collection |
| Collection | T1185 | Browser Session Hijacking |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment, based on available data, indicates that Gunra ransomware is poised to expand its operations globally, posing a serious threat to critical infrastructure sectors. Leveraging tactics such as data encryption, theft, and extortion, Gunra is expected to target both developed and developing regions to maximize financial returns. Its use of high-pressure ransom demands and threats of data leaks suggests a focus on organizations with valuable assets. Gunra is projected to remain a persistent and evolving global threat, necessitating strengthened cybersecurity measures.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490
logsource:
category: process_creation
product: windows
detection:
selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’
selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’
selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’
selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet
selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’
selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’
CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*)
fields:
– CommandLine
– ParentCommandLine
falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand)
level: high
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Trojan
Objective: Remote Access, Data exfiltration
Target Geography: Japan
Exploited Vulnerability: CVE-2025-0282
Active Malware of the Week
This week “DslogdRAT” is trending.
DslogdRAT
Researchers recently discovered that DslogdRAT malware was being used in attacks against organizations in Japan. The malware and a web shell were installed by exploiting a zero-day vulnerability (CVE-2025-0282), giving attackers remote control over infected systems. DslogdRAT can perform various actions, such as uploading and downloading files, executing malicious code, and setting up proxies. It also gathers basic information from compromised devices and sends it back to the attackers to support further malicious activity.
Attack Method
A web shell written in Perl was used as part of the attack to gain control over compromised systems. The script operated as a CGI program, checking incoming HTTP requests for a specific cookie value. When the correct token was detected, it allowed attackers to execute arbitrary commands sent through the request. This technique enabled the attackers to run malware like DslogdRAT on the targeted systems, helping them establish deeper control during the intrusion.
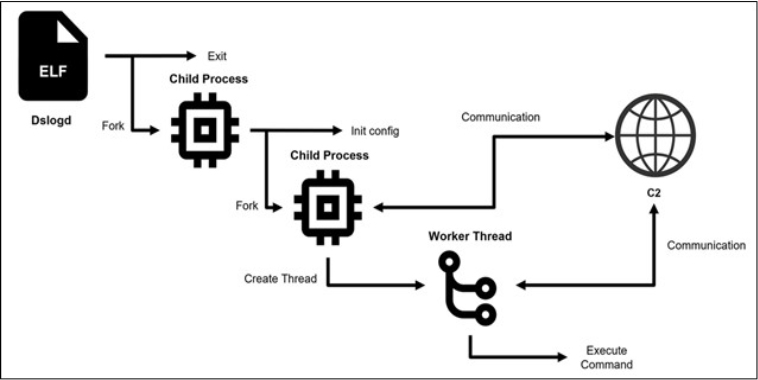
Upon execution, DslogdRAT’s main process spawns a child process before terminating itself. The first child process decodes the configuration data and then creates a second child process, which handles the core functionality of the malware. The first child process enters a loop, including sleep intervals, preventing it from being terminated. The second child process establishes communication with the command-and-control (C2) server, using the configuration data to initiate this connection. It then creates a worker thread to manage the data exchange with the C2 server and execute various commands. These threads are managed through the pthread library, allowing the malware to maintain ongoing communication and perform malicious activities remotely.
The configuration data for DslogdRAT is encoded and hardcoded within the malware, using XOR encoding with a key of 0x63 to decode it. Once decoded, the data reveals that DslogdRAT is set to operate between 8:00 AM and 8:00 PM, remaining in a sleep state outside these hours. This scheduling appears to be a deliberate tactic by the attackers, likely intended to reduce the risk of detection by limiting the malware’s activity to business hours.
DslogdRAT’s Communication Method and Commands
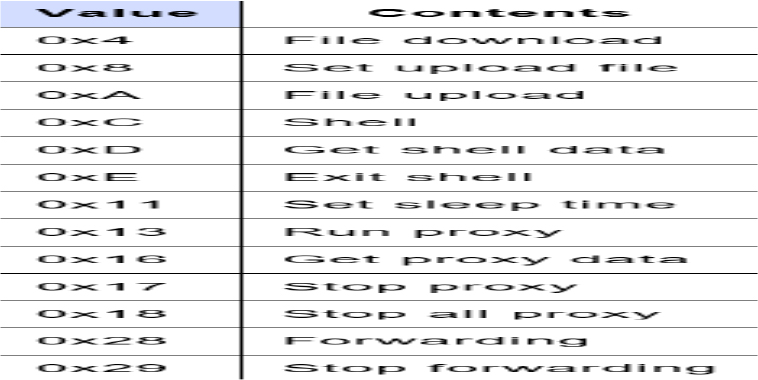
Once DslogdRAT establishes communication with the C2 server, it uses a simple XOR encoding and decoding process to exchange data. During the initial communication, the malware sends basic information about the infected host. It then waits for further commands from the server, which can include file uploads and downloads, execution of shell commands, and setting up proxy functionality. The encoding mechanism helps the malware obfuscate its communications, making it harder to detect while maintaining its ability to carry out malicious activities on the compromised system. The following are the commands supported by DslogdRAT:
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that DslogdRAT is likely to evolve into a more stealthy and persistent threat, making it harder for organizations to detect and remove. As attackers refine their ability to mimic normal system behavior and limit activity to business hours, they may succeed in staying hidden for extended periods, increasing the risk of prolonged data exposure or silent surveillance. This could lead to widespread data breaches, service disruptions, and unauthorized surveillance across various sectors.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Key Intelligence Signals:
Sophisticated Earth Kurma Cyber Espionage Targets Southeast Asia’s Public and Telecom Sectors
Summary:
The Earth Kurma APT campaign targets government and telecommunications sectors in Southeast Asia, utilizing a sophisticated set of malware and tools for cyberespionage. The attackers, active since at least 2020, primarily focus on data exfiltration through trusted cloud services such as Dropbox and OneDrive. Their operations involve using advanced custom malware, rootkits, and tools designed to evade detection, maintain persistence, and exploit the infrastructure of compromised organizations.
The attackers deploy keyloggers, such as KMLOG, to capture sensitive credentials. Persistence is achieved through loaders like DUNLOADER, TESDAT, and DMLOADER, which enable the continuous deployment of payloads and further malware installation. These loaders are designed to operate stealthily, employing techniques such as reflective loading and in-memory execution to avoid detection by security software.
Rootkits, including KRNRAT and MORIYA, are used to hide the attackers’ activities at the kernel level. MORIYA, for instance, intercepts and injects malicious code into TCP traffic, while KRNRAT serves as a backdoor with features like process manipulation and traffic concealment. These rootkits ensure that the attackers remain undetected while maintaining control over compromised systems.
For data exfiltration, Earth Kurma employs tools like SIMPOBOXSPY and ODRIZ to upload stolen documents to cloud storage services. The exfiltration process is highly targeted, focusing on documents with specific extensions such as .pdf, .docx, and .xlsx, which are archived and encrypted before being uploaded. The attackers leverage native Windows mechanisms like Distributed File System Replication (DFSR) to move exfiltrated files across the network and ensure they reach external servers.
This APT campaign highlights the persistent threat of state-sponsored cyberattacks, with a clear focus on strategic espionage using advanced malware and cloud services to evade detection and exfiltrate sensitive data. Effective mitigation requires securing network protocols, auditing critical directories, and enforcing strict driver installation policies.
Relevancy & Insights:
The Earth Kurma APT campaign, identified by researchers, targets government and telecommunications sectors in Southeast Asia using a stealthy and persistent malware ecosystem. While the exact initial access vector remains unknown due to delayed discovery, the group employs customized loaders (DUNLOADER, TESDAT, DMLOADER), rootkits (MORIYA, KRNRAT), and malware such as Cobalt Strike beacons for post-compromise persistence, lateral movement, and espionage. They use open-source tools like WMIHACKER, LADON, and FRPC for reconnaissance and privilege escalation, and tools like KMLOG for credential theft. Earth Kurma exfiltrates sensitive documents using Dropbox and OneDrive via custom tools SIMPOBOXSPY and ODRIZ, leveraging the Windows DFSR mechanism for stealthy data replication. Their malware TTPs align partially with known APTs such as ToddyCat and Operation TunnelSnake, though attribution remains inconclusive.
ETLM Assessment:
Earth Kurma is a sophisticated advanced persistent threat (APT) group known for targeting government and telecommunications sectors across Southeast Asia, particularly in countries such as the Philippines, Vietnam, Thailand, and Malaysia. Active since at least November 2020, the group specializes in cyber espionage, employing tailored malware and rootkits to infiltrate networks and extract sensitive information. Notably, Earth Kurma makes strategic use of public cloud services like Dropbox and OneDrive to discreetly exfiltrate stolen data, blending seamlessly into legitimate network traffic to evade detection.
The group uses sophisticated malware, including tools like TESDAT, SIMPOBOXSPY, KRNRAT, and MORIYA, along with rootkits and loaders to maintain persistence within victim networks. They target various vulnerabilities in the infrastructure and rely on advanced evasion techniques to avoid detection. Previously, similar tools were linked to other APT groups, but Earth Kurma operates independently with a tailored approach.
Looking forward, CYFIRMA assesses that the threat is expected to persist, with adaptive techniques and evolving toolsets to bypass security measures, making it critical for organizations to strengthen defenses and actively monitor for advanced threats.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial Access | T1078.004 | Valid Accounts: Cloud Accounts |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1564.001 | Hidden Files and Directories |
| Credential Access | T1056 | Input Capture |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518.001 | Security Software Discovery |
| Collection | T1056 | Input Capture |
| Command and Control | T1071 | Application Layer Protocol |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian hackers target Dutch and French critical infrastructure
The Dutch Military Intelligence and Security Service (MIVD) has issued a warning about increased cyber activity by Russian state-sponsored threat actors targeting the Netherlands’ critical infrastructure, according to The Record. The agency revealed that in 2023, Russian hackers attempted to sabotage the “digital operating system of a public facility” in the country. Although the attack caused no damage, the MIVD noted it was the first known instance of cyber sabotage targeting such a control system within the Netherlands.
Meanwhile, in a rare and direct accusation, France’s Ministry for Europe and Foreign Affairs publicly condemned cyberattacks linked to APT28, a hacking group associated with Russia’s military intelligence agency, the GRU. The ministry stated it “condemns in the strongest possible terms” the actions of the group, also known as Fancy Bear.
French officials reported that APT28 has been conducting cyber operations against approximately ten French entities since 2021. Targets included government services, private companies, and a sports organization involved in preparations for the Olympics.
APT28, active since at least 2004, has a history of high-profile cyberattacks, including the 2015 breach of French TV station TV5Monde and interference in France’s 2017 presidential election. The group has also targeted institutions in Germany, Poland, and across Europe and the U.S., employing tactics such as phishing, brute-force attacks, and exploiting zero-day vulnerabilities. According to France’s national cybersecurity agency (ANSSI), the group often uses inexpensive, easily obtained infrastructure—like rented servers and VPNs—to mask its activities and hinder attribution.
ETLM Assessment:
France’s decision to go public with the accusations comes amid heightened geopolitical tensions and growing concern over Russia’s ongoing invasion of Ukraine. President Emmanuel Macron said that Western allies plan to intensify pressure on Moscow over the next 10 days in a bid to force a ceasefire in Ukraine. Earlier this week, Russian President Vladimir Putin announced a so-called “humanitarian” truce in Russia’s war against Ukraine to mark the 80th anniversary of the end of World War II in Europe, which is a ploy to allow him to hold a military parade in Moscow undisturbed.
Spanish Judiciary to Investigate Whether Massive Blackout Was a Cyberattack
A massive power outage hit the Iberian Peninsula, disrupting electricity supplies across Spain, Portugal, Andorra, and parts of southern France. Spanish grid authorities indicated that full restoration could take between six and ten hours, while their Portuguese counterparts warned recovery might extend up to a week. The blackout disabled subway systems, phone networks, and traffic lights, severely impacting public transportation and causing major traffic congestion and flight delays throughout the region.
A judge at Spain’s National Court has launched an investigation to determine whether Monday’s nationwide blackout may have been caused by a cyberattack. As part of the inquiry, the judiciary has requested detailed reports from the national cybersecurity agency, the power grid operator, and the national police outlining the circumstances surrounding the outage. In a statement, the court said that although the exact cause of the blackout remains unclear, “cyber terrorism is among the possibilities,” prompting the need for a formal investigation.
With the investigation still ongoing, an electricity company has been hit with a cyber-attack in Nova Scotia, which has affected parts of its Canadian network and servers supporting portions of its business.
ETLM Assessment:
While the attack in Canada has not caused damage to the grid itself and the electricity generation and distribution operations, the blackout in Spain has been the worst in recent decades in all of Europe. As of writing, a cyberattack seems unlikely as the ultimate cause of the blackout, however, the case highlights the increasing vulnerability of interdependent grid operations in the 21st century, while hostile actors like China and Russia are making inroads to critical infrastructure virtually everywhere.
The Qilin Ransomware Impacts MS SUPPLY CHAIN SOLUTIONS (MALAYSIA) SDN. BHD
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia; MS SUPPLY CHAIN SOLUTIONS (MALAYSIA) SDN. BHD (https[:]//www[.]mscsm[.]com[.]my/), was compromised by Qilin Ransomware. MS Supply Chain Solutions (Malaysia) Sdn Bhd – (MSCSM) is a subsidiary of MITSUI-SOKO Supply Chain Solutions, Inc. This company provides integrated high-quality logistics services such as factory logistics solutions, storage, transport, value-added services, import and export services, and so on. The compromised data consists of sensitive financial data, customer and employee data, confidential personal data, etc. The total size of the compromised data is approximately 183 GB.
The following screenshot was observed published on the dark web:
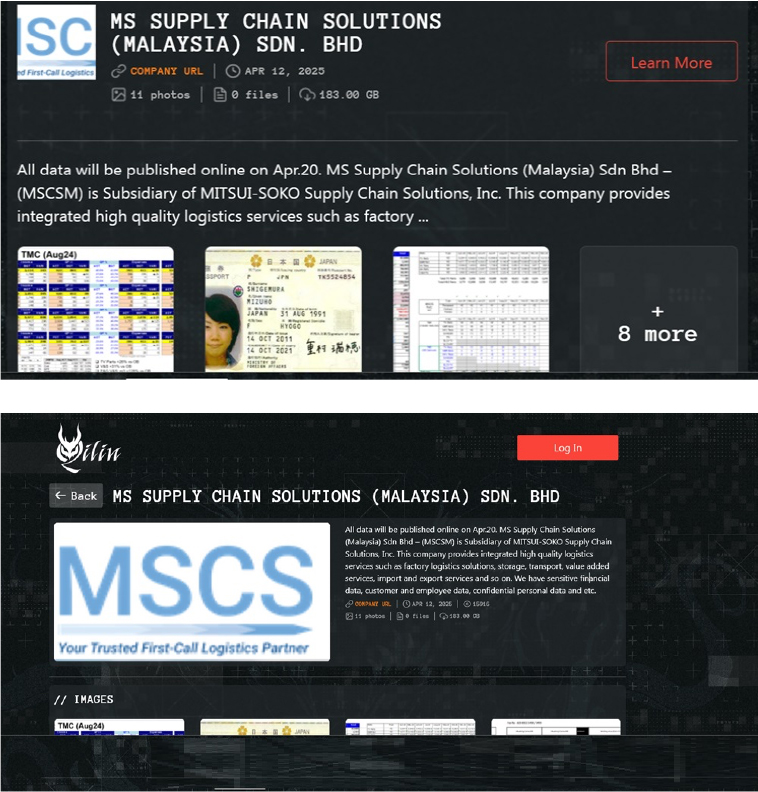
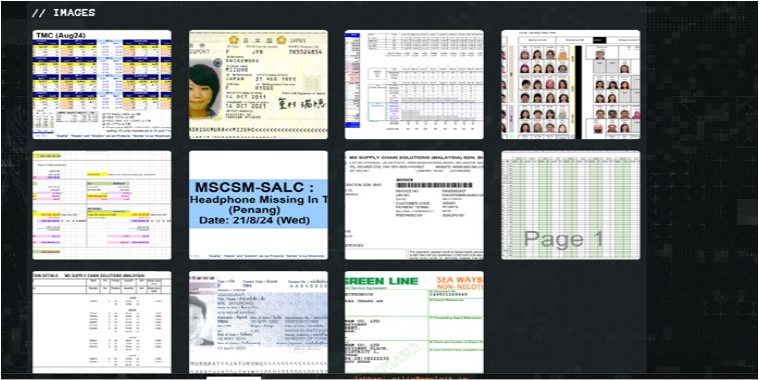
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion make it a particularly dangerous actor.
The Brain Cipher Ransomware Impacts MBM Gulf
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United Arab Emirates (UAE), MBM Gulf (https[:]//www[.]mbmdubai[.]com/), was compromised by Brain Cipher Ransomware. MBM Gulf is a prominent Mechanical, Electrical, and Plumbing (MEP) services provider based in Dubai, United Arab Emirates (UAE). The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data included confidential emails from company managers, financial reports, details of partnerships with key contractors, and personal information of employees.
The following screenshot was observed published on the dark web:
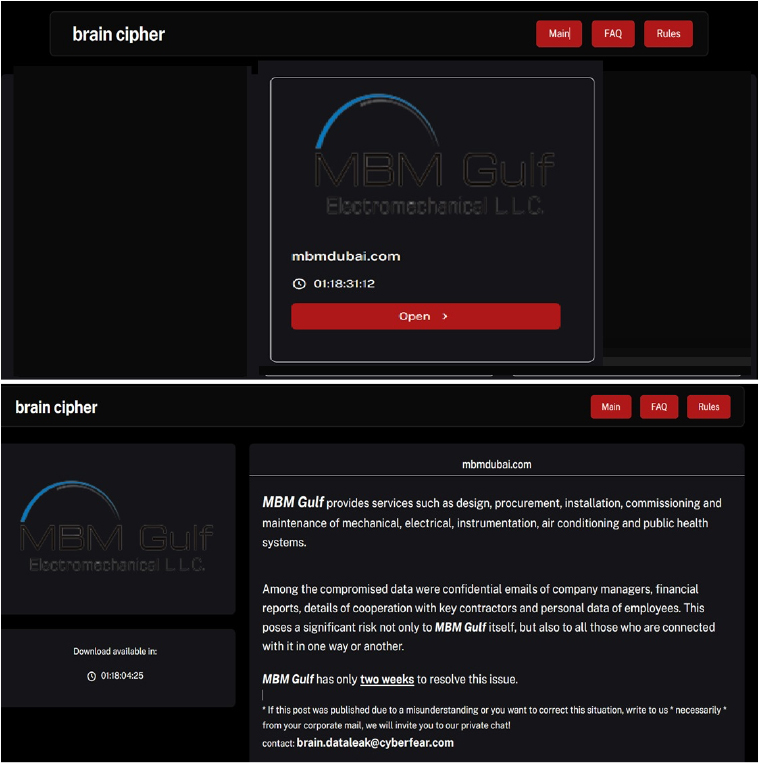
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Brain Cipher Ransomware represents a growing threat in the cybersecurity landscape, particularly due to its focus on critical infrastructure and government entities. Organizations must enhance their cybersecurity measures, including robust incident response plans and employee training on recognizing phishing attempts, to mitigate risks associated with this evolving threat. Continuous monitoring and updating of security protocols are essential to defend against such sophisticated attacks.
Vulnerability in Custom Admin-Bar Favorites plugin for WordPress
Relevancy & Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data in the “menuObject” parameter. A remote attacker can trick the victim into following a specially crafted link and execute arbitrary HTML and script code in the user’s browser in the context of a vulnerable website.
Impact:
Successful exploitation of this vulnerability may allow a remote attacker to steal potentially sensitive information, change the appearance of the web page, and perform phishing and drive-by-download attacks.
Affected Products:
https[:]//www[.]wordfence[.]com/threat-intel/vulnerabilities/id/417fb507-a414-4bc2-ab01-d6f2fc554350?source=cve
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
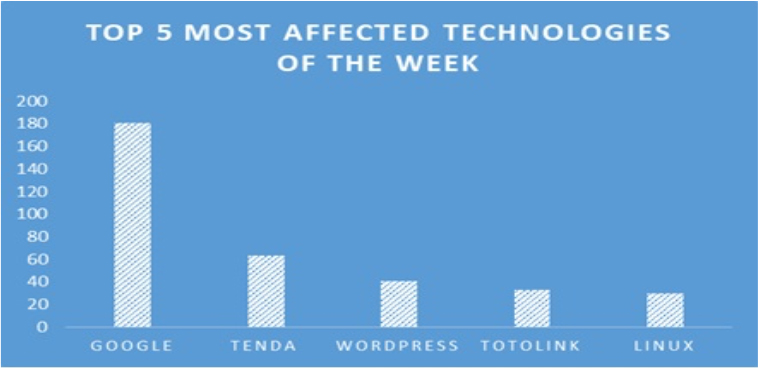
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in the Custom Admin-Bar Favorites plugin for WordPress can pose significant threats to user privacy and security. This can impact various industries globally, including technology, media, education, and beyond. Ensuring the security of the Custom Admin-Bar Favorites plugin is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding customized admin toolbar functionalities and ensuring secure, efficient access to favorite links within the WordPress dashboard across different geographic regions and sectors.
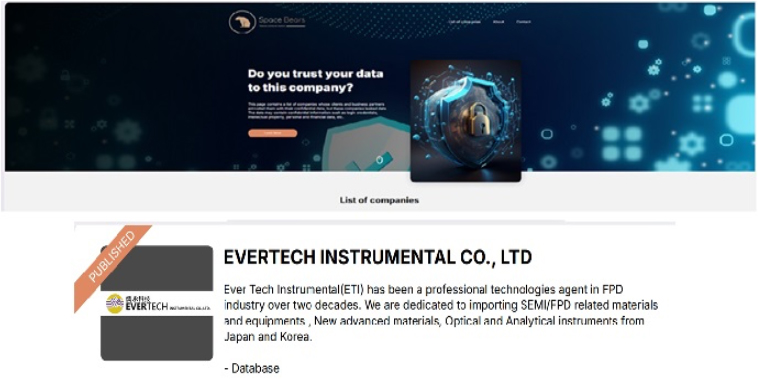
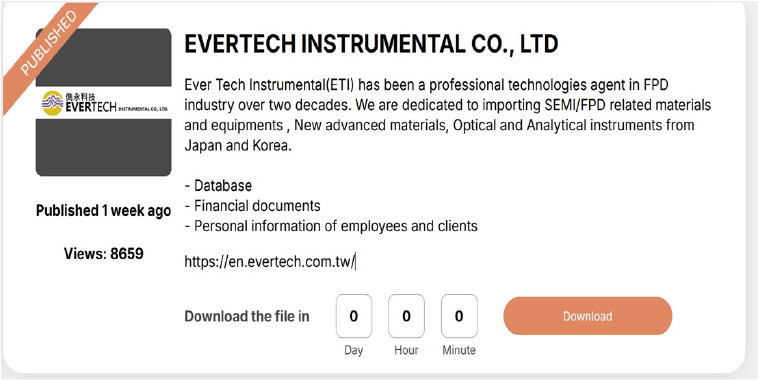
Space Bears Ransomware attacked and published the data of EVERTECH INSTRUMENTAL CO., LTD
Summary:
Recently, we observed that Space Bears Ransomware attacked and published the data of EVERTECH INSTRUMENTAL CO., LTD (https[:]//en[.]evertech[.]com[.]tw/) on its dark web website. EVERTECH Instrumental Co., Ltd. (ETI) is a Taiwan-based company that operates as a technology agent, specializing in the flat panel display (FPD) and semiconductor sectors. The company is primarily engaged in the import and distribution of equipment and materials for SEMI/FPD applications, advanced materials, as well as optical and analytical instruments sourced from Japan and Korea. The data breach resulting from the ransomware attack includes the database, financial documents, and personal information of both employees and clients.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Space Bears ransomware represents a significant threat in the evolving landscape of cybercrime. With its aggressive tactics, association with established ransomware operations like Phobos, and focus on double extortion, organizations are advised to bolster their cybersecurity measures to mitigate risks associated with such attacks. Continuous monitoring of this group’s activities will be essential for understanding their methods and potential impact on various sectors.
ICICI Bank (Saudi Arabia) Customers’ Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that a threat actor claims to be selling sensitive transaction notification data linked to ICICI Bank customers in Saudi Arabia. The dataset reportedly includes debit amounts, account numbers, and dispute resolution contact details.

Malaysia’s Prime Minister’s Data Advertised on a Leak Site
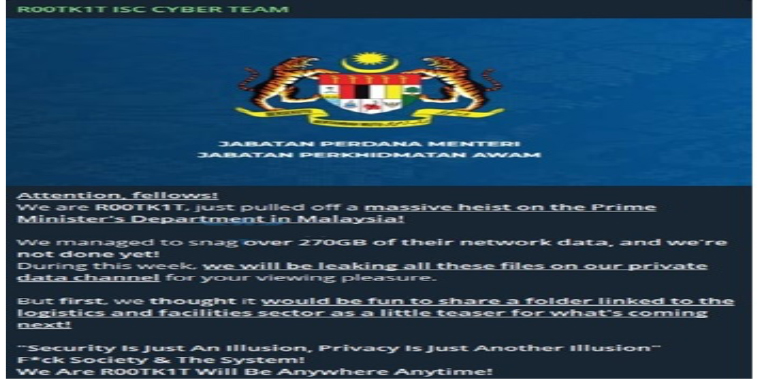
Summary:
The CYFIRMA Research team observed that R00TK1T ISC CYBER TEAM claims to have breached the network of Malaysia’s Prime Minister’s Department, exfiltrating over 270GB of data. The group has leaked a folder related to the logistics and facilities sector and announced plans to release the remaining files throughout the week.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
R00TK1T ISC CYBER TEAM represents a significant and volatile hacktivist threat actor characterized by its public-facing operations and geopolitically motivated attacks. The group executes disruptive campaigns targeting a diverse range of sectors, including critical infrastructure (telecommunications, aviation), government entities, and multinational corporations across various geographic locations. From a defensive standpoint, R00TK1T highlights the importance of a layered security posture. Continuous monitoring of the external attack surface, prompt patching of identified vulnerabilities, implementation of strong access controls, and monitoring threat intelligence feeds for specific mentions or related TTPs are crucial mitigation strategies.
Recommendations: Enhance the cybersecurity posture by
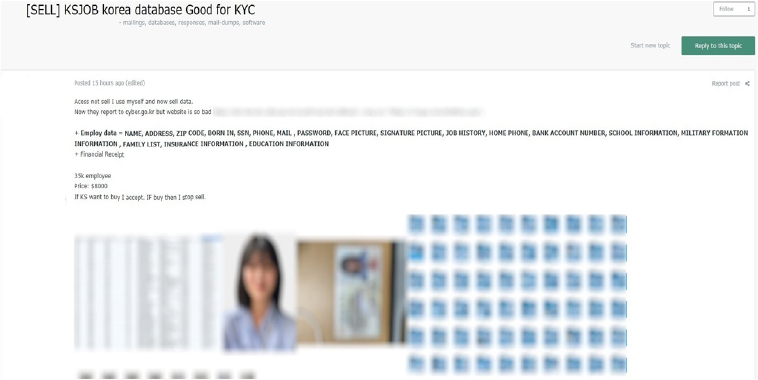
The CYFIRMA Research team observed that a threat actor is offering a database allegedly containing sensitive employee information from a Korean organization.
Data Includes:
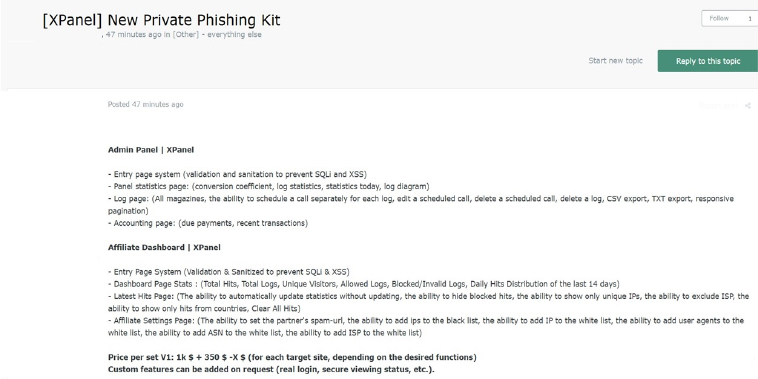
The CYFIRMA Research team observed that a threat actor is offering a private phishing kit named XPanel, featuring an admin and affiliate dashboard setup with extensive customization options for real-time data management and campaign automation.
Product:
XPanel (Admin Panel & Affiliate Dashboard)
Admin Panel Features:
Affiliate Dashboard Features:
Pricing:
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
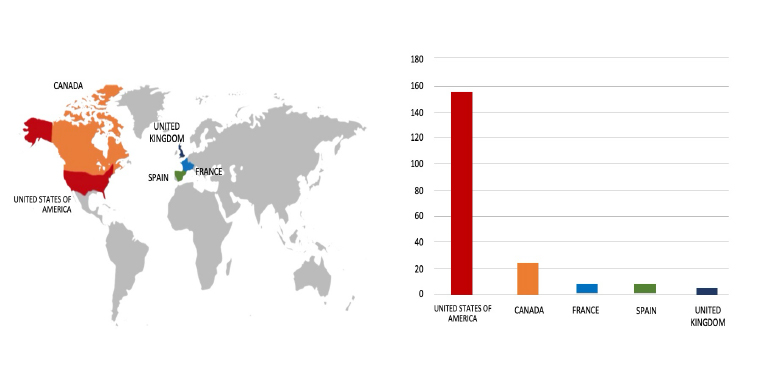
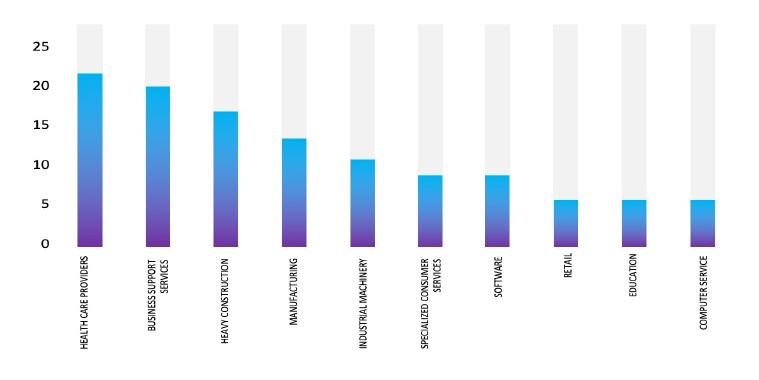
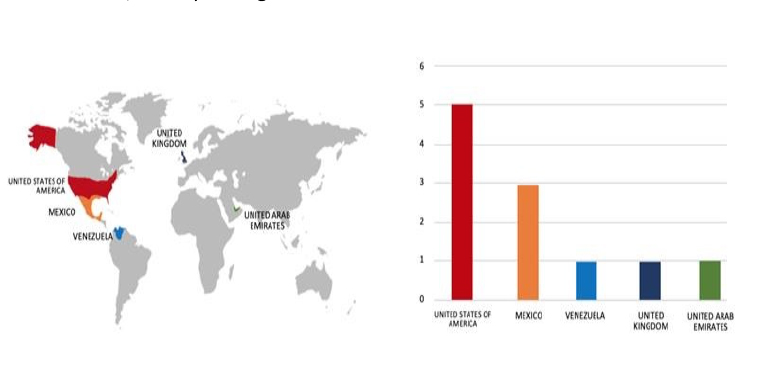
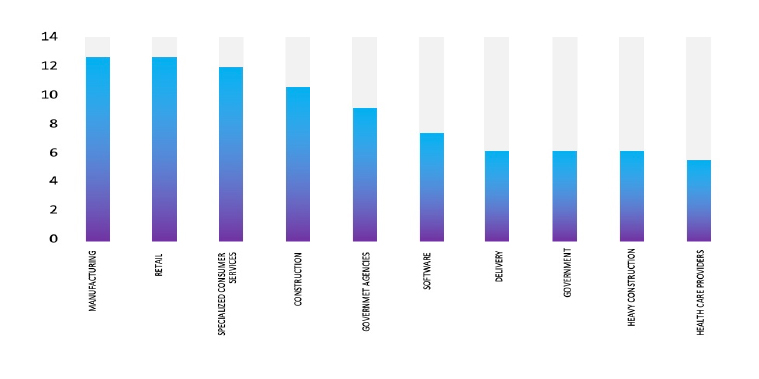
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph