



Key Intelligence Signals:
Tropical Scorpius aka Void Rabisu Shifted its Focus to Geopolitics and Deploys RomCom Backdoor
Summary:
Recently, researchers detected the campaign started in mid-2022 attributed to the threat actor named Void Rabisu, also known as Tropical Scorpius, who is connected to both the Cuba ransomware and the RomCom backdoor. The threat actor was financially motivated and used to target ransomware. However, the focus shifted in the month of October 2022, and the threat actor started attacking with geopolitical aims. Void Rabisu has been employing Google Ads to attract its targets and direct them to the lure sites. Additionally, the RomCom campaigns conducted by Void Rabisu involve the use of highly targeted spear phishing emails. This campaign distributing the RomCom backdoor malware is impersonating the websites of well-known or fictional software, tricking users into downloading and launching malicious installers. The recent RomCom activity has revealed several instances of websites used by malware operators from December 2022 to April 2023. These websites mimic legitimate software such as Gimp, Go to Meeting, ChatGPT, WinDirStat, AstraChat, System Ninja, Devolutions’ Remote Desktop Manager, and others. These deceptive websites are designed to trick users into downloading malicious RomCom software. The fake websites used in RomCom campaigns are promoted through Google advertisements and targeted phishing emails, primarily focusing on victims located in Eastern Europe. These websites distribute MSI installers that imitate legitimate applications but are compromised with a malicious DLL file called “InstallA.dll.” When the victim runs the installer, the malicious file extracts three additional DLLs into the %PUBLIC%\Libraries folder. These extracted DLLs are responsible for handling communication with the command-and-control server and executing commands as instructed by the operators.
Insights:
Void Rabisu demonstrates a level of sophistication in its operations, combining tactics such as Google Ads, targeted spear phishing, and the use of deceptive websites to distribute their malicious payloads. Their connection to Cuba ransomware and RomCom backdoor indicates a broad range of activities and potentially underscores their involvement in a variety of cyber threats.
The RomCom backdoor has evolved by incorporating advanced techniques used by both APT groups and prominent cybercriminal campaigns, indicating the adoption of detection evasion methods. Void Rabisu is an example of a financially motivated threat actor whose goals align with geopolitical circumstances, which is expected to continue and grow.
The Pentagon has recently presented its renewed 2023 cyber strategy to Congress. The Ministry says the strategy represents an evolution of the 2018 strategy document and provides direction for the implementation of the 2022 National Defense Strategy in cyberspace. The document itself is classified, but Pentagon has released an unclassified fact sheet, which emphasizes that the strategy is taking important lessons from Russia’s ongoing war on Ukraine, which “has demonstrated how cyber capabilities may be used in a large-scale conventional conflict.” The fact sheet also identifies the principal sources of threats in cyberspace to be China (characterized as an actor that pushes the tempo in the fifth domain), Russia (characterized as an actor with demonstrated capability and will to hit critical infrastructure), North Korea, Iran, “violent extremist organizations,” and transnational criminal organizations (often aligned with the “foreign policy objectives” of the governments that support and protect them, also known as privateers ).
Iranian threat actor Agrius has been observed continuing to target unnamed entities in Israel. Researchers’ observations suggest that what appear to be destructive ransomware attacks are masking influence operations. The APT group, now calling both itself and its newest ransomware strain “Moneybird,” has been seen in recent attacks deploying their unseen ransomware written in C++. The first point of compromise was public-facing web servers, which, once breached, gave hackers access to networks, enabling them to move laterally and conduct reconnaissance and data theft.
Another Iranian threat group has been observed attacking Israeli shipping and logistics companies in an attempt to steal customers’ data. This activity has been attributed with low confidence to a known APT TA456, also called Imperial Kitten. At least eight companies were impacted by the campaign, according to researchers.
A joint advisory from all Five Eyes countries (Australia, Canada, New Zealand, the United Kingdom, and the United States) reports a major Chinese cyberespionage operation that has reportedly succeeded in penetrating a range of US critical infrastructure sectors. The attack is attributed to a Chinese APT known as Volt Typhoon, a group that has been active for at least two years. The industries of communications, manufacturing, utilities, transportation, construction, maritime industries, government, information technology, and education have all become targets of the observed campaign. The threat actor has likely been trying to conduct espionage and keep access, without being discovered for as long as feasible, according to the observed behaviour.
Guam, a US territory in the Western Pacific that is home to significant US military bases, has been the target of a large portion of the alleged activity. Should China choose to follow Russia’s geopolitical lead and invade what it sees as a rebellious province, those bases would be crucial to any US involvement on behalf of Taiwan. China, for its part, rejects the accusations as the result of a planned American misinformation effort and denies taking part in any of the actions, the Five Eyes claim it did in connection with the Volt Typhoon.
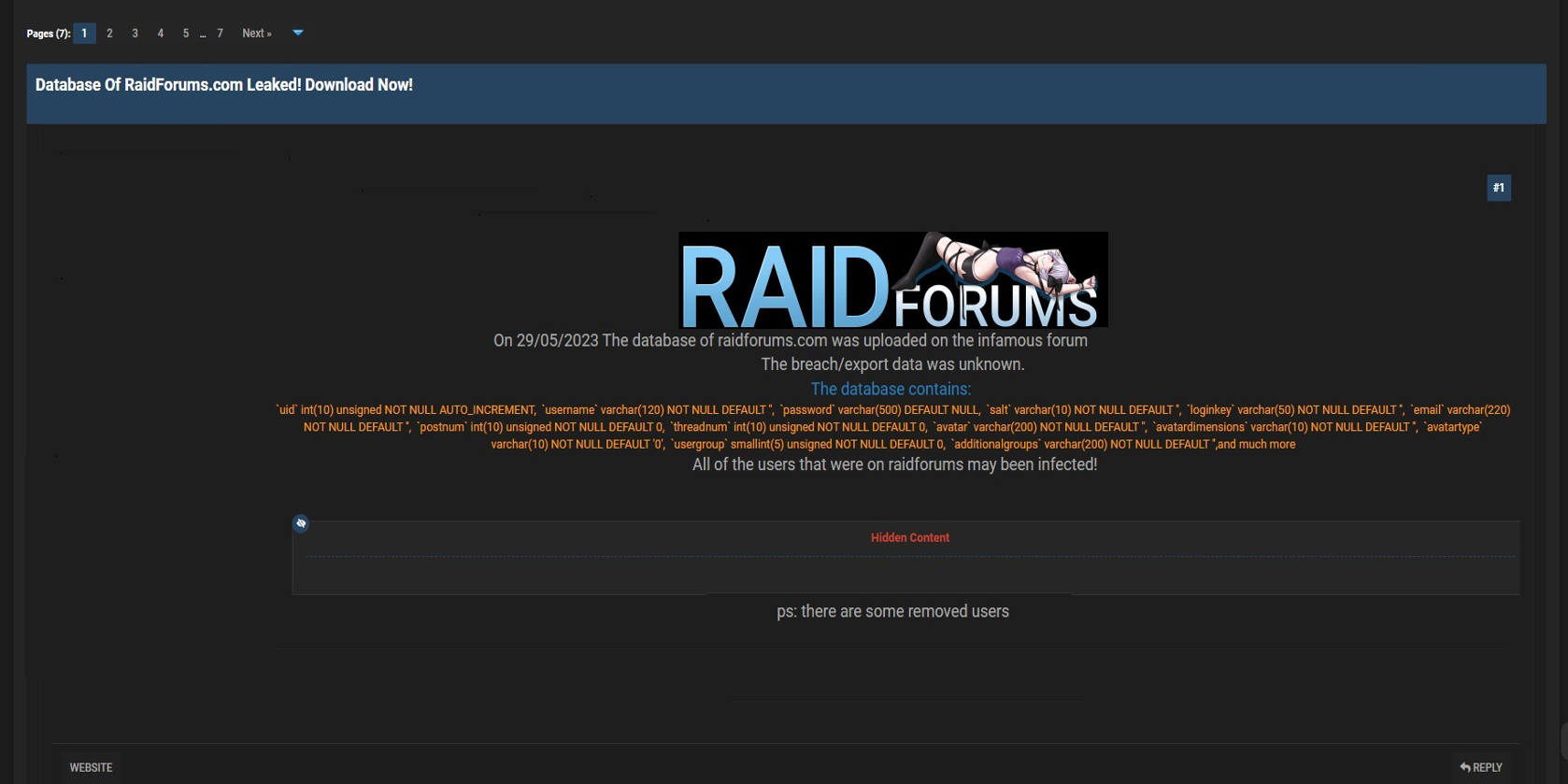
CYFIRMA Research team observed a potential data leak related to RaidForums, (www[.]raidforums[.]com). RaidForums is a database-sharing and marketplace forum. They have exclusive database breaches and leaks, plus an active marketplace. The compromised data includes various sensitive information, such as username (stored as varchar), password (stored as varchar), salt (stored as varchar), login key (stored as varchar), and other confidential data.
Source: Underground forums