



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows, Linux.
Target Geographies: Bangladesh, Canada, Germany, Portugal, Sweden, United States, UK.
Target Industries: Business Training and Employment Agencies, Business Services, Containers and packaging, Education, Farming, Fishing & Plantations, Government Agencies, Health Care, Heavy Construction, Industrial Goods and services, Industrial Machinery, Media, Real Estate, Restaurants and bars, Specialized Consumer Services.
The CYFIRMA Research and Advisory Team has identified recent updates of the Akira ransomware during its monitoring of various underground forums as part of the Threat Discovery Process.
Relevancy: From the onset of its operation, the ransomware has targeted various industries. The recent such targets include:
Akira’s ransomware operation is targeting corporate networks globally.
While another ransomware named Akira was released in 2017, there is no evidence suggesting that the current Akira ransomware operations are connected to it.
The ransomware strain targeting the Windows Operating system looks to be based on the Conti ransomware source code.
The group will add the file extension “.akira” to the encrypted files’ name during the encryption process. Upon encrypting the files on a computer, the ransomware generates a ransom note named “akira_readme.txt” in every folder, explaining the situation to the victim and providing links to the Akira data leak and negotiation sites.
The ransomware attempts to remove the Windows Shadow Volume Copies from the infected device once it is executed.
The ransomware will encrypt the files with the following file extensions:
.accdb, .accde, .accdc, .accdt, .accdr, .adb, .accft, .adf, .ade, .arc, .adp, .alf, .ora, .btr, .ask, .cat, .bdf, .ckp, .cdb, .cpd, .cma, .dad, .dacpac, .daschema, .dadiagrams, .db-shm, .db-wal, .dbf, .dbc, .dbt, .dbs, .dbx, .dbv, .dct, .dcb, .ddl, .dcx, .dlis, .dsk, .dqy, .dtsx, .dsn, .eco, .dxl, .edb, .ecx, .exb, .epim, .fdb, .fcd, .fmp, .fic, .fmpsl, .fmp12, .fol, .fpt, .gdb, .frm, .gwi, .grdb, .his, .hdb, .idb, .itdb, .ihx, .jet, .itw, .kdb, .jtx, .kexic, .kexi, .lgc, .kexis, .maf, .lwx, .mar, .maq, .mav, .mas, .mdf, .mdb, .mrg, .mpd, .mwb, .mud, .ndf, .myd, .nrmlib, .nnt, .nsf, .nyf, .nwdb, .oqy, .odb, .owc, .orx, .pdb, .pan, .pnz, .pdm, .qvd, .qry, .rctd, .rbf, .rodx, .rod, .rsd, .rpd, .sbf, .sas7bdat, .sdb, .scx, .sdf, .sdc, .spq, .sis, .sqlite, .sql, .sqlitedb, .sqlite3, .temx, .tps, .tmd, .trm, .trc, .udl, .udb, .usr, .vpd, .vis, .wdb, .vvv, .wrk, .wmdb, .xld, .xdb, .abcddb, .xmlff, .abx, .abs, .adn, .accdw, .icg, .hjt, .kdb, .icr, .maw, .lut, .mdt, .mdn, .vhd, .vdi, .pvm, .vmdk, .vmsn, .vmem, .nvram, .vmsd, .raw, .vmx, .subvol, .qcow2, .vsv, .bin, .vmrs, .avhd, .avdx, .vhdx, .iso, .vmcx.
During encryption, it will not encrypt the files found in the Recycle Bin, System Volume Information, Boot, ProgramData, and Windows folders. It will also avoid encrypting the Windows system files with .exe, .lnk, .dll, .msi, and .sys file extensions.
Windows Restart Manager API is employed by Akira to close processes or shut down Windows services that may be keeping a file open and preventing encryption.
Similar to other ransomware attacks, the Akira ransomware will initially breach a corporate network and then spread to other devices through lateral movement. The threat actors behind Akira will then attempt to obtain Windows domain admin credentials, which they will use to deploy the ransomware throughout the network.
Before encrypting the files, the attackers will first exfiltrate sensitive corporate data. They will then use this data as leverage during their extortion attempts, threatening to publicly release it if the ransom is not paid.
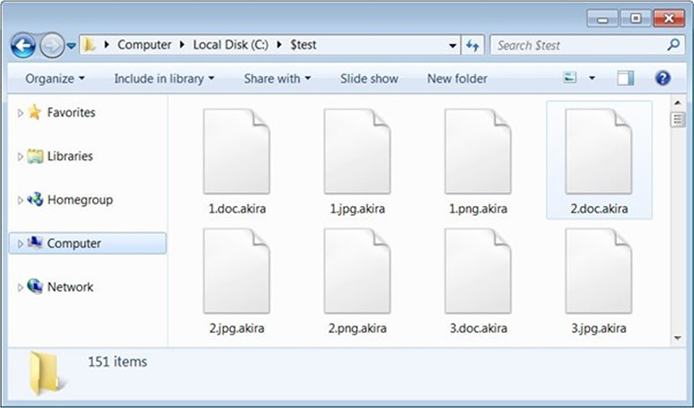
Screenshot of files encrypted by Akira ransomware (Windows). (Source: Surface Web)
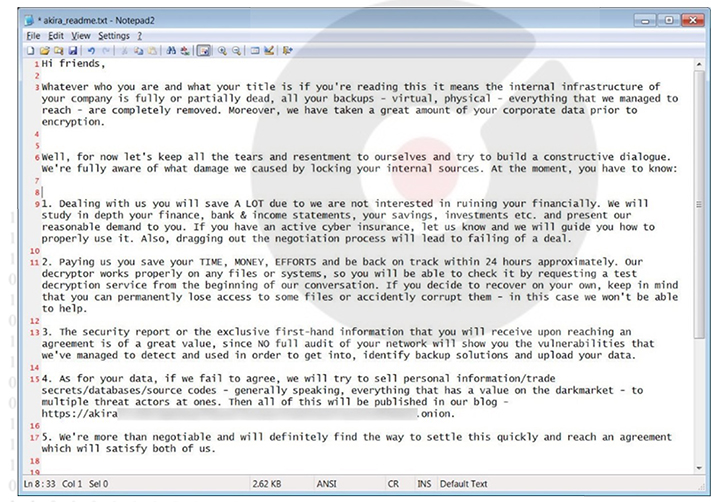
Windows Akira ransomware note. (Source: Surface Web)
The Akira ransomware group uses a Linux encryptor to target and encrypt VMware ESXi virtual machines.
Encrypted files will be renamed to have the “.akira” extension, and a hardcoded ransom note named akira_readme.txt will be created in each folder on the encrypted device.
According to researchers, the Linux encryptor used by the Akira ransomware group carries the project name ‘Esxi_Build_Esxi6,’ signifying a specific focus on targeting VMware ESXi servers.
In contrast to other VMware ESXi encryptors analyzed by researchers, Akira’s encryptors lack some advanced features like automatically shutting down virtual machines using the esxcli command before encryption.
However, the binary does offer specific command line options enabling attackers to tailor their assaults:
-p –encryption_path (specific file/folder paths)
-s –share_file (designated network drive path)
– n –encryption_percent (encryption percentage)
–fork (generation of a child process for encryption)
The -n parameter is particularly notable as it allows attackers to define how much data is encrypted on each file.
When encrypting files, the Linux Akira encryptor focuses on the following file extensions:
.4dd, .accdb, .accdc, .accde, .accdr, .accdt, .accft, .adb, .ade, .adf, .adp, .arc, .ora, .alf, .ask, .btr, .bdf, .cat, .cdb, .ckp, .cma, .cpd, .dacpac, .dad, .dadiagrams, .daschema, .db- shm, .db-wa, .db3, .dbc, .dbf, .dbs, .dbt, .dbv, .dbx, .dcb, .dct, .dcx, .dlis, .dp1, .dqy, .dsk, .dsn, .dtsx, .eco, .ecx, .edb, .epim, .exb, .fcd, .fdb, .fic, .fmp, .fmp12, .fmps, .fp3, .fp4, .fp5, .fp7, .fpt, .frm, .gdb, .grdb, .gwi, .hdb, .his, .idb, .ihx, .itdb, .itw, .jet, .jtx, .kdb, .kexi, .kexic, .kexis, .lgc, .lwx, .maf, .maq, .mar, .mas, .mav, .mdb, .mdf, .mpd, .mrg, .mud, .mwb, .myd, .ndf, .nnt, .nrmlib, .ns2, .ns3, .ns4, .nsf, .nv2, .nwdb, .nyf, .odb, .oqy, .orx, .owc, .p96, .p97, .pan, .pdb, .pdm, .pnz, .qry, .qvd, .rbf, .rctd, .rod, .rodx, .rpd, .rsd, .sas7bdat, .sbf, .scx, .sdb, .sdc, .sdf, .sis, .spq, .sqlite, .sqlite3, .sqlitedb, .temx, .tmd, .tps, .trc, .trm, .udb, .usr, .v12, .vis, .vpd, .vvv, .wdb, .wmdb, .wrk, .xdb, .xld, .xmlff, .abcddb, .abs, .abx, .accdw, .adn, .db2, .fm5, .hjt, .icg, .icr, .lut, .maw, .mdn, .mdt, .vdi, .vhd, .vmdk, .pvm, .vmem, .vmsn, .vmsd, .nvram, .vmx, .raw, .qcow2, .subvo, .bin, .vsv, .avhd, .vmrs, .vhdx, .avdx, .vmcx, .iso
The Linux locker avoids specific Windows-related folders and files, including executables. This implies that the Linux Akira version might be derived from its Windows counterpart. The files and folders are listed below,
winnt, temp, thumb, $Recycle.Bin, $RECYCLE.BIN, System Volume Information, Boot, Windows, Trend Micro, .exe, .dll, .lnk, .sys, .msi
Researchers found that the encryptor incorporates a public RSA encryption key. It utilizes several symmetric key algorithms for file encryption, encompassing AES, CAMELLIA, IDEA-CB, and DES.
The symmetric key serves to encrypt victim files, and subsequently, it undergoes encryption using the RSA public key. This strategy ensures that access to the decryption key remains restricted to those in possession of the attackers’ exclusive RSA private decryption key.
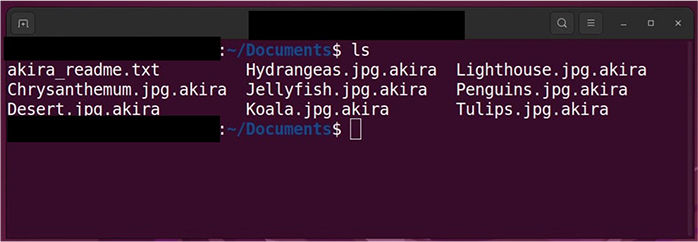
Screenshot of files encrypted by Akira ransomware (Linux). (Source: Surface Web)
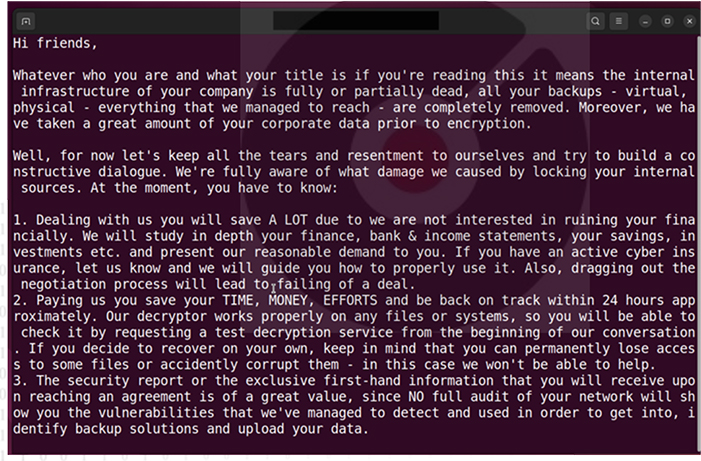
Akira ransom note dropped on Linux servers (source: surface web)
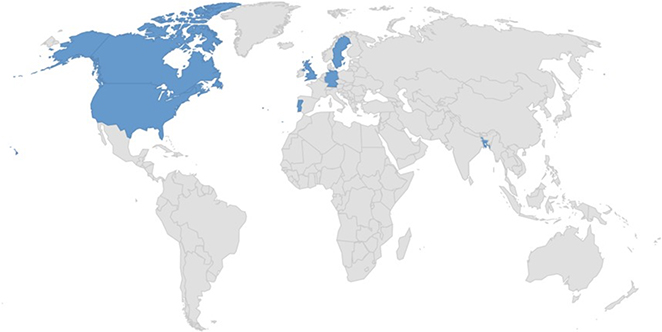
Countries targeted by Akira ransomware.
Following are the TTPs based on MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1190: Exploit Public-Facing Applicationts |
| 2 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1129:Shared Modules | ||
| 3 | TA0003: Persistence | T1176: Browser Extensions |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| 4 | TA0004: Privilege Escalation | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| 5 | TA0005: Defense Evasion | T1027: Obfuscated Files or Information |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 6 | TA0006: Credential Access | T1003: OS Credential Dumping |
| 7 | TA0007: Discovery | T1010: Application Window Discovery |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1518.001: Software Discovery: Security Software Discovery | ||
| T1614: System Location Discovery | ||
| 8 | TA0009: Collection | T1560: Archive Collected Data |
| T1005: Data from Local System | ||
| T1185: Browser Session Hijacking | ||
| 9 | TA0011: Command and Control | T1090: Proxy |
| T1105: Ingress Tool Transfer | ||
| 10 | TA0040: Impact | T1486: Data Encrypted for Impact |
Kindly refer to the IOCs section to exercise controls on your security systems. Sigma Rule:
title: Deletion of Volume Shadow Copies via WMI with PowerShell tags:
– attack.impact
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection_get:
CommandLine|contains:
– ‘Get-WmiObject’
– ‘gwmi’
– ‘Get-CimInstance’
– ‘gcim’ selection_shadowcopy:
CommandLine|contains: ‘Win32_Shadowcopy’ selection_delete:
CommandLine|contains:
– ‘.Delete()’
– ‘Remove-WmiObject’
– ‘rwmi’
– ‘Remove-CimInstance’
– ‘rcim’
condition: all of selection* falsepositives:
– Unknown level: high
(Source: Surface web)
Type: Banking Trojan
Objective: Steal Sensitive Information, Remote Access, Unauthorized financial transactions
Target Technology: Android OS
Target Geography: Southeast Asia
Target Industry: Banks
Active Malware of the Week
This week “MMRat” is trending.
Researchers have recently discovered a new, fully undetected Android banking trojan called MMRat, which has been targeting mobile users in Southeast Asia since late June 2023. MMRat has the ability to seize user input and screen content and can manipulate victim devices remotely to execute bank fraud. It employs a unique custom command-and- control protocol using protocol buffers (Protobuf), an open-source data format. This feature, which is rarely seen in Android banking trojans, enhances its performance during the transfer of large volumes of data.
The MMRat trojan comes from fake websites that look like real app stores. These websites use different languages to target specific people. However, researchers are unsure about how these fake links get onto people’s devices. The malware currently remains undetected on VirusTotal, highlighting the efficacy of its evasion techniques. Additionally, similar malware like GigabudRat and Vultur, utilizing tactics like keylogging and screen capturing, also achieve significant success in avoiding detection during their attack phases.
MMRat’s role in bank fraud involves a series of steps. In this attack scenario, the victim first downloads and installs MMRat, granting it permission. MMRat then establishes communication with a remote server, sending device status, personal data, and keylogging data. When the device is idle, the attacker can remotely awaken it, unlock the screen, and conduct bank fraud. Additionally, the attacker can capture the device screen for visual monitoring. The process concludes with MMRat uninstalling itself, erasing all signs of the malware.
MMRat can capture user input, screen content, and remotely control victims’ devices. It depends on the Android Accessibility service and MediaProjection API for its functionality.
Impersonation and persistence routine – MMRat employs disguises such as posing as a government or dating app to lower suspicion. Once launched, it directs victims to phishing websites. It sets up a receiver to monitor system events like powering on/off and reboots. Upon detecting these events, the malware initiates a 1×1-small pixel activity to maintain its presence on the device.
Network communication with remote server – Once the Accessibility service is activated, MMRat connects to a server controlled by the attacker. Remarkably, MMRat uses separate ports on the same server for various functions:
| Port | Protocol | Description |
| 8080 | HTTP | Data exfiltration |
| 8554 | RTSP | RTSP video streaming |
| 8887 | Customized | Command and Control |
The Communication and Control (C&C) protocol of MMRat is exceptional due to its personalized design using Netty (a network application framework) and Protobuf, which includes well-structured message formats. The threat actor employs a comprehensive structure to convey different message types, using the “oneof” keyword to represent diverse data types. Researchers carefully reconstructed the significant Protobuf layouts used in C&C communication. The “PackType” serves as an enum structure for C&C instructions, with the “pack” field containing specific data for various C&C commands.
Researchers observe the defined C&C commands and their corresponding explanations. This communication is two-way, split into server commands sent to the client and vice versa.
Collection of device status and personal information – MMRat gathers various device status and personal information like network details, screen activity, battery status, installed apps, and contact lists. Network data includes signal strength and type, while screen data indicates screen lock, active app, and displayed content. Battery data reveals the battery’s condition, contacts cover the user’s contact list, and installed apps encompass device applications. MMRat employs a timer task executing every second and a counter resetting every 60 seconds to promptly collect this data.
MMRat focuses on gathering the victim’s contact list and list of installed apps, likely with the intention of profiling the victim. This enables the threat actor to identify individuals with certain geographical or app-related attributes, potentially facilitating subsequent malicious actions.
Automatic permission approval – Once Accessibility permission is given, MMRat misuses it to acquire additional permissions and alter settings. For instance, during the data collection phase, MMRat can self-assign the READ_CONTACTS permission to gather contact data.
The code excerpt demonstrates MMRat’s capability to autonomously secure permissions. It achieves this by initiating the system dialog and automatically authorizing incoming permission requests. This automated approval mechanism identifies “ok” or related terms on the screen and uses Accessibility to simulate clicks. Consequently, MMRat can sidestep user involvement and independently acquire the required permissions for its harmful actions.
Actions and capturing user inputs – MMRat exploits the Accessibility service for keylogging, capturing user input and actions. This data aims to retrieve victim credentials and replay actions later. Unlike other keyloggers targeting specific scenarios, such as logging keys only when the victim is using bank apps, MMRat logs all user actions, transmitting them via the C&C channel. The threat actor seeks a wealth of action logs to determine the malware’s future steps. These logs are structured as LogInfo and serialized through Protobuf. Apart from keylogging, MMRat is particularly intrigued by lock screen patterns.
When the device is unlocked, the pattern is collected and uploaded via C&C, granting the attacker access even when the device is locked.
Capturing screen content – MMRat can capture and stream real-time screen content from the victim’s device to a remote server. It primarily employs the MediaProjection API to achieve this, recording the screen. However, another method called the “user terminal state” is used to bypass FLAG_SECURE protection. This capability likely complements remote control actions, allowing threat actors to monitor the device’s live status during bank fraud activities. Instead of capturing credentials, the malware continually checks for commands and halts screen content streaming if no commands are received within 30 seconds.
Android MediaProjection API – MMRat efficiently utilizes the MediaProjection API and exploits the open-source framework “rtmp-rtsp-stream-client-java” to stream video data to a remote server. This enables real-time recording and streaming of screen content via the Real Time Streaming Protocol (RTSP). Upon receiving the MEDIA_STREAM command, MMRat can record two types of data, screen, and camera data, based on the provided configuration. For instance, when capturing screen data, MMRat initiates an activity called DisplayActivity. This activity seeks recording permission through the createScreenCaptureIntent method, prompting a system dialog for approval. Notably, this system dialog is automatically accepted via auto-clicking. After obtaining approval, MMRat commences screen recording and uses the API startStream from the open-source framework repository to stream the data to the C&C server.
User terminal state – The “user terminal state” approach for capturing screen content in MMRat is distinct from the MediaProjection API method. In this approach, MMRat avoids recording the screen as a video. Instead, it leverages the Accessibility service to systematically extract all child nodes within Windows every second. The collected data is then uploaded via the C&C channel. As a result, only text-based information is obtained, lacking a graphical user interface, and resembling a “terminal.”
Despite its rudimentary nature, this method effectively gathers crucial information for remote monitoring and control, such as node data for interactions. While this approach demands additional effort from the threat actor to reconstruct data on the server side, it successfully bypasses FLAG_SECURE protection—a measure to prevent screenshots and screen recordings. Additionally, the implementation of Protobuf and customized Netty- based protocols optimizes performance, especially useful for the swift transfer of substantial screen data, providing a similar effect to a video stream for the threat actor.
Remote controlling – MMRat employs the Accessibility service to remotely manipulate victims’ devices, performing actions like gestures, screen unlocking, and text input. This capability, coupled with stolen credentials, facilitates bank fraud by malicious actors.
MMRat adopts preliminary steps for user evasion before executing its remote access routine. These steps include simulating a double-click to wake the device and using previously obtained unlock patterns to unlock the screen. Consequently, MMRat attains remote control over devices, even when users are not actively engaged with their phones.
Hiding tracks – MMRat has the ability to remove itself when it receives the C&C command UNINSTALL_APP. This action typically occurs after conducting bank fraud, adding a layer of complexity to tracking its actions.
Indicators of Compromise
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
New Threat Actor STAC4663 Linked to FIN8 Exploits RCE Vulnerability
Summary:
In a recent observation, the threat actor associated with the FIN8 group has been targeting Citrix NetScaler systems by exploiting the CVE-2023-3519 remote code execution vulnerability in a large-scale campaign. The attackers exploit the CVE-2023- 3519 vulnerability and share striking similarities with past attacks in terms of tactics, techniques, and procedures. In an attack observed in mid-August, the threat actors utilized the NetScaler vulnerability as a means of code injection. This included injecting payloads into “wuauclt.exe” or “wmiprvse.exe,” using BlueVPS ASN 62005 for staging malware and employing heavily obfuscated PowerShell scripts with distinct arguments. The researcher revealed tactics where the attacker deploys PHP web shells with random names onto the targeted machines. Researchers also mentioned that a similar attack Fox-IT had recently reported where around 2000 NetScaler systems were compromised worldwide due to CVE-2023-3519. The specifics of the injected payload are under ongoing analysis. A previous case with similar TTPs, though not tied to Citrix vulnerability, suggests a likely link to a recognized ransomware threat actor.
Researchers have labeled this pattern of activity as threat activity cluster number STAC4663. Citrix issued a patch on July 18, emphasizing that mitigation is solely possible through patching, as no workarounds exist.
Insights:
The deployment of obfuscated PowerShell scripts reveals a deliberate effort to evade detection and enact their malicious activities. The injection of payloads into legitimate system processes also reflects the intention of evading detections. In addition to this, the utilization of PHP web shells further underlines their strategy of establishing persistent backdoors on compromised machines. This tactic aligns with usual tactics seen across the cybersecurity landscape, where attackers focus on maintaining long- term access to systems.
Indicators of Compromise
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Crude “cyberattack” stops trains in Poland
A recent cyberattack in which an emergency radio signal was compromised, halted trains near the Polish city of Szczecin, resulting in forced stoppage of about twenty trains, affecting both freight and passenger service. The incident is currently under investigation by Poland’s internal security service ABW, however, the incident is likely to be a work of Russian hacktivist auxiliaries. Evidence for that attribution is circumstantial but compelling. The signals were interspersed with a recording of Russia’s national anthem and a speech by President Vladimir Putin. The Polish government has not called out the perpetrator yet but offered comments on previous attacks undertaken by the Russian Federation in conjunction with Belarus.
The emergency stop signal was transmitted over a legacy radio-frequency system that lacks either authentication or encryption, which makes it vulnerable to any attacker with the right equipment, which is both cheap and readily available. The emergency stoppage is triggered by a stop signal consisting of a series of three acoustic tones at a 150.100 megahertz frequency. The biggest difficulty such a hacker might face is getting physically close enough for their signal to be within range.
Future of Russia’s information operations upon death of Yevgeniy Prigozhin
Yevgeniy Prigozhin, who ran Russia’s Internet Research Agency and played a major role in developing Russian digital influence operations — most notably, interference in the 2016 U.S. elections — has been confirmed dead by the Russian authorities after a deadly plane crash.
One of the crucial parts of Prigozhin’s power in Russia has been his media empire centered around the aforementioned Internet Research Agency, also known as the Troll Factory. This part of the business was officially shut down earlier this month, after Mr. Prigozhin’s fall from grace, after the mutiny of his mercenaries by late June. Analysts speculate, however, that the core information operations and the psy-op part of the media group is currently being restructured and resurrected.
The Kremlin needs the services provided by Prigozhin’s troll factories, and will likely seek to save the capability, under the leadership of a different pro-Kremlin oligarch. Analysts speculate that this vacuum could be filled by the banker Yuri Kovalchuk, who owns most of the privately operated media in the country and is a close friend and ally of Vladimir Putin. The aftermath of Mr. Prigozhin’s mutiny and subsequent death may hold the information operations performed by the Kremlin back, but we should expect them to be back in full force within a couple of weeks or at maximum months. To read more about the role of Yevgeniy Prigozhin and the Troll Factory in Russian politics.
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in the dark forum that a company from the United States of America, (www[.]nasco[.]com), was compromised by Cl0p Ransomware. NASCO is a healthcare technology company, dedicated to co-creating digital health solutions for Blue Cross and Blue Shield companies. The data that has been compromised could potentially include sensitive and confidential information related to the organization, amounting to around 30 GB in size.
The following screenshot was observed published on the dark web:
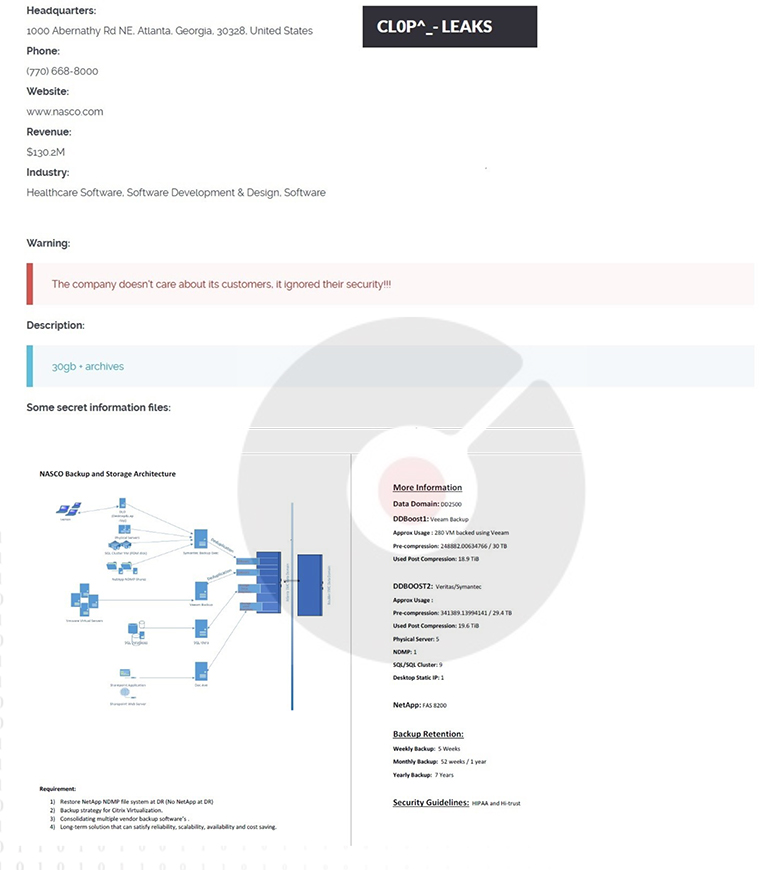
Source: Dark Web
Insights:
Recently, the Cl0p ransomware gang acknowledged its role in the data theft incidents involving MOVEit Transfer, where servers belonging to numerous companies were compromised through the exploitation of a zero-day vulnerability. This confirmation aligns with Microsoft’s attribution of these activities to the hacking group known as ‘Lace Tempest,’ also recognized as TA505 and FIN11.
The Cl0p ransomware victims across the globe from 25-08-2023 to 30-08-2023 are shown below.
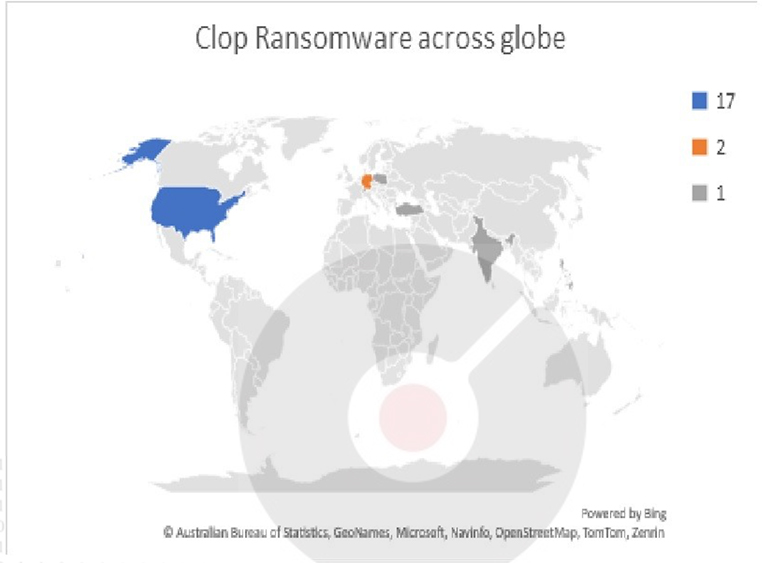
Summary:
The disclosed vulnerability allows a remote attacker to perform cross-site scripting (XSS) attacks.
Insights:
The vulnerability exists due to insufficient sanitization of user-supplied data. A remote attacker can trick the victim to follow a specially crafted link and execute arbitrary HTML and script code in user’s browser in context of vulnerable website.
Impact :
Successful exploitation of this vulnerability may allow a remote attacker to steal potentially sensitive information, change appearance of the web page, perform phishing and drive-by-download attacks.
Affected Products: : http[:]//codebeamer[.]com/cb/wiki/31346480
Hungary: Media freedom confronted with significant new threat from DDoS cyber-attacks
Summary:
Starting from April 2023, over 40 distinct media websites within Hungary have been targeted by Distributed Denial of Service (DDoS) attacks. This type of cyber assault, characterized by overwhelming website servers with millions of simultaneous access requests, effectively causing slowdowns or outages, has resulted in readers being unable to access news and information for prolonged periods. Although the precise intent behind these attacks is yet to be verified, most of the websites subjected to DDoS attacks are prominent independent media outlets in the country. This list encompasses Telex, HVG, 444.hu, Magyar Hang, and Népszava, all of which hold a critical stance toward Prime Minister Viktor Orbán’s government. In addition to these, international media enterprises like Forbes Hungary have also fallen victim to hacking attempts. While no actor has claimed responsibility, the hacker or hackers appear to go by the nickname HANO – an acronym in Hungarian for a type of disorder that affects the human body. In recent months, they have also left messages in Hungarian behind in the code of attacks, indicating that they are being coordinated domestically, rather than by foreign actors. The attacker appears to demonstrate a knowledge of the Hungarian media landscape and individual journalists.
Insights:
In alternate instances, within the code of DDoS attacks, messages were discovered that forewarned forthcoming assaults on specific media outlets. Subsequently, these predicted attacks transpired exactly as scheduled. The expenses linked to the extensive and prolonged nature of these DDoS attacks, spanning several months, also suggest that the individuals behind them possess relatively substantial financial resources, as stated by experts.
Vuliv Player’s Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to VuLiv Player, {www[.]vuliv[.]com}. VuLiv Player is an entertainment firm that offers services for mobile advertising platforms, remote content management, and media players. The data that has been compromised consists of UIDs, emails, operator, and circle information, along with other confidential details, all presented in SQL format. The overall size of the data is 5GB.
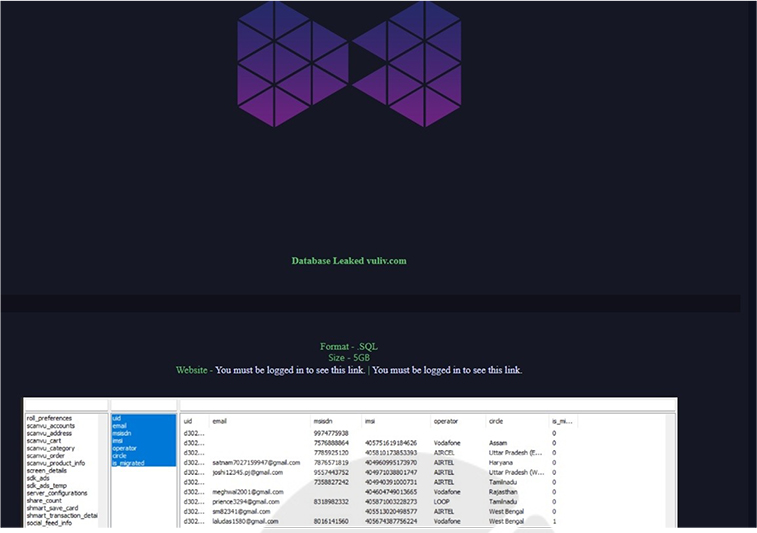
Source: Underground forums
Insights:
Cybercriminals driven by the pursuit of financial gains are constantly searching for exposed and susceptible systems and software. The majority of these malicious actors conduct their activities in hidden online communities, where they discuss relevant matters and trade stolen digital assets. In contrast to other financially motivated groups such as ransomware or extortion syndicates, who often publicize their exploits, these perpetrators prefer to remain discreet. They secure unauthorized access and filch valuable information by capitalizing on unpatched software or exploiting vulnerabilities within systems or applications. The ill-gotten data is subsequently promoted for sale within clandestine online spaces, and it may be further sold and repurposed by fellow attackers in their own campaigns.
CYFIRMA Research team observed a potential data leak related to Squeezer Software, {www[.]squeezer-software[.]com}. Squeezer Software is a company that operates in the Computer Software industry. The company is headquartered in Tunisia. The data that has been compromised includes user passwords, user email addresses, and other sensitive information in SQL format.
Source: Underground forums