



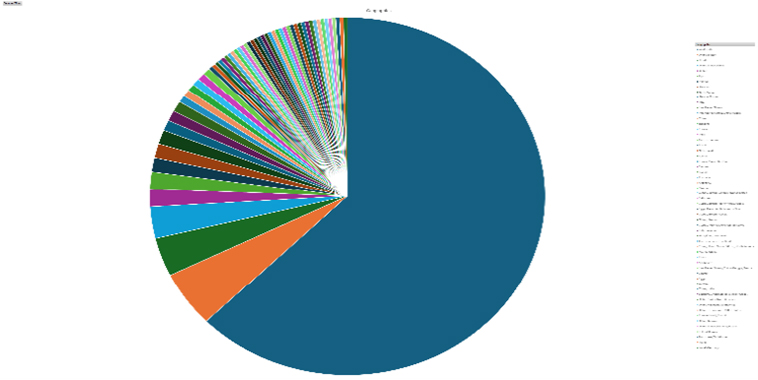
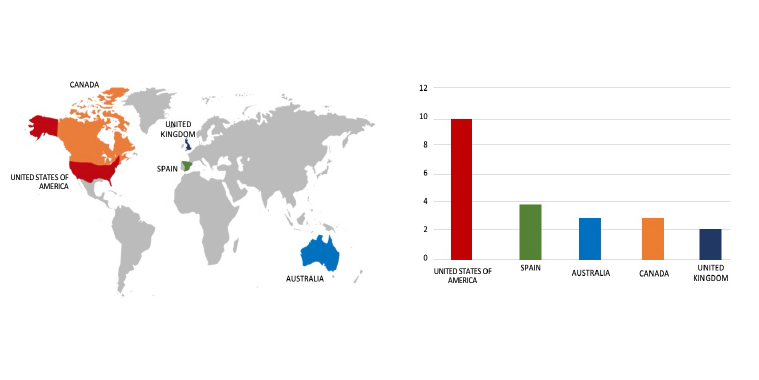
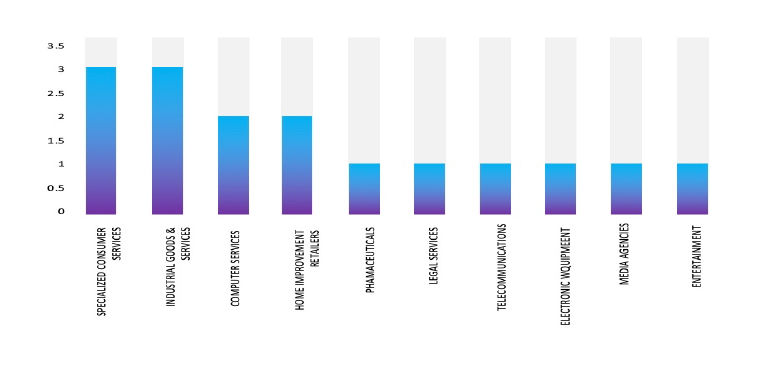
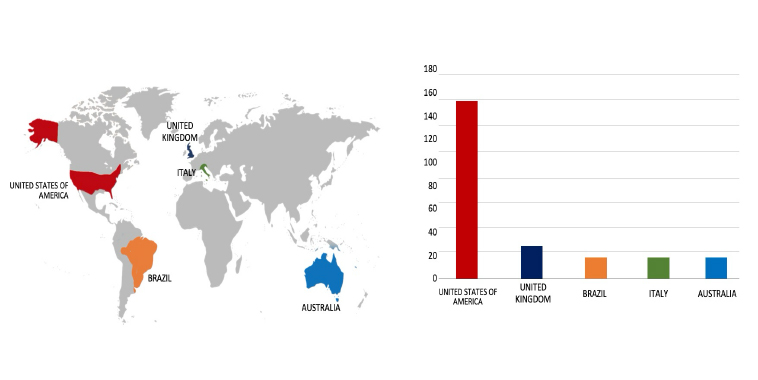
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
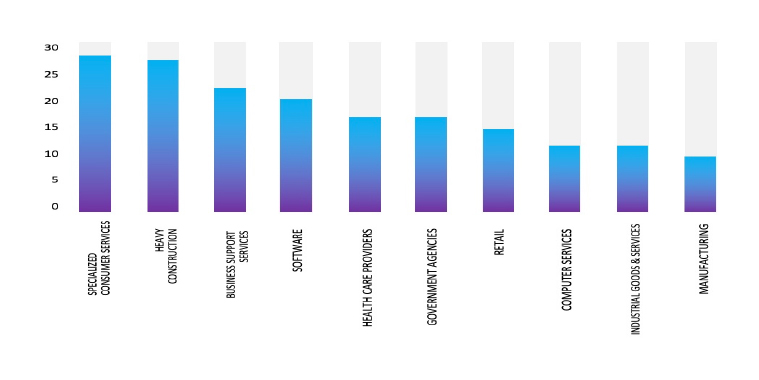
Geography-Wise Graph
Industry-Wise Graph
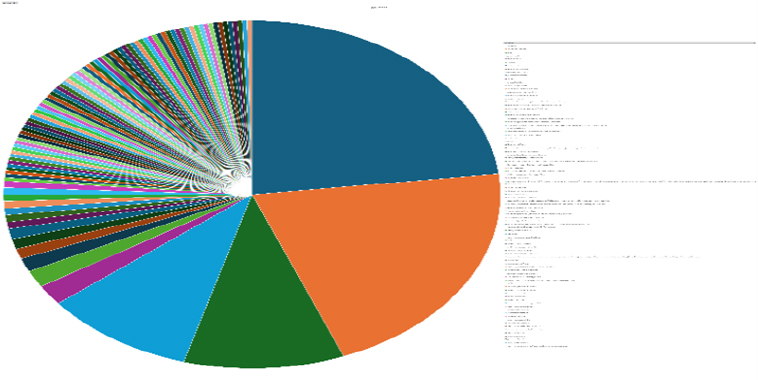
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.
Key Intelligence Signals:
Sophisticated Cyber Espionage Campaign Targets Asian Defense and Research Sectors with Cobalt Strike Implants
Summary:
Researchers have discovered a sophisticated cyber espionage campaign by an unknown threat actor, demonstrating a highly targeted approach toward strategic sectors. The primary targets include electrotechnical researchers, defense industry stakeholders, and individuals in electronic engineering education across Hong Kong, mainland China, and Pakistan, focusing on those handling sensitive, high-value information. The threat actor employs carefully crafted social engineering tactics, embedding relevant lures in malicious RAR archives containing decoy files themed around award nominations, postdoctoral applications, and defense industry events, thereby enticing the specific professional audience.
The infection chain begins with a RAR archive containing a malicious LNK file disguised as a PDF. Upon execution, this LNK file runs a VBScript (O365.vbs), which decodes and renames the Cobalt Strike payload (cache.bak) to mimic legitimate Windows executables like sigverif.exe. This technique enables the actor to establish a persistent, covert presence on the infected machine, supported by a scheduled task for recurring execution while self-deleting to evade detection.
Analysis of the Cobalt Strike beacon configuration shows meticulous planning: the implant communicates over HTTPS on port 443, utilizing the IP address 139[.]155[.]190[.]84 with a host header resembling a Tencent API endpoint. With operational parameters such as sleep and jitter timings, the beacon’s behavior is optimized to blend into normal traffic and minimize detection. Consistent naming patterns, including “ImeBroker.exe,” across campaigns point to an organized infrastructure.
Researchers also uncovered distinct machine IDs embedded within LNK files, which provide clues about the campaign’s regional focus. Specific IDs are found in lures aimed at Pakistan’s defense sector, hinting at targeted tactics and separate configurations for different geographic areas. The breadth of this campaign reveals a well-coordinated, persistent effort by the threat actor, likely aimed at gathering sensitive intelligence across Asia’s defense, research, and academic sectors.
Relevancy & Insights:
A recent cyber espionage campaign by an unknown threat actor leverages socially engineered lures and Cobalt Strike implants to infiltrate Asian defense, research, and academic sectors, targeting high-value information. The actor’s consistent use of themed lures—such as scientific awards and defense industry events—indicates a motive focused on intelligence gathering. This activity aligns with the actor’s past attacks involving industry-specific themes and sophisticated persistence mechanisms, pointing to a well-resourced group. Researchers, defense professionals, and academic institutions in these fields should remain vigilant, as the campaign’s methods and infrastructure suggest a sustained interest in these strategic sectors.
ETLM Assessment:
An unknown threat actor engaging in cyber espionage is targeting primarily Hong Kong and Pakistan across various high-value industries, including defense, electrotechnical engineering, and academia. The actor leverages advanced techniques utilizing Cobalt Strike, deploying malicious VBScript and LNK files within RAR archives to execute payloads in memory while evading detection. Their focus on critical sectors highlights a strategic intent to gather sensitive information, making organizations within these industries particularly vulnerable. As this threat landscape evolves, entities must remain vigilant and enhance their defenses against sophisticated tactics that prioritize stealth and persistence.
Recommendations:
| MITRE ATT&CK Tactics and Techniques | ||
| Tactics | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear-phishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1053 | Scheduled Task/Job |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055.002 | Process Injection: Portable Executable Injection |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Collection | T1213 | Data from Information Repositories |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
Russian Trolls Create Election Chaos in the US by Posing as Reputable Media
Russian state-backed actors are spreading massive amounts of fake news masquerading as information from reliable news sources in the final days of the 2024 US election season. Their goal is to fill the American news landscape with enough nonsense to affect the outcome of the election.
The main goal of the Kremlin’s full-scale propaganda campaign, Operation Overload, is to sway the US election by overloading already thin journalistic resources. There will be fewer journalists left to disprove the nonsense if the few reliable news outlets and journalists that remain in the US are always using their limited investigative resources to find fake news.
In order to make the misinformation appear to be from a reliable US news source, the group also adds branding and logos, making it harder for customers to distinguish between the two. The Russian fake news farm has most recently been spreading false material on Tim Walz, the vice-presidential candidate.
In order to undermine public confidence in the democratic process, incite domestic anxieties in the US about political violence and “civil war,” and take advantage of preexisting social divisions, the operation aims to directly introduce influence content into the mainstream discussion on divisive political issues.
ETLM Assessment:
Operation Overload has already employed this successful strategy. Similar initiatives in France recently helped the Russian state-sponsored outfit refine its fake news tactics. The program, which previously sought to sabotage the 2024 French elections and the Paris Olympics, is now concentrating on the US presidential election. It entails the development of fake news websites, phony fact-checking tools, and artificial intelligence (AI)-generated audio that imitates mainstream media sources.
The endeavour primarily uses automated social media posts to continuously spread false information, in addition to AI-generated material, propaganda saturating media, and fake news that has been manipulated to appear like real reporting. X (formerly Twitter) is where a lot of the misinformation about Operation Overload spreads. X accounts were identified as the source of three distinct fake narratives that the Russian troll farm had been spreading against Walz in recent days.
Operation Overload will persist in spreading three different types of misinformation in the coming days with the goal of influencing the US election: inciting political violence, attacking candidates, and demonizing Ukrainians and the LGBTQIA+ community.
The Sarcoma Ransomware Impacts Suntrust Properties
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the Philippines; Suntrust Properties (www[.]suntrust[.]com[.]ph), was compromised by Sarcoma Ransomware. Suntrust Properties, Inc. (SPI) is a leading real estate company in the Philippines, known for developing affordable residential communities, condominiums, and other properties. It is one of the largest real estate developers in the country. Suntrust focuses on offering homes for middle-income families, balancing affordability with strategic locations. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization. The total size of the compromised data is approximately 1 TB.
The following screenshot was observed published on the dark web:
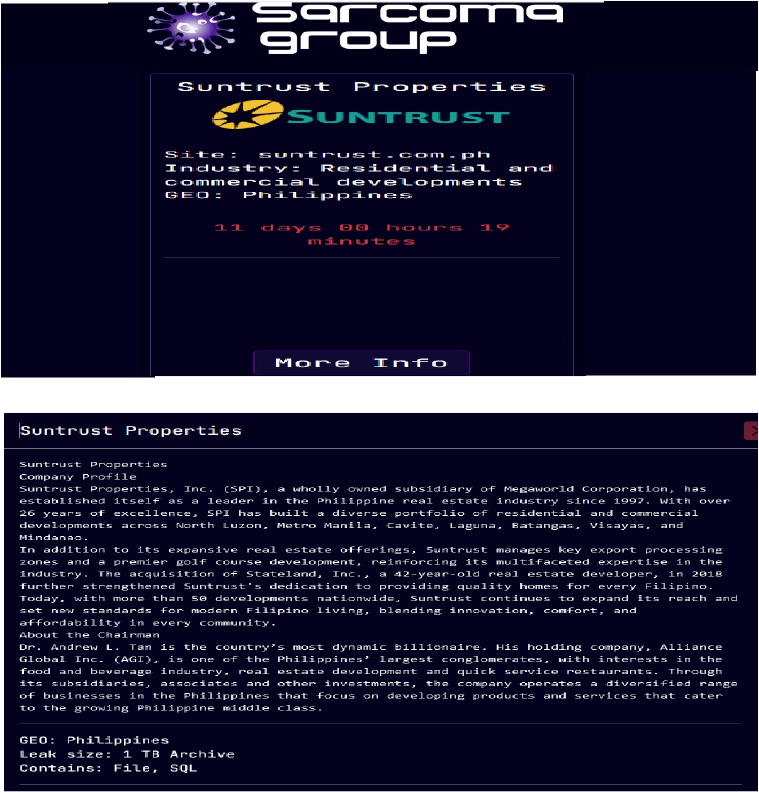
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, Sarcoma ransomware is rapidly becoming a significant threat due to its aggressive tactics and increasing victim count. Organizations must remain vigilant and proactive in their cybersecurity efforts to mitigate risks associated with this evolving threat landscape.
The RansomHub Ransomware Impacts the Yorozu Corporation
Summary:
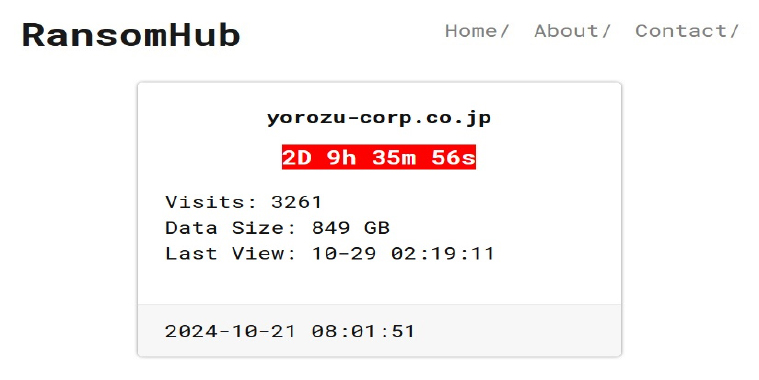
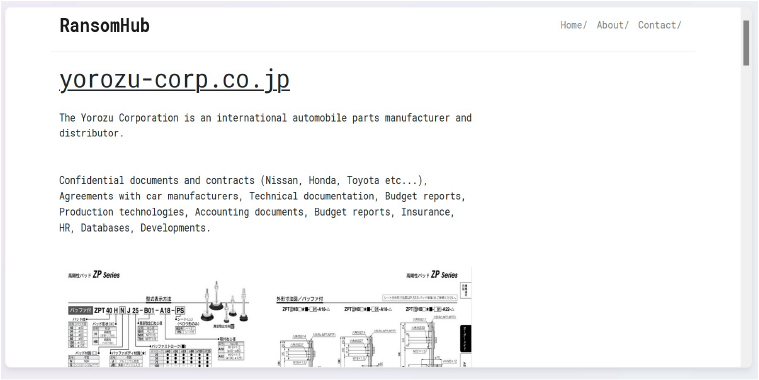
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan; Yorozu Corporation(www[.]yorozu-corp[.]co[.]jp), was compromised by RansomHub Ransomware. Yorozu Corporation is a Japanese company primarily operating in the automotive parts industry. The company specializes in the development, design, production, and sales of automotive parts, including suspension systems. Yorozu’s products serve major automotive manufacturers, such as Nissan, Toyota, Honda, and several global companies like Ford, General Motors, and Mercedes-Benz. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data encompasses a trove of sensitive and confidential records, originating from the organizational database. The total size of the compromised data is approximately 849 GB.
The following screenshot was observed published on the dark web:
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, RansomHub ransomware is expected to intensify its operations across various industries worldwide, with a notable focus on regions in the United States, Europe, and Asia. This prediction is reinforced by the recent attack on Yorozu Corporation, a prominent Automotive company from Japan, highlighting RansomHub’s significant threat presence in the Asia Pacific region.
Vulnerability in Cisco Adaptive Security Virtual Appliance and Secure Firewall Threat Defense Virtual SSL VPN
Summary:
The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Relevancy & Insights:
The vulnerability exists due to a lack of proper memory management for new incoming SSL/TLS connections on the virtual platforms within the VPN and management web servers.
Impact:
A remote attacker can pass specially crafted input to the application and perform a denial of service (DoS) attack.
Affected Products:
https://sec[.]cloudapps[.]cisco[.]com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftdvirtual-dos-MuenGnYR
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
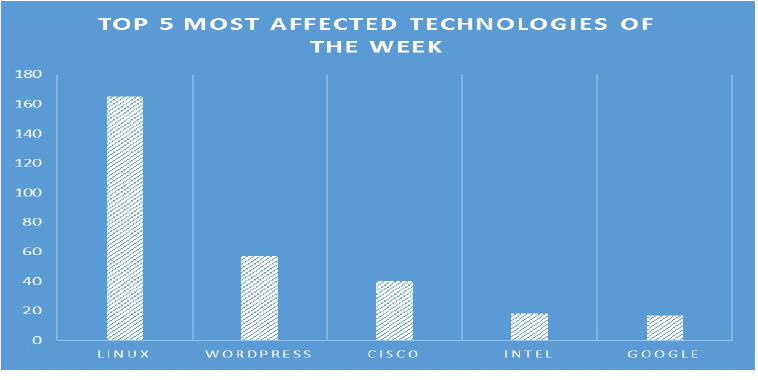
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment:
Vulnerability in Cisco Secure Firewall Threat Defense Virtual can pose significant threats to user privacy and security. This can impact various industries globally, including technology, finance, healthcare, and beyond. Ensuring the security of Cisco Secure Firewall Threat Defense Virtual is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding network firewall operations, including intrusion prevention, URL filtering, and malware defense, across different geographic regions and sectors.
KillSec Ransomware attacked and published the data of the Rudraksha Multispeciality Hospitals
Summary:
Recently, we observed that KillSec Ransomware attacked and published the data of Rudraksha Multispeciality Hospitals (www[.]rudrakshahospitals[.]com) on its dark web website. Rudraksha Multispeciality Hospitals, based in India, offers a wide range of healthcare services focused on providing advanced, compassionate, and affordable treatment. The hospital specializes in neurosurgery, general surgery, orthopedics, critical care, and plastic and reconstructive surgery, among other areas. It also provides comprehensive medical services in cardiology, endocrinology, urology, and pediatric care. Rudraksha Hospitals are equipped with modern surgical facilities and a state-of-the-art critical care unit designed to handle life-threatening conditions with timely and precise interventions. The data leak, following the ransomware attack, encompasses sensitive information, including personally identifiable information (PII), financial data, and confidential business details. This includes names, addresses of businesses, customer addresses, contact numbers, invoice details, amounts due, terms of payment, late charges, customer numbers, invoice numbers, and sales representative IDs.
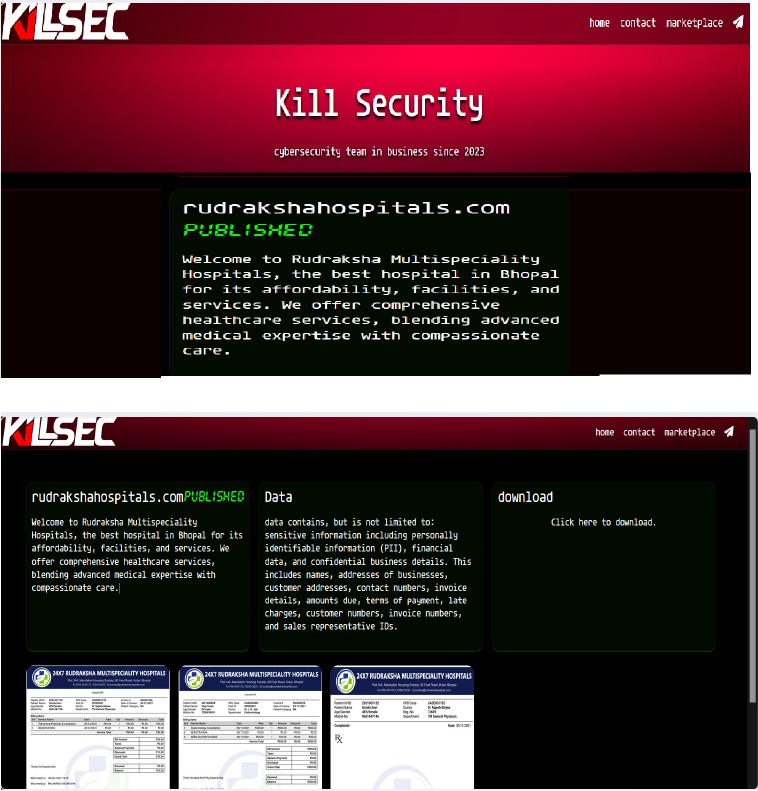
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
The emergence of KillSec’s Ransomware-as-a-Service (RaaS) platform represents a concerning development in the cybercrime landscape. By lowering the technical barrier to entry, this RaaS model allows less skilled individuals to engage in sophisticated ransomware attacks, potentially leading to an increase in such incidents globally.
According to CYFIRMA’s assessment, the KillSec ransomware group is expected to continue targeting a wide range of industries worldwide. Their advanced tactics, such as exploiting website vulnerabilities and conducting credential theft, make them a significant threat to organizations with inadequate security measures in place.
PT PETROLAB SERVICES Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed a potential data leak related to PT Petrolab Services(www[.]petrolab[.]co[.]id) in an underground forum.PT Petrolab Services is an Indonesian independent laboratory offering specialized testing, analysis, and consulting services across various industries. Petrolab serves over 2,500 clients across Southeast Asia, particularly within sectors like oil, mining, manufacturing, and energy. The exposed data includes details such as the Customer ID, Customer Name, Customer Abbreviation, Customer Administrative Address, Email, and other sensitive and confidential information. The data breach has been attributed to a threat actor identified as “Zenox8x”.
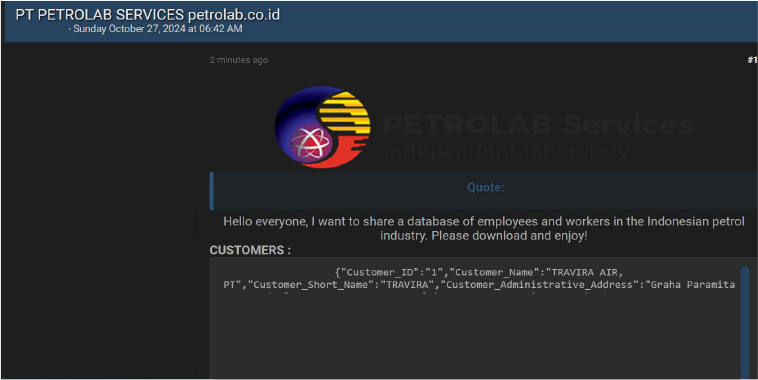
Source: Underground Forums
United News Data Advertised on a Leak Site
Summary:
In a recent post on a dark web forum, a threat actor claims to have breached the database of United News Network, a Philippine news and media company. The alleged database reportedly contains usernames and email addresses.
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
Threat actor “Zenox8x” is a relatively new threat actor that has emerged in the cybersecurity landscape, utilizing sophisticated tactics to execute attacks. Organizations are advised to enhance their cybersecurity measures, including regular updates, employee training, and incident response planning, to mitigate risks associated with such evolving threats.
Recommendations: Enhance the cybersecurity posture by
A dark web actor claims to have leaked data from 1StopBedrooms.com, an online furniture retailer in the USA. The breach reportedly exposes details from approximately 1 million orders, including customer addresses, email addresses, and phone numbers. The compromised data raises serious concerns about customer privacy and potential misuse for fraud or phishing attacks.
The breach highlights vulnerabilities in e-commerce platforms, emphasizing the need for robust data protection strategies. Affected customers are advised to be cautious of suspicious communications and monitor their accounts for any unauthorized activity. 1StopBedrooms.com has not yet provided an official response to the incident.
Source: Underground forums
The CYFIRMA Research team observed a potential data leak related to Elife Limo(ww[.]elifelimo[.]com) in an underground forum. Elife Limo is a global private transportation service offering airport transfers, limousine rentals, bus charters, and other specialized travel services in over 150 countries. Their offerings include various vehicle types like sedans, SUVs, minibusses, and specially equipped vans for wheelchair accessibility and pet transport. Known for their punctuality and professional chauffeurs, Elife also provides added services like flight tracking, free waiting periods at airports, and flexible cancellations. The Compromised User Data contains Full names, Airport check-ins, Email Addresses, Phone numbers, Flight numbers, Flight Arrival times & drop-off locations. The data breach has been attributed to a threat actor identified as “IntelBroker”.

Source: Underground forums
ETLM Assessment:
IntelBroker acts as an “intelligence broker,” breaching organizations and selling their compromised data on underground forums. They have claimed responsibility for over 80 data leaks, affecting more than 400 organizations. Based on the available information, CYFIRMA’s assessment indicates that IntelBroker represents a significant threat in the cybercrime landscape due to its aggressive tactics and high-profile targets. Organizations must remain vigilant and proactive in their cybersecurity measures to protect against such evolving threats.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Remote Access Trojan (RAT)
Objective: Data Exfiltration, Stealing Sensitive Information, Remote Access, Espionage
Target Technology: Windows OS
Active Malware of the Week
This week “PySilon” is trending.
PySilon
Recently, researchers identified PySilon RAT, an open-source remote access tool initially posted on GitHub in December 2022. PySilon RAT exemplifies how threat actors increasingly turn to open-source malware for its flexibility, robust capabilities, and ease of deployment. Written in Python, this tool is readily available on GitHub and supported by communities across Telegram and other forums, offering threat actors a powerful, customizable framework for malicious activities. The emergence of PySilon highlights the concerning trend of sophisticated, adaptable open-source tools making advanced malware campaigns more accessible than ever.
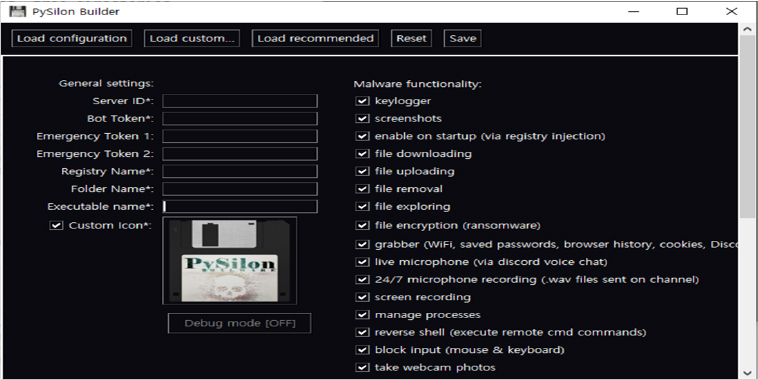
Fig: PySilon RAT malware builder program
The PySilon RAT builder allows users to customize configurations by specifying details like the Server ID, bot token for Discord bot development, and installation path in the system registry. Once these custom details are added to the pre-written Python code, the builder compiles it into an executable (.exe) file using PyInstaller.
Attack Method
When the generated executable file is executed on a user’s PC, it creates a new channel on a server controlled by the threat actor. Initially, the infected system’s IP address and other relevant information are sent to the attacker through chat. Each infected PC has its own dedicated channel, enabling the threat actor to manage and control each compromised device individually.
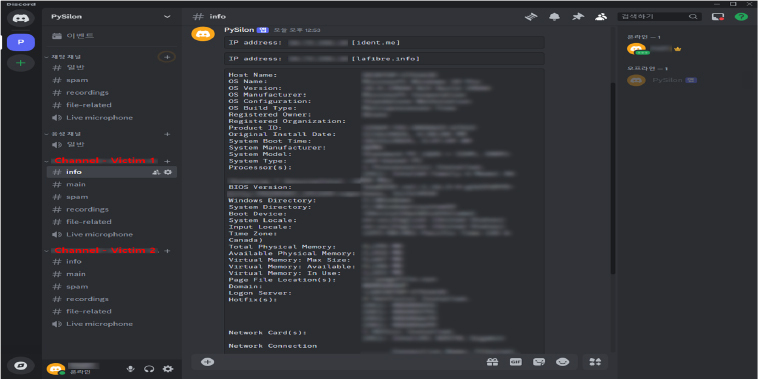
Fig: System information sent by the initially installed bot to the threat actor
When executed, the RAT malware replicates itself in the user folder and modifies the system registry’s RUN key to ensure persistence, launching automatically each time the PC starts. The threat actor can further customize the folder name used for replication. The malware also includes anti-virtual machine (VM) logic, detecting VM environments through specific file or process names, and will not run if a virtual environment is detected. The following commands are supported by PySilon.

The threat actor can then use the commands in the newly created channel’s chat to execute further malicious actions. Listed below are the primary actions the malware enables from the threat actor’s perspective.
Screen recording and audio recording
The malware enables screen and audio recording on the infected PC through Python modules like pyautogui, numpy, imageio, and sounddevice.
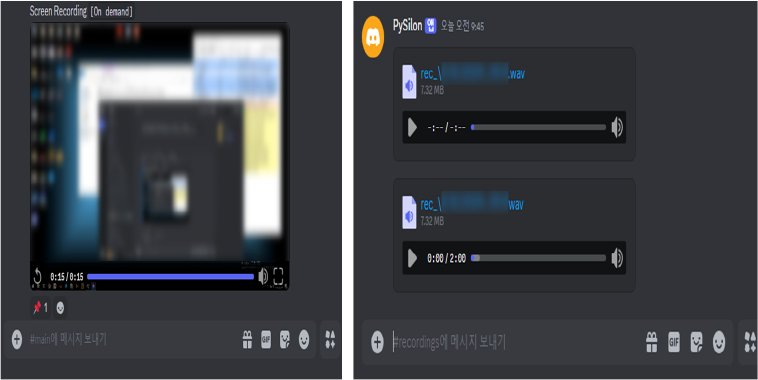
Fig: Screen and audio recording files sent to the threat actor
Collecting information
The “Grab” command in the RAT malware allows the threat actor to collect extensive information from the infected system, including the user’s personal and payment details, browser history, cookies, and various passwords. The information gathered includes Discord tokens, Nitro status, MFA details, email, phone number, passwords, cookie data, and browsing history.
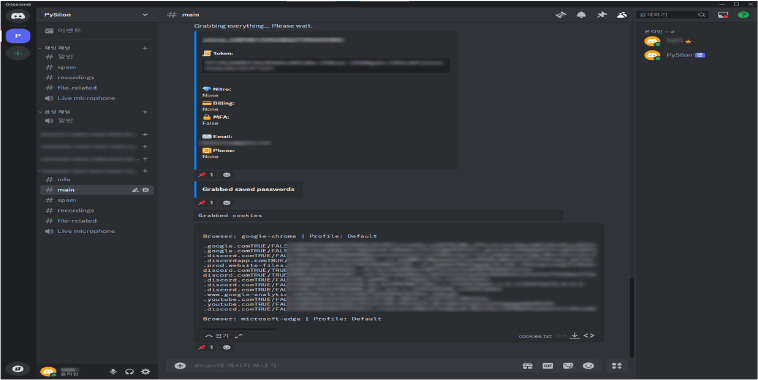
Fig: Collecting information
Keylogging
When the user presses “Enter,” the input content is sent to the threat actor’s server.
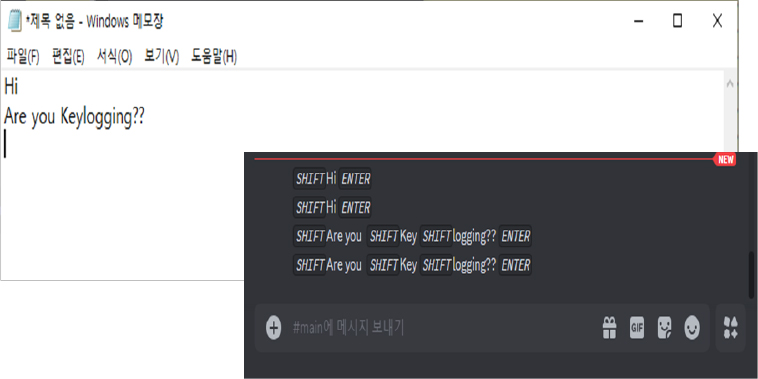
Fig: Keylogging
Folder encryption and additional malicious actions
The malware can encrypt files on the infected PC using the Fernet encryption algorithm, with the decryption key stored in the user folder. Encrypted files are marked with a .pysilon extension, and no ransom note is generated. Beyond encryption, the malware can modify the hosts file to control website access through a blacklist/whitelist, upload or download files, execute commands, manage processes, and even trigger a blue screen of death (BSOD) using Windows-native functions.
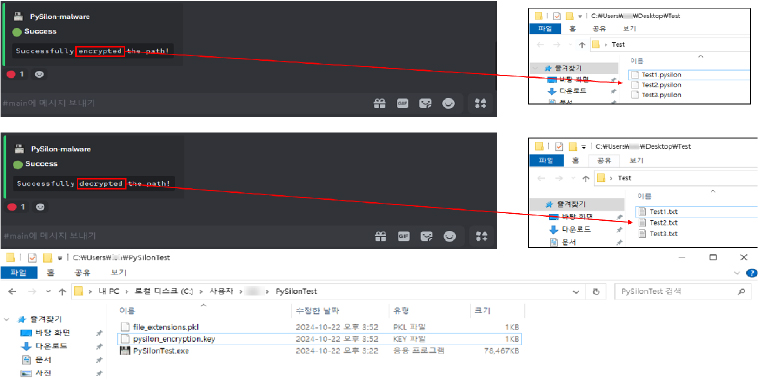
Fig: Encryption/decryption commands and Key file created in user folder
INSIGHTS
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that the rise of PySilon malware signals a future of heightened cybersecurity risks as threat actors increasingly leverage open-source tools for targeted attacks on organizations and employees. PySilon’s data extraction capabilities suggest that employee accounts will become key targets, with stolen credentials potentially granting attackers deeper access to corporate networks. This points to a shift toward stealthy, customized attacks, where malware adapts to exploit specific systems and user behaviors. PySilon’s persistent, covert nature could drive a surge in undetected breaches, intellectual property theft, and network disruptions, challenging traditional security measures. Additionally, as attackers extend their reach to employees’ personal devices, especially those used for remote work, organizations may need to adopt stronger, cross-device protections, while employees will be urged to prioritize data privacy across all platforms.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
Introduction
CYFIRMA Research and Advisory Team has found Destroy Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Destroy Ransomware.
Researchers recently discovered the Destroy ransomware, which is part of the “MedusaLocker” ransomware family.
Ransomware encrypts files and appends the “.destry30” extension to their filenames. The number in the extension may vary depending on the ransomware variant. Once the encryption process is complete, ransomware drops a ransom note titled “How_to_back_files.html.”
By the ransom note, this ransomware variant clearly targets companies rather than individuals.
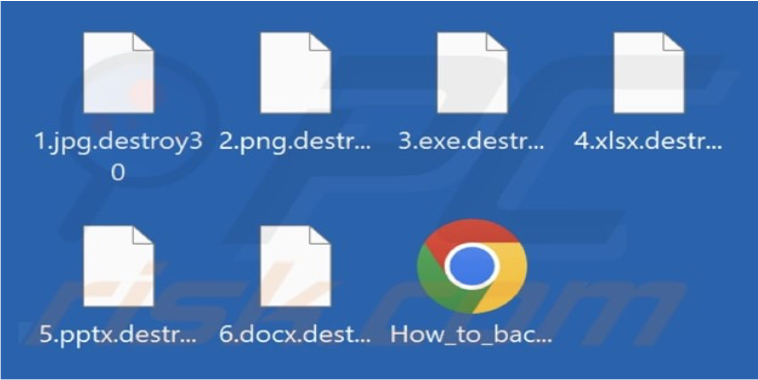
Screenshot of files encrypted by this ransomware (Source: SurfaceWeb)
The ransom note informs the victim that their company network has been compromised, resulting in the encryption of important files and the theft of confidential or personal data. The attackers demand a ransom in exchange for decryption.
The note also cautions against attempting to modify the encrypted files or using third-party decryption tools, as this could lead to permanent data loss. As a gesture, the attackers offer to decrypt up to three files for free as proof. However, if the ransom is not paid, they threaten to leak or sell the stolen data.
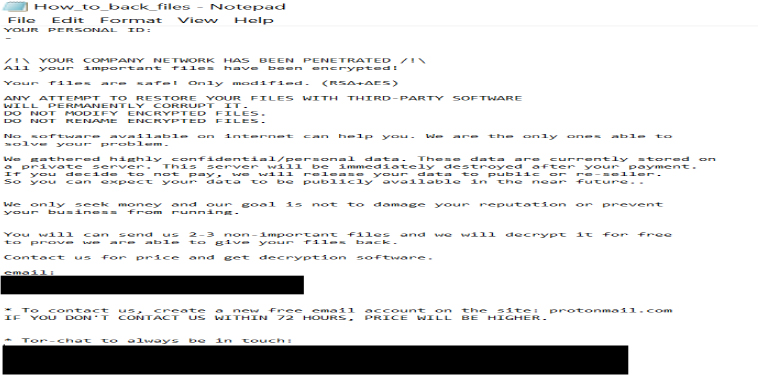
Appearance of Destroy ransomware’s ransom note “How_to_back_files.html” (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0001: Initial Access | T1091: Replication Through Removable Media |
| 2 | TA0002: Execution | T1047: Windows Management Instrumentation |
| T1059: Command and Scripting Interpreter | ||
| T1129: Shared Modules | ||
| 3 | TA0003: Persistence | T1543.003: Create or Modify System Process: Windows Service |
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 4 | TA0004: Privilege Escalation | T1134.004: Access Token Manipulation: Parent PID Spoofing |
| T1543.003: Create or Modify System Process: Windows Service | ||
| T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 5 | TA0005: Defense Evasion | T1027.002: Obfuscated Files or Information: Software Packing |
| T1027.005: Obfuscated Files or Information: Indicator Removal from Tools | ||
| T1036: Masquerading | ||
| T1070.004: Indicator Removal: File Deletion | ||
| T1112: Modify Registry | ||
| T1134.004: Access Token Manipulation: Parent PID Spoofing | ||
| T1140: Deobfuscate/Decode Files or Information | ||
| T1202: Indirect Command Execution | ||
| T1222: File and Directory Permissions Modification | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1548: Abuse Elevation Control Mechanism | ||
| T1562.001: Impair Defenses: Disable or Modify Tools | ||
| T1574.002: Hijack Execution Flow: DLL Side-Loading | ||
| 6 | TA0006: Credential Access | T1056.001: Input Capture: Keylogging |
| T1003: OS Credential Dumping | ||
| 7 | TA0007: Discovery | T1012: Query Registry |
| T1057: Process Discovery | ||
| T1082: System Information Discovery | ||
| T1083: File and Directory Discovery | ||
| T1120: Peripheral Device Discovery | ||
| T1497: Virtualization/Sandbox Evasion | ||
| T1614: System Location Discovery | ||
| 8 | TA0008: Lateral Movement | T1091: Replication Through Removable Media |
| 9 | TA0009: Collection | T1005: Data from Local System |
| T1056.001: Input Capture: Keylogging | ||
| T1074: Data Staged | ||
| 10 | TA0011: Command and Control | T1071: Application Layer Protocol |
| 11 | TA0040: Impact | T1486: Data Encrypted for Impact |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s analysis of available data indicates that MedusaLocker ransomware has been actively targeting a wide range of sectors, including Manufacturing, Healthcare, Finance, IT services, and much more, since 2019. Projections suggest that destroy, a more advanced variant of MedusaLocker, will likely use enhanced evasion techniques to broaden its impact, targeting both individuals and businesses. It is expected to continue affecting major industries worldwide. Therefore, maintaining vigilance and implementing robust cybersecurity measures are crucial to mitigating these evolving threats effectively.
SIGMA Rule:
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490
logsource:
category: process_creation
product: windows
detection:
selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’
selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’
selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’
selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet
selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’
selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’
CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*)
fields:
– CommandLine
– ParentCommandLine
falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand)
level: high
(Source: SurfaceWeb)
Indicators of Compromise
Kindly refer to the IOCs section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION