



CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – which could be relevant to your organization.
Type: Ransomware.
Target Technologies: MS Windows.
CYFIRMA Research and Advisory Team has found ransomware known as Vx-underground while monitoring various underground forums as part of our Threat Discovery Process.
Researchers have found a ransomware strain called Vx-underground, belonging to the Phobos ransomware family. It’s important to note that this malicious software is distinct from vx-underground, an online repository for malware-related content, such as source code, samples, and research papers.
Phobos emerged in 2019, is believed to be a ransomware-as-a-service stemming from the Crysis ransomware family. It achieved widespread distribution through numerous affiliated threat actors in 2023.
During the file encryption process, the malware appends the “.id[[unique_id].[staff@vx- underground.org].VXUG” string to the filenames. It’s important to note that the email address “[email protected]” is legitimate, and the final extension “VXUG” stands for VX-Underground.
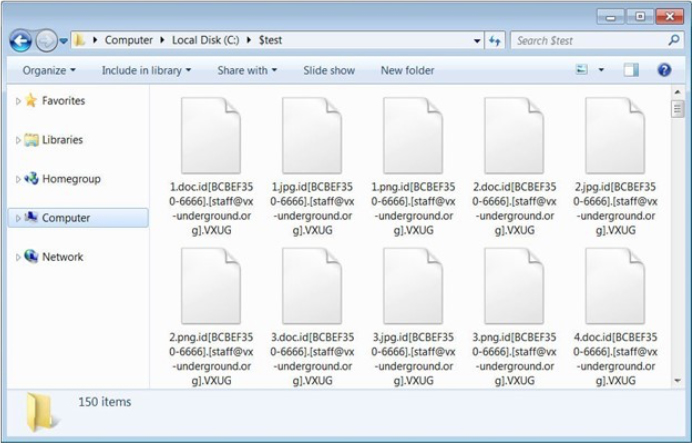
Screenshot of the files encrypted by Vx-underground ransomware (Source: Surface web)
Upon completion, ransomware generates two ransom notes on the Windows Desktop and other locations. The initial note, titled ‘Buy Black Mass Volume I.txt,’ playfully references VX by stating that the decryption password isn’t the common “infected,” which is typically used on all VX malware archives.
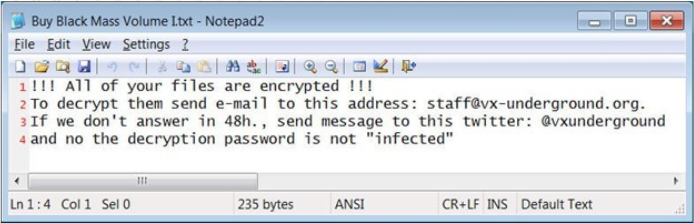
Text ransom note of Vx-underground ransomware (Source: Surface web)
The second note is an HTA file called ‘Buy Black Mass Volume II.hta.’ It’s a typical Phobos ransom note but customized to incorporate the VX-Underground logo, name, and contact details. The term “Black Mass” refers to books authored by VX-Underground.
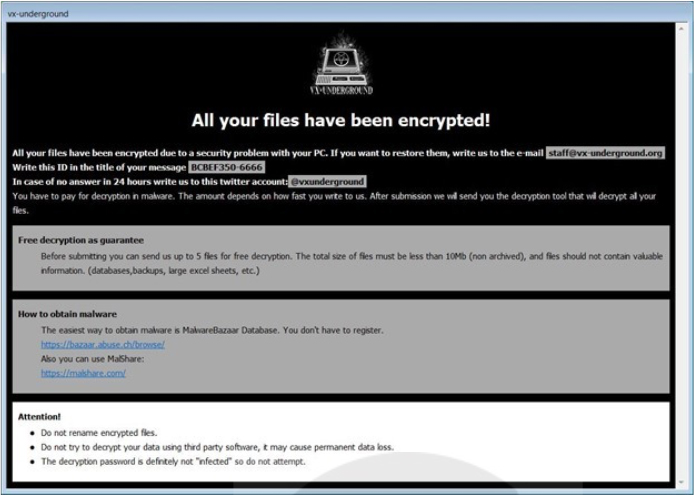
Ransomnote by Vx-underground ransomware (Source: Surface web)
The Vx-underground ransomware encrypts both local and network-shared files, avoiding critical system files to prevent system disruption. It excludes files already encrypted by other ransomware, employs a process closure strategy to ensure smooth encryption, and deletes Volume Shadow Copies. The ransomware disables the Firewall. The ransomware ensures persistence by copying itself to %LOCALAPPDATA% and registering with specific Run keys, initiating with every system restart. Additionally, it can extract geolocation data to assess the target’s potential value based on economic and geopolitical factors.
| Sr. No | Tactics | Techniques/Sub-Techniques |
| 1 | TA0002: Execution | T1047: Windows Management Instrumentation
T1053: Scheduled Task/Job T1106: Native API T1129: Shared Modules |
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job
T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder T1574.010: Hijack Execution Flow: Services File Permissions Weakness
|
| 3 |
TA0004: Privilege Escalation |
T1053: Scheduled Task/Job
T1055: Process Injection T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder T1574.010: Hijack Execution Flow: Services File Permissions Weakness |
| 4 | TA0005: Defense Evasion | T1036: Masquerading
T1055: Process Injection T1202: Indirect Command Execution T1497: Virtualization/Sandbox Evasion T1562.001: Impair Defenses: Disable or Modify Tools T1564.003: Hide Artifacts: Hidden Window T1574.010: Hijack Execution Flow: Services File Permissions Weakness |
| 5 | TA0006: Credential Access | T1003: OS Credential Dumping
T1552.002: Unsecured Credentials: Credentials in Registry |
| 6 | TA0007: Discovery | T1018: Remote System Discovery
T1057: Process Discovery T1082: System Information Discovery T1083: File and Directory Discovery T1497: Virtualization/Sandbox Evasion T1518.001: Software Discovery: Security Software Discovery |
| 7 | TA0009: Collection | T1005: Data from Local System
T1560: Archive Collected Data |
| 8. | TA0011: Command and Control | T1071.001: Application Layer Protocol: Web
Protocols T1095: Non-Application Layer Protocol T1105: Ingress Tool Transfer T1571: Non-Standard Port T1573: Encrypted Channel |
| 9 | TA0040: Impact | T1486: Data Encrypted for Impact |
CYFIRMA’s assessment, based on available information about Vx Underground, suggests that as ransomware threats continue to evolve, there is an anticipated increase in focus on sophisticated tactics. This includes leveraging detection evasion mechanisms, persistent strategies, and diverse techniques for reconnaissance and lateral movement. Further integration of anti-analysis capabilities to thwart debugging environments is expected. The use of Windows Management Instrumentation (WMI) for malicious purposes may rise, presenting challenges for detection. Organizations should prioritize robust cybersecurity measures, including behavioral analysis, to counter these advanced threats in the evolving landscape.
Kindly refer to the IOCs section to exercise controls on your security systems.
title: Suspicious File Creation Activity from Fake Recycle.Bin Folder tags:
– attack.persistence
– attack.defense_evasion logsource:
category: file_event product: windows
detection: selection:
– Image|contains:
# e.g. C:\$RECYCLER.BIN
– ‘RECYCLERS.BIN\’
– ‘RECYCLER.BIN\’
– ‘RECYCLE.BIN\’
– TargetFilename|contains:
# e.g. C:\$RECYCLER.BIN
– ‘RECYCLERS.BIN\’
– ‘RECYCLER.BIN\’
– ‘RECYCLE.BIN\’
condition: selection falsepositives:
– Unknown level: high
(Source: Surface web)
Type: Remote Access Trojan (RAT)
Objective: Remote Access, Espionage, Malware Implant Target Sectors: Education, Government and Business Services
Target Technology: Windows OS
This week “NetSupport RAT” is trending.
Threat actors have been misusing legitimate software, specifically NetSupport Manager, as a Remote Access Trojan (RAT) for unauthorized access and attacks. In recent weeks, researchers have identified over 15 new infections associated with NetSupport RAT. The affected sectors include Education, Government, and Business Services, indicating a concerning rise in malicious use within these industries.
NetSupport Manager, originally designed for remote technical support, has been exploited by threat actors as a Remote Access Trojan (RAT) in recent years. The RAT gained prominence in 2020 through a widespread COVID-19 phishing campaign. Its delivery methods include fraudulent updates, drive-by downloads, malware loaders like GhostPulse, and various phishing tactics. Due to its legitimate origins and broad availability, NetSupport Manager is used by multiple threat actors, including TA569 known for SocGholish malware. Its accessibility makes it attractive to a range of attackers, from novices to sophisticated adversaries. Older versions of NetSupport RAT employed .BAT and .VBS files, often as decoys, with only one responsible for executing the RAT and ensuring persistence.
Recent NetSupport RAT attacks involve the trojan being downloaded onto victims’
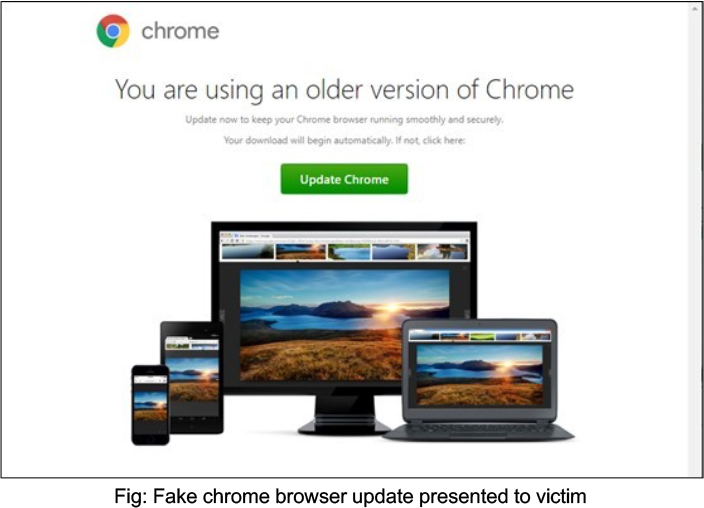
In this infection scenario, victims are lured into downloading a fake browser update when visiting compromised websites. These sites host a PHP script that convincingly presents a fake update. Clicking on the download link triggers the download of an additional JavaScript payload onto the victim’s endpoint, facilitating the infection. The attack unfolds in distinct stages:
1. Initial Compromise
2. Execution and Payload Handling
3. File Extraction and NetSupport Installation
4. Malicious Capabilities
5. Persistence
Researchers identified a suspicious PowerShell.exe process with a command line linked to a .JS file named “update_browser_10.6336.js,” confirming it as the NetSupport RAT. Upon examining the command line, a URL was discovered, specifically hxxps[:]//gamefllix[.]com/111.php?9279, which was used to download additional payloads through the DownloadString function in this particular attack.
When a compromised endpoint connects to the affected URL, the payload is downloaded. The obtained payload is the GET response of the obfuscated script from the compromised URL (gamefllix[.]com/111[.]php). The script seems to be base64 encoded, prompting researchers to attempt decoding using CyberChef; however, the output remains unreadable. Notably, the PK header at the file’s start indicates a ZIP archive. Some file names, such as CacheMD5.dat, CacheURL.dat, and client32.exe, along with an additional URL, emerge from the CyberChef output.
Researchers then used PowerShell in a secure environment to reconstruct the ZIP archive from the base64 encoded contents of gamefllix[.]com. The reconstructed files, including Client32.ini with GatewayAddress details, revealed that client32.exe established a network connection on port 443 using RADIUSSecret for authentication. NetSupport licensing information extracted from NSM.LIC includes the name HANEYMANEY under the licensee field, associated with threat actor TA569, known for delivering payloads via fake browser updates. While a direct correlation may be uncertain, the observed behavior raises suspicions of a compromised or leaked NetSupport Manager license.
Kindly refer to the IOCs Section to exercise controls on your security systems.
Key Intelligence Signals:
Unveiling WildCard: Advanced Threat Actor Targeting Critical Sectors in Israel
Summary:
Recent investigation into the WildCard APT group reveals a sophisticated threat landscape, initially identified through the SysJoker malware targeting Israel’s educational sector in 2021. The group’s expansion into creating intricate malware variants, such as the RustDown written in Rust, indicates a strategic focus on critical sectors within Israel. Despite gaining insights into WildCard’s tactics, their precise identity remains elusive, necessitating further in-depth analysis and collaboration within the information security community.
In October 2023, researchers uncovered RustDown, a new malware attributed to the WildCard APT group. Disguised as a PHP framework component, the 32-bit Windows executable utilizes obfuscation techniques, including encryption and dynamic PowerShell commands, for persistence and evasion. The PDB file path hints at the name “RustDown-Belal,” potentially connecting to a developer named Belal. RustDown exhibits similarities with WildCard’s earlier SysJoker variants, indicating a consistent threat actor. The malware’s complex obfuscation methods involve Base64 decoding and XOR key application. In the communication process with the command-and- control (C2), the WildCard’s RustDown malware employs a dead drop resolver, using a specific OneDrive link. The decoded C2 URL reveals an IP address. RustDown then communicates with the C2 via HTTP, using a format similar to SysJoker. The malware, like its predecessor, decodes the C2 and initiates an initial handshake by sending user information to /api/attach.
Relevancy & Insights:
Amid the Israeli-Hamas conflict, WildCard emerges as a non-traditional threat actor, The SysJoker malware, initially observed in 2021 and publicly disclosed in 2022, lacked attribution to a known actor. However, evidence suggests its involvement in the Israeli-Hamas conflict and a link to the 2016-2017 Electric Powder Operation against Israel Electric Company. The malware’s evolution, shifting from C++ to Rust, indicates a significant rewrite, potentially laying the groundwork for future modifications and enhancements. This campaign was attributed to Gaza Cybergang, a threat actor that is believed to be linked to the Palestinian organization Hamas.
ETLM Assessment:
The APT group, known for serving Hamas-affiliated interests, consistently targets Israeli organizations. However, it seems their activities are not restricted to this focus, as they are looking for possible expansion in their footprints to other geographies. The observed correlation suggests a more extensive strategic agenda that may have repercussions beyond a singular region, potentially influencing the global cyber landscape. Moreover, given the Tactics, techniques, and procedures (TTPs) employed by the group, the prospect of their expansion into new territories is a cause for concern. This underscores the critical need for heightened vigilance and proactive cybersecurity measures on a global scale to anticipate and effectively mitigate potential cyber threats originating from the operations of this group.
Recommendations:
Indicators of Compromise
Russian hackers activity puts European power utilities on alert
A recent report on cyber defense of Europe warns of an increased operational tempo of Russian hackers currently underway against critical infrastructure in NATO countries in an echo of similar concern published earlier by CYFIRMA analysts. According to the report, Russia mainly attempts to steal data, paralyse systems critical to the functioning of the state and society, or impersonate state institutions, among other things, in order to sow disinformation or gain access to data. The activity was illustrated by recent activity by the GRU’s (Russian military intelligence) Sandworm APT in response to which European electrical utility executives and government ministers have called for increased vigilance and security against the prospect of Russian cyberattacks against the continent’s power grid. The Energy Ministry of Poland stated it has observed thousands of attacks and probes against the Polish energy grid taking place live coming out of Russia and non-democratic countries allied to Russia further East. According to the statement of the ministry, this anti-Western bloc has created special teams of people working on attacking the democratic states of the European Union via the fifth domain to cause havoc and political discontent. Cyber threats and cyberattacks in the energy sector in the European Union remain the top concern according to the statement.
ETLM Assessment:
The logistics industry and other critical infrastructure like ports, commodity processing hubs, energy infrastructure or communications confront substantial risks from advanced threat actors. Data we have recently published on the logistics industry reveals a consistent pattern of attacks, with a clear emphasis on developed economies and major global logistics hubs. Although true that the detection of APT campaigns has declined, a correlation between the current geopolitical landscape and the most targeted countries remains evident. Moreover, Russia seems to be increasingly employing privateering actors, motivated by financial gains to put distance between Moscow and the potential political fallout. Such a trend is expected to continue as privateers are offered ever more leniency: in the eyes of the Kremlin, the more global instability they help to create, the more attention is deflected from its persecution of Ukraine, with fewer resources available to oppose it.
Iranian hacktivists claim an attack on a U.S. water utilities
A local Municipal Water Authority in Pennsylvania has recently made public that the Iranian hacktivist group known as Cyber Av3ngers had taken control of one of the local water utility’s booster stations. The attack, which affected a station that monitors and regulates pressure for several small towns in the state. The attack was detected early and according to authorities neither the safety nor the availability of the townships’ water was affected with the utility operator switching to manual control. The attackers displayed a message on the station’s monitors expressing their political purpose in broken english: “You have been hacked Down with Israel Every equipment ‘made in Israel’ is Cyber Aveng3rs legal target” (sic). The utility uses a control system provided by Unitronics; an Israeli company.
The same hacktivist collective claimed attacks on utilities before, but those utilities have been located directly in Israel – the attack inside the United States indicates an expansion of the group’s activities.
ETLM Assessment:
As we have warned in our assessments in previous weeks, we are likely to see a spike in the activity of Iranian APTs attacking Israel and other countries that support Israel. These attacks are likely just the beginning with many more to be revealed in due time. So far Israel seems to have been largely successful in blunting state-directed attacks since it employs a proactive cyber defensive approach adopted by the Israeli National Cyber Directorate (INCD), as well as the mobilization of the country’s cyber security ecosystem due to the high-tech nature of the Israeli economy. However, the same cannot be said of every country supporting Israel and the risk of potential spill out is imminent.
The conflict in Gaza has revealed the complex and contradictory forces that shape Iran’s behavior and interests in the Middle East, which are driven by both ideology and pragmatism. Iran’s proxies in the region, namely Lebanese Hezbollah, Iraqi Popular Mobilization Forces and Yemeni Houthis have all joined the struggle and started a low intensity war against Israel and the U.S., mostly by way of rocket and drone attacks.
Hezbollah alone has lost over 50 fighters but the recent speech by its leader Hassan Nasrallah and Iranian supreme leader Ali Khamenei suggest that these attacks are likely meant to show Iran’s strength and deterrence capabilities to Israel and the United States, but also that Iran and its proxies are walking a thin line trying to avoid a direct clash that could harm Iran’s interests and security. Iranian officials have been walking a tightrope between their ideological commitment to the Palestinian cause and their pragmatic calculations of regional interests and risks. Their statements expose the dilemmas and difficulties that Iran confronts in dealing with its friends and foes. But they also reflect their domestic concerns and calculations. This however does not apply to the fifth domain, where the risk of high scale physical retaliation seems low. Israel’s National Cyber Directorate confirms this observation and states that the prospect of an intensified Iranian cyber campaign is deeply worrying, since Iran “knows that they can act there [in cyberspace] more freely than in physical space”.
Kenso is Impacted by the LockBit 3.0 Ransomware
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Malaysia, (www[.]kenso[.]com[.]my), was compromised by LockBit 3.0 Ransomware. Kenso is engaged in manufacturing and distributing agrochemicals, fertilisers, and speciality hybrid vegetable seeds. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:
Source: Dark Web
Relevancy & Insights:
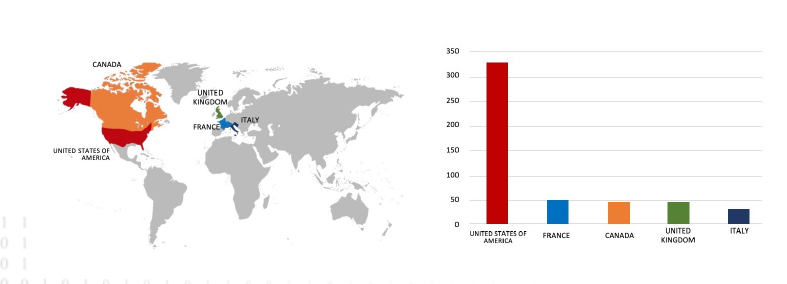
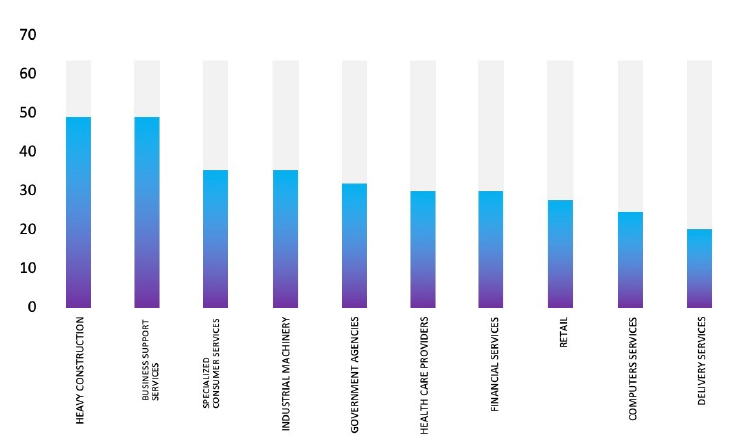
ETLM Assessment:
CYFIRMA assesses that LockBit 3.0 Ransomware will continue to pose a global threat to companies worldwide. We notice that the LockBit 3.0 Ransomware is increasingly utilizing vulnerabilities and exploits within the product to gain initial access, allowing it to move laterally within organizational networks. The recent targeting of Kenso; a manufacturing company, based in Malaysia highlights the global risk posed. The US is their preferred target geography; however, they clearly do not limit their geographical reach.
Vulnerability in Nextcloud Server
Summary:
The vulnerability allows a remote attacker to gain unauthorized access to otherwise restricted functionality.
Relevancy & Insights:
The vulnerability exists due to improper access restrictions.
Impact:
A remote user can update any personal or global external storage and make them inaccessible for everyone else as well.
Affected Products : https[:]//github[.]com/nextcloud/security- advisories/security/advisories/GHSA-f962-hw26-g267
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various products due to a range of vulnerabilities. The following are the top 5 most affected products.
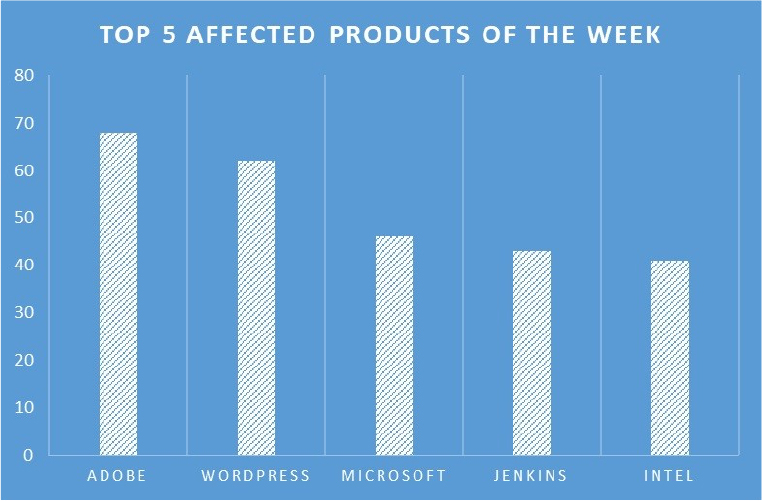
Anonymous Sudan Launches ‘Cyber Monday Sale’ for Skynet Godzilla DDoS Botnet
Summary:
Anonymous Sudan; a threat actor, is running a “Cyber Monday Sales Offer” for its Skynet Godzilla DDoS botnet. Speculations suggest that health claims about the group’s founder and financial difficulties may be a marketing ploy to boost sales. The dark web post advertises Skynet as a DDoS service used in their attacks, emphasizing its potency. Unusually, the group offers this tool as a service, contrary to typical cybercriminal behavior. The post hints at merging their tool with an unspecified entity, creating a more powerful combination, though the advantages remain unclear. The pricing details indicate that access to Skynet DDoS is offered at $100 for a day, $600 for a week, and $1700 monthly. The entity’s identity and the enhanced tool’s potential benefits are left ambiguous. The offer is valid until November 28. Skynet; a DDoS service, provided by Anonymous Sudan, has showcased its capability by launching attacks on several prominent targets. Notable victims include tech giants such as Apple and Telegram, cloud services like Azure, cybersecurity vendor Sucuri, content delivery network StackPath, and gaming giant PlayStation.
Relevancy & Insights:
Anonymous Sudan has gained notoriety among hacktivists by targeting prominent organizations with overwhelming DDoS attacks. In such a scenario, any such endorsement of tools/services by Anonymous Sudan would have endorsement benefits both monetarily and in gaining a larger subscriber base.
ETLM Assessment:
CYFIRMA assesses that the global impact of the Anonymous Sudan Skynet Sale is substantial. The sale of DDoS services serves as a strategic maneuver to bolster their influence within the hacking community, causing Operational Disruption for sales companies. Particularly, this tactic has a pronounced effect on script kiddies who admire such hackers and seek rapid notoriety. This underscores the critical need for governments and businesses to prioritize cybersecurity and address these concerns promptly.
Kaggle Careers Data Advertised in Leak Site
Summary:
CYFIRMA Research team observed a potential data leak related to Kaggle Careers, {www[.]kaggle[.]com}. Kaggle Career is the world’s largest online data science competition community with more than 4 million+ members across 194 countries. Kaggle’s Career network fell victim to a data breach that resulted in 3,000,000 companies having their wage and business information leaked. The breached data includes SL NO, CASE STATUS, EMPLOYER NAME, SOC NAME, JOB TITLE, FULL TIME POSITION, PREVAILING WAGE, and additional confidential information.
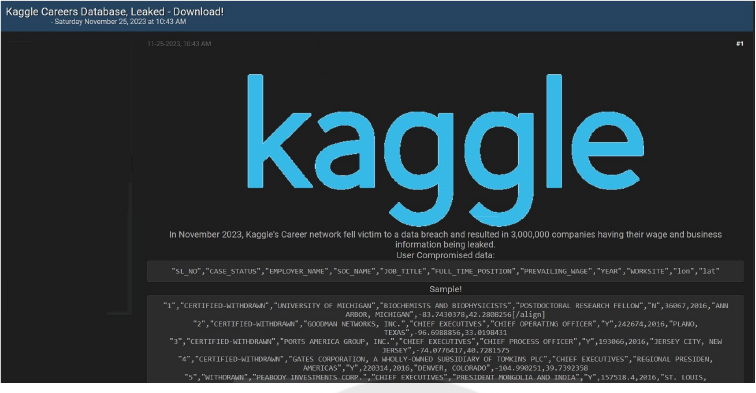
Source: Underground forums
Relevancy & Insights:
Opportunistic cybercriminals motivated by financial gains are always on the lookout for
exposed and vulnerable systems as well as applications. The majority of these attackers operate in underground forums engaging in related conversations and buying/selling stolen digital goods. Unlike other financially motivated attackers such as ransomware groups or extortion groups who often publicize their attacks, these attackers like to operate under the hood. They gain access and steal valuable data by taking advantage of an unpatched system or exploiting a vulnerability in an application or system. The stolen data is then advertised for sale in underground forums, resold, and repurposed by other attackers in their attacks.
ETLM Assessment:
Although the cause of the Kaggle Careers data leak remains unclear, the threat actors responsible have a history of carrying out breaches for both political and financial motives. For instance, the same threat actor recently put up for sale sensitive information from organizations such as General Electric and DARPA, demonstrating their involvement in both politically and financially motivated cyber intrusions. CYFIRMA assesses U.S. institutions without robust security measures and infrastructure are expected to face an elevated risk of potential cyberattacks from this threat actor.
CYFIRMA Research team observed a potential data leak related to ShadowFax, {www[.]shadowfax[.]in}. Shadowfax Technologies is a company that operates in the Logistics and Supply Chain industry. ShadowFax Technologies, a company with a focus on delivery services, experienced a data breach resulting in the unauthorized exposure of information belonging to 5 million users. The compromised data includes User ID, MSG ID, Mobile, Sender, Sent time, Provider, Status MSG, Message, and other sensitive details.

Source: Underground forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS