



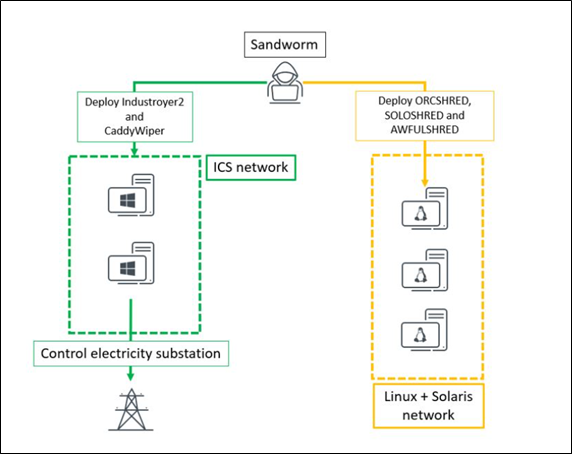
A new variant of Industroyer malware dubbed Industroyer2 was observed targeting energy providers in Ukraine. The threat actor Sandworm has been linked to this activity, used the same malware in 2016 to disrupt the power supply in Ukraine. In collaboration with CERT-UA, the researchers discovered that Sandworm made attempts to implant Industroyer2 malware against Ukrainian high-voltage electrical substations. The threat actor groups, in addition to Industroyer2, used other malware families including CaddyWiper, ORCSHRED, SOLOSHRED, and AWFULSHRED. At this point, researchers are unclear about the initial access vector, and nor are they sure about how the threat actor moved from IT to the ICS network.
Analyzing the timestamps of Industroyer2’s compilation and scheduled task entry created from an infection, it has been assessed that the threat actor had prepared the attack at least two weeks in advance.
Researchers highlight that the new variant Industroyer2 malware is believed to be based on the same source code as Industroyer with high confidence. The new malware variant is highly configurable and has detailed hardcoded configuration in its body as opposed to Industroyer which stored configuration in an .INI file. The said configuration drives the action of the malware and therefore, the attackers are required to compile Industroyer2 for each new victim or environment. Researchers assess that this limitation is not going to hinder Sandworm.
On April 8, a distributed denial-of-service attack took down the websites of the Finnish ministries of Defense and Foreign Affairs. The attack was suspected to be started at about noon, while Ukrainian President Zelenskyy was addressing Finland’s Members of Parliament (MPs).
The attack was observed targeting the Foreign Ministry’s external website and the Finnish government officials said the situation returned to normal at around 1 p.m. The State Department has taken steps to curb the attack, along with service providers and the Cyber Security Center.
Earlier that morning, before the cyberattacks, a Russian passenger jet was suspected of violating Finnish airspace. The clear infiltration by the IL-96-300 aircraft happened off the coast of the Gulf of Finland near the city of Porvoo and lasted about three minutes, according to the Ministry of Defense.
Even though the Finnish government has not blamed Russia for the DDoS attack, experts hypothesize that the attack could be linked to the support offered by Finland to Ukraine and the condemnation of the invasion.
Last week, an attacker group called “BlueHornet” claimed on Twitter about finding an experimental exploit for NGINX 1.18. As per their claims, the group has evaluated the exploit against an undisclosed number of organizations stating “ … handful of companies and corporations have fallen under it.”
The group explained the exploit involves two stages where the first stage starts with an LDAP injection. Later they had created a GitHub page detailing the issue and how to produce it. It further revealed that the exploit was handed to them by a sister group called “BrazenEagle” who had been working on the exploit for quite some time. They have intended to share the issue in a responsible disclosure to the NIGNX security team.
Taking notice of events, F5 which bought the popular web server is investigating the issue. In a blog post, F5 stated that the issue only affects LDAP reference implementations and does not affect NGINX Open Source or NGINX Plus.
This is an unusual move from the attacker group BlueHornet (AgainstTheWest, APT49) who has been known to the CYFIRMA Threat Intelligence team to leak data in underground forums. The data leaks from the groups have been related to organizations working in China, however, they claim to conduct operations against Russia, Iran, North Korea, Belarus, and Hong Kong as well.
Since one of the major underground forums, where AgainstTheWest was also active, has been taken offline by law enforcement and actions on its operator are soon to follow, it may be a move from the group to come in the good books of law enforcement.
Researchers have observed attackers trying to exploit the Spring4Shell – a Java-related flaw to install malware on vulnerable systems. The attacks have been said to emerge as soon as the flaw came into the public. Researchers highlight that soon after 30th March, attempts involving various webshell started to appear. It also included a variant of the Mirai botnet which first adopted the vulnerability. Another researcher observed similar activity where malicious actors actively exploited Spring4Shell to weaponize and execute Mirai botnet malware on vulnerable systems.
When the flaw Spring4Shell came into public light it almost went viral and was often compared with Log4Shell, despite not being as serious as Log4Shell. Although, Spring4Shell will be on the radar of attackers looking to weaponize it due to its simplistic exploitation. In addition, the details on how to leverage the Sping4Shell flaw and the relevant technical details are already in the public domain. This gives an opportunity to a group of attackers who may not as be as skilled as others and sets the stage for abuse on a larger scale.
The Cybersecurity and Infrastructure Security Agency (CISA) has already urged the developer to patch their system in case they are using Java Development Kit (JDK) from version 9.0 and above. The vulnerability also features in CISA’s ‘Catalog of Known Exploited Vulnerabilities. It should be noted that CISA’s ‘Catalog of Known Exploited Vulnerabilities’ is an excellent resource for organizations to keep up with trending vulnerabilities among attackers. The initiative aims to catalog the most important vulnerabilities that have been previously exploited by attackers and pose a serious risk. Organizations must monitor and prioritize these vulnerabilities listed in this catalog.