



Suspected Threat Actors: APT28 (Fancy Bear)
Researchers have recently observed a campaign by the group APT28 targeting users in Ukraine with malware that steals credentials stored in browsers. The APT28 is a notorious Russian threat actor with ties to Russian Intelligence primarily tasked with collecting intelligence for the Russian government.
Recently researchers found a document that leveraged the Follina (CVE-2022-30190) vulnerability to download and execute a new .NET stealer. The malicious document “Nuclear Terrorism A Very Real Threat.rtf” attempts to trick victims into opening the document by enticing fear into victims that the ongoing invasion of Ukraine will result in a nuclear conflict. The final payload being deployed in this campaign is almost identical to the variant reported by Google with some minor changes and aims to steal data from web browsers.
The malicious document in question is actually a .docx file while it pretends to be an RTF file compiled on June 10. This suggests that the attack was carried out around the same time. This file uses a remote template embedded in the Document.xml.rels file to retrieve a remote HTML file from a URL which in turn use uses a JavaScript call to invoke PowerShell script to download and execute the final payload. According to researchers this payload is a variant of a stealer that APT28 has used to target Ukrainians in the Past.
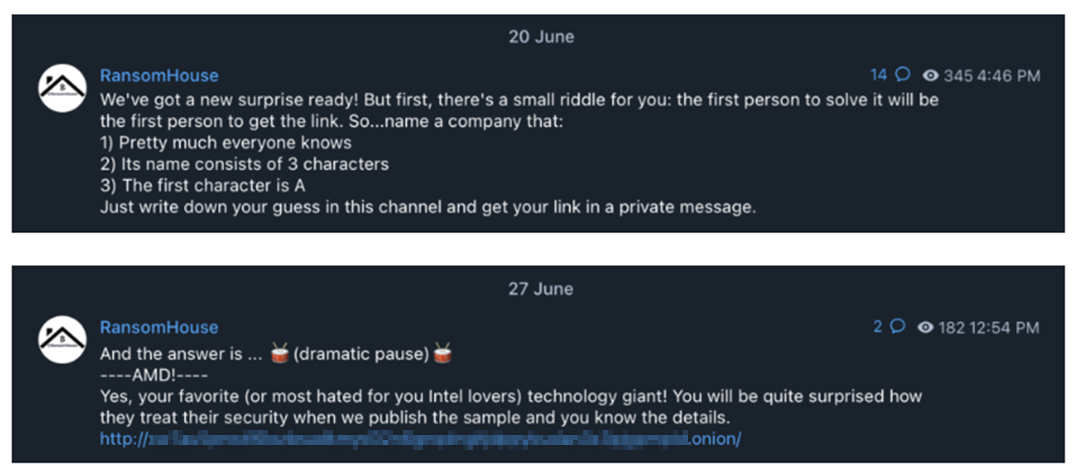
The semiconductor giant said in a statement they are conducting investigations on recent claims of an extortion group stealing data from the company. The extortion groups which go by the name of RansomHouse recently listed AMD on their leak site as one of its victims on Monday and claimed to have stolen more than 450 GB in January. The researcher who first spotted the claims found AMD passwords, system information, and other network files after examining a sample of the stolen data set.
On 20 June, the extortion groups had also bragged about the attack on their Telegram channel where they were offering stolen data to anyone who would guess the company name (AMD) after providing clues about their attack.
Researchers were also tipped by the RansomHouse themselves as to how they got into compromised AMD. According to RansomHouse claims, AMD was using “simple passwords” to protect its systems. In the tip, they said “… technology giants like AMD use simple passwords like [REDACTED] to protect their networks from intrusion. It is a shame those are real passwords used by AMD employees, but a bigger shame to AMD Security Department which gets significant financing according to the documents we got our hands on – all thanks to these passwords.”
First observed in December 2021, the RansomHouse extortion group despite the name and contrary to ransomware groups commonly observed today – does hot claim to be a ransomware group. It is taking a different approach to its cybercrime business. Going through their DLS and mission statement, they are projecting themselves as a “professional mediators community” likely between the victim and attacker. They claim to be not involved in any of the attacks or produce/use any type of ransomware and present themselves as a negotiator between related parties. In their mission statement, they go to a great length to justify their actions and their “associates.” At the same time blaming the victim organization for not protecting data with adequate security measures.
Unsurprisingly, extortion tactics remain the same as other ransomware groups. Organizations refusing negotiation or in case of arriving at a reasonable disagreement are threatened with name and shame.
RansomHouse, although claiming to be different than other ransomware groups that also rely on affiliates, has taken a different approach. RansomHouse is introducing a novel business approach to their cybercrime business, challenging the normal RaaS operations which are often a close-knit group of cybercriminals. The worrisome factor is their “offer” that enables it to be a ransom marketplace where anyone can feature stolen data of an organization.
Given the current state of ransomware where we already have a couple of established players that account for a huge chunk of ransomware incidents globally, newcomers are forced to come up with innovative solutions to make their mark.
Researchers observed an intrusion attempt by suspected ransomware against an unnamed target that made use of Mitel VoIP appliance as an initial entry point to gain RCE and gain access to the network. While tracing the source of the attack, researchers found a Linux-based Mitel VoIP device on the network perimeter and identified an exploit that was previously unknown alongside they found a couple of anti-forensic measures. The novel exploit relates to a high severity vulnerability that was fixed by Mitel in April 2022.
Timely patch management is extremely critical for perimeter devices. Although organizations with good patch management hygiene may still fall, victim, when threat actors resort to exploits that still have not been documented. Therefore, defense-in-depth becomes all the more crucial in such cases. In addition, to avoid facing any adverse event critical system must be isolated to the greatest extent possible from perimeter devices. Doing so will keep critical data safe as threat actors will not be able to get access to critical data in a “one hop” fashion from the compromised device even if they can overcome perimeter defenses.