



8 May 2021
A Chinese-speaking threat actor has been observed to be deploying a new backdoor in multiple cyber-espionage operations targeting military organizations from Southeast Asia spanning roughly two years. NAIKON, suspected to be a state-sponsored threat actor funded by China, known to targeted high-profile organizations and governmental and military entities is active for at least a decade. The threat actor has abused legitimate software, to side-load the second-stage malware Nebulae which is designed to gain persistence by adding new registry keys. The researcher highlighted that RainyDay or FoundCore were used as first-stage malware to deploy second-stage payload for various purposes including the Nebulae backdoor. Below are the legitimate software observed to be abused by NAIKON:
The infrastructure identified in the current campaign is similar to previously documented reporting, by another researcher last year. In the campaign observed in 2020 specific targets included countries from Asia-Pacific regions namely Australia, Indonesia, Philippines, Vietnam, Thailand, Myanmar, and Brunei. The motive behind the Naikon APT campaign is to gather geopolitical intelligence by infiltrating a government body. The data thus gathered is used to attack new government targets.
The group is suspected to be highly motivated and sophisticated. The researchers highlight that before the 2020 espionage campaign was detected, the threat actor spent the five years quietly developing their skills and introducing a new cyber-weapon with the Aria-body backdoor. The group has also been known to use common exploits attributed to multiple APTs groups and uniquely uses victim’ servers as command and control servers to evade detection.
Researchers found a sample of PortDoor, while tracking malicious RTFs (Rich Text Format), which is known to be used by Chinese state threat actors. It has been noted that RTF “bears the indicative ‘b0747746’ header encoding and was previously observed to have been used by Tonto, TA428 and Rancor threat actors. Tonto and TA428 have in the past attacked Russian research and defence related targets.
Over the years, the RoyalRoad weaponizer, also known as the 8.t Dropper/RTF exploit builder, has become a part of the arsenal of several Chinese-related threat actors such as Tick, Tonto Team and TA428. They regularly employ RoyalRoad for spear-phishing in targeted attacks against high-value targets.
Multiples threat actors have been targeting critical infrastructure, government research centres, manufacturing, and international relations in Central Asia with a mix of commodity malware and unknown backdoors. They planted backdoors to gain long-term access to network infrastructure, and their TTPs used are – spear-phishing, espionage, profiling, privilege escalation, XOR encryption to deliver additional payloads, and AES encryption to exfiltrate data.
The suspected Multiple Chinese APT groups are aggressively targeting Japanese companies and research centres involved in policy making, to further their state’s geo-political agenda.
The Belgian network Belnet was targeted by a major attack that began at 11 AM on 04th May 2021, paralyzing many Belgian services and institutions. Belnet is a government-funded ISP provider for the country’s educational institutions, research centres, scientific institutes and government services – including government ministries and the Belgian parliament.
More than 200 Belgian organizations use the services of Belnet. This attack on Belnet impacted all the organizations and their users connected to the network, profoundly disrupting their functioning.
The DDoS attack was suspected to be of magnanimous proportion, saturating the entire network. The fact that the hackers of the attack constantly changed tactics made it difficult to neutralize the attack. There seems to be no observed evidence of intrusion into Belnet servers or data theft. It is suspected that the attack was aimed solely at disrupt the Belnet network.
Government and industry have come together to combat a significant increase in the number of ransomware, and the newly formed ransomware working group has called for new measures to more actively monitor Bitcoin and cryptocurrency flows.
The task force includes law enforcement agencies, including FBI and US Secret Service agents, working alongside representatives from leading security and technology firms.
The proposed rules aim to respond to a record year for ransomware attacks. The target group estimates that ransomware syndicates raised about $ 350 million during 2020 – a 200% increase over the previous year targeting government agencies, hospitals, educational institutions, and private companies.
Researchers have observed that Melbourne-based Schepisi Communications – a platinum partner of Telstra, the largest wireless carrier in Australia – is hit by the Avaddon ransomware gang. The operator has published the exfiltrated data in a dark web forum which includes SIM cards and related information, financial information, contracts, banking information, and more. The leak also includes data from other Australian organizations including global food conglomerate Nestle.
Soon after researchers have observed the leaked data in the ransomware gang’s portal, Telstra confirmed there had been a security breach that affected one of its “dealers”.
The following screenshots were observed published in one of the dark web forums:

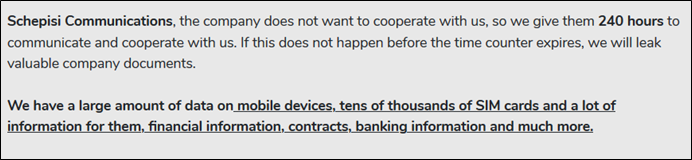
The Avaddon ransomware gang adopts a three-pronged approach to spearhead their ransomware operation to extort money from the affected victims. Apart from exfiltrating and encrypting the data, once the victim is compromised, the gang keeps them under DDoS attack until they “communicate and cooperate” with the ransomware gang. The victims are also provided a maximum of 10 days after which the data gets leaked into their dark web portal.
In February 2021, an open-sourced tool to decrypt systems infected with Avaddon ransomware was made available. However, once the existence of the decryption tool was made public, the Avaddon ransomware gang fixed their code within days mirroring a similar course of action taken by the Darkside ransomware gang. Following the incidents, experts suggest decryption utilities that take advantage of ransomware encryption bugs should be kept private and distributed to victims via non-public channels. In case such utilities need to be made public it should not accompany technical details that help the attackers patch their code.
Android users are being targeted via a set of fraudulent apps that made their way to the Google Play Store. Researchers have dubbed the malware behind the campaign as Etinu that posed as photo editors, wallpapers, puzzles, keyboard skins, and other camera-related apps. These fraudulent apps reaching over 700,000 downloads hijack SMS message notifications make unauthorized purchases via hijacking SMS message notifications. While the apps go through a review process to ensure their legitimacy, the researcher highlight that a clean version is provided for review, and malicious code is introduced at a later stage via updates.
The malware embedded in these fraudulent apps takes advantage of dynamic code loading (DCL) that prompts app publishers to load code that is not part of its static, initial codebase. To steal incoming SMS messages the malware hijacks Notification Listener without the SMS read permission which was observed in Android Joker Malware. Last month a new set of malicious android apps posing as app security scanners to distribute BRATA (Brazilian Remote Access Tool Android), capable of gathering sensitive information was observed. While researchers highlight that threats leveraging Notification Listener are likely to surge, it is deemed challenging for Play Store to spot all malicious apps due to a very high number of submissions per day. As Play Store lags, malicious apps slip through its security controls and in turn into victims’ phones.
A security researcher has published proof-of-concept exploit (PoC) and technical documentation for a high-severity vulnerability in Microsoft Exchange Server that allows a remote attacker to execute code on unpatched systems. The bug tracked as CVE-2021-28482 is one of four the vulnerability reported by National Security Agency (NSA) and has least severity among the four yet pose a serious risk to organizations. Apart from publishing technical details to achieve remote code execution in an authenticated Exchange Server environment, the researcher also released “PoC_CVE-2021-28482.py” demo exploit. The researcher highlights that businesses running on-premises instances that do not run Microsoft’s April update are vulnerable, and the risk is much higher to servers exposed over the internet.
The set of NSA reported vulnerability came soon after the discovery of ProxyLogon vulnerabilities which were suspected to be being actively exploited a month before a patch was made available. After the news and official advisory from Microsoft suggesting Exchange Servers were being targeted with Zero-day exploits by a threat actor named HAFNIUM, business rushed into high patch rate. It is expected that the ProxyLogon patch momentum may have allowed businesses to pay equal attention to later exposed NSA reported vulnerabilities. However, researchers highlight that organizations running an unpatched Exchange instance are at heightened risk as a single leaked credential may allow for a successful compromise.