• Attack Type: Phishing, Malware Implant
• Target Industry: Multiple
• Target Geography: South Korea
• Target Technology: Microsoft Windows
• Objective: Payload Delivery, Defence Evasion, Data Obfuscation, Data Exfiltration
• Business Impact: Data Leak, Operational Disruption, Financial
North Korean Threat Actor Lazarus Group known to employ new techniques and custom toolsets in its operations to increase the effectiveness of its campaigns has resorted to an interesting technique of bitmap (BMP) file embedded with malicious HTA (HTML Application) objects to drop its Loader. The attack likely starts by distributing phishing emails weaponized with a Korean-themed malicious document asking users to enable the macro to view the document. Upon macro execution, an HTA file compressed as a zlib file contained within a Portable Network Graphics (PNG) image file is called. The macro converts the PNG image file to decompressed BMP file format, thereby evading detection from security solutions. The HTA then drops a loader RAT stored as “AppStore.exe” which connects to the command-and-control server for further instruction.
The threat actor group behind this phishing campaign has improved its operating capabilities by hiding the malicious object such that it cannot be detected by security controls. Exfiltrated critical data can potentially be sold on underground forums or further leveraged to cause massive financial and reputational damage against the organization. Researchers observed the secondary payload has similarities with the custom encryption algorithm used by BISTROMATH RAT and code similarities with some of the known Lazarus malware families including Destover.
Russian hackers have a long history of going after organizations in Ukraine, but one group, Gamaradon, has its focus on the former Soviet republic. The campaign first appeared in January and ran through till mid-March. This activity coincides with escalating tensions between the two nations, with Russian troops buildup along the Ukrainian border. Researchers were unclear about the objective of the campaign because the remote template domains used in the campaign were down during the discovery.
Ukrainian National Security and Defense Council has alerted its government officials of potential cyber-attacks. The suspected Russian hackers capitalized on current events as part of the likely spearphishing attempts. One legitimate-looking document in the campaign is a Bulgarian-themed dissertation, during a time when Bulgarian prosecutors charged six Bulgarian government officials with spying for Russia.
Japanese local media outlets, citing unidentified sources in a police investigation, have reported that two Chinese nationals used fake IDs to register web servers between 2016 and 2017 that were subsequently used by the Chinese hacker group Tick. The latter used these servers to target Japanese companies and research institutes active in the aviation and national defense domains. To date, the only victim identified is the Japan Aerospace Exploration Agency (JAXA).
Since 2016, the Tick APT group has reportedly obtained unauthorized access to networks of organizations associated with critical infrastructure, heavy industry, manufacturing, and international relations. They are known to use custom malware called Daserf, but also employ multiple commodity and custom tools, exploit vulnerabilities, and uses social engineering techniques. The group’s reported TTP’s involve the usage of spear-phishing and watering hole attacks to breach the systems of its targets. The threat actors are also fluent in Japanese, crafting phishing emails in native Japanese and operating successfully within a Japanese-language environment.
The group has demonstrated the ability to identify a significant zero-day vulnerability within a popular Japanese corporate tool, SKYSEA Client View, and then use scan-and-exploit techniques to indiscriminately compromise Japanese Internet-facing enterprise systems. The group only proceeded with further activities in the case of companies that presented an interest. Once it no longer needs any information from a target, Tick attempts to remove all evidence of its activities on the compromised networks.
The targeted companies are key organizations involved in the transportation, warehousing, storage, and distribution of the COVID-19 vaccine. In early September 2020, the threat actor began sending spear-phishing emails before any COVID-19 vaccine variant was approved. These emails requested quotes for the Cold Chain Equipment Optimization Platform (CCEOP) program and impersonated Chinese biomedical firm Haier Biomedical.
The COVID-19 cold chain — an integral part of delivering and storing COVID-19 vaccines at safe temperatures, and the associated intellectual property (IP) — have become the primary source for
The calculated nature of this operation involving many interlinked and globally distributed target points has led researchers to attribute this to a nation-state activity.
• Attack Type: Social Engineering, Malware Implant
• Target Industry: Social Media
• Target Geography: Multiple
• Target Technology: WhatsApp
• Objective: Unauthorized Access, Data Theft
• Business Impact: Data Loss, Financial Loss
Researchers have disclosed an unusual baiting technique targeting WhatsApp users which claims to turn the application theme to pink along with certain ‘‘new features”. The app impersonates an official update from WhatsApp. The researcher highlights that the link is being spread through WhatsApp groups with #WhatsappPink leading to an APK download. The researcher suspects that the installation of malicious APK may allow the attacker to take complete control of the affected device and steal data.
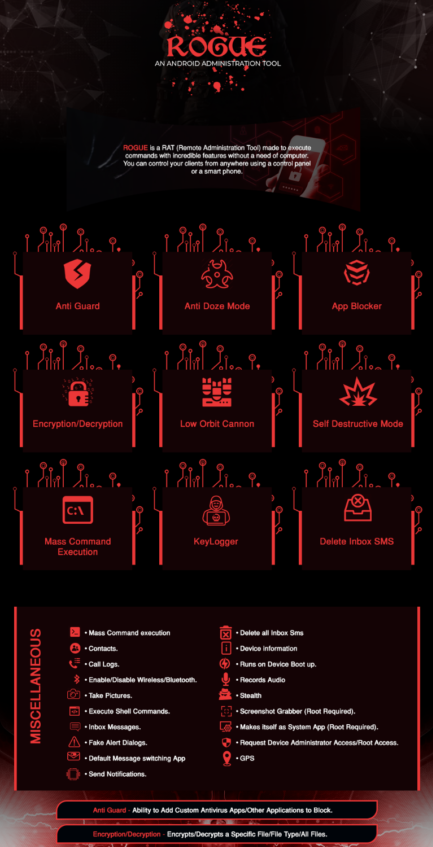
Rogue Mobile Apps, a counterfeit app designed to impersonate trusted brands are a constant problem for businesses as well as app stores trying to protect users from such malicious apps. Due to increased digitization and wider reach of social media, attackers have been increasingly using Rogue Mobile Apps as an attack vector. Earlier this year, while tracking threat actors Triangulum and HeXaGon Dev – known to have distributed multiple Android malware, including crypto miners, key loggers, and sophisticated P2P (Phone to Phone) mobile RATs – researchers have observed advertisements for “Rogue” mobile RAT for sale in one of the dark web marketplace.
• Target Industry: Defense and others
• Target Geography: US
• Target Technology: Pulse Connect Secure
• Vulnerabilities: CVE-2021-22893 (CVSS Base Score: 10)
• Vulnerability Type: Authentication Bypass, Remote Code Execution (RCE)
• Impact: Confidentiality (High), Integrity (High), Availability (High)
• Suspected Threat Actor: Keyhole Panda, UNC2630, UNC2717
Researchers have highlighted that the ongoing exploitation of the Pulse Secure Connect tool is suspected to be state-sponsored. Twelve different malware families are being tracked as part of the attack and suspect the involvement of Keyhole Panda, UNC2630 and UNC2717. The vulnerabilities highlighted under attack include three known flaws – CVE-2019-11510, CVE-2020-8260, CVE-2020-8243, and a newly disclosed zero-day flaw CVE-2021-2289. The vulnerability is an authentication bypass vulnerability that allows an unauthenticated user to execute remote arbitrary file execution on the Pulse Connect Secure gateway.
Pre-existing vulnerabilities in VPN solutions have emerged as a favorite target for cybercriminals and nation-state groups considering that large segments of the global workforce are working remotely and employing VPN to connect to organizational resources.