



22 May 2021
After the launch of a massive spam campaign targeting victims globally utilizing Avaddon ransomware, the operators started recruitment of affiliates in June 2020 which molded it into ransomware-as-a-service (RaaS) operations. Along with data encryption and the threat to leak the data, in January 2021, the operators started using distributed denial-of-service (DDoS) attacks as an extortion tactic to pressure victims into paying the ransom. Despite the recent Colonial Pipeline ransomware attack and response action taken by law enforcement agencies which reportedly affected some of the ransomware operators, the Avaddon ransomware operators seem to have remained undeterred.
The banking trojan QakBot, (aka Qbot, Pinkslipbot, and Quakbot) has evolved over the years, including Command & Control (C2) techniques, delivery mechanisms, and anti-analysis and reversing features. After the Emotet takedown, QakBot is becoming one of the prominent threats enabling cybercriminals to secure access into corporate networks. The malware is equipped with a multitude of evasion and info-stealing routines apart from worm-like functions that allow it to remain persistent. In the past QakBot has been known to drop other malware such as ProLock and Egregor ransomware.
The Snip3 crypter was recently observed by researchers while monitoring a highly sophisticated crypter-as-a-service that delivers numerous RAT families. The newly identified crypter deploys several advanced techniques such as executing PowerShell code with the “remote signed” parameter, detect Windows sandbox and VMware virtualization, using Pastebin and top4top for staging to bypass detection. Organizations that rely solely on detection-centric security strategy are at heightened risk as more and more malware are leveraging highly evasive techniques to bypass detection.
Dridex is often used in the initial infection stage to deliver company-wide ransomware operations and is largely distributed via malspam campaigns containing malicious attachments. The malware allows to contact a remote server, sends information about the infected system, and also can download and execute arbitrary modules on command.
CYFIRMA researchers suspect the above malware types will continue their propagation using massive malspam campaigns that center around the “spray and pray” approach for increased conversion rate. Organizations must enhance their security strategies using Content Threat Removal (CTR) techniques. As threat actors continuously seek new and innovative ways to breach into the organization such technology can help mitigating undetectable threats as it does not attempt to detect a threat, rather assumes all data is hostile and transform content to eliminate potential risks.
Researchers have identified a cyberattack attributed to the infamous FIN7 spreading a backdoor called Lizar. Disguised as a legitimate cybersecurity company, the threat actor distributed Lizar as a penetration testing tool for Windows networks. According to researchers, the newer Lizar version 2.0.4 variant, discovered in February, offers powerful data retrieval and lateral movement capabilities. The Lizar toolkit is structurally similar to previously used backdoor toolkit Carbanak and includes components: Lizar client, Lizar server, Lizar loader, and Lizar plug-ins. The loader and plug-ins run on an infected system and can be combined to form Lizar bot component that facilitates a modular architecture allowing scalability and independent development of all components. The researchers have observed three types of bots: DLLs, EXEs, and PowerShell scripts.
FIN7 has been observed leveraging the impressive technique of disguising malware as a package – from well-known cybersecurity firms, Check Point Software or Forcepoint – to push the Carbanak malware. While the Lizar toolkit is diverse and complex and still considered to be under development, it is already widely used to control infected systems.
The Japanese government is calling for more attention to cybersecurity risks on the part of the private sector working on critical infrastructure. The Japanese government plans to amend various laws governing each sector by passing an all-encompassing motion and a new law requiring each sector to be conscious of national security risks.
The sectors concerned include telecommunications, electricity, finance, railways, public services, and health. In other words, critical infrastructure. these sectors will be required to investigate issues arising from the use of foreign equipment or services, including cloud data storage and connections to servers abroad. The government will reportedly also monitor companies to support compliance and be empowered to prevent companies from using foreign equipment if they discover major problems.
The move comes a week after Colonial Pipeline – one of America’s largest pipeline operators, which supplies about 45% of the country’s east coast fuel – suffered a ransomware attack. Due to the cyber attack, the company had to temporarily shut down operations, freeze IT systems to isolate the infection, and pay a hefty fee to decrypt locked systems.
United States Federal Bureau of Investigation (FBI) and the Australian Cyber Security Centre (ACSC) are warning of an ongoing Avaddon ransomware campaign targeting organizations from a wide array of industries.
The investigators note that alongside leaking stolen data and encrypting systems, Avaddon threat actors are threatening victims with DDoS attacks to persuade them into paying ransoms. According to the FBI however, no evidence has been found of DDoS attacks following Avaddon ransomware attacks.
As a Ransomware-as-a-Service (RaaS) operation, the average ransom payment demanded by Avaddon affiliates is roughly 0.73 bitcoins (approximately USD 41,000) in exchange for the decryption tool (Avaddon General Decryptor).
Typically, Avaddon ransomware is delivered through phishing emails that contain malicious attachments in the form of a zip archive with malicious JavaScript inside. CYFIRMA observed Avaddon listing a Taiwan-based organization on their data leak site with a countdown hinting at an upcoming DDoS attack. Based on proximity, CYFIRMA researchers believe that Japan could be a potential next target for Avaddon operators. Alongside disrupting the targeted company’s network, DDoS will also have a secondary effect of disrupting any remediation activities, like processing backups of impacted servers.
The flaws mainly exist in the way Wi-Fi and connected devices manage data packets, especially in the handling of fragments and frames of data packets. The name FragAttack is a contraction of fragmentation and aggregation attacks which shows the place where the vulnerabilities were discovered. The majority of the flaws found were linked to the ability to inject plaintext frames, as certain devices can accept any unencrypted frame or plaintext aggregated frames that look like handshake messages. The disclosed vulnerabilities can be categorized as follows:
There are a few more implementation vulnerabilities that can be used to escalate the flaws listed above.
Researchers published details of FragAttacks after a nine-month embargo to give vendors time to roll out their patches. At present, the Microsoft patches are out, and patches for the Linux kernel are also on the way. Some networking vendors such as Cisco, Juniper, and Sierra are at different stages to release patches for some of their impacted devices. According to Wi-Fi Alliance, there is no evidence of the vulnerabilities being used against Wi-Fi users maliciously, and these issues are mitigated through routine device updates that enable detection of suspect transmissions or improve adherence to recommended security implementation practices.
The vulnerability tracked as CVE-2021-31166, discovered internally by Microsoft’s staff and patched in the May 2021 Patch Tuesday advisory. The vulnerability, considered to be the most dangerous vulnerability by researchers is a memory corruption vulnerability in the HTTP protocol stack. Microsoft highlights that an attacker may send a malformed packet and execute malicious code on the operating system kernel and could be used to create a network worm. A former Microsoft researcher has published proof-of-concept (PoC) code for exploiting CVE-2021-31166, that however does not include worming capability but only crashes unpatched systems.
While the bug appears extremely dangerous, it only impacts the recent version of Windows released last year and is unlikely to have been broadly deployed in production environments yet. Nevertheless, experts suggest such public PoC and other research work from the security community is usually an important first step towards threat actors experimenting with this attack. Eventually, extending the existing work, threat actors will come up with a workable exploit that helps them achieve their malicious objective. While there has not been reporting of any active exploitation of this vulnerability, organizations can get ahead of attackers by applying patch management best practices. Organizations with an effective patch management program can eliminate opportunities for exploitation.
CYFIRMA Researchers have observed data of petroleum giant British Petroleum (BP) being advertised for sale in an underground forum. The threat actor is suspected to have secured access to BP’s source code of the internal website, domain credential, and internal database information including access to TNSnames.ora file that contains network service names among other sensitive details. The threat actor has also claimed to access internal organization documents.
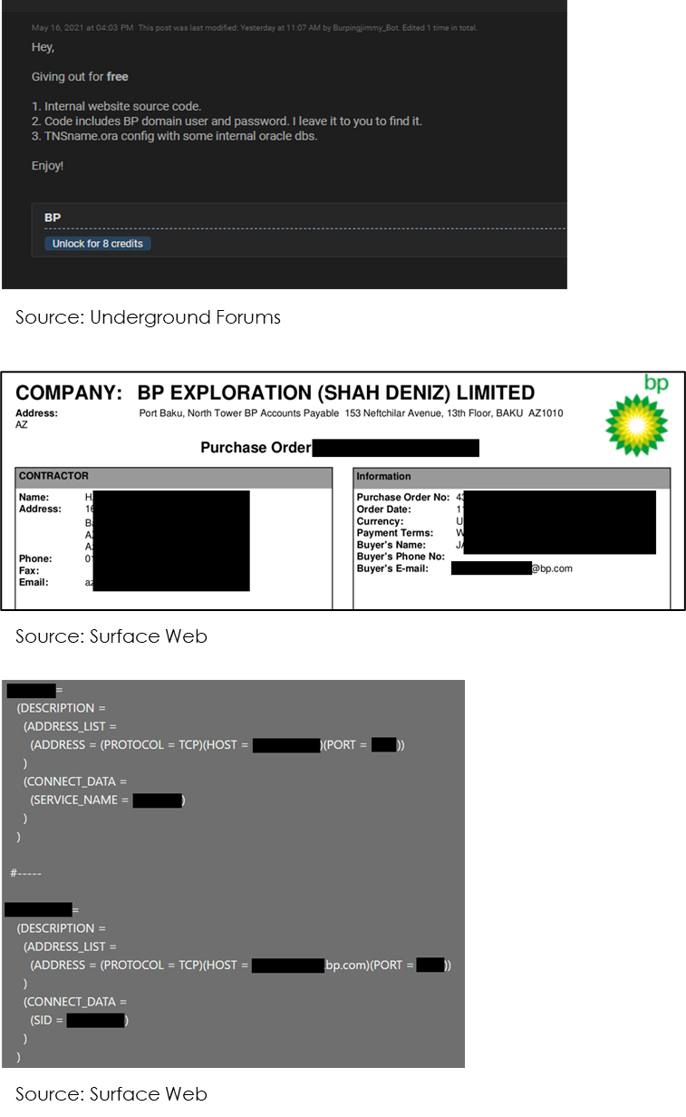
While breaches have a clear element of malicious intent such as a targeted cyber-attack, a leak may be purely accidental such as a human error. Despite the difference in motivation, the attack vector for both incidents largely remains the same. Compromised credential (aka credential theft or stolen credential) remains to be the most favorable mode of attack for cybercriminals. This stems from the fact that organizations have now migrated their workflows and communications to cloud-hosted services. It presents an attractive opportunity for cybercriminals as compromising a user in a cloud environment is much easier than following the cumbersome process of compromising the network. Other attack vectors leveraged by cybercriminals include social engineering techniques, human errors involving accidental action or inaction by an individual, and negligence in data security practices.
The current state of the pandemic has further escalated these issues with a largely remote and distributed workforce unprotected from the shield of corporate controls.
Organizations must pay special attention to business-critical data and take appropriate steps to help prevent mishaps involving unintentional exposure. Technical controls such as secure configuration, encryption (both in transit and at rest), privileged access, and vendor advisory must be adhered to in order to minimize such mishaps.