18 April 2021
Suspected Threat Actors: Twisted Spider, Viking Spider, Wizard Spider, and the Lockbit Gang
Summary: Emerging in June 2020, researchers state that four ransomware gangs (Twisted Spider, Viking Spider, Wizard Spider, and the Lockbit Gang) currently exist within the Cartel and are believed to have earned at least USD 75 million worth of Bitcoin from ransom payments. Last year, Twisted Spider issued a press release, claiming they joined forces with several other well-known ransomware attackers. The researchers observed a strong connection between the affiliated ransomware gangs sharing infrastructure, data leak sites, tactics, and re-investing profits to advance both tactics and malware. Attackers are moving towards automating their attacks, offering Ransomware as a Service (RaaS) and leveraging PR interviews, press releases, social media, call centers to harass and pressure victims into paying the ransom.
Insights: Financial gains remain to be the primary intent of a ransomware operator. To achieve the desired outcome, they resort to more aggressive tactics ranging from demanding ransom, the threat to leak data, double extortion to recently emerged “Ransom DDoS attacks” (RDDoS) where the RDDoS attackers use the threat of taking down a company’s website. This collaborative attempt adds another tactic to their arsenal and should be seen as a mere collective of ransomware gangs to appear more powerful and intimidate victims. The gangs may often work together on certain ransomware operations, however, do not present a centralized and authentic entity as in the cases of APT groups.
SUMMARY: Authorities have labelled this an extremist act but have yet to name the perpetrators. The incident occurred last week and impacted the Tehran-based nuclear facility’s power network. While calling the incident “sabotage” and “nuclear extremism”, authorities have confirmed that there were no casualties or leaks.
In the past, Stuxnet, a computer worm, has been used against Iran’s nuclear facilities. The worm switched off safety devices causing centrifuges to spin out of control.
Cyberattacks have proved to be the weapon of choice, often wielded by state-sponsored entities when targeting critical infrastructure installations of an ‘adversary’ as part of a wider geopolitical conflict.
SUMMARY: A previously undocumented Lazarus backdoor, dubbed Vyveva, was traced in an attack against a South African freight and logistics firm. While the initial compromise vector is still unknown, Vyveva shares multiple code similar with older Lazarus samples, namely, the NukeSped malware family.
Apart from the code similarities, the use of fake TLS in network communication, command-line execution chains, and the way of using encryption, and Tor services all point towards Lazarus, which is why Vyveva is attributed to the Lazarus group with “high confidence”.
Cyber espionage operations are often targeted towards industrial sectors, critical & strategic infrastructure with a focus on driving geopolitical issues, stealing state, and trade secrets. However, as reported in a recent campaign, CostaRicto, believed to be operated by hackers-for-hire – a group of APT mercenaries with diverse and random targets spanning across various geography.
SSC was hacked by GRU, via its 85th Center aka Unit 26165 in a campaign conducted between December 2017 and May 2018. GRU also targeted other prominent sporting bodies, including World Anti-Doping Agency (WADA) and FIFA. The hackers stole athletes’ personal details, such as medical records, and shared them with local media.
The incident that targeted World Anti-Doping Agency (WADA) was a response to accusations of government-sponsored doping which resulted in some Russian athletes being banned from the 2016 Olympic Games. Eventually, when charges were confirmed, WADA banned Russia from all international sport for four years, as of 9th December 2019. This has since fuelled the Russian hackers’ intent to “teach a lesson” to the authorities responsible for organizing the Olympic Games.
The timeline of the SSC’s data breach coincided with Sweden putting together a bid to host the 2026 Winter Olympics.
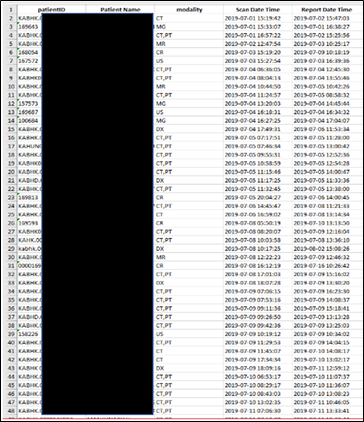
Summary: India’s largest cancer care provider HealthCare Global Enterprises Ltd was hit by the Avaddon ransomware group. The operator has published the exfiltrated data in a dark web forum which may include personally identifiable information (PII) and protected health information (PHI) of patients including diagnostic test reports, CT scans reports, MRI scan reports, prescriptions, patient list among other leaked information. The threat actor has also stated to perform DDoS attack.
The following screenshots were observed published in one of the dark web forums:

Summary: A new set of malicious Android apps posing as app security scanners on the official Play Store to distribute a backdoor capable of gathering sensitive information were identified by researchers. The malicious apps alert unsuspecting users of a security issue on their devices, prompting them to install a fake update of a specific app namely, Google Chrome, WhatsApp, and a non-existent PDF reader app. Once the action is authorized, BRATA requests permissions to access the device’s accessibility service, abusing it to capture lock screen PIN (or password/pattern), record keystrokes, take screenshots, and even disable the Play Protect.
Insights: BRATA (Brazilian Remote Access Tool Android), first documented in August 2019, emerged as an Android malware with screen recording abilities and morphed into a banking trojan. The malware has full device control as well as phishing capabilities. BRATA is yet another example of how simple social engineering techniques allow cybercriminals to trick and get total control of the victims’ devices.
Summary: While analyzing an exploit for a separate vulnerability, researchers discovered another zero-day exploit suspected to be linked to the BITTER APT group. CVE-2021-28310 is an out-of-bounds (OOB) write vulnerability in dwmcore.dll, which is part of Desktop Window Manager (dwm.exe). Due to the lack of bounds checking, attackers can create a situation that allows them to write controlled data at a controlled offset using DirectComposition API.
Insights: Apart from applying the patch, the organization should adhere to best security practices. It is suspected that the vulnerability has exploits available in the wild and potentially leveraged by several threat actors.
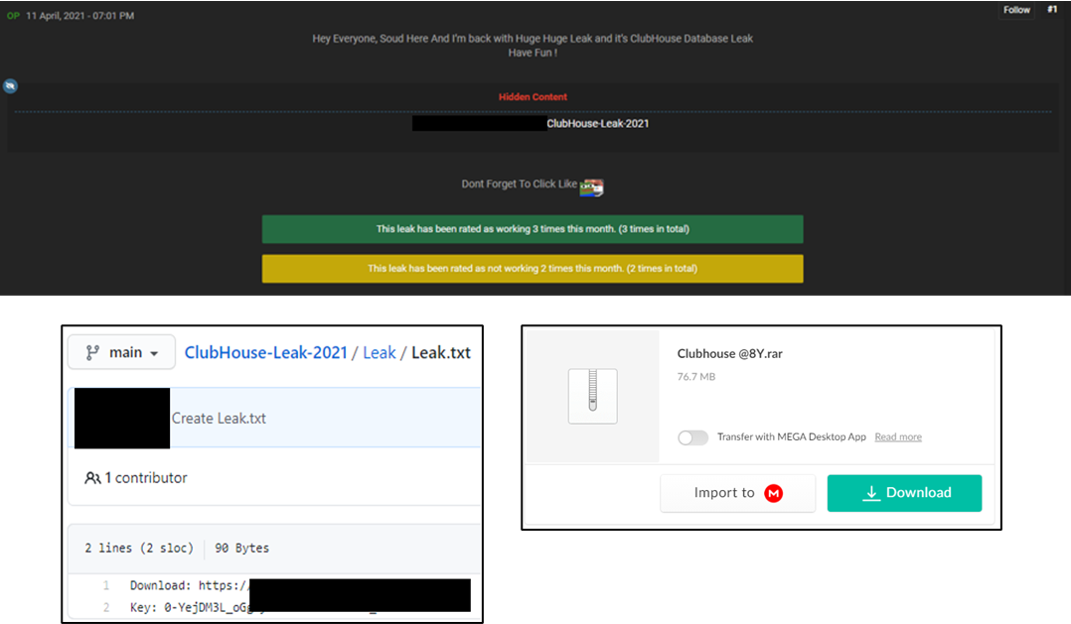
Summary: Clubhouse, an invitation-only social media app for iOS that facilitates auditory communication allegedly suffered a data leak that claims to have affected 1.3 million users. An unknown threat actor published links in one of the underground forums to the leaked data hosted on an external file-sharing site.
The following screenshots are related to the data leak:
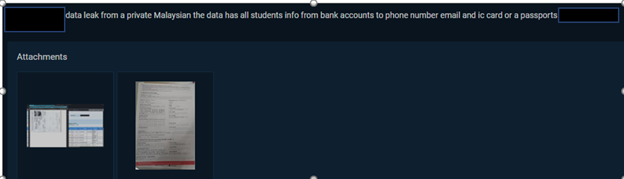
Summary: Details of students at a private Malaysian university, Help University, have been observed to be advertised for sale by unknown threat actors in the underground forums. The leaked data include details such as bank account details, phone number, email address, IC card, and passport details.
The following screenshots are related to the data leak: