



The malware, Red Alert 2.0, tricks users into downloading it by hiding in third-party app stores as fake versions of legitimate applications such as WhatsApp, Viber, and updates for both Android and Flash Player.
Once a user downloads one of these malicious apps into his or her devices and opens it, a popup overlay will appear prompting the user to enter their login credentials. The credentials are sent to the attacker’s command-and-control (C&C) server.
Red Alert 2.0 will block incoming calls from banks, presumably to block verification attempts. The malware also intercepts SMS text messages, sending messages to the attackers for future use. By disrupting the device’s actual communication capabilities, the attackers can maximize the time spent on malicious activities.
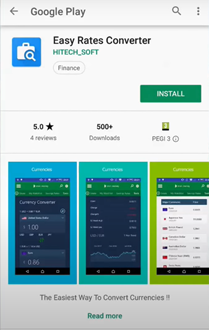
The malware is distributed through fake versions of legitimate applications or games via Google play store. Like the above image, the Easy Rates Converter application is a fake app which the application itself is clean. But once the application is installed on the mobile device it contacts its C2 server and requests the user to update the flash player to install an additional payload.
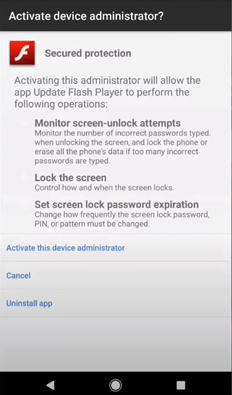
Once the user installs the flash player, it requests the user to activate the device administrator.
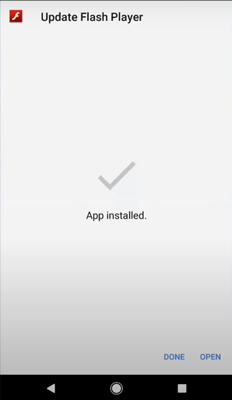
After the installation of the flash player, it is redirected to Play Store.
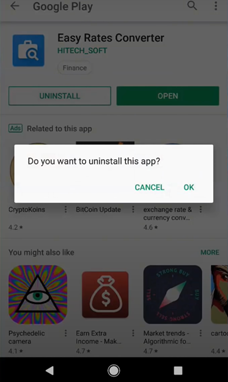
If a user were to suspect the app to be fake and proceeds to uninstall, the additional payload would still remain in the device.
The payload gathers information about the device and sends it to the C2 server. The C2 server provides the list of applications that the malware should target.
Whenever the victim launches the target application, the malware will create an overlay of the legitimate application and request the user to provide credentials as shown below.

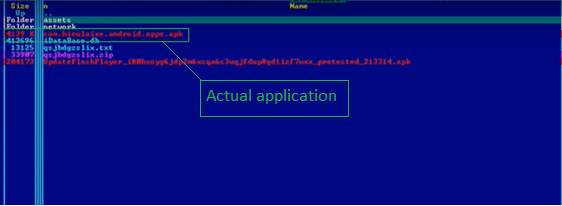
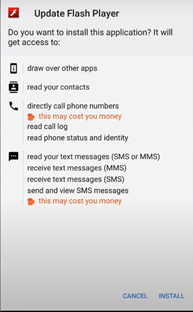
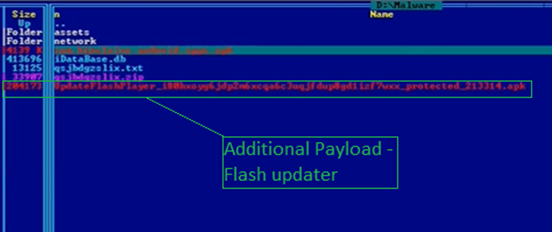
The app, when installed on the device, will request the user to install an additional payload as shown in the below image.
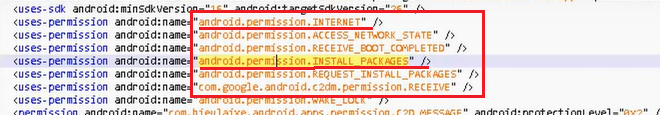
The list of permissions for the Application is as shown in the figure above. Suspicious indicators include permissions for Internet and permission to install packages.
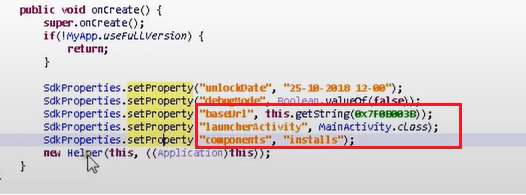
The highlighted code shows the app trying to contact C2 to download and install the additional payload.
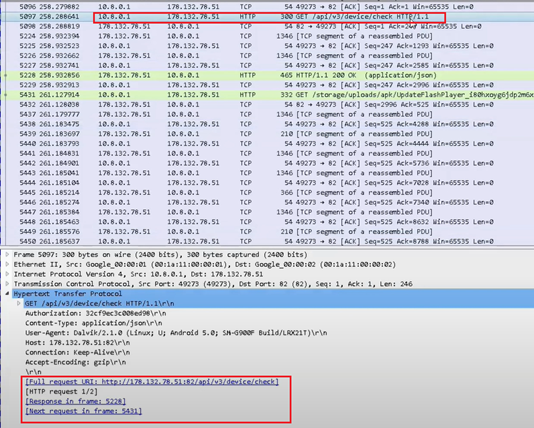
Capturing the network activity on the device, we could see the application establishing a connection with C2.
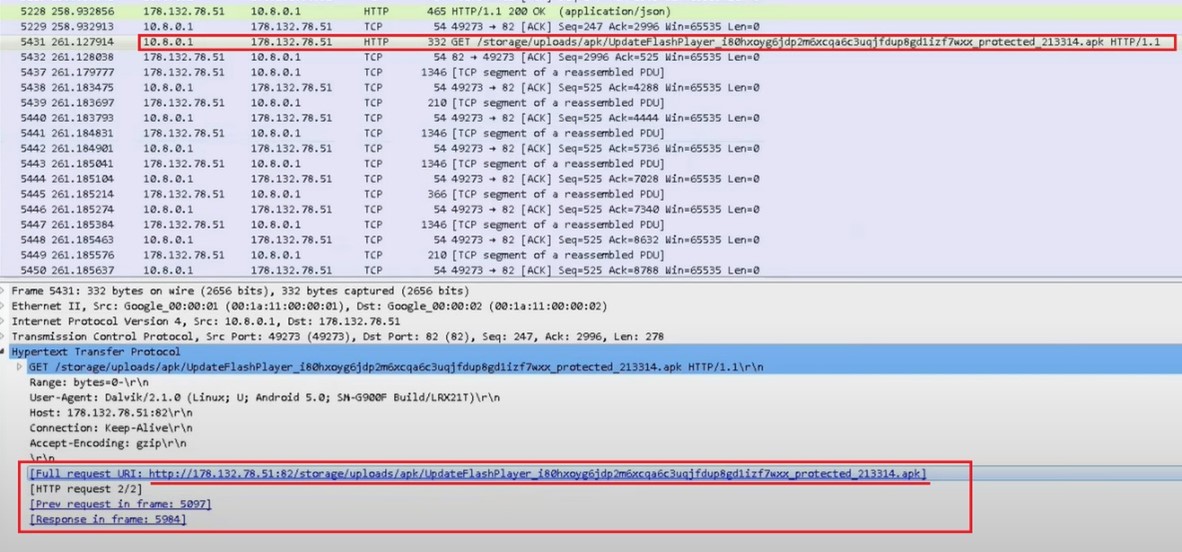
The application requests for the payload.
Once the payload is installed in the app, it gathers all information from the victim’s device and sends it to the C2 server.
The C2 server evaluates and sends the list of applications the payload should target.
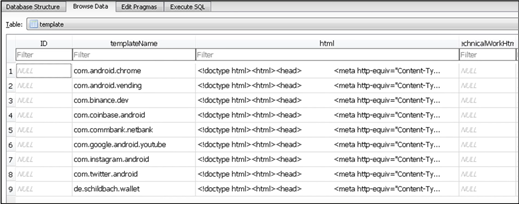
The payload opens an overlay page of the target application to steal credentials and other sensitive information like account details.
If you’d like to understand the cyber risk related to mobile apps, pls reach out to us at [email protected]