



Risk Score: 8
Confidence Level: High
Suspected Malware: SmokeLoader Malware
Function: Mainly act to download other malware and as Information Stealer.
Threat actor Associations: Association with Russians
Other Malwares related to SmokeLoader: Dofoil
First Seen: August 2011 but also recently seen in October 2021.
Target Industry: Multiple
Target Countries: Multiple
SmokeLoader is primarily a loader, and its main objective is to download or load a stealthier or more effective malware into the system. First detected in 2011 and its functioning is highly complex, and it increases its capability by adding new tactics/techniques regularly and constantly evolving with time. You may guess the advancement of the SmokeLoader from the fact that it was the first malware that used the “Propagate DLL Injection Method” when just its POC was released by researchers.
SmokeLoader variants are used for the purpose of information stealing, botnet, backdoor as well. SmokeLoader has also been used to install/load cryptominers, ransomware, banking trojans, and point of sale (POS) malware. The functionality of the malware changes with the attack type or target and depends on the modules used by attackers as the SmokeLoader is modular in nature.
Earlier, the SmokeLoader was sold on dark-web portals by the name SmokeLdr and since 2014, it is sold only to Russian-based threat actors.
The SmokeLoader is distributed through malicious documents like word or pdf documents send either through spam emails or targeted spear-phishing attacks. Once the victim downloads and opens the malicious document, the malware drops to the system and in the next stage injects malicious code into a compromised system process like explorer.exe and starts its malicious activity in disguise as a legitimate process.
File Details: As shown in Figure1, the following are the details related to the malware SmokeLoader.
File Type: Windows PE-32 Executable
MD5: 6a8f92ba4df2ba5415cd1fd97fcb87da
SHA256: fa611609c25485e53c73a059ae49eb25b8650727b0cf0d62ae4f72642e1b3d49
Subsystem: GUI
Compilation Time: March 2021
Figure1: Basic Information
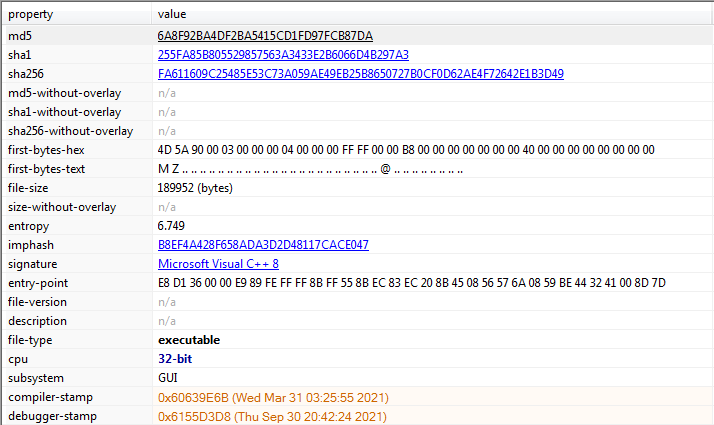
Figure1 above shows the basic information related to our malicious file, its hashes, it has Microfoft Visual C++ code and is a 32 bit PE executable. Further, the subsystem is GUI and has a compilation time of March 2021 which is quite recent.
Figure2: Sections
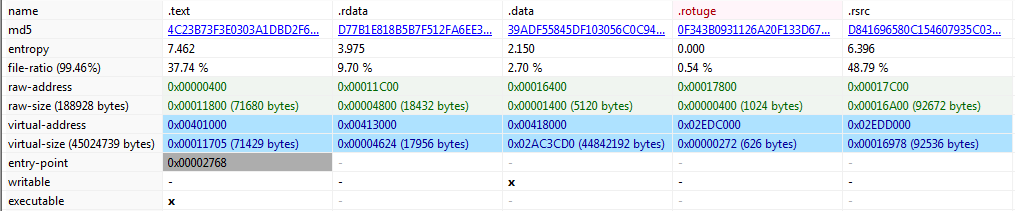
Figure2 above shows the sections present in our malware. All are looking quite normal imported by the malware except .rotuge section which is a suspicious ad when we checked it as shown in Figure3 given below. It is all empty which gives us an indication that may be used by malware later to store and access some code here.
Figure3:
Figure4: Libraries
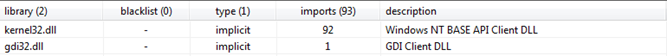
Figure4 above shows the libraries used by the malware, kernel32.dll used for core functionality such as access and manipulation of memory and gdi32.dll used for displaying and manipulating graphics.
Figure5: Imports/APIs
Figure5 shows above the APIs imported by the malware and indicates towards all the capabilities which we have mentioned earlier can be present int the SmokeLoader.
| Sr. No. | Tactics | Technique |
| 1 | Initial Access(TA0001) | Spam Emails |
| Spear Phishing | ||
| 2 | Execution(TA0002) | Shellcode |
| Scheduled Task | ||
| 3 | Persistence(TA0003) | Windows Registry Key/Startup Folder |
| 4 | Privelege Escalation(TA0004) | Windows Registry Key/Startup Folder |
| 5 | Evasion(TA0005) | Obfuscation |
| Process Injection/Process Hollowing | ||
| 6 | Credential Access (TA0006) | Credentials from Web Browsers & Files |
| 7 | Discovery(TA0007) | Files and Directories Discovery |
| 8 | Command & Control(TA0011) | Web Protocols |