


CYFIRMA’s cyber intelligence research centre have detected a suspected new ransomware campaign variant named ‘LetsDance’ targeting financial, retail, manufacturing and critical infrastructure companies. Our analysis highlights a North Korean threat actor group called TENJACKAL behind this campaign.
TENJACKAL is a financially motivated group first observed beginning of last year carrying out website defacement, malware and phishing campaigns in the United States, Brazil, Japan, Australia, Thailand and other South-East Asian countries. The members of the threat group are known to use existing malcodes, ransomware and malwares, repurposing them to create new attack strains.
We are seeing multiple Ransomware variants with a dramatic change in their attack nature and target selection, commodity ransomware campaigns are being replaced with customised campaigns targeting particular industries.
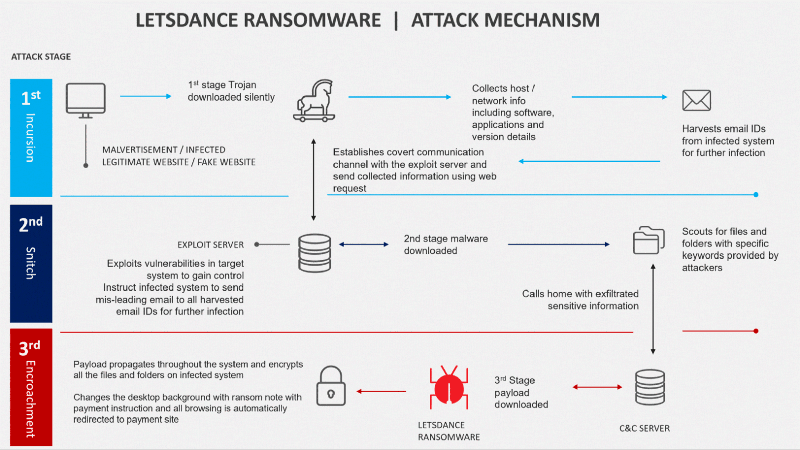
The LetsDance Ransomware uses a 3 stage attack technique called Incursion, Snitch and Encroachment (ISE Framework) to infect, propagate and demand pay.”
Spear-phishing, and the use of watering holes (fake websites) are predominant techniques used by LetsDance in the incursion stage of the attack.
LetsDance: 3 Stage Attack Tactic (Incursion, Snitch and Encroachment)

Attack Stage:
1 (Incursion): Attackers leverage a trojan designed to collect connected IT asset information (software, applications and version details)from the host network, and email IDs from the address book of the infected system. The malware is implanted on the targeted system when users are lured to visit a fake, infectious website via malvertisements or email invitation link to a user’s interest-specific website. Once the malware gets installed on the system, it communicates with the below command and control (C&C) servers for instructions and exfiltrates the information collected from the targeted entity.
Stage 1 malicious payload and C&C servers:
Malicious Payload:
9EC604D732759BB8B00312123AB262DD
C&C servers:
175.45.179.72
175.45.177.203
31.176.200.154
2.93.238.236
2 (Snitch): Collected system, applications and software details are analysed on the exploit server and based on potential vulnerabilities, the exploit attempts to gain access to the system. Parallel instructions are sent to the infected system to create and send misleading emails to all addresses from the stolen address book for further infection. A customized malicious payload is implanted onto the infected system to search all drives, directories, and subdirectories and then collects the file details and its attributes (size, extension, version, and specific strings such as “confidential”, “secret”, “sensitive”, “architecture”, “blueprint”, “usernames”, “passwords”, “credentials” etc.). This information is sent to another set of C&C servers for downloading customized encryption payload and webpage redirect malware onto the targeted system.
Stage 2 malicious payload and C&C servers
Malicious payload:
DC829558124F0E82CC7436BAD267A787
6B412B4CFA75F8DE31934F7AB653D36F
7CEDD997E8A9681A74D7F5ED46380D11
C&C servers:
199.16.146.87
175.45.177.109
175.45.177.35
2.93.238.98
175.45.177.101
2.93.238.209
3 (Encroachment): Once the encryption payload is downloaded onto the system, it encrypts all of the files and folders and changes the desktop background with a a message from the attackers.
Suspected encryption payload:
BCDEB71E0E6528311E63FCC3DFB44938
67989DFC5B16B52FD02BEBF25431AF09
BB6B7E38990C1549714E4FFC53622076
Along with the encryption payload, the C&C servers also drop a malicious program which redirects the user to a suspected webpage for payment.
Suspected webpage redirect malware:
F27A339786631136D2D5B5511A381E88
Strategic, Management and Tactical Recommendations:
Maintain multiple copies of data, files, folders to reduce the downtime in operations in case of a ransomware attack
Monitor or Block malicious malware files and C&C IPs via web proxy servers, AV solutions, firewalls, phishing controls and email gateways
Block IOCs (Indicators of Compromise) such as impersonating domains, malicious URLs, Host Names, IP Addresses, SHA fingerprint, Hashes under firewalls, proxies, end point, spam and phishing security control
Do not open emails from untrusted sources-Always verify sender email address before opening any emails coming from a source outside the organization.
Configure Anti-Virus/IDS (Intrusion Detection System) repositories with the identified hash signatures associated with the threat to protect all endpoints.
Build an APT-IR strategy, which is agile and proactive, keeping in mind business goals and priorities
Establish a Cybersecurity Awareness and Training (CSAT) Program and run regular checks, educate employees to download applications from trusted Appstore only.
Implement Network Segmentation-Limiting communication between services and systems on organization network level helps contain an infection and keeps a malware or a persistent threat from spreading.