



CYFIRMA Research team has seen an uptick in threat actor-orchestrated ransomware campaigns. We have reasons to believe that Prestige Ransomware has been used with notable features that differentiate it from other ransomware campaigns targeting transportation and other logistics industries in Ukraine and Poland.
In this report, CYFIRMA Research analysed a Prestige Ransomware sample which
In the analysis of the prevalent Prestige Ransomware sample taken from OSINT sources, the CYFIRMA Research team

Prestige Ransomware first appeared in the global external threat landscape in October 2022. The ransomware calls itself the “Prestige ranusomeware” in its note left on victim devices. The ransom note lists no specific sum of money expected by the hackers and simply provides an email that the victim can contact them and inquire about a decryption tool.
Researchers observed that the attacker had already gained access to privileged credentials from a prior compromise, for the targeted networks to deploy the ransomware. As of now, this campaign did not find any tangible connection to a known threat actor attempting to deploy ransomware into the networks of Ukrainian enterprises. Or, to any of the existing ransomware groups that may be related to earlier recent attacks conducted by Russia-linked threat actors.
Despite using similar deployment techniques, the campaign is distinct from recent destructive attacks leveraging AprilAxe (ArguePatch)/CaddyWiper or Foxblade (HermeticWiper) that have impacted multiple critical infrastructure organizations in Ukraine.
What we have observed in this and the previous campaigns:
File: sample.exe
Subsystem: Console
MD5: 8119c78b7cfb7d9ce37286ec9fc263e2
SHA1: 986ba7a5714ad5b0de0d040d1c066389bcb81a67
SHA256: 5fc44c7342b84f50f24758e39c8848b2f0991e8817ef5465844f5f2ff6085a57 File Type: PE32 Executable (Console) Intel 80386, For MS Windows
The file type of the Prestige Ransomware is a PE32 executable.

As we can observe, Prestige Ransomware is not packed.

As it can be observed, Prestige Ransomware is written in C/C++.

The string “Prestige.ranusomeware” present in the binary gives us a clear indication that it is prestige ransomware. As shown below.

To encrypt files, Prestige Ransomware leverages the following public key.


Using Blob Analyzer from CryptoTester, the public key was identified as RSA Key.

Prestige Ransomware leverages the Crypto++ library during the encryption of files.

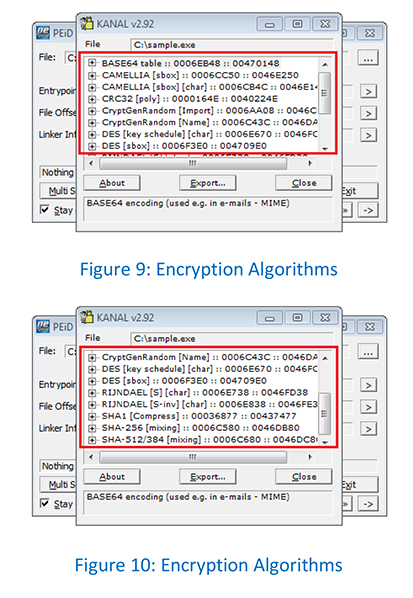
As it can be observed, Prestige Ransomware references multiple encryption algorithms such as AES and DES as shown below.
Prestige Ransomware traverses the directories, files, and processes to encrypt the content of files that have one of the hardcoded file extensions.
Prestige Ransomware enumerates through the directories and files through file APIs.


Prestige Ransomware uses reg.exe commands to register a custom file extension handler for files with .enc file extension.
C:\Windows\System32\reg.exe add HKCR\.enc /ve /t REG_SZ /d enc /f
C:\Windows\System32\reg.exe add HKCR\enc\shell\open\command /ve /t REG_SZ /d
“C:\Windows\Notepad.exe C:\Users\Public\README” /f

Prestige Ransomware attempts to stop the MSSQL Windows service before encrypting the files using the net.exe command.

Prestige Ransomware reads the files before encryption.

Handle to the file where encrypted data will be written.

Acquire the Crypto++ library as a container during the CryptAcquireContextA API call before the start of the encryption process.

Moves the file pointer of the specified file using SetFilePointerEx API.

Prestige Ransomware writes the encrypted data using WriteFile API.

After encrypting each file, the Prestige Ransomware appends the extension “.enc” to the existing extension of the file.

When a user tries to open encrypted files having file extension “.enc”, the custom file extension handler invokes Notepad to open C:\Users\Public\README which displays the ransom note “YOU PERSONAL FILES HAVE BEEN ENCRYPTED” describing what happened to the compromised system and includes an email address “[email protected]” to conduct ransom negotiations.

Prestige Ransomware encrypts files with below file extensions.


After running the Prestige Ransomware sample using OPNSense and two Win7 VMs network setup, Prestige Ransomware encrypted the files on the first machine but not infected other machines on the same network having access to shared folders.

As can be observed from the trace tool, Prestige Ransomware runs the below processes and creates new files, registry keys, and rename the encrypted files as shown below.
Processes: –
Process Created C:\Windows\SysWOW64\reg.exe
Process Created C:\Windows\SysWOW64\reg.exe
Process Created C:\Windows\SysWOW64\net.exe
Process Created C:\Windows\SysWOW64\net1.exe
Process Created C:\Windows\System32\wbadmin.exe
Process Created C:\Windows\System32\vssadmin.exe
Files: –
Create File C:\Users\Public\README C:\
Create File README
Registry Keys: –
Create Key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\enc
Create Key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\enc\shell
Create Key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\enc\shell\open
Create Key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\enc\shell\open\command
Rename Files: –
Rename File C:\BOOTSECT.BAK.enc

Operating System: Windows 7 Service Pack 1 [SP1] (64-Bit)
A memory dump (RAM dump) win7sp1x64.dmp was captured for memory analysis from the cuckoo sandbox on x64 Windows 7 SP1 system.
Prestige Ransomware runs the following command to delete the backup catalog from the system: –
C:\Windows\System32\wbadmin.exe delete catalog -quiet
Prestige Ransomware also runs the following command to delete volume shadow copies on the system: –
C:\Windows\System32\vssadmin.exe delete shadows /all /quiet
Below suspicious terminated and hidden processes are identified by psscan plugin among psxview results.

Threat actors behind ransomware attacks do not always have one goal of extorting money from victims.
As is the case with other ransomware, it might be inconclusive at this stage to assess the damage Prestige ransomware has caused. There is a significant uptick in discussions and mentions observed around Prestige ransomware which may mean that the infection footprint is sizeable and possibly continues to expand.
The activity observed around the sample analyzed shares victimology with recent Russian state-threat actor groups, in the targeted geographies, and in some cases overlaps with victims of HermeticWiper.
As the external threat landscape continues to evolve, wipers and destructive attacks not only in Ukraine but also in other geopolitically motivated attacks will continue to be a consistent component in such attacks.
| Sr.no | Tactics | Technique ID | Technique Name |
| 1 | 5fc44c7342b84f50f24758e39c8848b2f0991e8817ef5465844f5f2ff6085a57 | SHA-256 | sample.exe |
| Sr.no | Tactics | Technique ID |
| 1 | TA0002: Execution | T1059: Command and Scripting Interpreter T1106: Native API |
| 2 | TA0003: Persistence | T1053: Scheduled Task/Job |
| 3 | TA0005: Defense Evasion | T1112: Modify Registry T1497: Virtualization/Sandbox Evasion T1070.004: Indicator Removal on Host: File Deletion |
| 4 | TA0007: Discovery | T1012: Query Registry T1057: Process Discovery T1082: System Information Discovery T1518.001: Software Discovery: Security Software Discovery T1083: File and Directory Discovery |
| 5 | TA0040: Impact | T1486: Data Encrypted for Impact T1490: Inhibit System Recovery T1489: Service Stop |