


Mirai is a self-propagating botnet malware created by Paras Jha and his friends Josiah White and Dalton Norman. Their operation was aimed almost exclusively at Minecraft servers and other gaming services. Yet, due to its massive firepower, it managed to take down parts of core network infrastructures during its attacks, wreaking mayhem around the globe.
It wasn’t the first malware targeting IoT devices and connecting them to a malicious botnet. It was, however, the first to do it in a highly efficient way, causing high-profile incidents and even sparking fear of nation-state cyber assault. The original Mirai was consistently tweaked to compete with its “DDoS-as-a-Service” provider rival vDOS and their Gafgyt botnet.
After its rapid growth period in late 2016, Mirai managed to keep 200,000 – 300,000 enslaved devices and peaked at an unbelievable 600,000. To put these numbers in perspective, until Mirai, the average DDoS was 10-20 Gbps and 50 Gbps was considered massive. FBI special agents compared Mirai’s 1+ Tbps (1,000 Gbps) to Project Manhattan, where scientists working on the first nuclear bombs had no idea how much firepower they have created until they used it. Following up on this comparison, publishing the source code of Mirai was like sharing a nuclear bomb blueprint in the newspapers.
Unlike nuclear bomb blueprints though, Mirai’s source code was very simple. A multitude of dangerous actors immediately picked it up. They quickly spawned countless increasingly more potent variants aiming at a wider range of IoT devices and doing a range of specific things, including mining cryptocurrencies on NAS to hosting malicious proxies or gaining initial access for cybercriminals.
In the mid-2010s, Paras Jha, an undergraduate student at Rutgers University, was exploring DDoS attacks and emerging IoT devices while looking to make a quick buck. Most likely inspired by future rival vDOS – DDoS-as-a-Service provider, he eventually came up with the idea to sell DDoS mitigation to his own University while attacking it during important events, using old and proven mafia racketeering techniques in cyberspace. Expanding on this idea and being an avid Minecraft player, he started using DDoS to make money by taking down rival servers and then selling DDoS mitigation. For context, Minecraft had 55 million active monthly players at the time and successful server operators were making over $100,000 per month. Meaning that there was a lot of money to be made, which unsurprisingly sparked a DDoS arms race between Mirai and their rival vDOS.
Before the first big DDoS attack publicly attributed to Mirai there were countless, likely thousands of unreported attacks on Minecraft and other gaming servers, including Runescape or Steam. Most of the servers were run by teenagers and young adults who never bothered to report it and considered a problem solved after DDoS mitigation was bought from the very same people who attacked them in the first place.
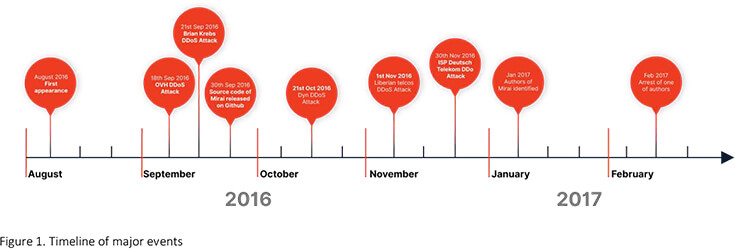
The first Mirai incident was reported after the 18th Sep 2016 attack against popular Minecraft servers hosted on French service OVH. As part of the Minecraft server hosting package, OVH also offered DDoS protection. And when they became a target, this DDoS protection was under attack and obliterated by Mirai’s unprecedented combined 1 Tbps DDoS assault consisting of 145,000 compromised IoT devices. Herein, one of the attacks alone peaked near 800 Gbps!
A few days later, cybersecurity journalist Brian Krebs and his website krebsonsecurity.com were hit by a 620 Gbps DDoS attack. This attack came after they published an article about vDOS operations, and it remains unclear how much involvement was there from vDOS or Mirai or both and more. The important takeaway was that Akamai – one of the biggest bandwidth and DDoS mitigation providers – was forced to give up pro-bono defense of Krebs’ website. Akamai stated that this attack was twice the size of the largest attack they had observed (Spamhaus ~300Gbps) while also sustaining for a long time. It would cost millions of dollars and impact paying customers of Akamai to defend against such sustained traffic.
The OVH attack was from the USA’s perspective a foreign event, but the attack on Brian Krebs quickly made waves and alerted US law enforcement and the cybersecurity community thereby giving Paras Jha and his friends some unwanted attention.
In response and in an attempt to hide their tracks, the perpetrators released source code for their IoT botnet under the pseudonym Anna-Senpai (a character from the anime Shimoneta) and named it Mirai – translating to “Future”. The inspiration for this came from the popular 2000s manga and anime series “Mirai Nikki” – “Future Diaries”. Creative inspirations aside, sharing source code is common practice as it in theory provides plausible deniability.
With the unprecedented firepower and the fact that Mirai was taking down internet core infrastructure along with its intended targets, experts everywhere were spinning theories about possible hostile nation-state assaults that were about to take place. It all came at an unfortunate time around the 2016 US presidential election. It was rumored that Russians were involved as they were reportedly actively meddling with elections, so naturally, the FBI scrambled to investigate and stop these DDoS attacks.
Attacks that came later and after the publishing of source code did not help the case. Namely, the now infamous attack against Dyn DNS service. The latter was never able to calculate the full scope of the attack, but reports estimate up to 1.2 Tbps. With a significant portion of the internet unable to translate domains into IP addresses, millions of computers and services like Amazon, Netflix, and PayPal stopped working. This attack was later attributed to a clone of Mirai based on published source code and nobody was officially charged and convicted for it.
Another incident effectively took down the internet in the entire country of Liberia and yet another misconfigured Mirai clone took out 900,000 routers of Deutsche Telekom in Germany significantly disrupting their service.
Thanks to how Mirai worked, an increasing number of clones and spin-offs started to delete each other from infected devices, leading to more and more fragmented botnets capable of lower and lower volumes of DDoS attacks. Effectively rendering itself unable to sustain its operations as a DDoS-as-a-Service business.
The original authors of Mirai were eventually identified, arrested in 2017, and sentenced. That spelled the end of the original Mirai. Its legacy lives on through countless clones and spin-offs that are more active and dangerous than ever.
Since the original Mirai is old news, there is little reason to do any in-depth analysis of its samples again. At the same time, its core functions are still relevant in many present-day variants.
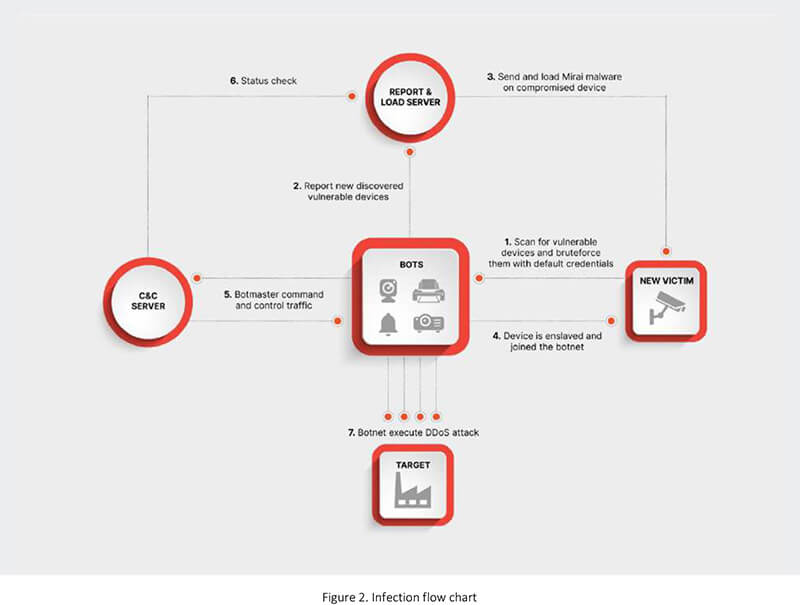
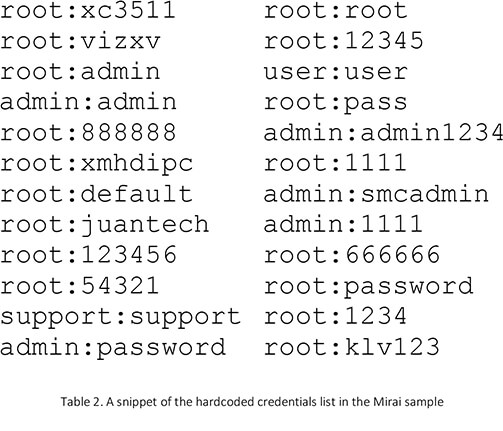
Mirai initially aimed at IP cameras and DVR on telnet ports, but when it entered its rapid growth period during September 2016, hardcoded credentials also contained VOIP phones, Xerox printers, network routers, and a lot more protocols. Apart from HTTP/HTTPS and FTP, the main booster for growth was the addition of TCP ports 7547 and 5555 used by CWMP (CPE WAN Management Protocol). As per the table below, CWMP grew to be the most significant chunk of Mirai while accounting for nearly a third of all devices.

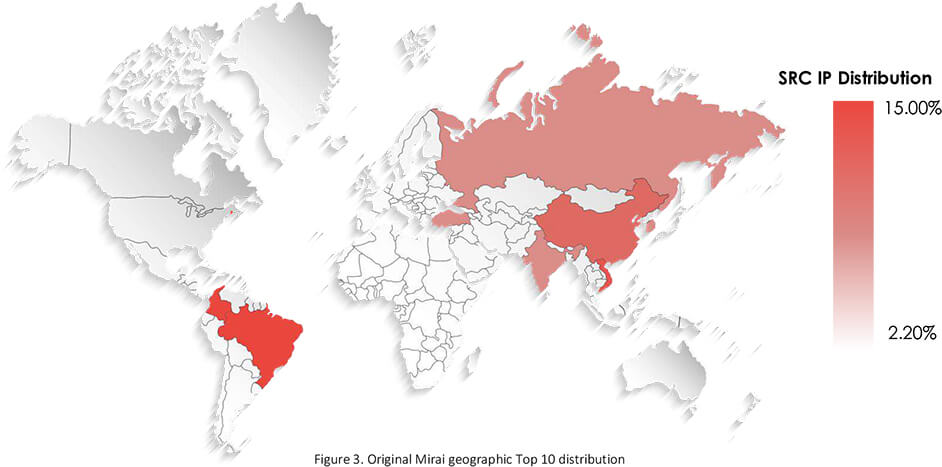
Notable are locations of enslaved devices. Typically we see that most of the attacked devices are located in the USA and EU countries as threat actors are seeking high-value targets. The original Mirai however had large chunks of its botnet in Southeast Asia and South America, with the USA not even making the Top 10. There are two reasons for this; one is the intent to go for mass rather than value (quantity over quality), and the second is cheap and knock-off device volume in Southeast Asian and South American markets.
When we look at the more recent distribution of modern variants of Mirai, we can see that it is a lot closer to the typical pattern. This can be explained by a change of motivation by threat actors operating these botnets – seeking high-value targets for cybercrime operations.
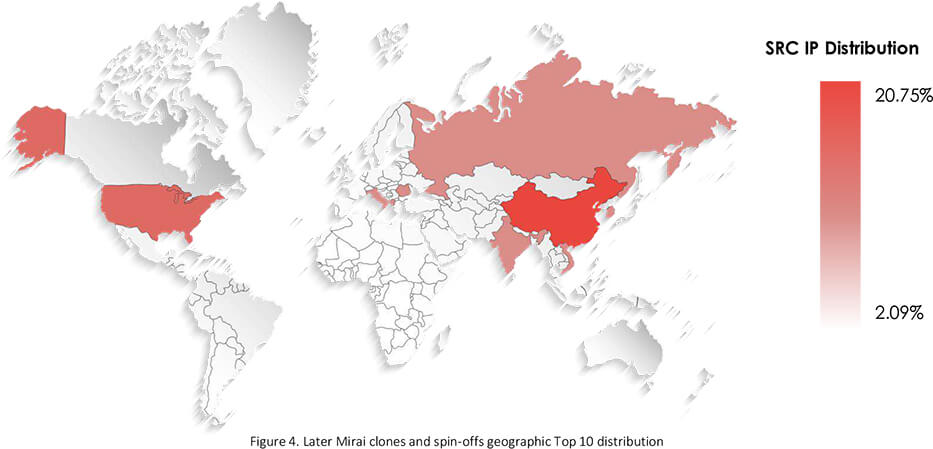
For specific devices and manufacturers, it is unfair to point out those which happened to be identified by unique default credentials, since about 80-90% of all enslaved devices were unknown and infected through generic default credentials.
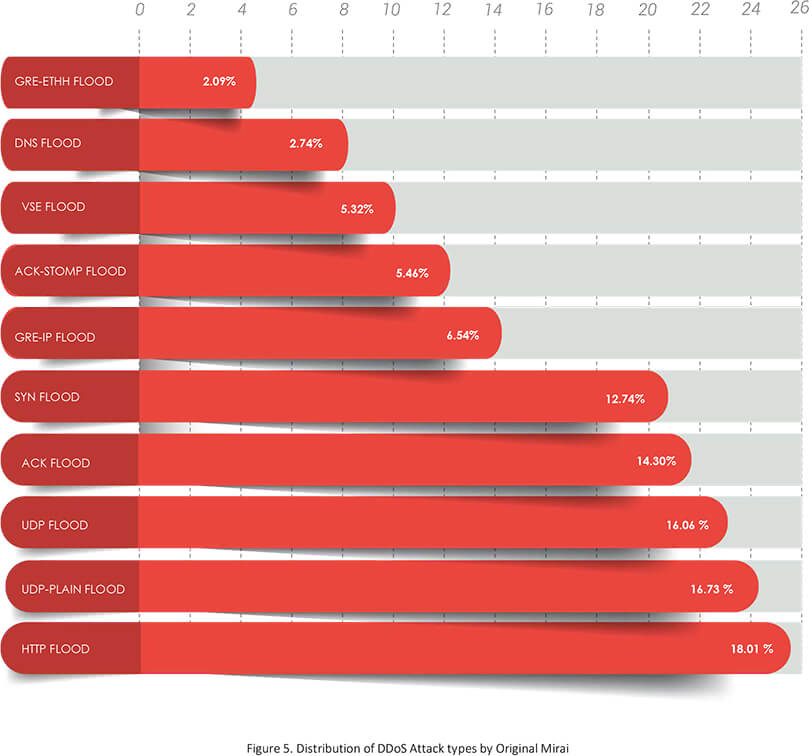
During late 2016 and early 2017, the original Mirai with its early clones launched approximately 20,000 DDoS attacks. About 80% of these attacks were common and simple types of flood attacks. Thanks to the massive firepower, attackers had little need to use or invent any sophisticated methods.
Even though the original Mirai and its authors ceased operation after their arrest in late 2017, their code still lives today. From the first blatant copies after public source code release to the latest iterations exploiting major vulnerabilities like log4shell or spring4shell, Mirai is going strong.
Listed below are some notable variants throughout the years. Particularly interesting is the late 2021 adoption of Mirai’s code into Gafgyt, which was around since 2014. Gafgyt likely served as inspiration for Paras Jha to dip into the DDoS racketeering business and was the botnet of vDOS – Mirai’s main competitor sparking the DDoS arms race to seize the booming DDoS-asa-Service market. If these weren’t malicious actors, it would be a wholesome full-circle story,
OWARI, an updated version of the Mirai botnet, surfaced sometime at the end of 2017. OWARI retained the default password technique to propagate the victim device and added a few exploit scanners like CVE-2017–17215 Huawei exploit as telnet devices were over abused and the default password attack was not yielding the good results. This enabled the botmaster to compromise the devices faster as the IoT attack space got crowded with the release of Mirai’s source code. Money and fun are two elements that drove the botnet author in the OWARI case. The Stresser as a Service model is used for monetary gain. Bot killer module was also introduced in OWARI to kill existing malware on the device, and then run a copy of its own.
This botnet is named OMG because of a string containing “OOMGA” in its configuration table. The OMG bot comes with HTTP and SOCKS proxy capabilities. OMG retained Mirai’s modules of attack, killer, and scanner and also included two strings to generate two random ports for the http_proxy_port and socks_proxy_port, reports them to the C&C, and adds a firewall rule to allow traffic on these ports. Open-source software 3proxy is used as a proxy server in OMG.
The SYLVEON botnet emerged in June 2019 and the author announced through a post on his Twitter account that he was going to abandon the project at the end of June 2019, but the botnet continues to exist. SYLVEON is a conventional IoT malware that was clearly based on the Mirai source code with some added attacks. Like the typical Mirai, SYLVEON was seen as exploiting TCP/23, and TCP/2323 ports. SYLVEON variant is seen as the most common infection in Taiwan.
Mukashi, a new variant of Mirai, uses brute-force attacks to log into Zyxel NAS, UTM, ATP, and VPN firewall products to take control of the devices and add them to a network of infected bots that can be used to carry out Distributed Denial of Service (DDoS) attacks. A preauthentication command injection vulnerability (CVE-2020-9054), which resides in a “web login.cgi” program used by the Zyxel devices, is potentially allowing attackers to perform remote code execution via command injection. Mukashi, like Mirai, searches the Internet for vulnerable IoT devices such as routers, NAS devices, security cameras, and digital video recorders (DVRs), while looking for potentialhosts that are only protected by factory-default credentials or commonly used passwords to include them in the botnet.
Gafgyt, a Linux-based IoT botnet that was discovered in 2014 and was used by the vDOS group, the main competition of Mirai. Mirai source code was discovered to be reused in Gafgyt in April 2021. Mirai-based modules are used in five different areas of Gafgyt, including HTTP flooding, UDP flooding, TCP flooding, STD module, and Telnet Brute-force. Gafgyt primarily targets vulnerable IoT devices, particularly Huawei routers, Realtek routers, and ASUS devices. It also frequently exploits known vulnerabilities like CVE-2017-17215 and CVE-2018- 10561 to deliver next-stage payloads to infected devices.
BotenaGo malware is written in Google’s Golang programming language and exploits the 19412-networking port or related modules’ backdoor vulnerability in IoT. BotenaGo malware made use of some Mirai techniques. An examination of the BotenaGo sample revealed that the same technique used in Mirai to brute-force authentication using a list of hardcoded credentials was used in BotenaGo. Many of the credentials retrieved from the BotenaGo scanning module correspond to those hardcoded in the Mirai source code. Another behavior associated with the Mirai botnet is that the same list of exclusion IPs from Mirai was used in the Botenago scanning procedure.
Enemybot attributed itself to Keksec, a threat group specializing in crypto mining and DDoS attacks, and is built on Gafgyt’s source code and several modules from Mirai’s original source code. Changes in encoding in recent samples indicate that the malware is actively developed/improved. The scanner module, killer module, and weak or default credentials were the three main modules observed in Enemybot from Mirai’s original source code. Enemybot improved the keyword list in the killer module to include more than 60 keywords to eliminate any competitors running on the target devices.
Mirai botnet revolutionized IoT malware with a very simple, yet brilliant approach to the infection chain. It was so successful and powerful that in the end, it became its own victim. Such massive firepower took down more than just the intended targets. This alerted the FBI who were wary of any potential hostile nation-state cyber assault leading to the fast arrest of Mirai’s authors. Further, after publishing the source code, the malware’s own feature of killing any other malware on compromised devices led to fragmentation where nobody was able to sustain a large enough botnet to keep the DDoSas-a-Service business sustainable.
However, through innovation and change in the botnet’s goals, such as cryptocurrency mining, Mirai’s code keeps on living and prospering with a bright future in sight. While traditional IT devices and infrastructure are more secure than ever, with every vendor making the security of their products a priority, IoT is still years behind. Many, mainly low-cost manufacturers, simply copy and stitch together various open-source codes to make their devices work. A lot of these open-source codes are not maintained and major vulnerabilities are discovered every year. At the same time, manufacturers often do not provide any updates to patch these vulnerabilities and they go unpatched for years or even decades for the entire life of the device. As an example, just log4shell alone is going to haunt IoT devices for years to come.