To proactively identify exposed external assets, shadow IT, Misconfigurations, certificates and forgotten systems that can be exploited by cyber criminals.

Uncover attack surfaces including open ports, weak certificates, Hardware / software misconfigurations, cloud weakness and exposure from third party connections.

24/7 monitoring is needed to detect new attack surfaces as and when they occur.

Gain visibility of your external facing assets which can be exploited by cyber criminals. Insights can be used to shrink your attack surface to reduce the mitigate risk.
By combining cyber-intelligence with attack surface discovery and digital risk protection, CYFIRMA delivers predictive, personalized, contextual, outside-in and multi-layered insights to help clients prepare against upcoming attacks.
Navigating the fog of cyberwar and delivering intelligence around emerging threats should not only be restricted to government organizations. Enterprises should also have access to military-grade intelligence, tuned to meet their commercial needs. Meet DeCYFIR – predictive and actionable intelligence for companies to stay ahead of adversarial forces.
Real-time continuous monitoring to identify shadow IT or porous systems which can be accessed by cybercriminals.
Learn MoreTrack, monitor, analyze. Decode threats heading your way with cyber-intelligence gathered just for you
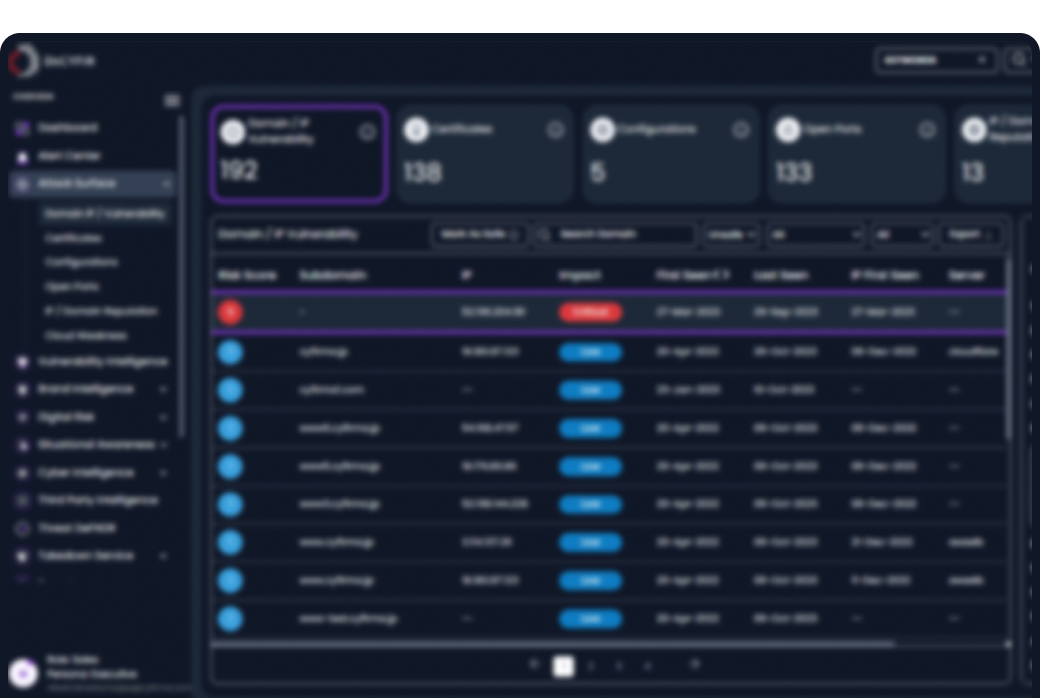
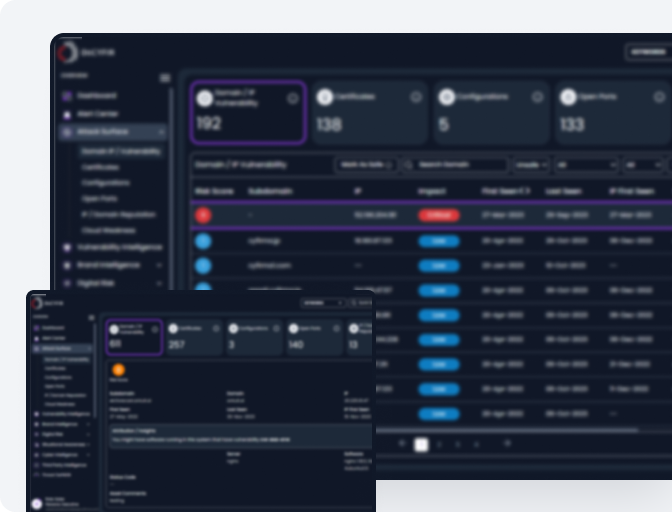
Your organization’s domains and IP addresses are prime real estate on the internet — and among the first targets adversaries scan for weaknesses. Exposed services, outdated software, misconfigured DNS records, or forgotten subdomains can provide an easy entry point for threat actors.
Digital certificates like SSL/TLS are vital for secure online communication, but if misconfigured or expired, they can expose organizations to risk. DeCYFIR, CYFIRMA’s threat landscape platform, provides visibility and control over certificates through its Attack Surface Intelligence, helping prevent such exposures.
Unlike traditional scanners, DeCYFIR doesn’t just flag misconfigurations, it adds contextual intelligence by mapping findings to real-world threats, adversary behaviors, and external risk indicators. This allows your security and operations teams to act on what matters most.
Open ports enable communication but, if exposed or misconfigured, can be exploited by attackers. DeCYFIR offers continuous visibility into exposed ports, helping security teams detect and remediate risks before they’re used in cyberattacks.
DeCYFIR continuously monitors the reputation of your domains and IP addresses across global threat intelligence feeds, blacklists, and adversary infrastructure databases. It provides real-time alerts, contextual insights, and remediation guidance, helping you maintain operational continuity, safeguard brand credibility, and prevent abuse of your digital assets all as part of a unified, intelligence-led attack surface management strategy.
Cloud environments offer agility but often expose misconfigurations, insecure APIs, and over-permissioned identities, creating risks. DeCYFIR continuously monitors cloud assets, correlates findings with threat intelligence, and delivers contextual insights to help security teams proactively harden cloud posture and reduce risk.
CYFIRMA is proud to be recognized by some of the most important and influential publications and organizations around the world.
DeCYFIR, continuously discovers and monitors login pages across your digital footprint, correlating exposures with active threat campaigns and attacker behaviors. It delivers contextual intelligence, prioritizes high-risk interfaces, and helps proactively secure access points to reduce the risk of compromise.
Get started