


The Android application Hicas, publicly advertised as a Smart Travel Packing Companion, was found to operate as a region-targeted fraudulent loan platform linked to a Chinese-operated digital loan ecosystem. While the application presents legitimate travel-related functionality to non-Indian users, it dynamically switches behavior on Indian devices, delivering a fully web-based loan workflow designed to coerce repayments through deceptive UI elements and aggressive psychological pressure.
The app has reportedly achieved over 500,000 downloads, indicating a significant reach and potential impact.
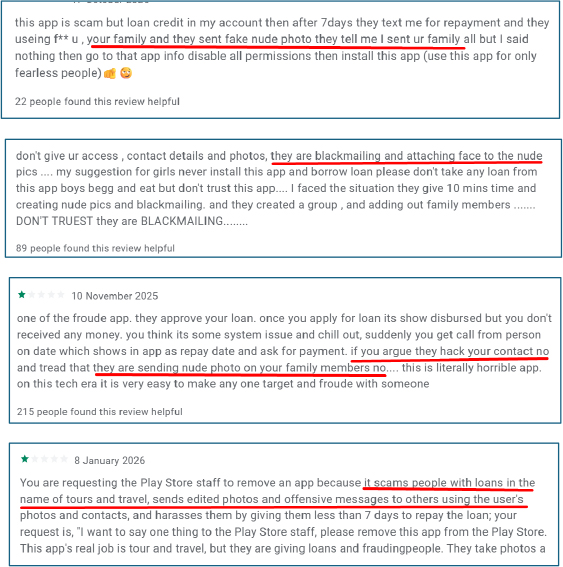
Static and dynamic analysis confirm that the application deliberately conceals its true functionality through heavy obfuscation, runtime string decryption, and remote configuration-driven logic, allowing operators to alter behavior post-installation without publishing application updates. The observed behavior closely aligns with user complaints alleging harassment, unauthorized data access, and exploitative lending practices commonly associated with Chinese-driven illegal loan applications operating in India.
This analysis examines an Android application identified as Hicas, available on the Google Play Store under the package name com.apptool.hicash.newhicash. Despite its public branding as a travel utility, evidence indicates that the application is intentionally misrepresented and functions as a loan scam platform targeting Indian users.
The investigation includes static code analysis, runtime behavior inspection, network traffic capture, asset inspection, and infrastructure attribution.
The application is listed on the Google Play Store as a travel utility, claiming to help users create and manage luggage checklists for trips. According to the store description and promotional screenshots, users can:
At the time of analysis, the application reports 500,000+ downloads and remains actively listed on the Play Store.
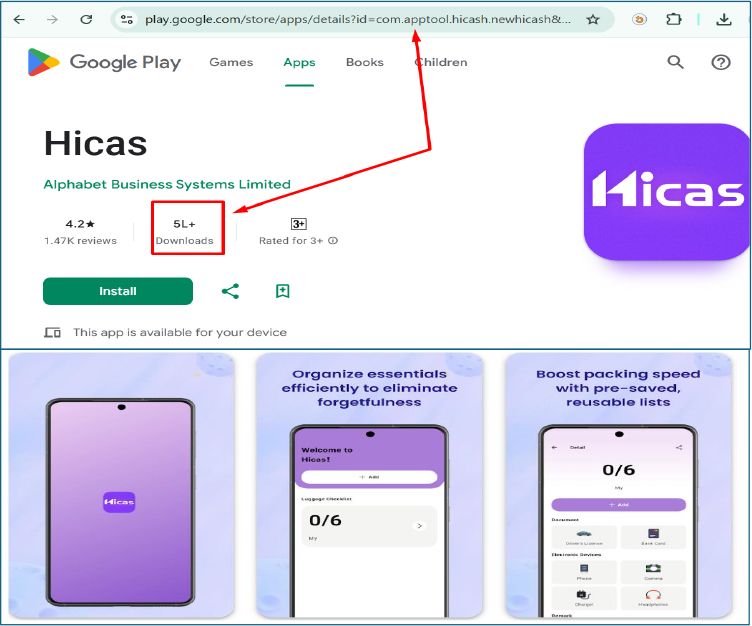
Developer Information
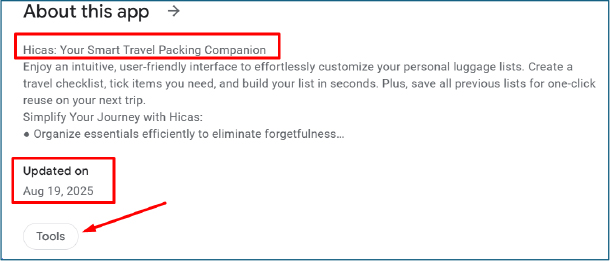
User Complaints and Abuse Indicators
User reviews consistently allege that the application operates as a fraudulent loan platform disguised as a travel utility. Complaints include false loan disbursement claims, unauthorized access to contacts and photos, image morphing for blackmail, aggressive harassment, excessive interest rates, and coercive repayment practices.
Region-Based Behavioral Switching
When the app detects non-Indian devices, the application behaves as advertised, providing travel-related features such as luggage list creation and trip planning. However, on devices identified as Indian, the application bypasses its stated functionality and instead presents a loan workflow, including login and borrowing features, indicating region-based dynamic behavior switching.
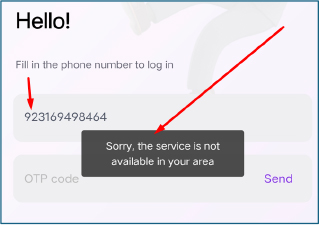
Further analysis shows that when a non-Indian country code with a random phone number is entered, the application displays a toast message stating, “Sorry, the service is not available in your area.” While the application claims to be a tour and travel utility, this country-specific restriction is inconsistent with its stated purpose. The behavior indicates intentional limitation of functionality to Indian users, supporting evidence of deliberate targeting for loan-based fraudulent activity.
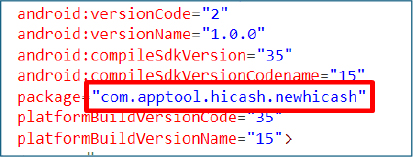
The application is packaged under the identifier com.apptool.hicash.newhicash, which does not align with the advertised application name “Hicas” or its claimed travel-related functionality. Additionally, the app targets SDK version 35, indicating compatibility with the latest Android releases, a choice that appears deliberate to ensure broader device coverage and reduced detection on modern platforms.
Permissions
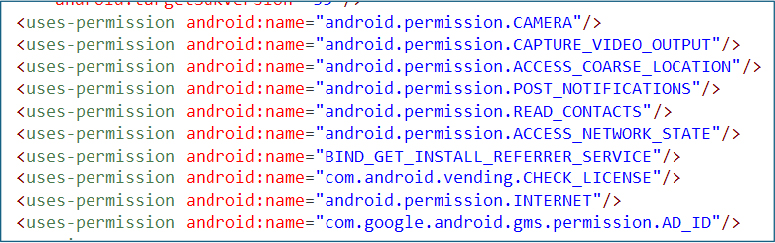
The application requests several high-risk permissions that are unnecessary for a legitimate travel or luggage-planning utility. These include access to the camera, contacts, location, and notifications, along with continuous internet and network state access. Such permissions are consistent with data collection, user surveillance, and potential abuse rather than basic tour and travel functionality, raising concerns about misuse aligned with reported harassment and loan-scam behavior.
Obfuscation and Code Protection
The smali code reveals extensive and aggressive obfuscation. Class and package names are composed of seemingly random characters, offering no semantic meaning. This level of obfuscation is indicative of an intentionally protected build, commonly used to conceal malicious logic and hinder reverse engineering, as well as to evade security tools and signature-based detection mechanisms.
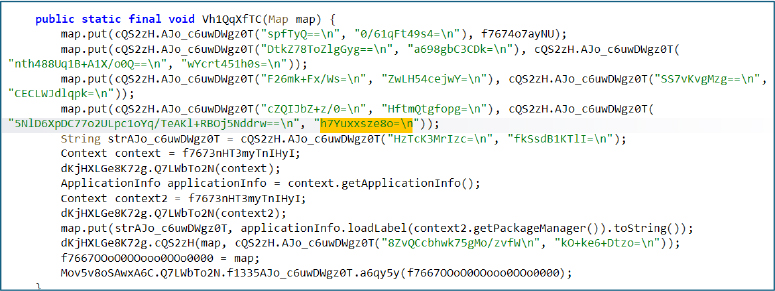
The decompiled APK code demonstrates the application’s heavy use of string encryption and obfuscation. Sensitive values are dynamically resolved at runtime through custom decoding functions, while method and variable names are nonsensical and randomly generated. This approach prevents straightforward static analysis and strongly indicates intentional efforts to conceal underlying logic and evade detection mechanisms.
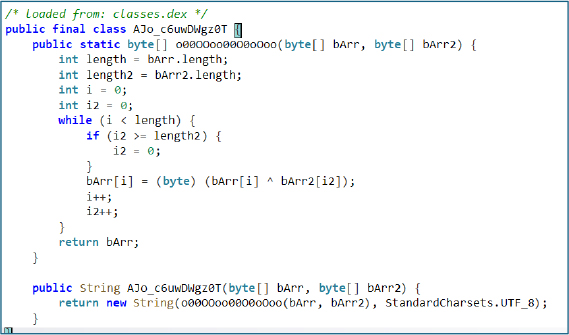
The class responsible for runtime string decryption, identified as Ajo_c6uwDWgz0T, shows that it implements a simple XOR-based decryption routine. The method iterates over encrypted byte arrays and applies a repeating XOR key to reconstruct plaintext strings at runtime. This confirms the use of basic XOR encryption to conceal string literals and evade static analysis.
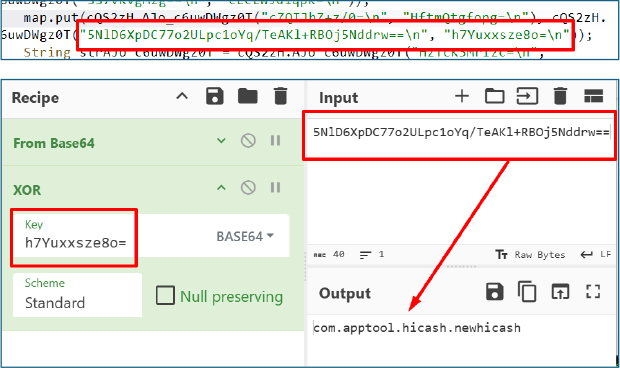
The first parameter represents the encrypted content to be decrypted, while the second parameter serves as the secret key used for the XOR operation. Using the same key, the encrypted strings can be successfully decoded, confirming consistent reuse of the key across the application for string obfuscation.
Since each string of every class uses a different secret key for string decryption, manual decoding becomes highly time-consuming and impractical. To address this, we developed a program that recursively scans all smali files, identifies encrypted strings and their corresponding keys, and automatically decodes them, enabling efficient large-scale string recovery across the codebase.
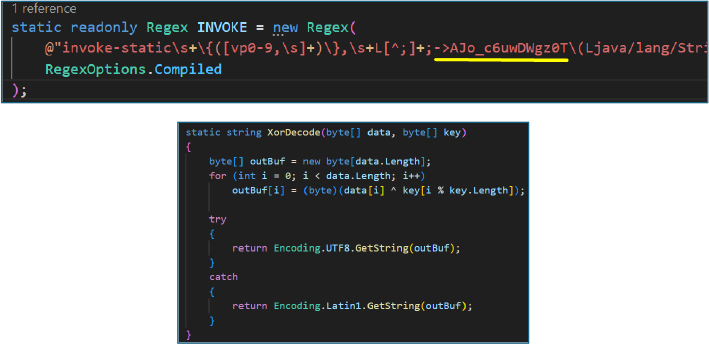
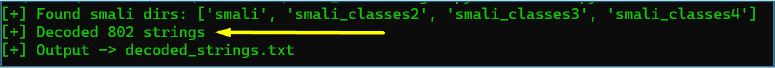
Using the automated decoding approach, a total of 802 encrypted strings were successfully identified and decrypted across the application codebase.
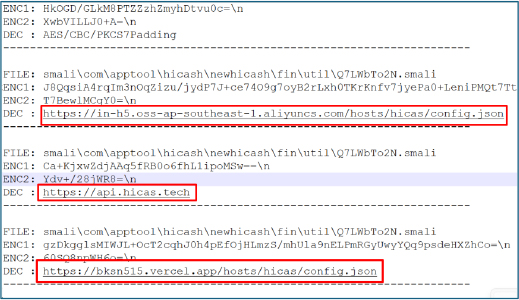
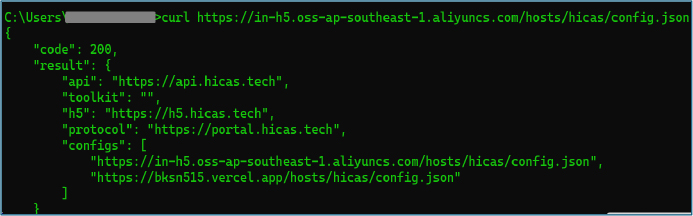
The decoded strings exposed the application’s primary malicious behavior. It shows that the app dynamically loads a WebView by querying a remote configuration hosted at in-h5.oss-ap-southeast-1.aliyuncs.com/hosts/hicas/config.json, with a fallback endpoint at bksn515.vercel.app/hosts/hicas/config.json. This remote configuration controls the app’s runtime behavior and content delivery.
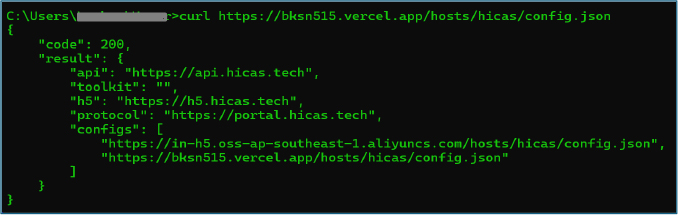
Querying the configuration endpoint returns a JSON response containing multiple runtime parameters, including API endpoints, H5 URLs, and protocol definitions. Analysis of both configuration URLs shows that they return identical JSON data, indicating redundant hosting of the same remote configuration used to control application behavior dynamically.
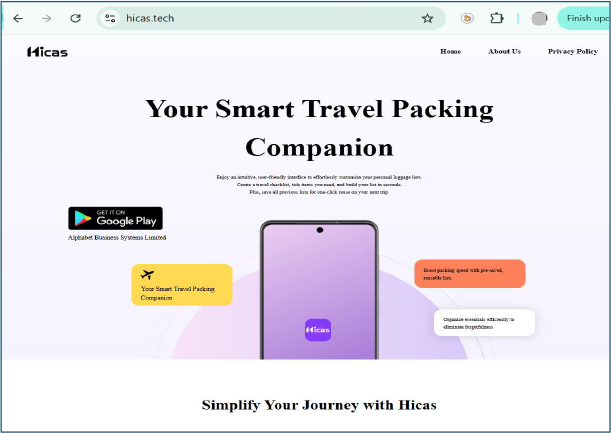
The official website associated with the application explicitly markets Hicas as a travel-related product. The site promotes the app as a “Smart Travel Packing Companion” and focuses solely on tour and travel use cases. No references to lending, financial services, or loan-related functionality are disclosed, further highlighting the discrepancy between the app’s public claims and its observed in-app behavior.
Domain Analysis
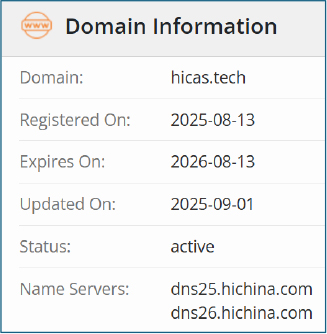
WHOIS data of the domain hicas.tech was created on August 13, 2025, updated on September 1, 2025, and is valid until August 13, 2026.
Remote Push Notification
By leveraging the Firebase Cloud Messaging service push notifications can be remotely controlled by the backend and abused to trigger additional actions within the application, including loading new malicious content via WebView or redirecting users to externally hosted payloads. This capability enables the operator to dynamically alter behavior post-installation and potentially deploy further malware without requiring an application update.
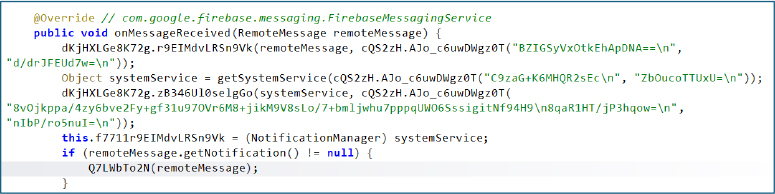
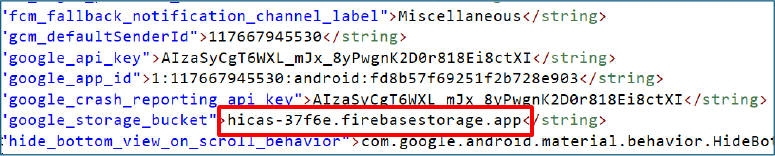
At the time of analysis, the Firebase Storage endpoint hicas-37f6e.firebasestorage.app was found to be inactive. However, this does not indicate permanent decommissioning. The infrastructure can be reactivated at any time, allowing the operators to resume real-time push notifications and potentially extend the attack chain by delivering additional malicious content or commands dynamically.
Contacts Harvesting
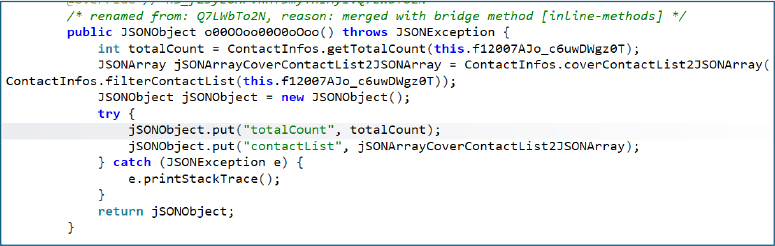
The below shows explicit functionality for contact harvesting. The method collects the total number of contacts from the device, processes the contact list, and serializes the data into a JSON object containing both the contact count and detailed contact entries. This structured output is indicative of intentional contact enumeration and packaging, likely for transmission to a remote backend, aligning with user reports of contact misuse and harassment.
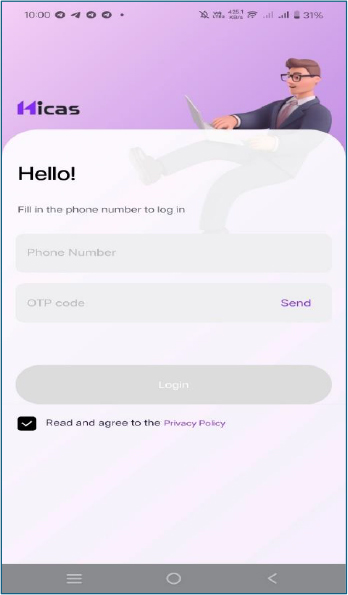
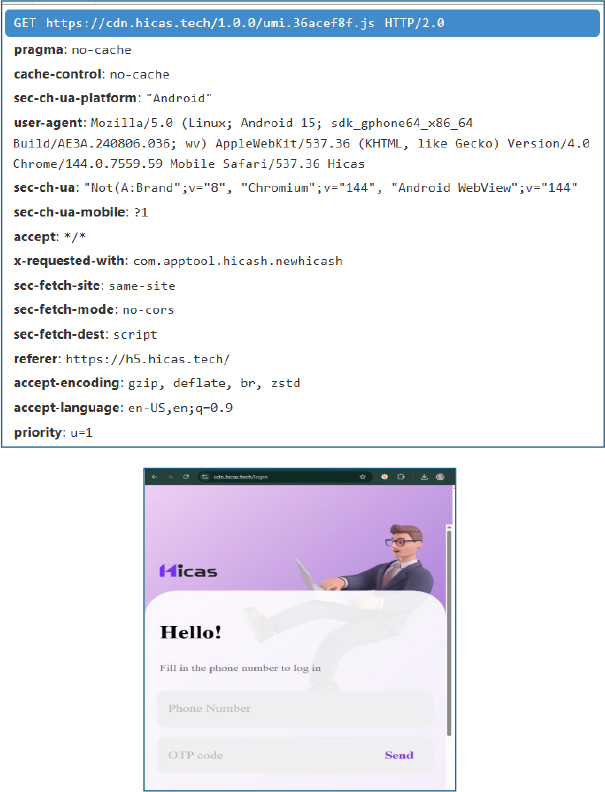
Upon launching the application, it immediately presents a login screen, rather than any travel or luggage-planning functionality, indicating that access is gated behind an account-based workflow aligned with the loan process.
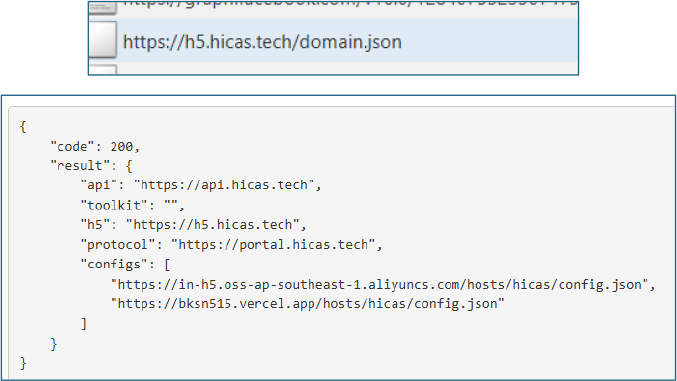
The application issues a GET request to https://h5.hicas.tech/domain.json to retrieve additional runtime configuration. The response provides further endpoint definitions, including WebView and API URLs, which are subsequently used to dynamically control in-app content and backend communication. This reinforces the application’s reliance on remote configuration to alter behavior post-installation.
At the same time, the application loads a dynamic WebView from cdn.hicas.tech and fetches UI resources such as JavaScript, CSS, and images at runtime. The requests include a custom header containing the application package name, which appears to be intentionally added to restrict access and hinder external analysis. This mechanism complicates API inspection and limits visibility into the delivered content, allowing the operators to tightly control and modify the interface served to infected devices.
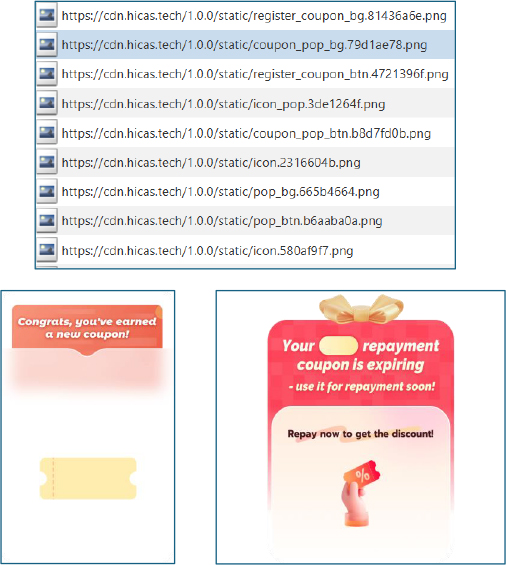
The remotely loaded assets further confirm the loan-focused functionality. The application dynamically retrieves multiple UI resources from cdn.hicas.tech, including images and banners explicitly labeled for repayment, coupons, and discount-driven prompts such as “Repay Now” and “Your repayment coupon is expiring.” These visual elements are designed to create urgency and pressure users into immediate repayment, reinforcing the coercive loan workflow delivered entirely through the remote WebView rather than any travel-related feature set.
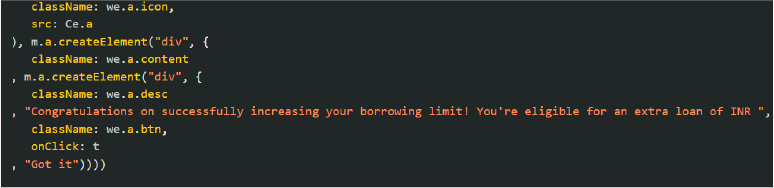
Inspection of the dynamically loaded JavaScript reveals explicit loan-related messaging embedded within the WebView content. The UI logic displays prompts such as “Congratulations on successfully increasing your borrowing limit! You’re eligible for an extra loan of INR …”, along with interactive buttons to proceed. This confirms that the remotely served WebView content is directly used to drive loan offers and user coercion, rather than any travel-related functionality claimed by the application.
This loan application is actively promoted on social media platforms, including YouTube, where promotional videos demonstrate how to obtain a loan while emphasizing quick approval, easy repayment, and low interest rates. The advertisements claim loan amounts of up to INR 120,000 with disbursement purportedly completed within three minutes, which contrasts sharply with the application’s observed behavior and reported user experiences.
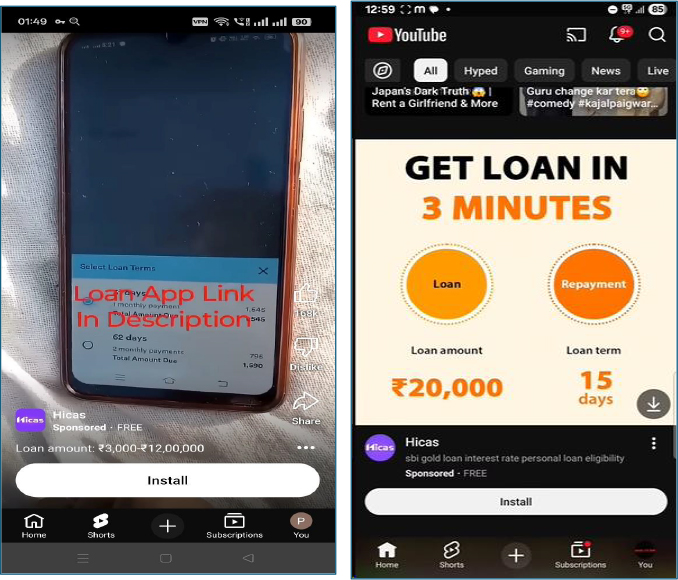
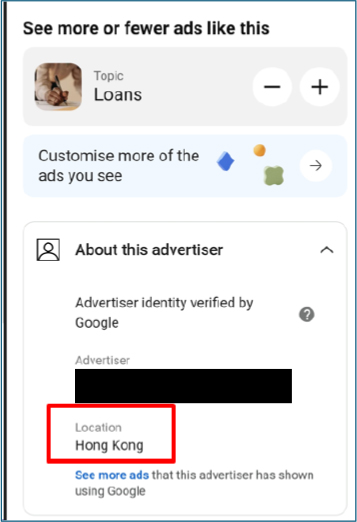
The associated advertisements shows that the ad campaigns are attributed to an advertiser registered in Hong Kong, as indicated by the advertiser identity details. This offshore ad origin, combined with the application’s India-specific loan targeting, suggests a cross-border operation leveraging social media advertising to lure Indian users into the loan scam ecosystem.
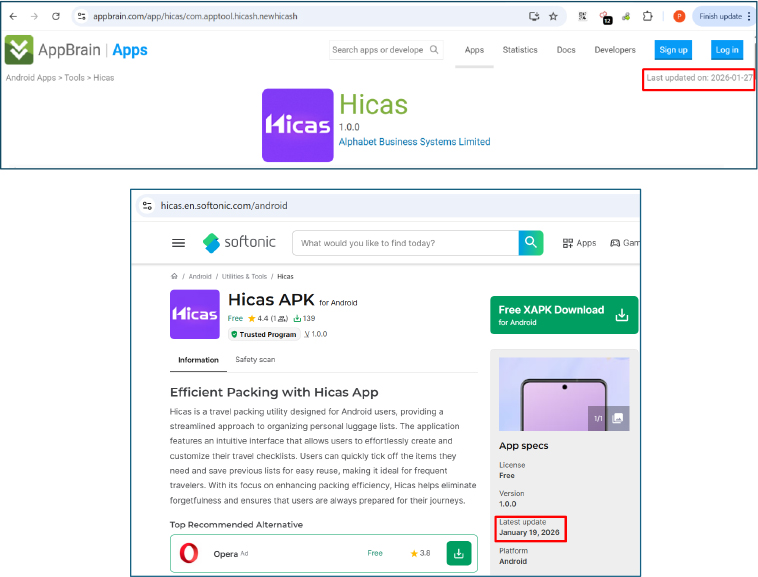
Analysis of open-source intelligence and third-party application marketplaces indicates that the developer is actively promoting and distributing the Hicas APK across multiple external platforms beyond the official app ecosystem. Screenshots reveal the application being hosted and updated on widely accessed APK aggregation and software distribution websites, such as Softonic and AppBrain, with clearly visible “latest update” timestamps. This multi-platform presence increases the application’s visibility and reach, enabling broader user acquisition outside controlled app store environments. By maintaining frequent updates and consistent versioning across these platforms, the developer leverages trusted download portals to build perceived legitimacy, thereby increasing the likelihood of user installation and reducing initial suspicion among potential victims.
The analysis confirms that the application operates in a manner inconsistent with its public description and declared purpose. Although presented as a travel and utility application on the Google Play Store, the app dynamically delivers a loan-focused workflow to targeted users through remotely controlled WebView content.
The application relies on region-based behavior switching, remote configuration, and aggressive obfuscation to conceal its true functionality and evade platform review. Core loan operations, repayment messaging, and pressure-based user interfaces are served at runtime, allowing the operators to modify behavior without publishing updates or disclosing financial activity upfront.
Multiple technical indicators, including excessive permission requests, contact harvesting logic, undisclosed data collection, and reliance on offshore infrastructure, align with user complaints describing harassment, coercive repayment practices, and misuse of personal data. These behaviors are not consistent with regulated digital lending practices.
The presence of the application on the Google Play Store further amplifies user risk by leveraging platform trust to appear legitimate. Combined with misleading branding and lack of regulatory disclosures, this significantly increases the likelihood of user harm.
Based on the collected evidence, the application should be classified as a deceptive and high-risk mobile loan platform rather than a legitimate travel utility. Coordinated platform enforcement, regulatory review, and user awareness are necessary to prevent further exploitation and reduce the risk of similar applications re-emerging under alternate identities.
| Indicator | Type | Remarks |
| 0ac8f10afbc7f73f75ff732e9637846604b009f15b99cce9344ad94b49490844 | Sha256 | Apk |
| hicas.tech | domain | webview |
| https://in-h5.oss-ap-southeast-1.aliyuncs.com/hosts/hicas/config.json | URL | C2 |
| https://bksn515.vercel.app/hosts/hicas/config.json | URL | C2 |
| S.N | Tactic | Technique |
| 1. | Initial Access (TA0027) | T1660: Phishing |
| 2. | Persistence (TA0028) | T1603: Scheduled Task/Job |
| 3. | Défense Evasion (TA0030) | T1628: Hide Artifacts T1628.002: User Evasion T1406: Obfuscated Files or Information |
| 4. | Credential Access (TA0031) | T1417: Input capture |
| 5. | Discovery (TA0032) | T1418: Software Discovery T1426: System Information Discovery T1422: Internet Connection Discovery |
| 6. | Collection (TA0035) | T1414: Input capture T1636.003: Contact list |
| 7. | Command and Control (TA0037) | T1437: Application Layer Protocol T1437.001: Web Protocols T1521: Encrypted Channel T1481: Web Services |
| 8. | Exfiltration (TA0036) | T1646: Exfiltration Over C2 Channel |
rule Android_Hicas_Fraud_Loan_App
{
meta:
description = “Detects Hicas Android application associated with fraudulent loan behavior”
author = “Cyfirma Research”
date = “2026-01-29”
hash_sha256 = “0ac8f10afbc7f73f75ff732e9637846604b009f15b99cce9344ad94b49490844”
category = “Android.Fraud”
confidence = “High”
strings:
$domain1 = “hicas.tech” ascii wide
$cfg1 = “in-h5.oss-ap-southeast-1.aliyuncs.com/hosts/hicas/config.json” ascii wide
$cfg2 = “bksn515.vercel.app/hosts/hicas/config.json” ascii wide
condition:
( uint16(0) == 0x504B and filesize < 40MB ) and
$domain1 and
any of ($cfg*)
}
For Individual Users
For Enterprises and Organizations