


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows OS
Target Country: USA
Target Industry: Manufacturing
Introduction:
CYFIRMA Research and Advisory Team has found Sicarii Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Sicarii Ransomware
Security researchers have identified Sicarii Ransomware, a recently observed ransomware-as-a-service (RaaS) operation active since late 2025. Sicarii encrypts victim files using AES-GCM encryption and appends the “.sicarii” extension to affected data. The malware is capable of collecting system, credential, and network information and includes functionality for data packaging and exfiltration prior to encryption. During execution, Sicarii performs widespread file encryption, modifies the desktop wallpaper, and drops a ransom note named “HOW_TO_RECOVER_DATA.html.” The operators claim responsibility for both data encryption and data theft and threaten to publish stolen information to pressure victims into payment. CYFIRMA Research notes inconsistencies in the group’s public claims and operational maturity, and there is no publicly available decryption tool. Payment does not guarantee data recovery or prevent potential data exposure.
The Sicarii ransomware drops a ransom note after completing its reconnaissance, data exfiltration, and encryption phases, serving as the primary extortion mechanism to inform the victim of the compromise. While the exact filename, wording, and ransom demands are not specified, the placement of the ransom note occurs immediately following file encryption using AES-GCM with the .sicarii extension appended to affected files. The ransom note is reinforced by additional pressure tactics, as the malware also deploys a destructive batch script (destruct.bat) configured to execute on system startup, corrupt bootloader components, and perform disk-wiping operations. This sequencing indicates that the ransom note functions as both a notification and a coercive element, warning victims of escalating damage if recovery or negotiation is delayed, despite the absence of explicitly documented ransom note content in the data.
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1543 | Create or Modify System Process |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543 | Create or Modify System Process |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562 | Impair Defenses |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552 | Unsecured Credentials |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1614 | System Location Discovery |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
Relevancy and Insights:
ETLM Assessment
CYFIRMA’s assessment suggests that Sicarii ransomware is likely to continue operating as a functional but immature extortion-focused operation, potentially refining its existing workflow rather than introducing fundamentally new tactics. The malware already combines file encryption, data exfiltration, credential harvesting, and destructive recovery-hindering mechanisms, indicating an intent to apply multi-layered pressure on victims. If activity continues, the group may further operationalize its ransomware-as-a-service model, improve stability of its tooling, and streamline victim disclosure to build credibility beyond its currently limited public track record. However, the operation’s inconsistent messaging, centralized and informal tradecraft, explicit ideological signaling, and early-stage development artifacts suggest that any evolution is more likely to involve incremental polishing of existing capabilities rather than rapid scaling or sophistication. As long as these behavioral and operational patterns persist, Sicarii’s future activity is expected to remain opportunistic, selectively targeted, and constrained by its apparent lack of operational maturity and internal discipline.
Sigma rule:
title: Suspicious Loading of Dbgcore/Dbghelp DLLs from Uncommon Location tags:
– attack.credential-access
– attack.t1003
– attack.defense-evasion
– attack.t1562.001 logsource:
category: image_load product: windows
detection: selection_img:
Image|contains:
– ‘:\Perflogs\’
– ‘:\Temp\’
– ‘:\Users\Public\’
– ‘\$Recycle.Bin\’
– ‘\Contacts\’
– ‘\Desktop\’
– ‘\Documents\’
– ‘\Downloads\’
– ‘\Favorites\’
– ‘\Favourites\’
– ‘\inetpub\wwwroot\’
– ‘\Music\’
– ‘\Pictures\’
– ‘\Start Menu\Programs\Startup\’
– ‘\Users\Default\’
– ‘\Videos\’
# – ‘\AppData\Local\Temp\’ some installers may load from here selection_dll:
ImageLoaded|endswith:
– ‘\dbgcore.dll’
– ‘\dbghelp.dll’ condition: all of selection_*
falsepositives:
– Possibly during software installation or update processes level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Type: DynoWiper | Objectives: Data theft, espionage, and financial gains | Target Technology: Windows OS | Targeted Sector: Polish Energy Sector | Target Geography: Poland | Threat Actor: Sandworm/ APT44 (Russian).
CYFIRMA collects data from various forums, based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “DynoWiper” is trending.
Overview of Operation DynoWiper
In late 2025, Poland’s energy sector was the target of a coordinated cyber operation intended to cause significant operational disruption. The activity was attributed to a Russia-linked threat actor and was directed against systems supporting both conventional power generation facilities and renewable energy infrastructure. Although the intrusion was detected at an early stage, enabling defenders to contain the activity and prevent any disruption to energy production or distribution, Polish authorities isolated affected systems to prevent further compromise.
Available evidence indicates that the operation was primarily destructive in nature. The attackers deployed a data-wiping malware strain known as DynoWiper, designed to damage systems and render them inoperable rather than to facilitate data theft, espionage, or financial gain. This approach reflects a broader trend of state-aligned threat groups using cyber operations as tools of strategic pressure rather than traditional cybercrime, while the response underscores the importance of continuous monitoring, incident readiness, and strong public-private collaboration.
The incident illustrates the increasingly complex threat environment facing European critical infrastructure operators. Energy systems, given their essential role in economic stability and public welfare, remain a priority target for hostile cyber operations. Even though this attempt did not result in operational disruption, it serves as a clear reminder that adversaries continue to probe defenses and evolve their capabilities in pursuit of high-impact outcomes.
Sandworm / APT44
Sandworm, also known in the security community as APT44, is a well-known state- sponsored cyber group associated with Russia. It has a long history of targeting critical infrastructure, particularly in the energy and industrial sectors. Over the past decade, Sandworm has been linked to some of the most disruptive cyber incidents in Europe, especially those affecting power utilities.
The group is recognized for conducting operations that prioritize impact and disruption rather than profit. Its campaigns often align with broader geopolitical tensions, suggesting coordination with strategic objectives. The attempted operation against Poland fits this pattern, signaling that Sandworm continues to expand its focus beyond traditional targets and into a wider European context.
Attack Method
The attack was carried out through the deployment of a specialized destructive malware strain known as DynoWiper, which permanently disables Windows-based systems by eliminating data and corrupting essential operating system components. Unlike financially motivated malware, DynoWiper does not encrypt files or attempt to communicate with victims. Instead, its sole purpose is to render affected hosts unusable by systematically destroying both user and system-level data, thereby preventing normal operation and complicating recovery efforts.
Upon execution, DynoWiper enumerates available storage volumes and recursively scans directory structures to locate files across multiple categories, including user documents, application resources, and configuration data. Malware removes file contents prior to deleting file entries, ensuring that data cannot be easily reconstructed through forensic techniques. Beyond file destruction, DynoWiper targets critical Windows components related to boot configuration, service management, and system initialization. Damage to these elements prevents successful startup of the operating system, often requiring complete reinstallation or restoration from trusted backups.
Operational use of DynoWiper suggests a controlled and deliberate deployment model. The malware is typically introduced after attackers have already obtained elevated privileges and established internal access within the environment. Rather than propagating automatically, it is manually triggered at a chosen stage of the intrusion, indicating that operators aim to maximize disruption at a strategically significant moment. This method reflects a broader strategy of using destructive cyber capabilities to impose denial of service through irreversible system damage rather than through temporary encryption or extortion.
The following are the TTPs based on the MITRE Attack Framework
| Tactic (ID) | Technique ID | Technique Name |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1566 | Phishing |
| Execution | T1204 | User Execution |
| Execution | T1059 | Command and Scripting Interpreter |
| Defense Evasion | T1070 | Indicator Removal on Host |
| Discovery | T1083 | File and Directory Discovery |
| Command and control | T1071 | Application Layer Protocol |
| Impact | T1485 | Data Destruction |
| Impact | T1561 | Disk Wipe |
| Impact | T1490 | Inhibit System Recovery |
INSIGHTS
ETLM ASSESSMENT
From an ETLM perspective, the emergence of destructive malware operations such as DynoWiper signals a future environment in which organizations must contend with cyber incidents that are designed to directly impair operational continuity rather than merely compromise information assets. As disruption-focused activity becomes more common, employees across technical and non-technical roles may increasingly experience cyber events such as business- disruptive crises rather than abstract security issues. Over time, this shift is likely to elevate organizational sensitivity to service availability, amplify the human impact of outages on daily workflows, and reinforce the perception of cyber risk as a persistent factor shaping workplace processes, expectations, and overall operational resilience.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule DynoWiper_String_Hash_Detection
{
meta:
description = “String and hash-based detection for DynoWiper (Win32/KillFiles.NMO)”
author = “CYFIRMA” date = “2026-01-27”
threat_actor = “Sandworm / APT44”
strings:
/* Known sample hash */
$hash1 = “4EC3C90846AF6B79EE1A5188EEFA3FD21F6D4CF6”
/* Embedded command and execution strings */
$str1 = “cmd.exe /c” wide ascii
$str2 = “powershell.exe” wide ascii
$str3 = “vssadmin delete shadows” wide ascii
$str4 = “bcdedit /set” wide ascii
/* Generic destructive keywords */
$str5 = “wipe” wide ascii
$str6 = “killfiles” wide ascii
$str7 = “destroy” wide ascii
$str8 = “delete all” wide ascii
condition:
any of ($hash1) or 4 of ($str*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Key Intelligence Signals:
Lazarus Group: Profiling a North Korean Advanced Persistent Threat and Its Global Impact
About the Threat Actor
Lazarus Group, active since at least 2009, is a highly sophisticated cybercriminal organization reportedly linked to the North Korean government and known to the U.S. government as Hidden Cobra. Members are believed to be affiliated with Lab 110, a unit of DPRK military intelligence.
The group is capable of rapidly developing and evolving malware and exploits and has recently focused on targeting cryptocurrency exchanges. Lazarus Group operates in at least two subdivisions: Andariel, targeting the South Korean government and organizations, and Bluenoroff, focused on financial gain and global espionage.
Details on Exploited Vulnerabilities
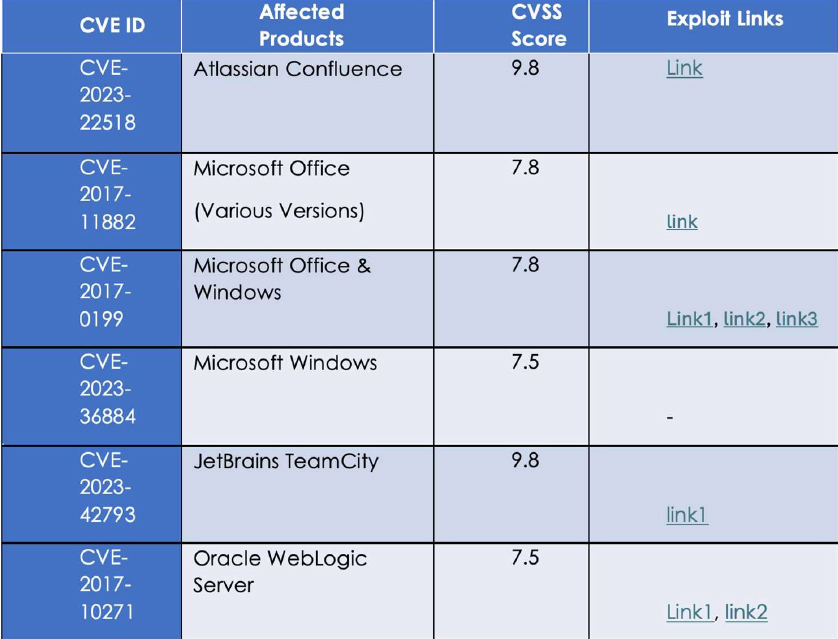
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1591.004 | Gather Victim Org Information: Identify Roles |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1608.002 | Stage Capabilities: Upload Tool |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1587.002 | Develop Capabilities: Code Signing Certificates |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.004 | Obtain Capabilities: Digital Certificates |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1566.003 | Phishing: Spear phishing via Service |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1106 | Native API |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Persistence | T1505.004 | Server Software Component: IIS Components |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1098 | Account Manipulation |
| Privilege Escalation | T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Privilege Escalation | T1134.002 | Access Token Manipulation: Create Process with Token |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1134.002 | Access Token Manipulation: Create Process with Token |
| Defense Evasion | T1218 | System Binary Proxy Execution |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.003 | Indicator Removal: Clear Command History |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1036.003 | Masquerading: Rename Legitimate Utilities |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.008 | Masquerading: Masquerade File Type |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.007 | Obfuscated Files or Information: Dynamic API Resolution |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1220 | XSL Script Processing |
| Defense Evasion | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Defense Evasion | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Defense Evasion | T1622 | Debugger Evasion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1221 | Template Injection Authentication Process: Conditional Access Policies |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1656 | Impersonation |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1622 | Debugger Evasion |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1124 | System Time Discovery |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1021.004 | Remote Services: SSH |
| Lateral Movement | T1534 | Internal Spear phishing |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1560 | Archive Collected Data |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1560.002 | Archive Collected Data: Archive via Library |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1001.003 | Data Obfuscation: Protocol or Service Impersonation |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1008 | Fallback Channels |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Exfiltration | T1048.003 | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
| Impact | T1561.001 | Disk Wipe: Disk Content Wipe |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1489 | Service Stop |
| Impact | T1485 | Data Destruction |
| Impact | T1529 | System Shutdown/Reboot |
| Impact | T1491.001 | Defacement: Internal Defacement |
Latest Developments Observed
The Threat actor is suspected to be linked to the Contagious Interview campaign, abusing Visual Studio Code task configuration files using ClickFix-style social engineering to trigger malicious payload execution. By misusing trusted IDE features, they can gain persistent access and steal sensitive data, including source code and intellectual property, while avoiding detection.
ETLM Insights
Lazarus Group operates with a clear state-aligned strategic intent, combining intelligence collection with financially motivated operations to support DPRK objectives. Recent activity indicates a sustained shift toward compromising developer environments and software supply chains, enabling high-impact intrusions without relying on traditional exploitation techniques.
Targeting priorities increasingly include developers, technology firms, and cryptocurrency ecosystems, where a single compromise can provide downstream access and significant financial leverage. The group’s evolving capabilities—marked by the use of cross-platform malware, cloud-hosted infrastructure, and developer-native tools—demonstrate a focus on stealth, persistence, and operational resilience.
These trends suggest continued expansion of supply-chain–centric attack methods, underscoring the need for intelligence-led visibility into developer workflows and execution behavior, as conventional security controls provide limited coverage against such threats.
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule Lazarus_SupplyChain_Attack
{
meta:
author = “CYFIRMA”
description = “Detects Lazarus Group activity targeting developer workflows via VS Code and supply-chain”
threat_actor = “Lazarus Group” date = “2026-01-27”
reference = “Jamf Threat Labs / Public IoCs”
strings:
// CVEs observed
$cve1 = “CVE-2017-11882”
$cve2 = “CVE-2017-10271”
$cve3 = “CVE-2023-22518”
$cve4 = “CVE-2017-0199”
$cve5 = “CVE-2023-36884”
$cve6 = “CVE-2023-42793”
// Domains
$domain1 = “knightsbridge-dex.vercel.app”
$domain2 = “tetrismic.vercel.app”
$domain3 = “mocki.io”
$domain4 = “sellinicapital.com”
$domain5 = “presentations.life”
// IPs
$ip1 = “141.193.213.20”
$ip2 = “188.165.53.185”
$ip3 = “199.59.148.209”
$ip4 = “119.28.118.4”
$ip5 = “118.70.180.174”
// Files / hashes
$file1 = “win32.exe”
$file2 = “hrm3jvh9v.dll”
$file3 = “eqfvkn”
$file4 = “00000077553a5b27a610ac98f29563bbd6e0decc020c2d49e4fa0d89197e7fd8”
condition:
any of ($cve*) or any of ($domain*) or any of ($ip*) or any of ($file*)
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
TikTok closes on a deal to spin off US operations
TikTok has finalized an agreement to spin off its U.S. operations into a new American- owned company, ending years of bipartisan pressure over national security concerns tied to its Chinese ownership. Under a 2024 law passed by the Biden administration, TikTok faced a U.S. ban unless its parent company, ByteDance, divested control of the app. According to NPR, U.S. investors—including Oracle, Silver Lake, and MGX—will hold more than 80 percent of the new entity, while ByteDance will retain just under a 20 percent stake. Former TikTok executive Adam Presser will serve as chief executive.
President Trump confirmed the deal in a Truth Social post, thanking Chinese President Xi Jinping “for working with us and, ultimately, approving the deal.” In a statement, TikTok said the majority American-owned joint venture will operate with safeguards designed to protect U.S. national security, including strict data protections, algorithm security measures, content moderation standards, and software assurances for American users.
ETLM Assessment:
The main reasons for the adoption of the TikTok “ban” were that it spies on its American users and sends their data to the Chinese Communist Party. A secondary reason was that it is subject to Chinese censorship and propaganda that seeks to induce American users to support the Party’s goals. Spying is the main reason because it is the easiest to prove – after details of it were presented to the US Senate, the vote on the motion was 50-0 in favour of the ‘ban’.
TikTok had to admit that it tracks the physical movements of selected journalists and sends the data to its Chinese parent company, and thereby to the Communist Party and Chinese intelligence services. In addition to physical location, the data TikTok collects can include facial and voice prints, browsing history, text messages, and other vital phone functions – TikTok has, in fact, systematically circumvented protections from Google and Apple against this app behavior. On top of that, the app’s integrated browser acted like a keylogger – that is, a spy program that recorded every keystroke a user made, which recorded everything, including passwords. The data can then be used to intimidate citizens through its alleged network of illegal police stations abroad.
Moreover, the Chinese government potentially could use TikTok to propagandize American youth and to silence those Americans who say things the Chinese government doesn’t like, which was clearly happening as an earlier CYFIRMA report on the topic has shown. As of writing, it is not clear what safeguards would be implemented under the auspices of the TikTok divestment deal to stop this from happening.
WorldLeaks Ransomware Impacts LTS Group
Summary:
CYFIRMA observed in an underground forum that a company from Japan, LTS Group (https[:]//ltsgroup[.]tech/), was compromised by WorldLeaks Ransomware. LTS Group is an IT outsourcing and technology services provider delivering software and digital solutions to businesses worldwide. The company is widely recognized as a global partner for software development, quality assurance and testing, and digital business process outsourcing (BPO). LTS Group operates in Japan, Vietnam, the United States, and South Korea. It serves a diverse client base across multiple industries, including e-commerce, healthcare, automotive, finance, education, and construction. The compromised data contains confidential and sensitive information belonging to the organization. The Total size of data compromised is approximately 43 GB.
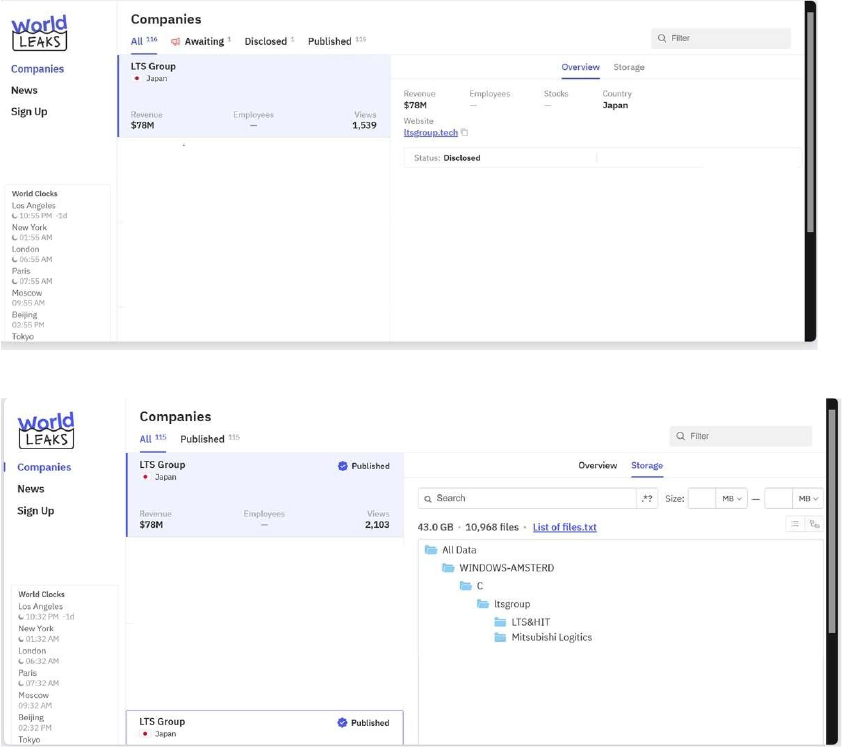
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the WorldLeaks ransomware group represents a modern evolution of the ransomware ecosystem, shifting toward data exfiltration and extortion-centric tactics. Emerging from Hunters International in early 2025, WorldLeaks operates a hybrid model combining Extortion-as-a-Service (EaaS) with limited encryption-based campaigns, demonstrating the strategic adaptation of cybercriminals to defensive maturity in enterprises.
The Gentlemen Ransomware Impacts Sincere Corporation
Summary
CYFIRMA observed in an underground forum that a company from Japan, Sincere Corporation(https[:]//www[.]sincerehq[.]com/), was compromised by the Gentlemen Ransomware. Sincere Corporation is a Japanese environmental services company that provides industrial waste, recycling, and building maintenance services. The data, which has been breached, has not yet appeared on the leak site, indicating that negotiations between the affected party and the ransomware group may be underway. The compromised data includes confidential and sensitive information belonging to the organization.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, the Gentlemen Ransomware is a highly adaptive and globally active threat that leverages dual-extortion tactics, combining data theft with file encryption. The group employs advanced evasion and persistence techniques, supports cross-platform and scalable ransomware deployment, and conducts targeted attacks across multiple industries and geographic regions. This combination of capabilities makes it a significant risk to enterprise cybersecurity defenses, particularly for organizations with limited detection and incident-response maturity.
Vulnerability in GNU Inetutils telnetd
Summary
The vulnerability allows a remote attacker to compromise the affected system.
Relevancy & Insights:
The vulnerability exists due to improper input validation when processing an attacker-controlled USER environment variable.
Impact:
A remote non-authenticated attacker can simply connect to the remote server with a specially crafted environment variable and obtain root privileges.
Affected Products:
https[:]//www[.]openwall[.]com/lists/oss-security/2026/01/20/2
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
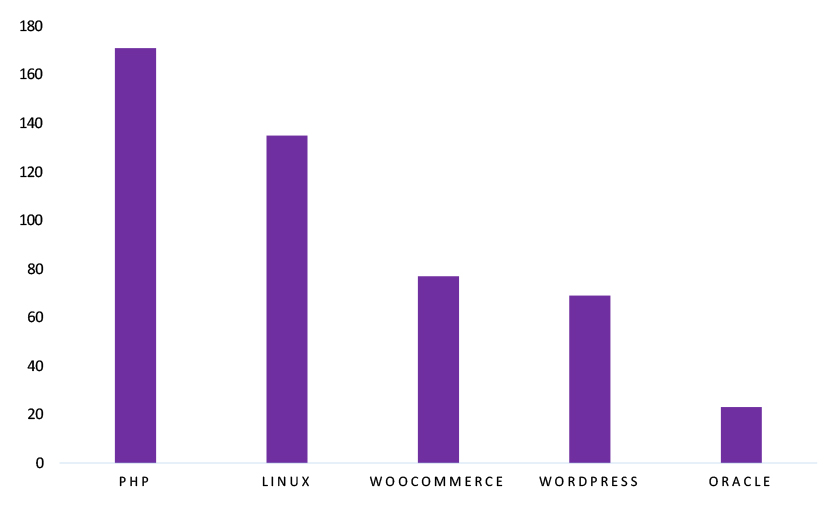
ETLM Assessment
A vulnerability in GNU Inetutils telnetd can pose significant threats to user privacy and system security. This can impact various industries globally, including technology, enterprise IT, education, and legacy system environments. Ensuring the security of GNU Inetutils telnetd is crucial for maintaining the integrity and protection of remote access services worldwide.
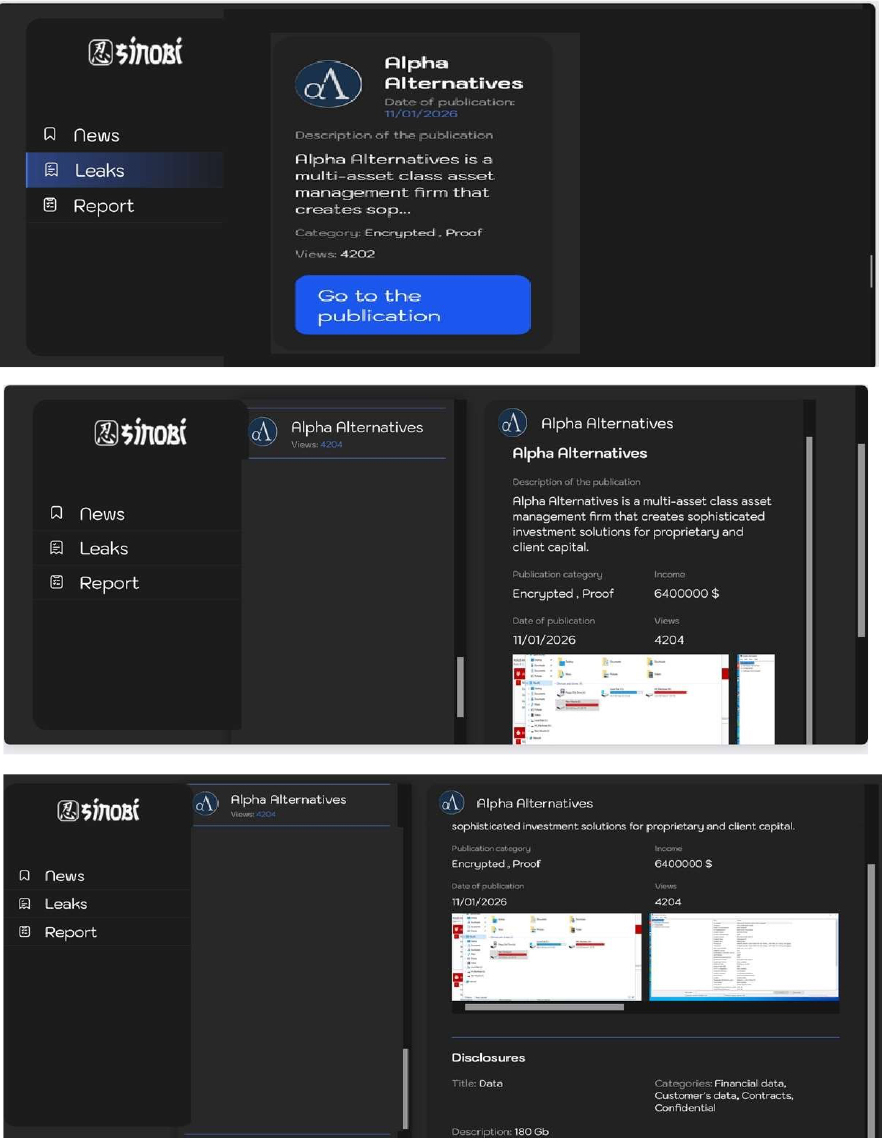
Sinobi Ransomware attacked and published the data of Alpha Alternatives
Summary:
Recently, we observed that Sinobi Ransomware attacked and published the data of Alpha Alternatives(http[:]//www[.]alphaalternatives[.]com/) on its dark web website. Alpha Alternatives is a multi-asset class asset management firm that creates sophisticated investment solutions for proprietary and client capital. The firm engages in alternative asset management, including equity, commodities, structured credit, and other niche investment areas. The ransomware incident led to the compromise of approximately 180 GB of data, including financial records, customer information, contractual documents, and other sensitive confidential data.
Relevancy & Insights:
ETLM Assessment:
According to CYFIRMA’s assessment, Sinobi Ransomware represents a persistent threat in the ransomware landscape, capable of disruptive attacks on both enterprises and mid-sized organisations.
Hopeful Co., Ltd Data Advertised on a Leak Site
Summary
The CYFIRMA research team has identified claims from a threat actor operating under the alias “888,” who alleges responsibility for a security breach involving Hopeful Co., Ltd.
Hopeful Co., Ltd., a Thailand-based health supplement company, is reported to have been compromised following the appearance of leaked data on a well- known hacking forum. The threat actor claims to have uploaded a database containing the personal information of approximately 158,000 unique customers. The breach is believed to have occurred in January 2026, with the exposed files reportedly including detailed records of e-commerce transactions and shipping logistics.
According to the threat actor, the compromised dataset includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.Top of FormBottom of Form
MHz Group Data Advertised on a Leak Site
Summary
The CYFIRMA research team has identified claims from a threat actor operating under the alias “888,” who alleges responsibility for a security breach involving MHz Group.
MHz Group, a UAE-based management consulting and software tool development company, is reported to have been compromised following the publication of leaked material on a well-known hacking forum.
According to the threat actor, the exposed data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “888” is assessed to be a highly active and capable group primarily engaged in data-leak operations. Multiple credible sources have associated this actor with a series of security incidents involving unauthorized access to systems and the sale or dissemination of stolen data on dark web marketplaces. These activities underscore the persistent and rapidly evolving cyber-threat landscape driven by underground criminal ecosystems and highlight the urgent need for organizations to reinforce their cybersecurity posture through continuous monitoring, improved threat-intelligence capabilities, and proactive defensive measures to protect sensitive information and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that Axtria, a global provider of cloud software and data analytics solutions with reported revenue of $1.2 billion, has allegedly suffered a significant data breach. The incident, which reportedly occurred in January 2026, involves the exfiltration and subsequent publication of the company’s proprietary data on the well-known hacking forum community.
According to the threat actor, the exposed data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

The CYFIRMA Research team has identified an alleged security compromise involving Zebra Technologies, an American multinational technology company specializing in marking, tracking, and computer printing solutions. According to claims posted by a threat actor on a well-known breach forum, the incident involved unauthorized access to sensitive source code repositories. The breach is reported to have occurred in January 2026 and impacts an organization with annual revenues exceeding USD 5.3 billion.
The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
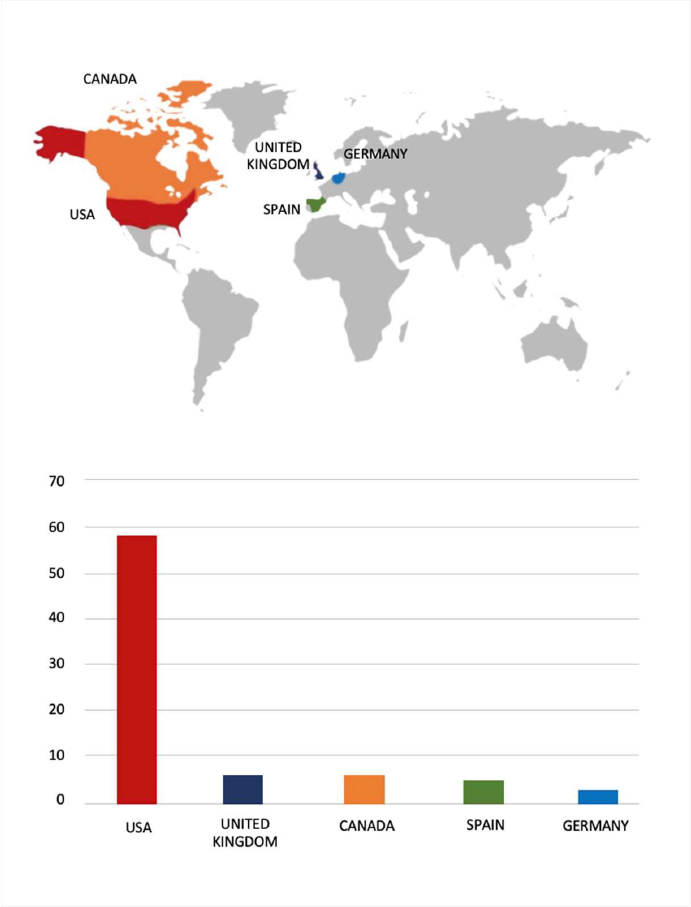
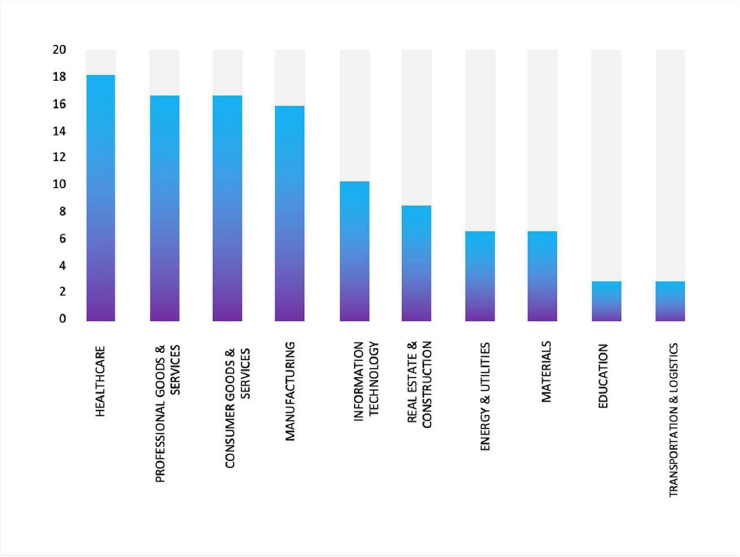
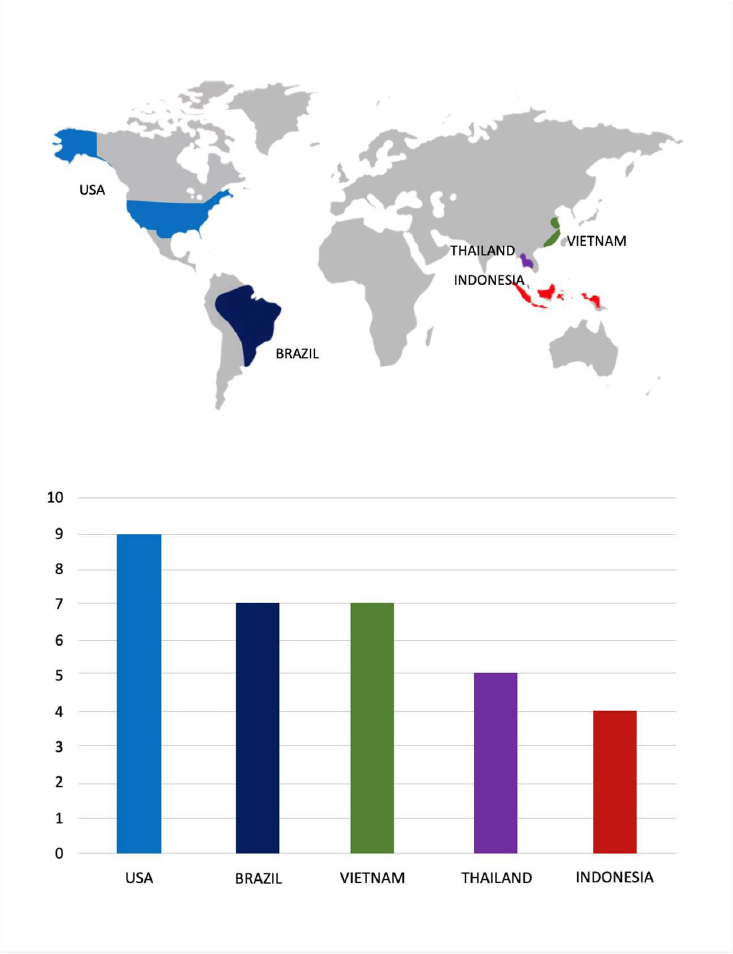
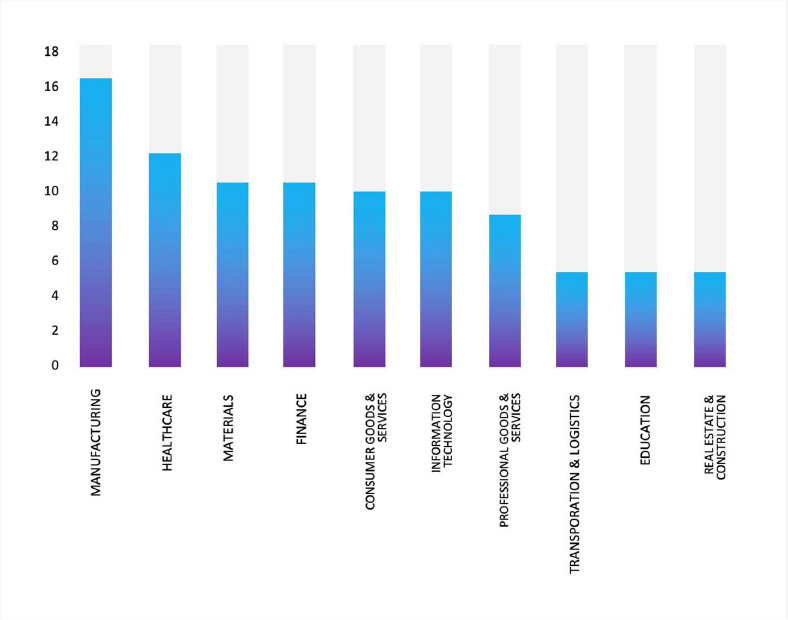
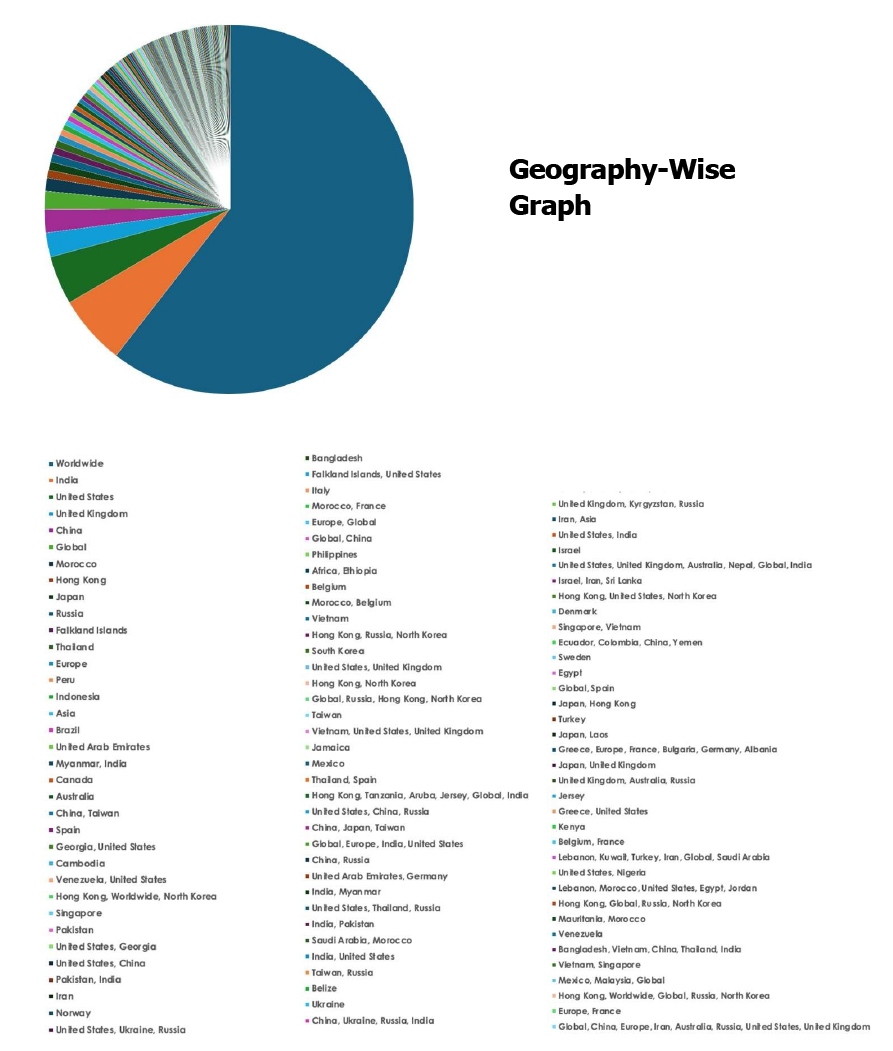
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.

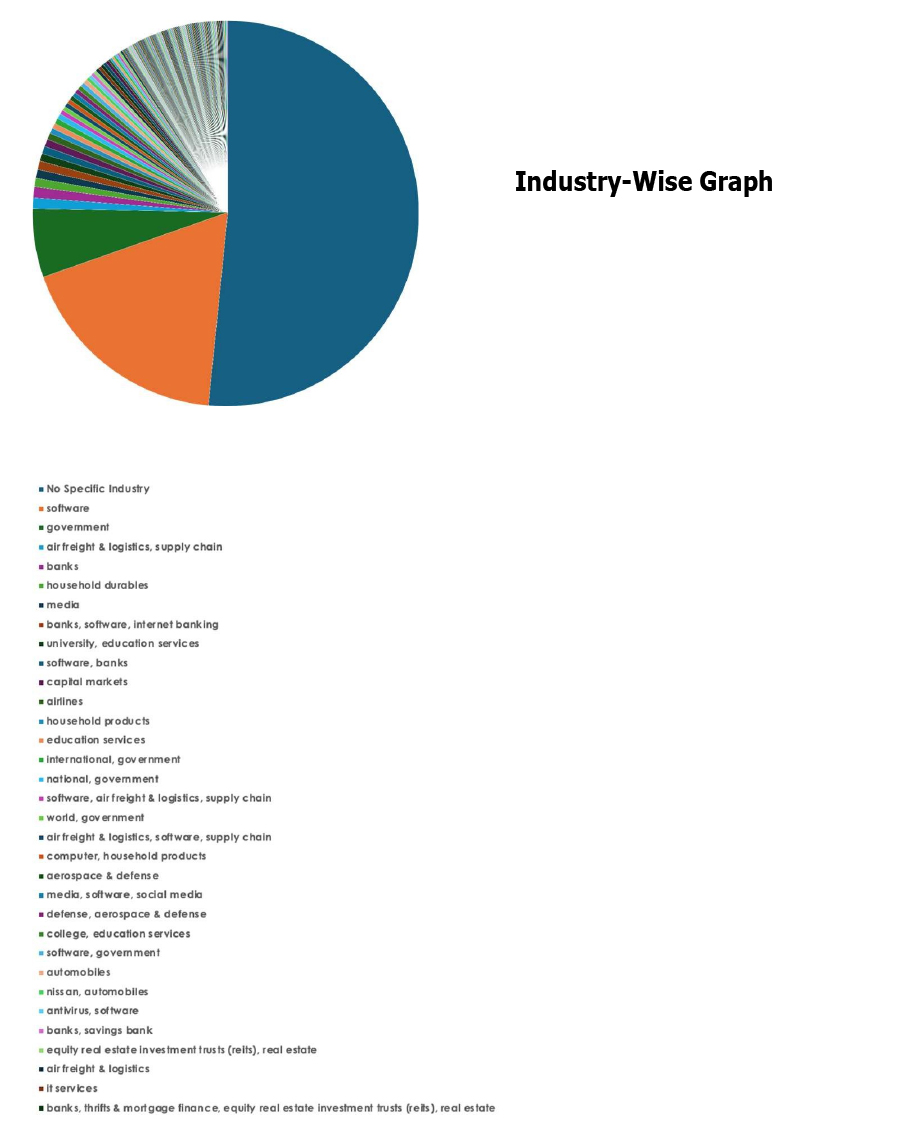
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.