


CYFIRMA assesses that Mamba 2FA is a representative of a broader class of adversary-in-the-middle phishing frameworks that have become increasingly prevalent in cloud-centric threat activity. The observed behaviors indicate a deliberate focus on realism, automation, and scale, enabling threat actors to bypass traditional security controls by closely emulating legitimate authentication experiences. Mamba’s design reflects a growing reliance on service-based phishing tooling, where operational efficiency and repeatability are prioritized over bespoke attack development. The continued visibility of Mamba 2FA within phishing activity highlights a wider trend in which phishing-as-a-service platforms are converging around similar capabilities and workflows. This convergence has contributed to an environment where phishing campaigns can be rapidly deployed, adapted, and sustained with minimal technical effort by operators. As a result, adversary-in-the-middle (AiTM) phishing remains a persistent and high-impact initial access vector across multiple sectors.
Mamba phishing-as-a-service began surfacing in phishing operations around 2023, during a period when threat actors increasingly shifted away from basic credential-harvesting techniques toward AiTM models. This shift was driven by the widespread adoption of multi-factor authentication across enterprise environments, which significantly reduced the effectiveness of traditional phishing pages. Mamba emerged as part of a new class of phishing frameworks designed to operate within this constraint by integrating authentication flow emulation, session handling, and real-time backend communication. From its inception, Mamba 2FA reflected a design philosophy centered on operational efficiency rather than novelty. Its workflow minimized visible user interaction, reduced friction during authentication, and relied on automation to handle identity context and credential relay. These characteristics positioned Mamba as a practical tool within the phishing-as-a-service (PhaaS) ecosystem, enabling scalable campaigns without requiring extensive operator oversight. As a result, Mamba was readily adopted by actors seeking reliable access-enablement tooling rather than bespoke attack development.
By 2025, AiTM phishing had become one of the most dominant initial access techniques observed across cloud-centric attack chains. During this period, Mamba 2FA was consistently associated with high-impact phishing activity, operating alongside several comparable kits that followed similar architectural patterns. The phishing landscape also saw the introduction of multiple new frameworks that adopted the same core principles, reinforcing a trend toward standardization across PhaaS offerings. Rather than displacing existing platforms, these new entrants contributed to a saturated environment in which kits evolved incrementally through feature parity, evasive enhancements, and infrastructure flexibility.
Analysis of the phishing URL reveals behavior consistent with Mamba AiTM phishing operations. The execution flow prioritizes automation and speed, reducing user interaction while enabling rapid credential capture and session handling.
Encoded Initial Request and Page Load
Upon access, the browser issues an HTTPS GET request to a URL path structured in the format
The encoded parameter contains a long, non-human-readable string, indicative of obfuscation and runtime data passing. This technique is commonly used to conceal operational parameters and hinder static URL-based detection.
The server responds with HTML content, initiating the phishing flow.
Observed characteristics:
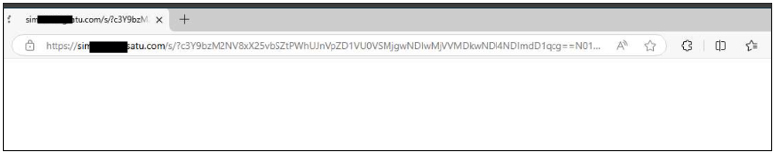
Automatic Identity Context and “Authenticating” State
Unlike phishing kits that prompt for an email address, the observed page does not request user email input. Instead, the page immediately displays an “Authenticating” or loading state, implying that the identity context has already been established.
This suggests the email address is:
This behavior reduces friction and accelerates victim progression through the phishing flow.
Observed characteristics:
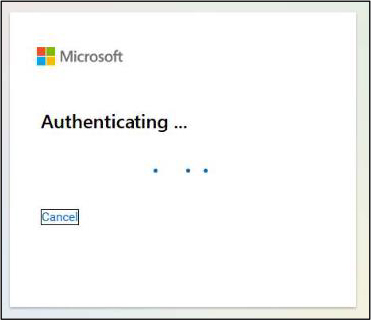
Microsoft-Style Password Prompt with Organizational Branding
Following the authentication state, the page presents a Microsoft-style password prompt. The interface closely mirrors a legitimate organizational login page, including:
Only the password field is displayed, reinforcing the illusion that the email identity has already been validated.
Observed characteristics:
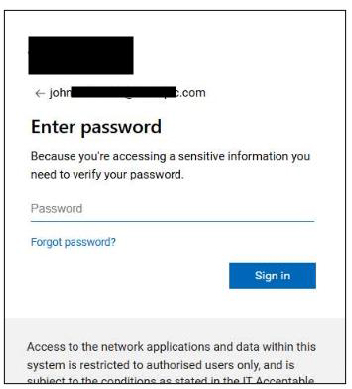
Client-Side Password Capture Logic
The password field is monitored by client-side JavaScript. Input handling occurs within the browser, preparing the entered credentials for transmission immediately upon submission.
This design aligns with Mamba 2FA’s focus on rapid credential relay rather than extended interaction flows.
Observed characteristics:
Redirection to Legitimate Destination
After password submission, the page redirects the browser to a legitimate website. No phishing-related content is displayed post-submission.
This redirection serves multiple purposes:
Delivery Mechanism (Observed and Common Practices)
Campaigns associated with Mamba phishing operations are most commonly delivered through email-based lures designed to drive the victim directly to the phishing URL. These lures typically impersonate routine business or security-related communications to create urgency and legitimacy.
Commonly observed delivery characteristics include:
In some cases, the phishing URL is delivered via redirect chains, where an initial benign-looking link forwards the victim to the final phishing page. This approach reduces early detection and allows operators to rotate infrastructure rapidly.
Overall, delivery techniques prioritize speed, believability, and minimal interaction, aligning with Mamba 2FA’s streamlined adversary-in-the-middle phishing workflow.
CYFIRMA assesses that Mamba 2FA is part of a broader, highly active PhaaS ecosystem in which AiTM capabilities have become increasingly standardized. The operational behaviors observed in Mamba 2FA, such as direct credential harvesting through high-fidelity cloud authentication clones, minimal user interaction, and near-real-time backend communication, closely mirror techniques seen across other established phishing kits. This alignment indicates that Mamba 2FA is not operating in isolation but rather reflects a shared development and tradecraft pattern common among modern phishing frameworks targeting cloud identity platforms, particularly Microsoft 365.
CYFIRMA further assesses that the phishing-kit landscape is undergoing continuous and incremental evolution, driven by competition among kit operators and defensive pressure from identity providers and security vendors. As a result, platforms such as Mamba 2FA are expected to adapt by incorporating features already observed in peer kits, including more advanced traffic filtering, improved sandbox and automation evasion, expanded identity provider targeting, and refined post-authentication deception techniques. This evolutionary trajectory suggests that Mamba 2FA may increase in sophistication over time, enhancing its resilience against detection and maintaining its effectiveness in facilitating MFA bypass and credential-based account compromise. Collectively, these trends reinforce the ongoing threat posed by AiTM phishing kits to enterprise cloud environments and underscore the need for continuous monitoring and adaptive defensive controls.
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.002 | Phishing: Link |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Credential Access | T1056.003 | Input Capture: Web Portal Capture |
| Credential Access | T1110.004 | Brute Force: Credential Stuffing |
| Credential Access | T1528 | Steal Application Access Token |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1127 | Trusted Developer Utilities Proxy Execution |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1132 | Data Encoding |
| Collection | T1056 | Input Capture |
| Collection | T1119 | Automated Collection |
| Impact | T1499.004 | Endpoint Denial of Service: Application or System Exploitation |
This assessment demonstrates that Mamba 2FA should be viewed within the context of an evolving phishing ecosystem rather than as an isolated threat. Its operational characteristics illustrate how phishing techniques have matured in response to the widespread adoption of multi-factor authentication, shifting the balance from simple credential theft toward session-aware attack models. The emergence of comparable platforms and new entrants further reinforces the durability of this approach. Given these conditions, the risk posed by frameworks such as Mamba 2FA is likely to persist as long as cloud-based identity services remain a primary attack surface. Effective mitigation will depend on layered identity security controls, improved detection of authentication anomalies, and continuous adaptation to emerging phishing methodologies. Monitoring ecosystem-level trends, rather than individual tools alone, will remain critical to anticipating and countering future developments in this threat space.
To reduce the risk posed by Mamba 2FA–style phishing campaigns and similar adversary-in-the-middle frameworks, organizations should adopt a multi-layered approach combining technical controls, user awareness, and continuous monitoring:
Identity and Access Management
Email Security and Threat Filtering
Endpoint and Network Protection
User Awareness and Training
Continuous Threat Intelligence and Monitoring