

Recent monitoring of underground forums and Telegram communities has identified the resurgence of the Scattered Lapsus$ collective. The actors appear to be leveraging the LizardSquad name in their messaging, though this remains unverified and may reflect reputation-building rather than a genuine partnership.
The collective, infamous for intrusions into major global enterprises, has re-emerged with scaled-up recruitment activity and a clearly defined target zone. They are actively seeking Initial Access brokers, insider collaborators, and corporate credentials that align with their selection criteria.
The improved operational structure suggests that clusters within the group now maintain “focused areas of expertise.” If these operators are combining capabilities (even symbolically) their ability to conduct large-scale compromise and extortion operations increases substantially.
Recent telemetry from closed Telegram clusters, credential-trading channels, and the access-broker ecosystem indicates a renewed operational footprint associated with actors linked to the Scattered Lapsus$ Hunters. Chatroom discussions repeatedly reference legacy threat brands such as LizardSquad, though these mentions remain unverified and are likely part of an intimidation or reputation-inflation strategy rather than proof of a formal alliance.
This regrouping is characterized by structured operators aligning to defined roles: social-engineering specialists, intrusion operators, credential brokers, insider-recruitment facilitators, and data-leak amplification nodes.
The cluster’s methodology reflects a blended TTP profile drawing from Lapsus$-style social-engineering intrusions, paired with infrastructure abuse patterns reminiscent of older threat groups, and monetization models consistent with Hunters-affiliated access brokers.
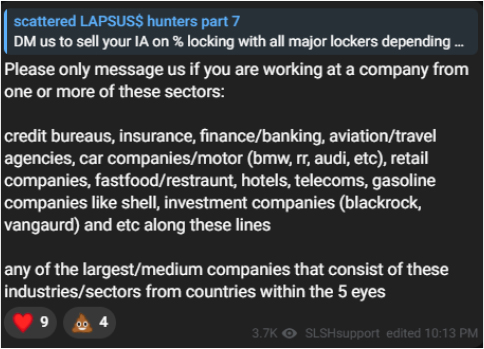
Early indicators highlight a pivot toward high revenue enterprises (≥ USD 500M) across telecommunications, software/gaming supply chains, BPO/call-center environments, and cloud/hosting providers, with operations oriented toward US, AU, UK, CA, and FR networks.
Threat Actor Resurgence:
Recent monitoring directly identified the re-emergence of the Scattered Lapsus$ Hunters group. Activity observed across multiple channels shows the collective has significantly rebuilt its operational footing. Through renewed access-broker deals and consistent posting behaviour, the group has re-established its internal structure and resumed coordinated intrusion operations. This suggests a shift back toward semi-structured, high-impact campaigns consistent with their historic activity.
Internal Discussion Review & Chatroom Analysis
The infamous Scattered Lapsus$ Hunters who went underground after their major supply chain intrusion via Salesforce third-party integrations (Gainsight and Salesloft) and attempted campaigns targeting Zendesk users-have resurfaced.
Chatroom discussions contain references to the LizardSquad name, although these appear unverified and likely intended to strengthen their perceived threat posture rather than confirm a real partnership.
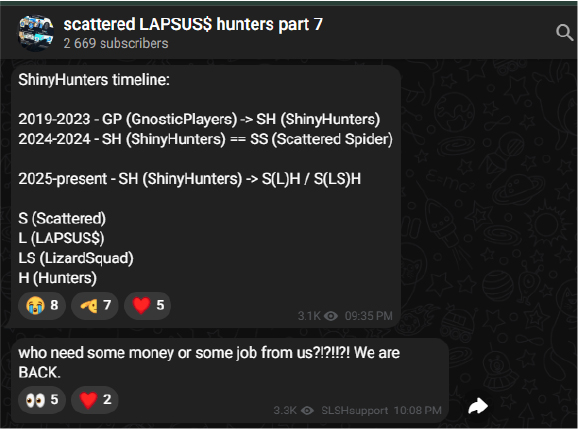
The group’s latest activities highlight a deliberate attempt to scale operations through active talent acquisition.
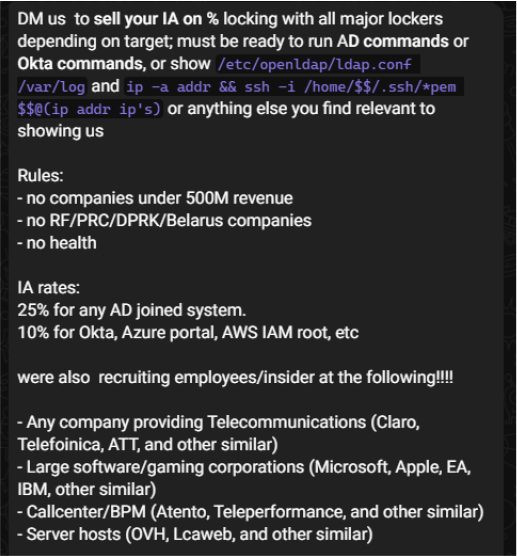
The collective is openly advertising Initial Access purchases, commission-based payouts, and insider recruitment efforts. This indicates the prioritization of privileged or directory-integrated access, suggesting operational goals involving post-authentication exploitation, credential abuse, and lateral movement.
Their explicit IA rules include:
Structured commission tiers include:
The group is also actively advertising for insider recruitment-seeking operators who can provide VPN, VDI, Citrix, or AnyDesk access from telecommunications providers, large software/gaming corporations, and call-center/BPM environments. Screenshots from the Telegram channel illustrate the industries they are targeting.
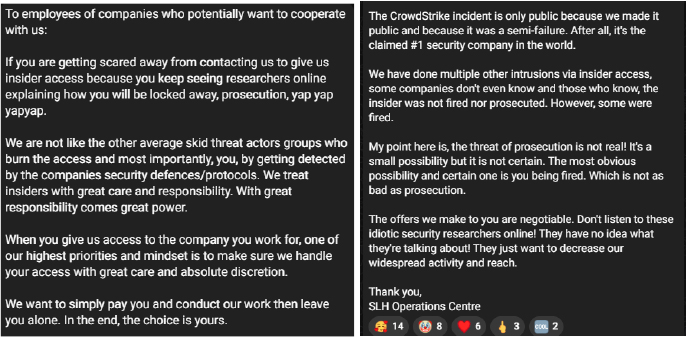
The group can also be seen addressing insider fears, referencing the recent CrowdStrike insider detection incident and assert that informants within their operation would remain undiscovered. They framed the CrowdStrike case as a self-inflicted disclosure following a failed insider attempt, using this narrative to reassure potential collaborators.
In the early days of their resurgence, the group shared a CrowdStrike internal dashboard and an Okta SSO page leaked to them by an employee.

The collective has also announced an in-development build of a new Ransomware-as-a-Service (RaaS) platform called “ShinySp1d3r”, described as a collaboration involving members associated with ShinyHunters, Scattered Spider, and Lapsus$.
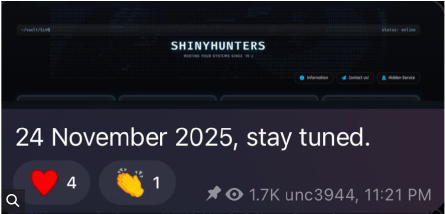
Emerging Risks Heading Into 2026
The threat actors routinely issue bold, provocative statements about planned attacks, sustaining their reputation as a highly disruptive threat collective. Screenshots provide additional insight into their intended activities, including threats to compromise and leak more customer data.
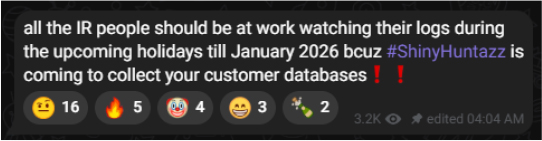
Their continuous recruitment posts-offering percentage-based payouts for AD-joined systems, Okta access, cloud credentials, and internal telemetry-suggest that insider-driven breaches will remain a core attack vector in 2026.
The group continues referencing multiple “partners,” each supposedly bringing unique expertise. If their collaboration model continues evolving-even symbolically-2026 may see a solidified ecosystem of sub-groups specializing in initial access, identity compromise, social engineering, and data extortion.
Recent intelligence indicates a strong resurgence of the Scattered Lapsus$ Hunters collective, which has re-emerged with a more structured operational model, expanded recruitment efforts, and renewed public activity. Chatroom observations show the group frequently invoking LizardSquad’s name, though this association is unverified and likely part of a reputation-building strategy rather than a confirmed operational partnership.
Their behaviour reflects a strategic pivot toward access-broker alignment, insider recruitment, and commission-structured Initial Access purchasing, with clear revenue, sector, and geopolitical filters. The collective is actively pursuing privileged identity access and infrastructure credentials across major enterprises, demonstrating a shift toward deeper post-authentication exploitation and lateral expansion.
They are also working to expand capabilities through the development of a joint Ransomware-as-a-Service platform, ShinySp1d3r, involving operators linked to ShinyHunters, Scattered Spider, and Lapsus$. Their leaked dashboards, claims of insider support, and escalating public threats all highlight a renewed intent to intensify operations and project confidence.
Heading into 2026, their aggressive messaging, persistent recruitment, and emphasis on identity-based access suggest increasing risk to telecommunications, cloud service providers, software vendors, and large enterprise environments.