


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows OS
Target Geography: United States, France, Taiwan, Thailand, South Africa, and other regions across Asia, Europe, Latin America, and Africa.
Target Industry: Technology, Healthcare, Government/Public Sector, Construction, and Manufacturing.
Introduction:
CYFIRMA Research and Advisory Team has found DEVMAN 21 Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
DEVMAN 21 Ransomware
Researchers have discovered a new ransomware strain called DEVMAN 21. This ransomware encrypts victim data, renames affected files by appending a unique extension (such as .devman21), and generates a ransom note titled “!!!README!!!.txt”.

Screenshot: File encrypted by ransomware (Source: Surface Web)
CYFIRMA’s assessment suggests that the DEVMAN 21 ransomware group is progressively shifting from a conventional file-encryption–centric model toward a more advanced, data-extortion–focused operation. The group utilizes strong hybrid cryptography (RSA-4096 and AES-256), threatens the public release of exfiltrated data, and applies time-based ransom escalation while conducting negotiations through anonymous channels such as Tor and qTox. Its operational methods include offering limited free decryption to establish credibility, stressing confidentiality during communications, and applying psychological pressure via data-leak threats, indicating a growing level of professionalism and organizational structure. Based on these observed behaviors, CYFIRMA assesses that DEVMAN 21 is likely to further expand its double-extortion strategy, enhance leak-site infrastructure for public exposure, and introduce more automated negotiation and payment mechanisms to support operational scale. Over time, the group may evolve into a persistent, service-oriented ransomware operation, consistent with broader trends across organized cyber-extortion groups.
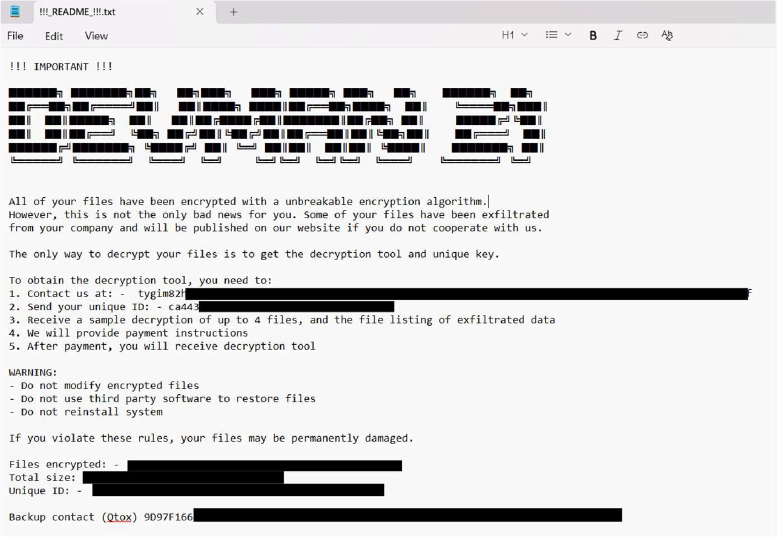
Screenshot: The appearance of DEVMAN 21’s ransom note (“!!!_README_!!!.txt”) (Source: Surface Web)
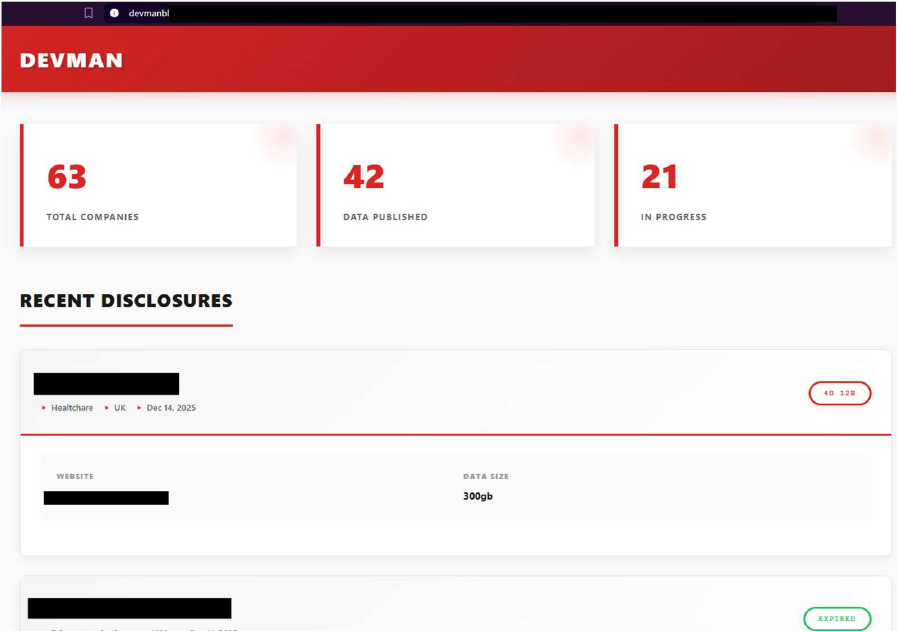
Screenshot: Data Leak site DEVMAN
The following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542 | Pre-OS Boot |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1547 | Boot or Logon Autostart Execution |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134.004 | Access Token Manipulation: Parent PID Spoofing |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1542 | Pre-OS Boot |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Credential Access | T1056 | Input Capture |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1614 | System Location Discovery |
| Collection | T1056 | Input Capture |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that the DEVMAN 21 ransomware group is likely to further advance its operations by building on its existing encryption-and-data- extortion model. Given its demonstrated use of file encryption combined with threats of public data disclosure, anonymous communication channels, and credibility-building tactics, such as limited free decryption, the group is expected to continue prioritizing campaigns that maximize coercive leverage over victims.
DEVMAN 21 may seek to standardize and streamline victim engagement processes through more consistent ransom communications and structured negotiation flows to support higher campaign volumes. The emphasis on data exfiltration suggests the group could expand proof-of-compromise practices, including selective data samples or staged disclosures, to reinforce pressure and accelerate payment decisions. Additionally, reliance on anonymized infrastructure indicates a likely focus on maintaining and hardening communication channels to improve operational resilience. Over time, and consistent with broader ransomware evolution trends, DEVMAN 21 may also explore scalable operating approaches that enable wider deployment of its tooling and sustain long-term extortion activity under a unified operational framework.
Sigma rule:
title: Disable Windows Defender Functionalities Via Registry Keys tags:
– attack.defense-evasion
– attack.t1562.001 logsource:
product: windows category: registry_set
detection: selection_main:
TargetObject|contains:
– ‘\SOFTWARE\Microsoft\Windows Defender\’
– ‘\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\’
– ‘\SOFTWARE\Policies\Microsoft\Windows Defender\’ selection_dword_1:
TargetObject|endswith:
– ‘\DisableAntiSpyware’
– ‘\DisableAntiVirus’
– ‘\DisableBehaviorMonitoring’
– ‘\DisableBlockAtFirstSeen’
– ‘\DisableEnhancedNotifications’
– ‘\DisableIntrusionPreventionSystem’
– ‘\DisableIOAVProtection’
– ‘\DisableOnAccessProtection’
– ‘\DisableRealtimeMonitoring’
– ‘\DisableScanOnRealtimeEnable’
– ‘\DisableScriptScanning’ Details: ‘DWORD (0x00000001)’
selection_dword_0:
TargetObject|endswith:
– ‘\DisallowExploitProtectionOverride’
– ‘\Features\TamperProtection’
– ‘\MpEngine\MpEnablePus’
– ‘\PUAProtection’
– ‘\Signature Update\ForceUpdateFromMU’
– ‘\SpyNet\SpynetReporting’
– ‘\SpyNet\SubmitSamplesConsent’
– ‘\Windows Defender Exploit Guard\Controlled Folder Access\EnableControlledFolderAccess’
Details: ‘DWORD (0x00000000)’
filter_optional_symantec:
Image|startswith: ‘C:\Program Files\Symantec\Symantec Endpoint Protection\’
Image|endswith: ‘\sepWscSvc64.exe’
condition: selection_main and 1 of selection_dword_* and not 1 of filter_optional_*
falsepositives:
– Administrator actions via the Windows Defender interface
– Third party Antivirus level: high
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Information Stealer| Objectives: Data Exfiltration & Credential Theft | Target Technology: Windows OS | Target Industry: Finance | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malwares that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week, “JSCEAL” is trending.
Overview of JSCEAL Infostealer Malware
JSCEAL is a sophisticated information-stealing campaign primarily targeting users of cryptocurrency applications. First identified in early 2024, the threat has steadily evolved from a limited operation into a mature and well-organized campaign. Ongoing research throughout 2025 indicates continuous development, with threat actors refining their techniques to maintain persistence and effectiveness, demonstrating a long-term commitment to the operation.
The campaign relies on impersonation of legitimate cryptocurrency trading platforms to distribute malicious installers, typically through fraudulent websites promoted via malicious advertising. Once executed, these installers initiate a carefully staged infection process that incorporates multiple verification and evasion steps before deploying the final malicious component. In certain cases, the attackers deliberately avoid delivering the payload to reduce exposure, reflecting a strategic focus on remaining undetected rather than immediate exploitation.
A defining feature of JSCEAL is its strong emphasis on stealth and resistance to security analysis. The campaign employs advanced obfuscation and anti-analysis techniques, which have historically resulted in very low detection rates, even when samples were widely circulated. Despite portions of the campaign becoming publicly known, ongoing monitoring indicates that JSCEAL remains active and continues to evolve. The threat actors consistently refine their methods to evade detection, underscoring a broader trend toward increasingly adaptive and covert malware campaigns targeting the cryptocurrency ecosystem, as well as the growing importance of proactive security controls.
Attack Method
The JSCEAL operation employs a structured, multi-layered intrusion process that emphasizes controlled execution and environmental validation. The initial access vector relies on paid online advertisements that redirect selected users through a managed chain of intermediary domains. These redirections serve both as traffic shaping and as an early filtering mechanism, ensuring that only targets matching predefined conditions are forwarded to the next stage, while all other visitors are presented with benign or unrelated content.
Once the redirection criteria are satisfied, the victim is presented with a professionally crafted download interface that delivers a malicious installer package. This installer is designed to function only when a parallel web component is active, creating a strict dependency between the local installation process and the remote site. During execution, the installer deploys multiple embedded components, establishes local listeners, and initializes persistence logic. To maintain user trust, the process simultaneously displays legitimate application content, effectively masking the underlying activity.
In later variants observed in mid-2025, the backend delivery and control mechanisms were substantially re-engineered. The attackers transitioned to a standardized infrastructure model featuring newly registered domains, consistent subdomain usage, and restrictive request handling. Server-side logic actively validates client behavior and rejects unexpected interaction patterns. Responses are deliberately staged, with misleading content delivered initially, followed by subsequent retrieval steps only after validation checks are met. This approach significantly disrupts automated analysis and limits unintended exposure.
The final execution phase involves the retrieval of a packaged runtime environment that enables the execution of obfuscated, precompiled script logic. This stage provides the operators with extensive control capabilities, including system interaction, data extraction, traffic manipulation, and remote task execution. Across all phases, the operation demonstrates a preference for precision, delayed execution, and adaptability, favoring long-term operational stability over rapid, high-noise deployment.
The following are the TTPs based on the MITRE Attack Framework for Enterprise
| Tactic (ID) | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization / Sandbox Evasion |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Command and control | T1071 | Application Layer Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1531 | Account Access Removal |
Operational Maturity and Scale Beyond Initial Indicators
The activity associated with this threat demonstrates a level of operational maturity that goes beyond simple opportunistic misuse of advertising channels. Over time, the actors have systematically expanded their footprint by refining domain holdings, diversifying infrastructure components, and optimizing user engagement mechanisms. This progression reflects not merely increased volume of exposure but also a deliberate shift toward a more resilient and coordinated set of practices, suggesting the involvement of organized planning and resource allocation rather than ad-hoc exploitative efforts.
Strategic Use of Legitimate Ecosystems Creates Subtle Exposure Paths
One of the more notable characteristics emerging from analysis is the interplay between deceptive artefacts and seemingly legitimate communication channels. By embedding malicious distribution vectors within mainstream advertising environments, the actors leverage trust-based mechanisms as indirect amplification points. This creates exposure paths that are subtle by design: users are drawn in by familiar interfaces and expected content, blurring the line between benign interaction and threat exposure. Such strategic embedding underscores how familiar digital ecosystems can be repurposed as vectors for distribution without triggering immediate suspicion.
Structural Adaptation Reflects Evasion and Containment Priorities
Beyond the surface narrative of expanded reach and obfuscation, the underlying adaptations observed signify a nuanced emphasis on containment and stealth.
Changes in infrastructure naming patterns, access controls, and response behaviors indicate a preference for reducing detectable footprints and isolating control channels from broad visibility. This structural evolution suggests that avoidance of discovery and analysis is not incidental but central to the operation’s design ethos. Rather than relying on aggressive exploitation tactics that leave clear signatures, the actors prioritize stealthy persistence and controlled interaction, indicating an operational philosophy that values operational longevity over immediate impact.
ETLM ASSESSMENT
From an ETLM perspective, CYFIRMA assesses that the emergence of operations such as JSCEAL points to a future threat environment characterized by lower visibility, increased attribution challenges, and deeper integration of malicious activity within routine digital workflows. As these threat operations continue to mature, organizations may encounter extended periods of undetected activity, elevating the risk of covert data exposure and abuse of trusted applications. Employees are likely to be increasingly leveraged as indirect entry points, as adversaries exploit commonplace actions such as downloading software, applying updates, or conducting online research, thereby narrowing the distinction between legitimate behavior and compromise. Over time, these developments may compel organizations to reevaluate how trust is established and maintained across users, applications, and execution contexts, as conventional assumptions around detection, early warning, and clear indicators of malicious activity become less effective against adaptive and low-profile threats.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rules
rule JSCEAL_Infostealer_Payload
{
meta:
description = “Detects JSCEAL-related artifacts based on known C2 domains and payload hashes”
author = “CYFIRMA” date = “2025-09-16”
strings:
/* Known JSCEAL C2 / infrastructure domains */
$d1 = “goldensecho.link”
$d2 = “nightfallglen.com”
$d3 = “evercircle.org”
$d4 = “silversoak.link”
$d5 = “calmtobridge.com”
$d6 = “freshstartwalk.org”
$d7 = “coralsshore.net”
$d8 = “everlantern.net”
$d9 = “sunhorizon.org”
$d10 = “auroratrails.link”
$d11 = “veloranest.net”
$d12 = “cedarwhispers.link”
$d13 = “velvetsforest.org”
$d14 = “moonscanyon.org”
$d15 = “flowhaven.link”
$d16 = “maplehaven.fyi”
$d17 = “toautumnlake.net”
$d18 = “ravencliff.org”
$d19 = “stillswaters.link”
$d20 = “amberstrail.net”
$d21 = “northhollow.net”
$d22 = “nordexahub.name”
$d23 = “lighttrail.name”
$d24 = “lowskymeadow.com”
$d25 = “emberstolight.com”
$d26 = “aurevospace.org”
$d27 = “radiantlagoons.com”
$d28 = “lunarapoint.org”
$d29 = “mapleonhaven.net”
$d30 = “cedarspath.com”
$d31 = “goldentrail.name”
$d32 = “forestsgate.com”
$d33 = “ironscove.net”
$d34 = “opencrest.name”
$d35 = “evergreengopath.org”
$d36 = “shadowsvale.net”
$d37 = “lunasfield.net”
$d38 = “whisperhavens.com”
$d39 = “amberfielder.com”
$d40 = “lumenivory.com”
$d41 = “wildflowerpath.org”
$d42 = “prismhills.com”
$d43 = “novaharbor.net”
$d44 = “starhavengo.com”
$d45 = “leafmollytrail.com”
$d46 = “skyinwinters.org”
$d47 = “starsmeadows.net”
$d48 = “warmtogrove.net”
/* Known JSCEAL-related SHA-256 hashes */
$h1 = “9615f60ea3cc1c65eb8fe6d77bb85fe6b455503193eab02310a873fccadd332e”
$h2 = “72af070240c149cda4ad6b6ebb581af4285402d1e2d1ae77dbdb8db41cce3828”
$h3 = “2e04eb129d72645e0167e58d404d1c5a258a97b897d61ed4ea05d2a59ab5d897”
$h4 = “f575032cbae83be2488a59d98f7ffd5c876c8e50f11e56e5a3b071456c2ce28f”
condition:
/* Match either known hashes OR multiple infrastructure indicators */ any of ($h*) or
2 of ($d*)
}
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Key Intelligence Signals:
o Coinbase Cartel Ransomware – One of the ransomware groups.
o Qilin Ransomware – One of the ransomware groups.
Please refer to the trending malware advisory for details on the following:
o Malware – JSCEAL
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
Strategic Cyber Intelligence: Ashen Lepus (WIRTE) Targeting Middle Eastern Entities
About the Threat Actor
Ashen Lepus is an APT group recognized for conducting espionage operations targeting Arabic-speaking government entities across the Middle East. The threat actor is suspected of being affiliated with, and operating on behalf of, Hamas- related groups in the region. The group is believed to have been active since at least 2018 and is thought to overlap with an Arabic-speaking, politically motivated threat cluster commonly referred to as the Gaza Cyber Gang.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2017- 0199 | Microsoft Office | 7.8 | Link1, Link2, Link3 |
| CVE-2017-11826 | Microsoft Office, SharePoint, Web Applications, Word Viewer | 7.8 | – |
| CVE-2017- 0261 | Microsoft Office | 7.8 | – |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1204.002 | User Execution: Malicious File |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1105 | Ingress Tool Transfer |
Latest Developments Observed
Recent observations indicate that Ashen Lepus has significantly evolved its operations with the introduction of the AshTag modular malware suite, enabling more stealthy, persistent, and hands-on espionage activity. The group has also expanded its targeting scope, with new geopolitical phishing lures and increased focus on countries such as Turkey. Additionally, its shift toward destructive capabilities, including the use of wiper malware against Israeli entities, highlights a move beyond traditional intelligence collection.
ETLM Insights
Ashen Lepus is actively expanding its external attack surface, with observable indicators pointing to sustained reconnaissance and infrastructure staging aligned with espionage-driven objectives. The actor demonstrates a systematic approach to identifying exposed assets, compromised credentials, and misconfigured services associated with government, diplomatic, and other high-value regional organizations. Its sustained and adaptive intelligence operations across the Middle East suggest alignment with broader regional geopolitical interests, supported by strong operational discipline and resilience—even during periods when affiliated threat clusters exhibit reduced visibility.
The group consistently leverages recurring patterns such as domain registration clustering, frequent rotation of command-and-control (C2) infrastructure, and the use of legitimate cloud and hosting providers to blend malicious activity into normal internet traffic. These techniques complicate detection efforts and enable rapid operational pivoting when infrastructure is identified or disrupted.
Ashen Lepus maintains a persistent and adaptable external presence, using infrastructure agility and credential-based access to support long-term espionage operations while minimizing attribution risk. Its behavior reflects a deliberate strategy of prolonged intelligence collection, selective targeting of high-value entities, and disciplined operational security, allowing sustained access to sensitive information over extended periods.
Overall, Ashen Lepus represents a methodical and strategically significant threat actor, underscoring the importance of heightened vigilance and proactive defense measures to protect diplomatic and governmental networks.
YARA Rules
rule Suspicious_CVE_IP_Domain_Indicators
{
meta:
description = “Detects files or data containing indicators related to CVE-2017-0199, CVE- 2017-11826, CVE-2017-0261, associated IPs, domains, and executable names”
author = “CYFIRMA” date = “2025-12-16”
threat = “Potentially malicious indicators linked to known CVEs and infrastructure”
strings:
// IP addresses as strings (ascii, exact match)
$ip1 = “198.105.122.96”
$ip2 = “198.105.117.37”
$ip3 = “192.253.246.169”
$ip4 = “192.99.111.228”
$ip5 = “192.52.167.125”
// CVE identifiers
$cve1 = “CVE-2017-0199” ascii nocase
$cve2 = “CVE-2017-11826” ascii nocase
$cve3 = “CVE-2017-0261” ascii nocase
// Domains
$domain1 = “david-gardiner.website” ascii nocase
$domain2 = “jonathanbartz.com” ascii nocase
$domain3 = “wayne-lashley.com” ascii nocase
// Executable name
$exe = “viewfile.exe” ascii nocase
condition:
any of ($ip*) or any of ($cve*) or any of ($domain*) or $exe
}
Recommendations Strategic
Management
Tactical
Russian hackers targeting critical infrastructure, Germany summons Russian envoy
In mid-December, amid escalating tensions over Russia’s war in Ukraine, Western governments highlighted a surge in Russian-linked hybrid threats, combining cyberattacks on critical infrastructure with disinformation campaigns aimed at undermining democracies.
The U.S. intelligence community, alongside partners from more than a dozen countries, including Germany, issued a joint cybersecurity advisory warning of opportunistic attacks by pro-Russian hacktivist groups–such as the Cyber Army of Russia Reborn (CARR), Z-Pentest, NoName057(16), and Sector16. These actors exploit poorly secured, internet-facing virtual network computing (VNC) connections to target operational technology in critical sectors, including water and wastewater systems, food and agriculture, and energy. While the groups have limited technical sophistication and often misunderstand the systems they disrupt– leading to haphazard outcomes–they have caused varying impacts, including physical damage. Some, like CARR, have documented ties to Russia’s GRU military intelligence, with evidence of state funding and direction.
Concurrently, Germany’s foreign ministry summoned the Russian ambassador in Berlin to protest a “massive increase” in Moscow-backed hybrid activities, ranging from disinformation and espionage to cyberattacks and sabotage attempts.
Officials cited clear evidence linking the GRU to a 2024 cyberattack on Germany’s air traffic control system, attributed to the hacker group Fancy Bear (APT28), as well as interference in February 2025’s federal election and domestic affairs via the “Storm-1516” campaign. This operation disseminated deepfakes, fabricated stories, and pseudo-journalistic content–such as false claims of scandals involving politicians like the Chancellor–often amplified on social media platforms.
ETLM Assessment:
Germany pledged coordinated European countermeasures, including new sanctions like travel bans and asset freezes on implicated individuals, to impose costs on Russia for these actions aimed at dividing society and eroding trust in democratic institutions– and indeed by mid-December, the EU Council imposed asset freezes and travel bans on 12 individuals and two entities involved in information manipulation and cyber operations aimed at destabilizing Europe and undermining democratic processes.
This will likely provoke Russia in several predictable ways, based on its historical pattern of responses to Western pressure; Russia will typically issue sharp condemnations, deny all allegations, and frame them as attempts to suppress free speech or silence pro-Russian voices. In retaliation, Moscow often mirrors actions by imposing counter-sanctions on EU officials, diplomats, or entities; expelling diplomats; or restricting Western media/NGOs in Russia and using hackers and propagandists to escalate hybrid activities–potentially intensifying cyberattacks on European infrastructure, amplifying disinformation campaigns, or greenlighting sabotage plots to demonstrate defiance and impose asymmetric costs.
The U.S. to enlist private cybersecurity firms to conduct offensive cyberattacks
The U.S. administration is preparing to enlist private cybersecurity firms in conducting offensive cyberattacks against foreign adversaries, marking a significant expansion of U.S. digital warfare beyond traditional intelligence agencies and military units. The new national cyber strategy, as reportedly drafted by the Office of the National Cyber Director, explicitly calls for “unleashing” private businesses to help impose costs on state-sponsored hackers and criminals targeting critical infrastructure, telecommunications networks, and businesses via ransomware.
Currently, no legal basis exists for private companies to independently launch offensive operations, and involvement could expose them to retaliation from foreign governments, whose intelligence services often rely on proxy hackers.
ETLM Assessment:
Despite these risks, the move reflects a consensus in the administration and intelligence community that the U.S. requires greater capacity to counter well- resourced adversaries, allowing government agencies to focus on high-end threats. Experts note that many defensive-focused firms possess tools and expertise adaptable for offense.
Coinbase Cartel Ransomware Impacts Renesas Electronics Corporation
Summary:
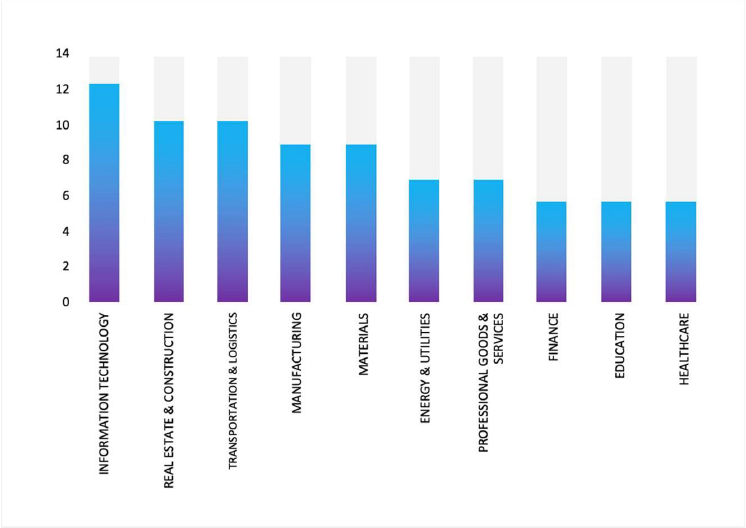
CYFIRMA observed in an underground forum that a company from Japan, Renesas Electronics Corporation (www[.]renesas[.]com), was compromised by Coinbase Cartel Ransomware. Renesas Electronics Corporation delivers trusted embedded design innovation with complete semiconductor solutions. Renesas provides quality and comprehensive solutions for a broad range of Automotive, Industrial, Home Electronics (HE), Office Automation (OA), and Information Communication Technology (ICT) applications. Renesas Electronics is headquartered in Tokyo, Japan. The compromised data includes confidential details such as physical geometry metrics (wafer diameter, die size, grid size, wafer area, die area), yield analysis reports, spatial defect distribution maps, and lot analysis records.
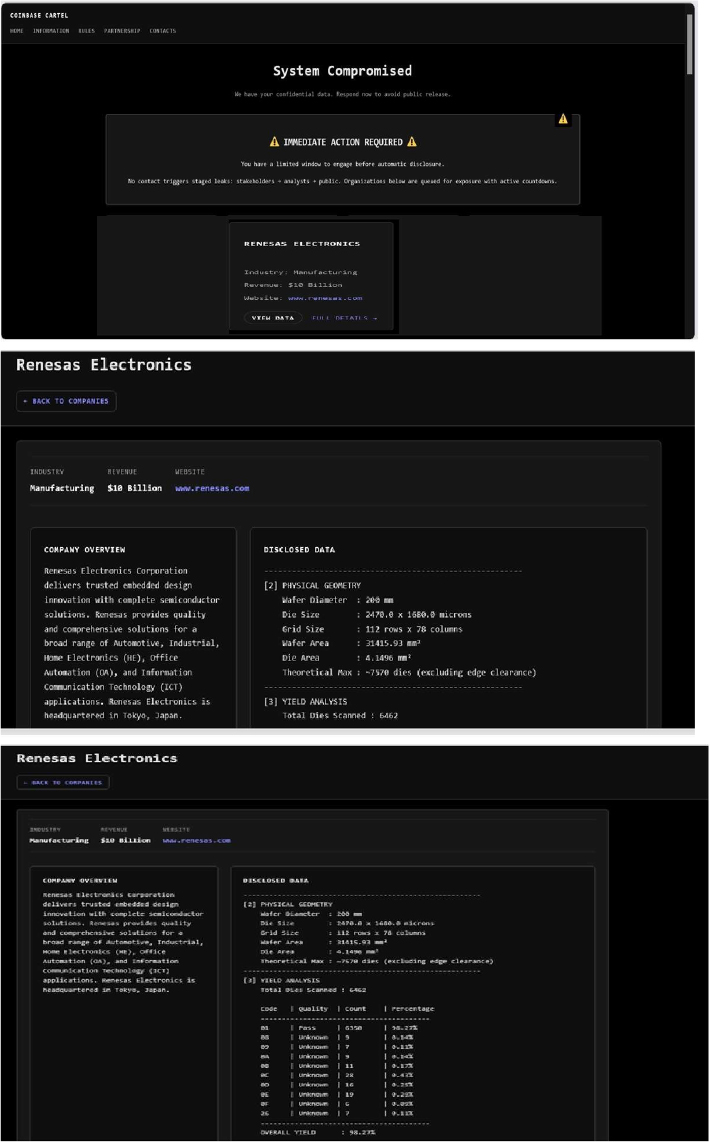
Source: Dark Web
Relevancy & Insights:
ETLM Assessment:
Based on recent assessments by CYFIRMA, Coinbase Cartel represents a fast- maturing, financially motivated extortion collective that has moved the goalposts from classic crypto-locking ransomware toward a predominantly data-theft and leak-driven model, significantly increasing legal, regulatory, and reputational risk even in the absence of encryption-driven outages.
Qilin Ransomware Impacts Sanko Air Conditioning Co., Ltd.
Summary:
CYFIRMA observed in an underground forum that a company from Japan, Sanko Air Conditioning Co., Ltd. (www[.]sanko-air[.]co[.]jp), was compromised by Qilin Ransomware. Sanko Air Conditioning Co., Ltd. is a Japanese company operating in the construction and building systems space, with a core focus on air-conditioning and related mechanical services. The compromised data contains confidential and sensitive information belonging to the organization.
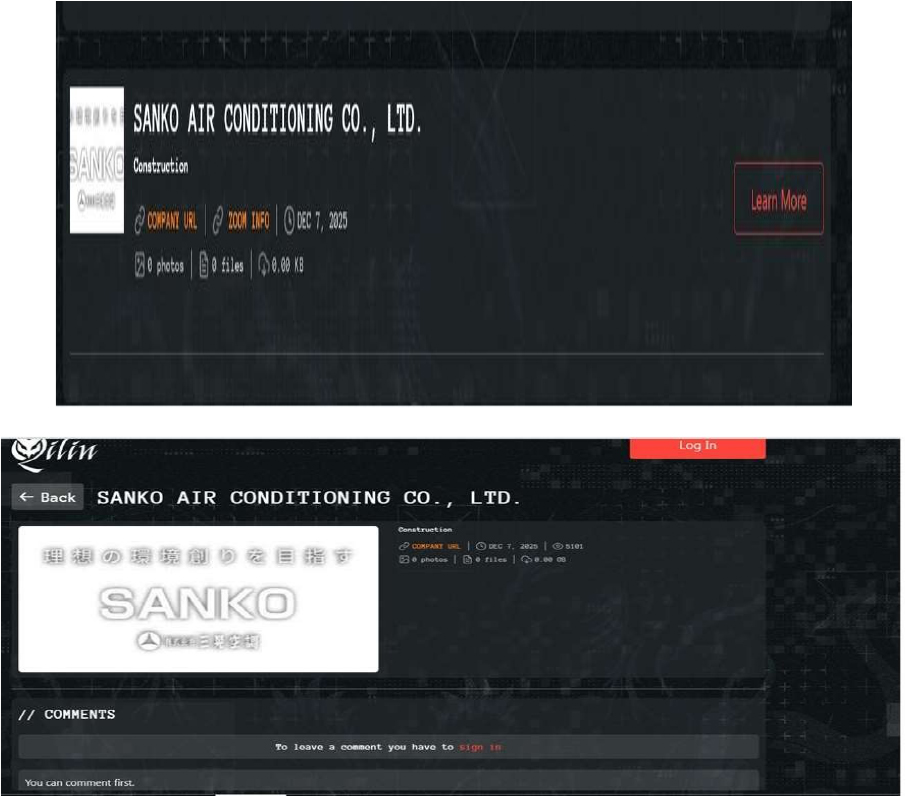
Source: Dark Web
Relevancy & Insights:

ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and a focus on speed and evasion, make it a particularly dangerous actor.
Vulnerability in Next.js App Router
Relevancy & Insights:
The vulnerability exists due to insecure input validation when processing serialized data.
Impact:
A remote attacker can send a specially crafted HTTP request, which can cause an infinite loop and prevent future HTTP requests from being served, leading to a denial-of-service condition.
Affected Products:
https[:]//react[.]dev/blog/2025/12/11/denial-of-service-and- source-code-exposure-in-react-server-components
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
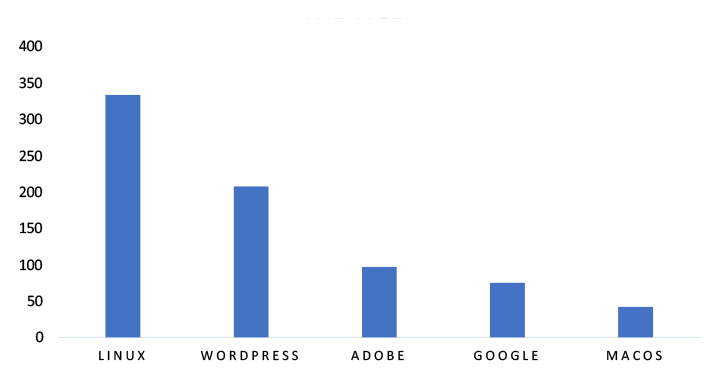
ETLM Assessment
Vulnerabilities in the Next.js App Router can pose significant threats to application integrity and user data privacy. This can impact various industries globally, including technology, e-commerce, finance, and enterprise IT. Ensuring the security of the App Router is crucial for maintaining the reliability and protection of modern full- stack React applications worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding Server Components, Server Actions, and dynamic routing mechanisms across different geographic regions and sectors.
DevMan Ransomware attacked and published the data of Quezon Power
Summary:
Recently, we observed that DevMan Ransomware attacked and published the data of Quezon Power (www[.]qpl[.]com[.]ph) on its dark web website. Quezon Power (Philippines), Limited Co. (QPL) is an independent power producer that operates a coal-fired power plant supplying electricity to the Luzon grid in the Philippines. The data leak from the ransomware attack includes employee records, HR information, project documents, power plant work logs, and SCADA source code, with the total volume of compromised data estimated at around 200 GB.
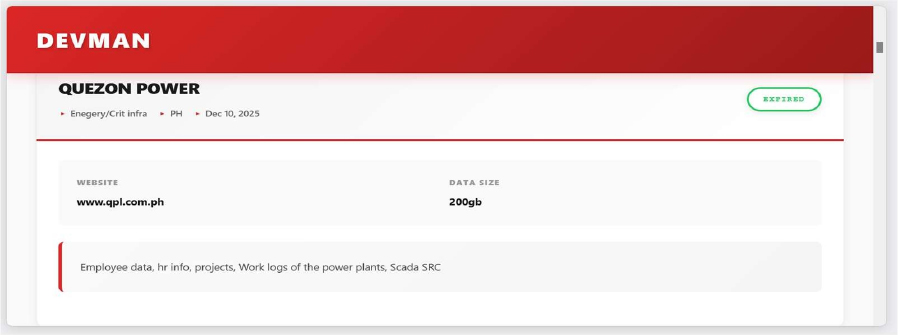
Source: Dark Web
Relevancy & Insights:
DevMan ransomware is a recently identified ransomware strain that emerged in early 2025, showing strong ties to the notorious DragonForce and Conti ransomware families but with distinct characteristics that set it apart as an independent threat. It primarily targets Windows 10 and 11 systems, including Windows server infrastructures, and is known for rapid file encryption and lateral movement within networks using SMB (Server Message Block) share.
ETLM Assessment:
According to CYFIRMA’s assessment, DevMan marks a notable advancement in the ransomware threat landscape. First observed in early 2025 as a customized derivative of DragonForce, the operation rapidly evolved and, by late 2025, had matured into a fully developed Ransomware-as-a-Service (RaaS) platform.
DevMan continues to pose a persistent cyber-extortion risk, primarily targeting organizations with inadequate security controls, underscoring the critical need for strong cybersecurity hygiene, continuous monitoring, and proactive defensive measures.
Sticker Japan Data Advertised on a Leak Site
Summary: The CYFIRMA research team has identified claims made by a threat actor, operating under the alias “Sorb,” who alleges responsibility for a security breach involving Sticker Japan.
Sticker Japan, a company specializing in business card and sticker printing services, is reportedly the victim of a data compromise. According to the threat actor, a database containing the personal information of approximately 110,000 users has been exfiltrated and offered for sale on a cybercrime forum, with an asking price of $150.
According to the actor and the sample data provided, the allegedly compromised information includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
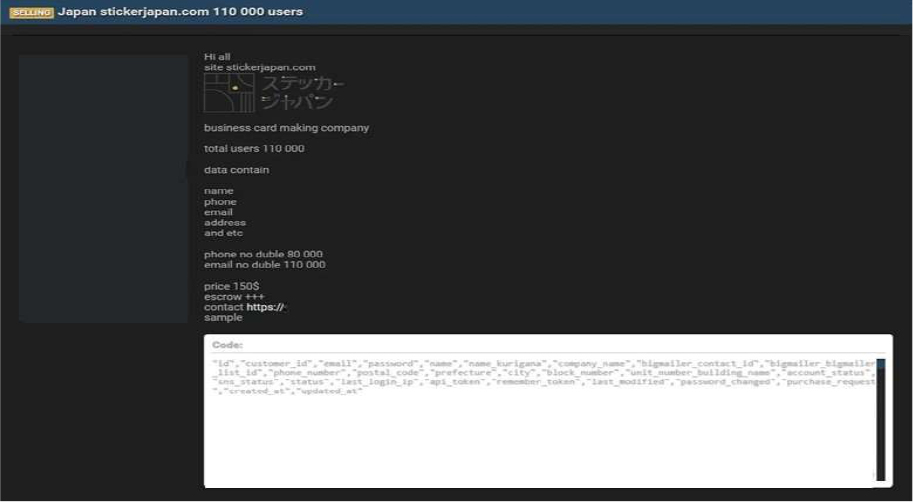
Source: Underground Forums
ThermoEx Company Limited Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team has identified claims suggesting that ThermoEx Company Limited, a prominent Thailand-based manufacturer of high-pressure equipment and heat exchangers, has been compromised.
According to listings observed on a cybercrime forum, a sizable database allegedly belonging to ThermoEx is being offered for sale for $15,000. ThermoEx is known for designing equipment in compliance with ASME standards and for serving major international clients, including Parker Hannifin, Linde, and several organizations within the petrochemical, oil, and gas sectors. The purported data leak is said to comprise approximately 170 GB of information, encompassing more than 108,000 files.
According to the actor, the allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.

Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously looking for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to gain access and steal valuable data. Subsequently, the stolen data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor referred to as “Sorb” is assessed to be a highly active and capable group primarily engaged in data-leak operations. Several credible sources have connected the actor to a range of security breaches involving unauthorized access to systems and the distribution or sale of stolen data on dark web marketplaces.
These activities highlight the persistent and rapidly evolving threat landscape driven by underground cybercriminal communities and underscore the importance for organizations to reinforce their cybersecurity posture through continuous monitoring, enhanced threat intelligence, and proactive defensive strategies to protect sensitive data and critical infrastructure.
Recommendations: Enhance the cybersecurity posture by:
The CYFIRMA Research team observed that Tabsyst, a web-based platform associated with educational management services, has allegedly been compromised, resulting in the sale of sensitive user data on a dark web forum. The platform appears to handle user registrations and management, as indicated by the “members” table exposed in the breach.
According to the actor, the compromised database is approximately 20.2 MB in size and contains 53,779 records. The actor claims the data is available in CSV format and includes a significant amount of financial information. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
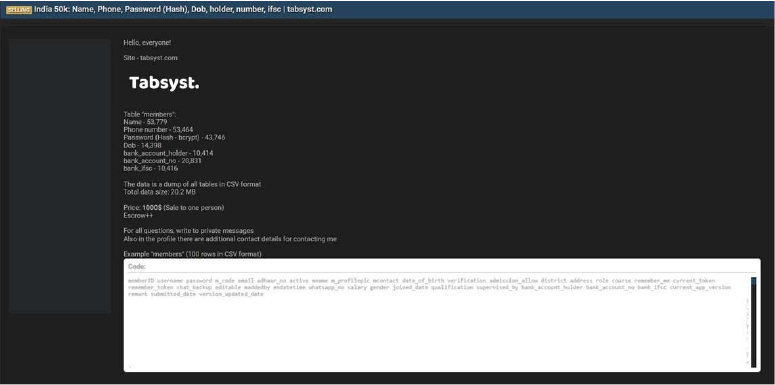
Source: Underground Forums
The CYFIRMA Research team has identified claims suggesting that myQNAPcloud, the cloud-based remote access service operated by QNAP Systems, has been targeted in a data-related offering on a cybercrime forum.
A threat actor alleges they have gained “internal access” to the service and is advertising this access for sale at $400. Although the actor has presented screenshots purportedly showing the interface of a specific QNAP NAS device (TS- 228), the listing implies a wider compromise of the myQNAPcloud platform.
According to the actor, the unauthorized access allegedly provides entry to sensitive information. The claimed data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
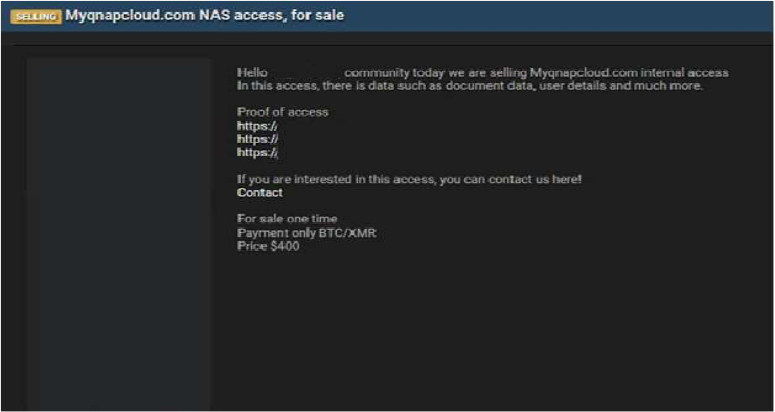
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
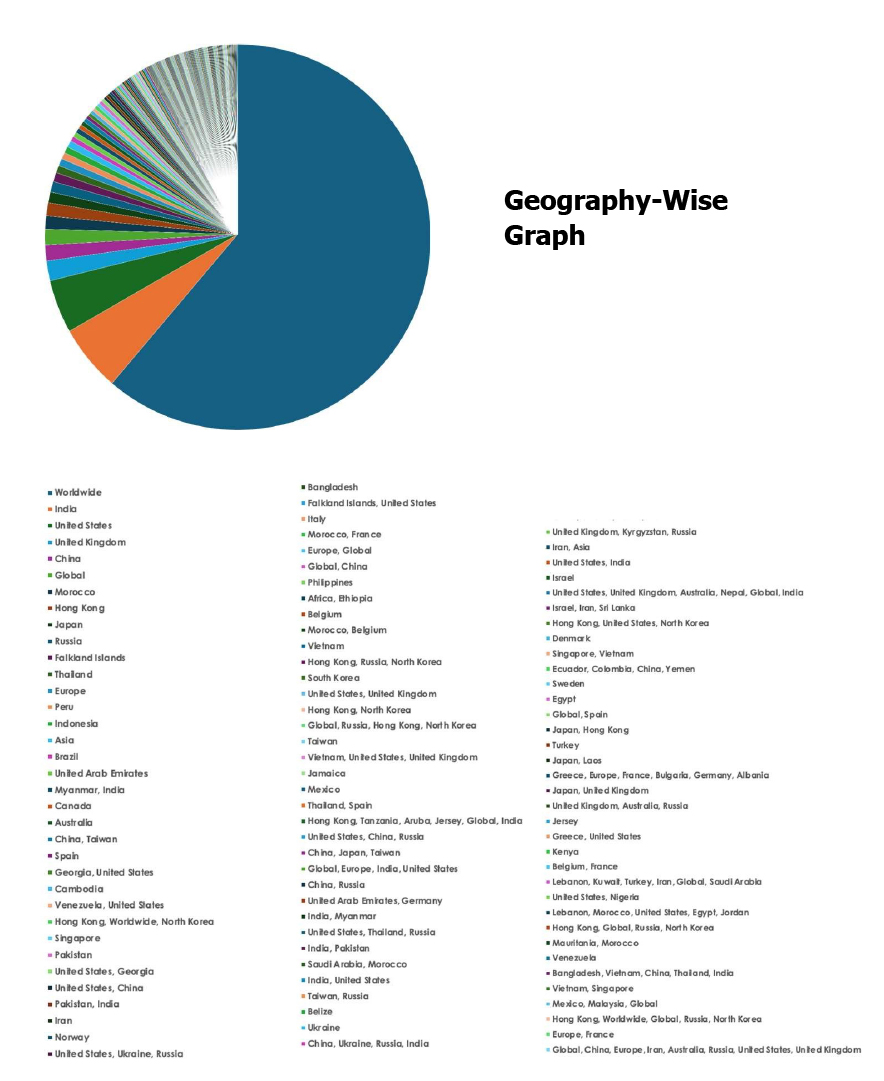
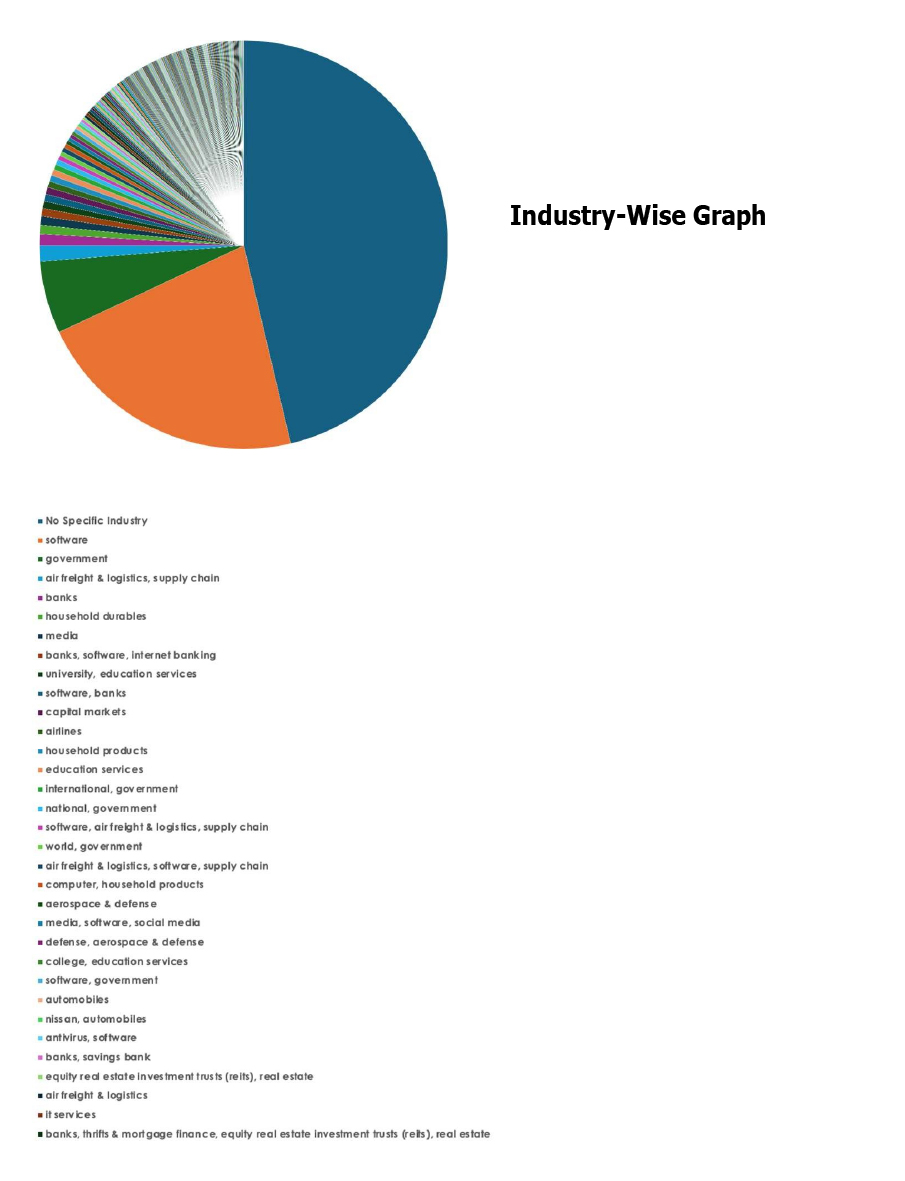
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.


For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.