


CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This covers a variety of topics that can be pertinent to your company, including technology, geography, and industries.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found Benzona Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Benzona Ransomware
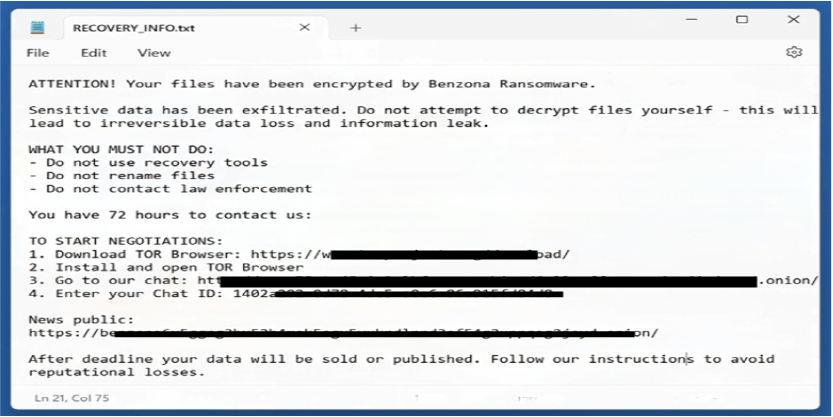
Researchers have identified Benzona as a ransomware strain that encrypts victims’ files and appends the “.benzona” extension to each affected item. Once active, it locks user data using strong cryptographic methods and prevents access without a decryption key controlled by the attackers. During infection, it also generates a ransom note named “RECOVERY_INFO.txt”, flags all encrypted files with the new extension to reinforce that control over the system has been taken. Removal of the malware stops further encryption, but already-locked files will be difficult to restored without external backups.

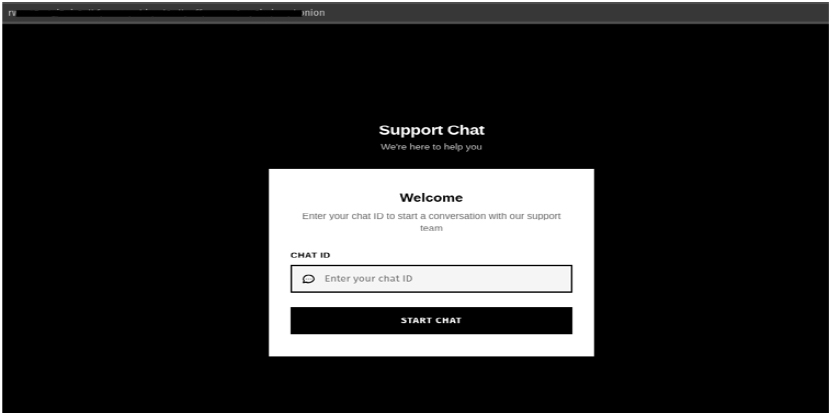
The ransomware’s note instructs victims to communicate with the attackers through a TOR-based chat portal, providing steps for downloading the TOR browser and entering a unique chat ID. In the message, the operators claim that files have been both encrypted and exfiltrated, warn victims not to rename files or use recovery tools, and threaten to leak or sell stolen data if contact is not made within 72 hours. The note emphasizes avoiding law enforcement and directs victims toward the attackers’ negotiation page, reinforcing pressure through statements about reputational risk and deadline based consequences.
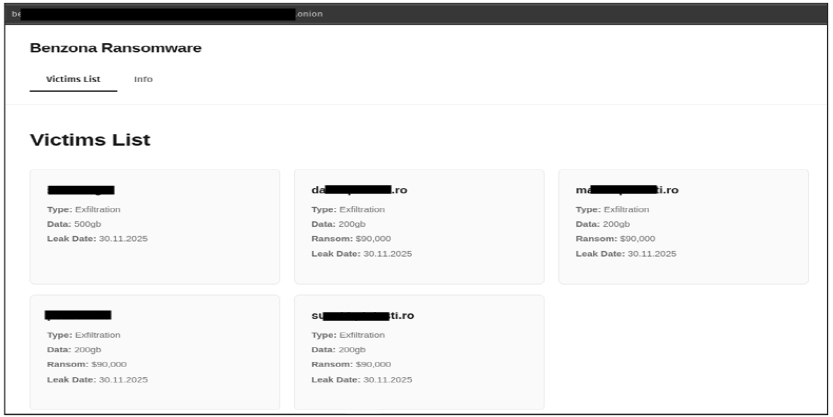
The Benzona extortion site functions as the group’s public-facing pressure mechanism, where stolen data and victim details are displayed to intensify coercion during negotiations. The site lists organizations alongside exfiltrated data volumes, ransom demands, and scheduled leak dates, using this information to signal the attackers’ willingness to publish or sell compromised material if payment is not made. Structured similarly to other double‑extortion platforms, it provides a centralized space for showcasing breaches, validating the threat to new victims, and reinforcing the group’s operational credibility within the criminal ecosystem.
Following are the TTPs based on the MITRE Attack Framework.
| Tactic | Technique ID | Technique Name |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1106 | Native API |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Collection | T1560 | Archive Collected Data |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Impact | T1485 | Data Destruction |
| Impact | T1489 | Service Stop |
| Impact | T1490 | Inhibit System Recovery |
Relevancy and Insights:
ETLM Assessment:
CYFIRMA’s assessment indicates that Benzona ransomware operates squarely within the double-extortion model, leveraging both data encryption and data theft to pressure victims into compliance. Its tactics mirror established ransomware-as-a-service (RaaS) behaviors, including fast deployment, automated file-locking mechanisms, TOR-based negotiation channels, and structured exfiltration processes intended to amplify leverage. Within the broader threat environment, Benzona fits the ongoing shift toward data driven coercion, layered extortion methods, and the use of public leak platforms all hallmarks of financially motivated actors that rely on scalable infrastructure and controlled communication pathways to optimize their operations.
Industry analyses of similar ransomware ecosystems indicate that threats functioning in this manner may continue gravitating toward deeper data-centric extortion, increased automation across the intrusion and encryption chain, and greater use of anonymized negotiation environments to obscure operator identity. As data theft becomes a primary pressure point, groups employing models comparable to Benzona are likely to reinforce their leak-site frameworks, broaden victim selection across varied sectors, and refine their coercive tactics to heighten reputational impact consistent with the prevailing trajectory observed across modern cyber-extortion campaigns.
Sigma Rule
title: Shadow Copies Deletion Using Operating Systems Utilities
tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490
logsource:
category: process_creation
product: windows
detection:
selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’
selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’
selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’
selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet
selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’
selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’
CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*)
falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand)
level: high
(Source: Surface Web)
Indicators of Compromise
Kindly refer to the IOCs section to exercise control of your security systems
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Type: Remote Access Trojan (RAT)
Objective: Credential Theft, Data Exfiltration, System Profiling, Remote Access
Target Technologies: Android OS
Target Industry: Financial Sector (Banks, Payment Services, Cryptocurrency Exchanges/Wallets)
Target Geography: Global
Active Malware of the Week
This week “Albiriox” is trending.
Overview of Albiriox Malware
Albiriox is a newly emerging Android remote access Trojan (RAT) sold under a Malware-as-a-Service (MaaS) model on underground cybercrime forums. It first appeared in September 2025 in a closed phase limited to high-reputation forum members and quickly evolved into a publicly accessible service by October 2025. Its core functionality blends VNC-style remote access with credential-stealing overlays, giving attackers both control and visibility over victim activity. Activity on these forums, along with language used and supporting infrastructure, strongly suggests that Russian-speaking threat actors are likely responsible for developing and operating Albiriox. Its distribution relies on deceptive applications and well-crafted social engineering schemes, enabling attackers to bypass basic security checks.
Once installed, Albiriox provides the operator with full, real-time control of an infected device, allowing fraudulent actions to be carried out directly inside legitimate banking or cryptocurrency applications. This method, known as On-Device Fraud, significantly complicates detection because all actions originate from the victim’s own device and appear authentic. The malware also uses various overlay screens to conceal unauthorized activity or prompt users to grant additional permissions.
Despite being relatively new, Albiriox is designed to target a wide range of financial and cryptocurrency applications, underscoring its operators’ broader ambitions and the potential for significant impact on Android users who rely on these services. Its rapid development, combined with built-in tools designed to evade security solutions, positions it as a growing concern for financial institutions. The rise of such tools underscores the need for stronger, behavior-based mobile security mechanisms capable of identifying early signs of device compromise and preventing fraudulent actions before they occur.
Attack Method
In this campaign, Albiriox relies on a socially engineered delivery chain that begins with deceptive mobile applications distributed through targeted phishing pages. In the early stages of the campaign victims are lured through SMS or messaging-platform links that lead to websites impersonating trusted brands, such as regional retail or service apps. These fake pages convincingly replicate legitimate play stores, encouraging users to download what appears to be an authentic application. Once the victim installs the decoy app, the hidden dropper immediately initiates the second stage of the attack by requesting permissions that allow installations from unknown sources, ultimately enabling the silent deployment of the Albiriox payload.
After installation, Albiriox establishes a covert foothold on the device by activating accessibility-based controls and background services. These features allow the malware to quietly prepare the environment for remote manipulation without alerting the user. The attackers can then initiate full device takeover using a built-in remote access module that streams the screen in real time and accepts operator commands. Through this mechanism, the threat actors navigate the victim’s banking or cryptocurrency apps as though they were using the device themselves, enabling seamless execution of unauthorized transactions.
To strengthen its operational cover, Albiriox employs overlay screens that mimic system processes or obscure the device display entirely. These overlays are used to conceal fraudulent actions performed during remote sessions or to prompt the victim for additional permission. By blending technical control, visual deception, and interactive manipulation, the attackers achieve a smooth and highly effective on-device fraud workflow, significantly reducing the chance of user suspicion or automated security detection.
Following are the TTPs based on the MITRE Attack Framework for Mobile
| Tactic | Technique ID | Technique Name |
| Initial Access | T1660 | Phishing |
| Persistence | T1398 | Boot or Logon Initialization Scripts |
| Privilege Escalation | T1404 | Exploitation for Privilege Escalation |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Credential Access | T1414 | Clipboard Data |
| Credential Access | T1417 | Input Capture |
| Discovery | T1418 | Software Discovery |
| Collection | T1430 | Location Tracking |
| Collection | T1409 | Stored Application Data |
| Command and control | T1429 | Audio Capture |
| Collection | T1437.001 | Application Layer Protocol: Web Protocols |
INSIGHTS
ETLM ASSESSMENT
From an ETLM perspective, CYFIRMA assesses that the emergence of Albiriox points toward a future in which mobile devices assume an increasingly central role in organizational risk. As employees continue to depend on smartphones for financial access, authentication, communication, and workflow integration, adversaries are likely to develop even more refined methods that blend seamlessly into normal device activity. This will make it progressively more difficult for enterprises to discern whether actions on a device originate from the legitimate user or from an attacker operating covertly in the background. Over time, this shift may compel organizations to adopt stronger mechanisms for validating mobile-initiated actions and to regard routine app interactions with heightened scrutiny. As personal and professional digital environments become further intertwined, Albiriox style campaigns may gradually erode confidence in everyday mobile usage, prompting both employees and enterprises to approach familiar device behaviors with increased caution.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Albiriox_IOCs
{
meta:
author = “CYFIRMA”
description = “Detects known IOCs associated with the Albiriox Android malware campaign”
date = “2025-12-01”
strings:
/* ———- APK Hashes ———- */
$sha256_1 = “070640095c935c245f960e4e2e3e93720dd57465c81fa9c72426ee008c627bf3”
$sha256_2 = “5e14181839816bbb4b55badc91f29d382e8d6f603eec2ed8f8b731c35def6b59”
$sha256_3 = “630b047722d553495def3b8e744f2f621209e1a77389c09a9a972eeb243f9ed8”
$sha256_4 = “a0c9d6eb1932c96a11301c00cf96ce9767fb11401e090f215f972df06b09a878”
/* ———- Malicious Domains ———- */
$d1 = “google-app-download.download”
$d2 = “google-get.download”
$d3 = “google-aplication.download”
$d4 = “play.google-get.store”
$d5 = “google-app-get.com”
$d6 = “google-get-app.com”
$d7 = “google-app-install.com”
/* ———- C2 Server ———- */
$ip1 = “194.32.79.94”
condition:
any of ($sha256*) or
any of ($d*) or
any of ($ip*)
}
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
Key Intelligence Signals:
o Cl0p Ransomware– One of the ransomware groups.
o Dire Wolf Ransomware – One of the ransomware groups.
o Malware – Albiriox
Lazarus Group Continuously Evolving its Attack Surface
About the Threat Actor
The Lazarus Group, active since at least 2009, is a highly sophisticated cyber-espionage and financially motivated threat actor linked to the North Korean government, specifically associated with Lab 110, a unit within DPRK military intelligence. The group maintains a dedicated malware development and exploitation team, enabling rapid refinement of tools, implants, and intrusion techniques.
In recent years, Lazarus has intensified its focus on cryptocurrency exchanges and financial platforms, reflecting its dual mandate of revenue generation and strategic intelligence collection. Its operations consistently target high-value firms worldwide, underscoring the group’s emphasis on monetization, data theft, and long-term espionage campaigns.
Details on Exploited Vulnerabilities
| CVE ID | Affected Products | CVSS Score | Exploit Links |
| CVE-2021-44228 | Apache Log4j | 10.0 | link1, link2,link3, link4, link5, link6, link7, link8, link9, link10, link11, link12, link13, link14,link15, link16 |
| CVE-2023-4966 | Citrix NetScaler ADC / Gateway | 7.5 | link |
| CVE-2023-22518 | Atlassian Confluence | 9.8 | link |
| CVE-2017-0147 | Microsoft Windows (Various Versions) |
7.5 | link1, link2 |
| CVE-2017-11882 | Microsoft Office (Various Versions) |
7.8 | link |
| CVE-2017-0199 | Microsoft Office & Windows | 7.8 | link |
| CVE-2023-36884 | Microsoft Windows | 7.5 | ————- |
| CVE-2023-42793 | JetBrains TeamCity | 9.8 | link1 |
| CVE-2024-3094 | XZ Utils (5.6.0 and 5.6.1) | 10.0 | ————- |
| CVE-2017-10271 | Oracle WebLogic Server | 7.5 | link1, link2 |
| CVE-2021-21551 | Dell systems with dbutil_2_3.sys driver | 7.8 | link1, link2 |
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1591.004 | Gather Victim Org Information: Identify Roles |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Resource Development | T1608.002 | Stage Capabilities: Upload Tool |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1587.002 | Develop Capabilities: Code Signing Certificates |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1584.004 | Compromise Infrastructure: Server |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.004 | Obtain Capabilities: Digital Certificates |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1566.003 | Phishing: Spear phishing via Service |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1106 | Native API |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Persistence | T1505.004 | Server Software Component: IIS Components |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1574.001 | Hijack Execution Flow: DLL |
| Persistence | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1098 | Account Manipulation |
| Privilege Escalation | T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Privilege Escalation | T1574.001 | Hijack Execution Flow: DLL |
| Privilege Escalation | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Privilege Escalation | T1134.002 | Access Token Manipulation: Create Process with Token |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Defense Evasion | T1134.002 | Access Token Manipulation: Create Process with Token |
| Defense Evasion | T1218 | System Binary Proxy Execution |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.003 | Indicator Removal: Clear Command History |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1202 | Indirect Command Execution |
| Defense Evasion | T1036.003 | Masquerading: Rename Legitimate Utilities |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1036.008 | Masquerading: Masquerade File Type |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1027.007 | Obfuscated Files or Information: Dynamic API Resolution |
| Defense Evasion | T1027.009 | Obfuscated Files or Information: Embedded Payloads |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1220 | XSL Script Processing |
| Defense Evasion | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Defense Evasion | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Defense Evasion | T1622 | Debugger Evasion |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1221 | Template Injection Authentication Process: Conditional Access Policies |
| Defense Evasion | T1574.001 | Hijack Execution Flow: DLL |
| Defense Evasion | T1574.013 | Hijack Execution Flow: KernelCallbackTable |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1078 | Valid Accounts |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1656 | Impersonation |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1497.001 | Virtualization/Sandbox Evasion: System Checks |
| Discovery | T1497.003 | Virtualization/Sandbox Evasion: Time Based Evasion |
| Discovery | T1087.002 | Account Discovery: Domain Account |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1046 | Network Service Discovery |
| Discovery | T1622 | Debugger Evasion |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1124 | System Time Discovery |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1021.004 | Remote Services: SSH |
| Lateral Movement | T1534 | Internal Spearphishing |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1560 | Archive Collected Data |
| Collection | T1560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1560.002 | Archive Collected Data: Archive via Library |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1557.001 | Adversary-in-the-Middle: LLMNR/NBT-NS Poisoning and SMB Relay |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1001.003 | Data Obfuscation: Protocol or Service Impersonation |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1090.001 | Proxy: Internal Proxy |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1008 | Fallback Channels |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1104 | Multi-Stage Channels |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Exfiltration | T1048.003 | Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
| Impact | T1561.001 | Disk Wipe: Disk Content Wipe |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1489 | Service Stop |
| Impact | T1485 | Data Destruction |
| Impact | T1529 | System Shutdown/Reboot |
| Impact | T1491.001 | Defacement: Internal Defacement |
Latest Developments Observed
The threat actor is suspected to have flooded the npm registry with an additional 197 malicious packages over the past month. These packages are designed to deliver a new variant of OtterCookie, which consolidates capabilities observed in BeaverTail and earlier OtterCookie iterations. The malware’s objective appears to be data theft, including clipboard contents, keystrokes, screenshots, browser credentials, documents, cryptocurrency wallet data, and seed phrases.
ETLM Insights
Lazarus Group operates with a dual strategic mandate driven by the DPRK’s national priorities:
Their operations are shaped by DPRK’s long-term geopolitical objectives: economic survival, military modernization, and strategic deterrence.
From an ETLM standpoint, Lazarus aligns with:
Lazarus Group is expected to:
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
YARA Rules
rule NPM_Suspicious_Package_SupplyChain_Activity
{
meta:
description = “Flags suspicious npm packages showing characteristics often seen in malicious supply chain attacks”
author = “CYFIRMA”
malware_family = “Generic npm supply-chain threat”
reference = “Behavior-based detection only”
strings:
// Obfuscated JavaScript indicators
$obs1 = /eval\s*\(\s*function/i
$obs2 = /function\s*\(\)\s*\{\s*return\s*function/i
$obs3 = /while\s*\(\s*true\s*\)/
// Clipboard harvesting / system interaction
$clip = “clipboard” ascii nocase
$keylog1 = “keydown” ascii nocase
$keylog2 = “keypress” ascii nocase
$screenshot = “screenshot” ascii nocase
// Browser credential access attempts
$cred1 = “password” ascii nocase
$cred2 = “loginData” ascii nocase
$cred3 = “Local Storage” ascii nocase
$cred4 = “IndexedDB” ascii nocase
// Suspicious postinstall scripts
$post1 = /postinstall[\”\’]?\s*:/ nocase
$curl = /curl\s+https?:\/\// nocase
$wget = /wget\s+https?:\/\// nocase
// Unexpected embedded binaries or base64 blobs
$b64a = /[A-Za-z0-9+\/]{200,}={0,2}/
$exe = “MZ” // Windows binary header
$elf = { 7F 45 4C 46 } // Linux ELF binary header
condition:
// Trigger on multiple suspicious indicators
( #obs1 + #obs2 + #obs3 >= 1 )
or ( $post1 and ( $curl or $wget ) )
or ( $clip or $keylog1 or $keylog2 or $screenshot )
or ( #cred1 + #cred2 + #cred3 + #cred4 >= 2 )
or ( $b64a and ( $exe or $elf ) )
}
Strategic Recommendations
Management Recommendations
Tactical Recommendations
Nato considers ‘more aggressive’ response to Russia’s hybrid warfare
NATO’s top military officer has signaled that the alliance is actively exploring a more aggressive and proactive response to Russia’s campaign of hybrid warfare, including cyber-attacks, sabotage, and airspace incursions. Admiral Giuseppe Cavo Dragone, chairman of NATO’s Military Committee, told the media that the alliance is moving beyond its traditionally reactive posture. “On cyber, we are kind of reactive. Being more aggressive or being proactive instead of reactive is something that we are thinking about,” he said. He noted that a pre-emptive strike could, in certain circumstances, be classified as a defensive action, though it remains “further away from our normal way of thinking and behaviour.” The debate has intensified following a series of incidents across Europe—many attributed to Russia or suspected to be Russian-linked—including the severing of undersea cables in the Baltic Sea, widespread cyber-attacks, and drone intrusions. Eastern European members in particular have pushed for NATO to adopt offensive countermeasures, especially in cyberspace where many allies possess significant capabilities.
Dragone acknowledged the challenges: “Being more aggressive compared with the aggressivity of our counterpart could be an option,” but stressed complications around legal and jurisdictional frameworks and deciding which actor would execute any response. He highlighted that NATO operates under far stricter ethical, legal, and jurisdictional constraints than Moscow, placing the alliance in “a harder position.” Russia’s foreign ministry swiftly condemned the admiral’s remarks as “extremely irresponsible” and evidence of NATO’s “readiness to continue moving towards escalation.” Dragone concluded that the core objective remains deterrence, whether achieved through retaliation or pre-emptive measures, and warned that future Russian pressure may force the alliance to confront these difficult choices more urgently.
ETLM Assessment:
As noted in last year’s CYFIRMA report, Europe has faced a surge in cyber-attacks and while definitive attribution remains complex, the sophistication of these attacks and the backdrop of geopolitical tensions strongly indicate Russian involvement. These attacks have targeted diverse organizations, causing widespread disruption and financial losses. Russia has solidified its position as a capable, motivated, and irresponsible cyber threat actor. Russian operatives have almost certainly escalated their cyber campaigns against Ukraine and its allies, aligning these operations with their military objectives and broader geopolitical ambitions.
Strained by the demands of an all-out war against Ukraine, Russia has increasingly outsourced cyber operations to privateers and other non-state actors. These groups, often beyond direct state control, introduce a heightened unpredictability to their activities. This trend is likely to persist, as the Kremlin grants these actors greater latitude. From Moscow’s perspective, fostering global instability serves to divert attention from its aggression in Ukraine, further stretching the resources of those who oppose it. According to public diplomacy, NATO stance on counter measures, especially in the cyber domain, might just be changing and we are likely to see an uptick in cyber action going both ways.
Cl0p Ransomware Impacts Mazda Motor Corporation
Summary:
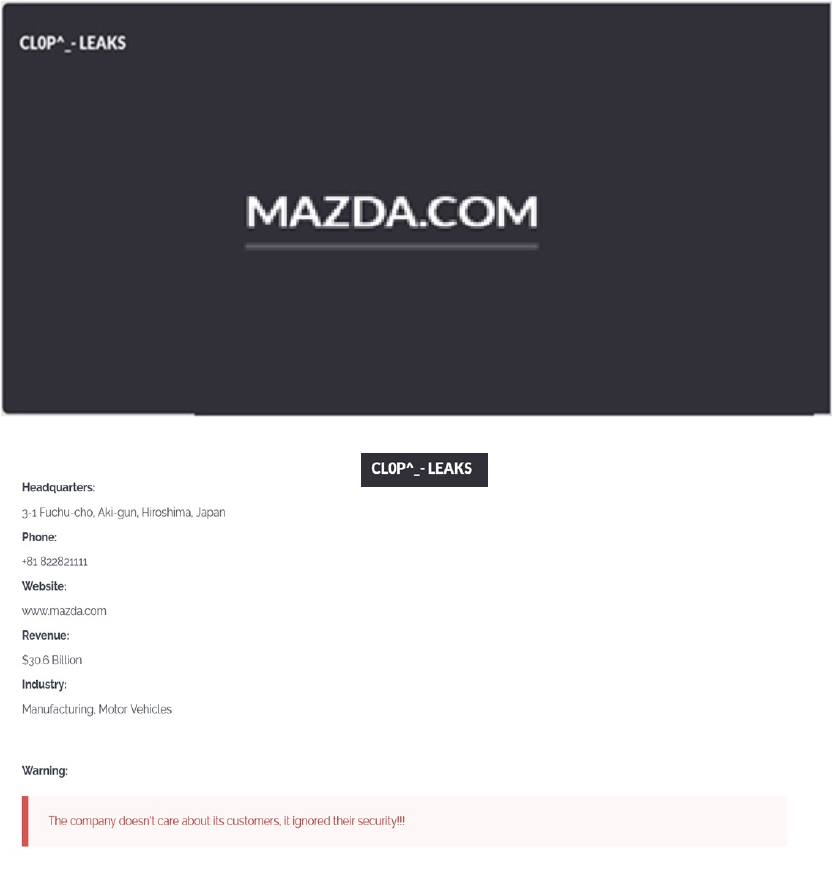
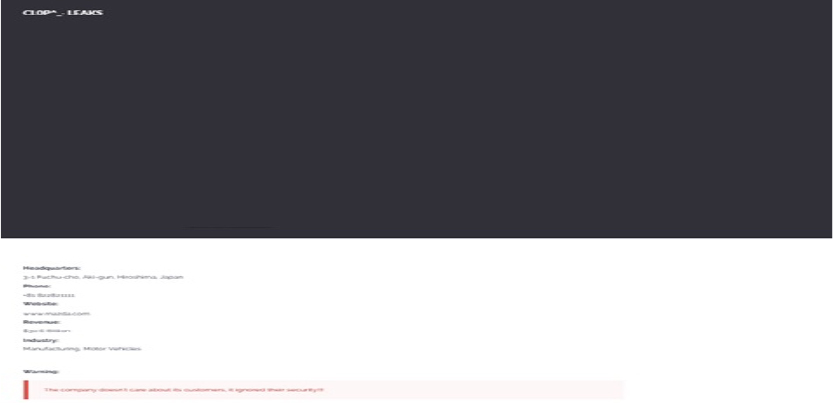
CYFIRMA observed in an underground forum that a company from Japan, Mazda Motor Corporation (https[:]//www[.]mazda[.]com/), was compromised by Cl0p Ransomware. Mazda Motor Corporation is a Japanese multinational automaker known for its production of stylish, high-quality cars and sports utility vehicles with innovative technology. The compromised data contains confidential and sensitive information belonging to the organization.
The following screenshot was observed published on the dark web:
Relevancy & Insights:

ETLM Assessment:
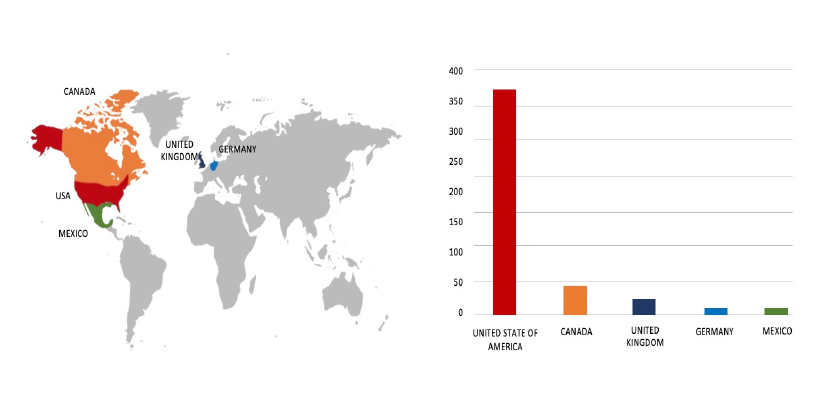
According to CYFIRMA’s assessment, Cl0p ransomware remains one of the most significant and disruptive threats in the current cybercrime landscape, particularly evident through its unprecedented volume of attacks and innovative extortion tactics witnessed in 2025. The Cl0p campaign reinforces the urgent need for holistic security strategies: rapid vulnerability management, robust incident detection, thorough supply chain risk assessments, and strong contingency plans for data exfiltration scenarios.
Dire Wolf Ransomware Impacts K.M. Packaging
Summary:
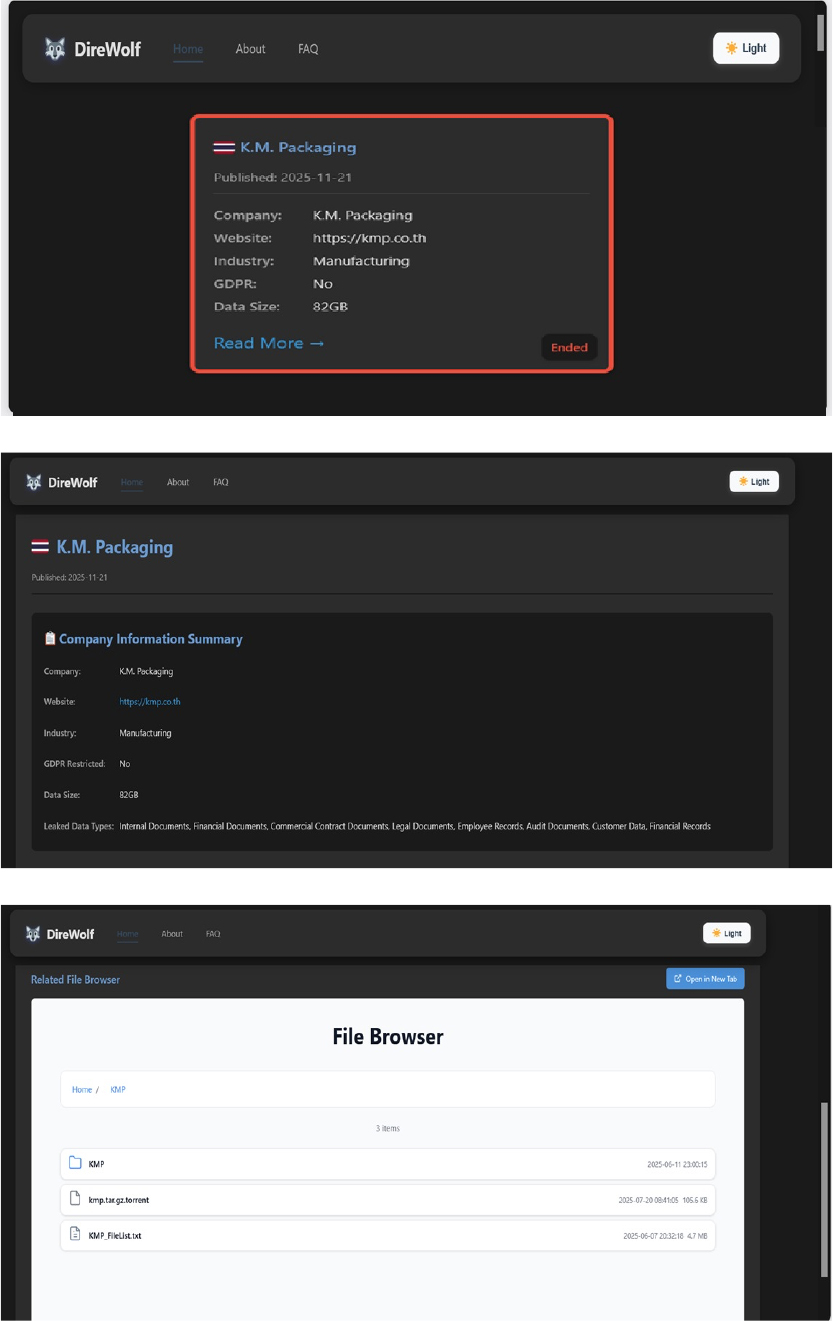
CYFIRMA observed in an underground forum that a company from Thailand, K.M. Packaging (https[:]//kmp[.]co[].th), was compromised by Dire Wolf Ransomware. K.M. Packaging Public Company Limited is a leading Thai manufacturer of eco-friendly paper packaging for food and beverages. The exposed dataset includes internal documentation, financial and audit records, commercial and legal contracts, employee files, and customer information, with the total volume of compromised data estimated at approximately 82 GB.
[MISSING IMAGE: , ]The following screenshot was observed published on the dark web:[MISSING IMAGE:,]
Relevancy & Insights:
ETLM Assessment:
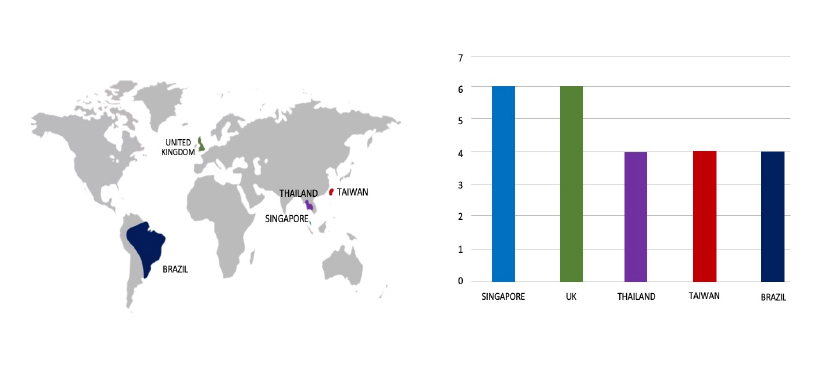
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion-based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
Vulnerability in Werkzeug
Relevancy & Insights:
The vulnerability exists due to the “safe_join” function, which allows path segments with Windows device names.
Impact:
A remote attacker can cause the reading of the file to hang indefinitely.
Affected Products:
https[:]//github[.]com/pallets/werkzeug/security/advisories/GHSA-hgf8-39gv-g3f2
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED PRODUCTS OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
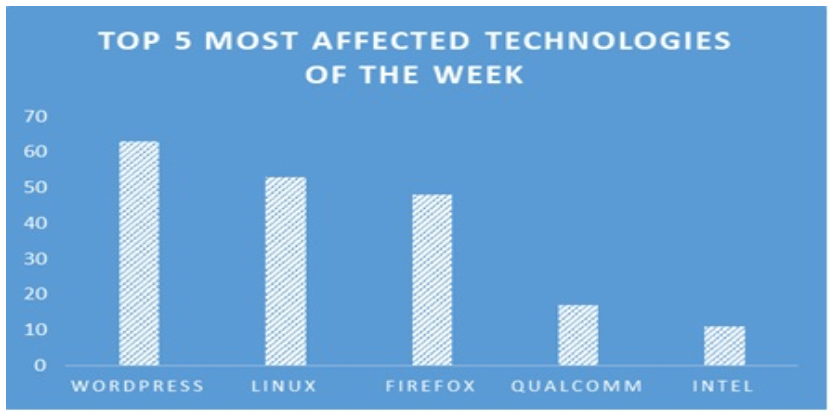
ETLM Assessment:
Improper Handling of Windows Device Names in Werkzeug can introduce significant risks to application security and user privacy. This vulnerability has the potential to affect a wide range of industries that rely on Python-based web frameworks, including financial services, manufacturing, healthcare, and public sector organizations. Ensuring the security of Werkzeug—often a core component in Flask and other Python web applications—is essential for protecting critical business data, backend services, and interconnected systems across diverse environments.
INC Ransomware attacked and published the data of Southern Lion Sdn. Bhd
Summary:
Recently, we observed that the INC Ransomware attacked and published the data of Southern Lion Sdn. Bhd (https[:]//www[.]southernlion[.]com[.]my/) on its dark web website. Southern Lion Sdn. Bhd. is a manufacturer and distributor of household & personal care products (Fast-Moving Consumer Goods (FMCG)) like fabric care, oral care, beauty care, and home care based in Malaysia. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
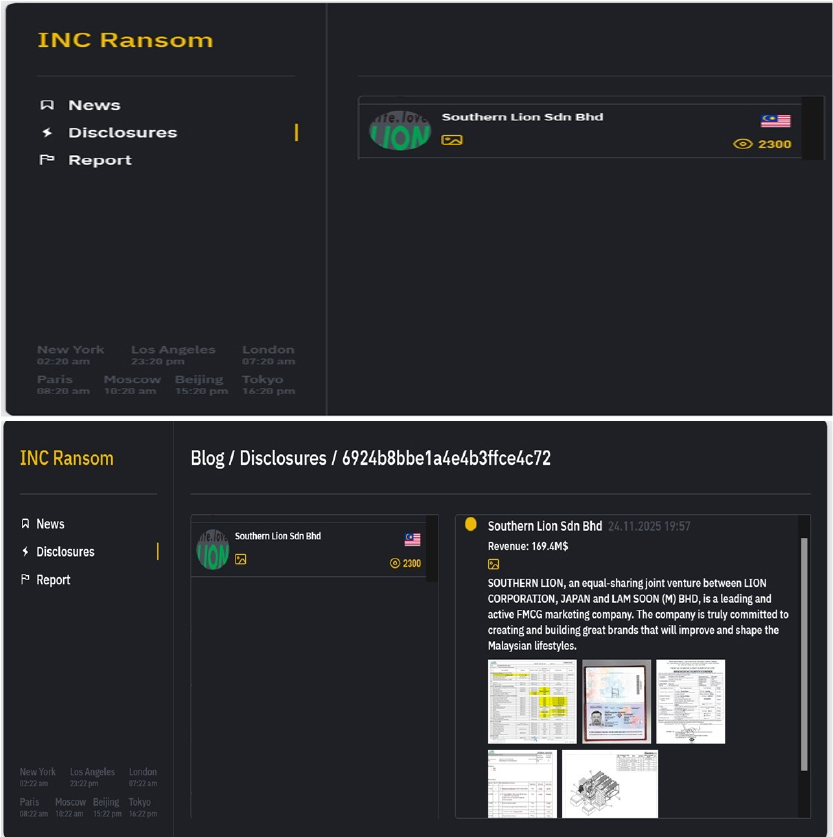
Relevancy & Insights:
INC Ransomware, also known as Incransom, is a cyber threat that emerged in mid-2023. Incransom uses strong encryption algorithms to lock files, making recovery without the decryption key virtually impossible. The ransomware typically appends specific file extensions to encrypted files, signalling that they have been compromised.
ETLM Assessment:
Based on recent assessments by CYFIRMA, INC Ransomware represents a significant threat within the evolving landscape of ransomware attacks. Its use of strong encryption methods and double extortion tactics highlights the increasing sophistication of cybercriminal operations. Organizations are advised to enhance their cybersecurity measures by implementing robust defenses against phishing attacks, maintaining updated security protocols, and monitoring for unusual network activity to mitigate risks associated with this and other ransomware variants. Continuous vigilance is essential to protect against the threats posed by emerging ransomware groups like INC Ransomware.
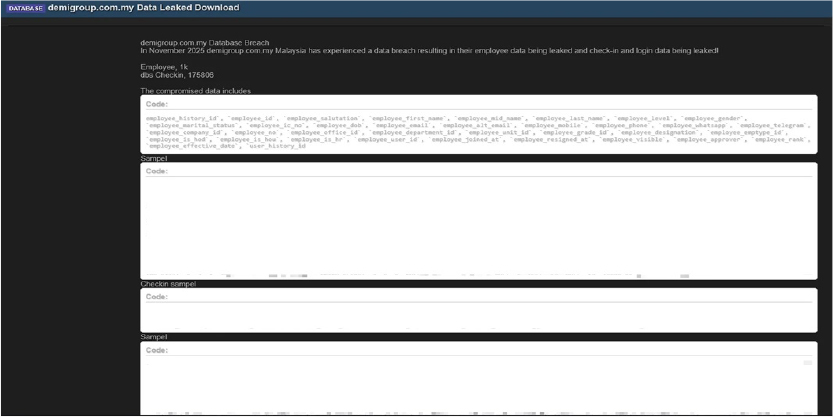
Demi Group Data Advertised on a Leak Site
Summary: The CYFIRMA research team has identified that a threat actor known as “KaruHunters” is alleging responsibility for the compromise of Demi Group, a Malaysian conglomerate that operates multiple subsidiaries, including ProOffice, Demi Couture, and ProView. The alleged breach, said to have taken place in November 2025, reportedly led to the exposure of sensitive internal databases, with detailed employee records and extensive activity logs exfiltrated.
The allegedly compromised data contains approximately 1,000 employee profiles and over 175,000 check-in/login records. According to the leaked samples, the exposed information includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
MagicSeller Data Advertised on a Leak Site
Summary:
The CYFIRMA Research team observed that magicseller[.]co[.]kr, a digital platform based in South Korea, has allegedly been compromised, resulting in the sale of a significant database on a cybercrime forum. The threat actor claims to be in possession of 500,000 user records related to the site. The actor has provided a sample of the data to verify the authenticity of the leak, although the sample provided appears to contain Portuguese language content, suggesting potential discrepancies in the data’s origin or a specific regional subset of the service.
According to the actor, the allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
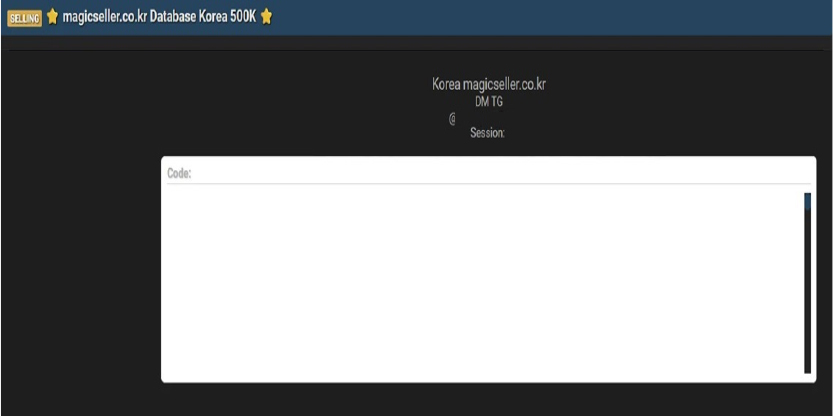
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “KaruHunters” is a highly active and sophisticated group specializing in data leaks. Numerous credible sources attribute multiple security breaches to this group, involving unauthorized access to systems and the illicit sale of stolen data on dark web marketplaces. KaruHunters’ operations highlight the persistent and evolving nature of cyber threats emerging from underground forums. These incidents underscore the critical importance for organizations to enhance their cybersecurity posture through continuous monitoring, leveraging advanced threat intelligence, and adopting proactive defense strategies to protect sensitive data and vital infrastructure.
Recommendations: Enhance the cybersecurity posture by
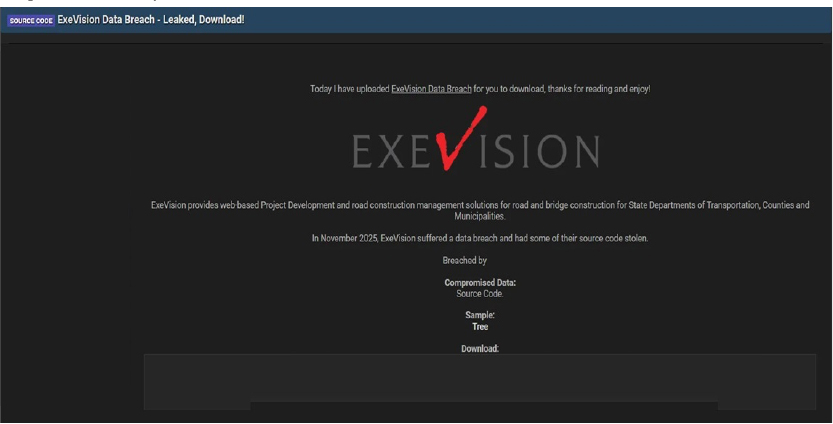
The CYFIRMA Research team observed that ExeVision, a company delivering web-based project development and road construction management solutions for State Departments of Transportation in Jordan, was allegedly compromised. The incident was disclosed on a dark web forum by a threat actor known as 888, who claims the breach occurred in November 2025 and resulted in the theft of the company’s source code.
The allegedly compromised data reportedly consists of the company’s proprietary source code. A file tree released by the actor as proof of the breach indicates the exposure of several critical development repositories and application directories, including:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
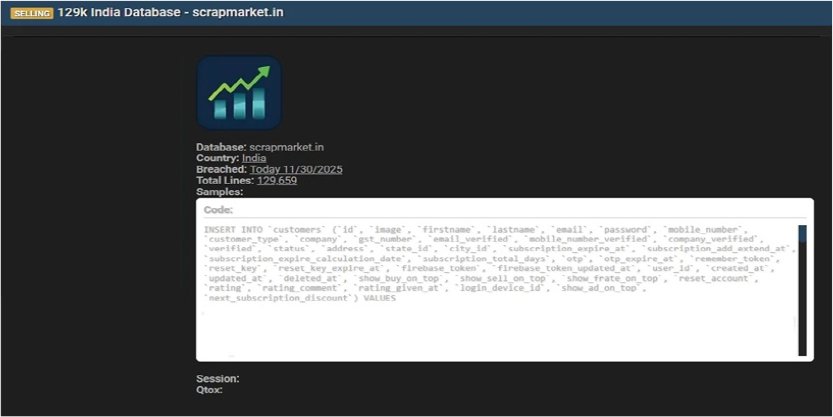
The CYFIRMA Research team observed that ScrapMarket[.]in, an Indian B2B platform facilitating the buying and selling of scrap materials, has allegedly been compromised by an unauthorized party. A database containing approximately 129,659 lines of user data has been listed for sale on a cybercrime forum. The breach, dated November 30, 2025, appears to affect a significant portion of the platform’s user base, including individual sellers and scrap dealers.
According to the samples provided in the leak, the compromised database contains sensitive user information. The allegedly compromised data includes:
The authenticity of this breach remains unverified at the time of reporting, as the claim originates solely from the threat actor.
STRATEGIC RECOMMENDATION
MANAGEMENT RECOMMENDATION
TACTICAL RECOMMENDATION
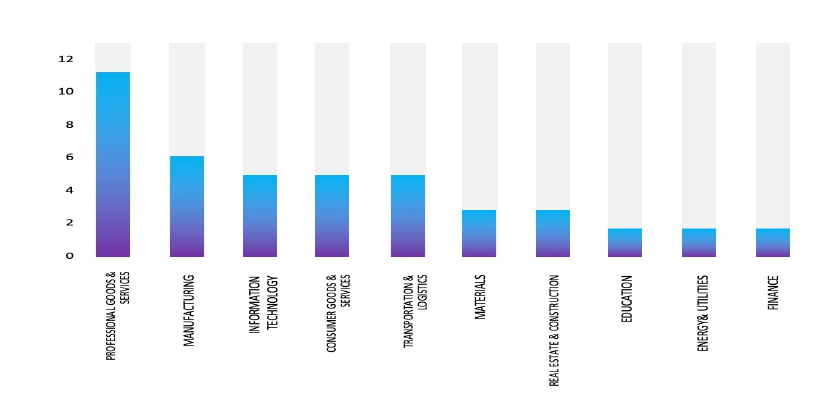
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
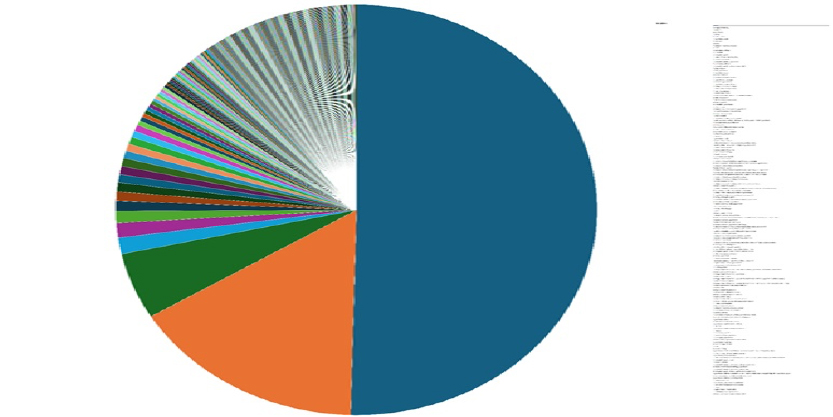
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, technology, please access DeCYFIR.